Improving the Safety and Security of Software Systems by Mediating SAP Verification
Abstract
1. Introduction
1.1. Research Approach and Contribution
- A thorough literature review to extract the MFs for software SAP;
- Identifying the verification practices for SAP and the techniques used to implement these practices;
- Analyzing the impact of identified verification practices on SAP individually;
- Validate the findings with the help of case studies.
1.2. Paper Organization
2. Background
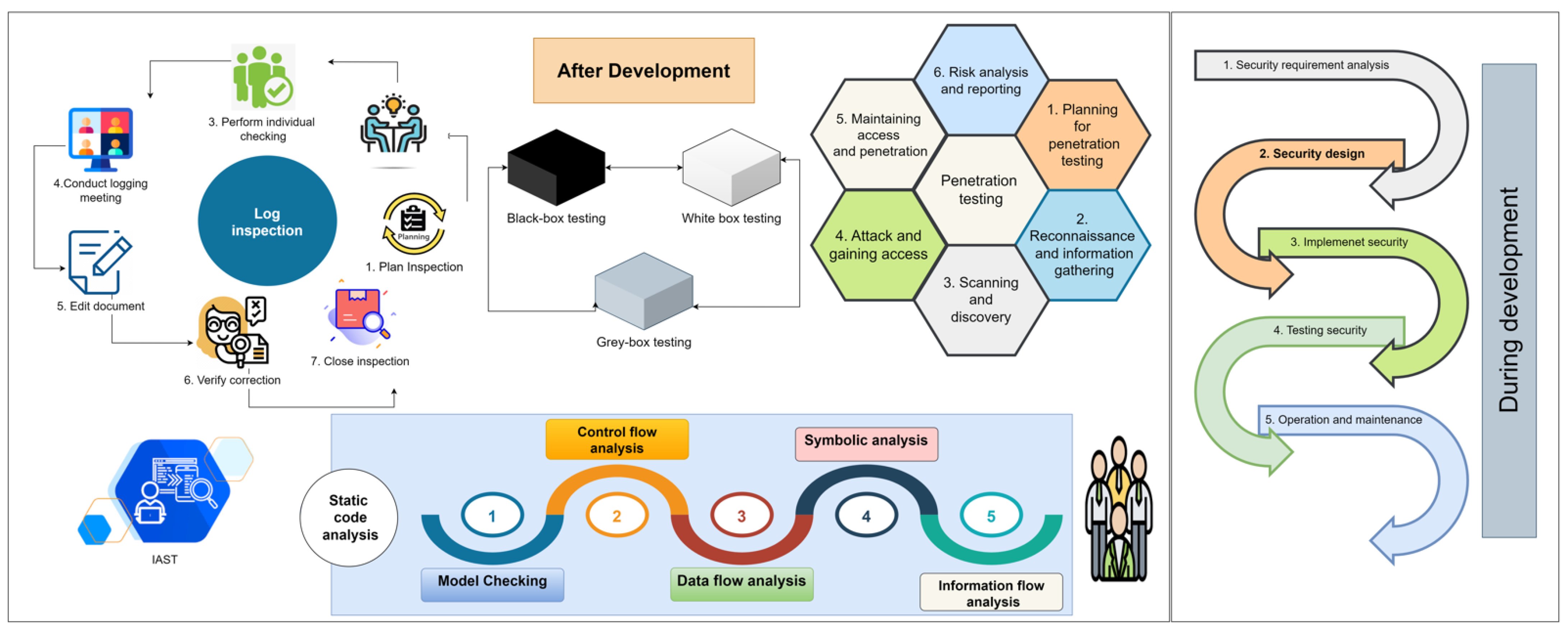
2.1. Software Security Verification
- Log inspection;
- Static code analysis;
- Profound penetration testing before release;
- Interactive application security testing (IAST).
