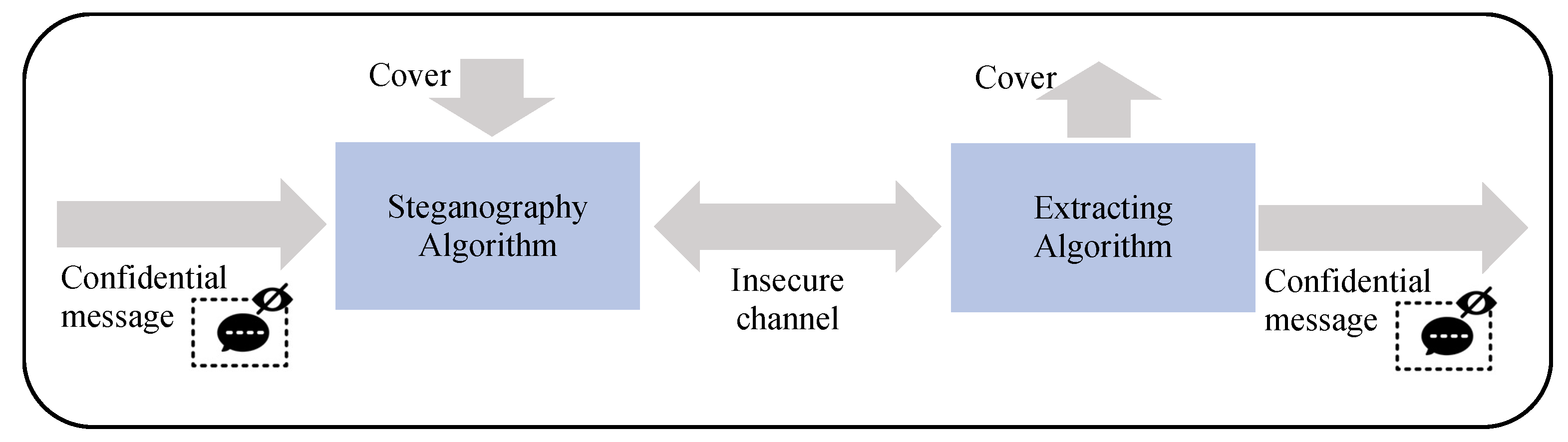
A Dynamic Multi-Layer Steganography Approach Based on Arabic Letters’ Diacritics and Image Layers
Abstract
1. Introduction
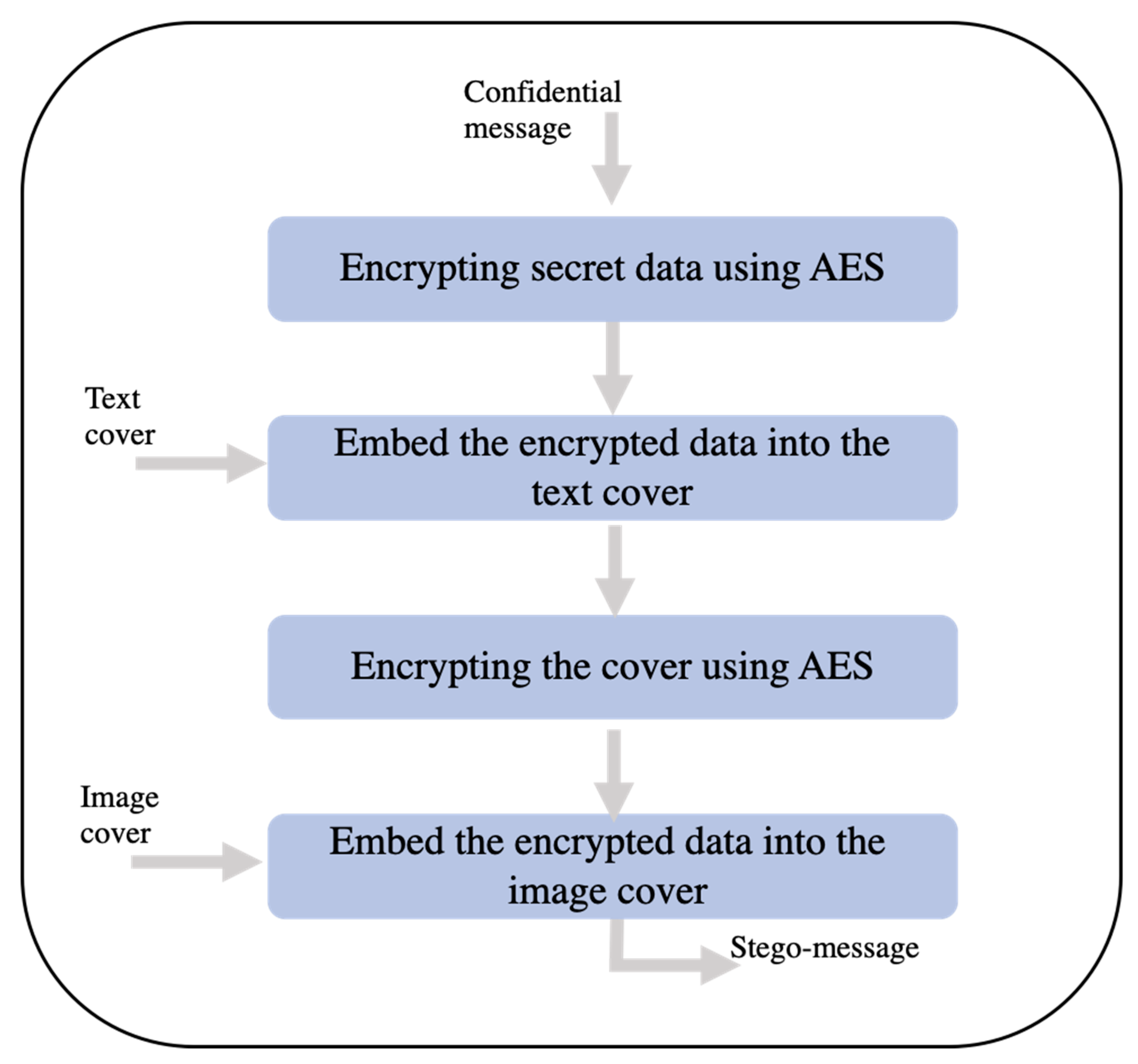
- The dynamic multi-layered concept: Previous research studies primarily focused on specific techniques or a combination of techniques to conceal information, such as using Arabic movements or kashida within texts. However, our work introduces a dynamic multi-layered concept that enables the concealment of secrets of various sizes. This approach provides flexibility and adaptability in hiding information within texts.
- A novel steganography algorithm: We propose a novel steganography algorithm that specifically addresses the method of hiding text with a text cover in different ways and scenarios and then embeds it in a cover image as another layer. By incorporating Arabic diacritics and Hamzas, our algorithm enhances the concealment process and makes it highly challenging for potential attackers to detect hidden information. This algorithm offers improved security and resilience against detection.
