Adaptive Trust-Based Framework for Securing and Reducing Cost in Low-Cost 6LoWPAN Wireless Sensor Networks
Abstract
:1. Introduction
- Propose an automatic security model for wireless sensor networks based on the level of trust between nodes. Building this trust depends on monitoring communications acts in a WSN environment. However, the main objective of this proposal is to provide security for the wireless sensor network as well as reduce its cost as much as possible.
- A new method for CH selection based on trust and other factors has been proposed.
- Suggest an adaptive encryption method based on the trust ratio of neighbouring nodes.
- The results were analysed based on the lifetime of the network and compared with existing algorithms.
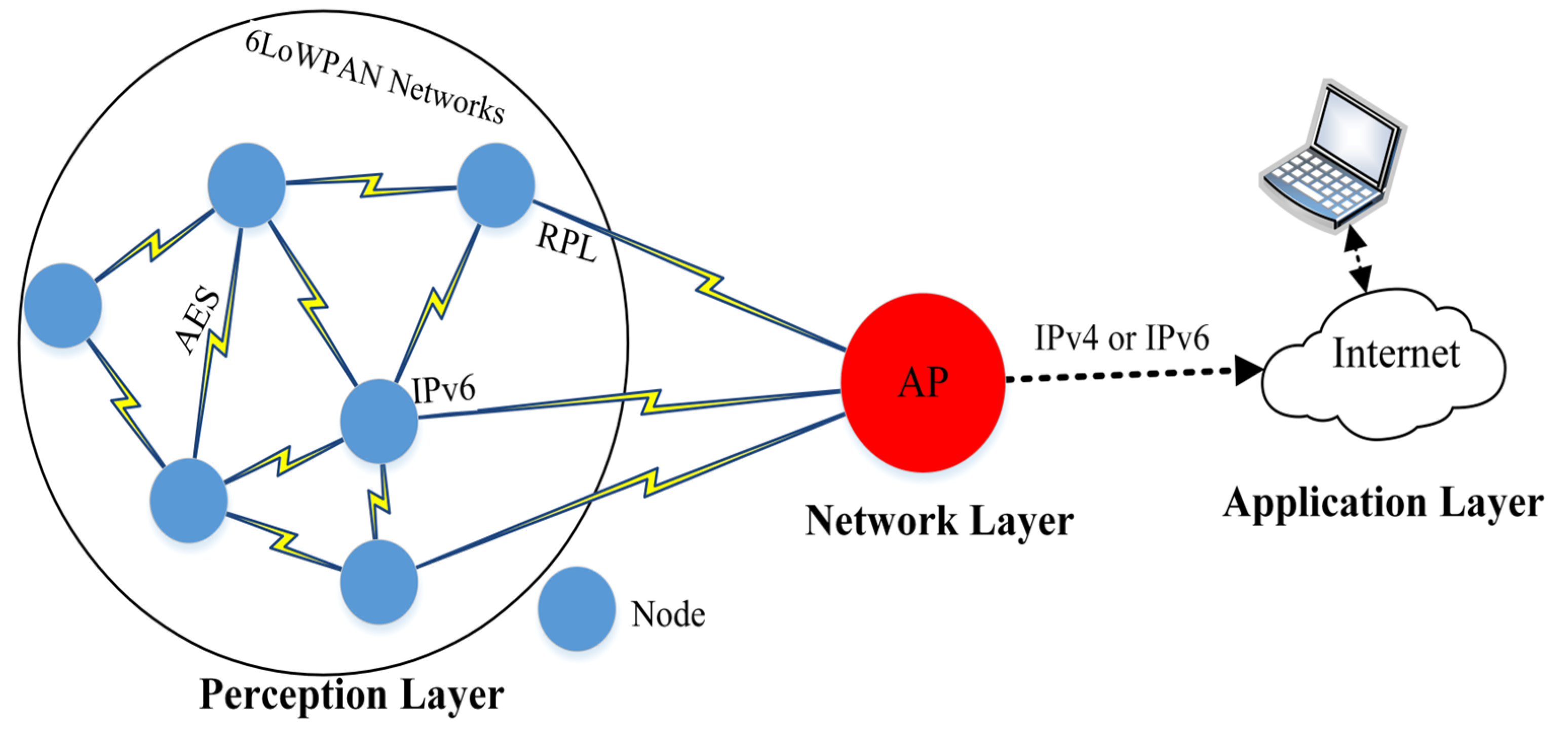
2. Background and Related Works
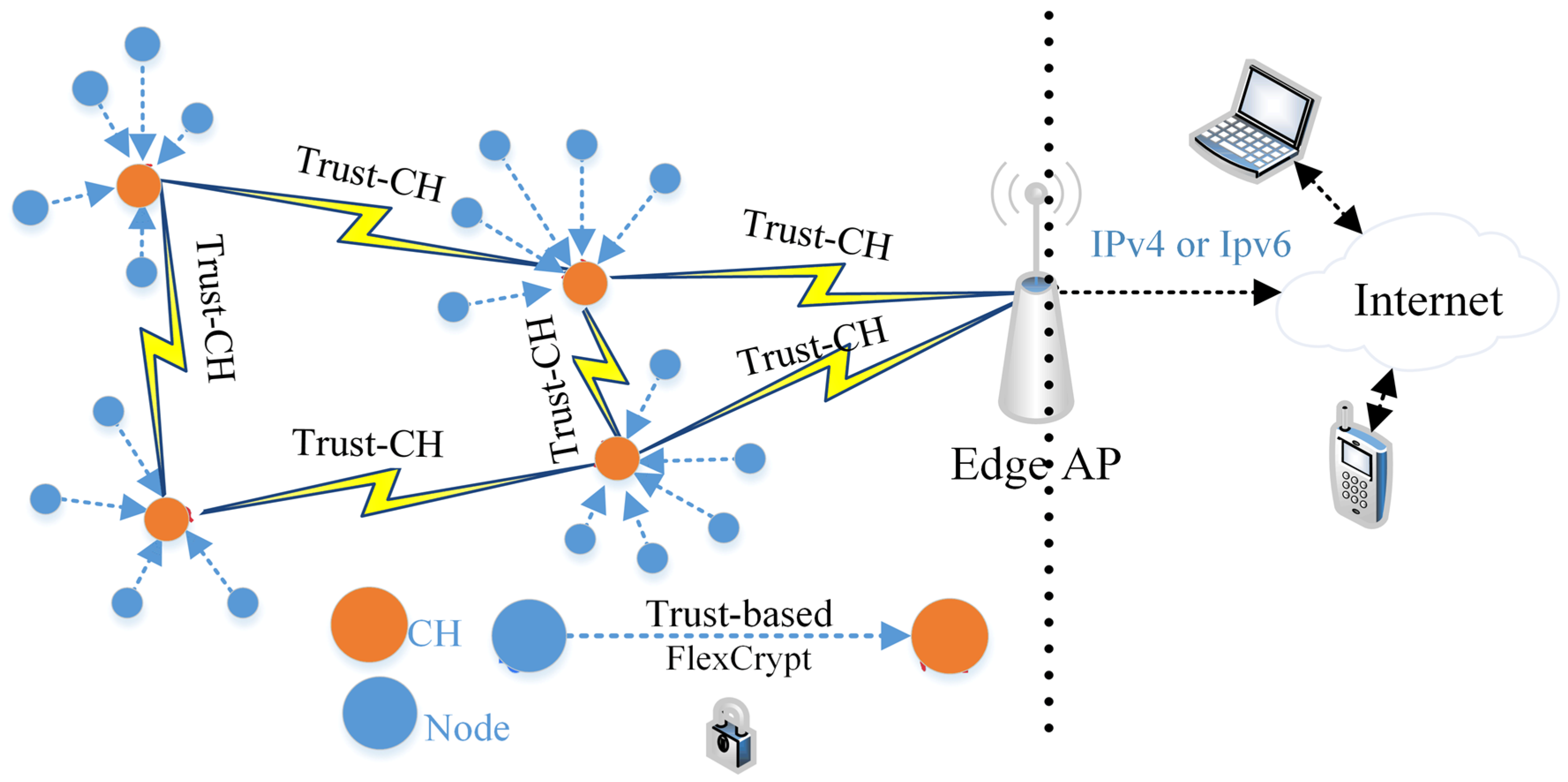
3. Proposed Trust-CH Framework
3.1. Trust-Based Calculation
- Packet of Transmission Behavior
- 2.
- Number of Repetitions
| Algorithm 1: The WSN trust-based calculation. |
| 1. for each i∊ do // all nodes |
| 2. represent the normal node |
| 3. CH represents the Cluster-head node |
| 4. for each xi ∊ CH do |
| 5. search xi in CH.T // CH table |
| 6. Find PF () |
| 7. Find AF() |
| 8. Calculate (TB()) |
| 9. Execute Equation (4) |
| 10. if T.xi.TL is malicious do |
| 11. Broadcast a warning message to all WSN trusted nodes |
| 12. Block the malicious node |
| 13. goto end // line 21 |
| 14. elseif T.xi.TL <> Null do |
| 15. Execute Equation (5) |
| 16. Send a message to all trusted WSN nodes and CHs |
