Abstract
Twin-field QKD (TF-QKD) protocols allow for increased key rates over long distances when compared to standard QKD protocols. They are even able to surpass the PLOB bound without the need for quantum repeaters. In this work, we revisit a previous TF-QKD protocol and derive a new, simple, proof of security for it. We also look at several variants of the protocol and investigate their performance, showing some interesting behaviors due to the asymmetric nature of the protocol.
1. Introduction
Quantum key distribution (QKD) allows two parties to establish a shared secret key that is secure even against computationally unbounded adversaries. This is a task that is impossible to achieve using classical communication alone, unless computational assumptions are made on the adversary’s capabilities. However, QKD has several limitations, especially in terms of distance. See [1,2,3] for a general survey on QKD.
In general, the key-rate of a QKD system is severely restricted by the total transmittance of the channel between parties. Several strategies can mitigate this, including trusted node networks [4,5,6] and quantum repeaters [7,8,9]. Quantum network research, in general, is a rapidly growing topic both for QKD [10] and the more general Quantum Internet [11] (the latter of which can support QKD, but also other applications such as distributed computing [12,13,14] and distributed quantum sensing [15,16,17,18]). However, an interesting third alternative for boosting QKD distances are so-called twin-field QKD (TF-QKD) protocols [19,20,21,22,23,24] which can even beat the PLOB bound [25].
Proving security of QKD protocols (TF or otherwise) is an important task, and developing novel proof techniques can be vital for advancing the state of the art (in addition to providing an additional proof of security which, itself, is interesting). Since TF-QKD can already be demonstrated experimentally over long distances [26,27] (even up to over 800 km [28]), it is important to study rigorously the underlying security proofs for these systems as they are applicable using today’s technology. Doing so affords researchers more mathematical tools to handle new protocols, and may even lead to improvements in performance under certain conditions as newer techniques may provide more optimistic security results in some cases (or, more formally, more optimistic bounds on the quantum min entropy between the users and an adversary system).
In this paper, we re-visit a TF-QKD protocol introduced in [19] and develop an entirely new proof of security using methods of quantum sampling as introduced in [29], and sampling-based entropic uncertainty relations [30]. Our proof is fairly simple and can be used potentially for other TF-QKD protocols. In particular, our method might be easily adapted to the sending-not-sending TF protocol [31].
While our new proof does not improve on previously produced key-rates, we feel it is still interesting to develop alternative methods. Indeed, by now numerous proofs of security have been performed for BB84, all leading to the same result; yet different methods can be applied to different protocols later “down the road”, and thus developing alternative techniques is an important area of research in quantum cryptography. We also make two small changes to the original protocol (which our new security proof can handle easily) and show some interesting behaviors of these new protocols, including improved performance. We are not aware of these two variants in the current literature, thereby making them a second contribution of this paper.
2. Preliminaries
We now introduce some notation and other preliminary concepts and technical lemmas that will be important in our work later. Let be a d-dimensional alphabet. Given a word and a subset , we write to denote the substring of q which is indexed by t and to mean the substring indexed by the complement of t. If t is a singleton , we often simply write to represent the i’th character of q.
Given and two real numbers, x and y, we write the following:
Given a word and a particular character , we write to denote the number of times a appears in the word q:
We use to denote the number of times a and b appear in q:
Let X be a random variable taking value , with probability . Then, denotes the Shannon entropy of X, namely . All logarithms in the paper are base two, unless otherwise specified. We use to denote the binary Shannon entropy, defined as .
A quantum state or density operator is a Hermitian positive semi-definite operator of unit trace, acting on some Hilbert space . If acts on , we write to denote the quantum state resulting from a partial trace over E, namely . This notation is similar for states acting on additional Hilbert spaces.
The Bell basis [32,33,34] is spanned by states :
where and are the Hadamard basis states, . Given a word , we write to denote .
Given a density operator , we write to be the von Neumann entropy of defined as . The conditional quantum min entropy is defined as follows [35]:
where is used to indicate that the operator is positive semi-definite. The smooth conditional min entropy, denoted as , is defined as follows [35]:
where the supremum is over all density operators such that , where is the trace distance of operator A.
