Revisiting the Detection of Lateral Movement through Sysmon
Abstract
:1. Introduction
- From a defender’s viewpoint, we elaborate on the outcomes of the executed experiments in an attempt to define solid criteria, which act as signatures per examined attack.
- Based on the derived criteria, the most impactful features were extracted as related to Sysmon’s identification of an adversary moving laterally.
- The proposed criteria, along with their related features, are evaluated based on their effectiveness on a potential lateral incident’s identification through Sysmon.
- A rule-based methodology is proposed that is dedicated to the identification, verification, and categorization of each lateral technique.
- The proposed methodology is implemented in a Python analyzing tool dubbed “PeX”. The tool along with the large dataset of Sysmon logs collected during the experiments are made publicly available to the community [2].
2. Related Work
3. Preliminaries on Lateral Movement
- The first method refers to network mapping and identification of the special characteristics of each distinct component along with potential vulnerabilities. During the reconnaissance phase, many OS’s built-in tools can be used. For instance, the ipconfig and ifconfig commands reveal IP configurations and localization information, while Netstat summarizes the most current network connections along with their users. Additionally, the local routing table tracks all the interconnected network paths, while the Address Resolution Protocol (ARP) cache reveals the matching of network IP addresses to their equivalent link layer (MAC) addresses. Vulnerability assessment and mapping tools are also in the attackers’ quiver, namely Nmap or its commercial equivalent Nessus [19]. Once the relevant information is gathered, the adversary is able to intrude and move laterally.
