Novel Feature Extraction Method for Detecting Malicious MQTT Traffic Using Seq2Seq
Abstract
1. Introduction
2. Related Studies
{tcp.flags, tcp.time_delta, tcp.len, mqtt.conack.flags, mqtt.conack.flags.reserved, mqtt.conack.flags.sp, mqtt.conack.val, mqtt.conflag.cleansess, mqtt.conflag.passwd, mqtt.conflag.qos, mqtt.conflag.reserved, mqtt.conflag.retain, mqtt.conflag.uname, mqtt.conflag.willflag, mqtt.conflags, mqtt.dupflag, mqtt.hdrflags, mqtt.kalive, mqtt.len, mqtt.msg, mqtt.msgid, mqtt.msgtype, mqtt.proto_len, mqtt.protoname, mqtt.qos, mqtt.retain, mqtt.sub.qos, mqtt.suback.qos, mqtt.ver, mqtt.willmsg, mqtt.willmsg_len, mqtt.willtopic, mqtt.willtopic_len}
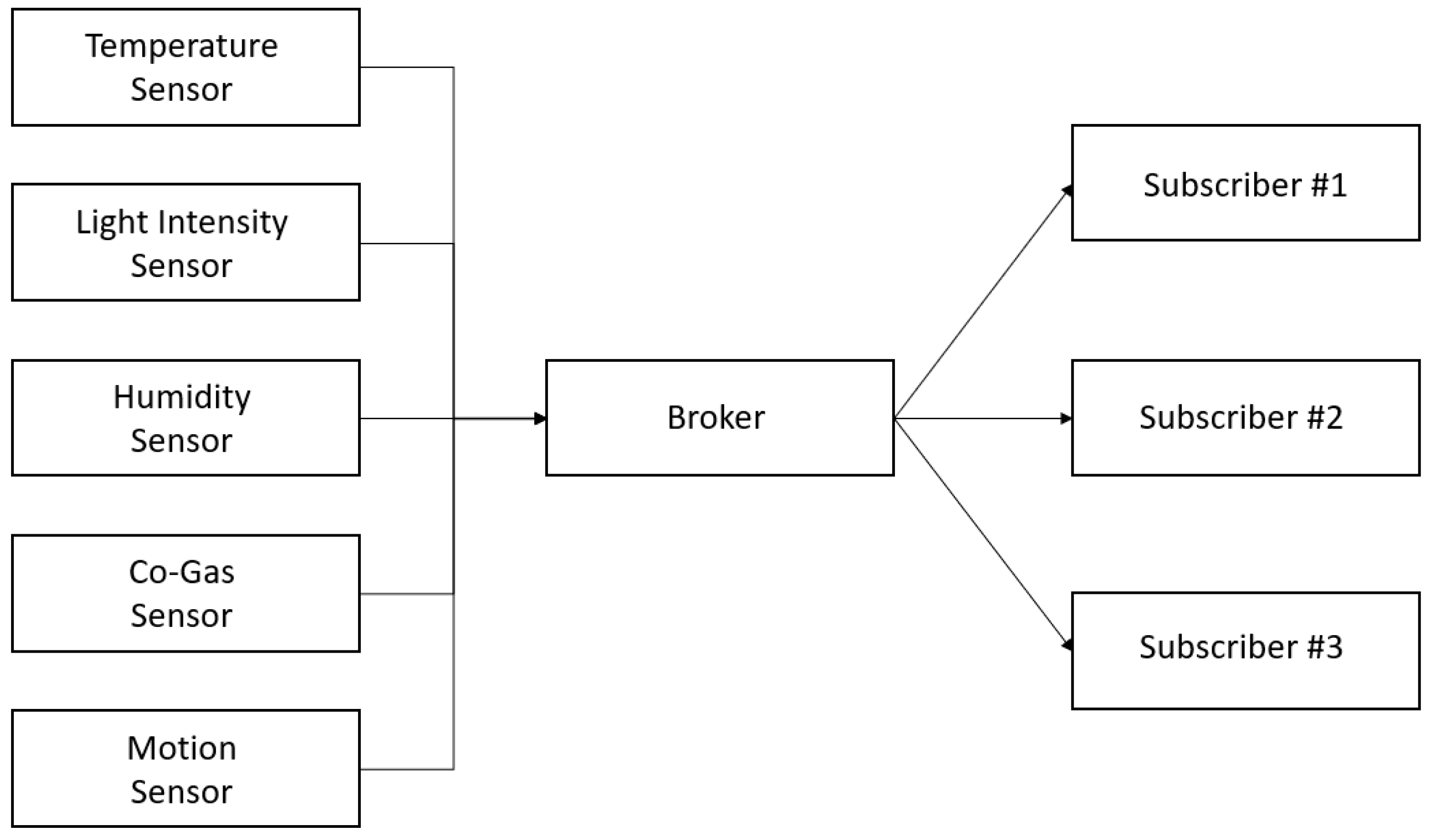
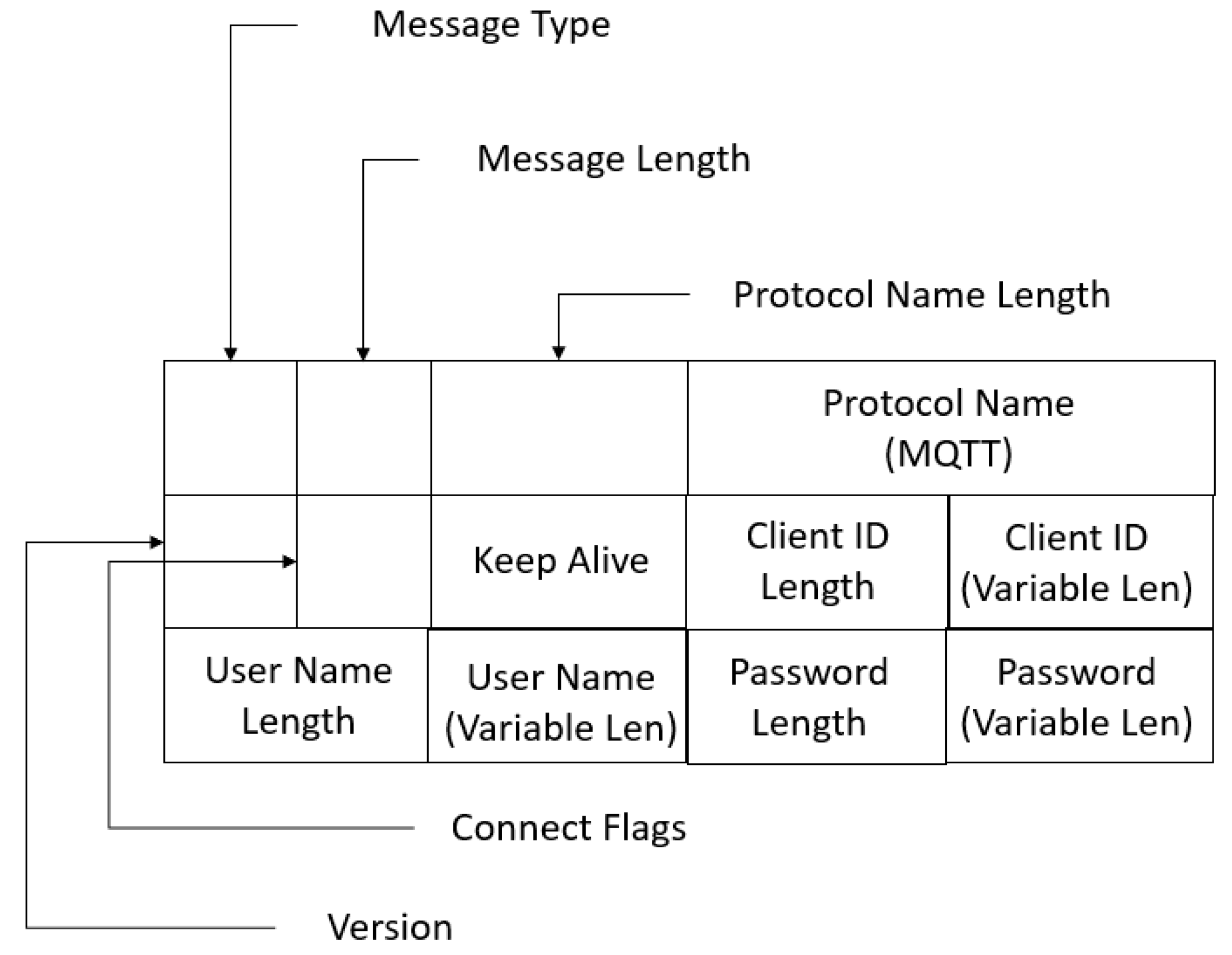
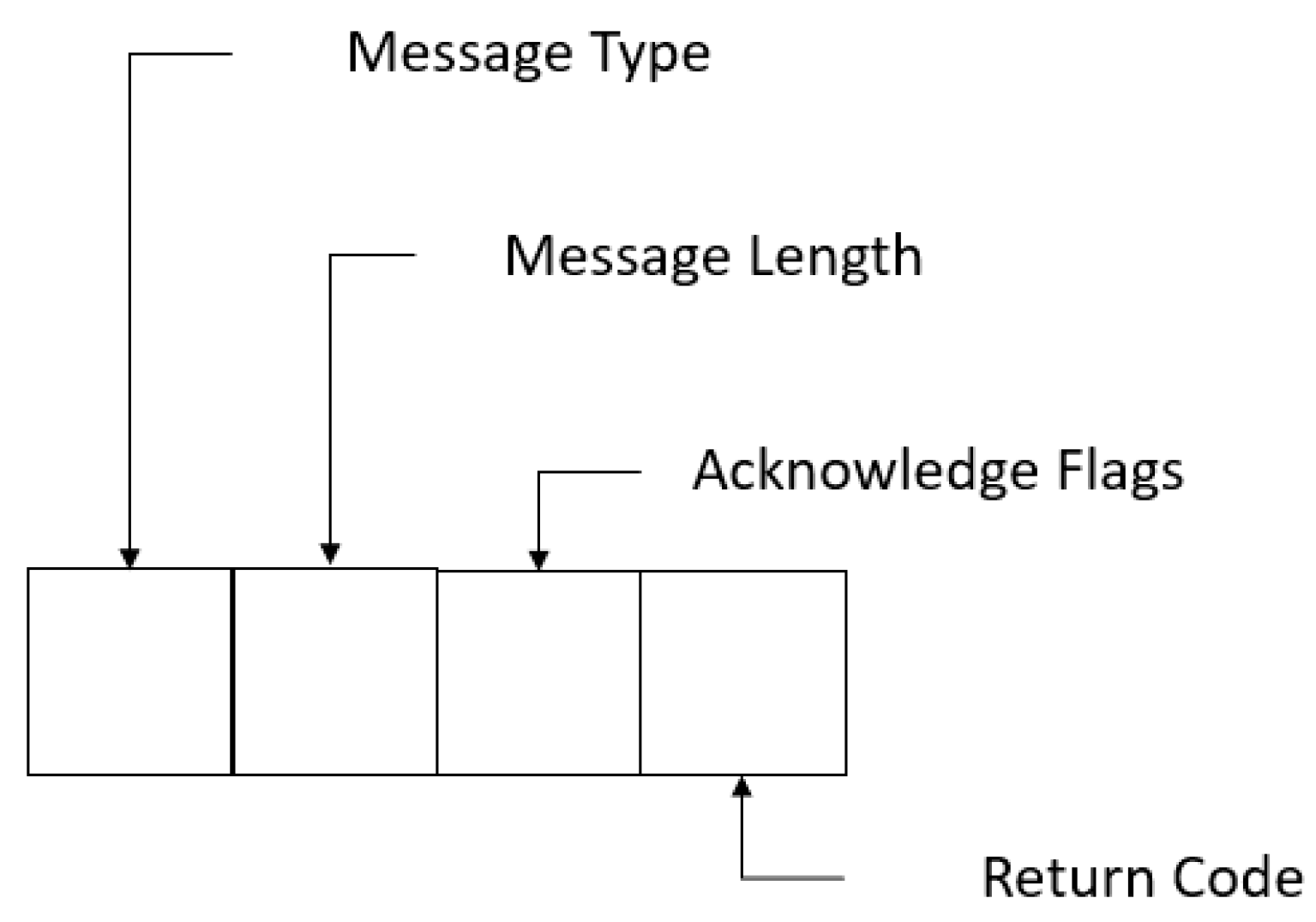
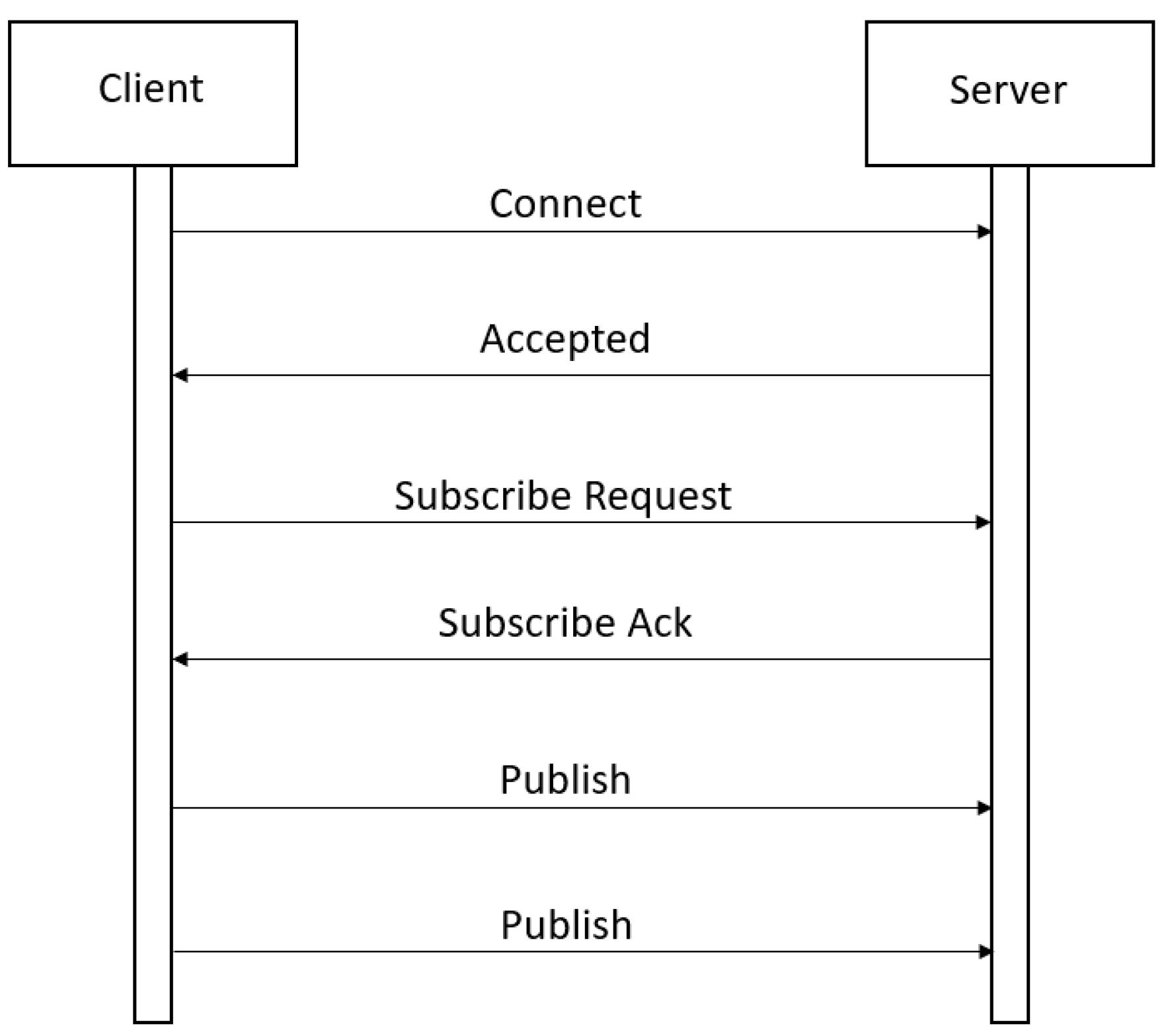
3. Message Queue Telemetry Transport (MQTT)
4. MQTT Attack Analysis
4.1. DoS Attack
4.2. Flood Attack
4.3. SlowITe Attack
4.4. Malformed Attack
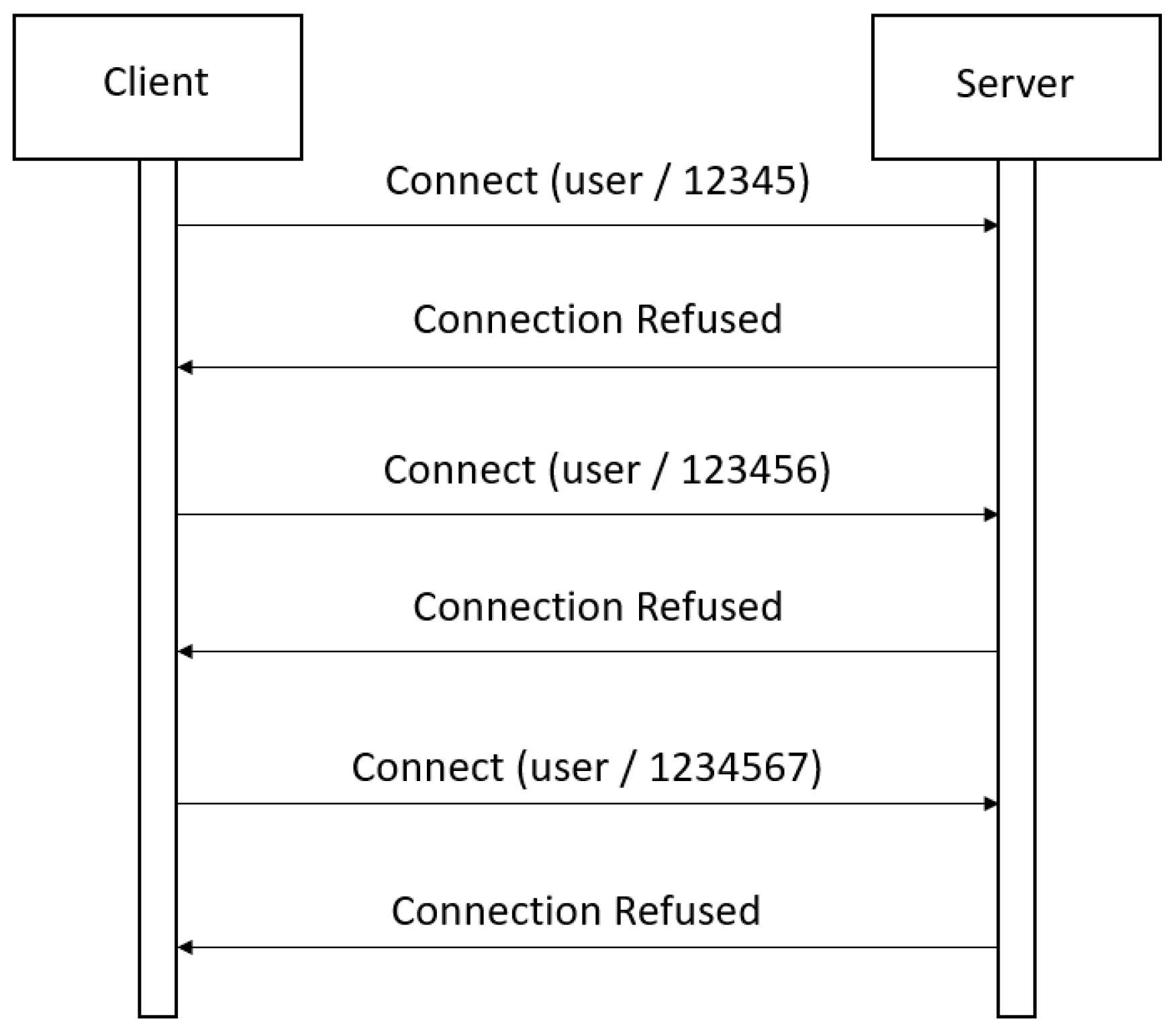
4.5. Brute-Force Attack
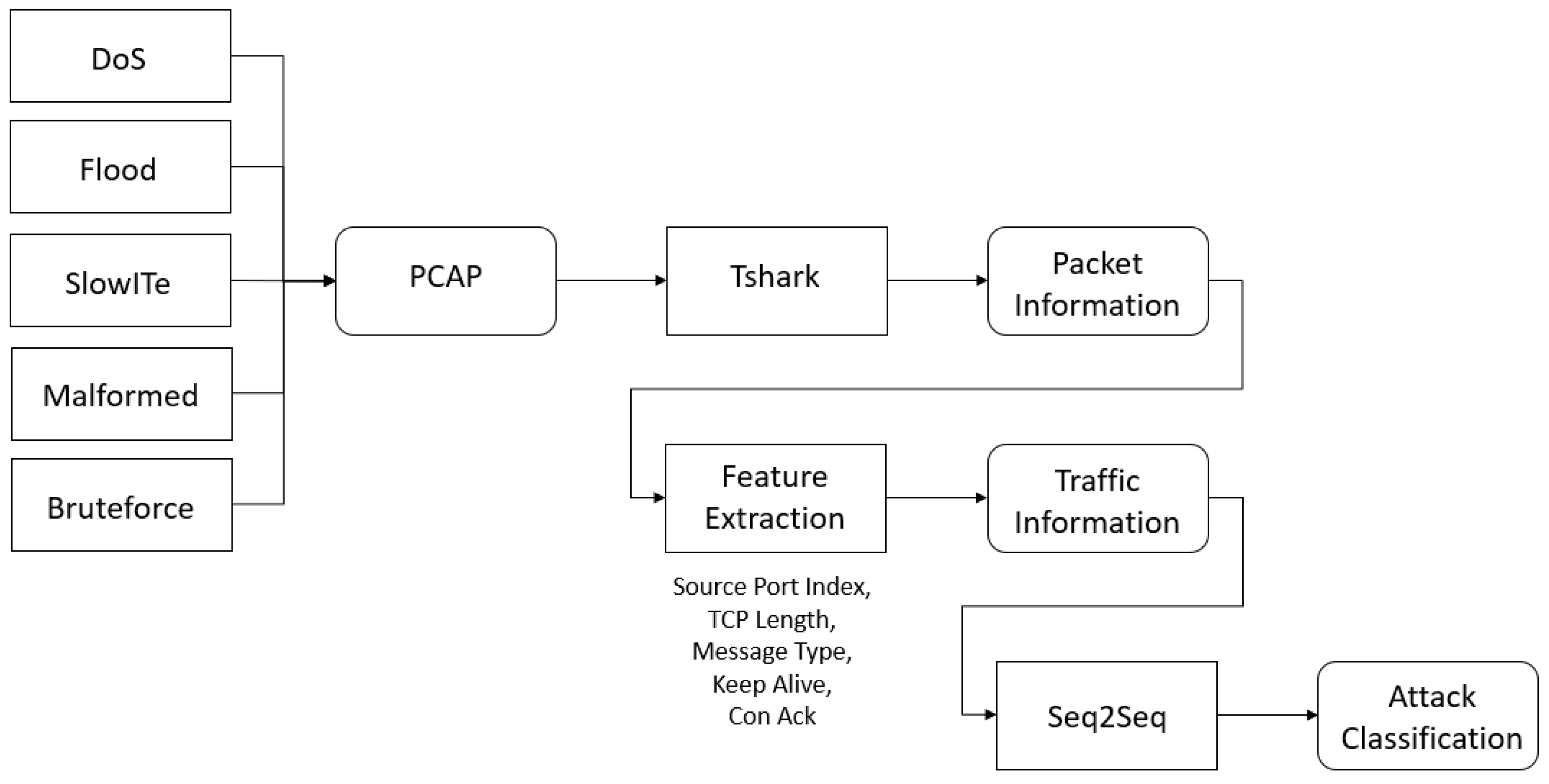
5. Feature Extraction
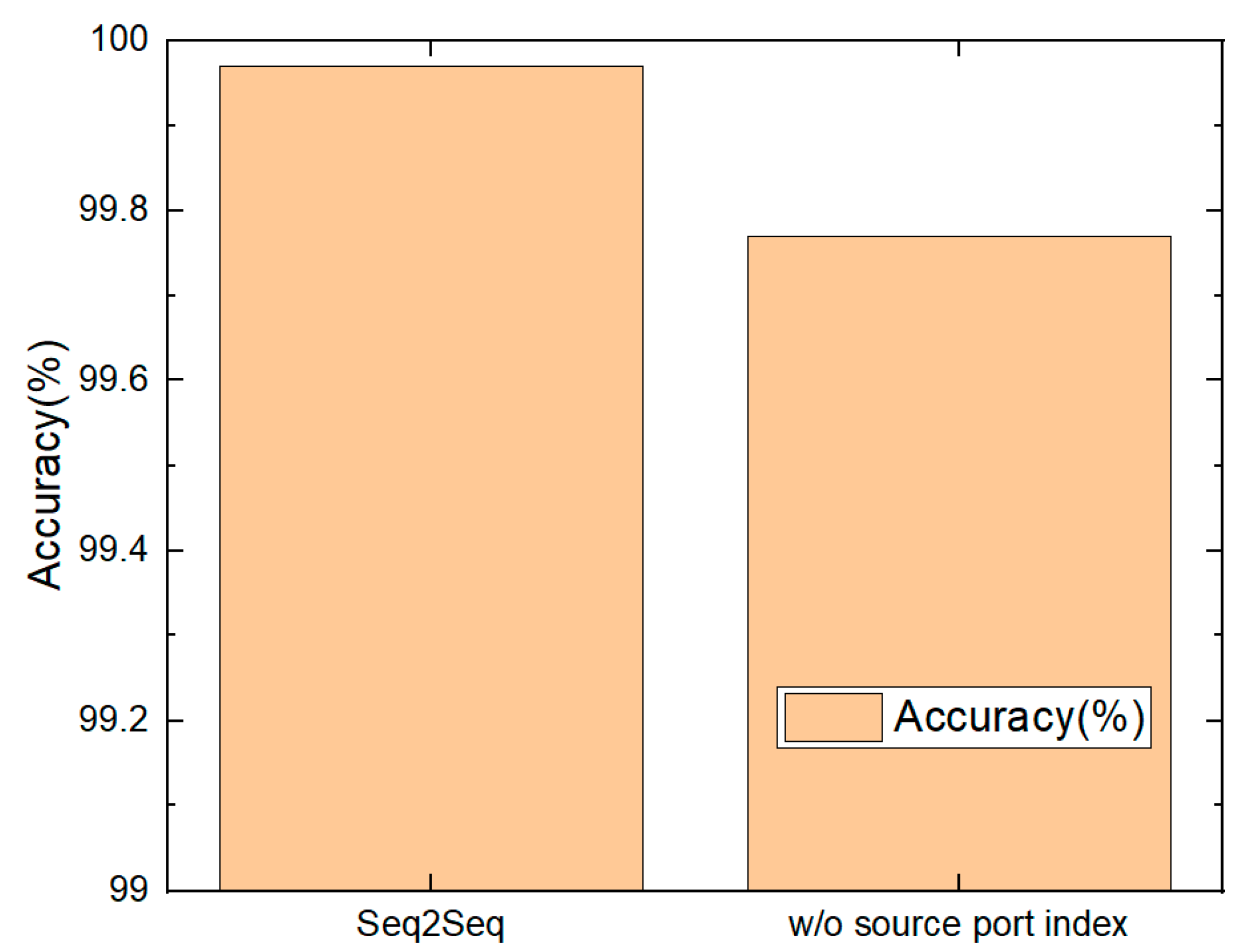
5.1. Source Port Index
