Hyperledger Fabric Access Control for Industrial Internet of Things
Abstract
:1. Introduction
2. Preliminary
2.1. Internet of Things
- Physical Devices and Controllers:Multiple physical devices and controllers are considered as “Things” in the Internet of Things. There exist all types of sensors, devices, machines, or intelligent edge nodes, to receive and transmit data between terminal equipment.
- Connectivity:The most important factor of IoT is the connectivity with reliable and instant data transmission. Different technology has been explored to propagate data such as radio frequency identification (RFID), cellular networks (4G/5G), Wi-Fi, Blue-tooth, ZigBee, routers, and switches.
- Edge Computing:Edge computing is a decentralized computing architecture, where a huge number of services are processed by a central node to divide into smaller tasks and distribute to edge nodes for processing. The edge node is close to the terminal device, which can make the transmission speed and data processing faster and reduce the delay. It is suitable for processing big data. Edge software has many service applications, and some can be completely independent of vertical applications. The most typical application is Microsoft’s Cognitive Service, an intelligent data analysis model based on Azure’s machine learning. Setting up edge nodes in the place closest to the data source can provide the computing power of the cognitive service data analysis model. Without the need to send data to the cloud, costs on transmission time and analysis results can be reduced.
- Data Accumulation:Data accumulation is to convert real-time data to static format, filter, and reduce the amount of data before being sent to database storage. The stored data can then be used by the other applications when it is not timely.
- Data Abstraction:Data abstraction unifies data formats from different databases and integrates them into the same place. Identity verification and authorization could be used to protect data through regularization, and indexing could provide quick access.
- Applications:Applications on personal computers, smart devices, and other equipment could verify data analysis results, receive early warning notifications, and provide the correct information to support users on decision makings and actual actions.
- Collaborations and Processes:Collaborations and processes are critical in IoT since most actions require the involvement of multiple devices and users.
2.2. Blockchain Concept
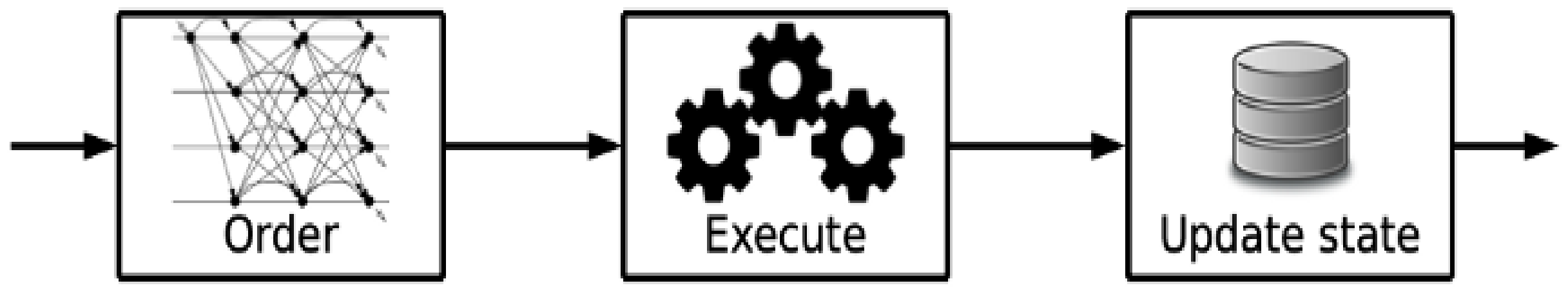
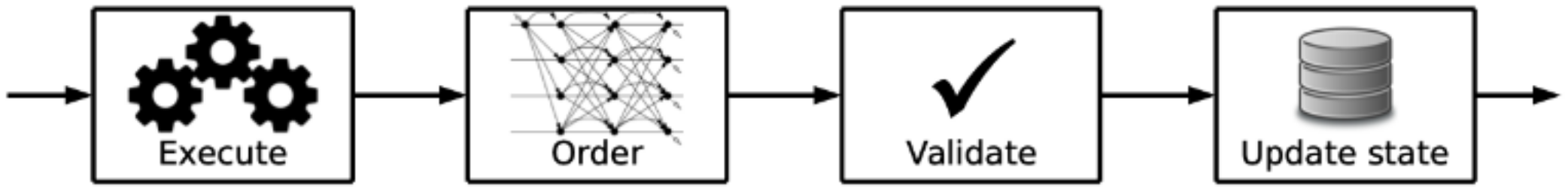
2.3. Hyperledger Fabric
2.4. Industrial Internet of Things (IIOT)
2.4.1. IIoT Concept
2.4.2. IIoT Security Issue
- Insecure IoT Gateway:IoT gateways are responsible for connecting IIoT devices with the cloud. IoT gateways access and analyze sensor data to make important decisions. Since the gateway is the medium for communication between IIoT devices, a secure design is required. IIoT devices become vulnerable to cyber threats such as MITM and DDoS. If IoT gateways are inadequately secured and compromised by these cyber threats, the entire IIoT network is at serious risk [7].
- Inefficient and Insecure Protocol, Server, and Access:We discuss this security issue on each of the following layers. Data collection layer, where most IIoT devices are located at. Devices might be vulnerable to viruses which lead to the construction of huge IoT botnet DDoS attacks.The data transport layer is responsible for combining sensor networks, mobile networks, and the internet. The communication protocol commonly used by IIoT is MQ Telemetry Transport (MQTT), which does not provide any encryption and authentication. As a result, intercepting data while communicating with other devices becomes easier and more vulnerable to threats [19].Data processing layer, where the data are processed with requirements of communication with servers, historical data servers, and remote monitoring of terminals. Firewalls cannot identify forged packets that conform to protocols and access control rules. Therefore, they are very easy to evade firewalls. Therefore, to transmit data securely, a secure communication protocol is required. Due to the use of MQTT transmission, the way of sharing data becomes vulnerable to network attacks, and more importantly, there should be an access control protocol so that only authorized parties can access the data. Thus, confidentiality, integrity, and availability of data will be achieved.
- Unsafe Cyber-Physical System:Cyber-Physical System (CPS) combines the Internet (cyber world) with the real world (physical). Many advanced systems adapted CPS such as self-driving cars, airplanes, smart homes, and smart factories. CPS is the foundation of IIoT, which handles a large amount of information and can better control and monitor the program. CPS is composed of IT equipment and connected, so there are many security loopholes, which become a concern for IIoT security [20]. CPS is vulnerable to cyber-attacks in the following ways [7]: Equipment, is vulnerable to physical attacks such as side-channel attacks and reverse engineering. Software is vulnerable to malicious attacks including Trojans and viruses. Communication Protocol is vulnerable to protocol attacks such as MITM and DDoS attacks. CPS Manufacturing System is vulnerable to social attacks, such as phishing and social engineering.
- Integration of information systems and operating systems:Industrial Control System (ICS) is a general term covering different information systems and technologies, such as Supervisory Control and Data Acquisition (SCADA), Distributed Control System (DCS), Programmable Logic Controller (Programmable Logic Controller, PLC), and so on. With the use of IIoT, the repositioning of the Industrial Control System (ICS) has greatly impacted the industry. The connection to the Internet and the sudden integration of IT in ICS makes it vulnerable to cybersecurity risks. Because OT systems are not designed with security in mind, it increases the risk of cyber-attacks on the IIoT. According to Industrial Cybersecurity 2018, most companies implementing IIoT (65%) believe there is a high risk of security breaches and attacks due to the sudden integration of OT in the IIoT environment. Unprotected network connectivity of OT environments and uncertain security issues due to the combination of IT and OT are both risky for IIoT technology. Therefore, secure IT and OT and secure ICS are required to protect the IIoT from damage.
- Unsafe SCADA:SCADA is a network of smart devices used to control and monitor specific machines or systems or processes. Machines or systems are connected to smart devices with the help of sensors. It helps to study the output produced by the device and make important decisions. SCADA provides control of the software using a programmable logic controller (PLC) that is part of the IIoT. This makes SCADA part of the IIoT and why it is important to implement the IIoT. According to SCADA systems having security vulnerabilities, these vulnerabilities have also become a threat to the IIoT. These security issues include Trojans, worms, DoS attacks, etc. Therefore, a secure SCADA is required to increase the efficiency and enhance the functionality of the IIoT.
