Cloud-Assisted Privacy Protection Energy Trading Based on IBS and Homomorphic Encryption in IIoT
Abstract
:1. Introduction
- We propose a uniform energy trading framework built on the blockchain in light of the IIoT energy trade scenarios now in use. This design reduces duplicate data transmitted to the blockchain and increases transaction efficiency by combining PCN-based off-chain transactions and cloud-assisted off-chain storage.
- Using IBS and Paillier homomorphic encryption, we propose a privacy protection mechanism and apply it to off-chain transactions on the blockchain, allowing transactions using pseudonyms to protect node identity privacy and transaction data information security.
- We have carried out simulation experiments, and the experimental results prove the effectiveness and feasibility of the scheme.
2. Related Work
2.1. Blockchain-Based Energy Trading Systems
2.2. Privacy Protection of Blockchain Transaction Data
3. Preliminary Knowledge
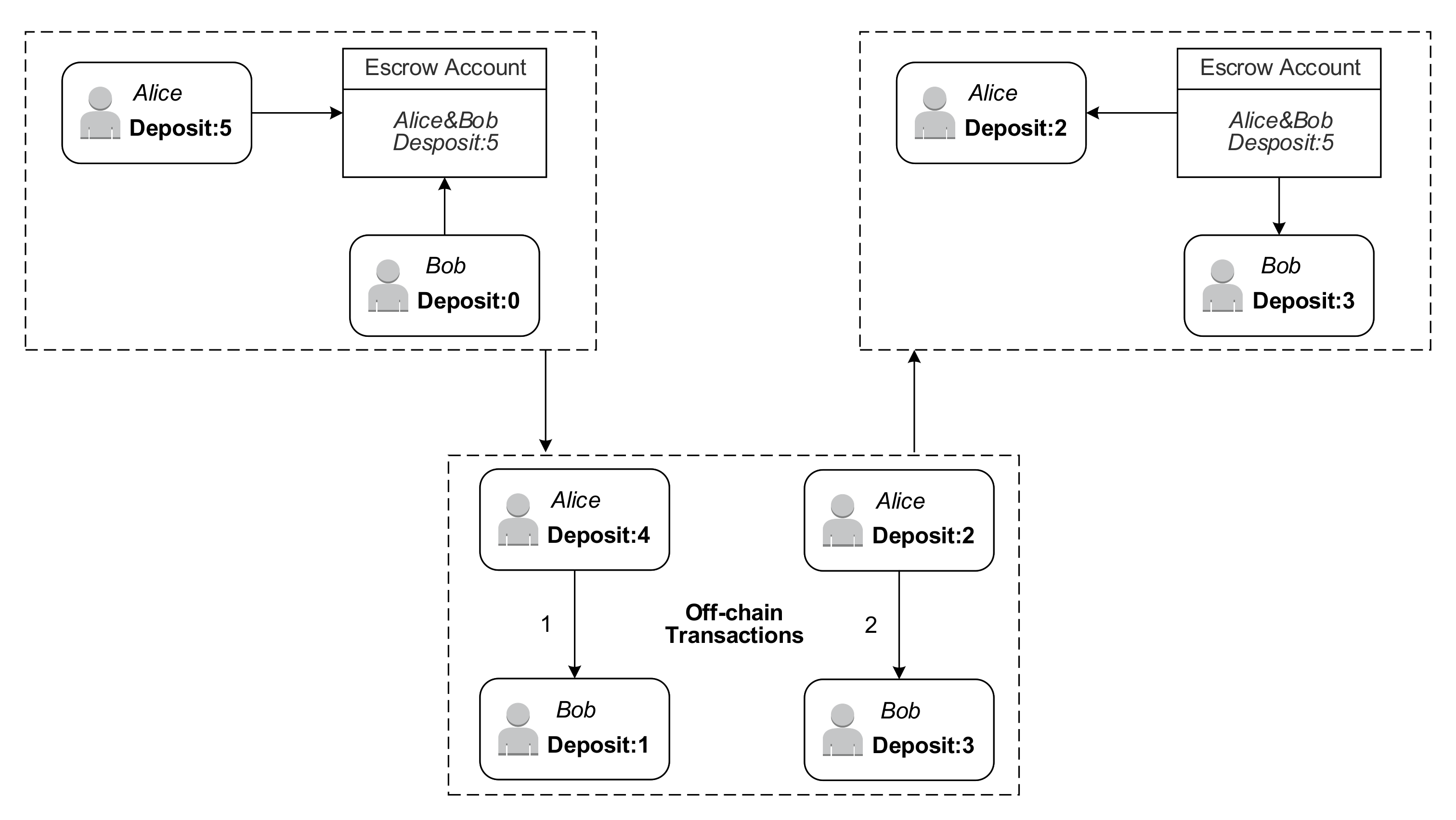
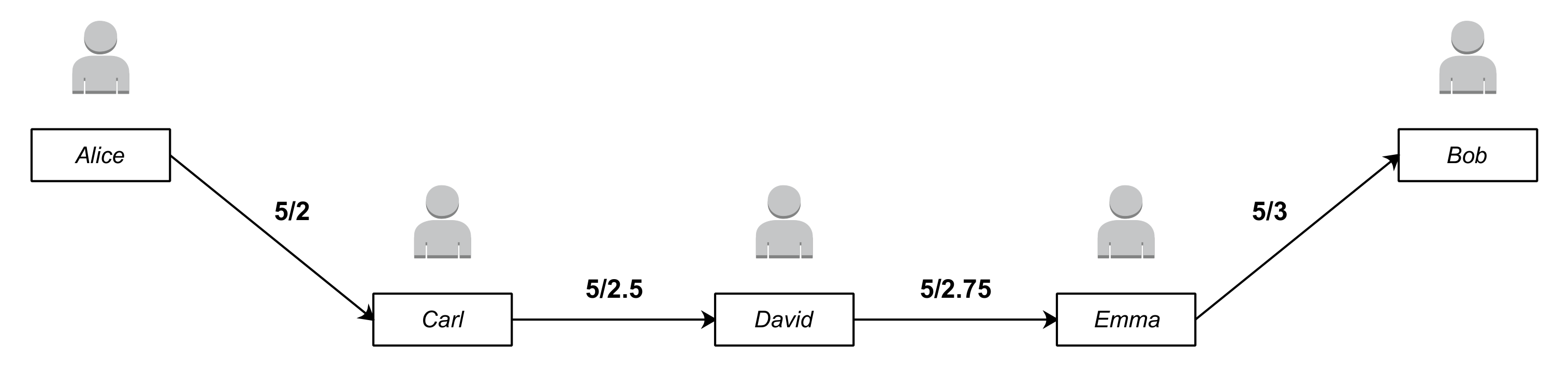
3.1. Payment Channel Network
3.2. Identity-Based Signature
- System master key establishment: KGC selects a random number as the main private key and calculates the element in as the main public key and KGC keeps s and discloses ;
- User key generation: assuming the identity identifier of the user is , KGC calculates on the finite field F.If is 0, it is necessary to recalculate the master private key and update all users’ private keys. If is not equal to 0, calculate :The user’s private key is . The user’s public key isSo far, the key pair of the user is ;
- Signature generation: assuming there is a message M, the signer calculates , selects the random number , calculates , then calculates , , and finally calculates .The signer’s signature value for the message can be obtained.