Quantum min entropy is a vital quantity in quantum cryptography as it relates directly to the number of uniform random secret bits one may extract from a quantum state [35]. In particular, given where the A register is classical and the E register is quantum, privacy amplification may be used to extract a uniform secret bit string. Let be the result after applying the privacy amplification process to . Then, it holds the following [35]:
In particular, after privacy amplification, the resulting output is almost a uniform random ℓ-bit string, independent of Eve’s system. To determine a suitable size for ℓ, one only need to measure the min entropy of the state before privacy amplification. For a given , the final key is said to be secure.
Quantum min entropy has a number of useful properties that we will require later. First, given a state of the form (i.e., a state classical on Z), the following holds:
The following lemma allows us to bound the entropy in a state after performing a certain type of quantum operation on it, if we know the min entropy in a suitable state that is close in trace distance:
Lemma 1
(from [36]). Let ρ and σ be two quantum states and be some CPTP map that acts as follows:
Then, the following holds:
where the probability is over the outcome x and .
Finally, the following lemma allows us to bind the min entropy of a superposition of Bell states (the lemma is found in [37], though its proof uses techniques similar to those in [29,35] for bounding the min entropy of a general superposition state):
Lemma 2
(from [37] based on a proof in [29,35]). Let and
where recall is the number of times 1 and 3 appear in the string i. Let be the state resulting from taking , measuring all A particles in the Z basis and then tracing out the B register. Then, the following holds:
Quantum Sampling
Our new proof of security will utilize a quantum sampling framework introduced by Bouman and Fehr in [29]. In this section, we review some of their work that we will need later.
A classical sampling strategy over is a triple of algorithms. The first is a process that randomly chooses a subset with probability . The second is a guessing function . The third is a target function . The strategy will first choose a random subset and observe . Next, a guess is computed ; this guess should be close to the value of the target function, but evaluated on the unobserved portion of the string . That is, .
Formally, and a subset t should be fixed. Then, the set of good words should be defined as follows:
Recall, we wrote that if and only if . A good word is one where the guess is always close to the target for the given subset t. The classical error probability of the sampling strategy is defined simply as follows:
From this definition, it holds that for any word , if the sampling strategy is performed on it, the probability that it fails (namely that the guess is not close to the target) is at most .
The main result from [29] was to extend this to the quantum domain. A classical sampling strategy can be promoted to a quantum one in a natural way: given a quantum state where the A register consists of N qudits, each qudit of dimension d, one chooses a subset t and measures the qudits, indexed by t, in some d dimensional orthonormal basis . This measurement results in a classical outcome . Then, according to Bouman and Fehr’s main result, the unmeasured portion behaves like a superposition of words that are close to the guess (with respect to the given target). To formalize this, a basis B is fixed and the following space is considered:
This subspace is called the ideal subspace; a state within it is called an ideal state. Note that if one is given an ideal state (which only makes sense at the moment for a specific subset t according to this definition and thus the superscript index), and if one performs a measurement in the B basis on subset t resulting in outcome , the post measured state must collapse to one that is of the following form:
Namely, it must collapse to a superposition of words that are close to the observed value (with respect to the given guess and target functions). The states may not be necessarily ideal; however, the following theorem says that for any quantum state, one can define a collection of ideal states that are close in trace distance to the given state.
Theorem 1
(from [29], but re-worded slightly for our application and approach). Let , B be a d-dimensional orthonormal basis, and be a pure quantum state where the A register consists of N qudits, each qudit of dimension d. It is assumed that the dimension of each system N is known. Given a classical sampling strategy with error probability , there is a collection of ideal states , indexed by all subsets t such that :
Furthermore,
Note that, the original proof of Theorem 1 assumes Eve’s ancilla is finite dimensional. This is without loss of generality in our proof since we are considering ideal sources.
Before leaving this section, we discuss an important sampling strategy which we will use later. This strategy was analyzed in [37] for Bell states. Given a word , a subset of size m is uniformly chosen at random from all m size subsets of . The guess and target functions are simply . This defines the set of good words as follows:
where recall is the number of 1’s and 3’s in the word .
The failure probability of this strategy was proven in [37] as follows:
3. Protocol
We now describe the specific TF-QKD protocol, introduced in [19], which we will be analyzing. A single round of the quantum communication stage consists of the following operations:
- Alice prepares an entangled quantum state of the form:where the A register is a private qubit memory, while the a register consists of a single photon in either the vacuum state or a non-vacuum state . This register will be transmitted to a central server. Finally, q is a publicly known parameter chosen by Alice and Bob which will be optimized later.