| 17. Do private authentication and encryption |
| 18. else |
| 19. T.xi.TL= |
| 20. Send a message to all trusted WSN nodes and CHs |
| 21. Do private authentication and encryption |
| 22. endif |
| 23. endfor |
| 24. endfor |
- 3.
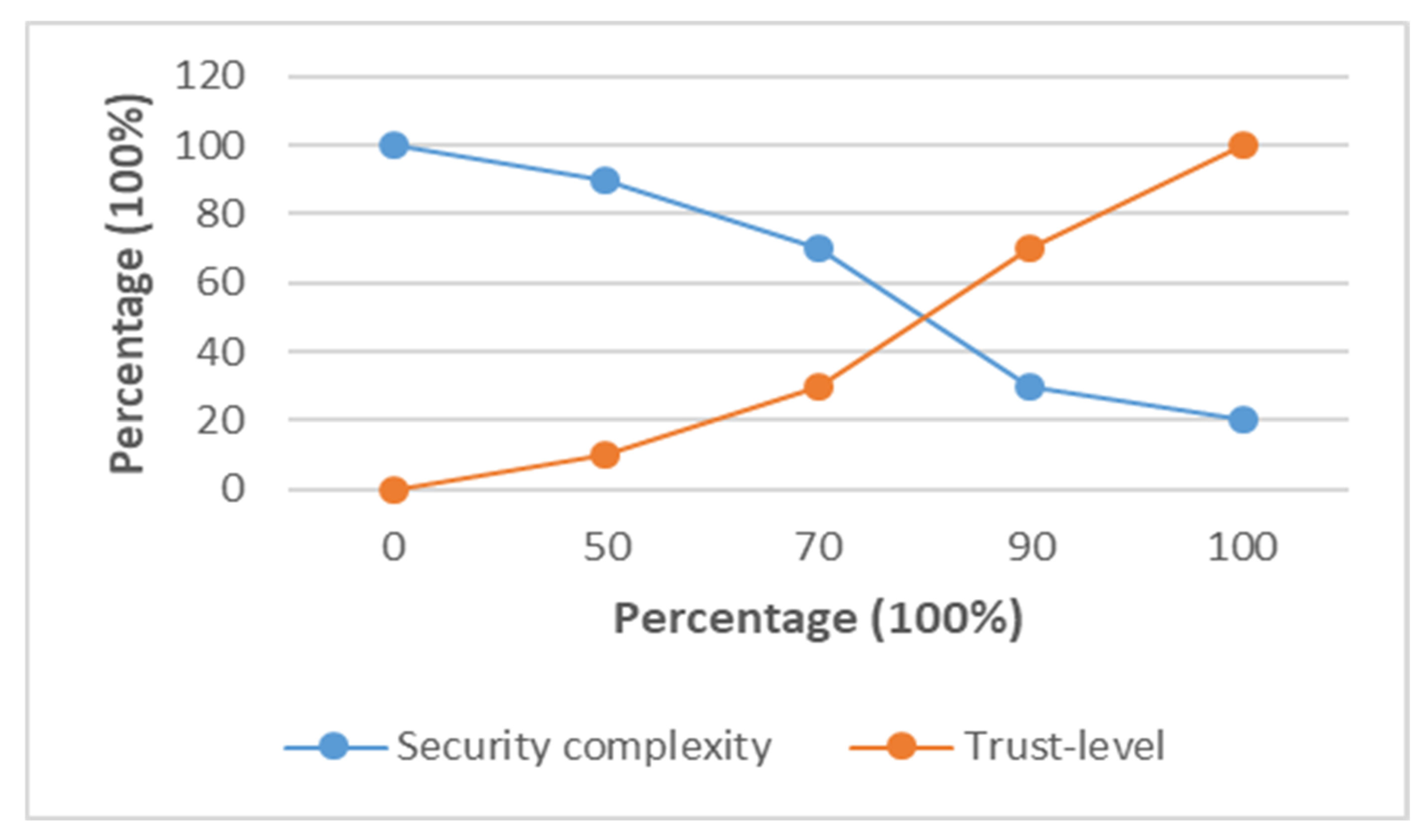
- Security Level
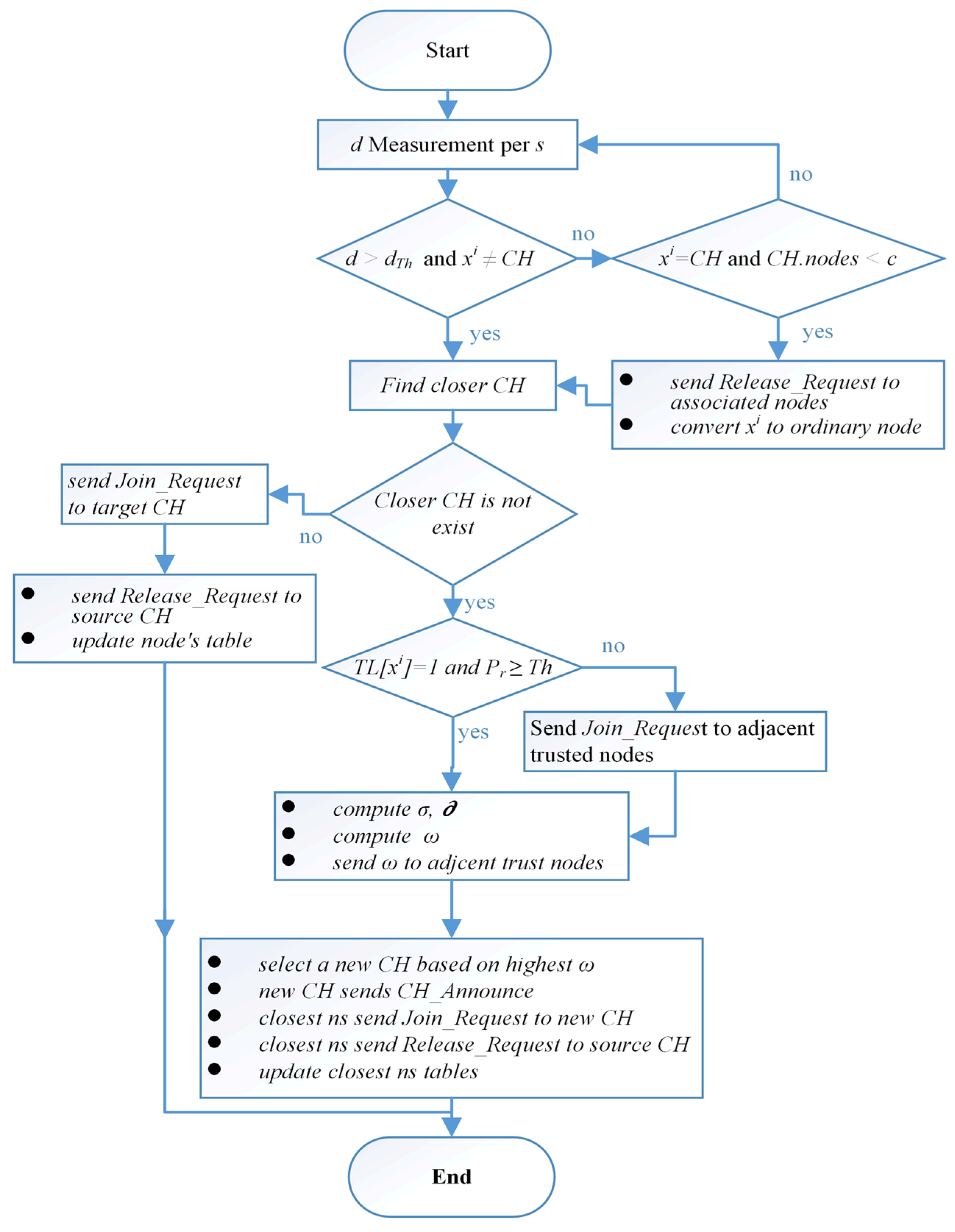
3.2. Dynamic Selection of Cluster Heads
- 1-
- The radio frequency computing power (P) model for the proposed is based on [21]. As most of the energy consumption of the WSN nodes is caused by the correspondence between them. Moreover, distance affects how much power is consumed for both WSN nodes (transmitter and receiver). The relationship based on the power consumption of the transmitter and receiver with distance and message size is shown in Equation (7) [17].where is the message size, is the distance between transmitter and receiver, is the total power consumption through sending over distance , is the node transmitter circuit consumption based on size and is the node transmitter circuit consumption based on signal amplification. Moreover, the will be equal to either βfsm for a free space model or to βtrm for the two-ray grounded propagation models depending on the between the transmitter and receiver. Moreover, the WSN node is responsible for receiving data messages from other nodes. Equation (8) [17] can be used to compute the power needed to receive the message:where is the power consumed when the node receives the message, is the power expanded by transmitter and receiver in nJ/bit and is the power dissipated by the receiving node in the reception of .
- 2-
- The WSN node energy threshold Since the CH node works centrally to the neighboring WSN nodes, the power consumption and computations will be higher, thus we must keep the node from collapsing by choosing the value. If the node energy reaches that value, it will be excluded from running for the CH position. Moreover, if it is also in this position and the amount of energy falls below the value, it is also replaced. This factor balances energy consumption between the nodes and maintains the lifetime of the entire network. The for each WSN node is calculated in Equation (9) [17].where is the power threshold of a node, is the number of neighbouring nodes and is a free space model. Furthermore, each node (N) sends the identifier (ID) and power level to all trusted nodes by data_message which is used to compute and update the table of trusted nodes in each session.
- 3-
- The average of the set of interactive factors. The number of adjacent nodes for each trusted node. The greater the number of WSN nodes close to it (nominated trusted node), the greater the chance of it becoming a CH node. Moreover, the average distances between the candidate node (CH) and the adjacent node will be taken into account, as shown in Equation (10) [17].
4. Implementation and Evaluation
4.1. Simulation and Performance Metrics
- The energy consumed and the remaining energy of the WSN nodes: It depends on the energy difference between different times to know the degree of impact of the proposed algorithm on the energy consumed.
