Data Security-Based Routing in MANETs Using Key Management Mechanism
Abstract
1. Introduction
1.1. Motivation
1.2. Contributions
- An efficient and energy-aware secure key management system is proposed, using two specialized nodes labeled Calculator key (CK) and Distribution key (DK);
- These two nodes, i.e., CK and DK, are responsible for the generation, verification, and distribution of secret keys;
- The energy and trust factors of MANET nodes are utilized for the selection of these nodes, i.e., CK and DK;
- Extensive experiments are performed for the verification and validation of the proposed secure key management system.
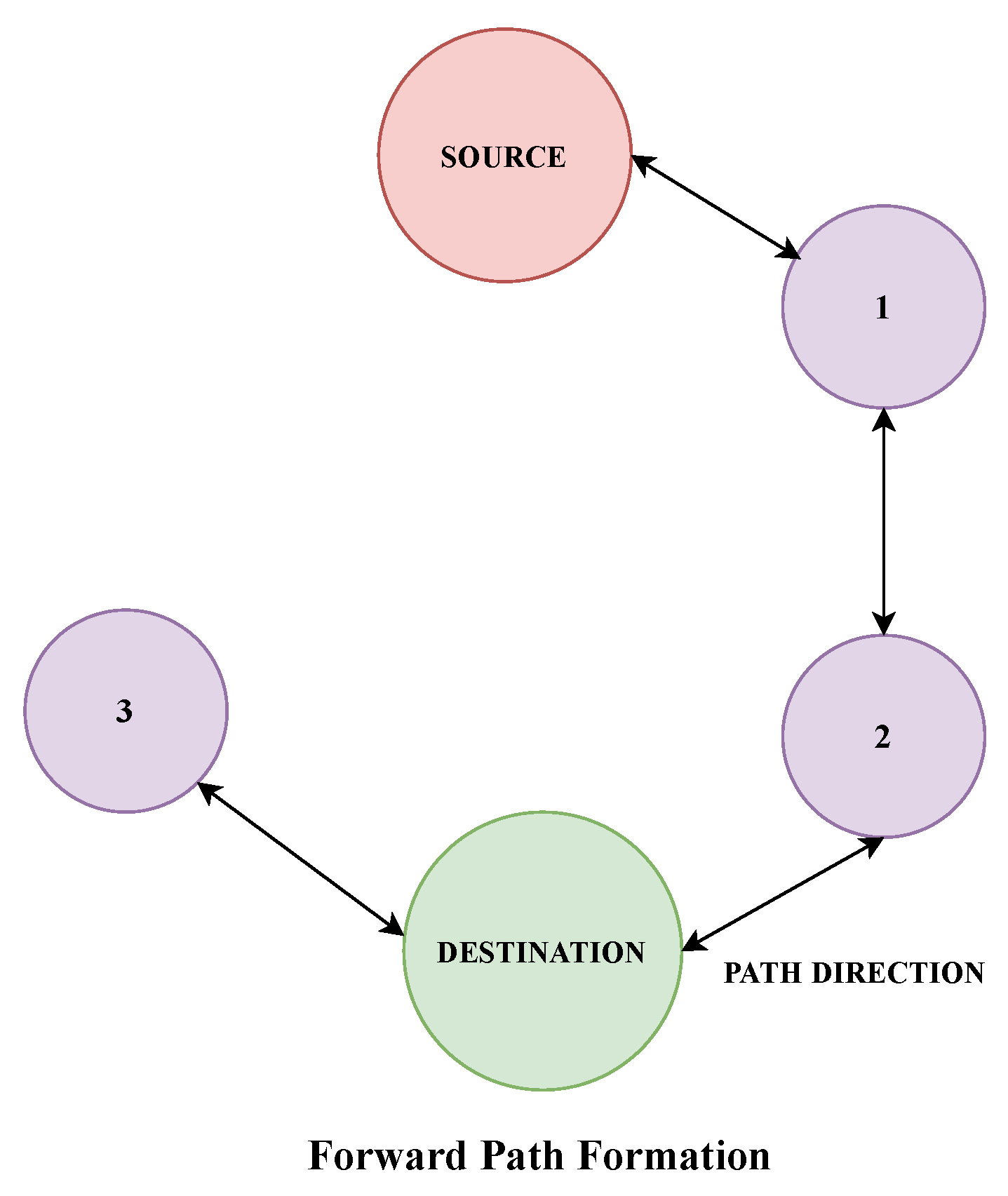
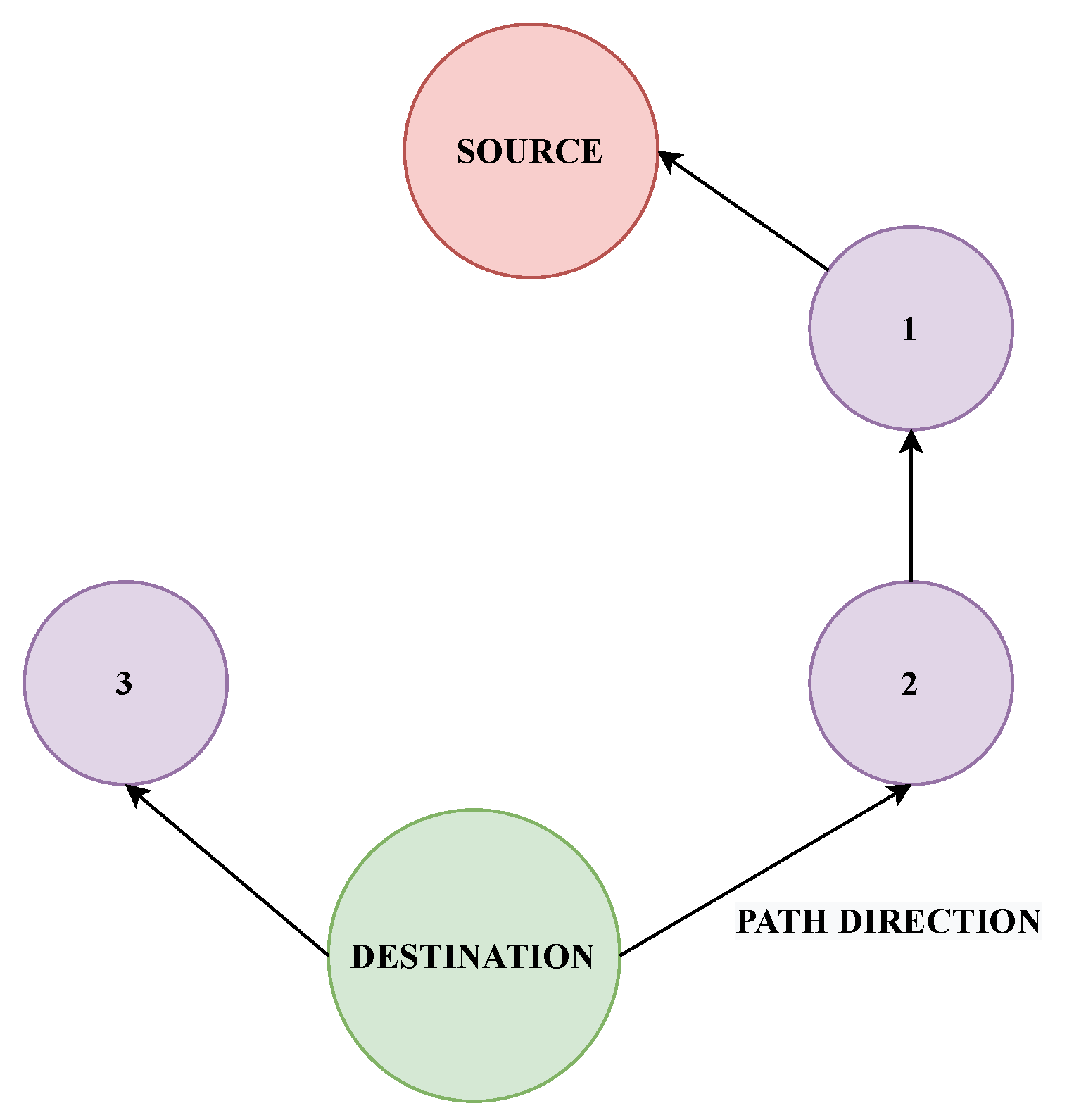