2.5. Access Control
2.5.1. Discretionary Access Control (DAC)
2.5.2. Mandatory Access Control (MAC)
2.5.3. Role-Based Access Control (RBAC)
2.5.4. Attribute-Based Access Control (ABAC)
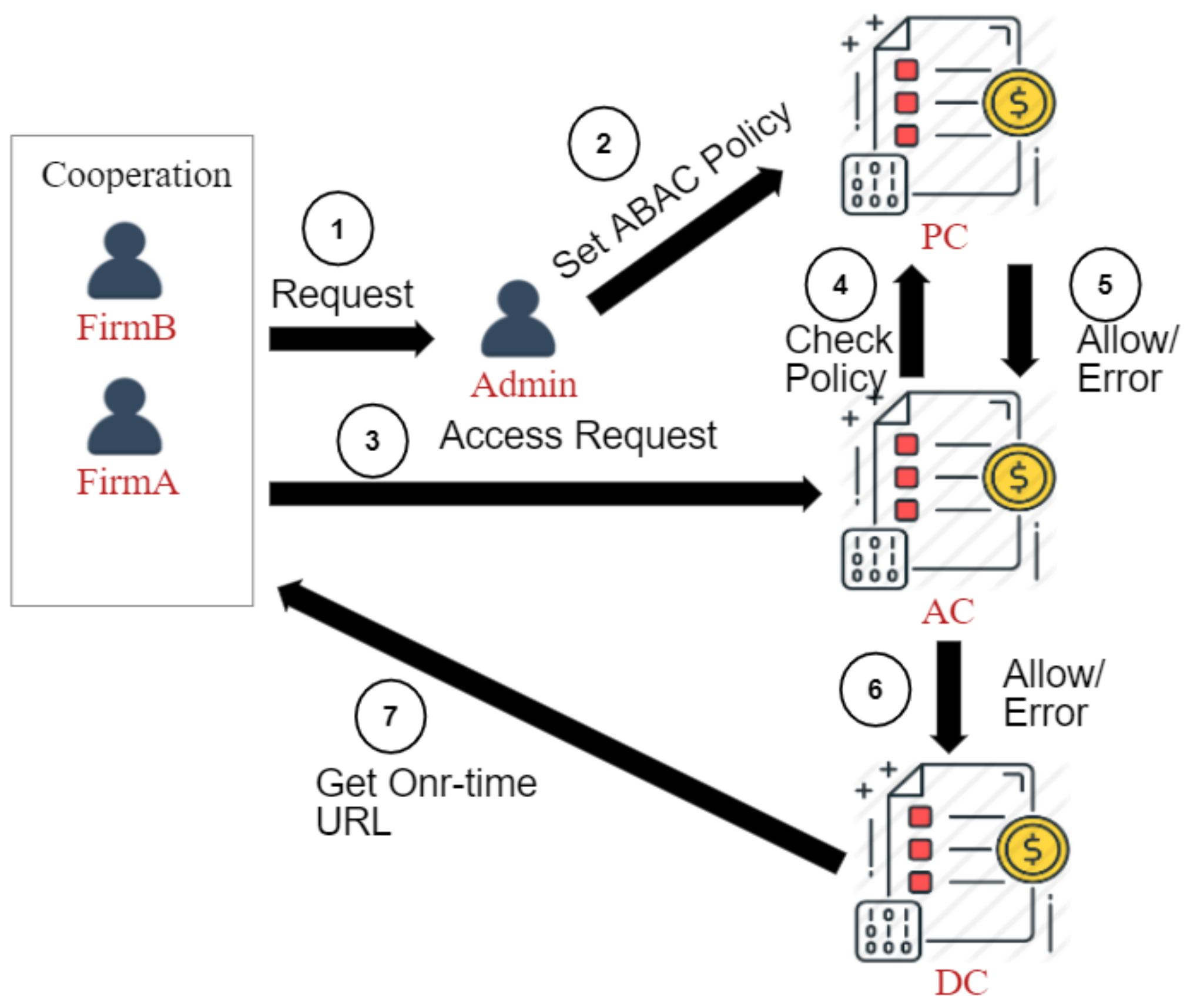
3. System Architecture
3.1. Smart Contract Design
3.1.1. Policy Contract (PC)
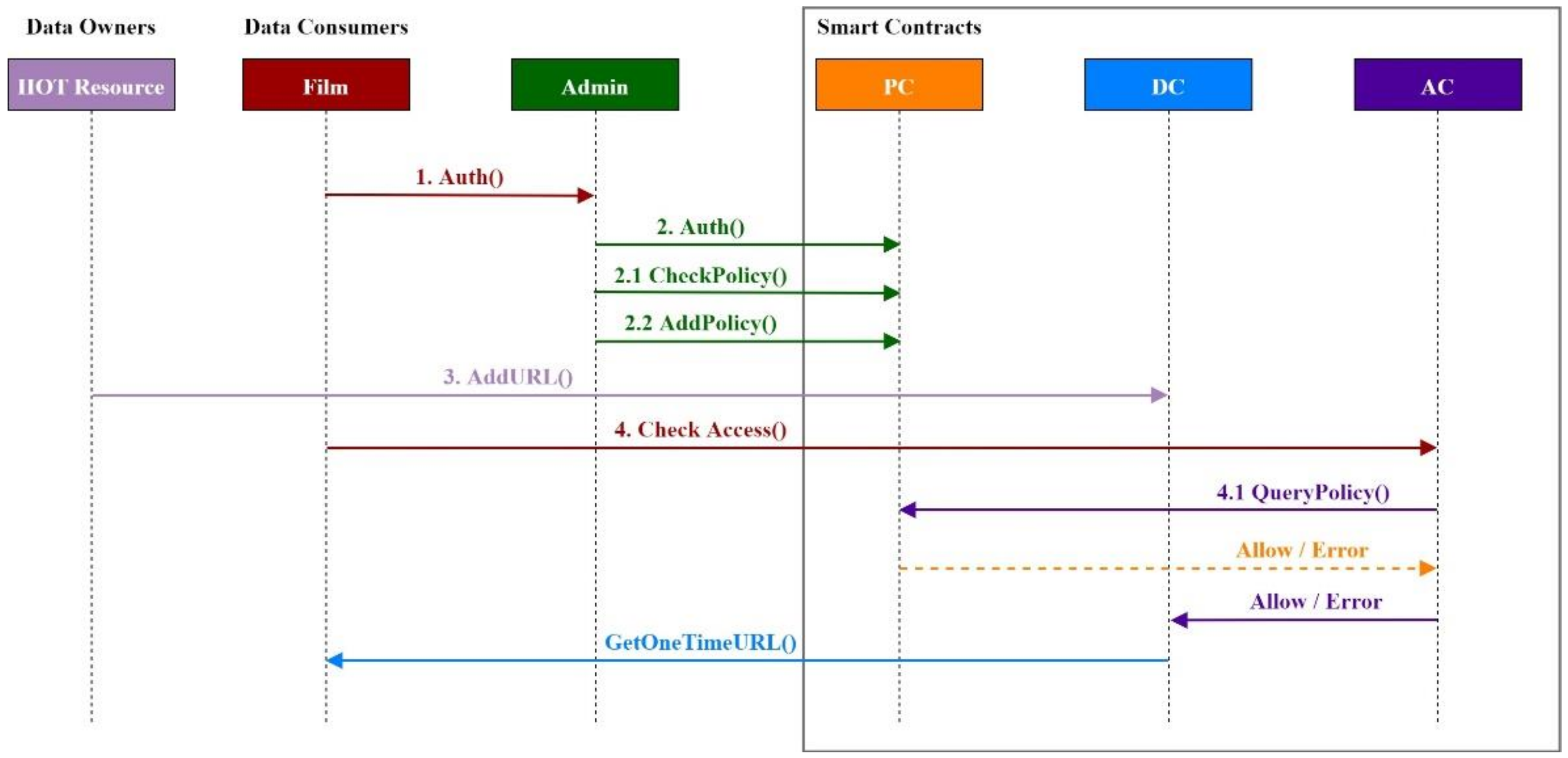
- Auth():The administrator and the data consumer define the ABAC Policy and transmit the request to the blockchain system. The administrator encrypts the data with the PC node’s public key and then signs the request with the private key. The PC calls Auth() to authenticate the admin using its public key and decrypt the data using its private key.
- CheckPolicy():The function to validate the ABAC policy, as shown in Algorithm 1.
| Algorithm 1: Check ABAC policy |
| Input: ABAC Policy Output: True or False <AS,AO,AE,AP>←ABAC Policy IsOK = True for item in AS do: if item ∉ <userID, role>then IsOK = False endif end for for item in AO do: if item ∉ <DeviceID, MAC>then IsOK = False endif end for if AE != 1 or 0 IsOK = False end if for item in AP do: if item ∉ <createTime,EndTime,allowedIP>then IsOK = False end if end for return IsOK |
- AddPolicy():The function to add the ABAC policy to the state database (SDB) in the Hyperledger, as shown in Algorithm 2.
| Algorithm 2: Add policy to blockchain |
| Input: ABAC Policy Output: Error or null @implement SmartContract Interface API stub ChaincodeStub←Invoke() if CheckPolicy (ABAC Policy) == False return Error (‘Wrong Policy’) end if ID ← SHA256(ABAC Policy.AS+ ABAC Policy.AO) err ← APIstub.PutState(ID, ABAC Policy) if err != null then return Error (err. Text) end if return null |
- DeletePolicy():Deletion of the policy occurs in two cases: when the administrator actively deletes the policy by calling this function, or when the CheckAccess() method is executed and the “end-Time” shows expired, then it will call this function in the PC to delete the relevant policy, as shown in Algorithm 3.
| Algorithm 3: Delete ABAC Policy form blockchain |
| Input: AS, AO Output: Error or null @implement SmartContract Interface API stub ChaincodeStub←Invoke() ID ←SHA256(AS + AO) err ←APIstub.GetState(ID) if err ! = null then return Error (err. Text) end if APIstub.DeleteState(ID) if err != null then return Error (err. Text) end if return null |
3.1.2. Device Contract (DC)
- AddURL():The function to store the URL in SDB using DeviceId the primary key.
