1. Introduction
Social engineering (SE), otherwise referred to as social hacking, includes the various methods through which security is breached by exploiting the nature of human beings rather than attacking the established technologies and systems used by organizations [
1,
2]. Several SE tactics exist that cybercriminals use to attain their malicious and selfish interests that harm the victim. Those tactics include gaining illegal access to digital and physical resources, tapping the confidential and private information of the victim [
3], installing malware and other harmful programs on the victim’s system, and persuading the victim to initiate actions that will turn out to endanger their day-to-day organizational activities and even their social lives. The peak danger of SE attacks is the disclosure of privileged information after massive data breaches, which may lead to significant financial losses for the affected organization.
This paper focuses on vishing, which is a special type of phishing attack using phone calls against organizations. Vishing is a highly effective and focused type of SE attack that employs speech to entice victims into providing personal information. Vishing attacks are now very difficult to detect, especially when hackers use artificial intelligence (AI) to mimic speech patterns. A real example is when a caller who sounded just like the CEO of a UK energy supplier called the CEO in March 2019. The CEO transferred
$243,000 to a “Hungarian supplier” since the conversation was so convincing, but the bank account belonged to a scammer [
4]. Another attack, showing how creative cybercriminals have become in this SE ruse, is demonstrated by a recent data breach at the Ritz in London that turned into vishing assaults on hotel visitors. The Ritz assault’s significance, among other high-profile incidents, shows that the phishing attack field has expanded as remote working has become more prevalent in corporate settings. The Ritz guests, who paid around
$3000 per night, fit a specific socioeconomic profile; as a result, the audio communications were carefully targeted and rehearsed. The attackers pretended to be from the Ritz and targeted corporate clients to obtain credit card information. Digital Trends claims that one victim fell for the hoax since the incoming phone number was faked to seem like the hotel’s real number (
https://www.forbes.com/sites/emilsayegh/2020/09/30/vishing-at-the-ritz-theres-a-new-type-of-cybercrime-in-town/?sh=386df16c700d, accessed on 5 November 2022). Due to the Ritz’s lack of consumer education regarding what calls to anticipate about their patronage during regular business hours, the vishing assault was very successful. Additionally, working from home enhances SE assaults, meaning that company staff must identify acaller to evaluate whether he is a remote employee or a hacker impersonating an employee [
5].
External factors may excite or provoke psychological traits in people, turning them into psychological flaws that could be the subject of an SE attack. We distinguish substantial influence overloading, reciprocity, deceptive relationships, responsibility and moral duty distribution, authority, integrity, consistency, and social verification that could influence the victim. Therefore, it is clear that human psychological conditions play a vital role in the success of SE attacks, even with security experts. We can never guarantee the separation between emotions and correct decisions.
This research seeks to respond to the question: How can businesses deal with people as a point of vulnerability that criminals might exploit through SE to further their illicit objectives? Enterprises must play a crucial part in making sure that this vulnerability is fixed and that SE assaults are drastically decreased. Creating a strong social media policy for the company’s premises, and even while employees are off-site, is a realistic strategy that businesses adopt to reduce SE assaults [
6]. However, such procedures and training will be ineffective if staff members do not follow them.
No defense framework or approach that effectively deals with human psychological characteristics exists, to the best of our knowledge. All of the existing defense approaches rely on security awareness and guidelines [
7,
8,
9,
10,
11]. We distinguish the SEADM model [
12], detailed in
Section 2, that processes the psychological conditions and depends on the victim’s decisions to stop communication with the attacker if the psychological conditions are deemed to be harmful. However, could we guarantee that the victim will follow the SEADM model?
This paper proposes a new effective SE defense model to overcome human weakness. The goal is to at least double the control of the transaction (i.e., from external sources) to ensure its integrity and avoid the possibility of the victim being deceived. We mainly implement the dual control and split knowledge principles [
13] to mitigate SE attacks and avoid single failures through the use of blockchain networks. Split knowledge and dual control are used to avoid the possibility of one person being able to make the complete transaction or obtain full access to the information by themselves. Dual control focuses more on the transactions and task completion; however, the split knowledge condition essentially focuses on the data being split between two or more persons to prevent any person from having complete knowledge (i.e., dual controlling the information).