2.1.1. SSDLC
2.1.2. Security Verification Technique
Log Inspection
Penetration Testing
Static Code Analysis
Interactive Application Security Testing (IAST)
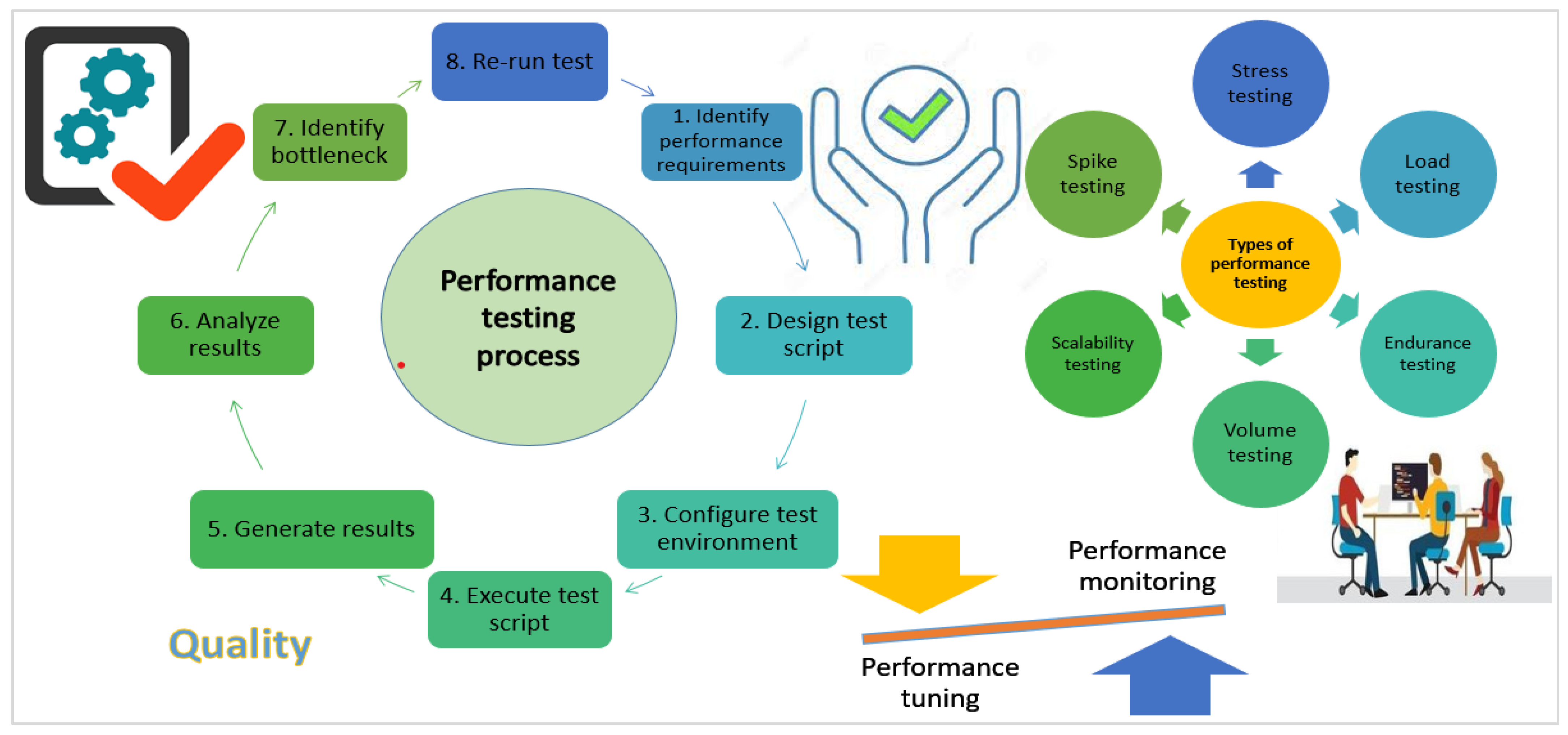
2.2. Software Performance Verification
2.2.1. Performance Verification Techniques
- They serve as a foundation for the testing;
- They aid in the tracking of a project’s progress;
- A QA team may use metrics to describe and quantify a problem to discover a solution;
- Metrics tracking over time helps the organization to compare test results and evaluate the effect of code changes.
- Assemble an exhaustive set of performance criteria by first identifying the specific business goals of your customer;
- A feature must be given an appropriate measure of success for it to be considered successful;
- If a software user receives a high performance, reliability, and functionality level, metrics should reflect this;
- Track metrics over time by doing repeated performance tests;
- Run each software item through its paces one at a time. Perform database, service, and other checks.
Log Inspection
Response Time Test
Resource Consumption Test
Throughput
3. Related Work
3.1. Existing SSDLC Models
3.1.1. SSE-CMM
3.1.2. Microsoft SDL
3.1.3. SAMM
4. Mediating Factors for SAP Verification
4.1. SAP Verification Planning and Methodology