- Signature verification: assuming the message received by the verifier and its signature are and , respectively, the verifier first verifies whether both and are correct. If one of them is not correct, the verification fails. Otherwise, P, u, and are calculated.Finally, is calculated and compared with . If it is consistent, the verification passes [30].During the above calculation, N is the order of elliptic curve used by the SM9 digital signature algorithm. , are the generators of the N-order cyclic subgroup and . is the signature private key generation function identifier. and are hash functions.
3.3. Paillier Homomorphic Encryption
- Key generation: arbitrarily select large prime numbers p, q, and calculate and ; If an integer is arbitrarily selected and is satisfied, and are the public key and private key, respectivelythe public key is and the private key is .
- Encryption: arbitrarily select , and for plaintext , the encrypted ciphertext .
- Decrypt: assuming the ciphertext is c, the decrypted ciphertext
- Additive homomorphism: for two plaintext and , Paillier homomorphic encryption operation is expressed as: . Following Paillier homomorphic encryption, the ciphertext is, accordingly, and , then and satisfy the following requirements:During the above calculation, is defined as the least common multiple of 2 parameters .
4. The Proposed Scheme
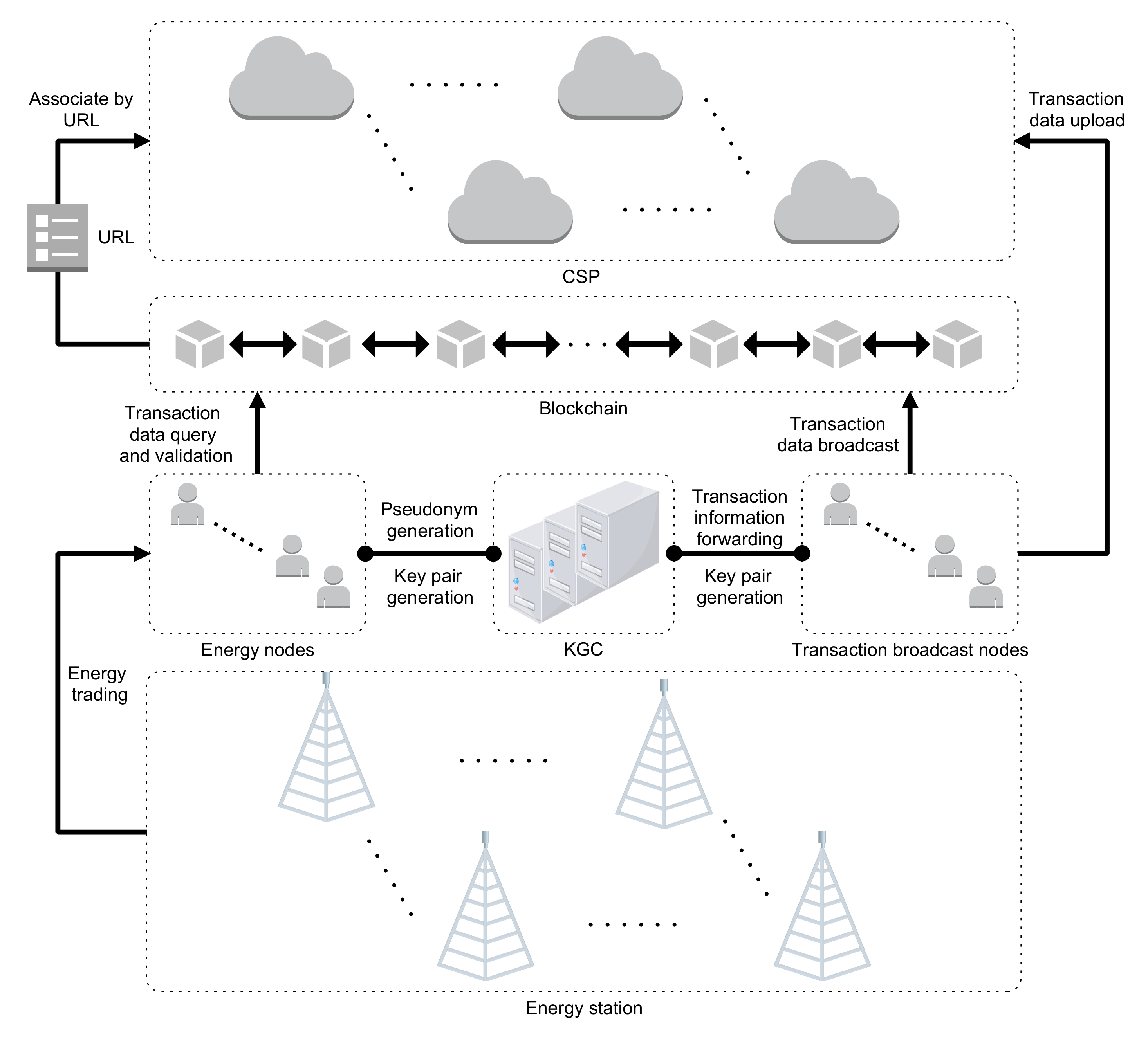
4.1. System Structure
- Energy nodes: the users can become energy nodes after registering, and the KGC then distributes the key pair. Energy nodes can engage in energy transactions to complete the blockchain’s point-to-point transaction information transfer procedure.