- Similarly, Bob creates the state:The A and B registers are kept private, while the a and b registers are sent to a central server.
- The central server routes the incoming registers through a 50:50 beam splitter with two detectors, and . The outcome of the detectors are reported to Alice and Bob. The possible outcomes are “0” (meaning detector clicked); “1” (meaning detector clicked); “” (meaning no detector clicked); and “” (meaning any other outcome, such as both detectors clicking).
- If the server reported “” or “”, Alice and Bob discard this round and their private qubits. If the server reported “1”, Bob applies a Pauli Z gate to his private ancilla, thereby flipping the phase of the state.
- If the server reported either “0” or “1”, Alice and Bob should now hold a Bell state . They will measure their private qubits in either the Z or the X basis. Some of the Z and X measurements will be used to test the fidelity of the state; the remaining Z basis states will be used for key distillation.
We note that there is a simple change to the above protocol which turns it into an equivalent prepare-and-measure protocol where Alice and Bob do not need to measure or hold private memories. For more details on that, the reader is referred to the original paper [19].
To see why the above protocol works, consider a single round. At the beginning, Alice and Bob create the joint state:
At this point, the registers are sent through a 50:50 beam splitter. We denote the output modes of the BS as and . We simply denote the action of this splitter (up to phase rotation) as follows:
where is the state resulting from the action of the beam splitter upon the receipt of two photons, one from Alice and one from Bob; the exact description of this state is not important for the following discussion.
After applying the BS to Equation (20), but before measuring the output of the BS, the state evolves to (after permuting subspaces) the following:
At this point, a measurement of the BS output register is performed and the outcome is broadcast. Assuming that is “small”, whenever a “” or “” is measured, Alice and Bob’s state should collapse to an entangled Bell state; when the outcome is , Bob will apply a Pauli Z gate to transform the state to . Since , there will be some error in the multi-photon case, and this is something that users must optimize. Thus, interestingly, for this TF-QKD protocol, even when there is no channel noise and everything is ideal, there will always be some error in Alice and Bob’s raw key, which error correction must later repair.
At this point, we comment that two varieties of the above protocol may be introduced, which we denote as Π and Π. For Π, Alice and Bob will only use rounds where the server reports an outcome of (if any other outcome is reported, including , that round is discarded); similarly, Π is defined to be the same, but Alice and Bob will only use rounds where the server reports an outcome of . The original protocol, where Alice and Bob use rounds where the server reports either or , will be denoted Π. While Π and Π may discard more rounds, we show later that improvements in key-rates can be found in some instances based on channel statistics. This is due to the asymmetric nature of the protocol (which we discuss in more detail in Section 5.1). We are not aware of these slight modifications being analyzed in prior literature.
Entanglement-Based Version
Instead of analyzing the above protocol, we will instead analyze the following entanglement-based protocol. It is not difficult to see that security of the following entanglement-based version will imply security of the above prepare-and-measure version. The entanglement-based version operates as follows:
- Eve creates a quantum state , where the A and B portions consist of N qubits each, while the C portion lives in a Hilbert space spanned by orthonormal basis for all (here, “v” will denote a vacuum observation and “?” an “other” event). The E portion is arbitrary. Alice and Bob are given the A and B registers, while the C register is sent to a trusted third party Charlie.
- Charlie measures his entire C register in the basis, broadcasting the result to all parties. Alice and Bob discard all qubits rounds where the reported outcome was “” or “?”. Let be the number of remaining systems not discarded.
- Alice and Bob choose a random subset of size (which may depend on ), and measure their respective systems, indexed by this subset, in the X basis which they subsequently broadcast to determine the fidelity of their state.
- Alice and Bob measure the remaining systems in the Z basis, leading to their raw key. They then further process this through error correction and privacy amplification as normal.
Entanglement-based versions of Π and Π are defined similarly, with only step 2 being changed.