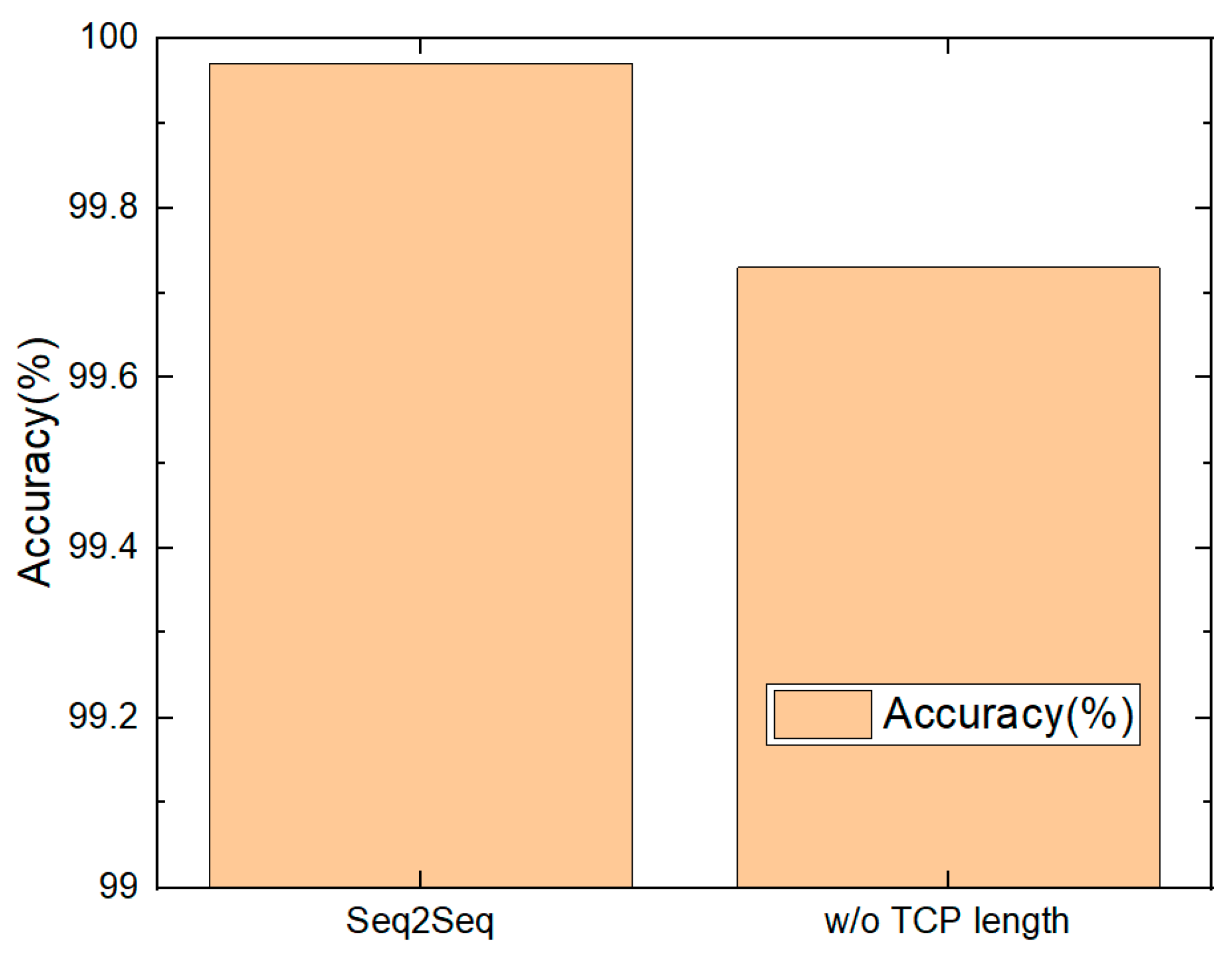
5.2. TCP Length
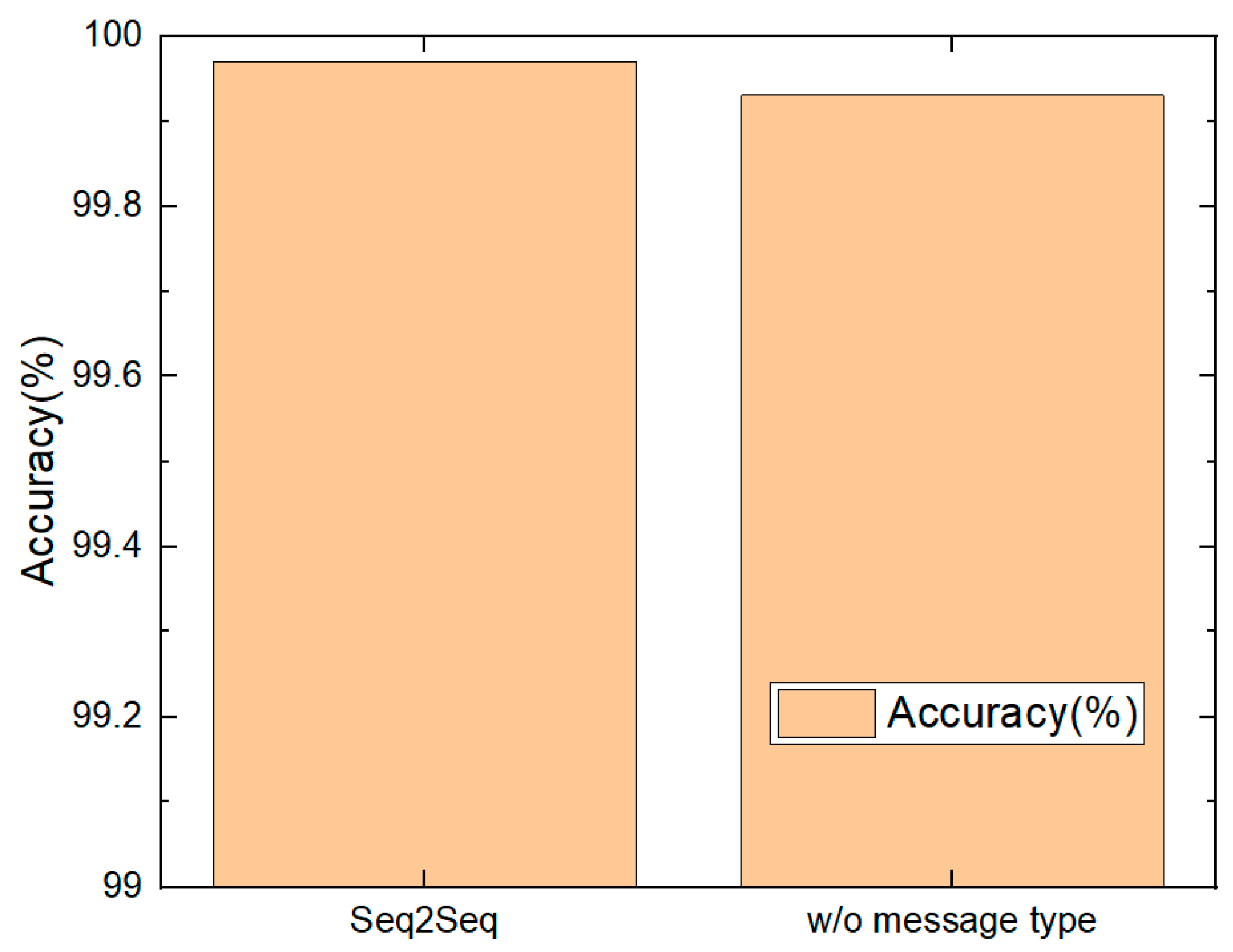
5.3. MQTT Message Type
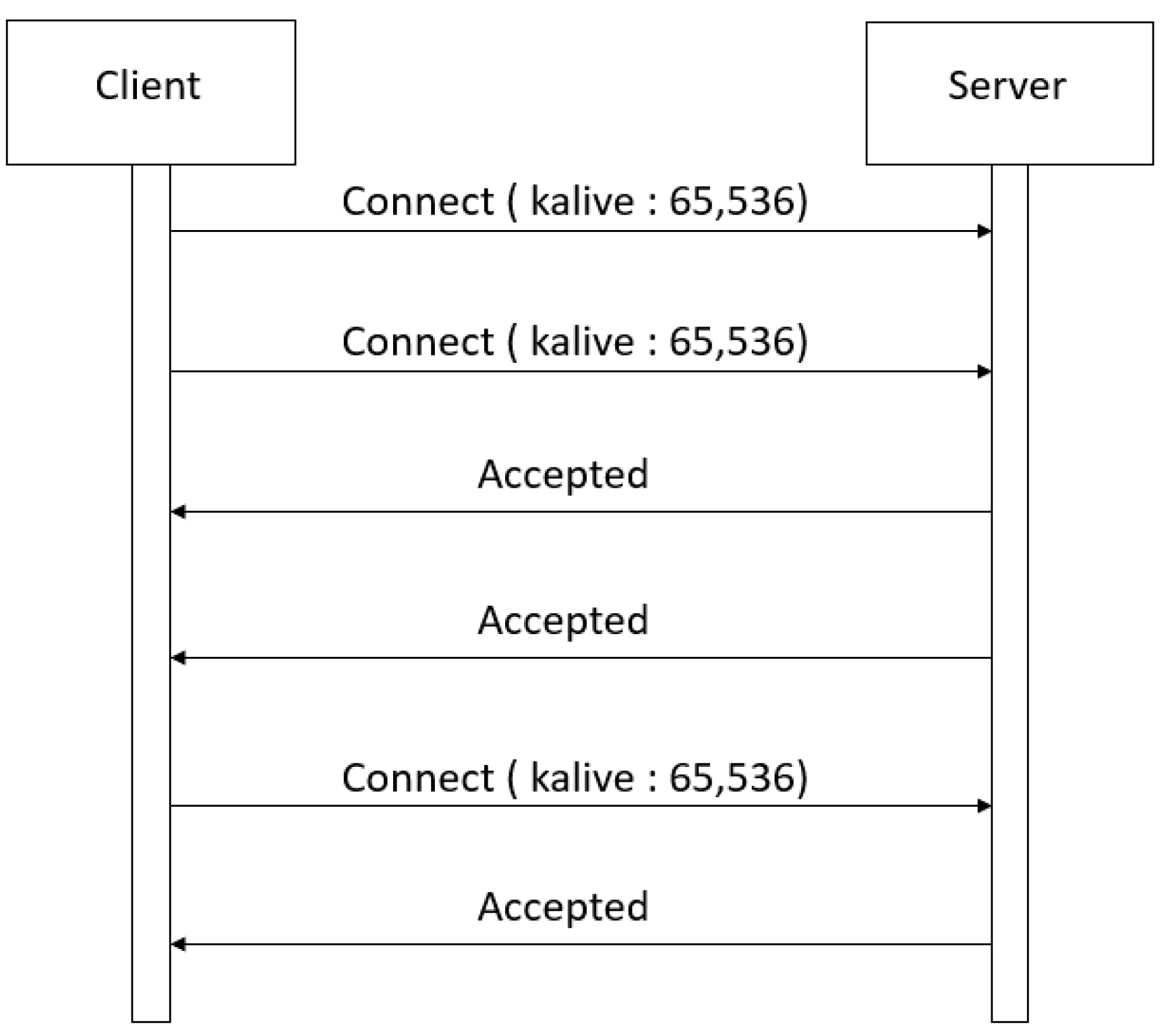
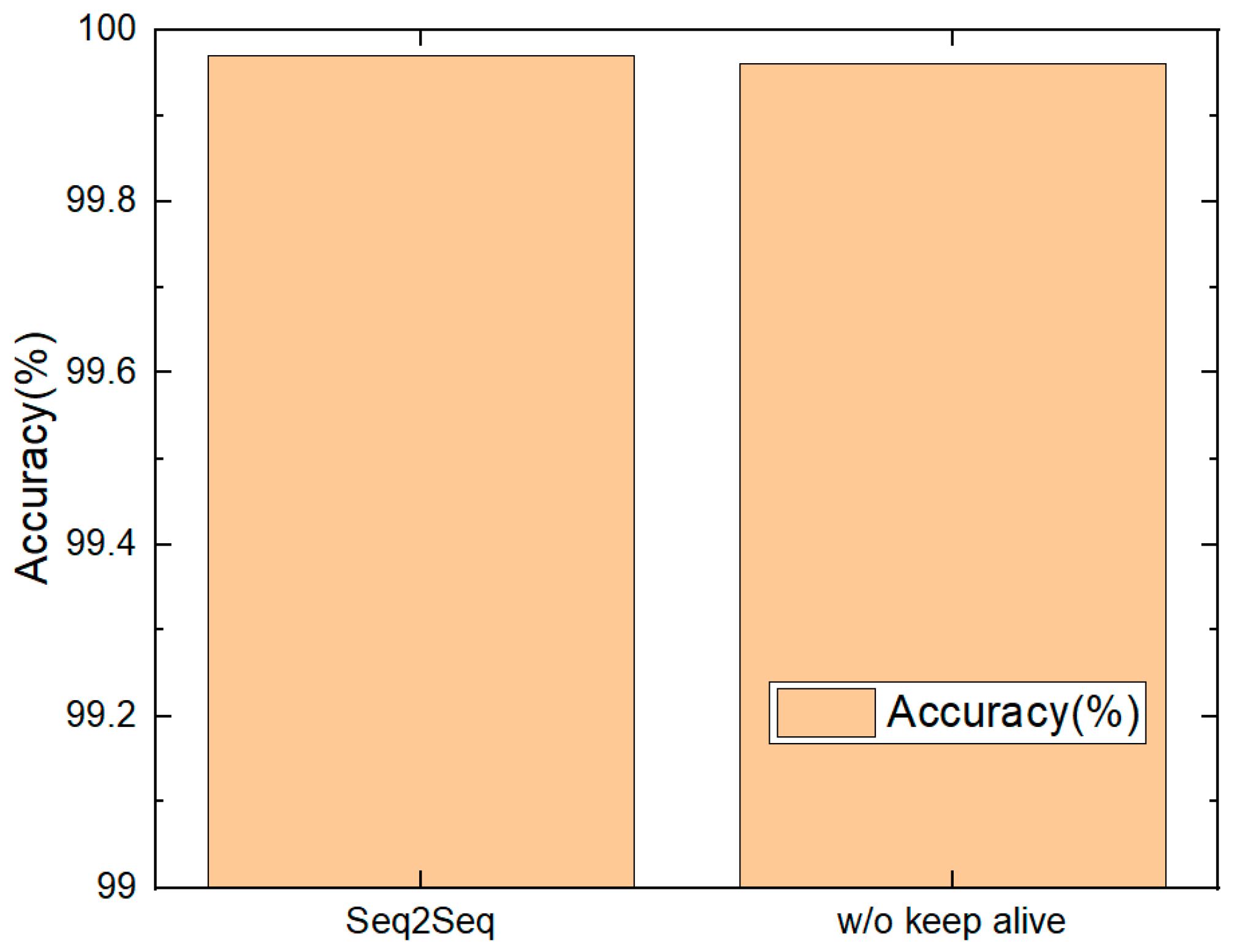
5.4. Keep Alive
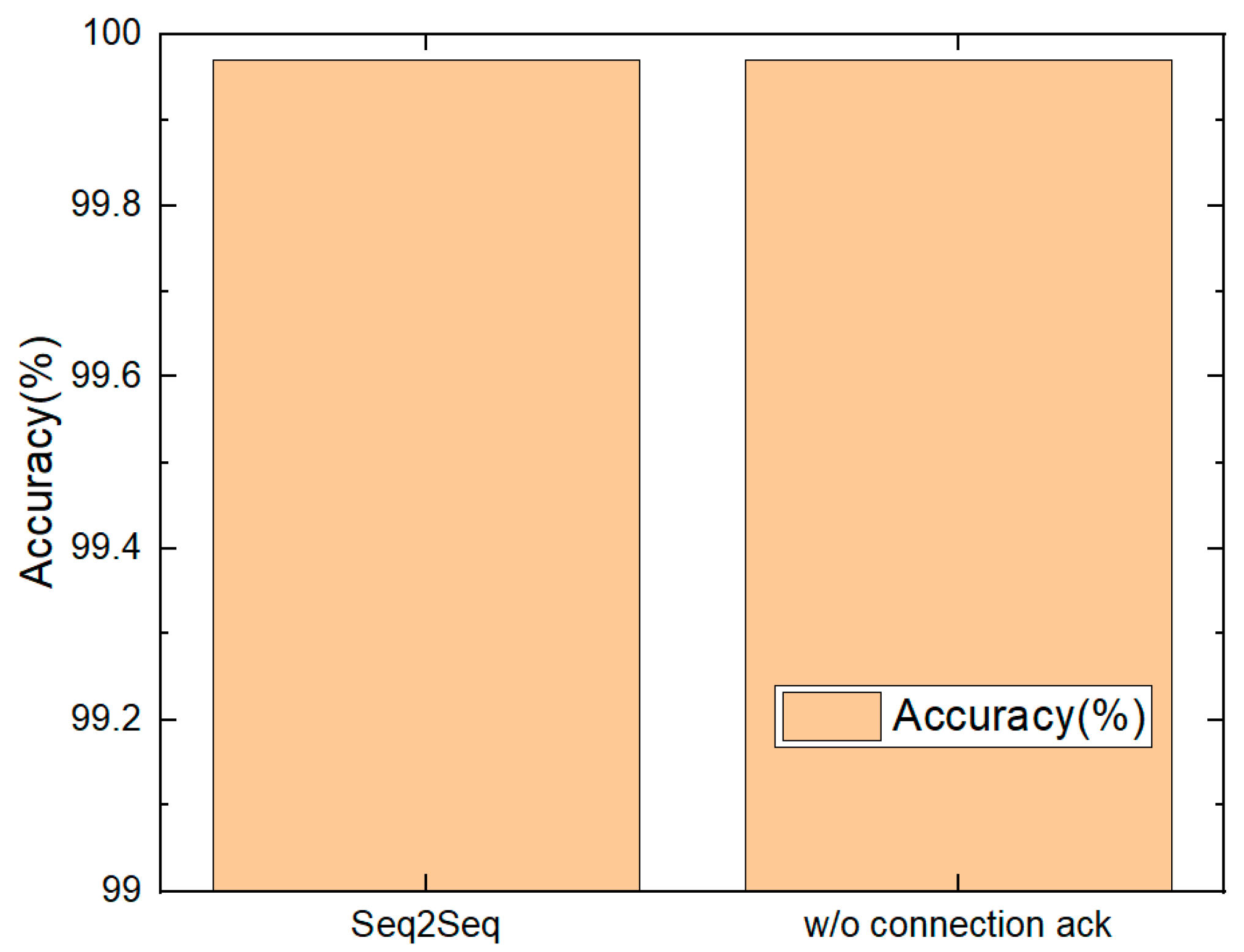
5.5. Con Ack
5.6. Preprocessing
{(1001, -1, 1, -1, -1), (1001, -1, 2, -1, 0), (1001, -1, 3, -1, -1), (1001, -1, 12, -1, -1), (1001, -1, 13, -1, -1), (1001, -1, 3, -1, -1),...}
{(1001, -1, 1, -1, -1), (1002, -1, 1, -1, -1), (1003, -1, 1, -1, -1),..., (1001, -1, 2, -1, 0), (1002, -1, 2, -1, 0),...}
{(1001, -1, 1, -1, -1), (1001, -1, 2, -1, 0), (1001, 1000, 3, -1, -1), (1001, 1000, 3, -1, -1), (1001, 1000, 3, -1, -1),...}
{(1001, -1, 1, 10,000, -1), (1002, -1, 1, 10,000, -1), (1001, -1, 2, -1, 0), (1002, -1, 2, -1, 0), (1003, -1, 1, 10,000, -1), (1003, -1, 2, -1, 0),...}
{(1001, -1, 1, -1, -1), (1001, -1, 2, -1, 0), (1001, -1, 8, -1, -1), (1001, -1, 9, -1, -1),..., (1001, -1, 3, -1, -1), (1001, -1, 3, -1, -1),...}
{(1001, -1, 1, -1, -1), (1001, -1, 2, -1, 5), (1002, -1, 1, -1, -1), (1002, -1, 2, -1, 5), (1003, -1, 1, -1, -1), (1004, -1, 2, -1, 5),...}
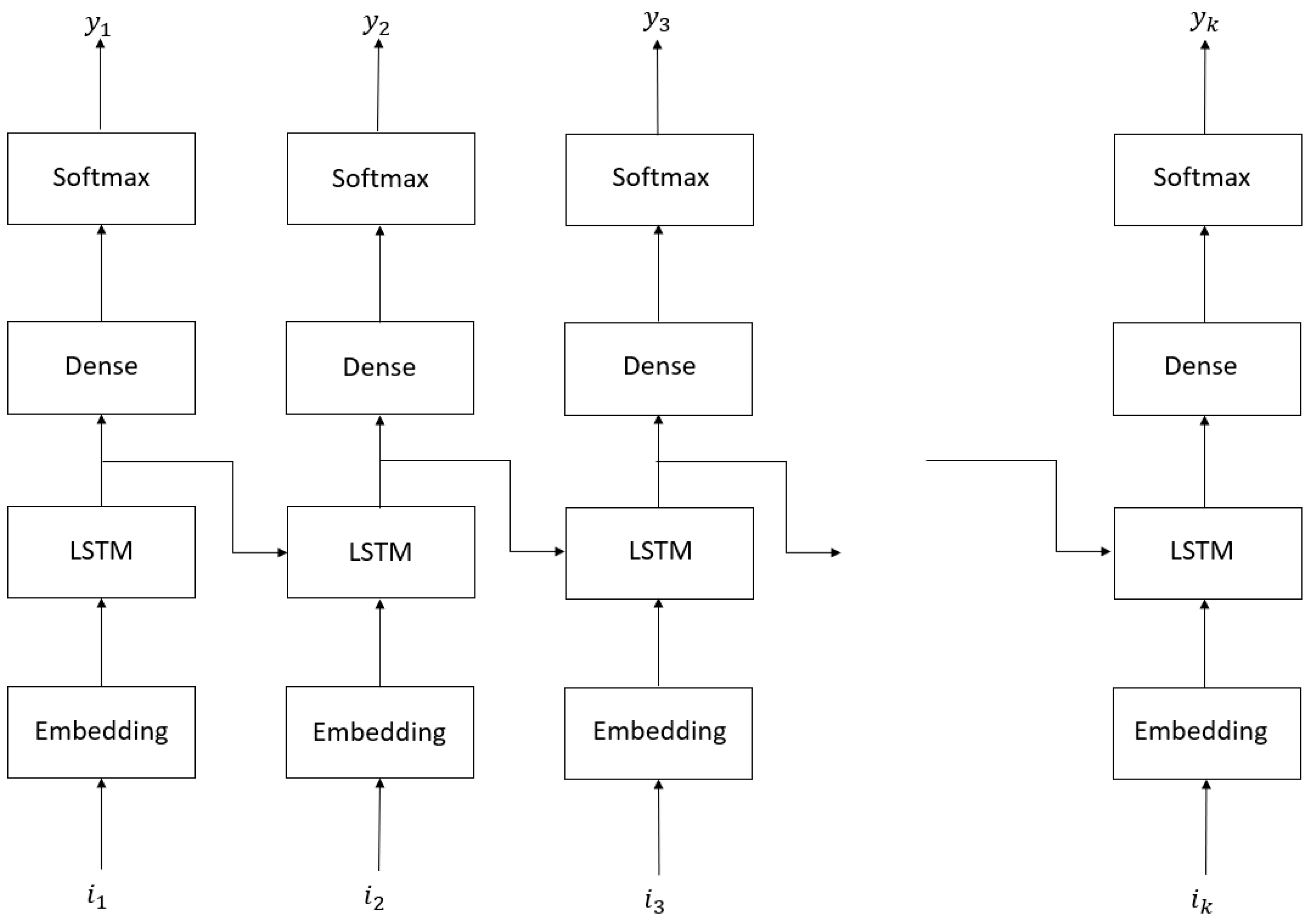