- Transaction broadcast nodes (TBN): as full nodes in the blockchain, they do not directly participate in transactions and are only responsible for broadcasting transaction information to other energy nodes.
- Energy station (ES): the energy station is accountable for powering energy nodes and has the authority to choose qualified participants in the energy trading system.
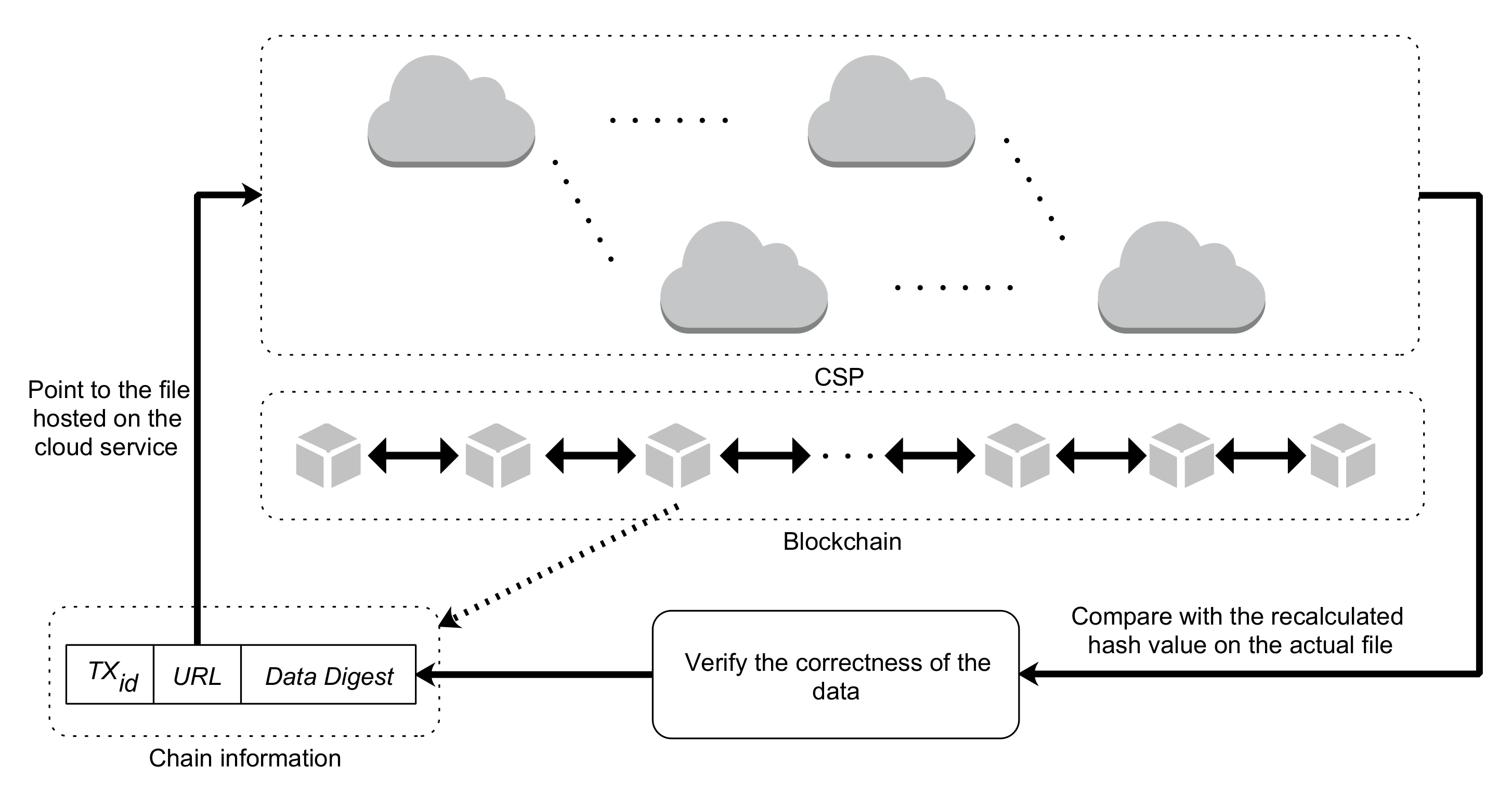
- Cloud service provider (CSP): stores complete transaction information to reduce data writing on the blockchain.
- Key generation center (KGC): for system nodes, the KGC serves as the authority for key generation and distribution. It also offers services for pseudonym generation, identity authentication, and transaction correctness checking.