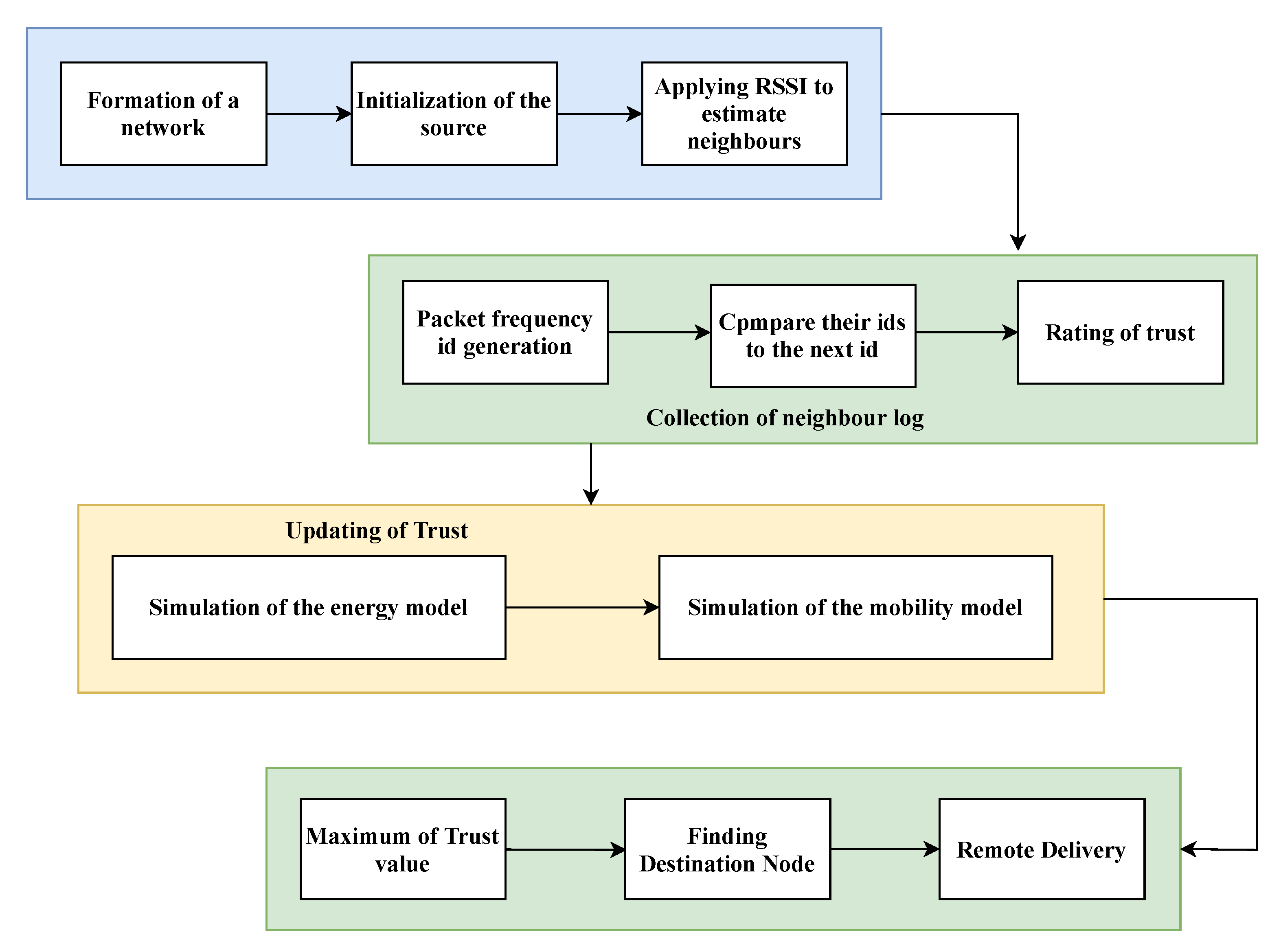
2. Proposed Model
2.1. Ad Hoc On-Demand Distance Vector
2.2. Trust Management
2.3. Mobility-Based Model Function
2.4. Energy Function Computation
2.5. Cryptographic Methods
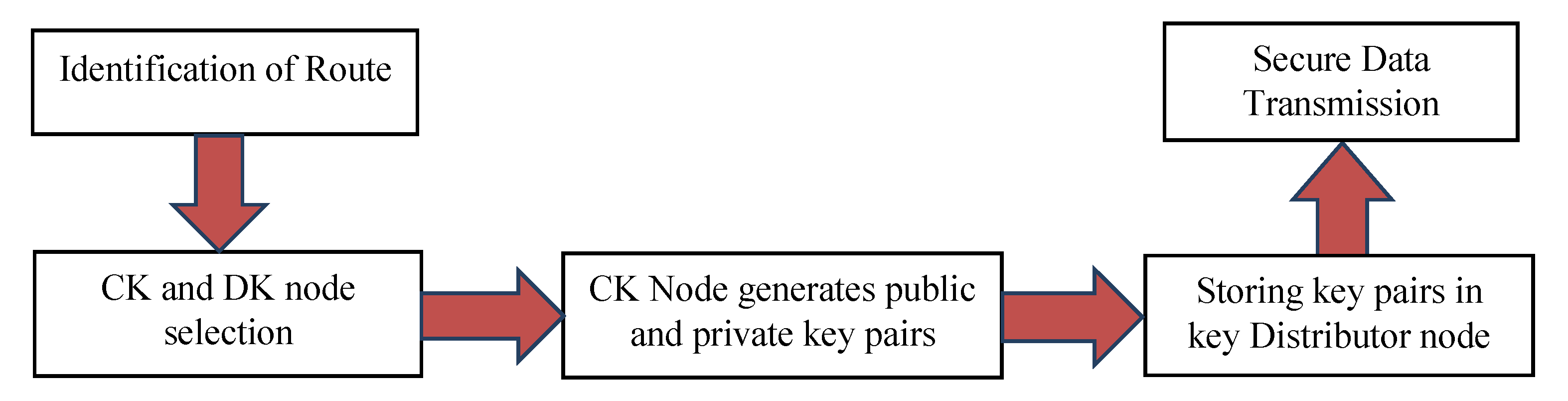
3. Secure Data Communication Framework
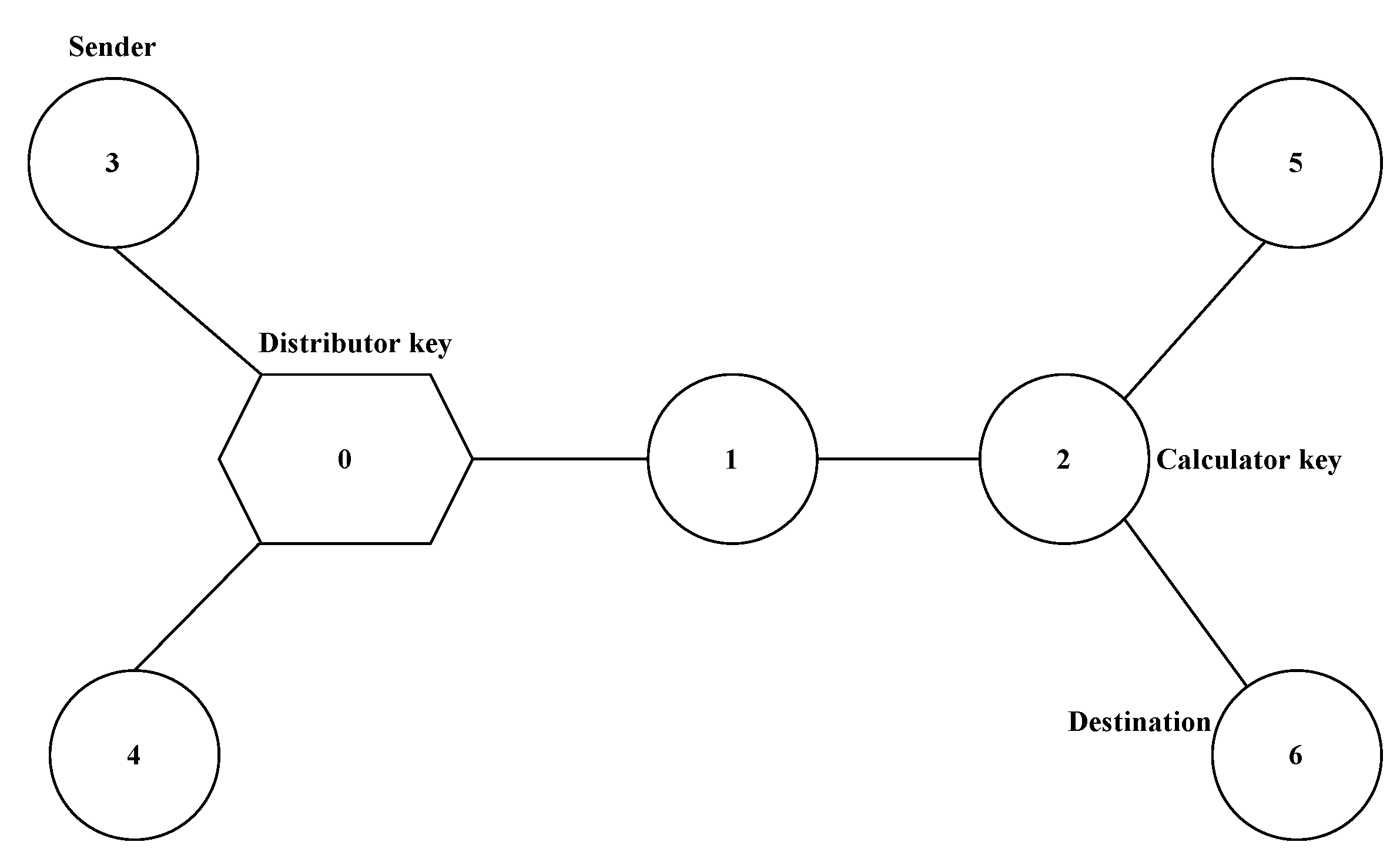
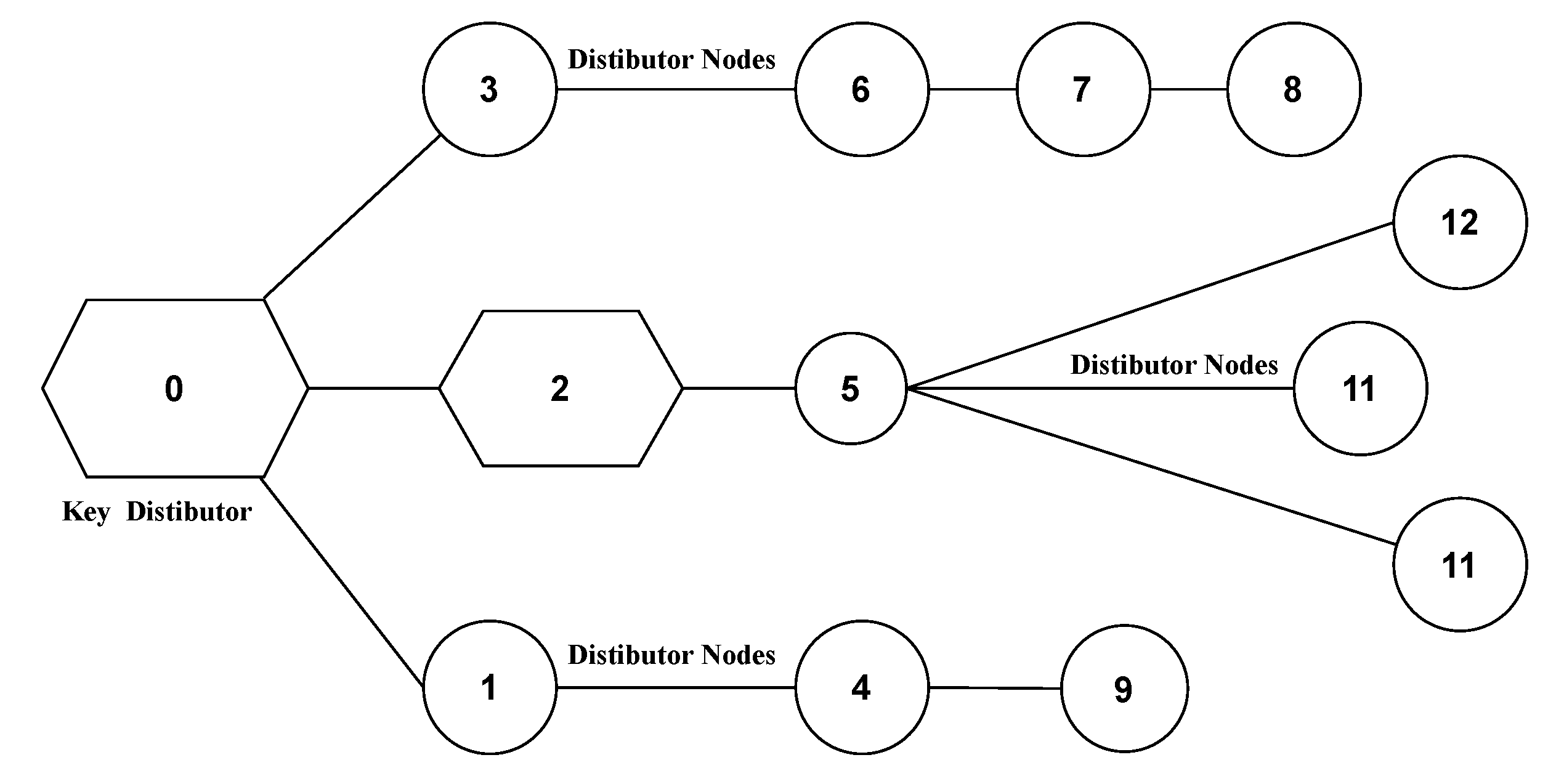
3.1. Selection of the Calculator Key (CK) and Distribution Key (DK)
Generation of the Private Key
3.2. Secure Data-Communication Framework
4. Simulation Environment and Performance Metrics
4.1. Simulation Environment
4.2. Malicious Nodes
| Adding malicious nodes 0 “[node-(15) set ragent-] malicious” |
| Node 15 is set as malicious 0 “[node-(25) set ragent-] malicious” |