2. Related Work
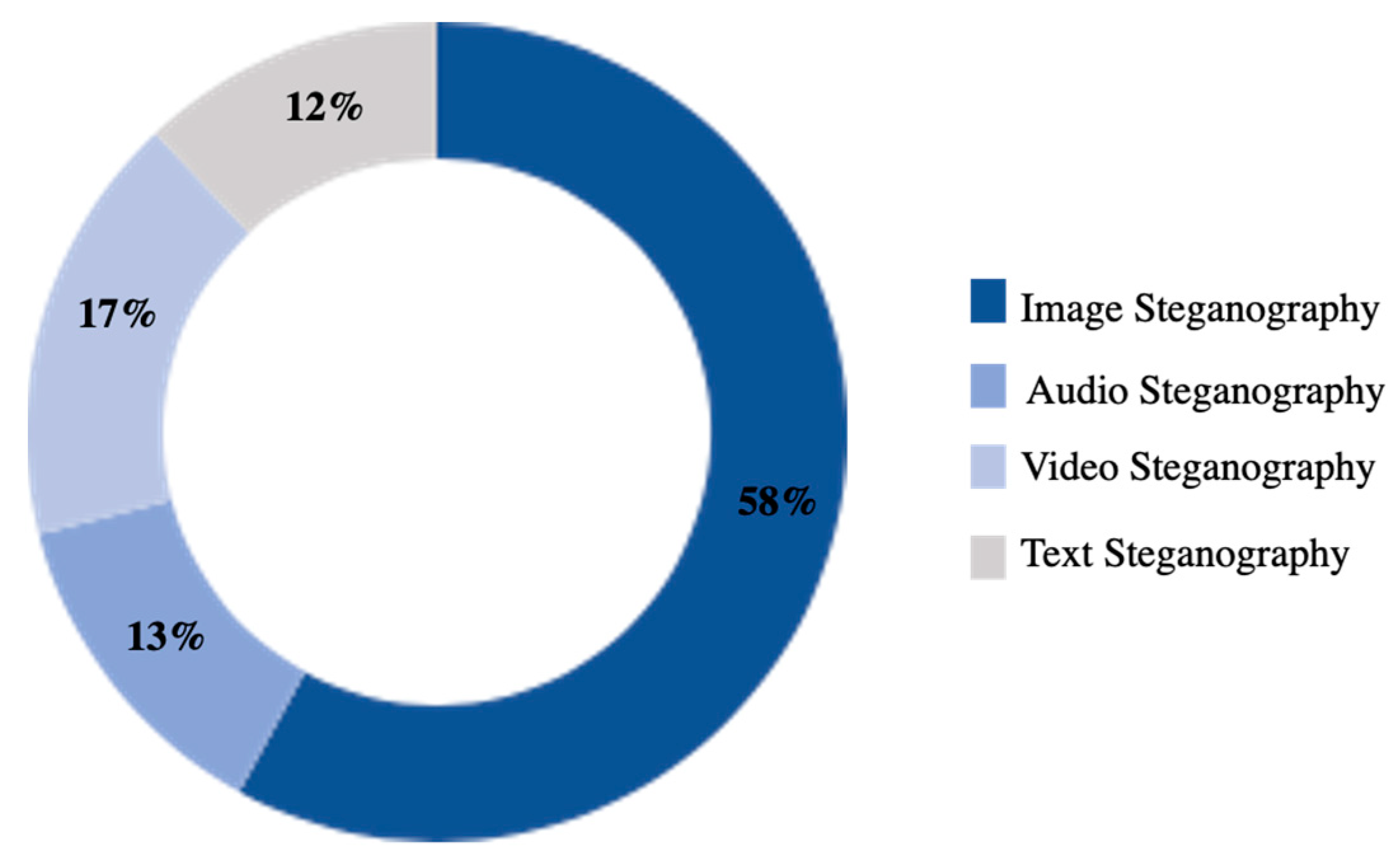
2.1. Image Steganography Methods
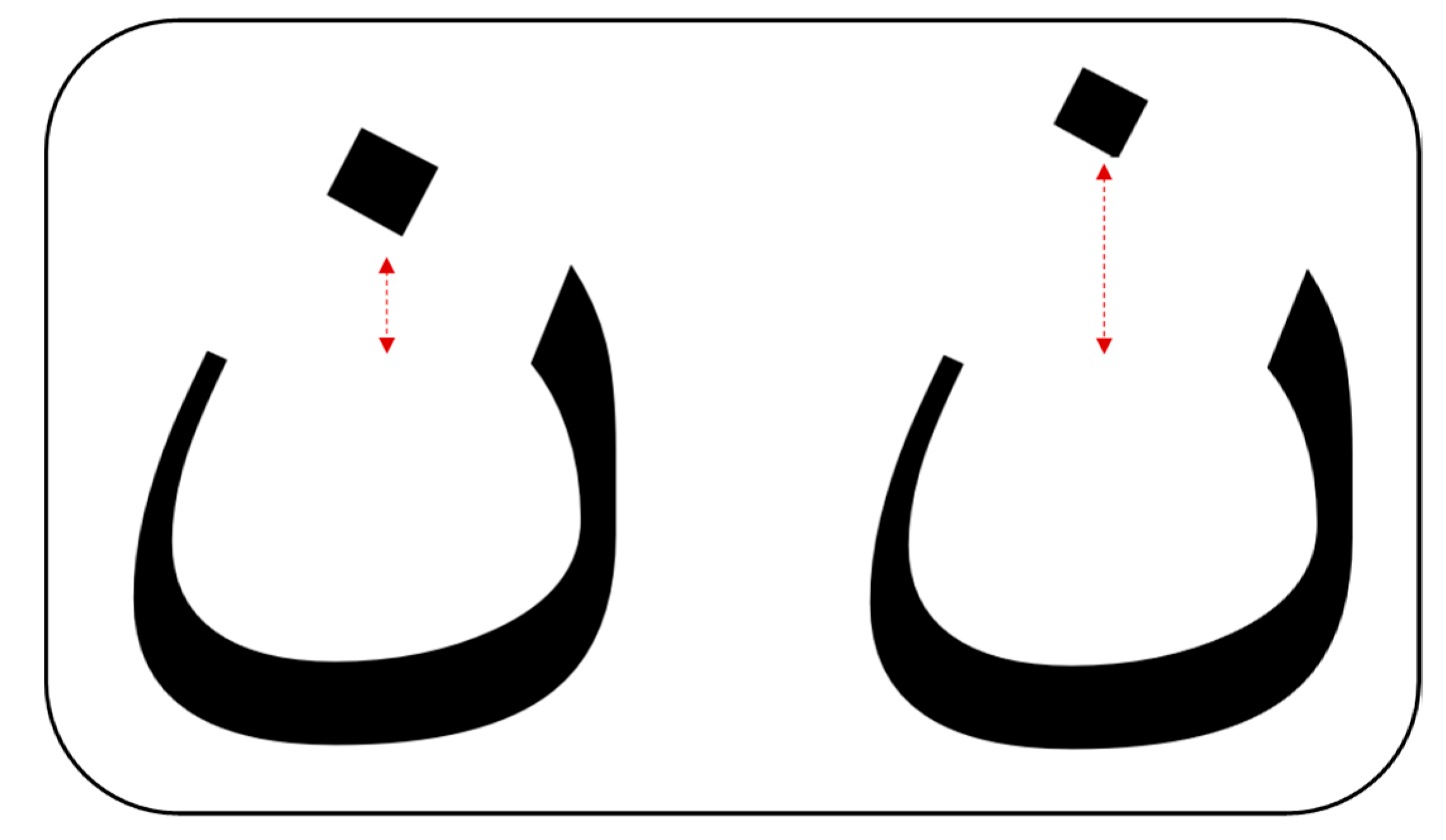
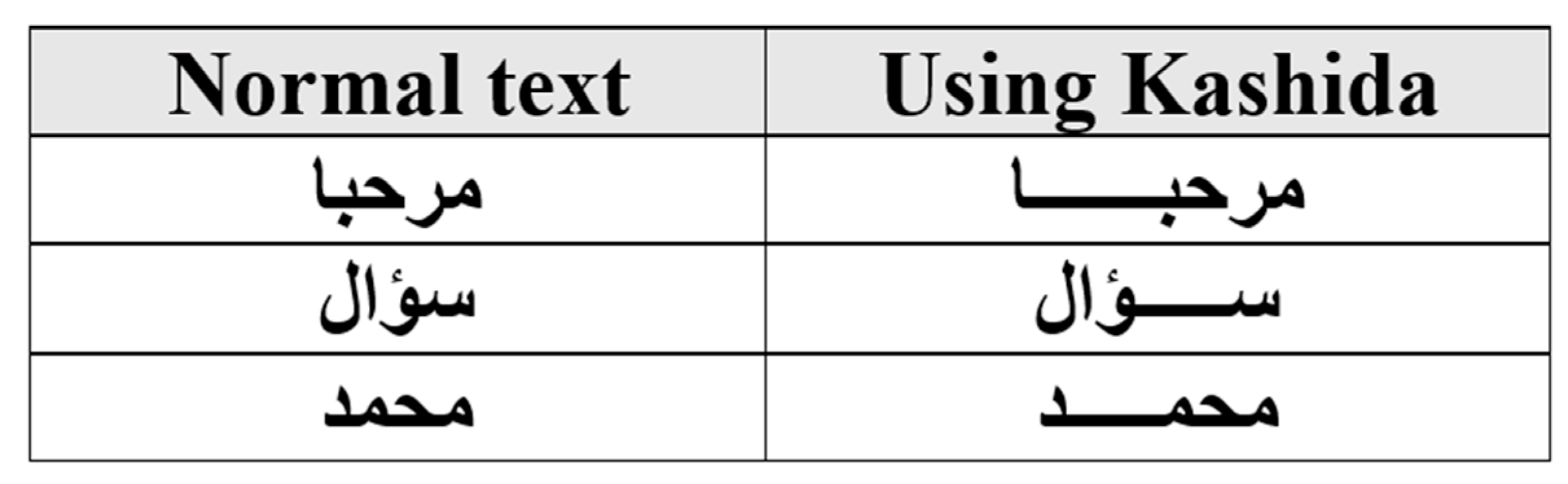
2.2. Arabic Text Steganography Methods
- The process of extracting the text requires an optical character recognition (OCR) process to extract it to establish the locations of the variable points in their places, in addition to the fact that a change in font type would lead to complete loss of the embedded data;
- The position of the hidden bits is not random; thus, the predictability can be exploited;
- Low sustainability.
 ) and Kasrah (
) and Kasrah ( ) diacritics in the concealment process. This drawback is that the hiding places in the cover text are not random.
) diacritics in the concealment process. This drawback is that the hiding places in the cover text are not random.3. The Proposed Approach
 ) in the case of 0 and to a Dammah (
) in the case of 0 and to a Dammah ( ) in the case of 1. However, the switch within the diacritics will be in an agreed sequence (Like Table 3) between the two parties (the sender and the receiver), in the sense that there is a map agreed upon between the two parties in the exchange places for information.