Note that in the entanglement-based version, Bob does not apply a Pauli correction gate, since Eve gets to prepare not only Alice and Bob’s state but also the state that would normally have been output from the BS; it is advantageous for Eve to “simulate” the Pauli correction before sending it to Bob (though she does not have to; however, not doing so would lead to additional X basis noise). It is not difficult to see that security of the entanglement based version above will imply security of the actual TF-QKD protocol. In the next section, we show a new proof of security, deriving an entropy bound for the entanglement-based version, which will subsequently produce a key-rate bound for the TF-QKD protocol.
We note that the protocols above are not novel; they are, at most, very slight variations of protocols from [19]. Π is identical to prior work in [19], while Π and Π are only minor variations of that protocol. As discussed in the introduction, the novelty of our work is in an alternative security proof, derived in the following section.
4. New Security Proof
We now present our new proof of security for the above TF-QKD protocol. Our proof uses the quantum sampling framework of Bouman and Fehr [29] discussed above, along with proof techniques used for sampling-based entropic uncertainty relations [30]. Namely, we prove security of the entanglement-based version which will imply security of the prepare-and-measure version. The main result is shown in the following theorem:
Theorem 2.
Let be the state Eve prepares where the A and B portions are N qubits each and the C portion is in a Hilbert space of dimension . After Charlie’s measurement of the C register, let be the resulting outcome and be the post measured state (tracing out the measured C register). Let be the number of signals not discarded, namely for Π-Total, for Π-Zero, and for Π-One. Alice and Bob will choose a random sample of size , measure those qubits in the X basis and determine the relative number of errors in that basis, denoted as . Then, it holds that, except with probability , if the remaining signals are measured in the Z basis
where
Proof.
Consider the post-measured state as discussed in the theorem statement. Without loss of generality, we may write this state as follows:
At this point, Alice and Bob discard certain systems based on the value of c. For instance, whenever , they will discard that round; furthermore, if they are running Π (respectively Π), they will discard rounds when (respectively ). This effectively traces out these systems. Let be defined as in the theorem statement and (the number of signals Rejected). It is easy to see that this operation, effectively tracing out certain systems of A and B, yields a mixed state which may be written as follows:
where . The A and B registers of are of qubits each.
At this point, Alice and Bob choose a random subset t of size (which may depend on ) with uniform probability and measure their respective systems in the X basis, observing the number of errors in this test set. The remaining qubits are measured in the Z basis. Our goal is to compute the min entropy of this final Z basis measurement.
We now switch to ideal states to complete our analysis. Next, r and c are fixed. Then, using Theorem 1, we construct the ideal states , such that for every , the following holds:
Also,
Now, using the sampling strategy discussed earlier, with error probability shown in Equation (19), and choosing as in Equation (23), we have . The above is true for any r and c; based on the triangle inequality, for every c, we have the following:
Let be the POVM element measuring Alice and Bob’s qubit in the X basis and reporting the same result (i.e., no error); let be the same, but when Alice and Bob’s outcomes are different (i.e., an X basis error). Note that whenever . Thus, can only be observed if (see Equation (4)).
After choosing t and measuring using POVM , resulting in outcome , it is clear from Equation (26), that the post-measured state must collapse to one that may be written in the following form:
Alice and Bob subsequently measure their remaining particles in the Z basis leading to their raw keys. The resulting density operator is denoted with . Using Lemma 2, along with Equation (8), we have the following:
Lemma 1 and Equation (28) completes the proof. □
The actual key-rate of the TF-QKD protocol then follows immediately and is stated in the corollary below:
Corollary 1.
Let be given. Then, except with probability , if the key-length of the TF-QKD protocol is set to
where leakEC is the information leaked during error correction, the final resulting key is -secure, for .
Proof.
This follows immediately from Theorem 2 and Equation (7). □
We note that our key-rate above agrees asymptotically with the prior work in [19] for Π and so our new proof above is simply an alternative method and not one that necessarily obtains higher results.
5. Evaluation
We now evaluate the key-rate assuming a lossy channel with detector mismatches and inefficiencies. In particular, each channel will have a transmittance of . We will assume, for evaluation purposes, that the server is honest, but has faulty devices. Thus, the server will perform the correct measurement; however, the detectors will have a non-zero dark count rate and a non-unit efficiency f. The measurement may also be misaligned in that it may report “0” when it should have, ideally, observed “1”.