| Node 25 is set as malicious 0 “[node-(35) set ragent-] malicious” |
| Node 35 is set as malicious |
4.3. Performance Metrics
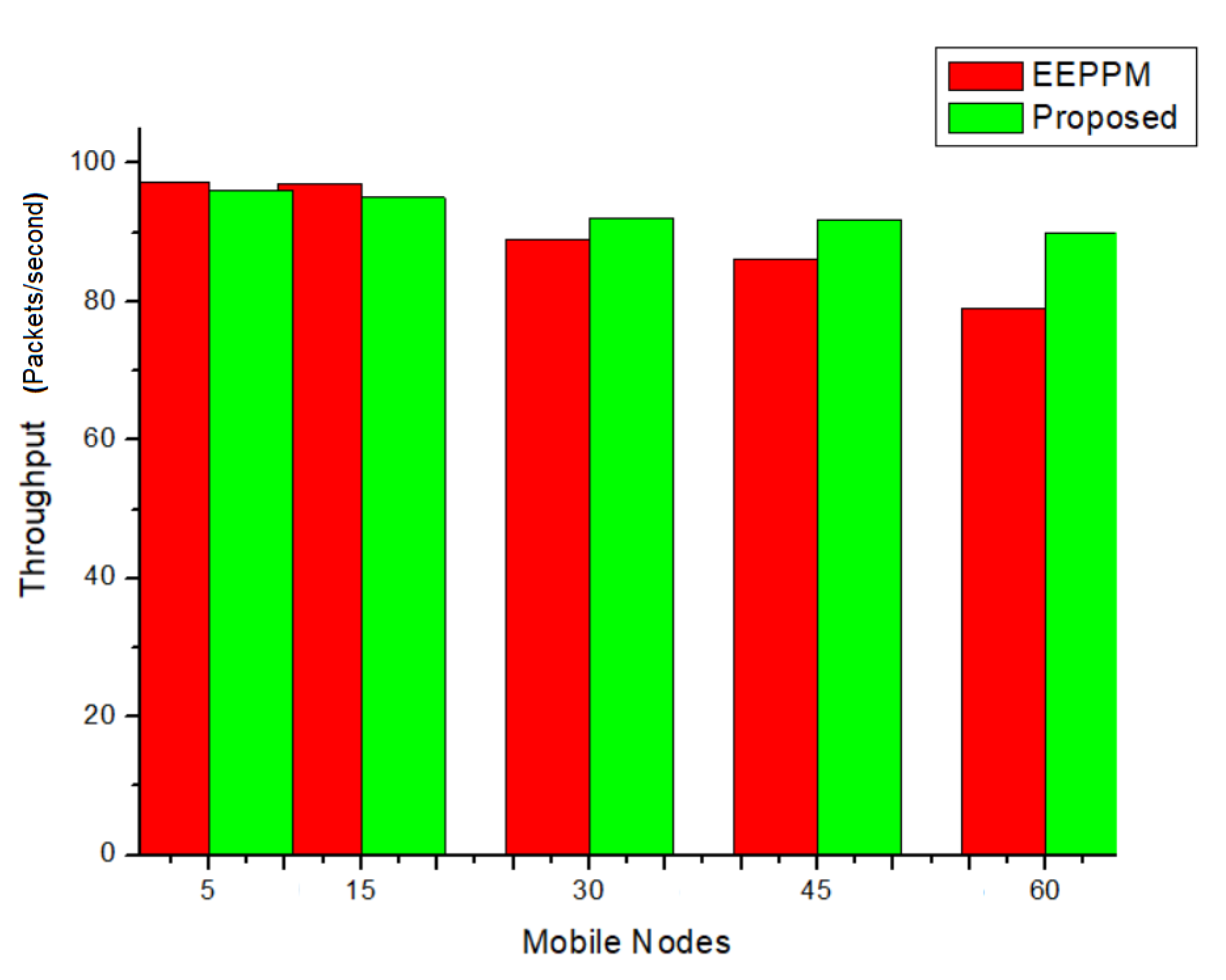
4.4. Throughput
4.5. Routing Overhead
4.6. Average End-to-End Delay
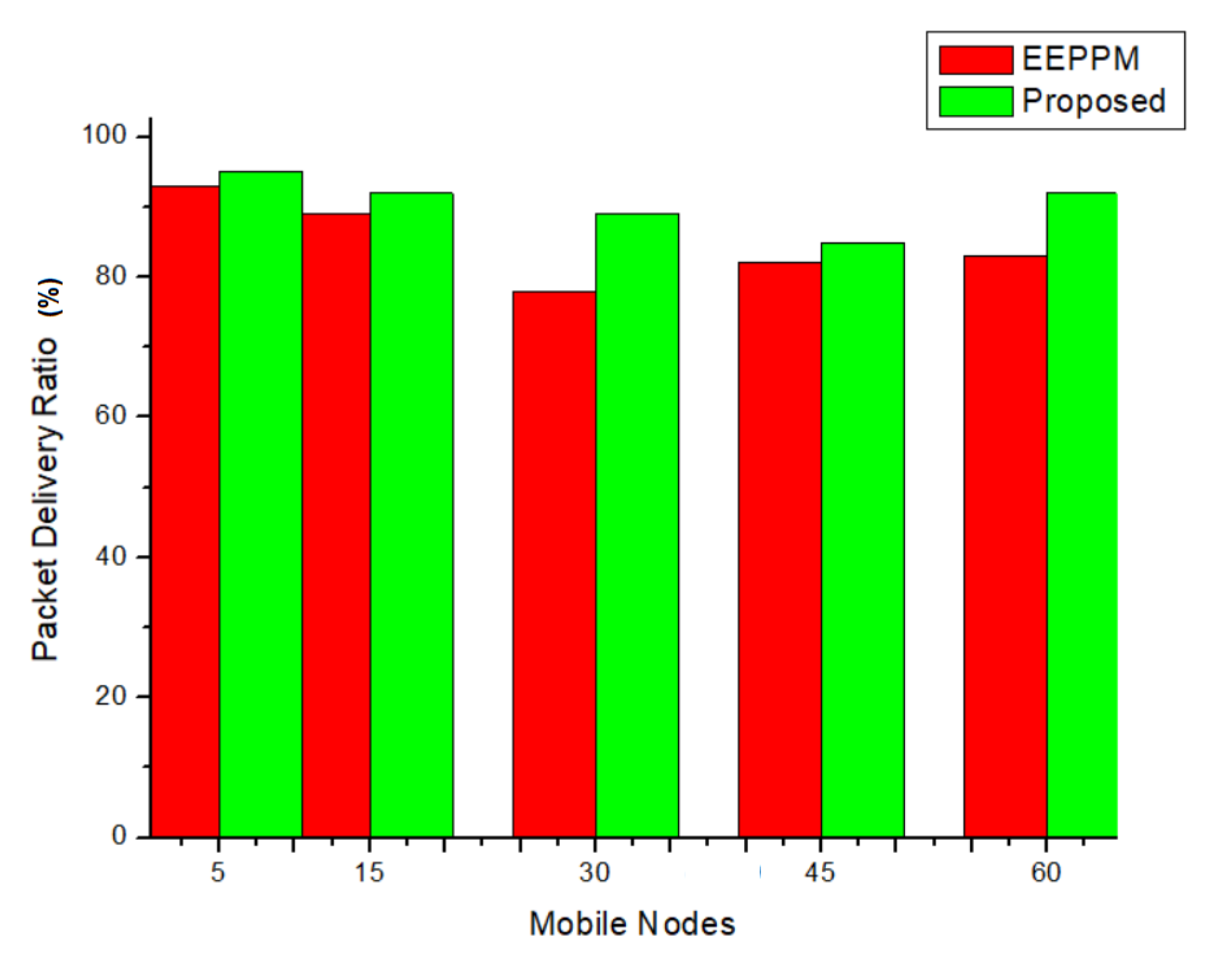
4.7. Packet-Delivery Ratio
5. Experimental Results and Comparative Analysis
5.1. Performance Analysis
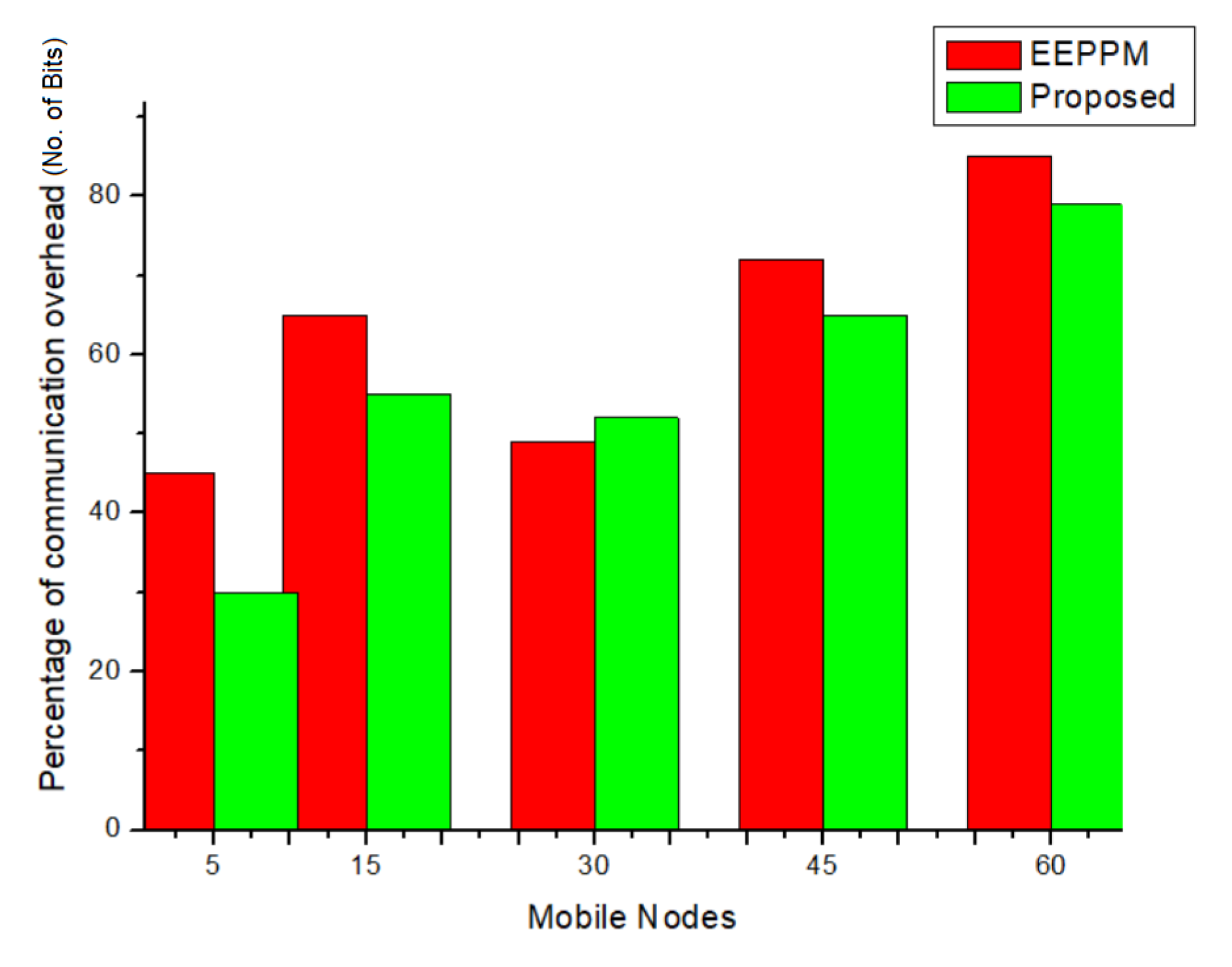
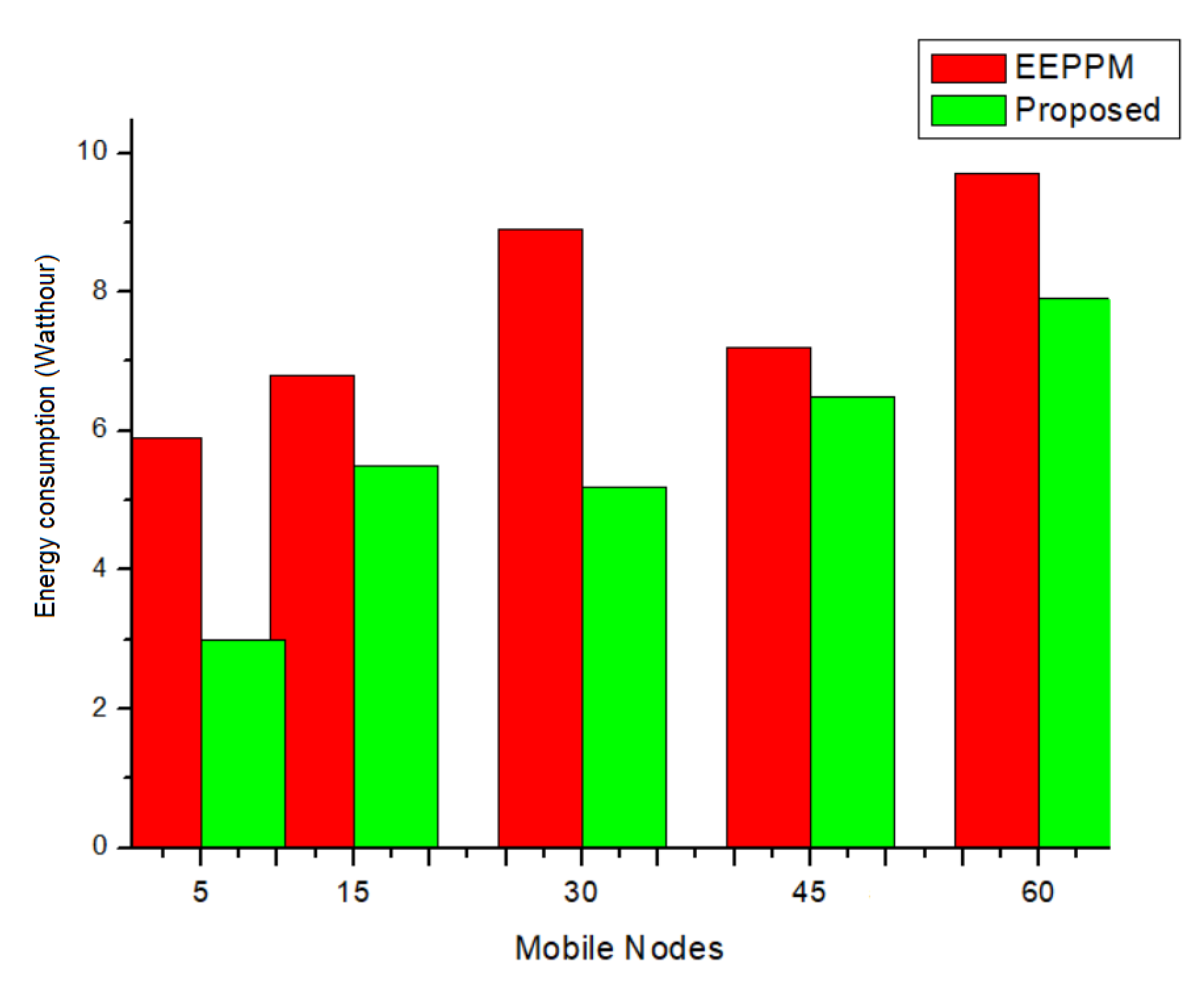
5.2. Comparative Analysis
5.3. Future Scope
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Ben Othman, J.; Mokdad, L. Enhancing data security in ad hoc networks based on multipath routing. J. Parallel Distrib. Comput. 2010, 70, 309–316. [Google Scholar] [CrossRef]