- GetOne-TimeURL():The function to generate a one-time URL by querying SDB with the DeviceId.
3.1.3. Access Contract (AC)
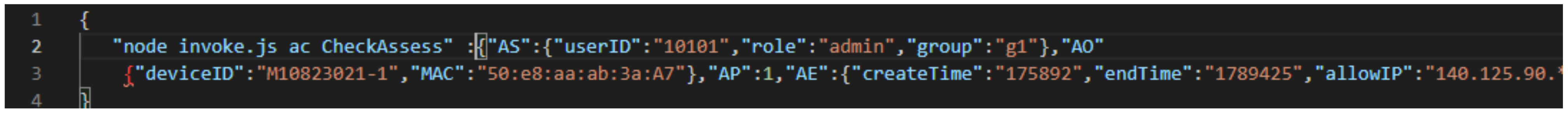
| Algorithm 4: Check user’s access |
| Input: ABAC-Request Output: Error or one-time URL < AuS;AuO;AuE >←GetAttributes(ABAC-Request) P=<P1,P2,P3…..Pn>←PC.QueryPolicy(AuS, AuO) if P = = Null then return Error end if for P in< P1,P2,P3…..Pn > do <AP,AE>←P if Value(ApP) = = ‘deney’ then continue if AuE∩ApE then continue URL←DC.GETONE_TIMEURL(AuO) end for if One-time != Null then return One-time URL else return end if |
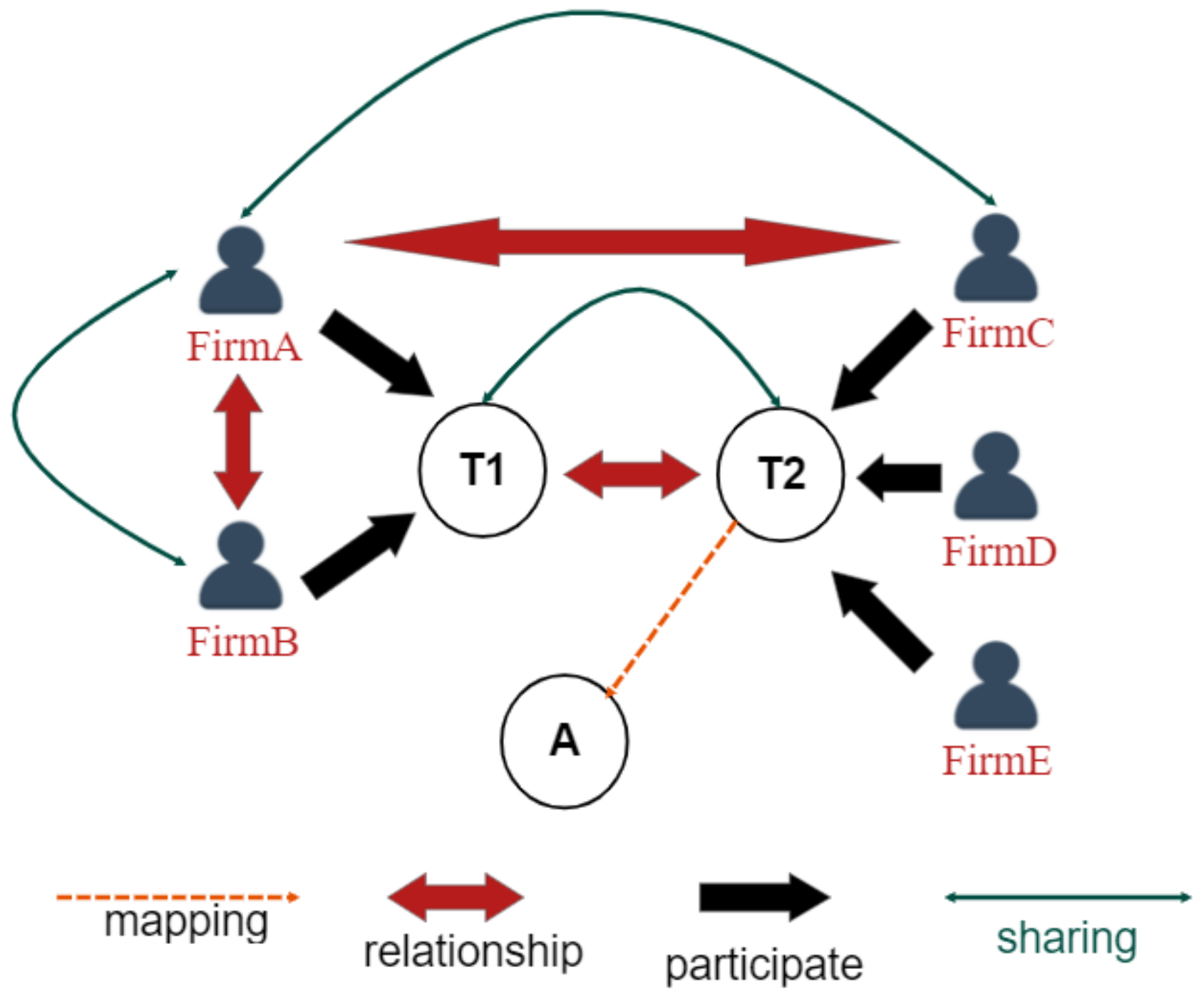
3.2. Hyperledger-IIOT System Structure
3.2.1. User
3.2.2. Blockchain
3.2.3. Smart Gateway
3.2.4. Industrial IoT Devices
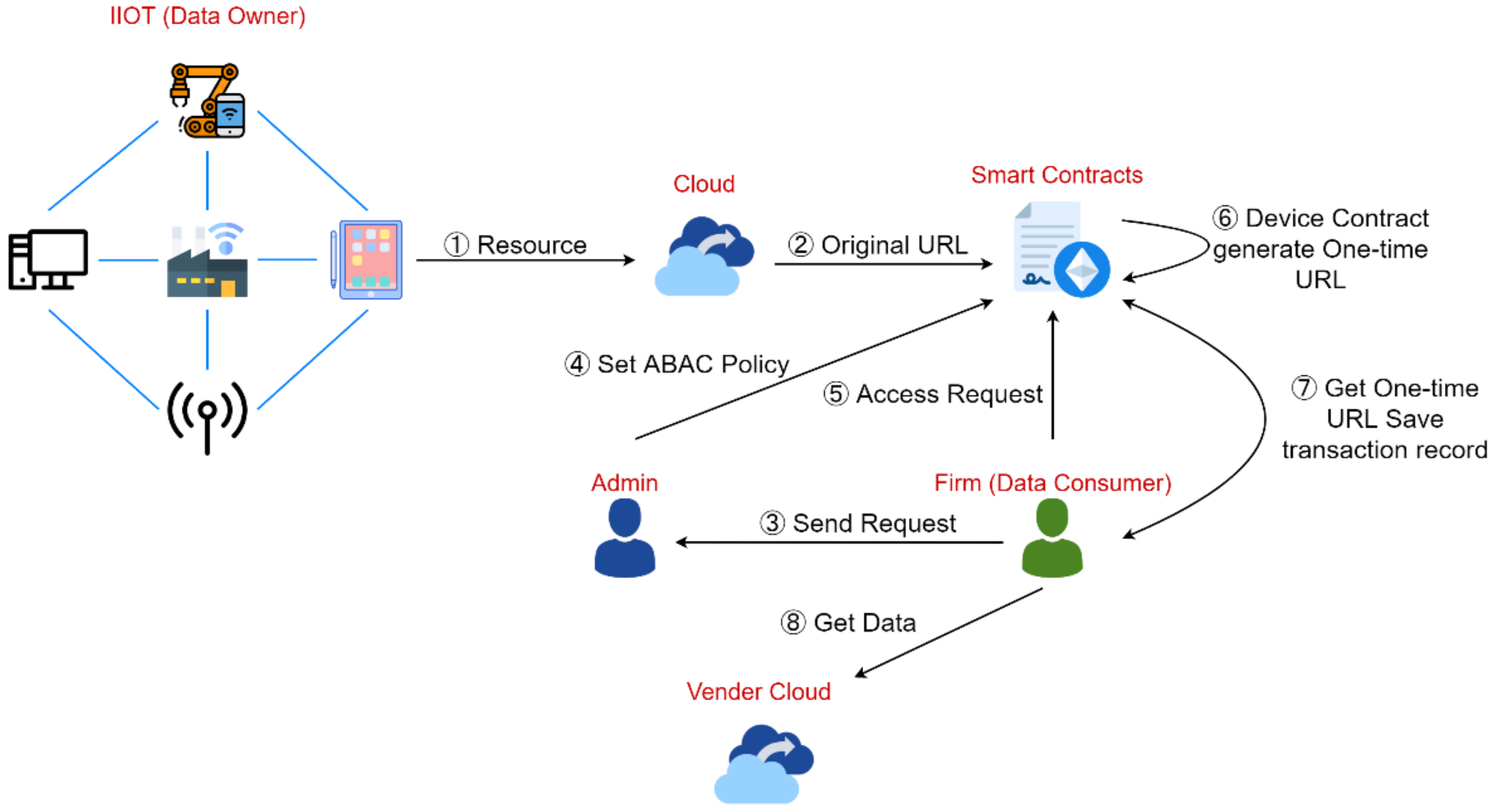
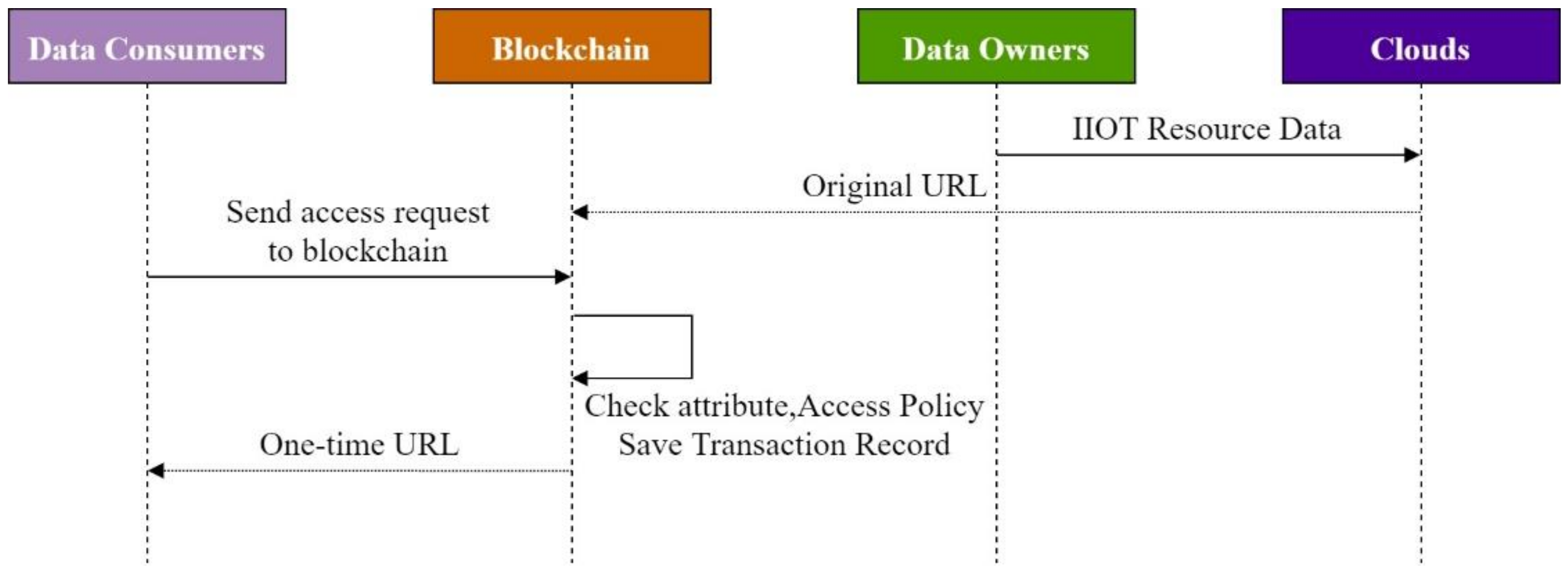
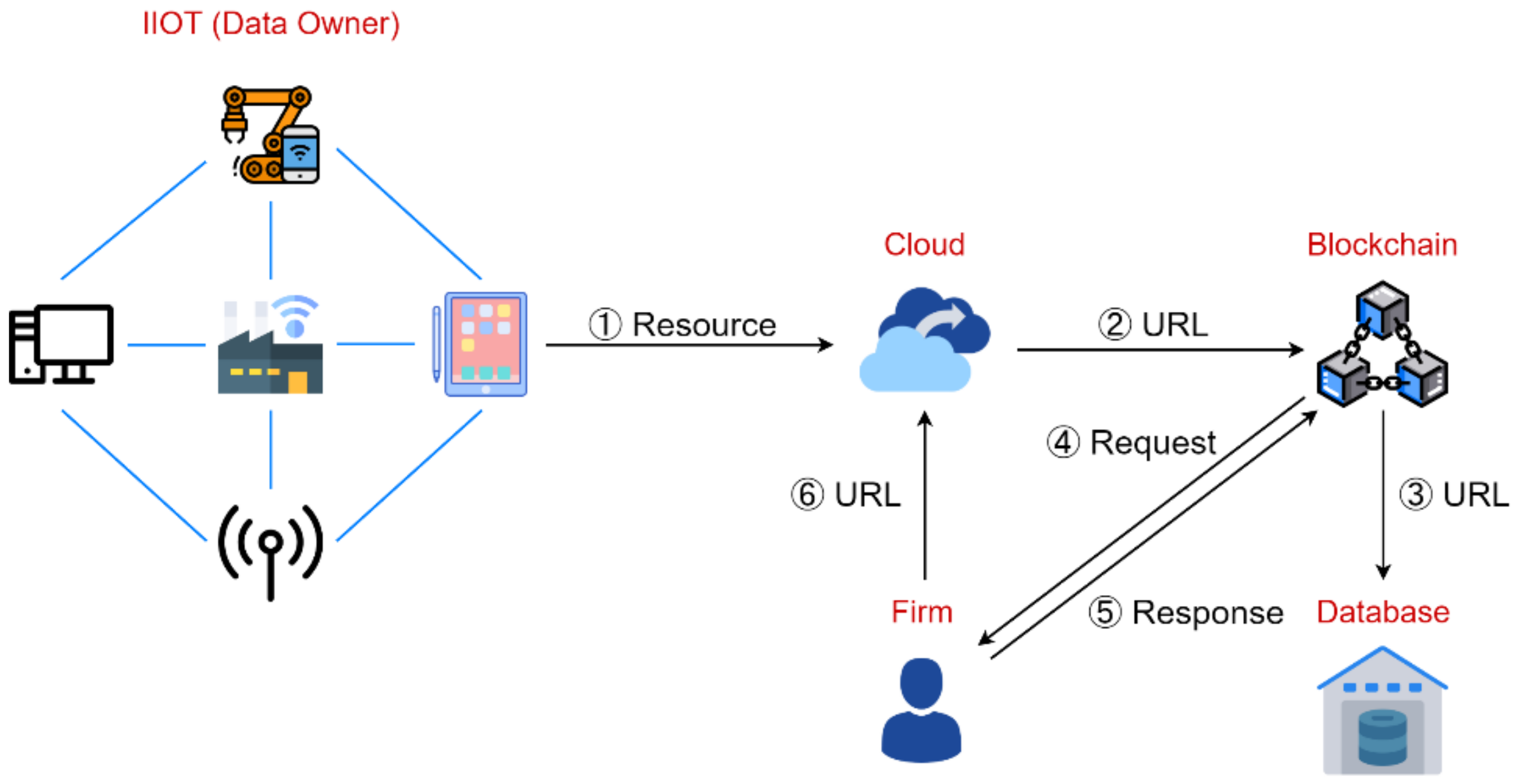
3.3. Hyperledger-IIOT System Flow
3.3.1. Industrial IoT Devices
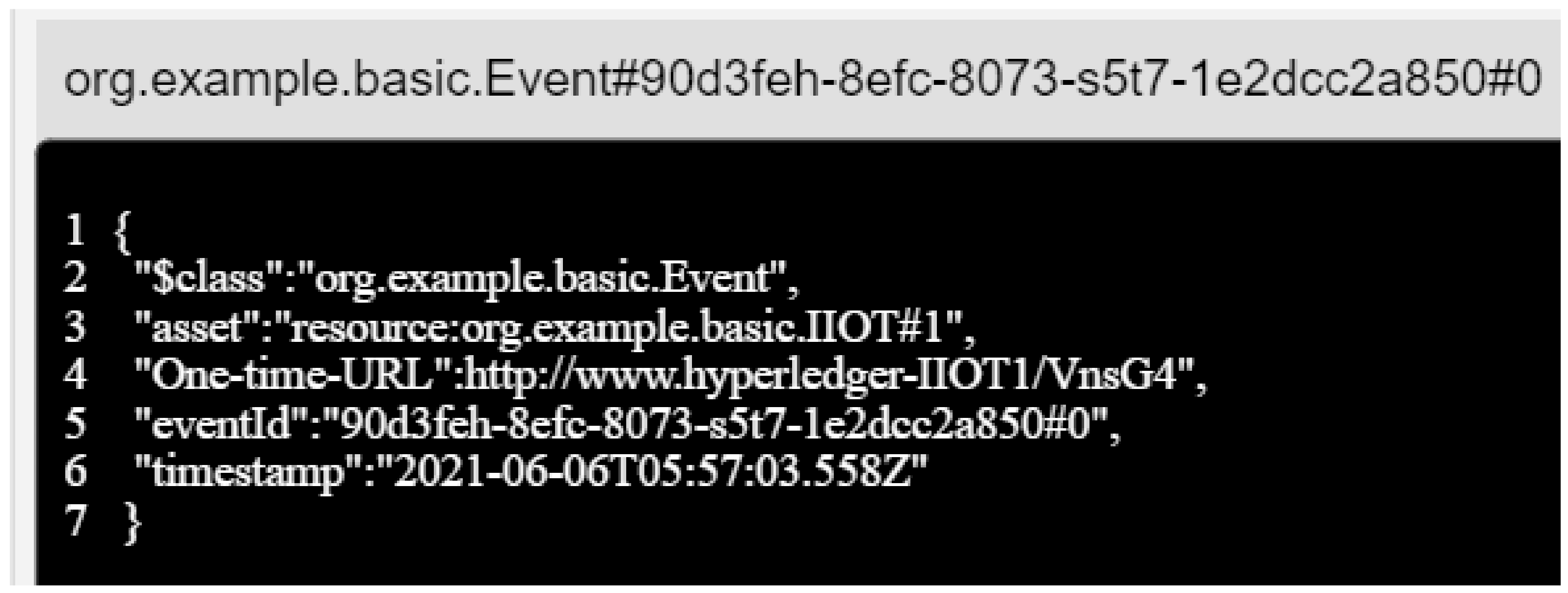
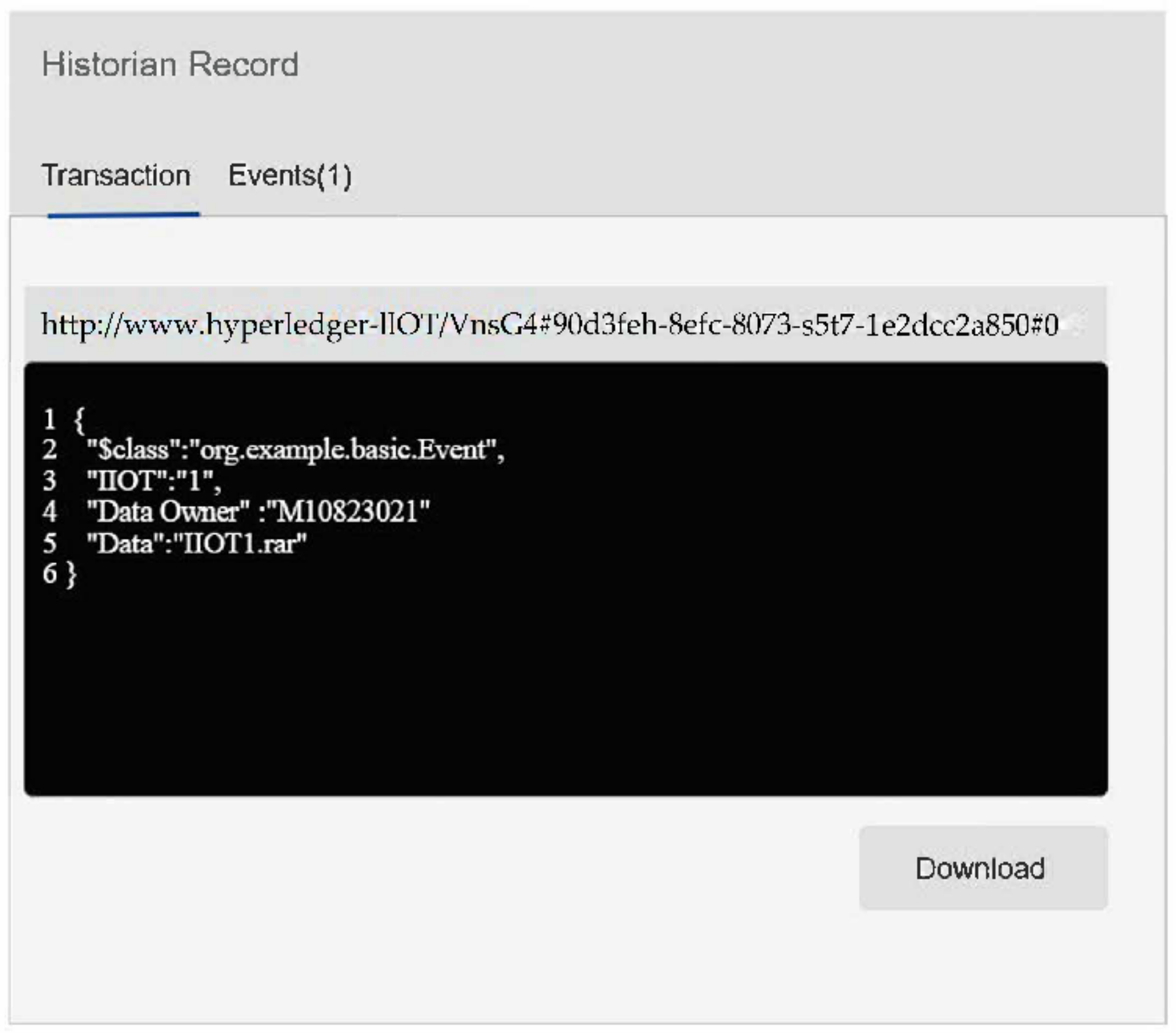
3.3.2. One-Time URL
4. Results
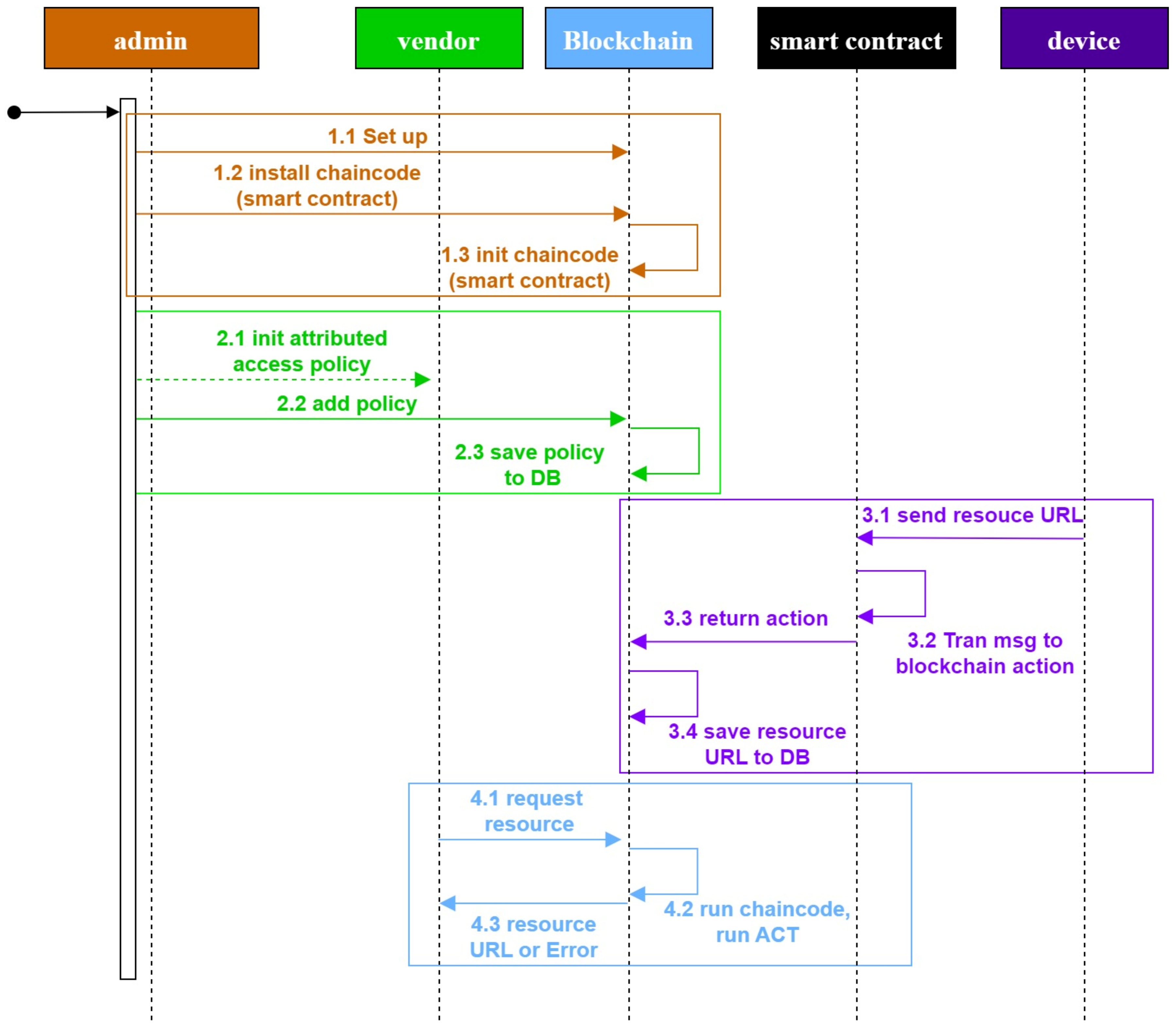
4.1. Hyperledger-IIoT Architecture
4.2. Hyperledger-IIoT Implementation Process
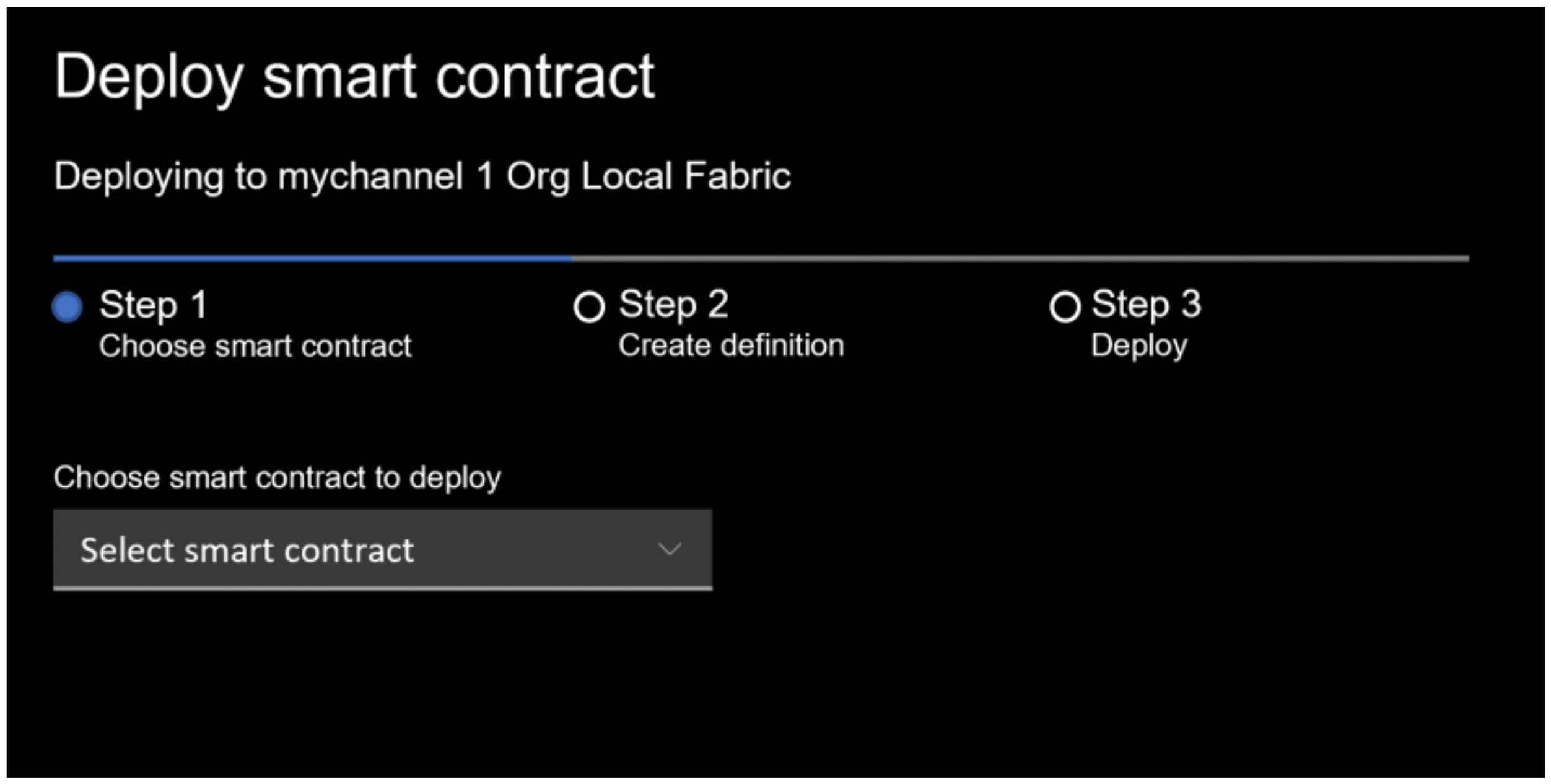
4.2.1. Hyperledger-IIoT Management Rank Implement
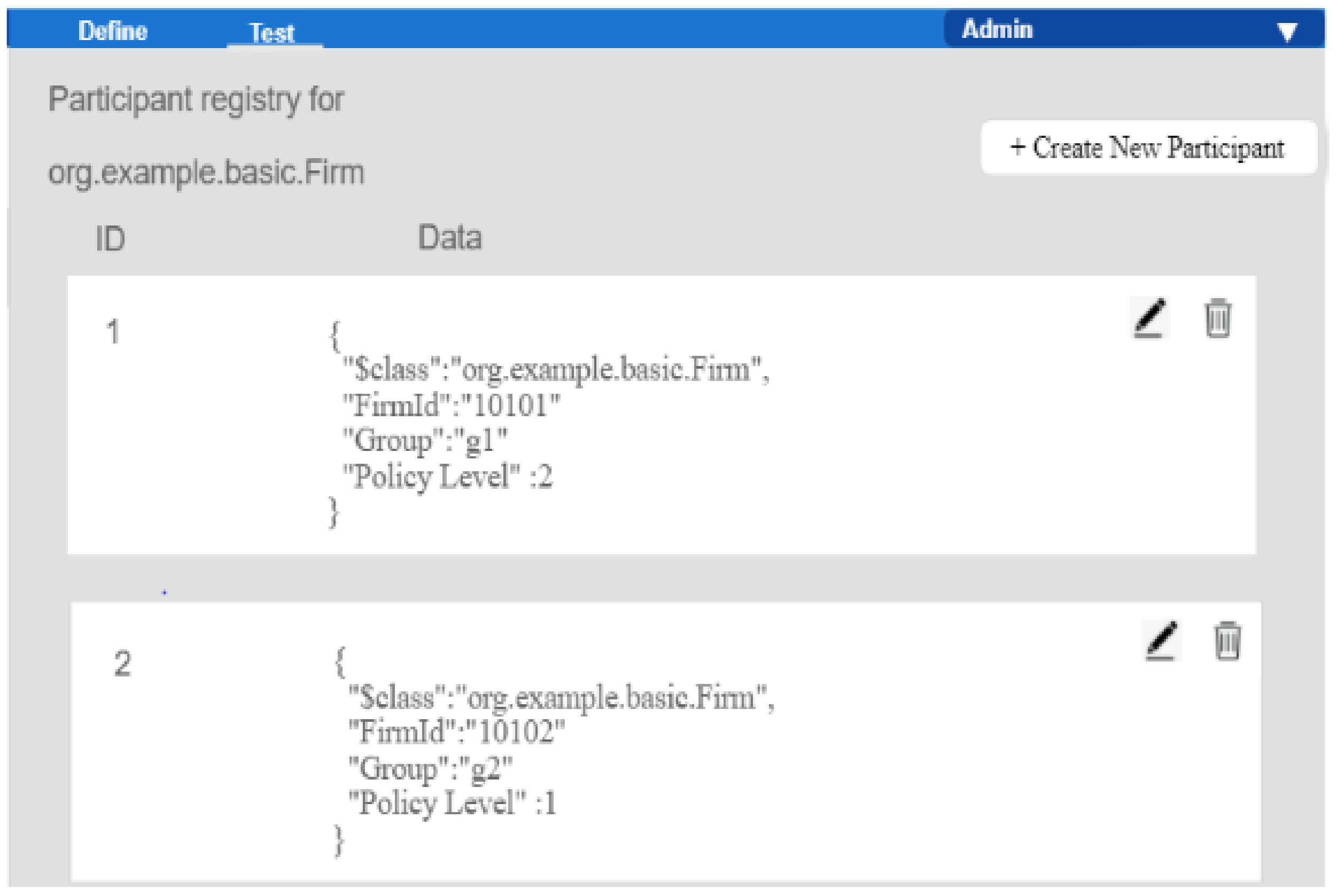