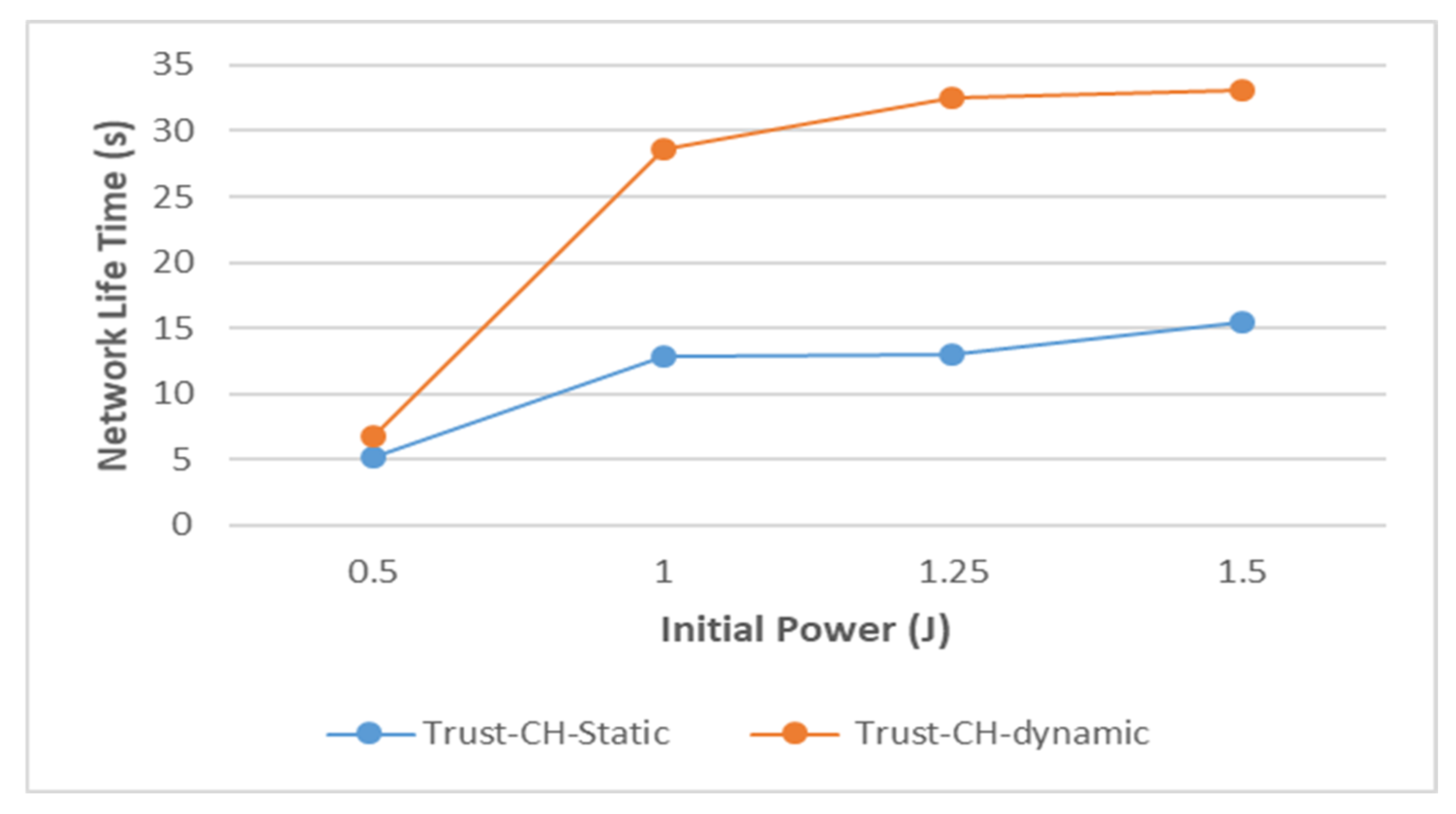
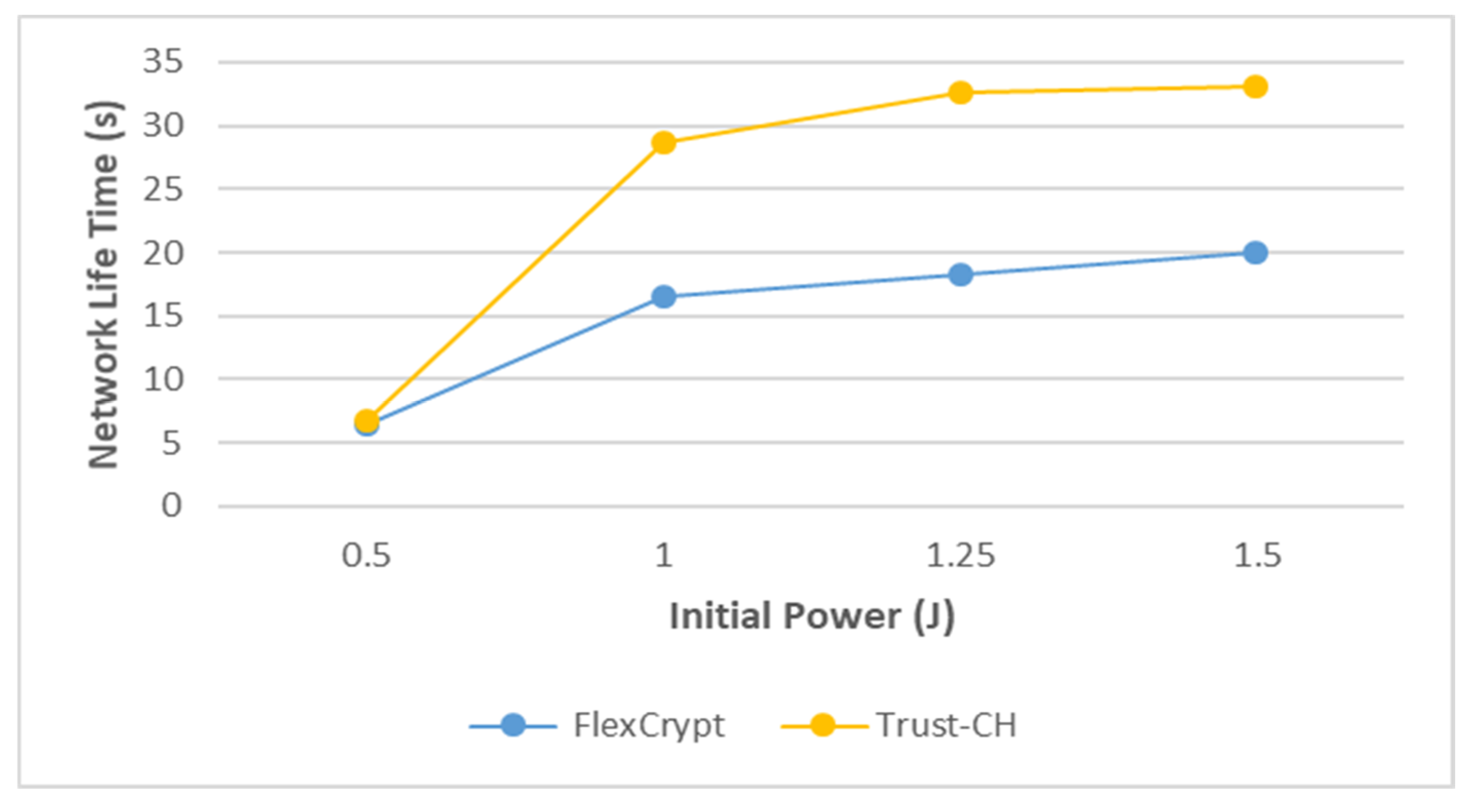
- Network lifetime: The life of the network is based on a measurement of the time period for the first node to reach zero in its amount of remaining power.