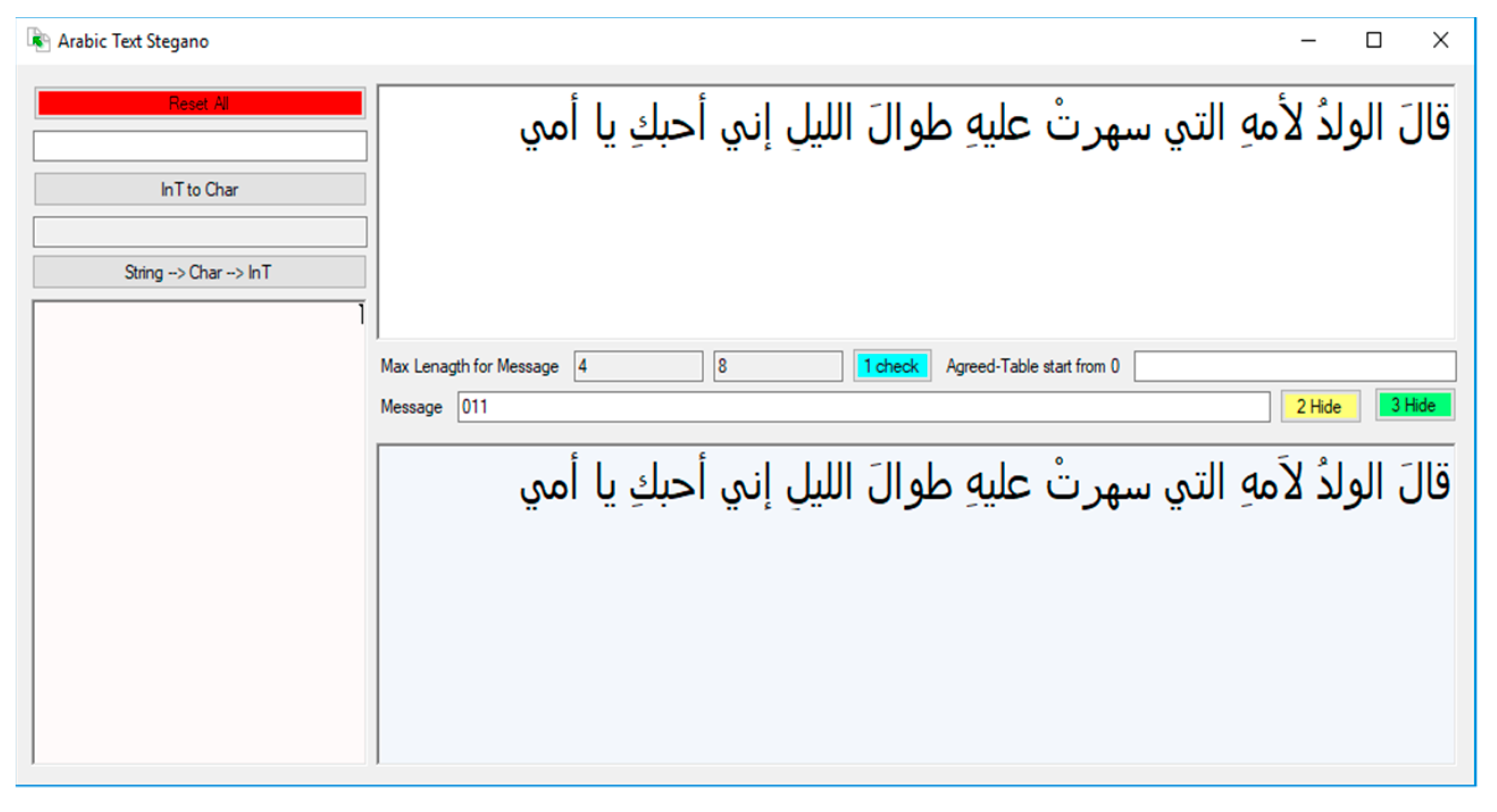
) in the case of 1. However, the switch within the diacritics will be in an agreed sequence (Like Table 3) between the two parties (the sender and the receiver), in the sense that there is a map agreed upon between the two parties in the exchange places for information.| Algorithm 1 First Scenario Algorithm |
| String Encrypt_First_Scenario(string message, int [] Positions, String Key, String CoverText) |
| Start Map [] = Positions []; String Sec_msg = AES.Encrypt(message, Key); Binary [] msg = Convert_To_Binary(Sec_Msg); Int L1 = Length (msg); Int L2 = Count (Map); Int L3 = Find_Count (“     ”, CoverText); // Number of all HARAKAT ”, CoverText); // Number of all HARAKATInt Index = 0; If (Map[End] <= L3) If (L1 == L2) While (Index < L1) Bit b = msg[Index]; If (b) CoverText [ Map[Index] ] = “  ”; ”; Else CoverText [ Map[Index] ] = “  ”; ”;End Index ++; End While Else return “Error Mapping”; End IF Else Return “Error Capacity“; End IF Return CoverText; |
| End Function |
| Algorithm 2 Second Scenario Algorithm |
| String Encrypt_Second_Scenario(String message, String Key, String CoverText) |
| Start String Sec_msg = AES.Encrypt(message, Key); Binary [] msg = Convert_To_Binary(Sec_Msg); Int L1 = Length (msg); Int L2 = Find_Count (“ أ إ”, CoverText); // Number of all HAMAZAT Int Index = 0; If ( L1 < L2) While (Index < L1) Bit b = msg[Index]; If (b) CoverText [Index] = “ اَ ”; Else CoverText [Index] = “ اِ ”; End Index ++; End While Else return “Error Mapping”; End IF Return CoverText; End Function |
4. Result and Discussion
4.1. Implementation
4.2. The Metrics of Evaluating Steganography
4.2.1. Imperceptibility
4.2.2. Capacity
4.2.3. Robustness
4.2.4. Security
4.3. Experimental and Investigations on the Proposed Method Based on the Steganography Metrics
4.3.1. Hypotheses
- First, Table 6 displays the details of the transcripts utilized in our experiments. Four different texts of lengths and properties were employed.
- Secondly, the secrets were randomly selected and comprise a combination of binary digits (zeros and ones).
- Thirdly, the proposed approach was evaluated by a team of five experts using the five-point Delphi method, where decisions were made based on the majority agreement among the team.
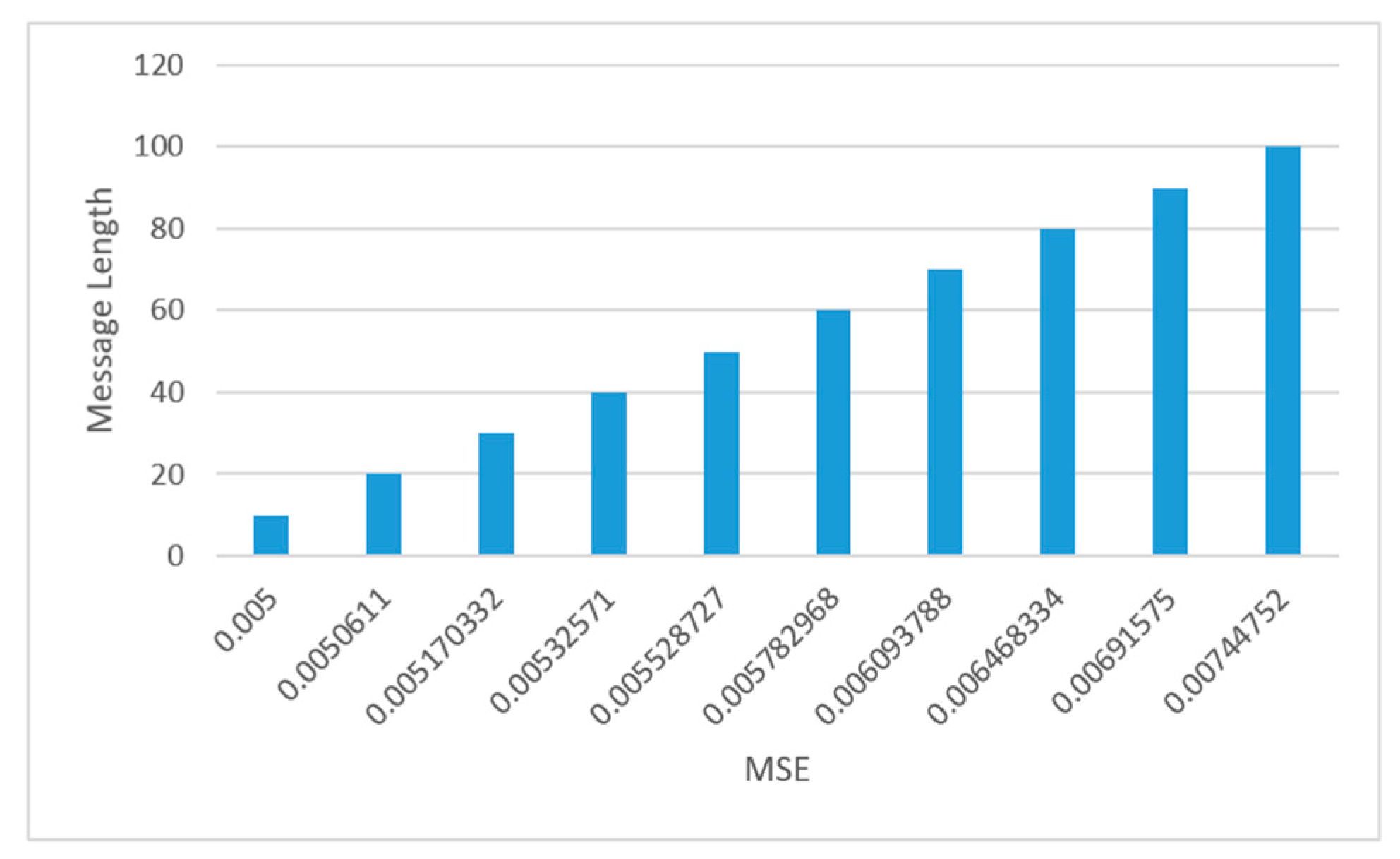
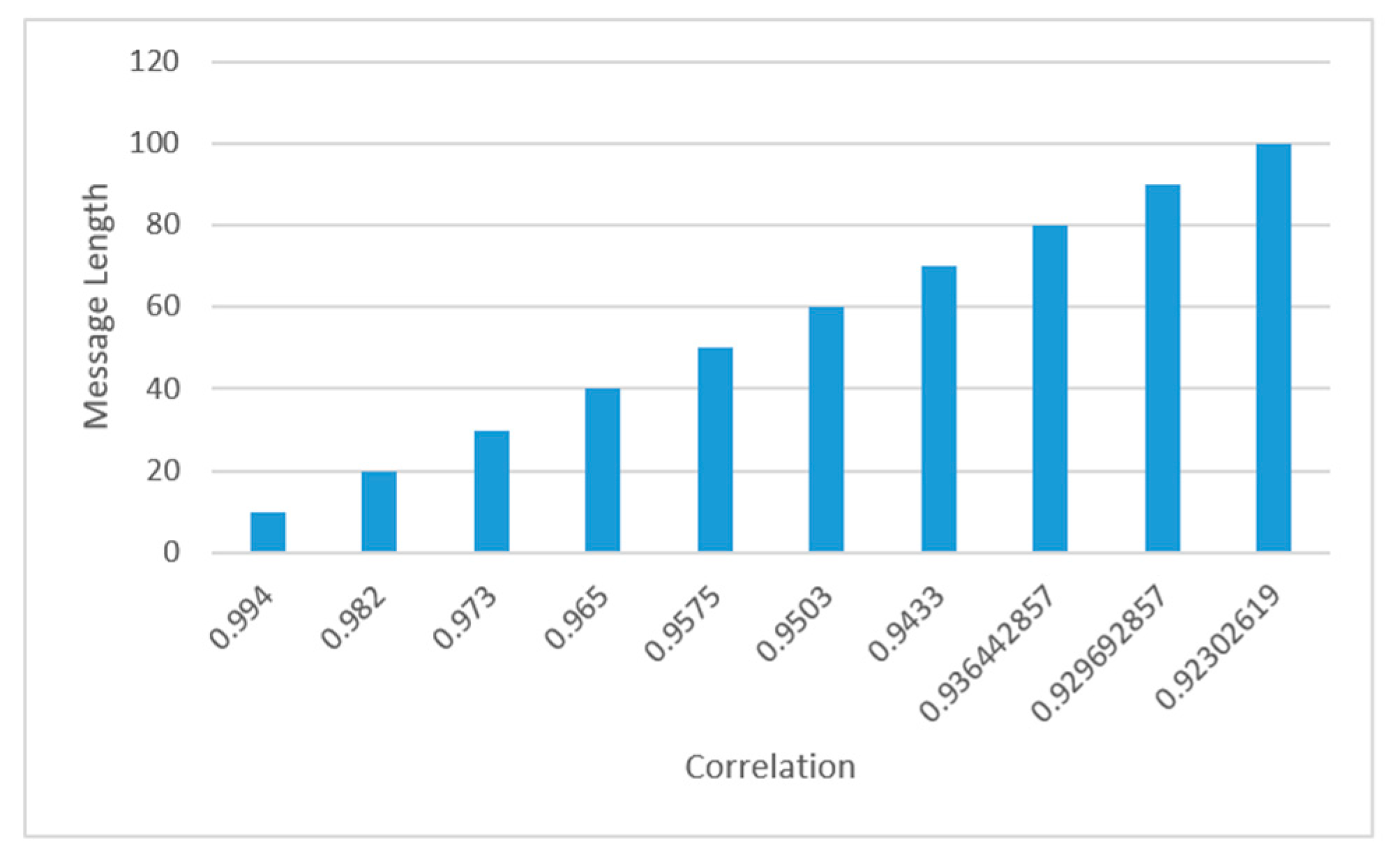
4.3.2. Capacity Feature
4.3.3. Security and Imperceptibility Features
| Algorithm 3 for Steganography layers selection. |
| Input (cover + secret) Output (hidden secret) Step1: Determine the scenario of choice for hiding secret messages: Diacritics or Hamzas Step2: Calculate the Capacity to determine which scenario has the highest capacity. Step3: Apply Testing for Crypto Analysis and Imperceptibility Criterion to evaluate the effectiveness of the chosen scenario.
Conceal the secret message within the chosen scenario by modifying the necessary characters according to the predefined MAP.
|
4.4. Comparison between the Proposed Method and the Other Methods Based on the Steganography Metrics
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Al-Shatnawi, A.M. A New Method in Image Steganography with Improved Image Quality. Appl. Math. Sci. 2013, 6, 3907–3915. [Google Scholar]
- Swanson, M.D.; Kobayashi, M.; Tewfik, A.H. Multimedia Data-Embedding and Watermarking Technologies. Proc. IEEE 1998, 86, 1064–1087. [Google Scholar] [CrossRef]
- Kaçar, S.; Konyar, M.Z.; Çavuşoğlu, Ü. 4D Chaotic System-Based Secure Data Hiding Method to Improve Robustness and Embedding Capacity of Videos. J. Inf. Secur. Appl. 2022, 71, 103369. [Google Scholar] [CrossRef]
- Alifah Roslan, N.; Izura Udzir, N.; Mahmod, R.; Gutub, A. Systematic Literature Review and Analysis for Arabic Text Steganography Method Practically. Egypt. Inform. J. 2022, 23, 177–191. [Google Scholar] [CrossRef]
- Duals. The 10 Most Word-Rich Languages in the World You Should Know about. Available online: https://blog.duals.app/the-10-most-word-rich-languages-in-the-world-you-should-know-about-cece2b91942e (accessed on 4 June 2023).
- Hussein, A. The Efforts of Al-Khalil Bin Ahmad Al-Farahidi and His Views on the Science of Dots through the Book The Decisiveness of Punctuation in Quran by Abi Amr Al-Dani: Exploration and Analysis. Islam. Sci. J. 2023, 14, 152–174. [Google Scholar] [CrossRef]
- Alanazi, N.; Khan, E.; Gutub, A. Efficient Security and Capacity Techniques for Arabic Text Steganography via Engaging Unicode Standard Encoding. Multimed. Tools Appl. 2021, 80, 1403–1431. [Google Scholar] [CrossRef]
- Divya, A.; Thenmozhi, S. Steganography: Various Techniques In Spatial and Transform Domain. Int. J. Adv. Sci. Res. Manag. 2016, 1, 81–89. [Google Scholar]