- Kumar, K.V.; Jayasankar, T.; Eswaramoorthy, V.; Nivedhitha, V. SDARP: Security based Data Aware Routing Protocol for ad hoc sensor networks. Int. J. Intell. Netw. 2020, 1, 36–42. [Google Scholar] [CrossRef]
- El-Hadidi, M.G.; Azer, M.A. Traffic Analysis for Real Time Applications and its Effect on QoS in MANETs, Intelligent, and Ubiquitous Computing Conference (MIUCC). In Proceedings of the 2021 International Mobile, Cairo, Egypt, 26–27 May 2021; pp. 155–160. [Google Scholar] [CrossRef]
- Wu, W.C.; Liaw, H.T. A Study on High Secure and Efficient MANET Routing Scheme. J. Sens. 2015, 2015, e365863. [Google Scholar] [CrossRef]
- Devi, V.S.; Hegde, N.P. Multipath Security Aware Routing Protocol for MANET Based on Trust Enhanced Cluster Mechanism for Lossless Multimedia Data Transfer. Wirel. Pers. Commun. Int. J. 2018, 100, 923–940. [Google Scholar] [CrossRef]
- Gomathy, V.; Padhy, N.; Samanta, D.; Sivaram, M.; Jain, V.; Amiri, I.S. Malicious node detection using heterogeneous cluster based secure routing protocol (HCBS) in wireless adhoc sensor networks. J. Ambient Intell. Humaniz. Comput. 2020, 11, 4995–5001. [Google Scholar] [CrossRef]
- Kousar, R.; Alhaisoni, M.; Akhtar, S.A.; Shah, N.; Qamar, A.; Karim, A. A Secure Data Dissemination in a DHT-Based Routing Paradigm for Wireless Ad Hoc Network. Wirel. Commun. Mob. Comput. 2020, 2020, e2740654. [Google Scholar] [CrossRef]
- Maheswari, M.; Geetha, S.; Kumar, S.S.; Karuppiah, M.; Samanta, D.; Park, Y. PEVRM: Probabilistic Evolution Based Version Recommendation Model for Mobile Applications. IEEE Access 2021, 9, 20819–20827. [Google Scholar] [CrossRef]
- Funderburg, L.E.; Lee, I.Y. A Privacy-Preserving Key Management Scheme with Support for Sybil Attack Detection in VANETs. Sensors 2021, 21, 1063. [Google Scholar] [CrossRef] [PubMed]
- Perkins, C.E.; Bhagwat, P. Highly dynamic destination-sequenced distance-vector routing (DSDV) for mobile computers. ACM SIGCOMM Comput. Commun. Rev. 1994, 24, 234–244. [Google Scholar] [CrossRef]
- Perkins, C. Ad Hoc on Demand Distance Vector (aodv) Routing Ietf. Internet Draft, draft-ietf-manet-aodv-00.txt. 1997. Available online: https://datatracker.ietf.org/doc/rfc3561/ (accessed on 16 January 2021).