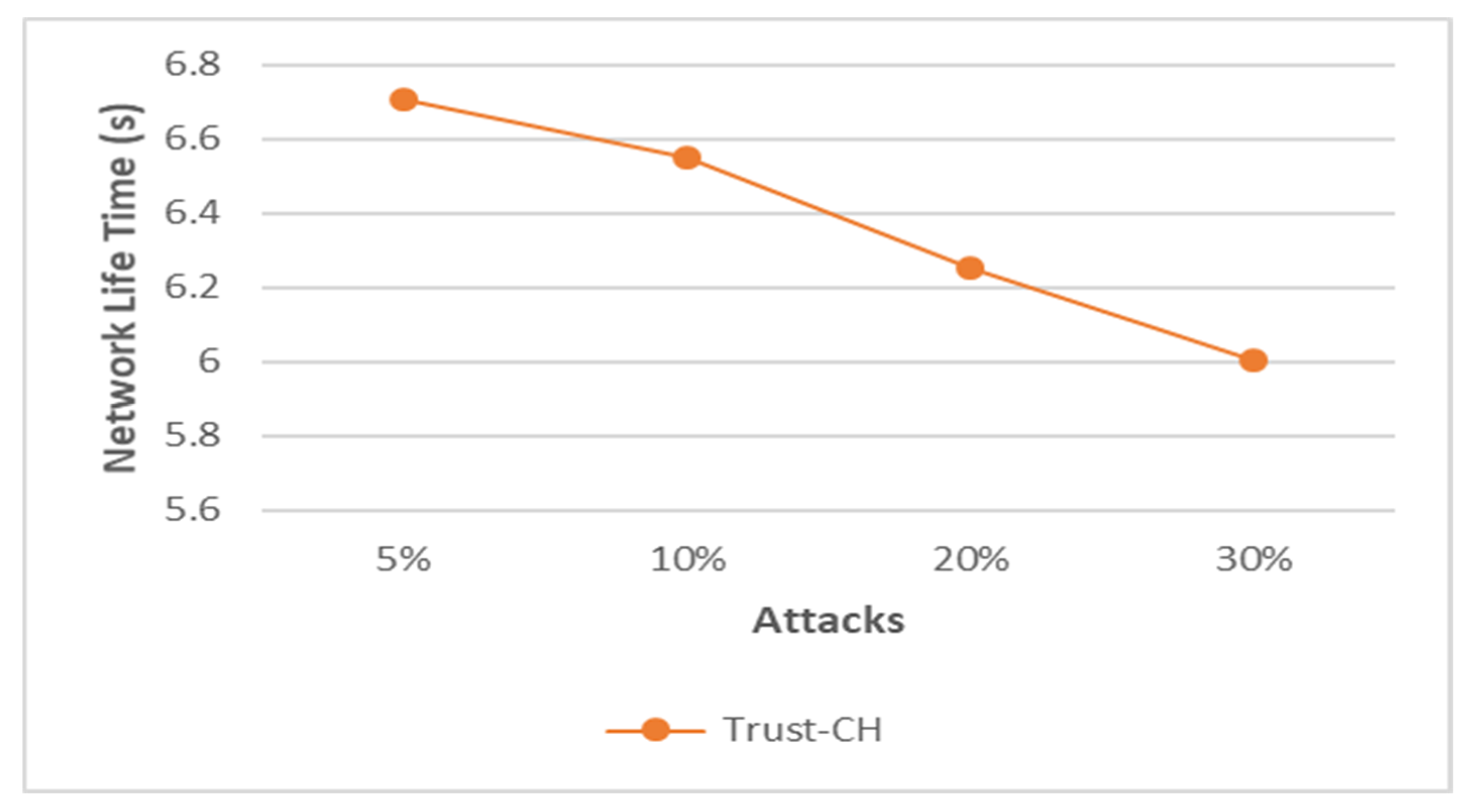
- Packet loss: This metric measures the rate at which packets fail to reach their destination when traveling over the network. Packet loss has several factors for its occurrence, but this proposal will refer to link the effect of attacks on its increase and energy consumption.