- Das, P.; Kushwaha, S.C.; Chakraborty, M. Data Hiding Using Randomization and Multiple Encrypted Secret Images. In Proceedings of the 2015 International Conference on Communications and Signal Processing (ICCSP), Melmaruvathur, India, 2–4 April 2015; pp. 298–302. [Google Scholar]
- Chan, C.-K.; Cheng, L.M. Hiding Data in Images by Simple LSB Substitution. Pattern Recognit. 2004, 37, 469–474. [Google Scholar] [CrossRef]
- Nosrati, M.; Hanani, A.; Karimi, R. Steganography in Image Segments Using Genetic Algorithm. In Proceedings of the 2015 Fifth International Conference on Advanced Computing & Communication Technologies, Haryana, India, 21–22 February 2015; pp. 102–107. [Google Scholar]
- Tahir, A.; Amit, D. A Novel Approach of LSB Based Steganography Using Parity Checker. Int. J. Adv. Res. Comput. Sci. Softw. Eng. 2015, 5, 314–321. [Google Scholar]
- Luo, W.; Huang, F.; Huang, J. Edge Adaptive Image Steganography Based on LSB Matching Revisited. IEEE Trans. Inf. Forensics Secur. 2010, 5, 201–214. [Google Scholar] [CrossRef]
- Basahel, A.; Yamin, M.; Ahmed, A.; Abi Sen, A. Enhancing Security of Transmitted Data by Improved Steganography Method. Int. J. Comput. Sci. Netw. Secur. 2019, 19, 239–244. [Google Scholar]
- Wu, D.-C.; Tsai, W.-H. A Steganographic Method for Images by Pixel-Value Differencing. Pattern Recognit. Lett. 2003, 24, 1613–1626. [Google Scholar] [CrossRef]
- Afrakhteh, M.; Ibrahim, S. Adaptive Steganography Scheme Using More Surrounding Pixels. In Proceedings of the 2010 International Conference on Computer Design and Applications, Qinhuangdao, China, 25–27 June 2010; Volume 1, pp. 225–229. [Google Scholar]
- Kadhem, S. Improving Hiding Security of Arabic Text Steganography by Hybrid AES Cryptography and Text Steganography. J. Eng. Res. Appl. 2016, 6, 60–69. [Google Scholar]
- Potdar, V.M.; Chang, E. Grey Level Modification Steganography for Secret Communication. In Proceedings of the 2nd IEEE International Conference on Industrial Informatics, 2004, INDIN ’04, Berlin, Germany, 24–26 June 2004; pp. 223–228. [Google Scholar]
- Al-Rahal, M.S.; Sen, A.A.; Basuhil, A.A. High Level Security Based Steganoraphy in Image and Audio Files. J. Theor. Applies Inf. Technol. 2016, 87, 29–37. [Google Scholar]
- Li, X.; Zhang, W.; Gui, X.; Yang, B. A Novel Reversible Data Hiding Scheme Based on Two-Dimensional Difference-Histogram Modification. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1091–1100. [Google Scholar] [CrossRef]
- Alsaawy, Y.; Abi Sen, A.A.; Alkhodre, A.; Bahbouh, N.M.; Baghanim, N.A.; Alharbi, H.B. Double Steganography—New Algorithm for More Security. In Proceedings of the 2021 8th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 17–19 March 2021; pp. 370–374. [Google Scholar]
- Divya, V.; Sasirekha, N. High Capacity Steganography Technique Based on Wavelet Transform. In Proceedings of the 2016 Online International Conference on Green Engineering and Technologies (IC-GET), Coimbatore, India, 19 November 2016; pp. 1–5. [Google Scholar]
- Kumar, V.; Kumar, D. A Modified DWT-Based Image Steganography Technique. Multimed. Tools Appl. 2018, 77, 13279–13308. [Google Scholar] [CrossRef]
- El-Khamy, S.E.; Korany, N.; El-Sherif, M.H. Robust Image Hiding in Audio Based on Integer Wavelet Transform and Chaotic Maps Hopping. In Proceedings of the 2017 34th National Radio Science Conference (NRSC), Alexandria, Egypt, 13–16 March 2017; pp. 205–212. [Google Scholar]
- Shafi, I.; Noman, M.; Gohar, M.; Ahmad, A.; Khan, M.; Din, S.; Ahmad, S.H.; Ahmad, J. An Adaptive Hybrid Fuzzy-Wavelet Approach for Image Steganography Using Bit Reduction and Pixel Adjustment. Soft Comput. 2018, 22, 1555–1567. [Google Scholar] [CrossRef]
- Sharifzadeh, F.; Akbarizadeh, G.; Seifi Kavian, Y. Ship Classification in SAR Images Using a New Hybrid CNN–MLP Classifier. J. Indian Soc. Remote Sens. 2019, 47, 551–562. [Google Scholar] [CrossRef]
- Durafe, A.; Patidar, V. Development and Analysis of IWT-SVD and DWT-SVD Steganography Using Fractal Cover. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 4483–4498. [Google Scholar] [CrossRef]
- Gutub, A.; Fattani, M. A Novel Arabic Text Steganography Method Using Letter Points and Extensions. In Proceedings of the WASET International Conference on Computer, Information and Systems Science and Engineering (ICCISSE), Vienna, Austria, 25–27 May 2007; pp. 28–31. [Google Scholar]
- Abdul-Aziz Gutub, A.; Al-Nazer, A.A. High Capacity Steganography Tool for Arabic Text Using ‘Kashida’. ISeCure 2010, 2, 107–118. [Google Scholar]
- Gutub, A.; Al-Juaid, N.; Khan, E. Counting-Based Secret Sharing Technique for Multimedia Applications. Multimed. Tools Appl. 2019, 78, 5591–5619. [Google Scholar] [CrossRef]