To evaluate, we require certain expected values for along with the expected noise. Let (respectively ) be the probability that the server sends the message “0” (respectively “1”). Then, the expected value of is simply , where N is the total number of rounds Alice and Bob perform for the protocol. To find these values under our evaluation setup, we trace the protocol’s execution.
First, consider the joint state created by Alice and Bob:
The qubits are sent through a lossy channel which, as in [19]. We model a beamsplitter with transmittance ; it is as follows:
Note that we introduced a new state to ensure that the above is unitary; however, and cannot be distinguished by the parties and will look like a vacuum in either case.
The above causes the joint state to evolve into the following:
At this point, the system enters the server’s measurement device which, before the actual measurement is performed, we model as a unitary operator C, where for any :
Ideally, . Note that the additional system in the above definitions are used only to ensure unitarity of C and that the server’s subsequent measurement cannot distinguish between and . Following the application of C, the server will measure the first of the two systems in its control, thereby leading to the reported outcome. Note that, since and are technically indistinguishable, both observations are reported simply as a “vacuum” by the server.
Applying C to the joint state in Equation (33), but before the actual measurement, yields the following:
At this point, the server measures and reports the outcome. This measurement will be affected by dark counts () and the detector efficiency (f). For simplicity in evaluation, we will simply assume that the double-photon outcomes (namely, ) do not interfere, constructively or destructively, with the other terms in the term. We will then simply assume that the probability of observing a in is and the probability of observing is . It turns out that, since q is large generally, this term does not significantly affect the key-rate and so this assumption does not play a major role in hurting or benefiting the key-rate. From this, we obtain the following:
Similarly, we obtain the following:
Next, we need the Z basis and X basis noise, conditioned on Alice and Bob not discarding the round, i.e., conditioned on the server sending a non-vacuum message in the Π protocol case or conditioned on sending either “0” or “1” for the Π or Π protocol case. Let be the probability of a Z basis error and the server sending the message “0”. Similarly, define , , and . From the above equations, the following expressions are easily found:
From these, the required conditional noise values may be determined for our evaluation scenario.
In our evaluations, we set , which was found to be roughly the optimal value. We also set to be . We found no significant affect on the key-rate for other values due to the high value of q and so we simply set this value as . For finite key rates, we set .
To evaluate, we use Corollary 1, setting , where Q is the Z basis error noise (e.g., for Π; this is similar for other protocol settings). A graph of the resulting asymptotic key-rates is shown in Figure 1 (comparing to the PLOB bound [25]). The finite key results are shown in Figure 2. Note that our key-rates agree asymptotically to previous results for the Π version and so we do not compare them to prior works for that setting; for other settings (namely Π and Π), we are not aware of any security proof, and so there is no comparison beyond comparing to Π.
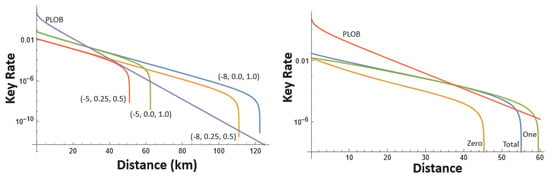
Figure 1.
(left) Asymptotic key-rate of the TF-QKD protocol version Π. Here, implies , and . We also compared it with the PLOB bound [25]. If d is the distance to Alice and Bob, we set . (right) Asymptotic key-rate of TF-QKD protocol Π, Π, and Π. Here we set , , and . Note that our key-rate agrees asymptotically with that from [19] for Π and so we do not plot a comparison; we are not aware of a key-rate result for Π or Π. We note that Π can yield strictly higher key-rates and support longer distances.
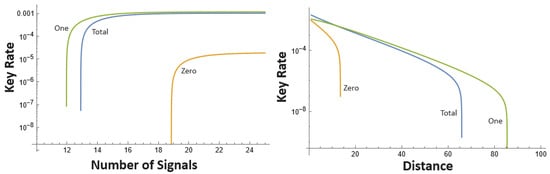
Figure 2.
(left) Key-rate as a function of the number of signals (note that x-axis is log-scale). Here, , distance is 25 km; ; and ; (right) Finite key-rate as a function of distance; here, we use the same parameters as in the left figure, but with . Again, we note that Π can outperform the other two protocol modes of operation.