4.2. Suitable Environment for SAP Verification
4.3. Organizational Support
4.4. Defining Complete SAP Requirements/Document Security Policy
4.5. Software Team Awareness
4.6. Cross-Functional Teams
4.7. Suitable Techniques of SAP Verification/Tool Support
4.8. SAP Monitoring and Audit/Define Measure
4.9. Allocation of Time and Budget to SAP Verification
4.10. Encourage Reusability
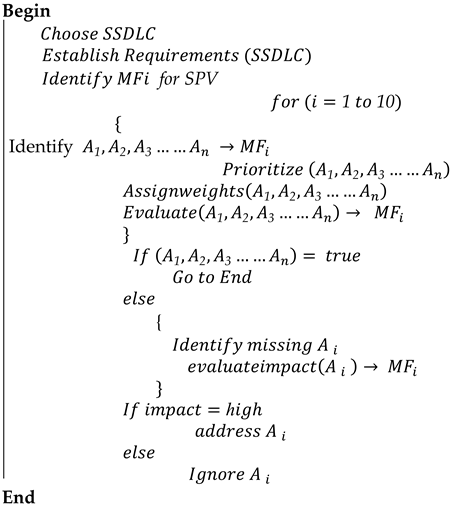
5. Proposed Methodology
| Algorithm 1: Working of the proposed Methodology |
| Let MF denote mediating factors; A1, A2, A3 …… An are actions to promote the MF; SPV refers to SAP verification, |
 |
6. Evaluation of Proposed Methodology Using Case Study
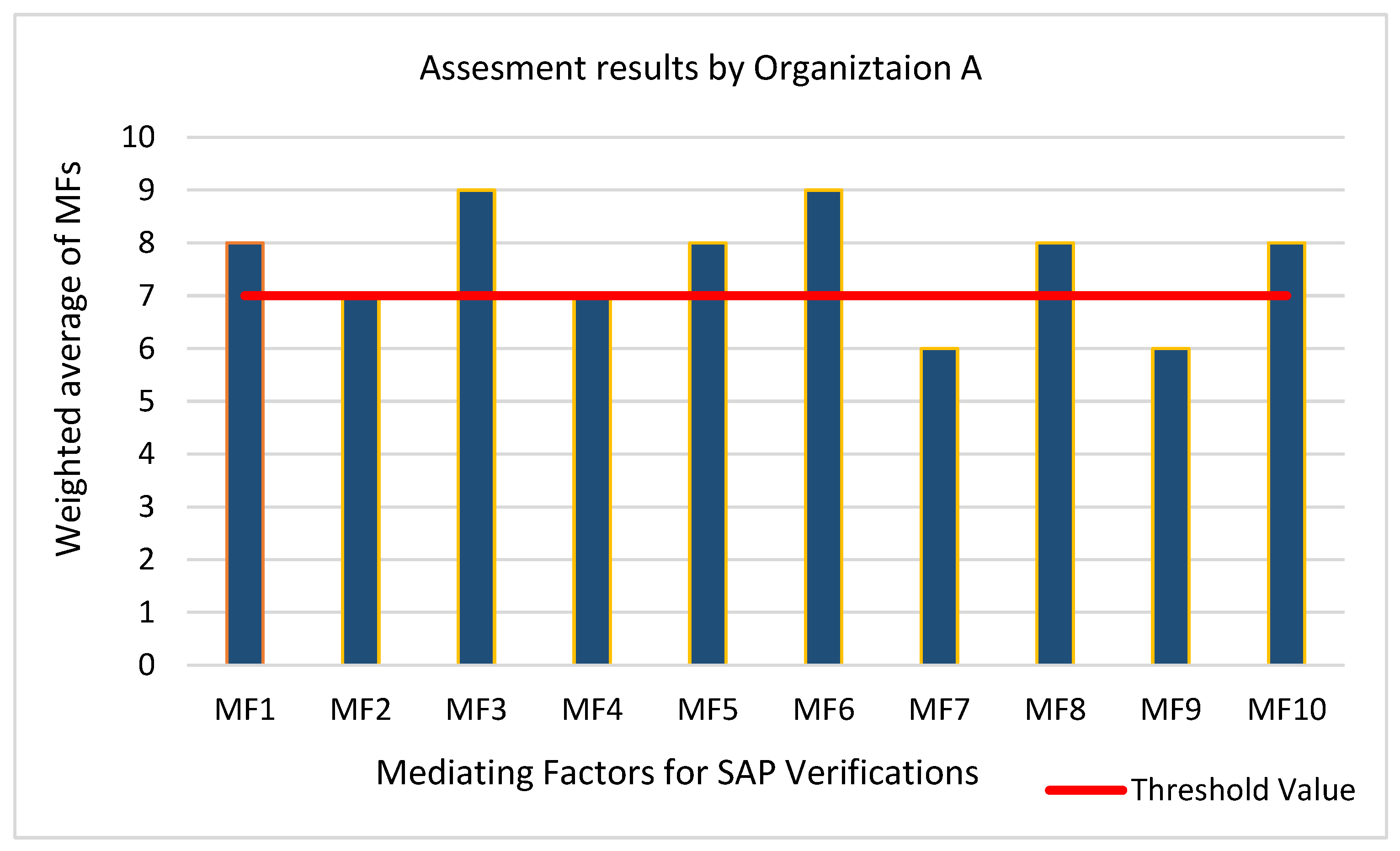
6.1. Results of an Analysis for an Organization A
- The company is committed to implementing SAP’s MFs. It has already implemented most of the specified practices since the computed values for most of the MFs were greater than or equal to the threshold value.
- Respondents said that the customer is usually unaware of the security needs of the product, due to which documenting the SAP verification requirement is a challenge.
- The organization is deficient in MF7 and MF9, indicating that management should offer tools for SAP verification and provide time and resources for SAP verification.