6. Seq2Seq Model for Detection of Malicious MQTT Traffic
7. Experimental Results
7.1. Setup
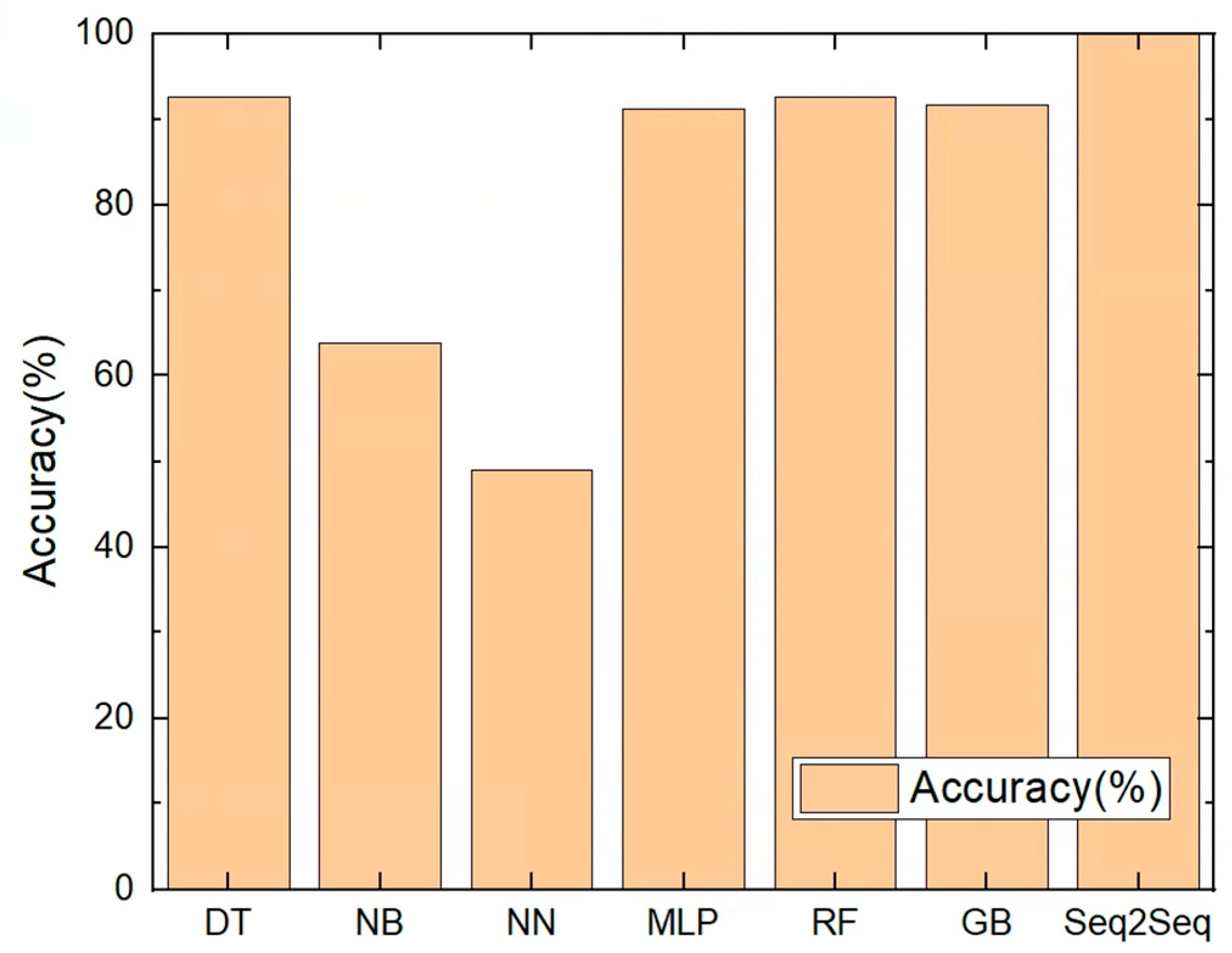
7.2. Accuracy
7.3. Analysis
8. Discussion
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Electricity AMI. Available online: http://www.aitimes.com/news/articleView.html?idxno=141421 (accessed on 8 November 2022).
- Gas AMI. Available online: http://www.gasnews.com/news/articleView.html?idxno=104555 (accessed on 8 November 2022).
- Water AMI. Available online: https://www.boannews.com/media/view.asp?idx=85538 (accessed on 8 November 2022).
- IoT Malware Statistics. Available online: https://blog.sonicwall.com/en-us/2019/10/sonicwall-encrypted-attacks-iot-malware-surge-as-global-malware-volume-dips/ (accessed on 8 November 2022).
- Vaccari, I.; Aiello, M.; Cambiaso, E. SlowITe, a Novel Denial of Service Attack Affecting MQTT. Sensors 2020, 20, 2932. [Google Scholar] [CrossRef]
- Vaccari, I.; Chiola, G.; Aiello, M.; Mongelli, M.; Cambiaso, E. MQTTset, a New Dataset for Machine Learning Techniques on MQTT. Sensors 2020, 20, 6578. [Google Scholar] [CrossRef] [PubMed]
- Tshark. Available online: https://tshark.dev (accessed on 8 November 2022).