5.1. A Discussion on the Asymmetric Nature of the Protocol
It is worth taking a closer look as to why Π and Π perform differently from the standard version Π. First, consider Equations (36) and (37). Note that, even under ideal conditions of , , and (which is what would be expected if all devices were perfect and there were simply natural loss ), for any , it holds that . Similarly, . The same inequalities hold for imperfect devices (i.e., when and ). This can be seen more clearly in Figure 3. Thus, anytime the server sends message 0, there is actually a greater chance of error than in the case of message 1. Therefore, under most conditions and under this channel scenario, discarding all messages of 0 actually improves the performance of the system. The users may decide, after measuring the channel statistics, to determine which mode of operation to perform; thus, the users can always optimize their choice of protocol after the quantum data have been transmitted and can therefore always choose the mode that will return the higher number of key-bits. It would be interesting to analyze these three protocols under other channel scenarios, beyond depolarizing. Note that our security proof can handle any channel scenario; however, we chose only depolarization channels for our evaluations in this section.
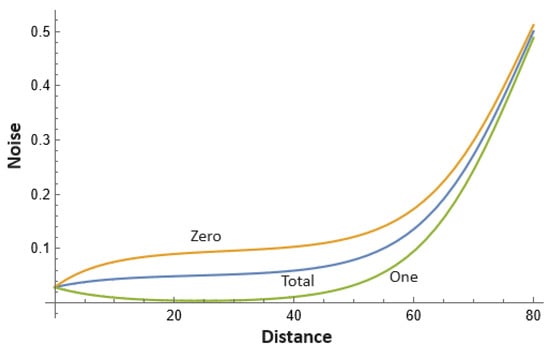
Figure 3.
Showing the total Z basis error rate for Π (top), Π (middle) and Π (bottom). Lower is better as it indicates less raw key error. The asymmetric nature of the protocol causes there to be fewer errors when the server sends message 1. See text for further discussion.
6. Closing Remarks
In this paper, we revisited a TF-QKD protocol introduced in [19] and derived a new proof of security for it. Our new proof uses methods from quantum sampling techniques [29]. While our new proof agrees with prior works and does not show higher key-rates compared to them, we still feel that alternative proof techniques are interesting and important. We also investigated two slight variants of the protocol and showed how they can lead to improved key-rates in some scenarios.
Many interesting future problems remain. It would be fruitful to further explore the two variants and see if additional improvements can be made. Furthermore, a finite key proof using decoy-state methods (using our sampling-based proof approach) would be interesting, especially for Π and Π. Adapting our proof technique to other TF-QKD protocols would also be very interesting; a particular candidate to start with would be the sending or not-sending (SNS) TF-QKD protocol [31] due to its similar encoding mechanism. Also, it would be interesting to discover whether or not asymmetric protocols (similar to Π and Π analyzed in this work) can be defined and shown to be more efficient for such protocols like the SNS TF-QKD mechanism.
Also, leading into more practical device considerations, it is known that for single-photon interference protocols (such as the TF protocol discussed in this paper), there are still challenges with matching the mode of the photon and detector, which ultimately affects the protocol’s performance [38]. Such issues must be considered in future works to address applicability issues of the protocol.
Funding
This research was funded by NSF under grant number 2143644.
Institutional Review Board Statement
Not Applicable.
Informed Consent Statement
Not Applicable.
Data Availability Statement
The data are contained within the article.