- Al-Nofaie, S.; Gutub, A.; Al-Ghamdi, M. Enhancing Arabic Text Steganography for Personal Usage Utilizing Pseudo-Spaces. J. King Saud Univ.-Comput. Inf. Sci. 2021, 33, 963–974. [Google Scholar] [CrossRef]
- Odeh, A.; Elleithy, K.; Faezipour, M. Steganography in Arabic Text Using Kashida Variation Algorithm (KVA). In Proceedings of the 2013 IEEE Long Island Systems, Applications and Technology Conference (LISAT), Farmingdale, NY, USA, 3 May 2013; pp. 1–6. [Google Scholar]
- Al-Nofaie, S.M.A.; Gutub, A.A.-A. Utilizing Pseudo-Spaces to Improve Arabic Text Steganography for Multimedia Data Communications. Multimed. Tools Appl. 2020, 79, 19–67. [Google Scholar] [CrossRef]
- Al-Alwani, W.; Mahfooz, A.B.; Gutub, A.A.-A. A Novel Arabic Text Steganography Method Using Extensions. World Acad. Sci. Eng. Technol. 2007, 83–86. [Google Scholar]
- Odeh, A.; Elleithy, K. Steganography in Arabic Text Using Zero Width and Kashidha Letters. Int. J. Comput. Sci. Inf. Technol. IJCSIT 2012, 4, 1–11. [Google Scholar] [CrossRef]
- Roslan, N.A.; Mahmod, R.; Udzir, N.I. Sharp-Edges Method in Arabic Text Steganography. J. Theor. Appl. Inf. Technol. 2011, 33, 32–141. [Google Scholar]
- Roslan, N.A.; Mahmod, R.; Udzir, N.I.; Zurkarnain, Z.A. Primitive structural method for high capacity text steganography. J. Theor. Appl. Inf. Technol. 2014, 67, 373–383. [Google Scholar]
- Ali, A.E. A New Text Steganography Method by Using Non-Printing Unicode Characters. Eng. Technol. J. 2010, 28, 72–83. [Google Scholar]
- Mohamed, A.A. An Improved Algorithm for Information Hiding Based on Features of Arabic Text: A Unicode Approach. Egypt. Inform. J. 2014, 15, 79–87. [Google Scholar] [CrossRef]
- Obeidat, A. Arabic Text Steganography Using Unicode of Non-Joined to Right Side. J. Comput. Sci. 2017, 13, 184–191. [Google Scholar] [CrossRef]
- Khami, M.J. Unicode with Rules Arabic Text Data Hiding. J. Educ. Pure Sci. 2018, 8, 52–76. [Google Scholar]
- Ditta, A.; Azeem, M.; Naseem, S.; Gulzar Rana, K.; Adnan Khan, M.; Iqbal, Z. A Secure and Size Efficient Algorithm to Enhance Data Hiding Capacity and Security of Cover Text by Using Unicode. J. King Saud Univ.-Comput. Inf. Sci. 2022, 34, 2180–2191. [Google Scholar] [CrossRef]
- Aabed, M.A.; Awaideh, S.M.; Elshafei, A.-R.M.; Gutub, A.A. Arabic Diacritics Based Steganography. In Proceedings of the 2007 IEEE International Conference on Signal Processing and Communications, Dubai, United Arab Emirates, 25–27 November 2007; pp. 756–759. [Google Scholar]
- Gutub, A.; Elarian, Y.; Awaideh, S.; Alvi, A. Arabic Text Steganography Using Multiple Diacritics; University of Sharjah: Sharjah, United Arab Emirates, 2008. [Google Scholar]
- Bensaad, M.L.; Yagoubi, M.B. Boosting the Capacity of Diacritics-Based Methods for Information Hiding in Arabic Text. Arab. J. Sci. Eng. 2013, 38, 2035–2041. [Google Scholar] [CrossRef]
- Gutub, A.; Ghouti, L.; Elarian, Y.; Awaideh, S.; Alvi, A. Utilizing Diacritic Marks for Arabic Text Steganography. Kuwait J. Sci. Eng. KJSE 2010, 37, 89–109. [Google Scholar]
- Memon, M.S.; Shah, A. A Novel Text Steganography Technique to Arabic Language Using Reverse Fat5th5ta. Pak. J. Eng. Technol. Sci. 2015, 1, 106–113. [Google Scholar] [CrossRef]
- Ahmadoh, E.M.; Gutub, A.A.-A. Utilization of Two Diacritics for Arabic Text Steganography to Enhance Performance. LNIT 2015, 3, 42–47. [Google Scholar] [CrossRef]
- Daemen, J. AES Proposal: Rijndael. Available online: https://www.cs.miami.edu/home/burt/learning/Csc688.012/rijndael/rijndael_doc_V2.pdf (accessed on 4 June 2023).
- Majeed, M.A.; Sulaiman, R.; Shukur, Z.; Hasan, M.K. A Review on Text Steganography Techniques. Mathematics 2021, 9, 2829. [Google Scholar] [CrossRef]
- Li, B.; He, J.; Huang, J.; Shi, Y.Q. A Survey on Image Steganography and Steganalysis. J. Inf. Hiding Multimed. Signal Process. 2011, 2, 142–172. [Google Scholar]
- Shih, F.Y. Digital Watermarking and Steganography: Fundamentals and Techniques, 2nd ed.; CRC Press: Boca Raton, FL, USA, 2017; ISBN 978-1-4987-3877-4. [Google Scholar]
- Jero, S.E.; Ramu, P.; Swaminathan, R. Imperceptibility—Robustness Tradeoff Studies for ECG Steganography Using Continuous Ant Colony Optimization. Expert Syst. Appl. 2016, 49, 123–135. [Google Scholar] [CrossRef]
- An Introduction to Arabic Calligraphy: 1 Hardcover—Illustrated, 28 Octobers 2016. Online at Desertcart KSA. Available online: https://www.desertcart.com.sa/products/49607260-an-introduction-to-arabic-calligraphy-1?gclid=CjwKCAjwyeujBhA5EiwA5WD7_Uo-HlQaKj1oXO5pI0L6hYXs478Yw2Pr6RSn90IPJVq9TC87Agmi6BoCkt8QAvD_BwE (accessed on 3 June 2023).