4.2. Privacy-Preserved Security Energy Trading
4.2.1. Initialization
- If, for any link in the path , the initial balance of u0 is the sum of the payment amount and the accumulation of fees charged by all intermediate nodes,where and ’s transfer amount is shown by . denotes the amount of bitcoin that will eventually obtain. denotes the total transaction fee charged by intermediate nodes from to .
- The balance of any channel on the path should be no less than the total amount of the transfer fee and the fees charged for all subsequent links, which are expressed as a backward balance constraint:
- At the same time, the current channel balance should also be more than the balance after the total expenditure charged by all the intermediate nodes on the previous link, which is expressed as a forward balance constraint:
- The transfer fee on any path must be less than the available capacity of the current channel—that is, it needs to satisfy the following condition:
- The transfer needs to be completed within the HTLC tolerance on each channel in the path. is the HTLC tolerance, which means the maximum tolerance time of using the current channel.
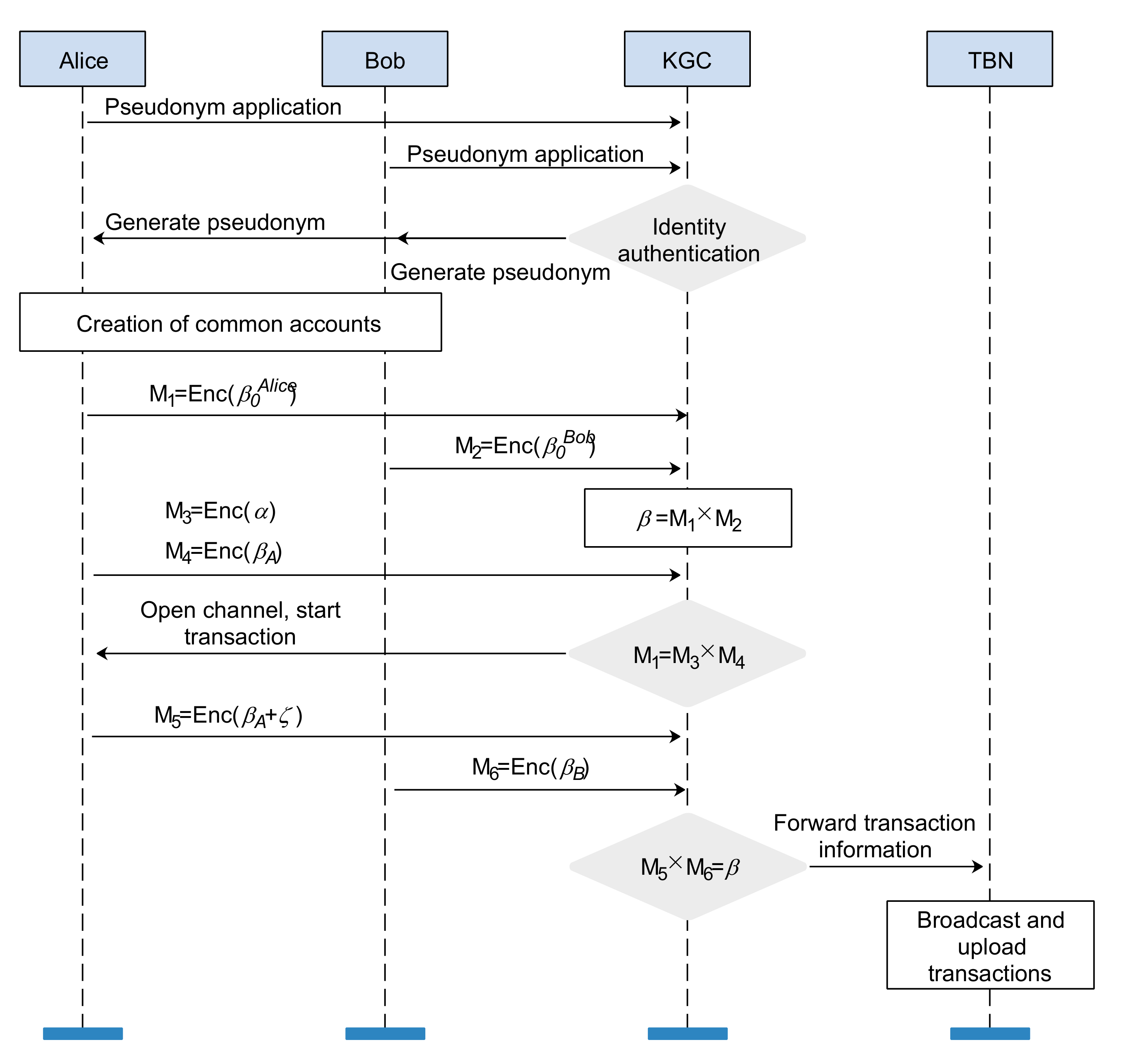
4.2.2. Pseudonym Generation
| Algorithm 1 Digital signature. |
|
| Algorithm 2 Signature verification. |
|
4.2.3. Open Channel
| Algorithm 3 HTLC. |
|
4.2.4. Transaction
| Algorithm 4 Transactions for intermediate nodes. |
|
| Algorithm 5 Process of contract completion. |
|
4.2.5. Close Channel
5. Performance Analysis
5.1. Safety Analysis
5.2. Anonymity Analysis
5.3. Traceability of Pseudonyms
5.4. Scheme Comparison
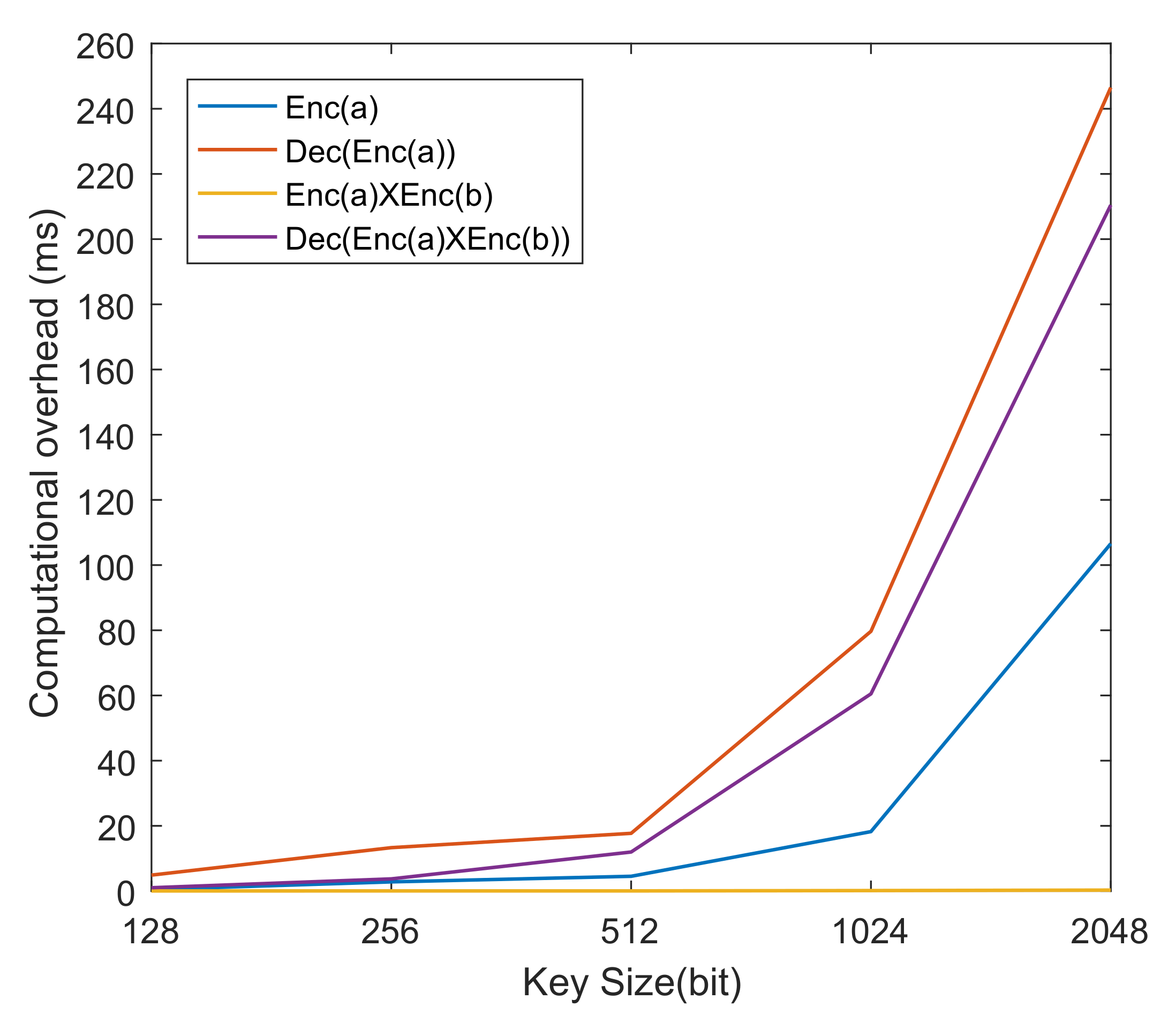
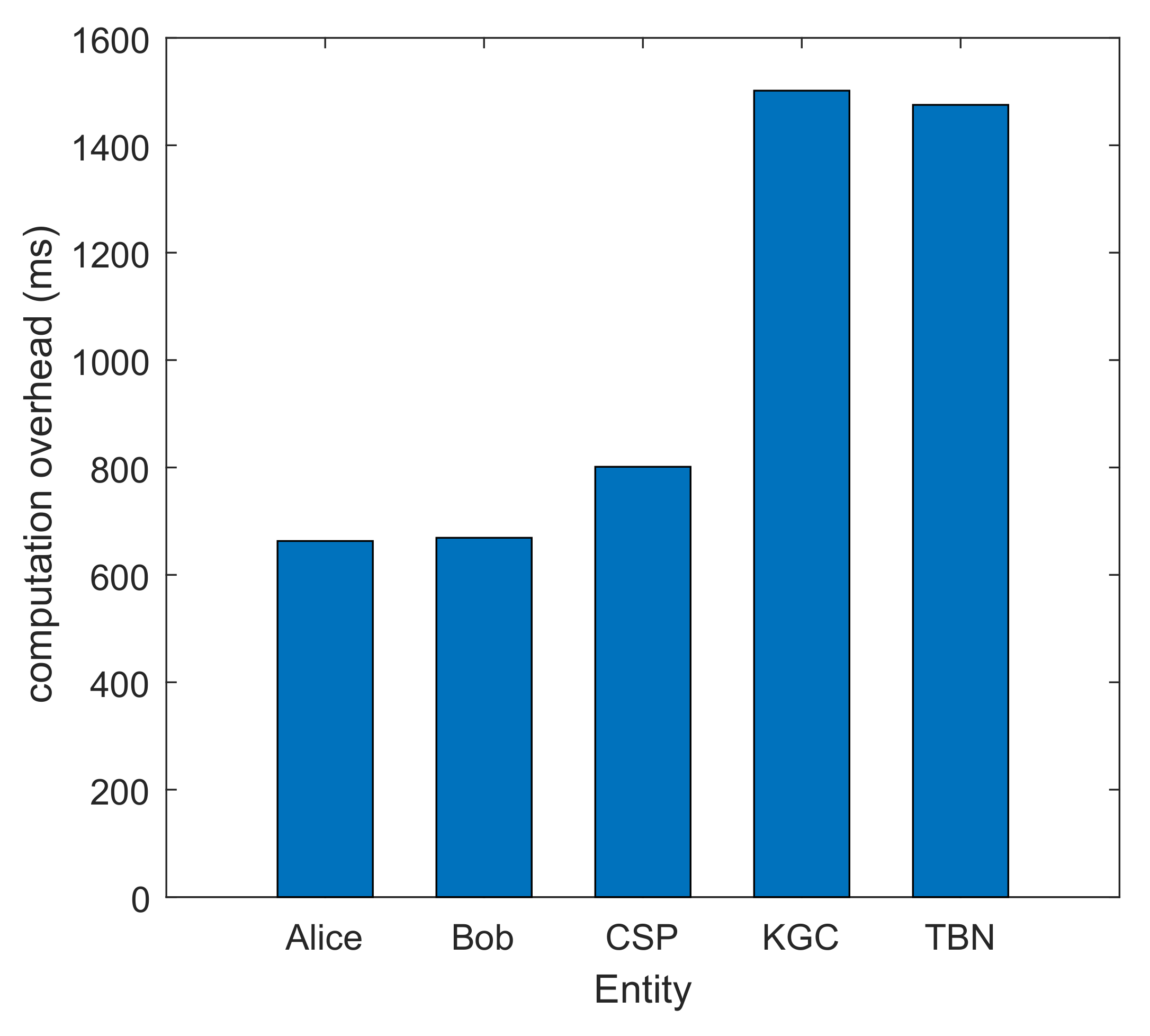
5.5. Computation Overhead
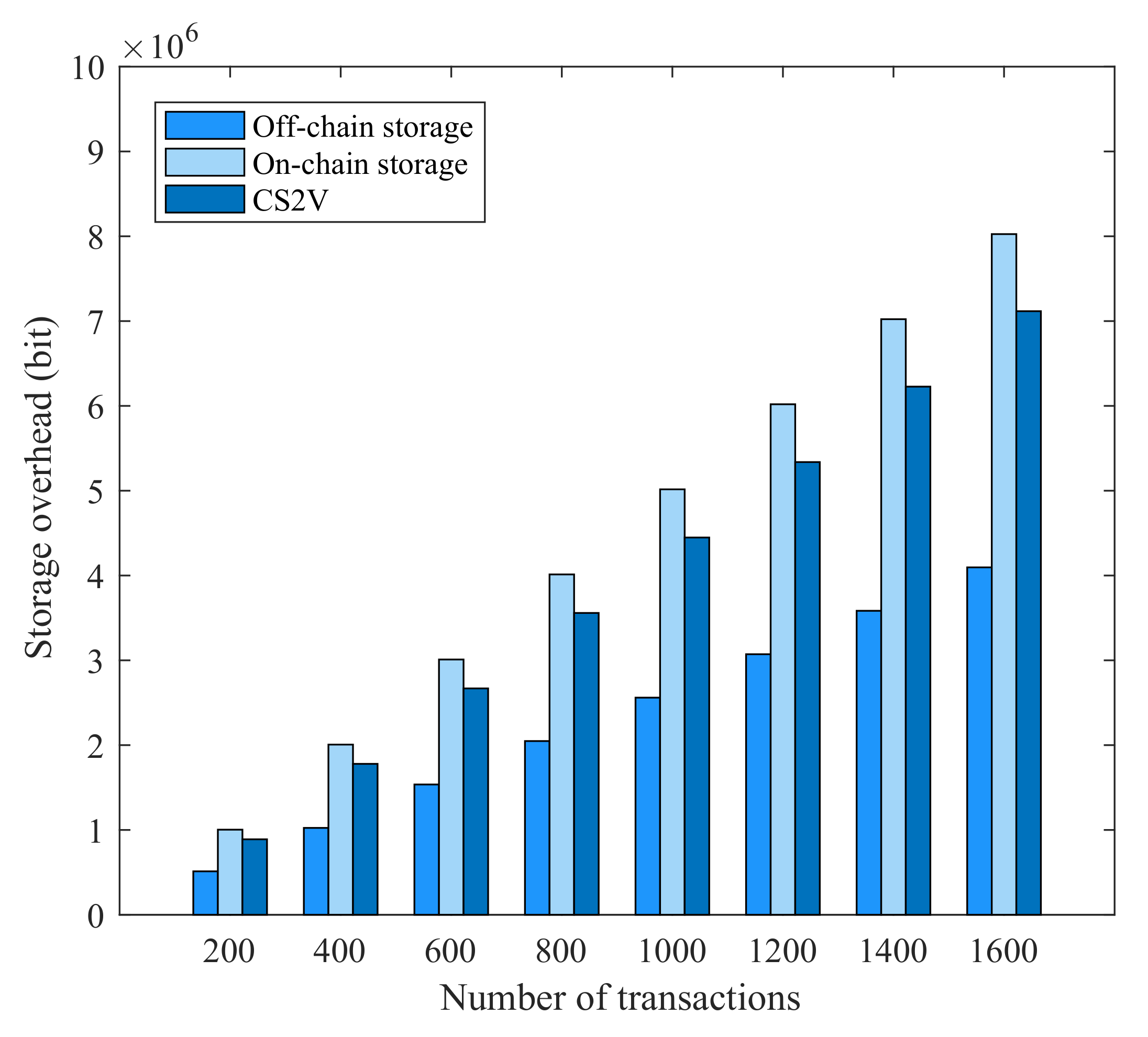
5.6. Communication Overhead and Storage Overhead
6. Discussion
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Li, M.; Hu, D.; Lal, C.; Conti, M.; Zhang, Z. Blockchain-Enabled Secure Energy Trading with Verifiable Fairness in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2020, 16, 6564–6574. [Google Scholar] [CrossRef]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2017, 14, 3690–3700. [Google Scholar] [CrossRef]