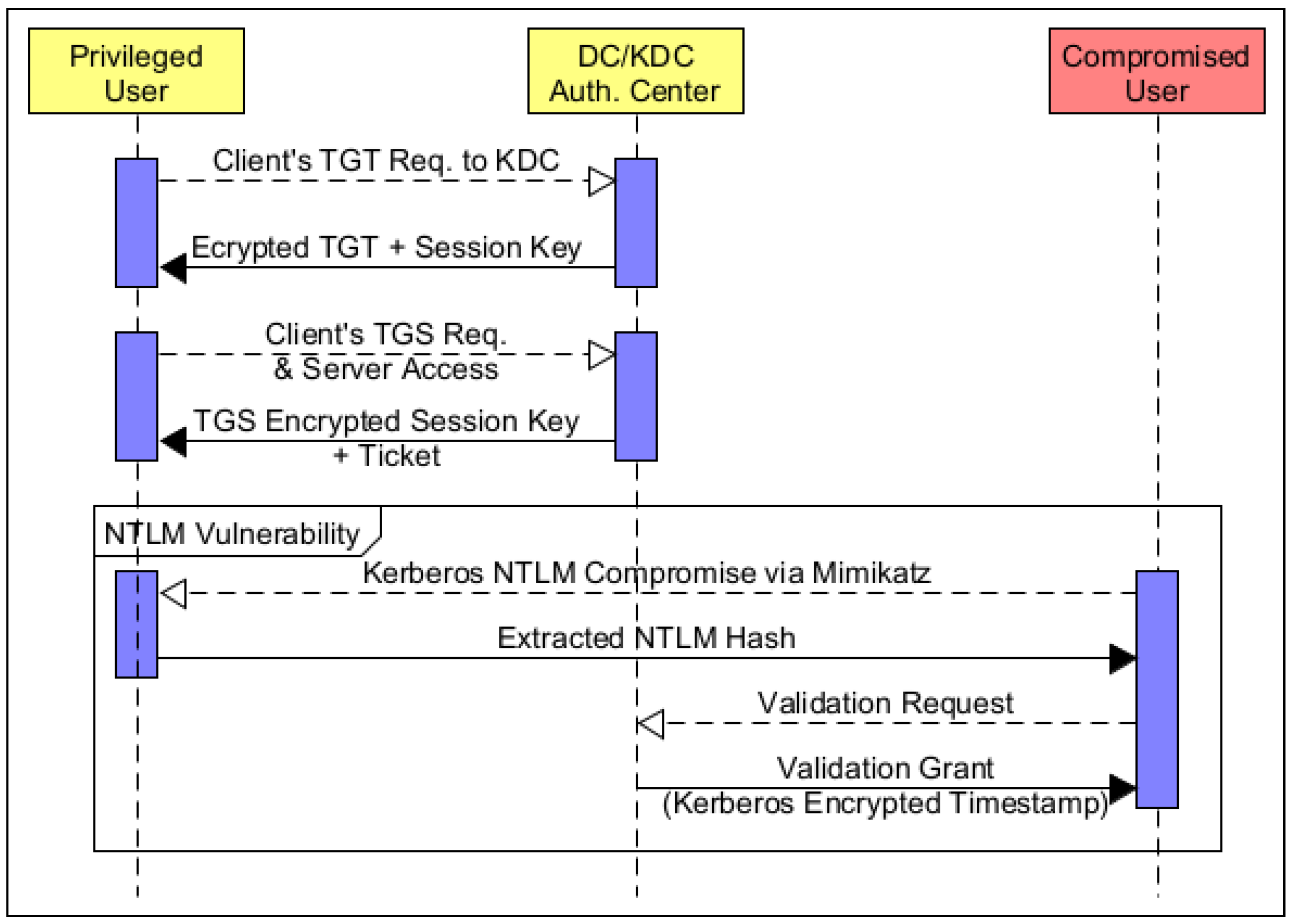
- The second customary method refers to the use of phishing techniques for the acquisition of account credentials by any means. To this end, the opponent can take advantage of tools, say, Metasploit Pro, to craft numerous phishing emails that have been perfectly cloned to appear as originating from a legitimate source. Additionally, keylogger tools, including Revealer Keylogger Free, KidLogger, and BlackBox Express, provide a powerful equivalent solution for activity monitoring and screen recording at the victim’s side. Mimikatz, presented in Section 6.2, is another powerful credential exploitation and hash dumping penetration testing tool.
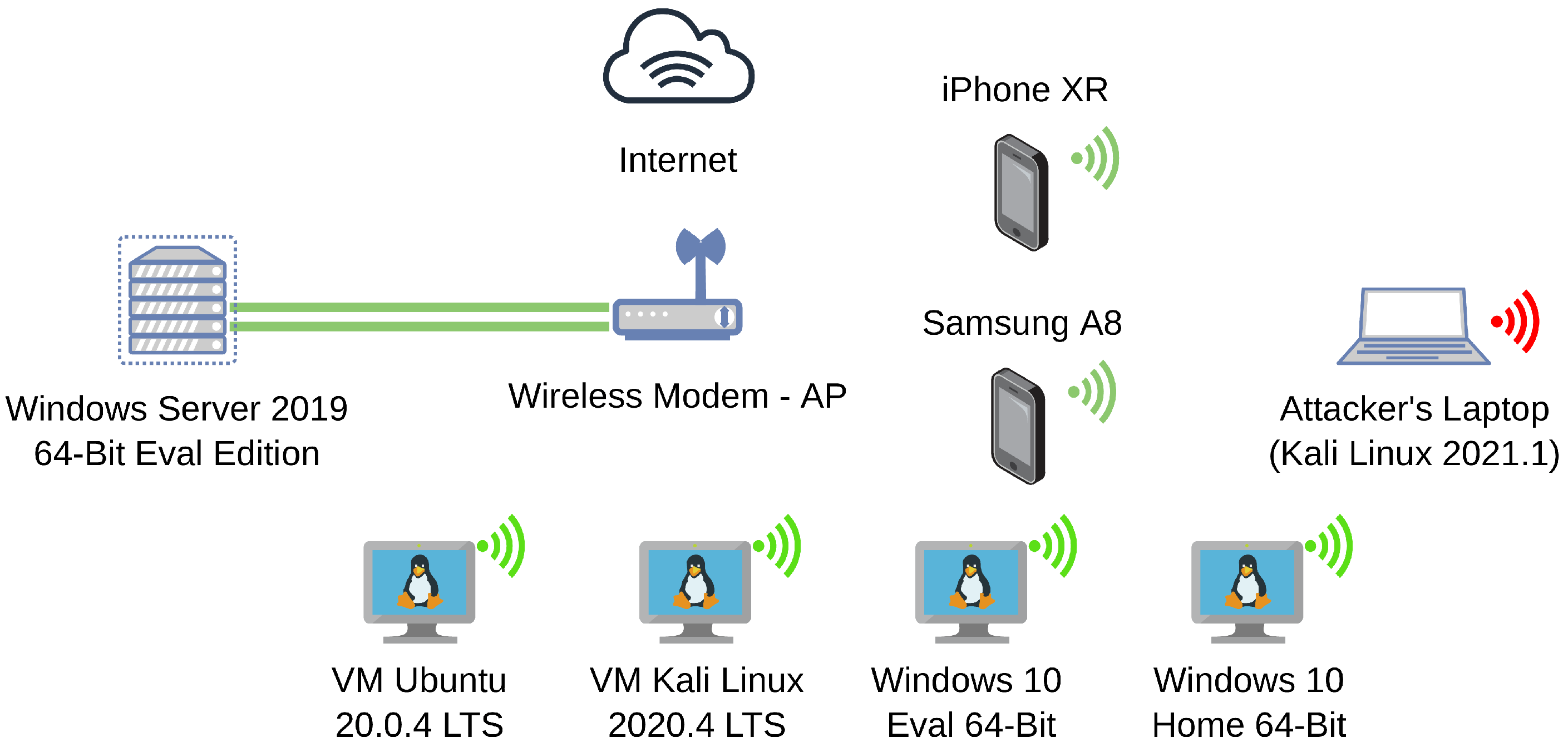
4. Testbed
5. Lateral Movement Categories on Windows Environments
5.1. Exploitation of Remote Services
5.2. Pass the Hash Credential Override
5.3. Pass the Ticket Credential Override
5.4. Golden Ticket
5.5. Silver Ticket
5.6. Post Exploitation on Stored Passwords with LaZagne Project
6. Methodology
- 1
- <Sysmon schemaversion="13.30">
- 2
- <HashAlgorithms>md5,sha256,IMPHASH</HashAlgorithms>
- 3
- <CheckRevocation/>
- 4
- <EventFiltering>
- 5
- <RuleGroup name="Sysmon_Event_1(ProcessCreate)" groupRelation="or">
6.1. Exploitation of Remote Services
6.1.1. Exploitation of ms17-010
6.1.2. Exploitation of EternalBlue
6.1.3. Deployment of WannaCry