- Shirali-Shahreza, M.H.; Shirali-Shahreza, M. Arabic/Persian Text Steganography Utilizing Similar Letters with Different Codes. Arab. J. Sci. Eng. 2010, 35, 213–222. [Google Scholar]
- Bensaad, M.L.; Yagoubi, M.B. High Capacity Diacritics-Based Method for Information Hiding in Arabic Text. In Proceedings of the 2011 International Conference on Innovations in Information Technology, Abu Dhabi, United Arab Emirates, 25–27 April 2011; pp. 433–436. [Google Scholar]

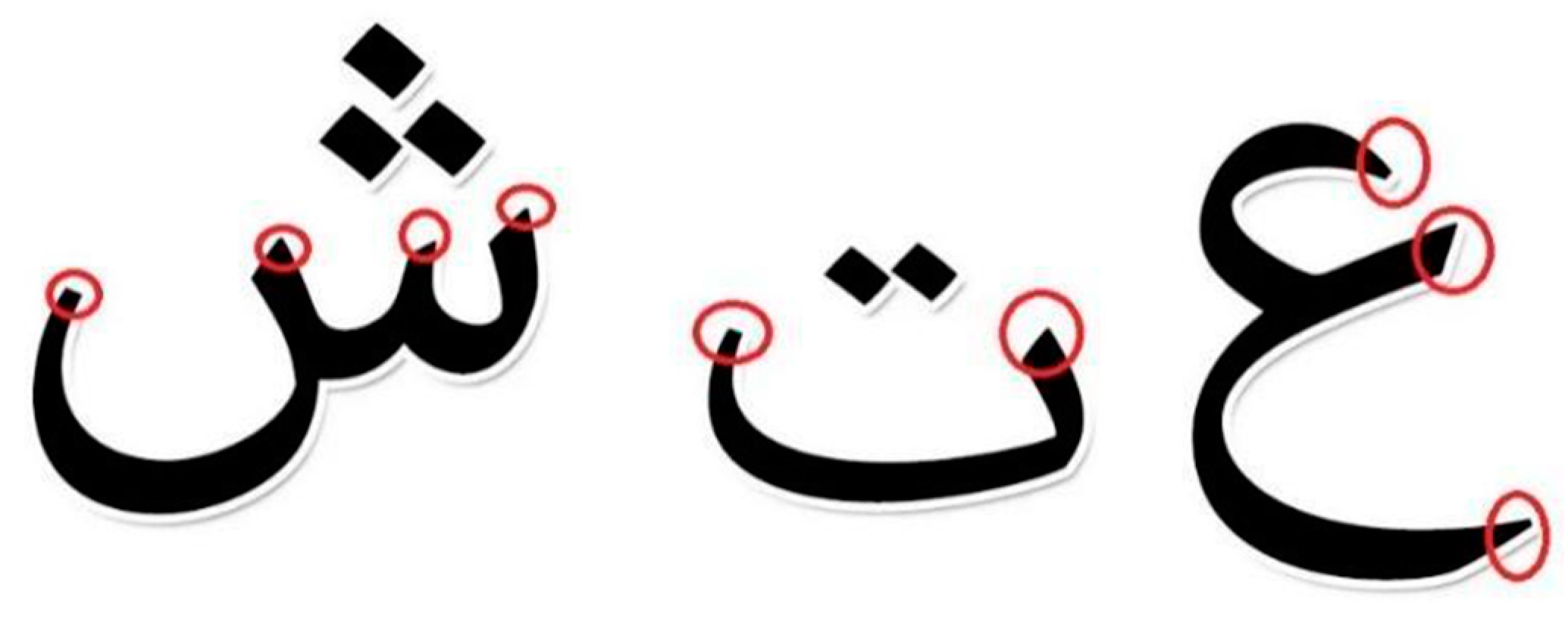



| النطق Pronunciation | الرمز Symbol | الحركة Diacritics | الحرف Letter |
|---|---|---|---|
| با |  | فتحة | الباء |
| بو |  | ضمة | |
| بي |  | كسرة | |
| ب |  | سكون | |
| بن |  | تنوين الفتح | |
| بون |  | تنوين الضم | |
| بين |  | تنوين الكسر | |
| ابب |  | الشدة |
| معزولاً Isolated | في أخرها At its End | في أوسطها In its Middle | في أول الكلمة At the Beginning of the word |
|---|---|---|---|
| ي | ــــي | ـــــيــــــ | يــ |
| ك | ــــك | ــــكـــــ | كـــ |
| The bit number of the secret message to be hidden | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | … |
| The number of the diacritic used in concealment | 1 | 5 | 50 | 70 | 71 | 72 | 80 | 100 | 102 | 104 | 105 | 106 | … |
| Password | Key | We Padded the “Key” to 16 Characters by Zeros, or MD5 Can Be Used | |
|---|---|---|---|
| Secret Message | “Message” | ||
| Encrypted Message | U3YeVbnZ6vDUksOOZSoWng== | Note: Many algorithms can be used here RSA, AES, DES, etc. | |
| Binary Message | 00011000 01010101 00110011 01011001 01100101 01010110 01100010 01101110 01011010 00110110 01110110 01000100 01010101 01101011 01110011 01001111 01001111 01011010 01010011 01101111 01010111 01101110 01100111 00111101 00111101 | Note: The first 8 bits represent the length of the message, which is 24 = 00011000 The next 8 bits represent the “U” character | |
| Cover Text Second Scenario we rely on the Hamza | :تتميّز اللّغة العربيّة عن كافّة اللّغات العالميّة الأُخرى بمجموعةٍ من الخصائص وهي: الأصوات: من المُميّزات الأساسيّة للّغة العربيّة؛ إذ يُعتَبر نظام النّطق فيها من أهمّ أنظمة الكلام اللغويّ، فيُستخدَم اللّسان، والحلق، والحنجرة من أجل نطق الحروف والكلمات بناءً على أصواتها، وتُقسَم الأصوات في اللّغة العربيّة إلى مجموعة من الأقسام، مثل أصوات الإطباق، وأصوات الحنجرة، وغيرها. المُفردات: هي الكلمات التي تتكوّن منها اللّغة العربيّة، ويُصنَّف المعجم اللغويّ الخاص فيها بأنّه من أكثر المعاجم اللغويّة الغنيّة بالمفردات والتّراكيب؛ فيحتوي على أكثر من مليون كلمة. وتُعتبر المفردات الأصليّة في اللّغة العربيّة عبارةً عن جذور ثلاثيّة للكلمات الأُخرى، فينتج الجذر اللغويّ الواحد العديد من الكلمات والمُفردات. كما أن اللفظ بالإعتماد على الحركات والصرف المرتبط بالمفردات وجزورها والنحو الذي يمثل أساس الجملة فيها … كل ذلك مما يمزها عن باقي اللغات. لذلك تُصنّف اللّغة العربيّة كواحدةٍ من اللّغات التي تَحتفظ بنظامٍ نحويٍّ خاصّ بها، ويُساعد في إعراب جُملها وبيان طُرق كتابتها.. | ||