4.2.2. Hyperledger-IIoT Data Consumer Rank Implement
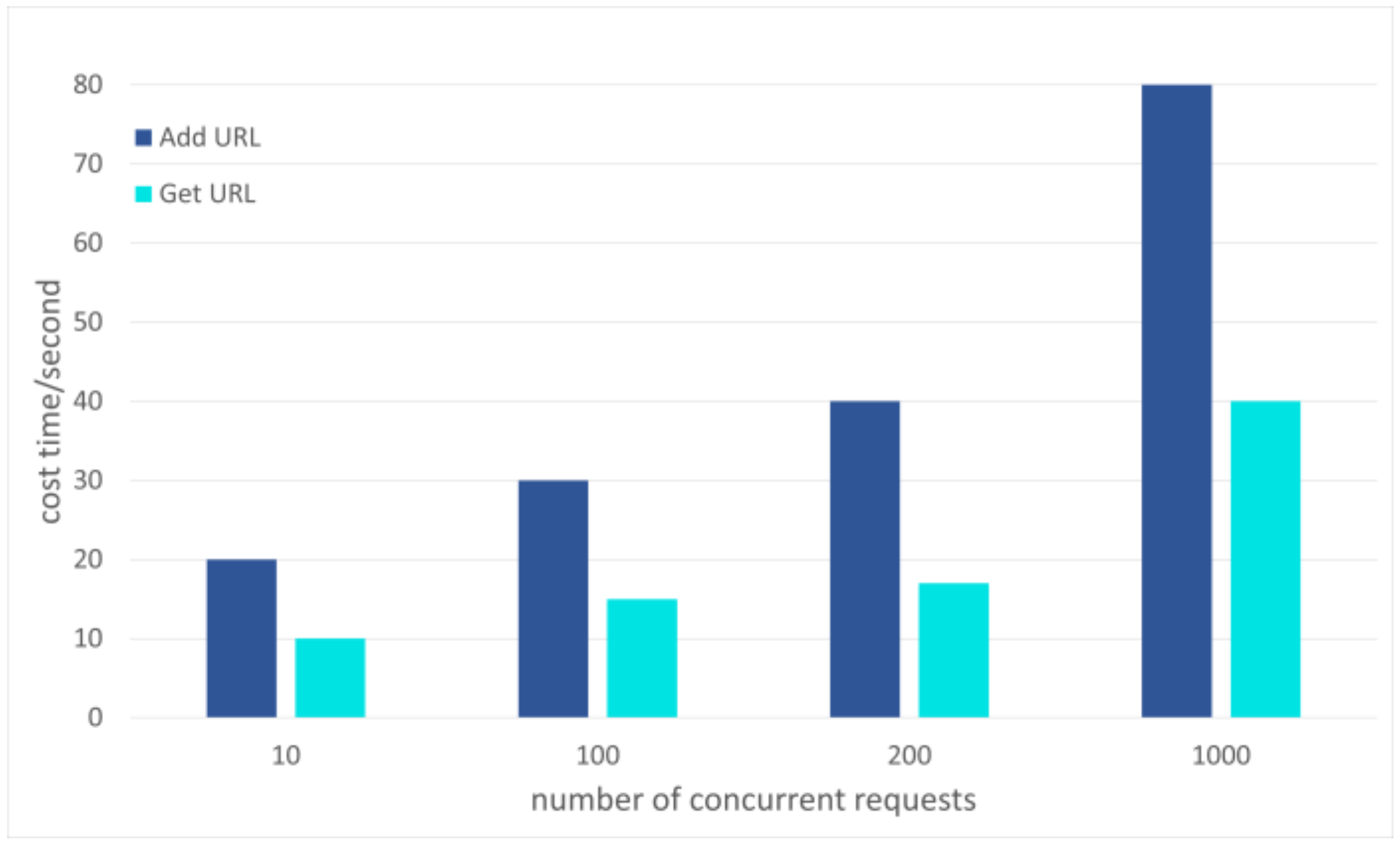
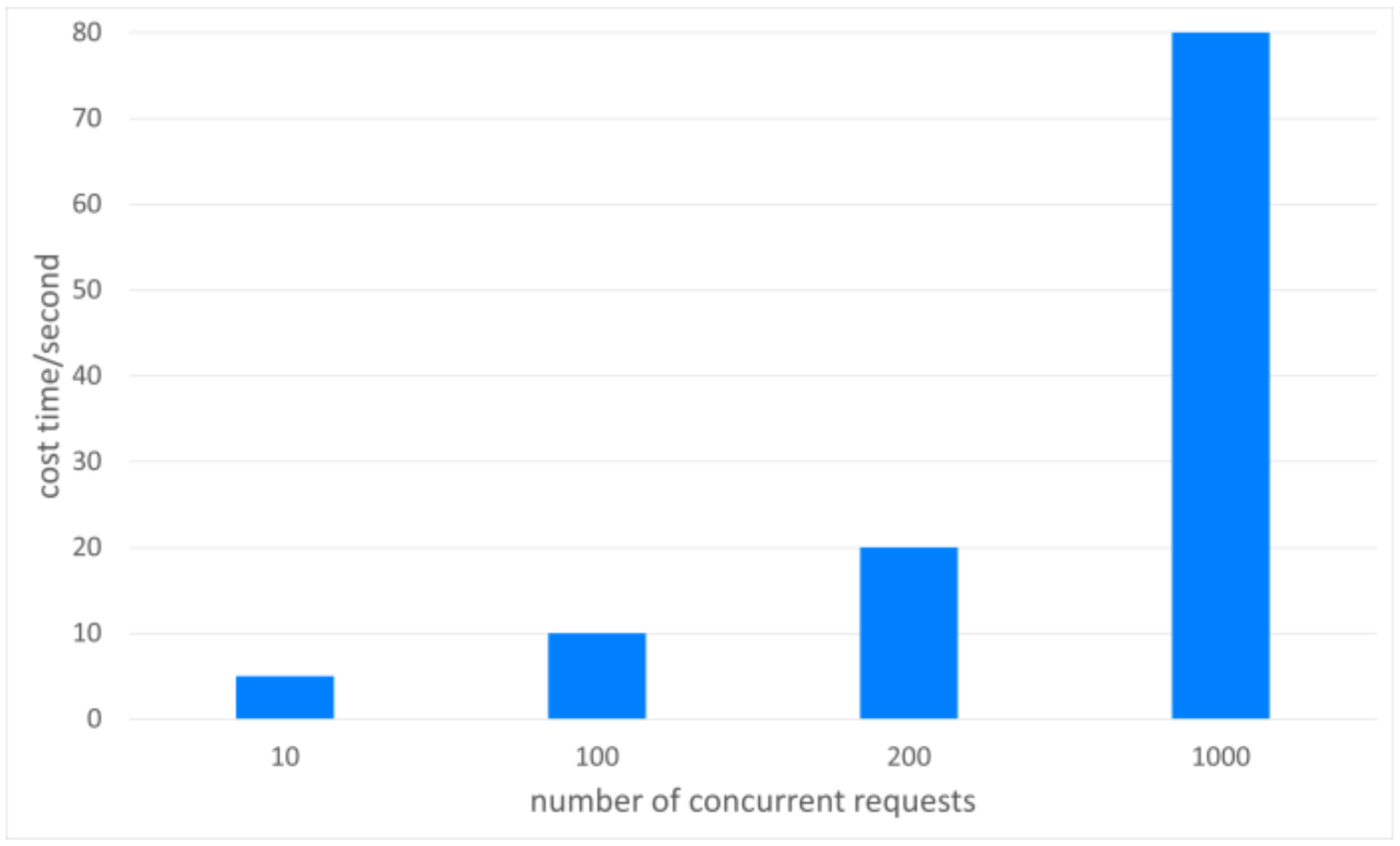
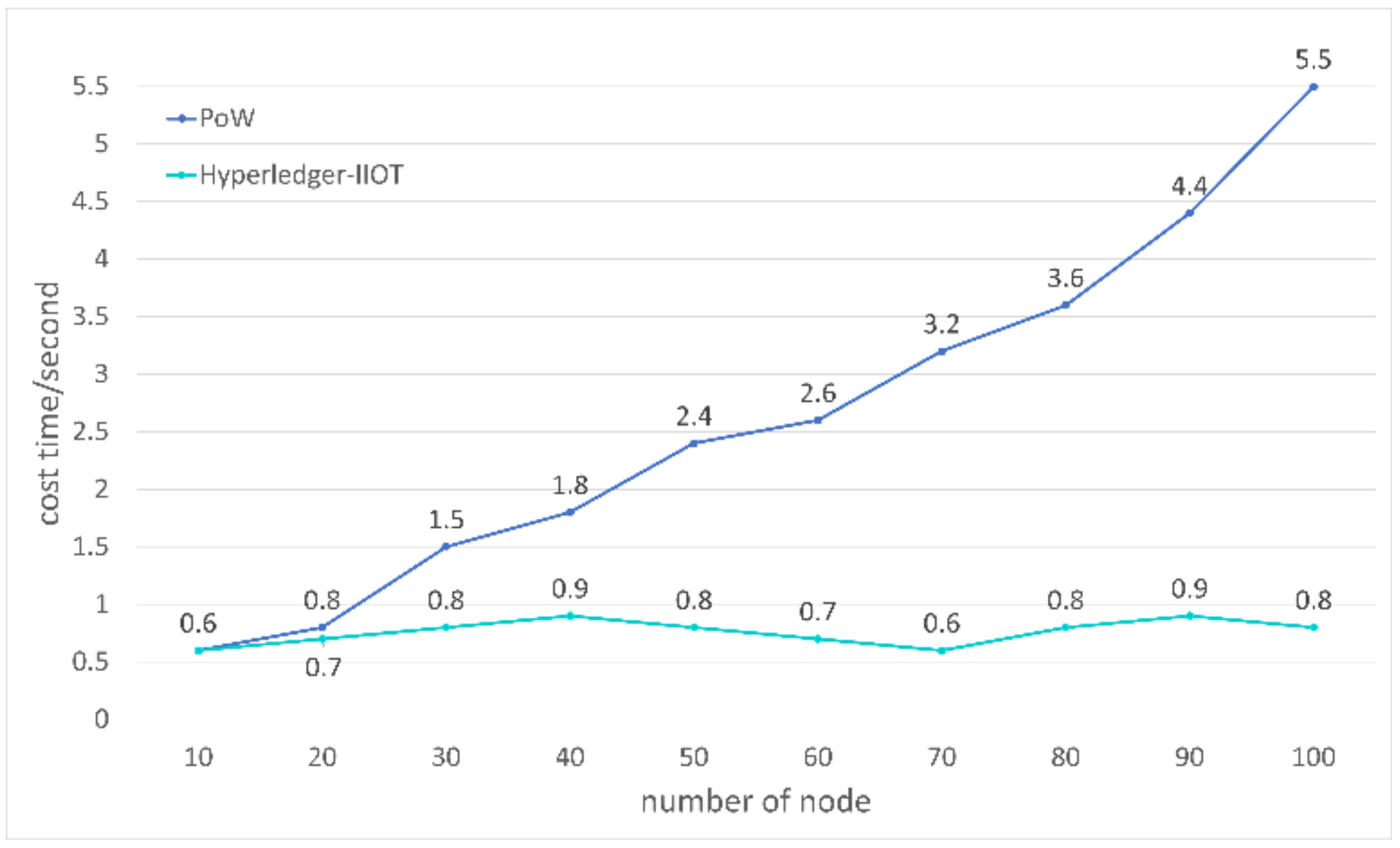
5. Evaluation and Discussion
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- AlAbdullatif, A.; AlAjaji, K.; Al-Serhani, N.S.; Zagrouba, R.; AlDossary, M. Improving an identity authentication management protocol in IIoT. In Proceedings of the 2019 2nd International Conference on Computer Applications & Information Security (ICCAIS), Riyadh, Saudi Arabia, 1–3 May 2019; pp. 1–6. [Google Scholar]
- Djenna, A.; Harous, S.; Saidouni, D. Internet of Things Meet Internet of Threats: New Concern Cyber Security Issues of Critical Cyber Infrastructure. Appl. Sci. 2021, 11, 4580. [Google Scholar] [CrossRef]
- Kaur, S.; Chaturvedi, S.; Sharma, A.; Kar, J. A Research Survey on Applications of Consensus Protocols in Blockchain. Secur. Commun. Netw. 2021, 2021, 6693731. [Google Scholar] [CrossRef]
- Gourisetti, S.N.G.; Cali, Ü.; Choo, K.-K.R.; Escobar, E.; Gorog, C.; Lee, A.; Lima, C.; Mylrea, M.; Pasetti, M.; Rahimi, F.; et al. Standardization of the Distributed Ledger Technology cybersecurity stack for power and energy applications. Sustain. Energy Grids Netw. 2021, 28, 100553. [Google Scholar] [CrossRef]