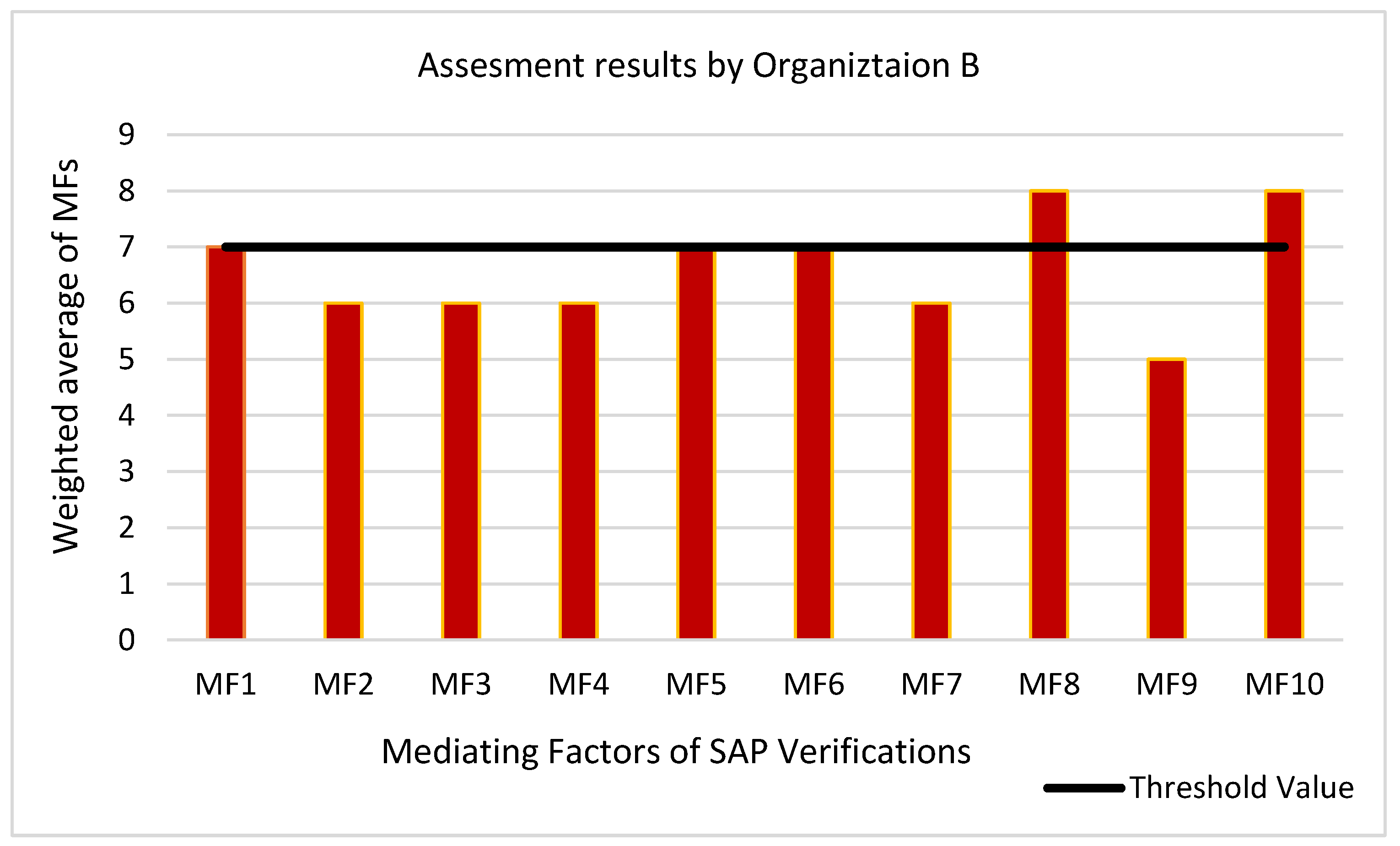
6.2. Results of an Analysis for an Organization B
- Most of the MFs have not been adapted by Organization B, as the weighted sum of most of these MFs was less than the threshold values.
- The respondents told us that organizations do not provide tool support, time and budget allocation, and training to the employees while they expect secure and quality products.
- SAP requirements are not documented properly, which hinders the process of SAP verification.
- The customer is not actively involved in documenting and testing security requirements.
- There is a need to adapt the mentioned practices to promote SAP culture in the organization.
6.3. Case Study Participants’ Recommendations/Feedback
- The participants were able to understand the proposed methodology without any assistance; they only asked for an explanation of some of the mentioned practices
- The mentioned MFs and their corresponding actions helped them to assess the current SAP verification level of their organizations
- The management team showed interest in implementing the mentioned practices in their organizations and considered them suitable for achieving a secure and quality product.
6.4. Findings and Implications
6.5. Threats to Validity
6.5.1. Construct Validity
6.5.2. External Validity
6.5.3. Internal Validity
7. Conclusions and Future Work
- This approach might be tailored to the demands of various organizations based on their facilities and methods.
- The proposed technique might be modified to include special features linked to the technologies such as IoT, big data, Blockchain, and cloud computing.
- The suggested technique might be published publicly and updated with new academic and industrial practices.
- The evaluation process might be automated in the future to reduce the burden from user’s shoulders and to remove biasedness.
- This study considered SAP as a set of unrelated metrics, which is not always correct. SAP, by its nature, tends to bear contradictions. For instance, the more cryptographically secure a software is, the less its performance metrics’ values. In the future, this issue may be addressed.
- Further evaluation cases may be added to strengthen the findings.