Acknowledgments
The author would like to thank the reviewers for their helpful comments which greatly improved the quality of the manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Scarani, V.; Bechmann-Pasquinucci, H.; Cerf, N.J.; Dušek, M.; Lütkenhaus, N.; Peev, M. The security of practical quantum key distribution. Rev. Mod. Phys. 2009, 81, 1301–1350. [Google Scholar] [CrossRef]
- Amer, O.; Garg, V.; Krawec, W.O. An introduction to practical quantum key distribution. IEEE Aerosp. Electron. Syst. Mag. 2021, 36, 30–55. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. arXiv 2019, arXiv:1906.01645. [Google Scholar] [CrossRef]
- Peev, M.; Pacher, C.; Alléaume, R.; Barreiro, C.; Bouda, J.; Boxleitner, W.; Debuisschert, T.; Diamanti, E.; Dianati, M.; Dynes, J.; et al. The SECOQC quantum key distribution network in Vienna. New J. Phys. 2009, 11, 075001. [Google Scholar] [CrossRef]
- Zhang, Q.; Xu, F.; Chen, Y.A.; Peng, C.Z.; Pan, J.W. Large scale quantum key distribution: Challenges and solutions. Opt. Express 2018, 26, 24260–24273. [Google Scholar] [CrossRef] [PubMed]
- Tysowski, P.K.; Ling, X.; Lütkenhaus, N.; Mosca, M. The engineering of a scalable multi-site communications system utilizing quantum key distribution (QKD). Quantum Sci. Technol. 2018, 3, 024001. [Google Scholar] [CrossRef]
- Kimble, H.J. The quantum internet. Nature 2008, 453, 1023–1030. [Google Scholar] [CrossRef]
- Wehner, S.; Elkouss, D.; Hanson, R. Quantum internet: A vision for the road ahead. Science 2018, 362, eaam9288. [Google Scholar] [CrossRef]
- Amer, O.; Krawec, W.O.; Wang, B. Efficient routing for quantum key distribution networks. In Proceedings of the 2020 IEEE International Conference on Quantum Computing and Engineering (QCE), Denver, CO, USA, 12–16 October 2020; pp. 137–147. [Google Scholar]
- Cao, Y.; Zhao, Y.; Wang, Q.; Zhang, J.; Ng, S.X.; Hanzo, L. The evolution of quantum key distribution networks: On the road to the qinternet. IEEE Commun. Surv. Tutorials 2022, 24, 839–894. [Google Scholar] [CrossRef]
- Rozenman, G.G.; Kundu, N.K.; Liu, R.; Zhang, L.; Maslennikov, A.; Reches, Y.; Youm, H.Y. The quantum internet: A synergy of quantum information technologies and 6G networks. IET Quantum Commun. 2023, 4, 147–166. [Google Scholar] [CrossRef]
- Van Meter, R.; Devitt, S.J. The path to scalable distributed quantum computing. Computer 2016, 49, 31–42. [Google Scholar] [CrossRef]
- Yimsiriwattana, A.; Lomonaco, S.J., Jr. Distributed quantum computing: A distributed Shor algorithm. In Proceedings of the Quantum Information and Computation II, Orlando, FL, USA, 12–14 April 2004; SPIE: Bellingham, WA, USA, 2004; Volume 5436, pp. 360–372. [Google Scholar]
- Cuomo, D.; Caleffi, M.; Cacciapuoti, A.S. Towards a distributed quantum computing ecosystem. IET Quantum Commun. 2020, 1, 3–8. [Google Scholar] [CrossRef]
- Zhang, Z.; Zhuang, Q. Distributed quantum sensing. Quantum Sci. Technol. 2021, 6, 043001. [Google Scholar] [CrossRef]
- Ge, W.; Jacobs, K.; Eldredge, Z.; Gorshkov, A.V.; Foss-Feig, M. Distributed quantum metrology with linear networks and separable inputs. Phys. Rev. Lett. 2018, 121, 043604. [Google Scholar] [CrossRef] [PubMed]
- Proctor, T.J.; Knott, P.A.; Dunningham, J.A. Multiparameter estimation in networked quantum sensors. Phys. Rev. Lett. 2018, 120, 080501. [Google Scholar] [CrossRef] [PubMed]
- Eldredge, Z.; Foss-Feig, M.; Gross, J.A.; Rolston, S.L.; Gorshkov, A.V. Optimal and secure measurement protocols for quantum sensor networks. Phys. Rev. A 2018, 97, 042337. [Google Scholar] [CrossRef] [PubMed]