- Zhang, Y.; Kasahara, S.; Shen, Y.; Jiang, X.; Wan, J. Smart Contract-Based Access Control for the Internet of Things. IEEE Internet Things J. 2019, 6, 1594–1605. [Google Scholar] [CrossRef] [Green Version]
- Liang, W.; Tang, M.; Long, J.; Peng, X.; Xu, J.; Li, K.-C. A Secure FaBric Blockchain-Based Data Transmission Technique for Industrial Internet-of-Things. IEEE Trans. Ind. Inform. 2019, 15, 3582–3592. [Google Scholar] [CrossRef]
- Puri, V.; Priyadarshini, I.; Kumar, R.; Kim, L.C. Blockchain meets IIoT: An architecture for privacy preservation and security in IIoT. In Proceedings of the 2020 IEEE International Conference on Computer Science, Engineering and Applications (ICCSEA), Gunupur, India, 13–14 March 2020; pp. 1–7. [Google Scholar]
- Wang, S.; Hou, Y.; Gao, F.; Ji, X. A novel IoT access architecture for vehicle monitoring system. In Proceedings of the 2016 IEEE 3rd World Forum on Internet of Things (WF-IoT), Reston, VA, USA, 12–14 December 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 639–642. [Google Scholar]
- Yeasmin, S.; Baig, A. Permissioned Blockchain-based Security for IIoT. In Proceedings of the 2020 IEEE International IOT, Electronics and Mechatronics Conference (IEMTRONICS), Vancouver, BC, Canada, 9–12 September 2020; pp. 1–7. [Google Scholar]