Blockchain is a mechanism for storing data in a way that makes system changes, hacking, and cheating hard or impossible. A blockchain is simply a network of computer systems that duplicates and distributes a digital record of transactions throughout the entire network. Each block on the chain comprises several transactions, and each participant’s ledger receives a copy of each new transaction that takes place on the blockchain. Transactions on a blockchain are stored with an unchangeable cryptographic signature known as a hash. Distributed ledger technology (DLT) refers to a decentralized database that is governed by several users.
Our proposed method is the first that uses security principles for detection and mitigation of vishing attacks (i.e., a kind of SE attack achieved through phone calls). We first categorize the SE attacks according to the security principle required to stop them. Then, this paper proposes a new practical vishing attack defense model for organizations that delineates the security principles to use to avoid attacks. The blockchain is a crucial solution used to ensure that decisions are taken transparently and collectively and that each transaction is trustworthy, backed up with a securely stored record [
14]. It has a wide area of applications such as healthcare [
15], agriculture [
16], smart cities [
17], etc. Blockchain is used mainly to enhance the dual control security principle by creating a new block only when all parties decide about a potential phone call and demonstrate the split knowledge principle since the victim does not have complete knowledge of any secret or sensitive information. The proposed model is for organizations and not for individuals. Thus, the word ‘victim’, in this paper, refers to the organization’s employees targeted by the SE attacker. To summarize, the paper’s contributions are:
The Categorization of SE attacks based on the security principles required to avoid them.
The proposition of a new framework that uses blockchain networks to dual control any potential transaction through its management flow and to enable split knowledge so that the victim does not have complete information and needs to request the remaining information from other parties within the blockchain network.
The easy adoption and practical implementation of the proposed model within organizations, using free open blockchain platforms.
The proposed framework has the following advantages:
Avoiding the psychological status of the recipient of the vishing calls.
Avoiding the recipient of the call having to act alone.
Helping to make the right decision about received calls.
Dual controlling critical phone calls.
Using Blockchain to ensure that decisions are made collectively and transparently.
Ensuring the accountability of any critical decision regarding phone call requests.
The remainder of this paper is divided as follows.
Section 2 surveys the current works dealing with defense against SE attacks and discusses their limitations. In
Section 3, we propose a new categorization of SE attacks based on the defensive measures to stop them.
Section 4 presents a proposed new vishing defense model that uses Blockchain techniques to implement security principles. In
Section 5, we demonstrate the easy adoption of the proposed framework using a hyperledger fabric and an open and free blockchain network. In
Section 6, we discuss how well the suggested model performed. Finally, we conclude the paper in
Section 7.
2. Related Work
Existing research and models aiming to protect organization assets from SE attacks targeting the psychological status of the victim are scarce. We did not identify any model that dual controls potential transactions, and no approach that uses blockchain to implement security principles to deal with SE attacks.
An organization’s employees can utilize the methodology suggested in papers [
12,
18] to find social assaults in engineering in a contact center setting. The model is a quick and effective technique to see if the requester is attempting to coerce an individual into providing details for which the requester does not have permission. The psychological and computer science viewpoints are the two basic approaches of SE. The psychological viewpoint is concerned with the individual’s emotional condition and cognitive capacities. One of the cornerstones of information security is information sensitivity, addressed from a computer science perspective. Social engineers exploit a variety of psychological vulnerabilities and triggers, which have been identified. Strong effect, overloading, reciprocation, deception, diffusion of responsibility and moral duty, authority and integrity, and consistency are among them. Human characteristics, such as our limited ability to digest information, our use of heuristics (cognitive process or shortcuts designed to make judgments simple, which might lead to a major error), individual interests, and our susceptibility to emotional manipulation.