- Hya, S.; Oriol, V.; Quoc, V.L. Sequence to Sequence Learning with Neural Networks. In Proceedings of the NDSS, San Diego, CA, USA, 23–26 February 2014. [Google Scholar]
- Antivirus Software. Available online: https://en.wikipedia.org/wiki/Antivirus_software (accessed on 8 November 2022).
- Intrusion Detection System. Available online: https://en.wikipedia.org/wiki/Intrusion_detection_system (accessed on 9 November 2022).
- Gibert, D. Convolutional Neural Networks for Malware Classification. Master’s Thesis, Universitat de Barcelona, Barcelona, Spain, 2016. [Google Scholar]
- Choi, S.; Bae, J.; Lee, C.; Kim, Y.; Kim, J. Attention-Based Automated Feature Extraction for Malware Analysis. Sensors 2020, 20, 2893. [Google Scholar] [CrossRef] [PubMed]
- Šrndic, N.; Laskov, P. Detection of Malicious PDF files Based on Hierarchical Document Structure. In Proceedings of the NDSS, San Diego, CA, USA, 26 February–1 March 2017. [Google Scholar]
- Choi, S. Malicious Powershell Detection Using Graph Convolution Network. Appl. Sci. 2021, 11, 6429. [Google Scholar] [CrossRef]