- Li, D.; Yao, Y.; Shao, Z.; Wang, L. From digital Earth to smart Earth. Chin. Sci. Bull. 2014, 59, 722–733. [Google Scholar] [CrossRef]
- Zhong, R.Y.; Xu, X.; Klotz, E.; Newman, S.T. Intelligent Manufacturing in the Context of Industry 4.0: A Review. Engineering 2017, 3, 616–630. [Google Scholar] [CrossRef]
- Green, J. The Internet of Things Reference Model. In Proceedings of the Internet of Things World Forum (IoTWF) White Paper, Seoul, Korea, 6–8 March 2014. [Google Scholar]
- Abuhashim, A.; Tan, C.C. Smart Contract Designs on Blockchain Applications. In Proceedings of the 2020 IEEE Symposium on Computers and Communications (ISCC), Rennes, France, 7–10 July 2020; pp. 1–4. [Google Scholar]
- Hylock, R.H.; Zeng, X. A Blockchain Framework for Patient-Centered Health Records and Exchange (HealthChain): Evaluation and Proof-of-Concept Study. J. Med. Internet Res. 2019, 21, e13592. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Liu, H.; Han, D.; Li, D. Fabric-iot: A Blockchain-Based Access Control System in IoT. IEEE Access 2020, 8, 18207–18218. [Google Scholar] [CrossRef]
- Androulaki, E.; Barger, A.; Bortnikov, V.; Cachin, C.; Christidis, K.; De Caro, A.; Yellick, J. Hyperledger fabric: A distributed operating system for permissioned blockchains. In Proceedings of the Thirteenth EuroSys Conference, Porto, Portuga, 23–26 April 2018; pp. 1–15. [Google Scholar]