The authors of [
12] propose an SE attack detection defense model (SEADM), which uses a decision tree composed of several manageable components to help in the decision making in possible SE attacks. The first and most crucial stage in this paradigm, and one that must be considered throughout the process, is for the person to be aware of and analyze their emotional state regularly. The subject should assess the emotions elicited by the requester, as exploitation of psychological vulnerabilities is designed to provoke specific emotional states in order to obtain information. People are more likely to be SE victims if they are in a state of negative emotions: the level of focus is low, impatience and frustration are strong, and an individual may offer information to a requester to get rid of them. It is crucial to note that assessing one’s emotional conditions can be time-consuming, and some people cannot do so. As a result, an electronic questionnaire for automatic self-evaluation would be implemented, the correct completion of which would lead to the right decisions. The phone or email request should be passed to another person if the individual or the self-evaluation questionnaire indicates that the person is extremely emotional. Unfortunately, there is a chance that some people may use this as a means of assigning someone else their work responsibilities, which will just irritate everyone.
The risks of SE, such as obtaining privileged knowledge, can result in significant losses for the institution. SEADM was established as a non-deterministic flowchart that relies on extensive qualitative sub-procedures in order to serve as a model for identifying SE attempts in their initial stages. An enhanced version proposed by [
19] concentrates on formalizing the SEADM’s most recent iteration into an abstract deterministic finite-state automation. Their research effort intends to improve the extensibility of the SEADM and reduce the complexity of its implementation by rebuilding the operation to be cycle-free and predictable.
The I-E model, which is based on human vulnerability, was utilized to achieve socialization in the publication [
20]. The vulnerabilities exploited by various SE techniques were examined, and several defensive approaches to fix human flaws were deduced based on this model. The report identifies pieces of malware that have been activated through SE routes, including psychological and technical ruses. Some persuasive psychological approaches include victim curiosity, empathy, excitement, fear, and greed. Human vulnerability is a strategic connection in both the attack and defense aspects of an SE assault, as we can see from the workflow of an SE attack. It is vital to avoid human vulnerability to thwart exploitation; social engineers depend on exploiting such vulnerabilities. The internal and external nature that evokes human vulnerabilities, called the I-E model based on the effects of human conditions and vulnerabilities, are the two basic levels for producing the features of a person’s human psychological states. Features of human nature can be categorized into two broad groups from a psychological standpoint: positive and negative. According to the I-E-based paradigm, there are various defensive strategies to repair human vulnerabilities; these defense measures are divided into objective and subjective approaches, as discussed in [
20].
Another tool proposed by [
21] provides the attacked subject another chance to confirm his or her decision when clicking on new links from untrusted sources. However, their application still depends on the individual, who may be subjected to psychological disruption. Authors from Bournemouth University proposed a new SE attack defense framework named MINDSPACE [
22]. The framework describes the victim’s behavior regarding different SE attack types. However, they did not explicitly propose defensive mechanisms to deal with them. In paper [
23], the authors survey the facts of SE attacks targeting the banking sector in New Zealand. They then propose a mitigation model by decomposing SE attacks in five steps and presenting recommendations to prevent the attack being successful at each stage. Their approach still requires the victim to strictly follow the guidelines and avoid exposure to a single-point failure.