- Dong, Z.; Luo, F.; Liang, G. Blockchain: A secure, decentralized, trusted cyber infrastructure solution for future energy systems. J. Mod. Power Syst. Clean Energy 2018, 6, 958–967. [Google Scholar] [CrossRef]
- Guan, Z.; Lu, X.; Wang, N.; Wu, J.; Du, X.; Guizani, M. Towards secure and efficient energy trading in IIoT-enabled energy internet: A blockchain approach. Future Gener. Comput. Syst. 2020, 110, 686–695. [Google Scholar] [CrossRef]
- Chowdhury, M.J.M.; Usman, M.; Ferdous, M.S.; Chowdhury, N.; Harun, A.I.; Jannat, U.S.; Biswas, K. A cross-layer trust-based consensus protocol for peer-to-peer energy trading using fuzzy logic. IEEE Internet Things J. 2021, 9, 14779–14789. [Google Scholar] [CrossRef]
- Kim, M.; Lee, J.; Oh, J.; Park, K.; Park, Y. Blockchain based energy trading scheme for vehicle-to-vehicle using decentralized identifiers. Appl. Energy 2022, 9, 119445. [Google Scholar] [CrossRef]
- Huang, X.; Zhang, Y.; Li, D.; Han, L. A Solution for Bilayer Energy-Trading Management in Microgrids Using Multiblockchain. IEEE Internet Things J. 2022, 9, 13886–13900. [Google Scholar] [CrossRef]
- Baza, M.; Sherif, A.; Mahmoud, M.M.E.A.; Bakiras, S.; Alasmary, W.; Abdallah, M.; Lin, X. Privacy-Preserving Blockchain-Based Energy Trading Schemes for Electric Vehicles. IEEE Trans. Veh. Technol. 2021, 70, 9369–9384. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M. Privacy-Preserving Energy Trading Using Consortium Blockchain in Smart Grid. IEEE Trans. Ind. Inform. 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Yahaya, A.S.; Javaid, N.; Almogren, A.; Ahmed, A.; Gulfam, S.M.; Radwan, A. A Two-Stage Privacy Preservation and Secure Peer-to-Peer Energy Trading Model Using Blockchain and Cloud-Based Aggregator. IEEE Access 2021, 9, 143121–143137. [Google Scholar] [CrossRef]
- Zhang, Y.; Yang, D.; Xue, G. CheaPay: An Optimal Algorithm for Fee Minimization in Blockchain-Based Payment Channel Networks. In Proceedings of the 2019 IEEE International Conference on Communications (ICC), Shanghai, China, 20–24 May 2019; pp. 1–6. [Google Scholar]