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Arbain, A.F.; Jawawi, D.N.A.; Kadir, W.; Ghani, I. Case study on non-functional requirement change impact traceability for Agile software development. Int. J. Adv. Sci. Eng. Inf. Technol. 2020, 10, 34–40. [Google Scholar] [CrossRef]
- Rahman, M.S.; Reza, H. Systematic mapping study of non-functional requirements in big data system. In Proceedings of the 2020 IEEE International Conference on Electro Information Technology (EIT), Chicago, IL, USA, 31 July 2020–1 August 2020; pp. 25–31. [Google Scholar]
- Alwadi, A.; Nahhas, A.; Bosse, S.; Jamous, N.; Turowski, K. A Modernized Model for Performance Requirements and their Interdependencies. In Proceedings of the 2019 IEEE/ACS 16th International Conference on Computer Systems and Applications (AICCSA), Abu Dhabi, United Arab Emirates, 3–7 November 2019; pp. 1–8. [Google Scholar]
- Alwadi, A.; Nahhas, A.; Bosse, S.; Jamous, N.; Turowski, K. Toward a performance requirements model for the early design phase of IT systems. In Proceedings of the 2018 Sixth International Conference on Enterprise Systems (ES), Limassol, Cyprus, 1–2 October 2018; pp. 9–16. [Google Scholar]
- Mirakhorli, M.; Galster, M.; Williams, L. Understanding software security from design to deployment. ACM SIGSOFT Softw. Eng. Notes 2020, 45, 25–26. [Google Scholar] [CrossRef]
- Humayun, M.; Jhanjhi, N.; Almufareh, M.F.; Khalil, M.I. Security Threat and Vulnerability Assessment and Measurement in Secure Software Development. Comput. Mater. Contin. 2022, 71, 5039–5059. [Google Scholar] [CrossRef]
- Yuce, B.; Schaumont, P.; Witteman, M. Fault attacks on secure embedded software: Threats, design, and evaluation. J. Hardw. Syst. Secur. 2018, 2, 111–130. [Google Scholar] [CrossRef]
- Yarza, I.; Agirre, I.; Mugarza, I.; Cerrolaza, J.P. 2022. Safety and security collaborative analysis framework for high-performance embedded computing devices. Microprocess. Microsyst. 2022, 93, 104572. [Google Scholar] [CrossRef]
- Aruna, E.; Reddy, A.R.M.; Sunitha, K. Secure SDLC Using Security Patterns 2.0. In IOT with Smart Systems; Springer: Berlin/Heidelberg, Germany, 2022; pp. 699–708. [Google Scholar]
- Ribeiro, V.V.; Cruzes, D.S.; Travassos, G.H. A perception of the practice of software security and performance verification. In Proceedings of the 2018 25th Australasian Software Engineering Conference (ASWEC), Adelaide, SA, Australia, 26–30 November 2018; pp. 71–80. [Google Scholar]
- Khan, R.A.; Khan, S.U.; Khan, H.U.; Ilyas, M. Systematic Literature Review on Security Risks and its Practices in Secure Software Development. IEEE Access 2022, 10, 5456–5481. [Google Scholar] [CrossRef]
- Rodriguez, M.; Piattini, M.; Ebert, C. Software verification and validation technologies and tools. IEEE Softw. 2019, 36, 13–24. [Google Scholar] [CrossRef]
- Fujdiak, R.; Mlynek, P.; Mrnustik, P.; Barabas, M.; Blazek, P.; Borcik, F.; Misurec, J. Managing the secure software development. In Proceedings of the 2019 10th IFIP International Conference on New Technologies, Mobility and Security (NTMS), Canary Islands, Spain, 24–26 June 2019; pp. 1–4. [Google Scholar]
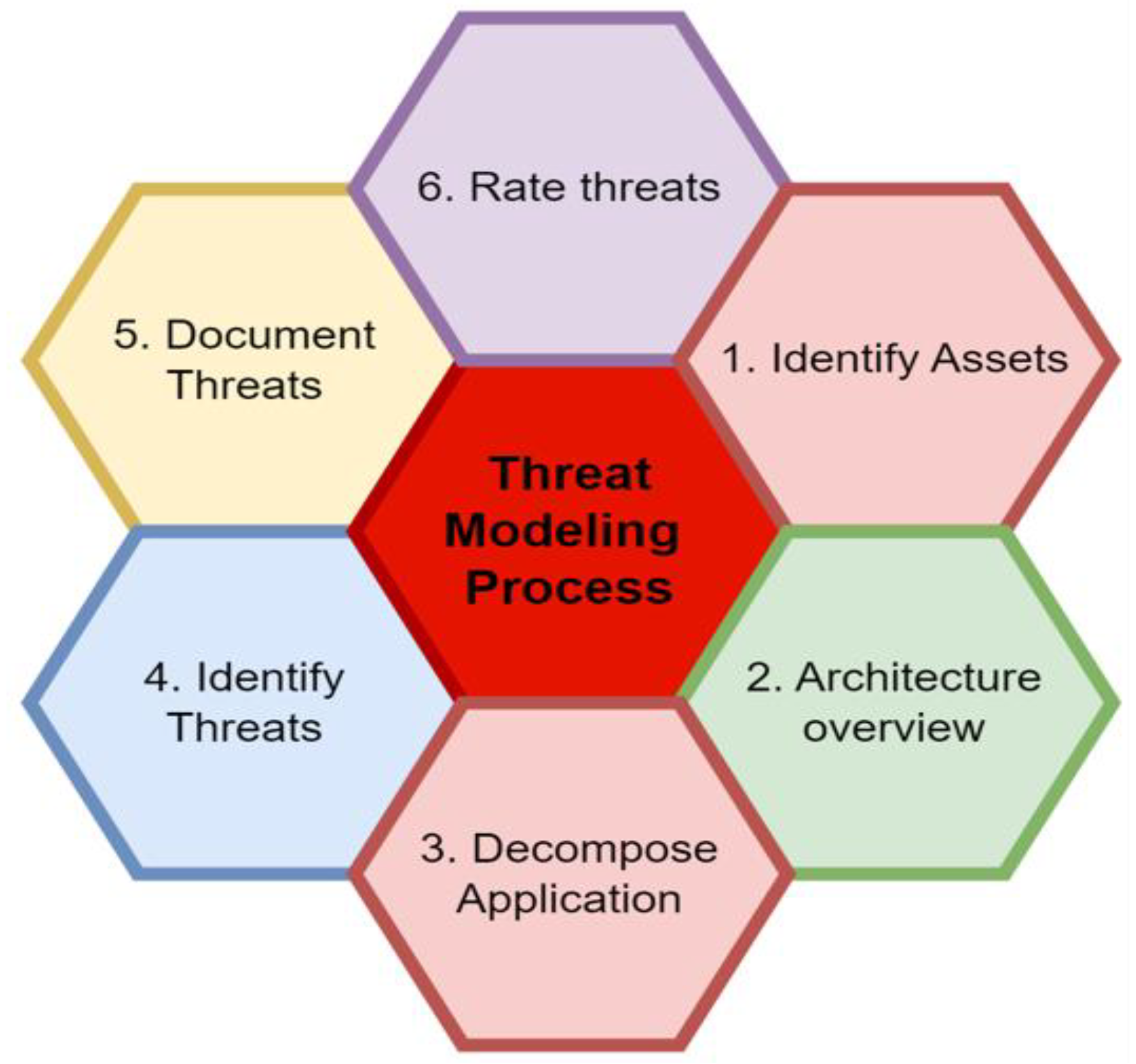
- Kamal, A.H.A.; Yen, C.C.Y.; Hui, G.J.; Ling, P.S. Risk Assessment, Threat Modeling and Security Testing in SDLC. arXiv 2020, arXiv:2012.07226. [Google Scholar]
- Varela-Vaca, Á.J.; Rosado, D.G.; Sánchez, L.E.; Gómez-López, M.T.; Gasca, R.M.; Fernández-Medina, E. CARMEN: A framework for the verification and diagnosis of the specification of security requirements in cyber-physical systems. Comput. Ind. 2021, 132, 103524. [Google Scholar] [CrossRef]