6.1.4. Exploitation of BlueKeep
- mstsc.exe: It is related to Microsoft Terminal Services Client (MSTSC) Windows shared library (DLL) and allows access to RDP clients to perform a remote desktop connection through command line or PowerShell. If leveraged by an adversary, the relevant DLL may allow the execution of arbitrary controversial code remotely without the mediation of GUI or a SOCKS proxy connection [23].
- RTSApp.exe: It is related to the Royal TS remote management software from code4ward. Royal TS supports both Windows RDP and RDS, protocol and services. If not found in C:\\Program Files\\code4ward\\royal_ts, then it should be checked for potential malware activity, which refers to an LM attack [24,25].
- ws_TunnelService.exe: This process belongs to VMware and there are no references to Virustotal for potential malicious behavior. However, when identified in a system that neglects VMware from its utilities, then the collected digital signature’s hash algorithm of the file should be checked as potentially malicious [26].
- RemoteDesktopManagerFree.exe, RemoteDesktopManager.exe, RemoteDesktopManager64.exe, mRemote.exe: The mentioned processes are strongly related to Windows handling of remote desktop connections. They comprise nonstandard tools of Windows that utilize destination port 3389 and should be considered potentially dangerous for LM orchestration [25,27,28].
- Terminals.exe, spiceworks-finder.exe, thor.exe, thor64.exe: These executable files are not Windows native and, when in existence, should be evaluated as potentially malicious and related to malware-based LM behavior [24].