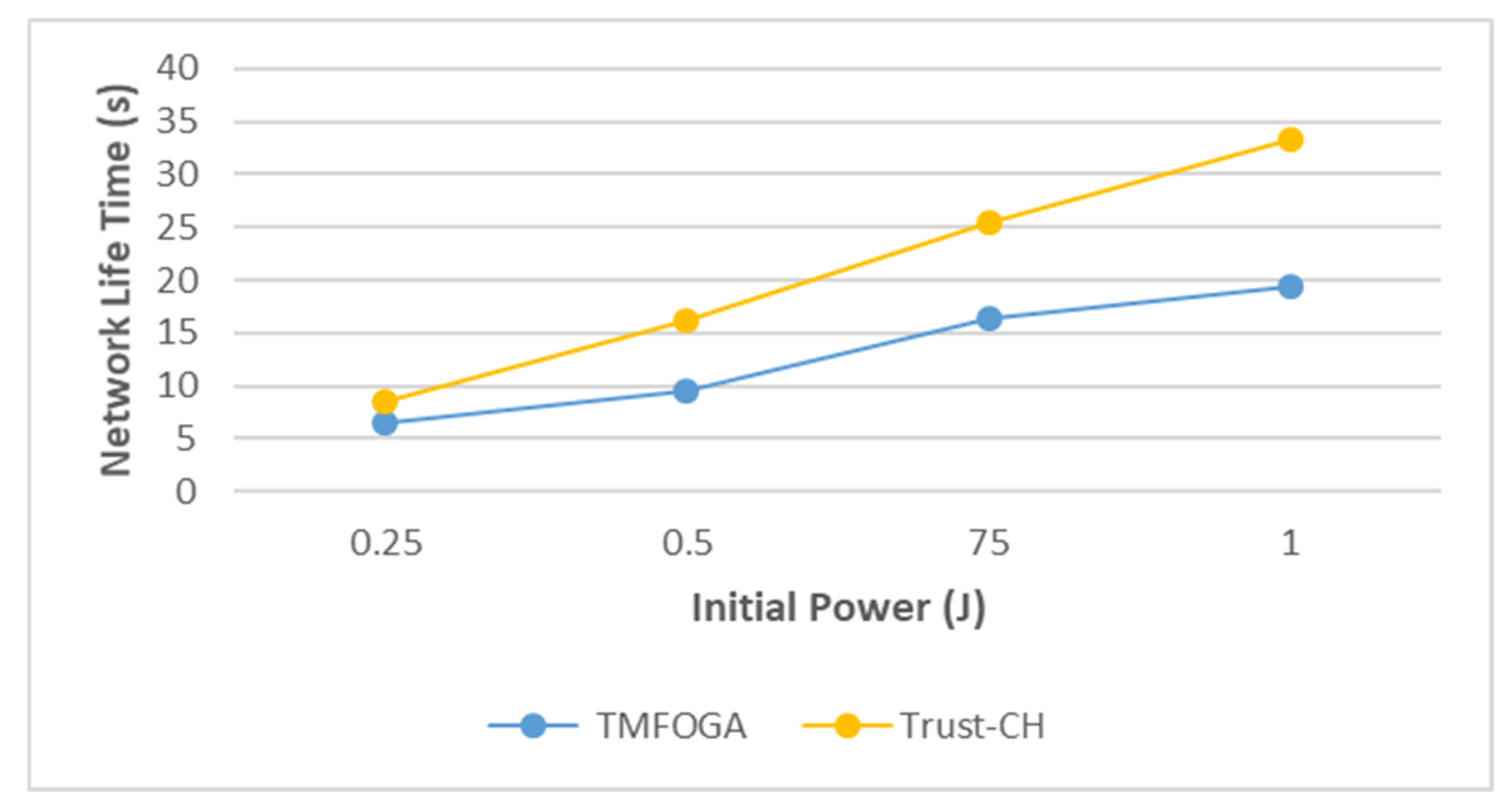
4.2. Experimental Results
4.3. Threats Resistance
5. Conclusions and Future Work
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Al-Emran, M.; Malik, S.I.; Al-Kabi, M.N. A Survey of Internet of Things (IoT) in Education: Opportunities and Challenges. In Toward Social Internet of Things (SIoT): Enabling Technologies, Architectures and Applications; Springer International Publishing: Berlin/Heidelberg, Germany, 2020; pp. 197–209. ISBN 9783030244139. [Google Scholar] [CrossRef]
- Zhang, G.; Kou, L.; Zhang, L.; Liu, C.; Da, Q.; Sun, J. A New Digital Watermarking Method for Data Integrity Protection in the Perception Layer of IoT. Secur. Commun. Netw. 2017, 2017, 3126010. [Google Scholar] [CrossRef]
- Mostfa, A.A.; Xiao, W.; Sharkawy, A.-N. Development of in-shoe wearable pressure sensor using an Android application. AIP Conf. Proc. 2022, 2386, 050024. [Google Scholar] [CrossRef]
- Yang, N.; Wang, Z.; Gravina, R.; Fortino, G. A survey of open body sensor networks: Applications and challenges. In Proceedings of the 2017 14th IEEE Annual Consumer Communications and Networking Conference, CCNC, Las Vegas, NV, USA, 8–11 January 2017; pp. 65–70. [Google Scholar] [CrossRef]
- Precedenceresearch Home Healthcare Market Size, Share & Growth Analysis Report by Equipment Type (Therapeutic, Diagnostic), by Service (Skilled Home Healthcare Services, Unskilled Home Healthcare Services)-Global Industry Analysis, Trends, Segment Forecasts, Regional Outl. Available online: https://www.precedenceresearch.com/home-healthcare-market (accessed on 1 September 2021).
- Al-Kashoash, H.A.A.; Kharrufa, H.; Al-Nidawi, Y.; Kemp, A.H. Congestion control in wireless sensor and 6LoWPAN networks: Toward the Internet of Things. Wirel. Netw. 2019, 25, 4493–4522. [Google Scholar] [CrossRef]
- Kumar, V.; Tiwari, S. Routing in IPv6 over Low-Power Wireless Personal Area Networks (6LoWPAN): A Survey. J. Comput. Netw. Commun. 2012, 2012, 316839. [Google Scholar] [CrossRef]
- Olsson, J. 6LoWPAN demystified. Tex. Instrum. 2014, 13, 1–13. [Google Scholar]
- Gupta, M.; Sinha, A. Enhanced-AES encryption mechanism with S-box splitting for wireless sensor networks. Int. J. Inf. Technol. 2021, 13, 933–941. [Google Scholar] [CrossRef]
- Ahmad, R.; Wazirali, R.; Abu-ain, T. Machine Learning for Wireless Sensor Networks Security: An Overview of Challenges and Issues. Sensors 2022, 22, 4730. [Google Scholar] [CrossRef]
- Bogdanov, A.; Khovratovich, D.; Rechberger, C. Biclique Cryptanalysis of the Full AES. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 2011; Volume 7073 LNCS, pp. 344–371. ISBN 9783642253843. [Google Scholar] [CrossRef]
- Wheeler, D.J.; Needham, R.M. TEA, a tiny encryption algorithm. In Lecture Notes in Computer Science (Including Subseries Lecture Notes in Artificial Intelligence and Lecture Notes in Bioinformatics); Springer: Berlin/Heidelberg, Germany, 1995; Volume 1008, pp. 363–366. ISBN 3540605908. [Google Scholar] [CrossRef] [Green Version]
- Medileh, S.; Laouid, A.; Nagoudi, E.M.B.; Euler, R.; Bounceur, A.; Hammoudeh, M.; AlShaikh, M.; Eleyan, A.; Khashan, O.A. A flexible encryption technique for the internet of things environment. Ad Hoc Netw. 2020, 106, 102240. [Google Scholar] [CrossRef]
- Ahmad, R.; Sundararajan, E.A.; Abu-Ain, T. Analysis the Effect of Clustering and Lightweight Encryption Approaches on WSNs Lifetime. In Proceedings of the 2021 International Conference on Electrical Engineering and Informatics (ICEEI), Kuala Terengganu, Malaysia, 12–13 October 2021; IEEE: Selangor, Malaysia, 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Alshrif, F.F.; Sundararajan, E.A.; Ahmad, R.; Alkhatib, Y. New Framework for Authentication and key Establishment to Secure 6LoWPAN Networks. In Proceedings of the 2021 International Conference on Electrical Engineering and Informatics (ICEEI), Kuala Terengganu, Malaysia, 12–13 October 2021; IEEE: Selangor, Malaysia, 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Wazirali, R.; Ahmad, R.; Al-Amayreh, A.; Al-Madi, M.; Khalifeh, A. Secure Watermarking Schemes and Their Approaches in the IoT Technology: An Overview. Electronics 2021, 10, 1744. [Google Scholar] [CrossRef]
- Darabkh, K.A.; El-Yabroudi, M.Z.; El-Mousa, A.H. BPA-CRP: A balanced power-aware clustering and routing protocol for wireless sensor networks. Ad Hoc Netw. 2019, 82, 155–171. [Google Scholar] [CrossRef]
- Sujanthi, S.; Nithya Kalyani, S. SecDL: QoS-Aware Secure Deep Learning Approach for Dynamic Cluster-Based Routing in WSN Assisted IoT. Wirel. Pers. Commun. 2020, 114, 2135–2169. [Google Scholar] [CrossRef]
- Darabkh, K.A.; Al-Maaitah, N.J.; Jafar, I.F.; Khalifeh, A.F. EA-CRP: A Novel Energy-aware Clustering and Routing Protocol in Wireless Sensor Networks. Comput. Electr. Eng. 2018, 72, 702–718. [Google Scholar] [CrossRef]