- Zhu, J.; He, S.; Liu, J.; He, P.; Xie, Q.; Zheng, Z.; Lyu, M.R. Tools and benchmarks for automated log parsing. In Proceedings of the 2019 IEEE/ACM 41st International Conference on Software Engineering: Software Engineering in Practice (ICSE-SEIP), Montreal, QC, Canada, 27 May 2019; pp. 121–130. [Google Scholar]
- Khan, S.; Parkinson, S. Discovering and utilising expert knowledge from security event logs. J. Inf. Secur. Appl. 2019, 48, 102375. [Google Scholar] [CrossRef]
- Dieber, B.; White, R.; Taurer, S.; Breiling, B.; Caiazza, G.; Christensen, H.; Cortesi, A. Penetration testing ROS. In Robot Operating System (ROS); Springer: Berlin/Heidelberg, Germany, 2020; pp. 183–225. [Google Scholar]
- Hong, K. Performance, Security, and Safety Requirements Testing for Smart Systems through Systematic Software Analysis. Doctoral Dissertation, University of Michigan Library, Ann Arbor, MI, USA, 2019. [Google Scholar]
- Ismail, A.A.; Hamza, H.S.; Kotb, A.M. Performance evaluation of open source iot platforms. In Proceedings of the 2018 IEEE global conference on internet of things (GCIoT), Alexandria, Egypt, 5–7 December 2018; pp. 1–5. [Google Scholar]
- Mandrioli, C.; Maggio, M. Testing self-adaptive software with probabilistic guarantees on performance metrics. In Proceedings of the 28th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering, Piraeus, Greece, 19–28 August 2020; pp. 1002–1014. [Google Scholar]
- Almeida, F.; Carneiro, P. Performance metrics in scrum software engineering companies. Int. J. Agil. Syst. Manag. 2021, 14, 205–223. [Google Scholar] [CrossRef]
- Guo, J.; Yang, D.; Siegmund, N.; Apel, S.; Sarkar, A.; Valov, P.; Czarnecki, K.; Wasowski, A.; Yu, H. Data-efficient performance learning for configurable systems. Empir. Softw. Eng. 2018, 23, 1826–1867. [Google Scholar] [CrossRef]
- Bengtsson, M.; Alfredsson, E.; Cohen, M.; Lorek, S.; Schroeder, P. Transforming systems of consumption and production for achieving the sustainable development goals: Moving beyond efficiency. Sustain. Sci. 2018, 13, 1533–1547. [Google Scholar] [CrossRef] [PubMed]
- Ferme, V.; Pautasso, C. A declarative approach for performance tests execution in continuous software development environments. In Proceedings of the 2018 ACM/SPEC International Conference on Performance Engineering, Berlin, Germany, 9–13 April 2018; pp. 261–272. [Google Scholar]
- Ribeiro, V.; Cruzes, D.S.; Travassos, G.H. Understanding Factors and Practices of Software Security and Performance Verification. In Proceedings of the 19th Brazilian Symposium on Software Quality, Sbcopenlib, Brazil, December 2020, Sbcopenlib, Brazil, 1–4 December 2020; pp. 11–20. [Google Scholar]
- Zhioua, Z.; Short, S.; Roudier, Y. Static code analysis for software security verification: Problems and approaches. In Proceedings of the 2014 IEEE 38th International Computer Software and Applications Conference Workshops, Vasteras, Sweden, 21–25 July 2014; pp. 102–109. [Google Scholar]
- Cortellessa, V.; Trubiani, C.; Mostarda, L.; Dulay, N. An architectural framework for analyzing tradeoffs between software security and performance. In Proceedings of the International Symposium on Architecting Critical Systems, Prague, Czech Republic, 23–25 June 2010; pp. 1–18. [Google Scholar]
- Ribeiro, V.V.; Cruzes, D.S.; Travassos, G.H. Moderator factors of software security and performance verification. J. Syst. Softw. 2022, 184, 111137. [Google Scholar]
- Hong, D.K. Requirements Testing and Verification for Smart Systems through Systematic Software Analysis. 2019. Available online: http://www.hongkedavid.com/academic/phd-defense-ke.pdf (accessed on 10 December 2022).