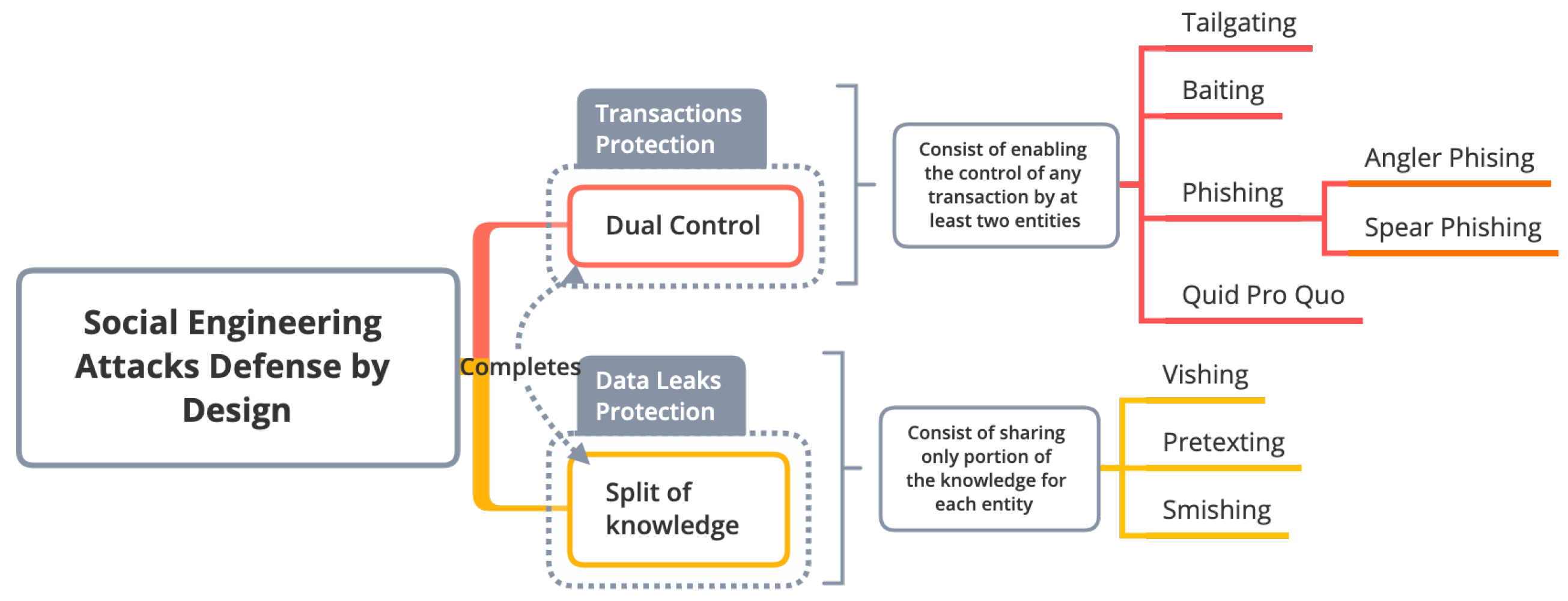
3. Preventing Social Engineering Attacks Using Security Principle
In this effort, we propose implementing two security principles to deal with human weaknesses: split knowledge and dual control. To the best of our knowledge, no previous model or research has implemented those security principles to deal with SE attacks and the reliance on human decisions. This section categorizes different SE attacks according to the security principles that will stop them. In addition, this is the first categorization that links defense techniques with specific SE attacks, rather than simply categorizing attacks [
11]. We aim to implement a solution using security principles that avoid dependence on the psychological status of the individual, even if he or she is well trained. Human decisions and actions are unpredictable during any psychological condition, and employees in certain circumstances will threaten any organization’s policy. The idea is to minimize the privileges and need-to-know for employees to a minimum, so that no one could disclose complete knowledge or make a transaction without the endorsement of at least one other person. Thus, even if one person breaches security guidelines, the second will usually discover it and avoid disclosing information or making suspicious transactions. Of course, the use of those security principles is applicable only within organizations where information is classified according to its sensitivity and tasks are distributed over several employees.
The categorization process of SE attacks is based on the following factors:
Split knowledge is a subset of the dual control principle but related only to the information. Dual control is more related to processes and mechanisms. The categorization is based on whether stopping the hacker from knowing the information or completing the hacking operation will avoid the attack or not. In other words, if the SE attack fails when the information is not completelty gathered, then the SE attack is classified within the split knowledge category. Equally, if the SE attack fails when the operation is not completed, then the SE attack is classified within the dual control category. Some of the SE attacks could be stopped by both split knowledge or dual control. In this case, we categorize them as dual control since it represents the big umbrella.
We show in the
Figure 1 only the SE attacks that use different contact/communication techniques with the victim. Therefore, attacks such as piggybacking and whaling are not depicted in
Figure 1 but mentioned as similar attack types.