- Naseer, S.; Saleem, Y.; Khalid, S.; Bashir, M.K.; Han, J.; Iqbal, M.M.; Han, K. Enhanced Network Anomaly Detection Based on Deep Neural Networks. IEEE Access 2018, 6, 48231–48246. [Google Scholar] [CrossRef]
- Zhang, B.-C.; Hu, G.-Y.; Zhou, Z.-J.; Zhang, Y.-M.; Qiao, P.-L.; Chang, L.-L. Network Intrusion Detection Based on Directed Acyclic Graph and Belief Rule Base. ETRI J. 2017, 39, 592–604. [Google Scholar] [CrossRef]
- Wang, W.; Sheng, Y.; Wang, J.; Zeng, X.; Ye, X.; Huang, Y.; Zhu, M. HAST-IDS: Learning Hierarchical Spatial-Temporal Features Using Deep Neural Networks to Improve Intrusion Detection. IEEE Access 2017, 6, 1792–1806. [Google Scholar] [CrossRef]
- Nagarajan, S.M.; Deverajan, G.G.; Bashir, A.K.; Mahapatra, R.P.; Al-Numay, M.S. IADF-CPS: Intelligent Anomaly Detection Framework towards Cyber Physical Systems. Comput. Commun. 2022, 188, 81–89. [Google Scholar] [CrossRef]
- Gopal, D.G.; Saravanan, R. Selfish node detection based on evidence by trust authority and selfish replica allocation in DANET. Int. J. Inf. Commun. Technol. 2016, 9, 473–491. [Google Scholar] [CrossRef]
- Nagarajan, S.M.; Deverajan, G.G.; Kumaran, U.; Thirunavukkarasan, M.; Alshehri, M.D.; Alkhalaf, S. Secure Data Transmission in Internet of Medical Things Using RES-256 Algorithm. IEEE Trans. Ind. Inform. 2021, 18, 8876–8884. [Google Scholar] [CrossRef]
- MQTT. Available online: https://mqtt.org (accessed on 8 November 2022).
- Koroniotis, N.; Moustafa, N.; Sitnikova, E.; Turnbull, B. Towards the development of realistic botnet dataset in the Internet of Things for network forensic analytics: Bot-IoT dataset. Future Gener. Comput. Syst. 2019, 100, 779–796. [Google Scholar] [CrossRef]
- Ghazanfar, S.; Hussain, F.; Rehman, A.U.; Fayyaz, U.U.; Shahzad, F.; Shah, G.A. IoT-Flock: An Open-source Framework for IoT Traffic Generation. In Proceedings of the International Conference on Emerging Trends in Smart Technologies, Karachi, Pakistan, 26–27 March 2020. [Google Scholar]
- Palmieri, A.; Prem, P.; Ranise, S.; Morelli, U.; Ahmad, T. MQTTSA: A Tool for Automatically Assisting the Secure Deployments of MQTT Brokers. IEEE World Congr. Serv. 2019, 2642, 47–53. [Google Scholar]
- Keras. Available online: https://keras.io (accessed on 8 November 2022).
- Random Forest. Available online: https://scikit-learn.org/stable/modules/generated/sklearn.ensemble.RandomForestClassifier.html (accessed on 8 November 2022).