- Nasir, Q.; Qasse, I.A.; Abu Talib, M.; Nassif, A.B. Performance Analysis of Hyperledger Fabric Platforms. Secur. Commun. Netw. 2018, 2018, 3976093. [Google Scholar] [CrossRef] [Green Version]
- Yu, X.; Guo, H. A Survey on IIoT Security. In Proceedings of the 2019 IEEE VTS Asia Pacific Wireless Communications Symposium (APWCS), Singapore, 28–30 August 2019; pp. 1–5. [Google Scholar]
- Mugarza, I.; Flores, J.L.; Montero, J.L. Security Issues and Software Updates Management in the Industrial Internet of Things (IIoT) Era. Sensors 2020, 20, 7160. [Google Scholar] [CrossRef] [PubMed]
- Wells, L.J.; Camelio, J.A.; Williams, C.B.; White, J. Cyber-physical security challenges in manufacturing systems. Manuf. Lett. 2014, 2, 74–77. [Google Scholar] [CrossRef]
- El Sibai, R.; Gemayel, N.; Bou Abdo, J.; Demerjian, J. A survey on access control mechanisms for cloud computing. Trans. Emerg. Telecommun. Technol. 2020, 31, e3720. [Google Scholar] [CrossRef]
- Lu, K. A Study on the Success Factors of Taiwanese Enterprises’ Strategic Alliance. In Proceedings of the Industrial Management International Academic Research Association, Kaohsiung, Taiwan, 27 May 2001; pp. 14–31. (In Chinese). [Google Scholar]