It should be noted that attacks, such as honeytraps, scareware, pharming, and watering hole assaults, which are categorized as spoofing attacks and employ spoofing techniques to deceive the target, are not taken into account, since those assaults are carried out without the victim having to be involved. For instance, eavesdropping, shoulder surfing, and dumpster diving assaults do not necessitate conversation with the victim. Instead, they include information acquisition by illegal listing, peering over someone’s shoulder, or searching for treasure in someone else’s garbage, respectively.
Figure 1 shows the proposed categorization of SE attacks and the security principle to stop them.
3.1. Defenses Based on Split Knowledge Principle
Split knowledge is a great security principle within organizations to avoid information disclosure by one person. It consists of dual controlling the knowledge (such as part of the password, cryptographic keys, etc.) to complete the task. In the USA, the cryptographic key responsible for launching nuclear bombs is divided among several persons, not only the president. Thus, the country is confident that such a critical decision will only be achieved after confirmation from the different parties. Split knowledge is achieved through precise definitions of privileges, good account management, and job rotation. This section will describe the different SE attacks that could be mitigated and stopped by implementing the split knowledge principle.
We should note that an organization will classify data according to the sector it belongs to, as explained in
Section 4.1. By Split knowledge, we mean that every person in the organization knows only the information he or she needs (need to know) according to the data classes defined by the organization, so the information is split between the different employees.
3.1.1. Smishing
Smishing is a mashup of the words SMS and phishing. Smishing is a type of cyberattack in which the attacker deceives the victim into disclosing sensitive information or handing over money. The cybercriminals dupe the victim into thinking the message came from a well-known person or group. They frequently ask the victim to click on websites or contact a specific number to verify, update, or reactivate their account [
24]. We distinguish another SE attack that uses instant messages named spimming. Spimmers typically employ bots to gather instant message IDs and send spam to victims. A bot is an application that performs automated activities over the network.
For cybercriminals, bank smishing is the most profitable sort of attack. Cybercriminals prey on the victim’s fear of having their bank accounts compromised. They usually send the victim a text message purporting to be from the bank, warning them about a large financial transfer or a new payee being introduced. When the target responds and follows the instructions, the attackers collect sensitive information such as bank account login credentials and other personal information. The attacker can quickly access your bank account once they obtain your credentials. As a business owner, you must educate your personnel on how to recognize smishing and other sorts of attacks. The victim’s psychological situation, on the other hand, puts training provisions in jeopardy.
When the split knowledge concept is employed, the victim will lack the necessary information to satisfy the attacker’s objectives, rendering their attacks ineffective. Split knowledge will ensure that the victim does not possess the complete information to execute the transaction desired by the requester (possible hacker).
3.1.2. Vishing
Vishing is a unique assault that falls under the general umbrella of phishing and has the same objectives as phishing. Vishing uses fake phone numbers, voice-altering software, SMS messaging, and SE to deceive consumers into giving critical information that can be utilized for identity theft, financial gain, or account takeover. Voice is commonly used by vishing to mislead users.
Vishing, unlike phishing, is primarily a telephone-based assault that involves calls to a user’s cell phone number. The first step would be for the visher to send a large number of text messages to possible victims from a vast list of phone numbers. The message may instruct users to dial the attacker’s phone number. Another vishing technique involves sending a pre-recorded message to potential victims, which is then robo-dialed. To erase accents and develop confidence, it uses computer-generated audio communications. The voice message then leads the user to a human agent who either continues the fraud or asks them to visit an attacker-controlled website. The goal of vishers is to mislead the victims into thinking that they caller has authority by providing social proof [
25].
Educating users helps organizations recognize vishing attacks, which they can then ignore or report. Individuals should never hand out personal information to someone who contacts them via text message or phone call. Those defenses all rely on an individual’s accurate judgment; therefore, any error will result in losses for the organization. By applying split knowledge and dual control principles, the victim will not have complete sensitive information, and any suspicious call will be checked; therefore, the damages will be mitigated.
3.1.3. Pretexting
Pretexting is a SE method used to trick people into handing over information. A pretext is a made-up scenario concocted by threat actors to acquire a victim’s personal information. Threat actors generally ask victims for specific information during pretexting assaults, claiming, for example, that it is required to authenticate the victim’s identity. The threat actor steals this data and then uses it to launch secondary attacks or commit identity theft [
26].