- Jain, T.K.; Saini, D.S.; Bhooshan, S.V. Cluster head selection in a homogeneous wireless sensor network ensuring full connectivity with minimum isolated nodes. J. Sens. 2014, 2014, 724219. [Google Scholar] [CrossRef]
- Darabkh, K.A.; Albtoush, W.Y.; Jafar, I.F. Improved clustering algorithms for target tracking in wireless sensor networks. J. Supercomput. 2017, 73, 1952–1977. [Google Scholar] [CrossRef]
- Abuarqoub, A.; Hammoudeh, M.; Adebisi, B.; Jabbar, S.; Bounceur, A.; Al-Bashar, H. Dynamic clustering and management of mobile wireless sensor networks. Comput. Netw. 2017, 117, 62–75. [Google Scholar] [CrossRef] [Green Version]
- Zhao, Y.; Liu, K.; Xu, X.; Yang, H.; Huang, L. Distributed dynamic cluster-head selection and clustering for massive IoT access in 5G networks. Appl. Sci. 2019, 9, 132. [Google Scholar] [CrossRef]
- Elhoseny, M.; Farouk, A.; Zhou, N.; Wang, M.M.; Abdalla, S.; Batle, J. Dynamic Multi-hop Clustering in a Wireless Sensor Network: Performance Improvement. Wirel. Pers. Commun. 2017, 95, 3733–3753. [Google Scholar] [CrossRef]
- Bozorgi, S.M.; Shokouhi Rostami, A.; Hosseinabadi, A.A.R.; Balas, V.E. A new clustering protocol for energy harvesting-wireless sensor networks. Comput. Electr. Eng. 2017, 64, 233–247. [Google Scholar] [CrossRef]
- Khashan, O.A.; Ahmad, R.; Khafajah, N.M. An automated lightweight encryption scheme for secure and energy-efficient communication in wireless sensor networks. Ad Hoc Netw. 2021, 115, 102448. [Google Scholar] [CrossRef]
- Obert, J.; Chavez, A.; Johnson, J. Distributed renewable energy resource trust metrics and secure routing. Comput. Secur. 2020, 88, 101620. [Google Scholar] [CrossRef]
- Fang, W.; Zhang, W.; Chen, W.; Pan, T.; Ni, Y.; Yang, Y. Trust-Based Attack and Defense in Wireless Sensor Networks: A Survey. Wirel. Commun. Mob. Comput. 2020, 2020, 2643546. [Google Scholar] [CrossRef]
- Singh, M.; Sardar, A.R.; Majumder, K.; Sarkar, S.K. A Lightweight Trust Mechanism and Overhead Analysis for Clustered WSN. IETE J. Res. 2017, 63, 297–308. [Google Scholar] [CrossRef]
- Jayasinghe, U.; Lee, G.M.; Um, T.-W.; Shi, Q. Machine Learning Based Trust Computational Model for IoT Services. IEEE Trans. Sustain. Comput. 2019, 4, 39–52. [Google Scholar] [CrossRef]
- Mazumdar, N.; Om, H. DUCR: Distributed unequal cluster-based routing algorithm for heterogeneous wireless sensor networks. Int. J. Commun. Syst. 2017, 30, e3374. [Google Scholar] [CrossRef]
- Ahmad, R.; Wazirali, R.; Bsoul, Q.; Abu-Ain, T.; Abu-Ain, W. Feature-Selection and Mutual-Clustering Approaches to Improve DoS Detection and Maintain WSNs’ Lifetime. Sensors 2021, 21, 4821. [Google Scholar] [CrossRef] [PubMed]
- Arumugam, G.S.; Ponnuchamy, T. EE-LEACH: Development of energy-efficient LEACH Protocol for data gathering in WSN. Eurasip J. Wirel. Commun. Netw. 2015, 2015, 76. [Google Scholar] [CrossRef]
- Awais Javed, M.; Zeadally, S.; Hamid, Z. Trust-based security adaptation mechanism for Vehicular Sensor Networks. Comput. Netw. 2018, 137, 27–36. [Google Scholar] [CrossRef]
- El-Sayed, H.; Ignatious, H.A.; Kulkarni, P.; Bouktif, S. Machine learning based trust management framework for vehicular networks. Veh. Commun. 2020, 25, 100256. [Google Scholar] [CrossRef]
- Mehetre, D.C.; Roslin, S.E.; Wagh, S.J. Detection and prevention of black hole and selective forwarding attack in clustered WSN with Active Trust. Clust. Comput. 2019, 22, 1313–1328. [Google Scholar] [CrossRef]
- Yu, X.; Li, F.; Li, T.; Wu, N.; Wang, H.; Zhou, H. Trust-based secure directed diffusion routing protocol in WSN. J. Ambient. Intell. Humaniz. Comput. 2020, 13, 1405–1417. [Google Scholar] [CrossRef]
- Das, R.; Dash, D.; Sarkar, M.K. HTMS: Fuzzy Based Hierarchical Trust Management Scheme in WSN; Springer: New York, NY, USA, 2020; Volume 112, ISBN 0123456789. [Google Scholar] [CrossRef]
- Sharma, R.; Vashisht, V.; Singh, U. eeTMFO/GA: A secure and energy efficient cluster head selection in wireless sensor networks. Telecommun. Syst. 2020, 74, 253–268. [Google Scholar] [CrossRef]
- Qureshi, S.G.; Shandilya, S.K. Nature-inspired adaptive decision support system for secured clustering in cyber networks. Multimed. Tools Appl. 2022, 1–35. [Google Scholar] [CrossRef]
- Ahmad, R.; Sundararajan, E.A.; Othman, N.E.; Ismail, M. An efficient handover decision in heterogeneous LTE-A networks under the assistance of users’ profile. Telecommun. Syst. 2018, 68, 27–45. [Google Scholar] [CrossRef]
- Halder, M.; Nowsin, M.; Sheikh, A.; Rahman, S.; Rahman, A. Performance Analysis of CoAP, 6LoWPAN and RPL Routing Protocols of IoT Using COOJA Simulator. Int. J. Sci. Eng. Res. 2018, 9, 1670–1677. [Google Scholar]
- Githhub. Available online: https://github.com/contiki-os/contiki/wiki/An-Introduction-to-Cooja (accessed on 7 October 2021).