- Assal, H.; Chiasson, S. Security in the software development lifecycle. In Proceedings of the Fourteenth Symposium on Usable Privacy and Security (SOUPS 2018), Baltimore, MD, USA, 12–14 August 2018; pp. 281–296. [Google Scholar]
- Robey, D.; Khoo, H.M.; Powers, C. Situated learning in cross-functional virtual teams. Tech. Commun. 2000, 47, 51–66. [Google Scholar] [CrossRef]
- Ghilic-Micu, B.; Mircea, M.; Stoica, M. The audit of business intelligence solutions. Inform. Econ. 2010, 14, 66. [Google Scholar]
- Mao, M.; Humphrey, M. Scaling and scheduling to maximize application performance within budget constraints in cloud workflows. In Proceedings of the 2013 IEEE 27th International Symposium on Parallel and Distributed Processing, Cambridge, MA, USA, 20–24 May 2013; pp. 67–78. [Google Scholar]
- Sudhakar, G.P.; Farooq, A.; Patnaik, S. Soft factors affecting the performance of software development teams. Team Perform. Manag. Int. J. 2011, 17, 187–205. [Google Scholar] [CrossRef]
- Kessel, M.; Atkinson, C. Integrating reuse into the rapid, continuous software engineering cycle through test-driven search. In Proceedings of the 2018 IEEE/ACM 4th International Workshop on Rapid Continuous Software Engineering (RCoSE), Gothenburg, Sweden, 29 May 2018; pp. 8–11. [Google Scholar]
- Xu, Y.; Liu, Z.; Zhang, C.; Ren, J.; Zhang, Y.; Shen, X. Blockchain-based trustworthy energy dispatching approach for high renewable energy penetrated power systems. IEEE Internet Things J. 2021, 9, 10036–10047. [Google Scholar] [CrossRef]
- Rogachev, A. Economic and mathematical modeling of food security level in view of import substitution. Asian Soc. Sci. 2015, 11, 178. [Google Scholar] [CrossRef]
- Rashid, Y.; Rashid, A.; Warraich, M.A.; Sabir, S.S.; Waseem, A. Case study method: A step-by-step guide for business researchers. Int. J. Qual. Methods 2019, 18, 1609406919862424. [Google Scholar]
- Al-Matouq, H.; Mahmood, S.; Alshayeb, M.; Niazi, M. A maturity model for secure software design: A multivocal study. IEEE Access 2020, 8, 215758–215776. [Google Scholar] [CrossRef]
- Niazi, M.; Cox, K.; Verner, J. A measurement framework for assessing the maturity of requirements engineering process. Softw. Qual. J. 2008, 16, 213–235. [Google Scholar] [CrossRef]
- Niazi, M.; Saeed, A.M.; Alshayeb, M.; Mahmood, S.; Zafar, S. A maturity model for secure requirements engineering. Comput. Secur. 2020, 95, 101852. [Google Scholar] [CrossRef]
- Niazi, M.; El-Attar, M.; Usman, M.; Ikram, N. An empirical study identifying high perceived value requirements engineering practices in global software development projects. In Proceedings of the 7th International Conference on Software Engineering Advances (ICSEA), Lisbon, Portugal, 18–23 November 2012; pp. 283–288. [Google Scholar]
| Abbreviations | Full Form |
|---|---|
| IAST | Interactive application security testing |
| MF | Mediating factors |
| MS-SDL | Microsoft security development lifecycle |
| NFR | Non-functional requirements |
| QA | Quality assurance |
| RE | Requirement engineering |
| ROI | Return on investment |
| SAMM | Software assurance maturity model |
| SCA | Static code analysis |
| SDLC | Software development lifecycle |
| SSD | Secure software development |
| SSDLC | Secure software development lifecycle |
| SSE-CMM | System security engineering capability maturity model |
| SAP | Security and performance |
| SVTs | Security verification techniques |
| ZAP | Zed attack proxy |
| Security Practices | SSE-CMM | MS-SDL | SAMM |
|---|---|---|---|
| Physical security | Yes | No | No |
| Logical security | Yes | No | No |
| Definition of security requirements | Yes | Yes | Yes |
| Secure configuration management | Yes | No | No |
| Following all applicable laws, policies, and procedures | Yes | No | Yes |
| Threat modeling | Yes | Yes | Yes |
| Risk analysis | Yes | Yes | Yes |
| Security architecture | Yes | Yes | Yes |
| Security training and awareness | Yes | Yes | Yes |
| Secure design | Yes | Yes | Yes |
| Source code analysis | No | Yes | Yes |
| Vulnerability analysis | Yes | Yes | Yes |
| Security verification | Yes | Yes | Yes |
| Vulnerability management | Yes | Yes | Yes |
| Secure development techniques and applications | Yes | Yes | Yes |
| Security in an active operating environment | Yes | Yes | Yes |
| Secure integration with peripheral | Yes | Yes | Yes |
| Secure delivery | Yes | No | Yes |
| MFs | MFs Detail | Actions | Actions/Practices to Promote MFs |
|---|---|---|---|
| MF1 | SAP verification planning and methodology | A1 | Use of tools to guide planning |
| A2 | Define acceptance criteria | ||
| A3 | Define systematic verification methodology | ||