- Cavoukian, A.; Polonetsky, J.; Wolf, C. Smartprivacy for the smart grid: Embedding privacy into the design of electricity conservation. Identity Inf. Soc. 2010, 3, 275–294. [Google Scholar]
- Poon, J.; Dryja, T. The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments. 2016. Available online: https://www.bitcoinlightning.com/wp-content/uploads/2018/03/lightning-network-paper.pdf (accessed on 10 August 2022).
- Paillier, P. Public-key cryptosystems based on composite degree residuosity classes. In Proceedings of the 1999 International Conference on the Theory and Applications of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; pp. 223–238. [Google Scholar]
- Abdella, J.; Shuaib, K. Peer to peer distributed energy trading in smart grids: A survey. Energies 2018, 11, 1560. [Google Scholar] [CrossRef]
- Chen, S.; Zhang, L.; Yan, Z.; Shen, Z. A Distributed and Robust Security-Constrained Economic Dispatch Algorithm Based on Blockchain. IEEE Trans. Power Syst. 2021, 37, 691–700. [Google Scholar]
- Lu, X.; Guan, Z.; Zhou, X.; Wu, L.; Du, X.; Guizani, M. An Efficient and Privacy-Preserving Energy Trading Scheme Based on Blockchain. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Pop, C.D.; Antal, M.; Cioara, T.; Anghel, I.; Salomie, I. Blockchain and Demand Response: Zero-Knowledge Proofs for Energy Transactions Privacy. Sensors 2020, 20, 5678. [Google Scholar] [CrossRef] [PubMed]
- Feng, Y.; Xiao, Y.; Li, D.; Fu, X. PCN-based Secure Energy Trading in Industrial Internet of Things. In Proceedings of the 2020 International Conference on Blockchain and Trustworthy Systems, Dali, China, 6–7 August 2020; pp. 305–318. [Google Scholar]
- Shen, M.; Liu, H.; Zhu, L.; Xu, K.; Yu, H.; Du, X.; Mohsen, G. Blockchain-assisted secure device authentication for cross-domain industrial IoT. IEEE J. Sel. Areas Commun. 2020, 38, 942–954. [Google Scholar]
- Aitzhan, N.Z.; Svetinovic, D. Security and privacy in decentralized energy trading through multi-signatures, blockchain and anonymous messaging streams. IEEE Trans. Dependable Secur. Comput. 2016, 15, 840–852. [Google Scholar]
- Yang, Y.; Cai, J.; Zhang, X.; Yuan, Z. Privacy preserving scheme in block chain with provably secure based on SM9 algorithm. J. Softw. 2019, 30, 1692–1704. [Google Scholar]