- Choi, S. Malicious PowerShell Detection Using Attention against Adversarial Attacks. Electronics 2020, 9, 1817. [Google Scholar] [CrossRef]
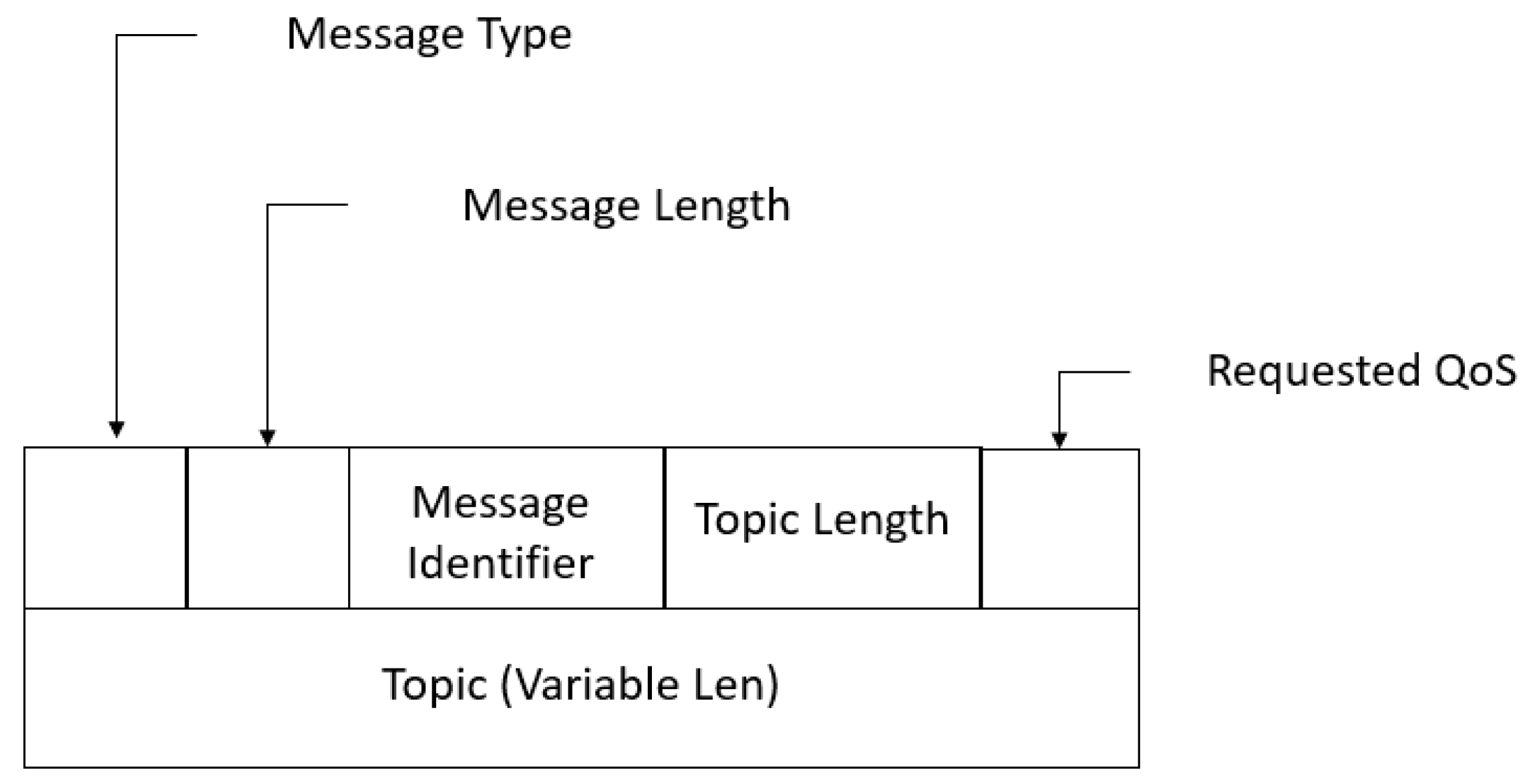
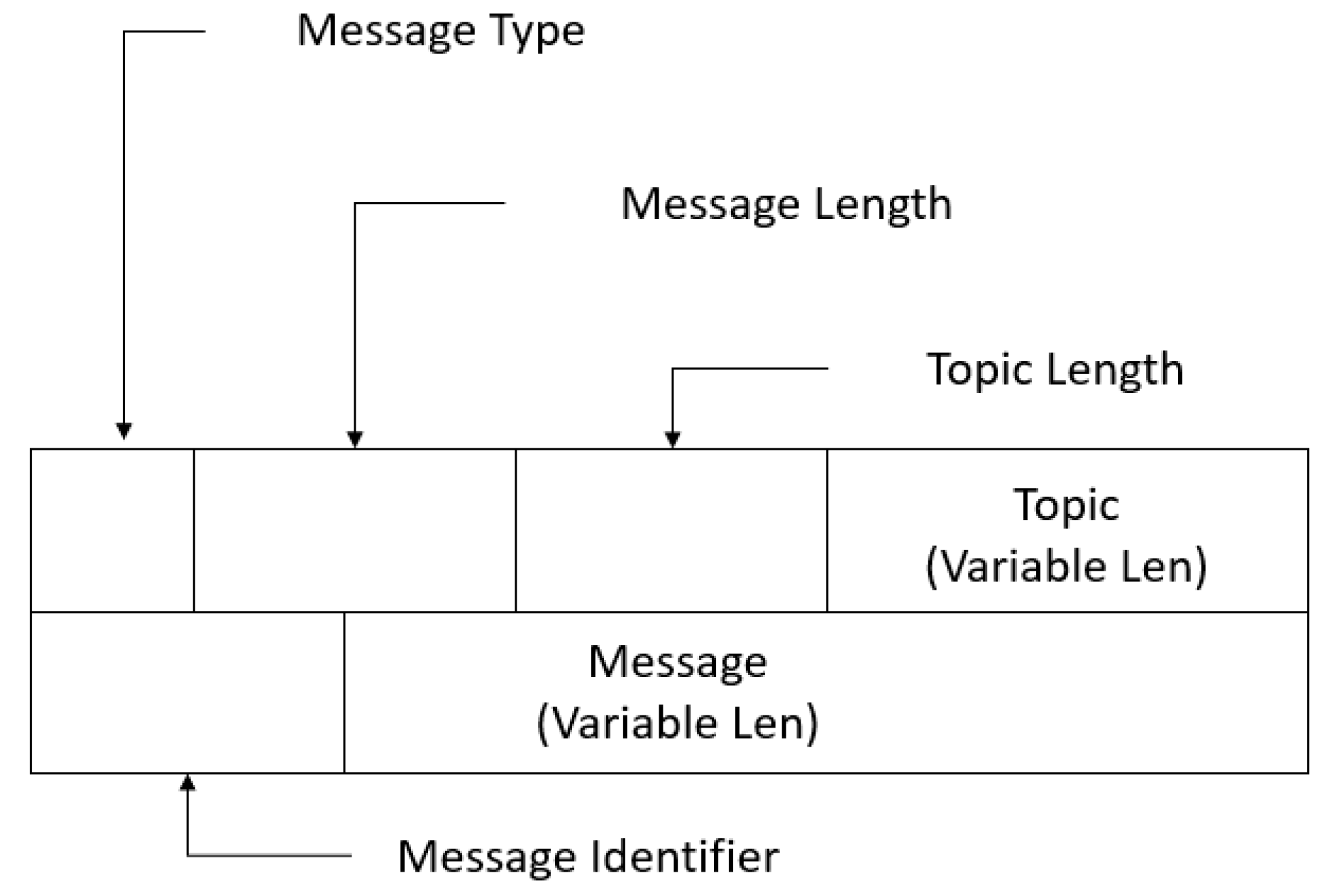
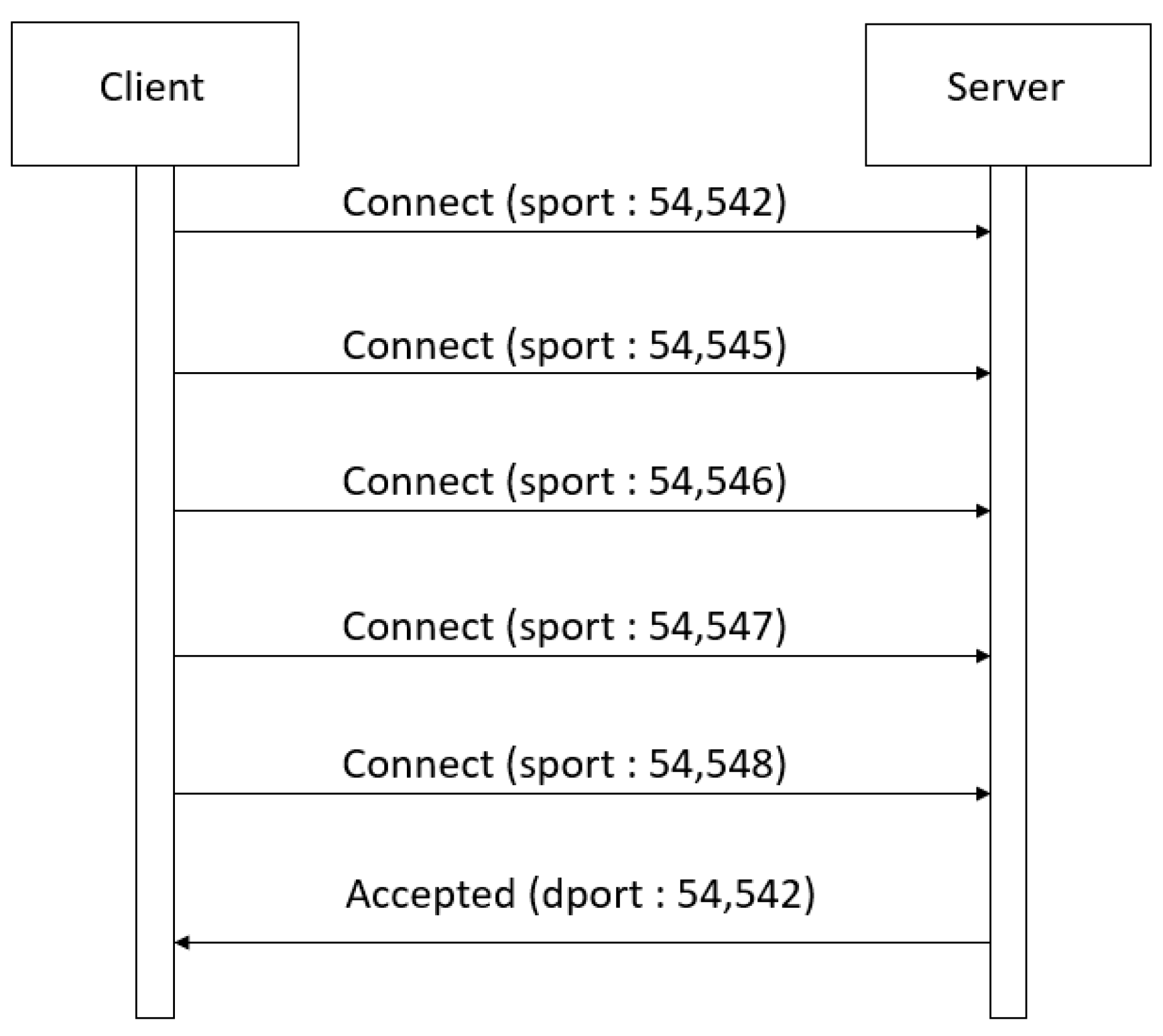
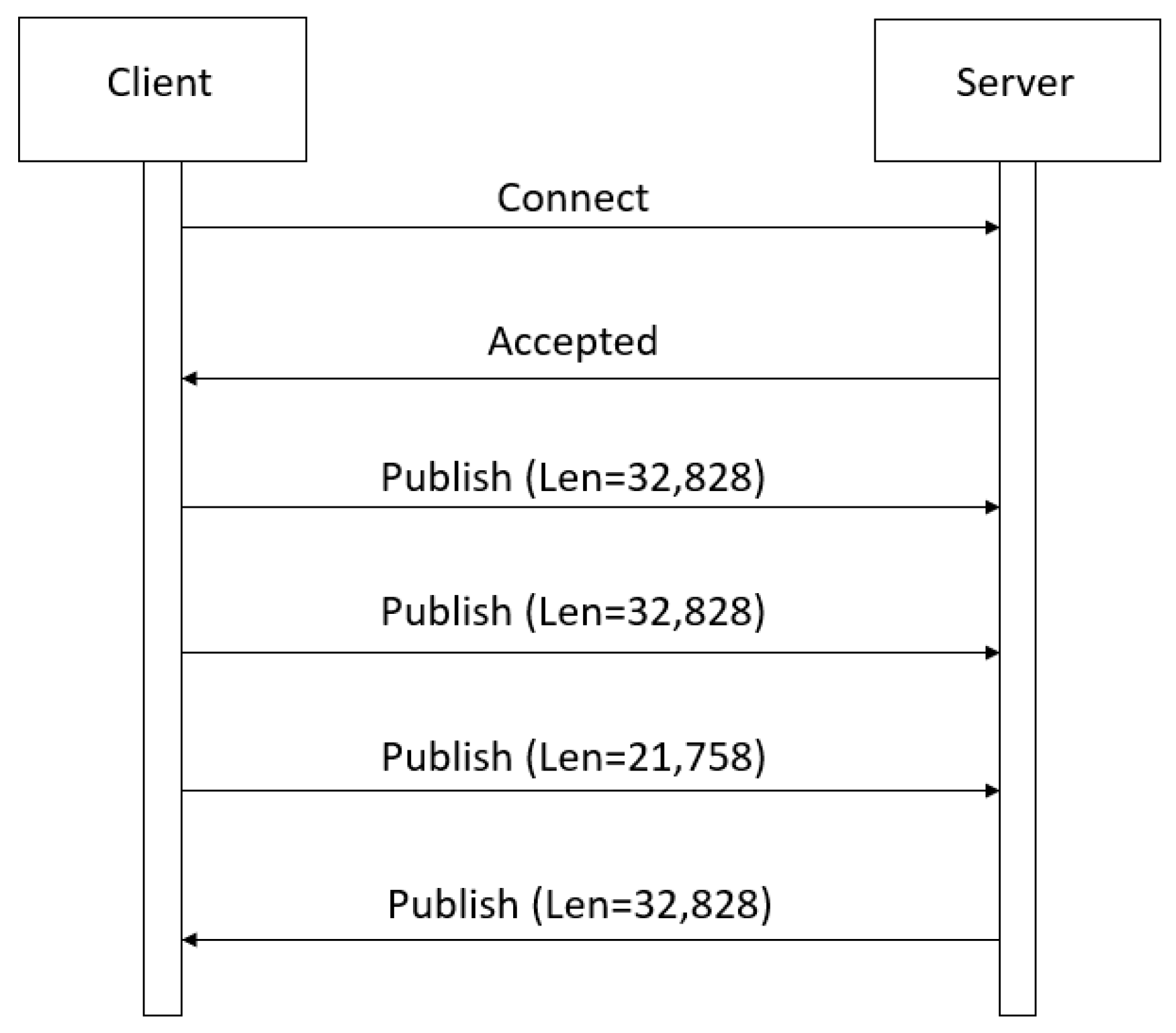
| Type | Value | Direction | Description |
|---|---|---|---|
| Reserved | 0 | - | - |
| CONNECT | 1 | C -> S | Connection Req |
| CONACK | 2 | S -> C | Ack for Req |
| PUBLISH | 3 | C <-> S | Publish |
| PUBACK | 4 | C <-> S | ACK (QoS 1) |
| PUBREC | 5 | C <-> S | QoS 2 |
| PUBREL | 6 | C <-> S | QoS 2 |
| PUBCOMP | 7 | C <-> S | QoS 2 |
| SUBSCRIBE | 8 | C -> S | Subscribe |
| SUBACK | 9 | S -> C | Ack for Sub |
| UNSUBSCRIBE | 10 | C -> S | Unsubscribe |
| UNSUBACK | 11 | S -> C | Ack for Unsub |
| PINGREQ | 12 | C -> S | Ping Req |
| PINGRESP | 13 | S -> C | Ack for Ping |
| DISCONNECT | 14 | C -> S | Disconnect |
| Reserved | 15 | - | - |
| Source Port Index | TCP Length | Message Type | Keep Alive | Connection Ack | |
|---|---|---|---|---|---|
| DoS Attack | O | - | - | - | - |
| Flood Attack | - | O | O | - | - |
| SlowITe Attack | - | - | - | O | - |
| Malformed Attack | - | - | O | - | - |
| Brute-force Attack | O | - | - | - | O |
| Attack | File Name | Number of Packets |
|---|---|---|
| Normal | capture_1w_mqtt_1800s.pcap | 22,360 |
| DoS | capture_malariaDoS_mqtt.pcap | 93,317 |
| Flood | capture_flood_mqtt.pcap | 303 |
| SlowITe | slowite_mqtt.pcap | 3048 |
| Malformed | malformed_mqtt.pcap | 3656 |
| Brute force | Brute-force_mqtt.pcap | 2921 |
| Predicted | |||||||
|---|---|---|---|---|---|---|---|
| Normal | BF | DoS | Flood | SlowITe | Malformed | ||
| Actual | Normal | 4419 | - | - | - | - | - |
| BF | - | 606 | - | - | - | - | |
| DoS | - | - | 18,653 | - | - | - | |
| Flood | - | - | - | 62 | - | - | |
| SlowITe | - | - | - | - | 408 | - | |
| Malformed | 1 | - | 4 | - | - | 735 | |
| Predicted | |||||||
|---|---|---|---|---|---|---|---|
| Normal | BF | DoS | Flood | SlowITe | Malformed | ||
| Actual | Normal | 4419 | - | - | - | - | - |
| BF | 10 | 588 | - | - | - | - | |
| DoS | 12 | 3 | 18,637 | - | - | 1 | |
| Flood | - | - | 9 | 53 | - | - | |
| SlowITe | - | - | - | - | 408 | - | |