| Text after Hiding first 16 bits. We changed 6 characters. (Green) | :تتميّز اللّغة العربيّة عن كافّة اللّغات العالميّة الأُخرى بمجموعةٍ من الخصائص وهي الأصوات: من المُميّزات الأساسيّة للّغة العربيّة؛ إذ يُعتَبر نظام النّطق فيها من اَهمّ اَنظمة الكلام اللغويّ، فيُستخدَم اللّسان، والحلق، والحنجرة من أجل نطق الحروف والكلمات بناءً على أصواتها، وتُقسَم الأصوات في اللّغة العربيّة اِلى مجموعة من الأقسام، مثل أصوات الاِطباق، واَصوات الحنجرة، وغيرها. المُفردات: هي الكلمات التي تتكوّن منها اللّغة العربيّة، ويُصنَّف المعجم اللغويّ الخاص فيها باَنّه من اَكثر المعاجم اللغويّة الغنيّة بالمفردات والتّراكيب؛ فيحتوي على أكثر من مليون كلمة. وتُعتبر المفردات الأصليّة في اللّغة العربيّة عبارةً عن جذور ثلاثيّة للكلمات الأُخرى، فينتج الجذر اللغويّ الواحد العديد من الكلمات والمُفردات. كما أن اللفظ بالإعتماد على الحركات والصرف المرتبط بالمفردات وجزورها والنحو الذي يمثل أساس الجملة فيها … كل ذلك مما يمزها عن باقي اللغات. لذلك تُصنّف اللّغة العربيّة كواحدةٍ من اللّغات التي تَحتفظ بنظامٍ نحويٍّ خاصّ بها، ويُساعد في إعراب جُملها وبيان طُرق كتابتها. | ||
| Encrypted text | 0gO0UBikrTtP4eH0gY6QKjak5P5C5QnqTNEI8pwR8hWO/fB88MabKXayAEUNr2wuCRKVSTwXkqkBesLfB99AvJ1N059XLOKKcVo8sB66V8G2LZh9ou53RrRHqz1hNDSd8DSIMHFDbNWcUrVE9iGXsuwsTLltQUdymYLAKvCbGB+84MbFrVgkCN0B7/ouKqHthBH1+3lMzx0nJzDtt/5pPM5jhT3MFBzE30XGbRclLBjBfW8eYXYdZHBJg9pqdD8vSTY2axH9ksNkY6zygslGHM/rlTPbuo0s1baTg5ws3SUkoqC1RO4xihHSNyUvahX5iNsPtCANrZnCVRC5Rjx4py8LC67IqhDxmT+yFDBOtWMkF6O31LnfmrNv1DqTvuwiiTweBymyyLzz1SdkfbWsY9CQgoX/+83kCR1os0YaedToVvtffrbKgej9OSVPVunpthqDVXf0DMvhDCHAnVfiQNAYXkhoODTP/pWBzBDta1eEtysfg4D4uGA9uwcqGqohrfc2utuogNHIrTj/UfiWSFo9IM1vC3TJ1VVS/8Dt4gW7n9zHhlLsa10BRAXpwdFByjnPjua5nvI1kDLH/FS9S7O94p6CMAJuHWt9bYKMxFaW41zecnmTAwgbtGnIWe33TbrZ/iavv30Q9+7ZTStI5KZlLqw8lugy9hk7jyOT2TL5S8bLF/0TKgoIi0AOztjBHnruglBeMK/ziovHkNR6xDak5P5C5QnqTNEI8pwR8hWkTzcQZn1gEWPzypkjDM3iZi57j7TxNa8QJMjHJJdMB1FNx5MqN1pU5EDHu9QpFwFel5UKY67bD4OQdEd+mQgBTahTRzrMWFJTi/zx7VQr2uNGBzXBP140KMEQCp3JUfTN6vRRsD7C1El3O5+ZrvwJQa4EWqpZ71T/91FnVOZfUQBLLMbErO/QiQoY0ahQR5+coKkgyqIV9LtS3qIS3rAPlKxGSIAXLwVs93oU+18Yhw+okLVuGCFFLTenT5m9Q8Uf2Dl+M1In+7aSlmFnJRpeKXf12KrnwBusoGzckKnufKnsnY2tAZ0J5CV33B9ZK/NBiurNvSShmetLuR0nJ4hRB5fXvdiqUg9+ehuTE5VKmx+N4UugJ9Q0IeChmWttonBVTIkcmeLS93OhNJ1M7uRdeldGHdt8w/icIgj/JR8ko5Y209Vl51YMN/RBVbKxesey7LWLb1/YdiaxfBvdY4rNQzD2QcWieUAvxiLDS3cdHzofRQv6m1CnSX/X1pCVIXJjcwlghf7EFLx+ks7Pdn00B3xGZVACMKI/LesnwUF3KWvbuHMucbJkJ2uzGQHGQTyCCYpqNNkuXVr4jjwt2k/DHvn9vES5zXGJQC+yfS4f6OR5/UtmlreutWfXMKmPg7iwU658MduhpxwkAS2lDH4WSgQRLBf5N/C0h78WgecjdWVYbRajw267qvGKsZzJqtPOFCK2pHusqzLjc+/hHAuZiht7hUzTDEWxjasvXNQpbsfEsyP4YeXpneEB0pqRom6khskO1aikwblh9tOr+lIrEcNaf5IJhxaxPqxD3HRF/PzubE3CG/ExpyOrrJyLvhetSr1f9+jLG5LGbAovkdqCmWOy0f7DUcT8wNvIny3vtixACqlsr4xYuW/37qInkojPcbKLSoCjzhKQTDzklnkxy1TOSlwsx2nbnJELu+ZrO6CHdxOYCRCmDD8hQm5ibyFKXjKbhpkYYWRrdNDIkWXaI9q2sWmZzgTT9tLgCjcLZlgYN1Ir907Ea89t/1PeIKvCAqsRnbIQ242Yfh6imnXCcbHM9Hj4ilwyF9a0BhuWgUMvytPeA1jqNnfs+hywOPMiYxVIcuxG7fWTiIYGoIi9mlnqSThMaAE1RXXq2mr4nSnlA2N6aakJuvUoAfXoxBRM31OIKMF2o9P55XhS2EoFfkeybfFGPFxPZTZL0x4TroUzVUuAiun0lFQJU6nIC3gRdurSJ3DkbJi/P9gwX57+RDeWAVioYNxVdQp7MHiE5004eaNG7aP4AmzH1c+cJKF4uLZVAawnf+9jrXbrN/a8IayhNb/IOtzbvWhu69DOwaUwr4qFx+HzHlEwczoUoxMQb+oc1FIQ4xssaArape7dF99LkXLomxFibSudS1ToJpXHvUalvEW3ZI1LkRhFV7JcTdo+9GjG/lWR4/kwtS1MhBkZ2Mi214YSpafiE8ovnCmy37COTeeX+QcYRneNg0NPSh4pYqFmy5YZm6Kneq3eZDUJiktC2qMbSImQiors5E97lL+wvbMsrbG8vr6e9NCMyU1aXIkO9XpiUBqKjMvnVCYmxx/jDi37V1rMrB/XA+UWVYNPNhjzbEMk9GDCX1engVT3jWFsTo4Hed5/Acw5PTlsGrDoiZzFhHxw5t6QzQ== | ||
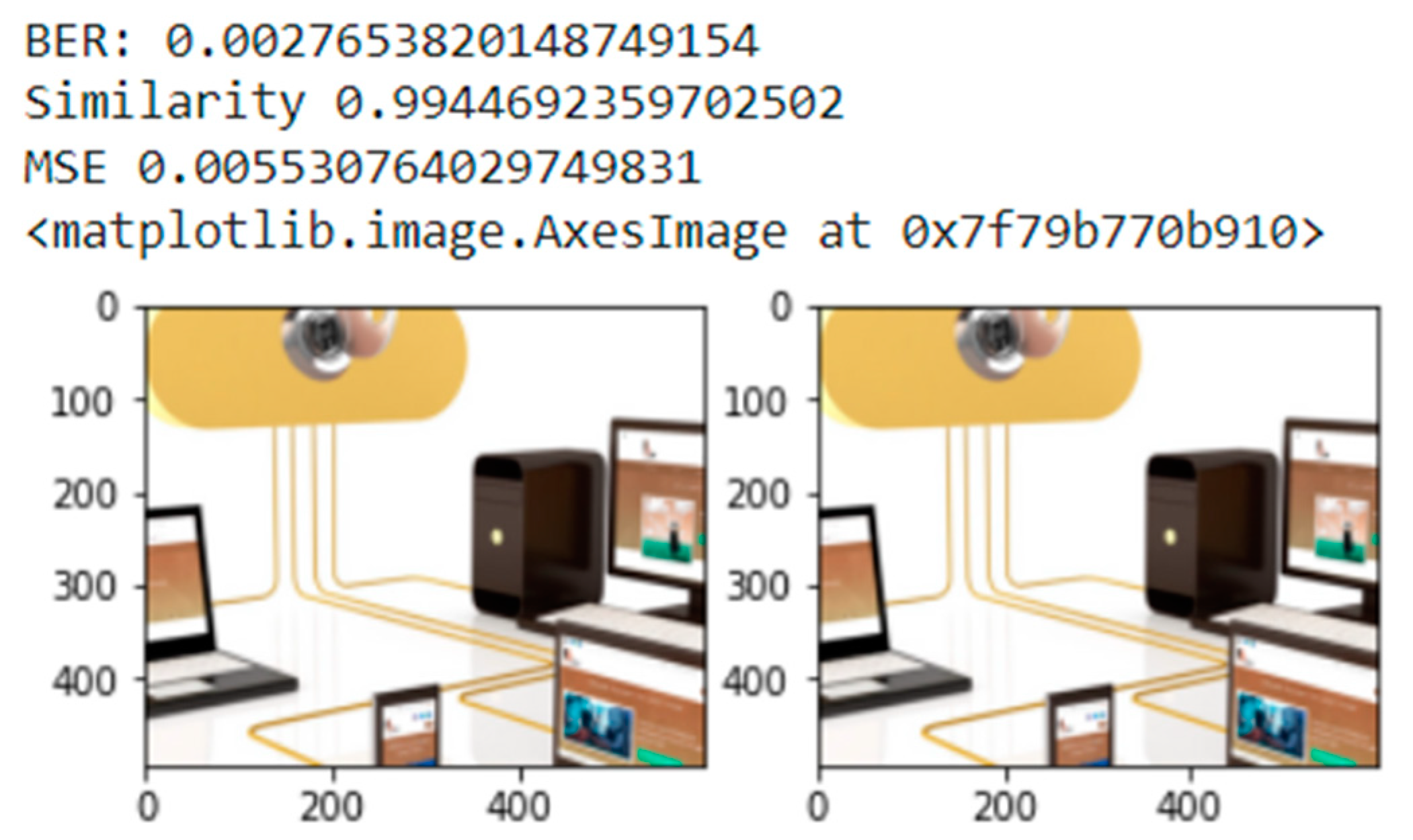
| Size of required cover | 2380 chars × 8 = 19,040 pixels will be changed Image 150 × 130 = 19,500 Pixels with three layers for RGB | ||
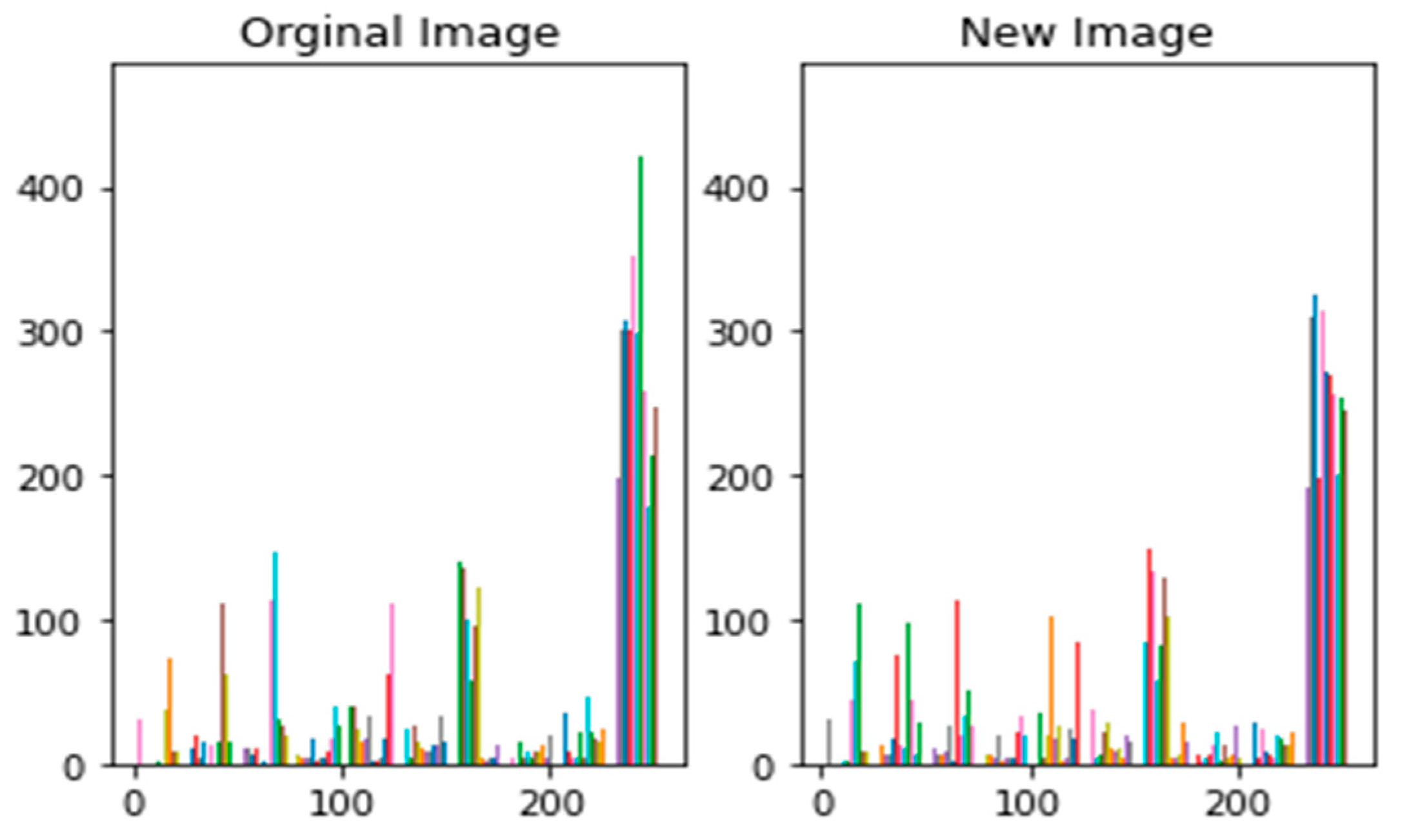