- Wang, Q.; Qin, B.; Hu, J.; Xiao, F. Preserving transaction privacy in bitcoin. Future Gener. Comput. Syst. 2020, 107, 793–804. [Google Scholar]
- Subramaniyaswamy, V.; Jagadeeswari, J.; Indragandhi, V.; Jhaveri, R.H.; Vijayakumar, V.; Kotecha, K.; Ravi, L. Learning with Error Algorithm for Faster Encryption of IoT Sensor Signal-Based Edge Devices. Secur. Commun. Netw. 2020, 107, 793–804. [Google Scholar]
- Sasikumar, A.; Ravi, L.; Kotecha, K.; Saini, R.J.; Varadarajan, V.; Subramaniyaswamy, V. Sustainable Smart Industry: A Secure and Energy Efficient Consensus Mechanism for Artificial Intelligence Enabled Industrial Internet of Things. Comput. Intell. Neurosci. 2022, 2022, 1419360. [Google Scholar]
- Shamir, A. Identity-based cryptosystems and signature schemes. In Proceedings of the Workshop on the Theory and Application of Cryptographic Techniques, Paris, France, 9–11 April 1984; pp. 47–53. [Google Scholar]
- Boneh, D.; Franklin, M. Identity-based encryption from the Weil pairing. In Proceedings of the Annual International Cryptology Conference, Santa Barbara, CA, USA, 19–23 August 2001; pp. 213–229. [Google Scholar]
- Cheng, Z. The sm9 Cryptographic Schemes. Cryptology ePrint Archive. 2017. Available online: https://eprint.iacr.org/2017/117 (accessed on 10 August 2022).
- Liu, S.G.; Liu, R.; Rao, S.Y. Secure and efficient two-party collaborative SM9 signature scheme suitable for smart home. J. King Saud-Univ.-Comput. Inf. Sci. 2022, 34, 4022–4030. [Google Scholar] [CrossRef]
- Yang, X.; Yuan, S.; Zhou, H.; Ding, B. A proxy-protected proxy signature based on SM9. In Proceedings of the 2021 IEEE Sixth International Conference on Data Science in Cyberspace (DSC), Shenzhen, China, 9–11 October 2021; pp. 166–170. [Google Scholar]
- Rivest, R.L.; Adleman, L.; Dertouzos, M.L. On data banks and privacy homomorphisms. Found. Secur. Comput. 1978, 4, 169–180. [Google Scholar]


| Scheme | Confidentiality of Transaction Amount | PCN | Cloud Assistance | Anonymity of Nodes |
|---|---|---|---|---|
| [1] | yes | no | no | yes |
| [8] | yes | no | no | yes |