| Malformed | 7 | - | 7 | - | - | 726 | |
| Predicted | |||||||
|---|---|---|---|---|---|---|---|
| Normal | BF | DoS | Flood | SlowITe | Malformed | ||
| Actual | Normal | 4419 | - | - | - | - | - |
| BF | - | 606 | - | - | - | - | |
| DoS | - | - | 18,653 | - | - | - | |
| Flood | 62 | - | - | - | - | - | |
| SlowITe | - | - | - | - | 408 | - | |
| Malformed | 2 | - | 2 | - | 1 | 735 | |
| Predicted | |||||||
|---|---|---|---|---|---|---|---|
| Normal | BF | DoS | Flood | SlowITe | Malformed | ||
| Actual | Normal | 4419 | - | - | - | - | - |
| BF | - | 606 | - | - | - | - | |
| DoS | - | - | 18,652 | - | - | 1 | |
| Flood | - | - | - | 62 | - | - | |
| SlowITe | - | - | - | - | 408 | - | |
| Malformed | 1 | - | 13 | - | 2 | 724 | |
| Predicted | |||||||
|---|---|---|---|---|---|---|---|
| Normal | BF | DoS | Flood | SlowITe | Malformed | ||
| Actual | Normal | 4419 | - | - | - | - | - |
| BF | - | 606 | - | - | - | - | |
| DoS | - | - | 18,650 | - | 3 | - | |
| Flood | - | - | - | 62 | - | - | |
| SlowITe | - | - | - | - | 408 | - | |
| Malformed | 1 | - | 1 | - | 2 | 736 | |
| Predicted | |||||||
|---|---|---|---|---|---|---|---|
| Normal | BF | DoS | Flood | SlowITe | Malformed | ||
| Actual | Normal | 4419 | - | - | - | - | - |
| BF | - | 606 | - | - | - | - | |
| DoS | - | 1 | 18,652 | - | - | - | |
| Flood | 1 | - | - | 61 | - | - | |
| SlowITe | - | - | - | - | 407 | 1 | |
| Malformed | 1 | 1 | - | - | - | 738 | |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Choi, S.; Cho, J. Novel Feature Extraction Method for Detecting Malicious MQTT Traffic Using Seq2Seq. Appl. Sci. 2022, 12, 12306. https://doi.org/10.3390/app122312306
Choi S, Cho J. Novel Feature Extraction Method for Detecting Malicious MQTT Traffic Using Seq2Seq. Applied Sciences. 2022; 12(23):12306. https://doi.org/10.3390/app122312306
Chicago/Turabian StyleChoi, Sunoh, and Jaehyuk Cho. 2022. "Novel Feature Extraction Method for Detecting Malicious MQTT Traffic Using Seq2Seq" Applied Sciences 12, no. 23: 12306. https://doi.org/10.3390/app122312306
APA StyleChoi, S., & Cho, J. (2022). Novel Feature Extraction Method for Detecting Malicious MQTT Traffic Using Seq2Seq. Applied Sciences, 12(23), 12306. https://doi.org/10.3390/app122312306