Pretexting assaults develop a false sense of trust with a targeted victim, whereas phishing attempts prefer to leverage urgency and fear to exploit victims. This means that threat actors need to fabricate a plausible explanation that does not lead victims to suspect illegal activity.
3.2. Defenses Based on Dual Control Principle
The dual control principle uses two or more separate entities (usually persons) to complete tasks. Thus, the responsibility of making a transaction is shared between the involved entities, which prevents a single person from accessing or using the materials individually.
This security principle will avoid the reliance just on one person’s decision who may be subjected to a psychological situation. So, at least two persons, according to the organization’s policy, will handle any transaction, which will reduce the possibility of human errors.
3.2.1. Quid Pro Quo
A quid pro quo attack is a low-level sort of SE-based hacking and a form of baiting. A cyberhacker offers the victim something in return rather than attempting to trick him or her out of curiosity or fear. It basically comes down to “a favor for a favor”, which is what the Latin term implies. Attackers solicit information from the victim in exchange for anything. Given that humans adhere to the psychological reciprocity rule, the idea of exchange is essential. This implies that the victim feels obligated to repay someone for everything they offer or accomplish for him (
https://blog.mailfence.com/quid-pro-quo-attacks/, accessed on 5 November 2022).
Quid pro quo assaults, like all other types of SE attacks, target an organization’s human aspect. These attacks endanger your employees’ online safety and jeopardize your entire company’s cybersecurity [
27].
Employees could be protected against SE attacks such as quid pro quo by implementing certain practices and rules. Security awareness training for all organization employees is required to spot prevalent SE approaches. However, it is still contingent on the victim’s psychological condition and rigorous adherence to the training.
3.2.2. Tailgating
Tailgating is a straightforward physical SE technique that allows hackers to have access to password-protected physical assets. Tailgating is when you closely follow an authorized individual into a restricted location. When a typical employee swings a hefty door, a tailgating social engineer may seize it just as it closes, walking right into the targeted physical system. Organizations are particularly vulnerable to tailgating SE attacks if they have a large number of employees and a high rate of staff turnover. Another similar SE attack called piggybacking differs from tailgating in that piggybacking entails an authorized person intentionally allowing a hacker to enter a restricted zone thinking he or she has a legitimate reason for being there.
To prevent tailgating attacks, businesses should ensure that the reception area is well-lit and that identification mechanisms are in place. Tailgating can also be controlled and thwarted with visitor badges and video surveillance. Employees should be cautious and follow security best practices in general. Dual entry control for the organization will provide extra defense lines and prevent tailgating.
3.2.3. Baiting
Baiting assaults, as the name describes, pique a victim’s interest or avarice by making a false promise. In order to steal private information or infect systems with dangerous software, they manipulate individuals into falling into a trap. The most despised kind of baiting uses tangible material to spread malware [
26]. For instance, attackers can set out the bait—malware-laced ash disks—in plain sight in places where potential victims are likely to encounter them (such as restrooms, elevators, or the parking lot of a targeted business). The lure has a realistic appearance and is tagged, for example, as the corporation’s salary report.
Employing a dual control system, where at least two or more persons are in charge of a single process, will help defend organizations from cyber dangers.
3.2.4. Phishing
Phishing is a category of SE assault that is mainly used to gain sensitive information from users, such as login credentials and credit card information. It occurs when an attacker shows up masquerading as a trustworthy entity and convinces a victim to open an instant message, email, or text message. The recipient is duped into entering a malicious link, which can lead to a malware installation, the disclosure of sensitive data, and system freeze as part of a ransomware assault [
28]. Whaling is a type of phishing attack when it targets a specific high-profile person and uses the same techniques as phishing.
Two-factor authentication (2FA) is the most effective approach for preventing phishing attacks when logging into sensitive applications since it offers an extra degree of verification. Users need two things to use 2FA: something they know, such as a password and username, and something they have, such as their smartphones. It would be best to use a 2FA approach to avoid psychological difficulties for more than one individual.