- Broch, J.; Johnson, D.B.; Maltz, D.A. The Dynamic Source Routing Protocol for Mobile Ad Hoc Networks. draft-ietfmanet-dsr-03. txt. Work-in-Progress. 1998. Available online: https://www.ietf.org/proceedings/42/I-D/draft-ietf-manet-dsr-00.txt (accessed on 16 January 2021).
- Saxena, N.; Tsudik, G.; Yi, J.H. Efficient Node Admission and Certificateless Secure Communication in Short-Lived MANETs. IEEE Trans. Parallel Distrib. Syst. 2009, 20, 158–170. [Google Scholar] [CrossRef]
- El Defrawy, K.; Tsudik, G. ALARM: Anonymous Location-Aided Routing in Suspicious MANETs. IEEE Trans. Mob. Comput. 2011, 10, 1345–1358. [Google Scholar] [CrossRef]
- Khan, A.; Sun, Q.T.; Mahmood, Z.; Ghafoor, A.U. Energy efficient partial permutation encryption on network coded MANETs. J. Electr. Comput. Eng. 2017, 2017, 4657831. [Google Scholar] [CrossRef]
- Dhurandher, S.K.; Obaidat, M.S.; Verma, K.; Gupta, P.; Dhurandher, P. FACES: Friend-Based Ad Hoc Routing Using Challenges to Establish Security in MANETs Systems. IEEE Syst. J. 2011, 5, 176–188. [Google Scholar] [CrossRef]
- Chen, S.; Wu, M. Anonymous multipath routing protocol based on secret sharing in mobile ad hoc networks. J. Syst. Eng. Electron. 2011, 22, 519–527. [Google Scholar] [CrossRef][Green Version]
- Qin, Y.; Huang, D.; Li, B. STARS: A Statistical Traffic Pattern Discovery System for MANETs. IEEE Trans. Dependable Secur. Comput. 2014, 11, 181–192. [Google Scholar] [CrossRef]
- Saxena, N.; Yi, J.H. Noninteractive Self-Certification for Long-Lived Mobile Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2009, 4, 946–955. [Google Scholar] [CrossRef]
- Hammamouche, A.; Omar, M.; Djebari, N.; Tari, A. Lightweight reputation-based approach against simple and cooperative black-hole attacks for MANET. J. Inf. Secur. Appl. 2018, 43, 12–20. [Google Scholar] [CrossRef]
- Subramaniyan, S.; Johnson, W.; Subramaniyan, K. A distributed framework for detecting selfish nodes in MANET using Record- and Trust-Based Detection (RTBD) technique. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 205. [Google Scholar] [CrossRef]
- Veeraiah, N.; Ibrahim Khalaf, O.; Prasad, C.V.P.R.; Alotaibi, Y.; Alsufyani, A.; Alghamdi, S.A.; Alsufyani, N. Trust Aware Secure Energy Efficient Hybrid Protocol for MANET. IEEE Access 2021, 9, 120996–121005. [Google Scholar] [CrossRef]
- Srilakshmi, U.; Veeraiah, N.; Alotaibi, Y.; Alghamdi, S.A.; Khalaf, O.I.; Subbayamma, B.V. An Improved Hybrid Secure Multipath Routing Protocol for MANET. IEEE Access 2021, 9, 163043–163053. [Google Scholar] [CrossRef]
- Elhoseny, M.; Shankar, K. Reliable Data Transmission Model for Mobile Ad Hoc Network Using Signcryption Technique. IEEE Trans. Reliab. 2020, 69, 1077–1086. [Google Scholar] [CrossRef]
- Sankaran, K.S.; Vasudevan, N.; Devabalaji, K.R.; Babu, T.S.; Alhelou, H.H.; Yuvaraj, T. A Recurrent Reward Based Learning Technique for Secure Neighbor Selection in Mobile AD-HOC Networks. IEEE Access 2021, 9, 21735–21745. [Google Scholar] [CrossRef]
- Malathi, M.; Jayashri, S. Modified Bi-directional Routing with Best Afford Path (MBRBAP) for Routing Optimization in MANET. Wirel. Pers. Commun. 2016, 90, 861–873. [Google Scholar] [CrossRef]
- Aftab, F.; Zhang, Z.; Ahmad, A. Self-Organization Based Clustering in MANETs Using Zone Based Group Mobility. IEEE Access 2017, 5, 27464–27476. [Google Scholar] [CrossRef]
- Kaur, M.; Singh, D.; Kumar, V.; Gupta, B.B.; Abd El-Latif, A.A. Secure and Energy Efficient-Based E-Health Care Framework for Green Internet of Things. IEEE Trans. Green Commun. Netw. 2021, 5, 1223–1231. [Google Scholar] [CrossRef]
- Zhang, T.; Zhao, S.; Cheng, B.; Farina, M.; Huang, J.; Chen, J.; Ren, B.; Hou, S. Lightweight SOA-Based Multi-Engine Architecture for Workflow Systems in Mobile Ad Hoc Networks. IEEE Acess 2018, 6, 14212–14222. [Google Scholar] [CrossRef]
- Kannhavong, B.; Nakayama, H.; Nemoto, Y.; Kato, N.; Jamalipour, A. A survey of routing attacks in mobile ad hoc networks. IEEE Wirel. Commun. 2007, 14, 85–91. [Google Scholar] [CrossRef]
- Singh, T.; Saxena, N.; Khurana, M.; Singh, D.; Abdalla, M.; Alshazly, H. Data Clustering Using Moth-Flame Optimization Algorithm. Sensors 2021, 21, 4086. [Google Scholar] [CrossRef]
- Chauhan, K.K.; Sanger, A.K.S. Key Management for Group Based Mobile Ad Hoc Networks. In International Conference on Computer Science and Information Technology; Springer: Berlin/Heidelberg, Germany, 2012; pp. 455–464. [Google Scholar] [CrossRef]
- Shibu, K.R.; Suji Pramila, R. Load Based Key Generation for MANETs: A Comparative Study with DSR and AODV. Wirel. Pers. Commun. 2021, 116, 1703–1712. [Google Scholar] [CrossRef]