| [10] | no | no | no | yes |
| [20] | no | no | yes | yes |
| [21] | no | no | no | yes |
| [22] | no | no | no | yes |
| [23] | yes | no | no | no |
| Proposed | yes | yes | yes | yes |
| Entity | Operation |
|---|---|
| represents signature operation | |
| represents signature verification operation | |
| represents encryption operation | |
| represents decryption operation | |
| represents ciphertext multiplication |
| Entity | Operation |
|---|---|
| Alice | + 4 |
| Bob | + 2 |
| KGC | 2 + 3 |
| TBN | 2 |
| CSP |
| Entity | Computation Overhead |
|---|---|
| Alice | 644.9301 ms |
| Bob | 659.9820 ms |
| KGC | 1501.5812 ms |
| TBN | 1475.2068 ms |
| CSP | 801.2629 ms |
| Operation | 128 bits | 256 bits | 512 bits | 1024 bits | 2048 bis |
|---|---|---|---|---|---|
| 0.4764 ms | 2.8156 ms | 4.5277 ms | 18.2366 ms | 106.5709 ms | |
| 4.8908 ms | 13.3131ms | 17.7056 ms | 79.6857 ms | 246.5112 ms | |
| 0.0319 ms | 0.0409 ms | 0.0412 ms | 0.1439 ms | 0.2872 ms | |
| 1.0243 ms | 3.7358 ms | 11.9766 ms | 60.4985 ms | 210.4611 ms |
| Entity | Communication Overhead |
|---|---|
| Alice | 1.394 KB |
| Bob | 0.794 KB |
| KGC | 1.027 KB |
| TBN | 1.037 KB |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wang, H.; Xiao, Y.; Feng, Y.; Qian, Q.; Li, Y.; Fu, X. Cloud-Assisted Privacy Protection Energy Trading Based on IBS and Homomorphic Encryption in IIoT. Appl. Sci. 2022, 12, 9509. https://doi.org/10.3390/app12199509
Wang H, Xiao Y, Feng Y, Qian Q, Li Y, Fu X. Cloud-Assisted Privacy Protection Energy Trading Based on IBS and Homomorphic Encryption in IIoT. Applied Sciences. 2022; 12(19):9509. https://doi.org/10.3390/app12199509
Chicago/Turabian StyleWang, Huajie, Yao Xiao, Yong Feng, Qian Qian, Yingna Li, and Xiaodong Fu. 2022. "Cloud-Assisted Privacy Protection Energy Trading Based on IBS and Homomorphic Encryption in IIoT" Applied Sciences 12, no. 19: 9509. https://doi.org/10.3390/app12199509
APA StyleWang, H., Xiao, Y., Feng, Y., Qian, Q., Li, Y., & Fu, X. (2022). Cloud-Assisted Privacy Protection Energy Trading Based on IBS and Homomorphic Encryption in IIoT. Applied Sciences, 12(19), 9509. https://doi.org/10.3390/app12199509