3.3. How Security Principles Prevents Social Engineering Attacks
Following the classification of SE attacks and showing how defenses can be based on the security principles that thwart them, in this part, we will discuss how such security principles may prevent SE attacks. Each SE attack is described in
Table 1 along with the security concepts that may be used to mitigate it at the data and management levels.
3.3.1. Split Knowledge Effectiveness Analyis
The proposed model is designated for corporations and organizations in a working environment. It is not to protect individuals from SE attacks outside their job.
As we mentioned in
Section 4.1, data within the organization are supposed to be classified according to the organization sector (governmental or private). So, the [recipient], who will be the first person in contact with a possible SE hacker, knows only public information. He or she does not have secret information to disclose. Smishing, for instance, uses SMS to contact the victim. If the victim (recipient) does not know the private information since the knowledge is split and classified, he or she will redirect the request through the blockchain network to another background verifier. Mostly, the second verifier will discover that the SMS is a kind of smishing and notify the recipient. The goal is to deal with the problem of single-point vulnerability presented by the recipient, but through split knowledge, the problem will be handled by more than one person who does not witness the psychological circumstances. Therefore, the secret information will not be disclosed since any transaction must be endorsed by several verifiers determined by the organization. Even, if one verifier is tricked, the transaction will be accepted only if all the verifiers endorse it. In addition, it will not be a summative gathering of the information by the hacker since the transaction atomic can only be accepted after all defined organization peers endorse it.
Similarly, split knowledge will protect corporations against all SE attacks classified on its category.
3.3.2. Dual Control Effectiveness Analysis
Dual control is an implementation of a defense-in-depth strategy. It involves more protection mechanisms to complete any transaction. Dual control requires at least two persons to handle any transaction so that if one person is tricked, the second will discover it. For instance, quid pro quo, tailgating, baiting, and phishing attack success depends on bypassing one direct person. It does not require information disclosure but mostly incites the victim to do something. Dual control will stop those attacks since every transaction will be verified twice.
Similarly, dual control will protect corporations against all SE attacks classified in its category.
6. Discussion
Throughout this paper, we described a new SE attack defense model that avoids the psychological issues exploited by the SE attacker [
26]. In
Table 2, we depicted the proposed model’s advantages compared to the existing models dealing with SE attacks, which are very scarce. In addition, the table describes features of the model enabling the implementation of security principles.
6.1. Ability of the Model to Deal with Employee’s Psychological Status
The models listed in
Table 2 all aim to solve the dependence on individual psychological status when subjected to SE. Except for ours, their success depends on the person’s strict compliance with the instructions of the model; however, the model never enforces compliance, so the victim could ignore the regulations and therefore be defeated by the attacker.
Existing models such as SEADM rely on the person’s strict compliance with the model’s instructions; however, the model never compels the person. Consequently, the victim could ignore the regulations and therefore accede to the requests of the attacker. The SEADM and similar models require humans with robotic hearts and minds to effectively deal with SE attackers experienced in exploiting the psychological susceptibility of the victim. However, an individual’s actions depend on their culture, environment, and things that are important to them; if these are correctly exploited, the victim will not follow the organization’s regulations.
Only our proposed model, which involves background checks, can double-check a transaction before it takes place since one of the model’s purposes is to avoid a single point of vulnerability. By enforcing security principles, we are confident that the attacker will not succeed in his objective by just bypassing the person called; the attacker must also get beyond the background checks conducted by other persons, about whom the attacker knows nothing. The control and monitoring of the attacker’s attempt to trick the recipient are enabled via the blockchain model’s component. The model, via the blockchain data’s flow, will treat the request from the recipient who received the suspicious call first by translating it into a smart contract. Then, the orderer will deliver the transaction to all required peers (verifiers). The transaction is accepted if all peers endorse it; otherwise, it is rejected. This is how the model implements dual control and benefits from the blockchain management mechanisms. We are aware that SE relies on the attacker carefully collecting information on the victim to craft successful deception. Since the background verifier(s) are unknown to the attacker, they cannot be psychologically deceived.