| A4 | Choose a methodology that meets stakeholder demands and avoids sloppy methods | ||
| A5 | Create and update procedures that fit the defined methodology and organizational needs | ||
| MF2 | Suitable environment for SAP verification | A1 | Execution environment simulation with virtualization technology |
| A2 | Keeping the verification team up to date on the latest technology utilized in the project | ||
| A3 | Assembling test agents in a virtual environment | ||
| A4 | Using automated verification | ||
| A5 | Simulating a software’s actual behavior by mimicking actions | ||
| MF3 | Organizational support | A1 | Keeping the software team updated on SAP |
| A2 | Educating the customer on the current situation of SAP | ||
| A3 | Regular security meetings | ||
| A4 | Resource assignment for SAP verification | ||
| A5 | External audit to support SAP verification | ||
| A6 | Promoting training | ||
| MF4 | Defining complete SAP requirements/document security policy | A1 | Using techniques for the identification of SAP requirements |
| A2 | Involving the verification team in the RE process | ||
| A3 | Motivating the verification team to examine the testability of the specifications | ||
| A4 | Involving the RE team in SAP verification activities | ||
| MF5 | Software team awareness | A1 | Promote training |
| A2 | Keeping the development team well-informed about SAP | ||
| A3 | Regular meetings | ||
| MF6 | Cross-functional teams | A1 | Building a team with multiple skills |
| A2 | Invest in training to improve team qualification | ||
| A3 | Promoting interaction and communication | ||
| A4 | Encourage agile/scrum | ||
| A5 | Hire qualified people | ||
| A6 | Leader swapping | ||
| MF7 | Suitable techniques of SAP verification/tool support | A1 | Identification of suitable tools |
| A2 | Encourage the use of freely available tools | ||
| A3 | Allow the verification team to suggest tools | ||
| A4 | Training of new tools | ||
| A5 | Support from the tool vendor | ||
| A6 | Using best practices toolset | ||
| A7 | Develop a culture of tool usage | ||
| MF8 | SAP monitoring and audit/define measure | A1 | Define key metrics relevant to project needs |
| A2 | External audit | ||
| A3 | Monitoring plans | ||
| [MF9 | Allocation of time and budget to SAP verification | A1 | Budget forecasting |
| A2 | Categorizing budget | ||
| A3 | Budgetary control | ||
| A4 | Keep customers informed about the benefit of SAP verification | ||
| MF10 | Encourage reusability | A1 | Keep track of prevalent faults and utilize test cases to discover their failures. |
| A2 | Using other comparable systems’ expertise to define the needs | ||
| A3 | Reusing functional test cases that reflect real-world use | ||
| A4 | Adapting settings from related systems test scenarios | ||
| A5 | Vulnerability mapping by domain to identify situation-specific vulnerabilities | ||
| A6 | Design real-time scenarios |
| Scales | Definition |
|---|---|
| 0 (poor) | Management does not feel the need to implement/adapt MFs and their corresponding practices for SAP verification |
| 2 (weak) | Management realized the importance of adapting MFs and their corresponding practices for SAP verification |
| 4 (Fair) | Management has defined a plan for the adaptation of MFs and their corresponding practices for SAP verification |
| 6 (marginally qualified) | MFs and their corresponding practices for SAP verification are used for some projects |
| 8 (Qualified) | Management has integrated the MFs and their corresponding practices in the SAP verification process |
| 10 (Expert) | Management is fully committed to using MFs and their corresponding practices for SAP verification throughout the organization |
| MF1 | A1 | A2 | A3 | A4 | A5 |
|---|---|---|---|---|---|
| W | 1 | 0.9 | 1 | 0.9 | 0.8 |
| X | 9 | 10 | 8 | 8 | 8 |
| WX | 9 | 9 | 8 | 7.2 | 6.4 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Almufareh, M.F.; Humayun, M. Improving the Safety and Security of Software Systems by Mediating SAP Verification. Appl. Sci. 2023, 13, 647. https://doi.org/10.3390/app13010647
Almufareh MF, Humayun M. Improving the Safety and Security of Software Systems by Mediating SAP Verification. Applied Sciences. 2023; 13(1):647. https://doi.org/10.3390/app13010647
Chicago/Turabian StyleAlmufareh, Maram Fahaad, and Mamoona Humayun. 2023. "Improving the Safety and Security of Software Systems by Mediating SAP Verification" Applied Sciences 13, no. 1: 647. https://doi.org/10.3390/app13010647
APA StyleAlmufareh, M. F., & Humayun, M. (2023). Improving the Safety and Security of Software Systems by Mediating SAP Verification. Applied Sciences, 13(1), 647. https://doi.org/10.3390/app13010647