| Cover Image |  | Image after Hiding |  |
| Correlation | MSE | BER |
|---|---|---|
| 0.994 | 0.005 | 0.002 |
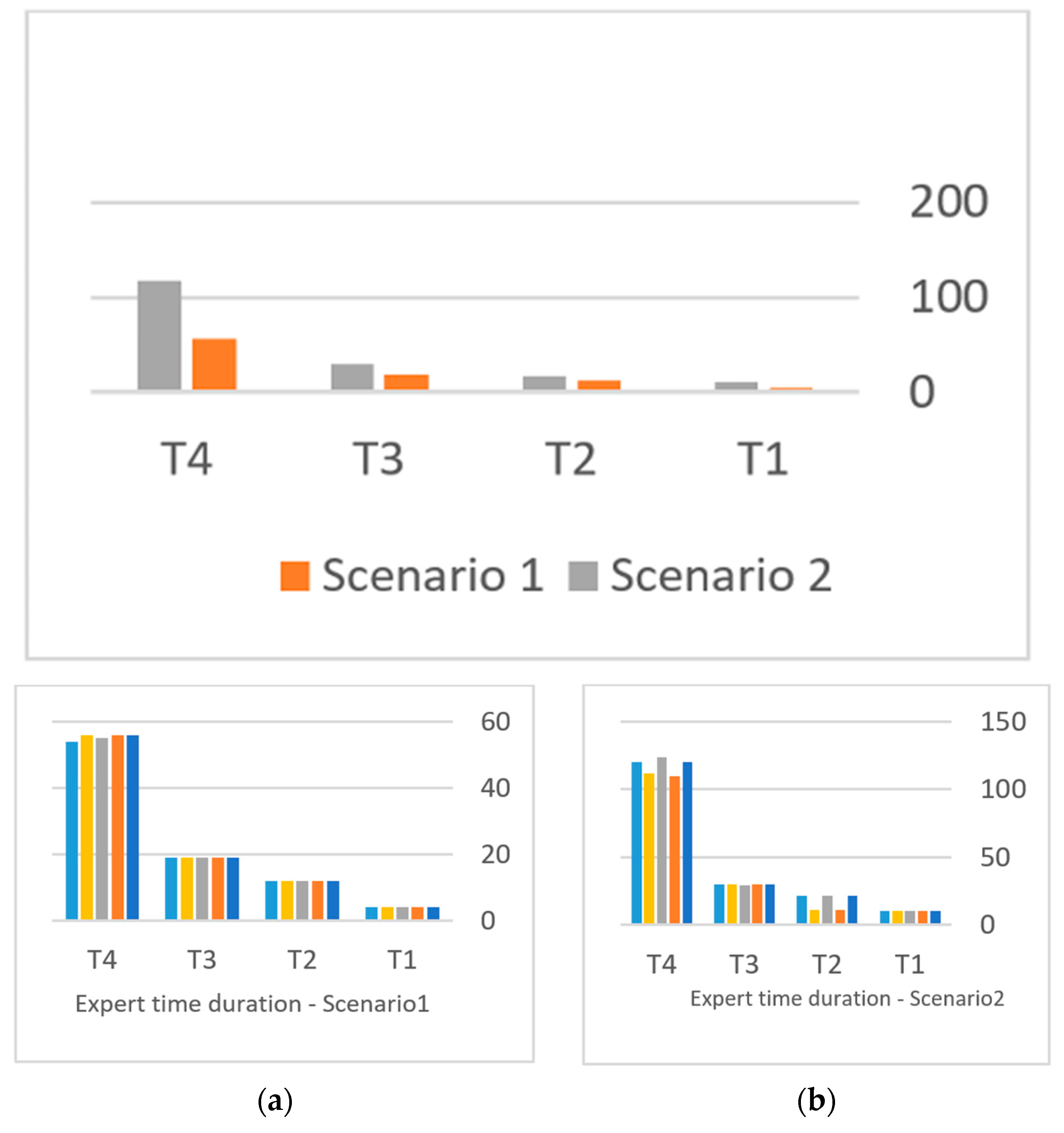
| # | Description | Size (Characters) | Number of Hamzas | Number of Diacritics | Secret msg Size (Bits) | Scenario 1 No. Changes | Scenario 2 No. Changes |
|---|---|---|---|---|---|---|---|
| T1 | Small Text without Diacritics | 120 | 20 | 0 | 10 | 4 | 10 |
| T2 | Small Text with some Random Diacritics | 719 | 17 | 21 | 10 | 5 | 11 |
| T3 | Medium Size text | 2500 | 59 | 1200 | 50 | 19 | 30 |
| T4 | relatively long | 15,000 | 310 | 7000 | 200 | 56 | 123 |
| Reference # | Approach Used | Imperceptibility | Capacity | Robustness | Security |
|---|---|---|---|---|---|
| [17] | Hybrid | high | high | high | high |
| [29] | Kashida | unknown | high | unknown | unknown |
| [32] | Diacritics | unknown | high | unknown | unknown |
| [54] | Kashida | unknown | high | unknown | unknown |
| [30] | Hybrid | high | unknown | unknown | unknown |
| [31] | Kashida | unknown | high | unknown | high |
| [33] | Kashida | unknown | high | unknown | unknown |
| [34] | Kashida | unknown | high | unknown | unknown |
| [35] | Kashida and Unicode | unknown | unknown | unknown | unknown |
| [36] | Kashida | unknown | unknown | unknown | unknown |
| [37] | shape | unknown | high | unknown | unknown |
| [55] | Kashida | unknown | high | unknown | unknown |
| [38] | Unicode | unknown | high | unknown | unknown |
| [39] | Unicode | unknown | high | unknown | unknown |
| [40] | Unicode | unknown | high | unknown | unknown |
| [41] | Unicode | unknown | high | unknown | unknown |
| [42] | Unicode | unknown | unknown | unknown | unknown |
| [43] | Unicode | high | high | unknown | |
| [44] | Diacritics | unknown | high | unknown | unknown |
| [45] | Diacritics | unknown | high | unknown | unknown |
| [56] | Diacritics | unknown | high | unknown | unknown |
| [46] | Diacritics | unknown | high | unknown | unknown |
| [47] | Diacritics | unknown | high | unknown | unknown |
| [48] | Diacritics | Low | high | unknown | unknown |
| [4] | Diacritics | unknown | high | high | high |
| our approach | Diacritics and Hamzas | high | high | high | high |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alqahtany, S.S.; Alkhodre, A.B.; Al Abdulwahid, A.; Alohaly, M. A Dynamic Multi-Layer Steganography Approach Based on Arabic Letters’ Diacritics and Image Layers. Appl. Sci. 2023, 13, 7294. https://doi.org/10.3390/app13127294
Alqahtany SS, Alkhodre AB, Al Abdulwahid A, Alohaly M. A Dynamic Multi-Layer Steganography Approach Based on Arabic Letters’ Diacritics and Image Layers. Applied Sciences. 2023; 13(12):7294. https://doi.org/10.3390/app13127294
Chicago/Turabian StyleAlqahtany, Saad Said, Ahmad B. Alkhodre, Abdulwahid Al Abdulwahid, and Manar Alohaly. 2023. "A Dynamic Multi-Layer Steganography Approach Based on Arabic Letters’ Diacritics and Image Layers" Applied Sciences 13, no. 12: 7294. https://doi.org/10.3390/app13127294
APA StyleAlqahtany, S. S., Alkhodre, A. B., Al Abdulwahid, A., & Alohaly, M. (2023). A Dynamic Multi-Layer Steganography Approach Based on Arabic Letters’ Diacritics and Image Layers. Applied Sciences, 13(12), 7294. https://doi.org/10.3390/app13127294