- Curty, M.; Azuma, K.; Lo, H.K. Simple security proof of twin-field type quantum key distribution protocol. npj Quantum Inf. 2019, 5, 64. [Google Scholar] [CrossRef]
- Yin, H.L.; Chen, Z.B. Finite-key analysis for twin-field quantum key distribution with composable security. Sci. Rep. 2019, 9, 17113. [Google Scholar] [CrossRef]
- Wang, Z.H.; Wang, R.; Yin, Z.Q.; Wang, S.; Lu, F.Y.; Chen, W.; He, D.Y.; Guo, G.C.; Han, Z.F. Tight finite-key analysis for mode-pairing quantum key distribution. Commun. Phys. 2023, 6, 265. [Google Scholar] [CrossRef]
- Zhang, X.X.; Wang, Y.; Jiang, M.S.; Zhou, C.; Lu, Y.F.; Bao, W.S. Finite-key analysis of asymmetric phase-matching quantum key distribution with unstable sources. J. Opt. Soc. Am. B 2021, 38, 724–731. [Google Scholar] [CrossRef]
- Maeda, K.; Sasaki, T.; Koashi, M. Repeaterless quantum key distribution with efficient finite-key analysis overcoming the rate-distance limit. Nat. Commun. 2019, 10, 3140. [Google Scholar] [CrossRef] [PubMed]
- Guillermo, C.L.; Álvaro, N.; Koji, A.; Go, K.; Marcos, C.; Mohsen, R. Tight finite-key security for twin-field quantum key distribution. npj Quantum Inf. 2021, 7, 22. [Google Scholar]
- Pirandola, S.; Laurenza, R.; Ottaviani, C.; Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 2017, 8, 15043. [Google Scholar] [CrossRef] [PubMed]
- Liu, H.; Jiang, C.; Zhu, H.T.; Zou, M.; Yu, Z.W.; Hu, X.L.; Xu, H.; Ma, S.; Han, Z.; Chen, J.P.; et al. Field test of twin-field quantum key distribution through sending-or-not-sending over 428 km. Phys. Rev. Lett. 2021, 126, 250502. [Google Scholar] [CrossRef] [PubMed]
- Chen, J.P.; Zhang, C.; Liu, Y.; Jiang, C.; Zhang, W.J.; Han, Z.Y.; Ma, S.Z.; Hu, X.L.; Li, Y.H.; Liu, H.; et al. Twin-field quantum key distribution over a 511 km optical fibre linking two distant metropolitan areas. Nat. Photonics 2021, 15, 570–575. [Google Scholar] [CrossRef]
- Wang, S.; Yin, Z.Q.; He, D.Y.; Chen, W.; Wang, R.Q.; Ye, P.; Zhou, Y.; Fan-Yuan, G.J.; Wang, F.X.; Chen, W.; et al. Twin-field quantum key distribution over 830-km fibre. Nat. Photonics 2022, 16, 154–161. [Google Scholar] [CrossRef]
- Bouman, N.J.; Fehr, S. Sampling in a quantum population, and applications. In Proceedings of the Annual Cryptology Conference, Santa Barbara, CA, USA, 15–19 August 2010; Springer: Cham, Switzerland, 2010; pp. 724–741. [Google Scholar]
- Yao, K.; Krawec, W.O.; Zhu, J. Quantum sampling for finite key rates in high dimensional quantum cryptography. IEEE Trans. Inf. Theory 2022, 68, 3144–3163. [Google Scholar] [CrossRef]
- Wang, X.B.; Yu, Z.W.; Hu, X.L. Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 2018, 98, 062323. [Google Scholar] [CrossRef]
- Bell, J.S. On the einstein podolsky rosen paradox. Phys. Phys. Fiz. 1964, 1, 195. [Google Scholar] [CrossRef]
- Braunstein, S.L.; Mann, A.; Revzen, M. Maximal violation of Bell inequalities for mixed states. Phys. Rev. Lett. 1992, 68, 3259. [Google Scholar] [CrossRef]
- Sych, D.; Leuchs, G. A complete basis of generalized Bell states. New J. Phys. 2009, 11, 013006. [Google Scholar] [CrossRef]
- Renner, R. Security of quantum key distribution. Int. J. Quantum Inf. 2008, 6, 1–127. [Google Scholar] [CrossRef]
- Krawec, W.O. Security of a High Dimensional Two-Way Quantum Key Distribution Protocol. Adv. Quantum Technol. 2022, 5, 2200024. [Google Scholar] [CrossRef]
- Krawec, W.O. Entropic Uncertainty for Biased Measurements. arXiv 2023, arXiv:2305.09753. [Google Scholar]
- Chen, Z.; Wang, X.; Yu, S.; Li, Z.; Guo, H. Continuous-mode quantum key distribution with digital signal processing. npj Quantum Inf. 2023, 9, 28. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).