- Singh, A.; Maheshwari, M.; Nikhil; Kumar, N. Security and Trust Management in MANET. In International Conference on Advances in Information Technology and Mobile Communication; Springer: Berlin/Heidelberg, Germany, 2011; pp. 384–387. [Google Scholar] [CrossRef]
- Pamarthi, S.; Narmadha, R. Adaptive Key Management-Based Cryptographic Algorithm for Privacy Preservation in Wireless Mobile Adhoc Networks for IoT Applications. Wirel. Pers. Commun. 2021. [Google Scholar] [CrossRef]
- Zhang, T.; Xu, X.; Zhou, L.; Jiang, X.; Loo, J. Cache Space Efficient Caching Scheme for Content-Centric Mobile Ad Hoc Networks. IEEE Syst. J. 2019, 13, 530–541. [Google Scholar] [CrossRef]
- Zhang, D.G.; Zhao, P.Z.; Cui, Y.Y.; Chen, L.; Zhang, T.; Wu, H. A New Method of Mobile Ad Hoc Network Routing Based on Greed Forwarding Improvement Strategy. IEEE Access 2019, 7, 158514–158524. [Google Scholar] [CrossRef]
- Xu, H.; Zhao, Y.; Zhang, L.; Wang, J. A Bio-Inspired Gateway Selection Scheme for Hybrid Mobile Ad Hoc Networks. IEEE Access 2019, 7, 61997–62010. [Google Scholar] [CrossRef]
- Dbouk, T.; Mourad, A.; Otrok, H.; Tout, H.; Talhi, C. A Novel Ad-Hoc Mobile Edge Cloud Offering Security Services Through Intelligent Resource-Aware Offloading. IEEE Trans. Netw. Serv. Manag. 2019, 16, 1665–1680. [Google Scholar] [CrossRef]
- Bettstetter, C.; Hartenstein, H.; Pérez-Costa, X. Stochastic properties of the random waypoint mobility model. Wirel. Netw. 2004, 10, 555–567. [Google Scholar] [CrossRef]
- Gupta, B.; Tiwari, M.; Lamba, S.S. Visibility improvement and mass segmentation of mammogram images using quantile separated histogram equalisation with local contrast enhancement. CAAI Trans. Intell. Technol. 2019, 4, 73–79. [Google Scholar] [CrossRef]
- Hu, G.; Chen, S.H.K.; Mazur, N. Deep Neural Network-based Speaker-Aware Information Logging for Augmentative and Alternative Communication. J. Artif. Intell. Technol. 2021, 1, 138–143. [Google Scholar]
- Ghosh, S.; Shivakumara, P.; Roy, P.; Pal, U.; Lu, T. Graphology based handwritten character analysis for human behaviour identification. CAAI Trans. Intell. Technol. 2020, 5, 55–65. [Google Scholar] [CrossRef]
- Jiang, D.; Hu, G.; Qi, G.; Mazur, N. A fully convolutional neural network-based regression approach for effective chemical composition analysis using near-infrared spectroscopy in cloud. J. Artif. Intell. Technol. 2021, 1, 74–82. [Google Scholar] [CrossRef]
- Xu, Y.; Qiu, T.T. Human Activity Recognition and Embedded Application Based on Convolutional Neural Network. J. Artif. Intell. Technol. 2021, 1, 51–60. [Google Scholar] [CrossRef]
- Basavegowda, H.S.; Dagnew, G. Deep learning approach for microarray cancer data classification. CAAI Trans. Intell. Technol. 2020, 5, 22–33. [Google Scholar] [CrossRef]
- Kaur, M.; Kumar, V.; Yadav, V.; Singh, D.; Kumar, N.; Das, N.N. Metaheuristic-based deep COVID-19 screening model from chest X-ray images. J. Healthc. Eng. 2021, 2021, 8829829. [Google Scholar] [CrossRef] [PubMed]


| Parameters | Value |
|---|---|
| Number of nodes | 5–60 nodes |
| Packet size | 1000 byte |
| Radio range | 150 m |
| Area | 500 m × 500 m |
| Number of traffic sources | 4 |
| Pause time(s) at simulation | I0 s |
| Traffic type | CBR |
| Send rate of traffic | 4 packets/second |
| Routing Protocol | AODV |
| Mobility model | Random Waypoint Mobility [40] |
| Data rate | 11 Mbps |
| Simulation Time | 100 s |
| Protocol | EED | PDR | Throughput | Energy Consumption |
|---|---|---|---|---|
| ENACSC [13] | 37.1317 | 81.8833 | 82.9983 | 6.6934 |
| ALARM [14] | 34.8151 | 84.6249 | 85.9999 | 6.2702 |
| FACES [16] | 39.3981 | 79.6719 | 81.0619 | 7.4092 |
| AMRP [17] | 38.8883 | 80.1767 | 81.5717 | 7.3336 |
| STARS [18] | 33.7127 | 85.5723 | 87.3473 | 6.1544 |
| NSC [19] | 39.8206 | 79.5294 | 80.6294 | 7.1802 |
| Proposed | 31.0567 | 87.9426 | 89.9438 | 5.5893 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Bondada, P.; Samanta, D.; Kaur, M.; Lee, H.-N. Data Security-Based Routing in MANETs Using Key Management Mechanism. Appl. Sci. 2022, 12, 1041. https://doi.org/10.3390/app12031041
Bondada P, Samanta D, Kaur M, Lee H-N. Data Security-Based Routing in MANETs Using Key Management Mechanism. Applied Sciences. 2022; 12(3):1041. https://doi.org/10.3390/app12031041
Chicago/Turabian StyleBondada, Praveen, Debabrata Samanta, Manjit Kaur, and Heung-No Lee. 2022. "Data Security-Based Routing in MANETs Using Key Management Mechanism" Applied Sciences 12, no. 3: 1041. https://doi.org/10.3390/app12031041
APA StyleBondada, P., Samanta, D., Kaur, M., & Lee, H.-N. (2022). Data Security-Based Routing in MANETs Using Key Management Mechanism. Applied Sciences, 12(3), 1041. https://doi.org/10.3390/app12031041