- Sun, S.; Du, R.; Chen, S.; Li, W. Blockchain-Based IoT Access Control System: Towards Security, Lightweight, and Cross-Domain. IEEE Access 2021, 9, 36868–36878. [Google Scholar] [CrossRef]






| OS | Ubuntu 18.04.5 |
|---|---|
| Language | Golang |
| Docker | v19.03.13 |
| Docker-compose | v1.25.5 |
| Hyperledger fabric | v2.1 |
| Hyprtledger-IIoT | ||
|---|---|---|
| Node | Consensus Speed (Second) | PoW |
| 10 | 0.6 | 0.6 |
| 50 | 0.8 | 2.4 |
| 80 | 0.8 | 3.6 |
| 100 | 0.8 | 5.5 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shih, D.-H.; Wu, T.-W.; Shih, M.-H.; Chen, G.-W.; Yen, D.C. Hyperledger Fabric Access Control for Industrial Internet of Things. Appl. Sci. 2022, 12, 3125. https://doi.org/10.3390/app12063125
Shih D-H, Wu T-W, Shih M-H, Chen G-W, Yen DC. Hyperledger Fabric Access Control for Industrial Internet of Things. Applied Sciences. 2022; 12(6):3125. https://doi.org/10.3390/app12063125
Chicago/Turabian StyleShih, Dong-Her, Ting-Wei Wu, Ming-Hung Shih, Guan-Wei Chen, and David C. Yen. 2022. "Hyperledger Fabric Access Control for Industrial Internet of Things" Applied Sciences 12, no. 6: 3125. https://doi.org/10.3390/app12063125
APA StyleShih, D.-H., Wu, T.-W., Shih, M.-H., Chen, G.-W., & Yen, D. C. (2022). Hyperledger Fabric Access Control for Industrial Internet of Things. Applied Sciences, 12(6), 3125. https://doi.org/10.3390/app12063125