- Ahmad, R.; Ismail, M.; Sundararajan, E.A.; Othman, N.E.; Zain, A.M. Performance of movement direction distance-based vertical handover algorithm under various femtocell distributions in HetNet. In Proceedings of the 2017 IEEE 13th Malaysia International Conference on Communications (MICC), Johor Bahru, Malaysia, 28–30 November 2017; Volume 2017-Novem, pp. 253–258. [Google Scholar] [CrossRef]
- Abu-Ain, T.; Ahmad, R.; Sundararajan, E.A. Analysis the Effect of Dynamic Clustering and Lightweight Symmetric Encryption Approaches on Network Lifetime in WSNs. Res. Sq. 2021, 1–28. [Google Scholar] [CrossRef]



| Refs | Technique | Key Idea | Strengths | Weaknesses |
|---|---|---|---|---|
| [19] | Clustering method | Uses two heads in order to balance energy between nodes |
|
|
| [20] | Clustering method | CH is selected based on various factors |
|
|
| [33] | Clustering method | CH is selected based on the highest residual energy | Reduce nodes power consumption |
|
| [26] | Automated encryption | Balance nodes security and power |
|
|
| [29] | lightweight trust algorithm | Monitoring WSN node’s parameters | Support different types of internal attacks |
|
| [34] | Adaptive trust-based | Adjust the security level based on the trust level of nearby vehicles |
|
|
| [35] | Centric trust framework | Using decision tree classification and artificial neural networks |
|
|
| [30] | Trust metrics framework | k-meant clusters to categorize interactions as reliable and untrustworthy |
|
|
| [36] | Trusted and Secure Routing | Cuckoo search algorithm |
|
|
| [37] | Energy Trust Model | establishing a trustworthy communication pathway |
|
|
| [38] | Hierarchical trust management | Balanced weight subcluster formation uses Fuzzy S-means to the CH-identification scheme |
|
|
| [39] | Trust clustering model | Using GA to choose the appropriate CH |
|
|
| Notations | Description |
|---|---|
| xi | Node number i |
| Node number j | |
| Time | |
| The weight of the node | |
| Constant values | |
| Block size | |
| The power consumed when the node sends the message | |
| Message length | |
| The distance | |
| The node transmitter circuit consumption based on signal amplification | |
| βfsm | Free space model |
| βtrm | Two-ray grounded propagation models |
| The power consumed when the node receives the message | |
| The power dissipated by the receiving node | |
| The power threshold of a node | |
| The number of neighboring nodes | |
| Power expanded by transmitter and receiver | |
| The average of interactive factors | |
| Total number of nodes | |
| Candidate node | |
| Average distance | |
| The average weights | |
| The number of adjacent nodes | |
| Residual energy | |
| The average distances between the candidate node (Trusted node) and the existing CH nodes | |
| Minimum number of host nodes | |
| Distance between CH nodes and the host nodes | |
| Total number of CHs operating at time (t) |
| Parameter | Value |
|---|---|
| WSN size | 60 m × 120 m |
| AP location | X = 30, Y = 90 |
| n | 200 |
| Node speed | 5 meter/second |
| q size | 64 bytes |
| Control message size | 25 bytes |
| P initial | 0.5 J (joule) |
| βtrm | 0.0013 PJ/bit/m4 |
| βfsm | 10 PJ/bit/m2 |
| Pelec | 50 nJ/bit |
| Pr | 0.005 J |
| Pb | 0.005 for 16 bits |
| dT | 87 m |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ahmad, R.; Wazirali, R.; Abu-Ain, T.; Almohamad, T.A. Adaptive Trust-Based Framework for Securing and Reducing Cost in Low-Cost 6LoWPAN Wireless Sensor Networks. Appl. Sci. 2022, 12, 8605. https://doi.org/10.3390/app12178605
Ahmad R, Wazirali R, Abu-Ain T, Almohamad TA. Adaptive Trust-Based Framework for Securing and Reducing Cost in Low-Cost 6LoWPAN Wireless Sensor Networks. Applied Sciences. 2022; 12(17):8605. https://doi.org/10.3390/app12178605
Chicago/Turabian StyleAhmad, Rami, Raniyah Wazirali, Tarik Abu-Ain, and Tarik Adnan Almohamad. 2022. "Adaptive Trust-Based Framework for Securing and Reducing Cost in Low-Cost 6LoWPAN Wireless Sensor Networks" Applied Sciences 12, no. 17: 8605. https://doi.org/10.3390/app12178605
APA StyleAhmad, R., Wazirali, R., Abu-Ain, T., & Almohamad, T. A. (2022). Adaptive Trust-Based Framework for Securing and Reducing Cost in Low-Cost 6LoWPAN Wireless Sensor Networks. Applied Sciences, 12(17), 8605. https://doi.org/10.3390/app12178605