6.2. Ability to Enforce Security Principles (Dual Control and Split Knowledge)
To the best of our knowledge, no approach deals with the psychological depression of the victim regarding vishing attacks by enforcing the organization’s policies. Our proposed model enforces the organization’s rules by implementing two security principles: split knowledge and dual control. The main idea is to subject suspected SE attacks to double or greater verification. The enforcement of security policies is enabled through blockchain deployment. It manages dual control through separation of the request (smart contract) sent by the client (recipient) and the required verification by peers (background verifiers) to endorse (accept) or reject it. Consequently, split knowledge is enforced, since the information known by the recipient is not sensitive based on the organization’s data sensitivity classification, as explained in
Section 4.1.
The blockchain has the power to coordinate between the different parties without negatively impacting the business process. Moreover, blockchain technology will not delay the response to the request, since we adopt a private blockchain network, which does not require proof of work to create a new block. In addition, the proposed approach will not cause any business disruption by requiring more entities to verify customers’ requests since the organization can determine the minimum number of endorsers needed to create a new block according to the sensitivity of the transaction and the business requirements.
The ability to avoid a single point of failure is a consequence of security principles enforcement since any potential transaction is dually verified.
6.3. Ability to Keep Track of Completed Transactions
In our proposed model, accepted transactions are securely recorded using blockchain technology, maintaining their integrity, validity, and transparency. Additionally, since no block will be deleted or changed, blockchain technology ensures that past transactions can be easily tracked. Relational databases cannot match the immutability and transparency of the blockchain. Therefore, once the block data are published to the blockchain, no one will be able to refute them, ensuring the non-repudiation feature needed in such a potential investigation [
33].
The other existing studies do not provide tracking features for employees’ actions to hold accountable those violating the company regulations.
6.4. Ability to Integrate and Adopt the Model Easily within the Organization
We demonstrated the easy implementation and deployment of blockchain technology within any organization using an already implemented open-source blockchain network; specifically, we selected the hyperledger fabric private blockchain network. This paper is the only study among the research referred to, such as SEADM [
12] and its enhanced version SEADM II [
18], that provides technical guidance for implementing the suggested model within organizations.
7. Conclusions
This paper proposed a new model for defense against SE attacks, which uses blockchain technology to enforce security principles. Our model specifically addresses vishing assaults, which are currently very successful, especially when using social networks to acquire information.
We also categorized the SE attacks based on the security principles that could avoid them; essentially, all SE attacks can be mitigated using the principles of dual control and split knowledge.
We demonstrated our proposed model’s easy adoption and materialization within any organization using open-source private blockchain networks. The main philosophy of the proposed approach is to avoid a single point of failure and increase the in-depth defense principle regarding SE attacks. Our proposed model is the first, to the best of our knowledge, to require vishing attacks to be checked at least twice by different entities using blockchain technology.
Blockchain technology is a key component of the proposed solution since it provides flexible and trustful flow management of different transactions within the organization. Flow management is required to enable security principles (i.e., dual control and split knowledge), while trusted recording is essential to ensure transparency, non-repudiation, and accountability. Usually, during the hiring of an employee, the organization requires him or her to sign a non-disclosure agreement in which the employee is informed about the confidential data and sharing rules. The organization must have a mechanism to track any agreement breach while ensuring non-repudiation and transparency between employees. Blockchain technology enables non-repudiation and accountability of every employee action through its immutability (i.e., permanent and unaltered), distribution (i.e., all network participants have a copy of the ledger for complete transparency), and security (i.e., ledger secured with cryptographic techniques) characteristics. Blockchain technology outperforms traditional databases in terms of security since every block is encrypted and extremely hard to compromise. It also provides management process inclusion to coordinate amongst the many network partners. As a result, integrating the blockchain into an organization’s network is easier, quicker, and less expensive.
We aim to include forensics requirements during the block creation to ensure the admissibility of the records. The use of ontological data representation will automate the search for valuable evidence quickly [
34,
35]. In addition, we aim to create new metrics that compute the effectiveness of our proposed approach regarding SE attacks using metric elicitation methodologies [
36].