- reg.exe, chrome.exe: The second process is one of the most common among Windows users, as it is the executable of the Chrome browser. Despite the reliability of the process, adversaries can take advantage of the frequency with which it appears on the target system by leveraging Chrome’s launcher. This is accomplished through the remote manipulation of the target’s registry permissions to eventually grant RCE and RDP exploitation. The simultaneous presence of the two processes or the occurrence of the second in a subfolder of the user’s profile folder, in conjunction with the utilization of TCP port 3389, should be examined as malicious [29,30].
6.2. Credential Exploitation Attacks
6.2.1. Pass the Hash
6.2.2. Pass the Ticket
6.2.3. Golden/Silver Ticket
6.2.4. Discussion on Mimikatz-Related Attacks
- 1
- <ProcessCreate onmatch="include">
- 2
- <CommandLine condition="contains">C:\Windows\system32\lsass.exe</CommandLine> <!-- Possible indication for the execution of the Lateral Movement Skeleton Key Attack -->
- 3
- <CommandLine condition="contains">C:\Windows\system32\smb.exe</CommandLine>
- 4
- <ParentCommandLine condition="is">lazagne.exe windows</ParentCommandLine>
- 5
- <CommandLine condition="is">C:\Users\Administrator\mimikatz_trunk\x64\mimikatz.exe</CommandLine>
- 6
- <Image name="lsass ProcessCreate" condition="is">C:\Windows\system32\lsass.exe</Image>
- 7
- <Image name="svchost ProcessCreate" condition="is">C:\Windows\System32\svchost.exe</Image>
- 8
- <Image name="ProcessCreate" condition="end with">smb.exe</Image>
- 9
- <Image name="Mimikatz Execution" condition="is">C:\Users\Administrator\mimikatz_trunk\x64\mimikatz.exe</Image>
- 10
- <Image name="lazagne" condition="is">C:\Users\Administrator\Downloads\lazagne.exe</Image> <!-- The LaZagne project is an open source application used to retrieve lots of passwords stored on a local computer. -->
- 11
- <Image name="klist" condition="is">C:\Windows\System32\klist.exe</Image>
- 12
- </ProcessCreate>
- 1
- <ProcessCreate onmatch="include">
- 2
- <CommandLine name="Privilege Escalation" condition="contains">Get-Keystrokes</CommandLine> <!-- keylogging or keyboard capturing, is the action of logging keys pressed, time and the active window. -->
- 3
- <CommandLine name="Privilege Escalation" condition="contains">Get-TimedScreenshot</CommandLine> <!-- Takes screenshots and saves them to a folder, with a timestamp to reveal the time and date of the screenshot. -->
- 4
- <CommandLine name="Privilege Escalation" condition="contains">Get-VaultCredential</CommandLine> <!-- Displays Windows vault credential objects including cleartext web credentials. -->
- 5
- <CommandLine name="Privilege Escalation" condition="contains">Invoke-CredentialInjection</CommandLine> <!-- Displays Windows vault credential objects including cleartext web credentials. -->
- 6
- <CommandLine name="Privilege Escalation" condition="contains">mimikatz</CommandLine> <!-- Mimikatz is an open-source application that allows users to view and save Kerberos tickets and hashes. -->
- 7
- </ProcessCreate>
- DLLs identified in both this paper and [10]: cryptbase.dll, imm32.dll, kernel32.dll, msctf.dll, ntdll.dll, sechost.dll, shell32.dll , user32.dll, wininet.dll
- DLLs identified only in this paper: cryptdll.dll, hid.dll, samlib.dll, vaultcli.dll, WinSCard.dll
6.2.5. Post Exploitation on Stored Passwords with LaZagne Project
6.2.6. Discussion upon Password Exploitation with LaZagne Project
- 1
- <ProcessCreate onmatch="include">
- 2
- <ParentImage condition="is">C:\Users\Administrator\Downloads\lazagne.exe</ParentImage>
- 3
- <ParentCommandLine condition="is">lazagne.exe windows</ParentCommandLine>
- 4
- <ParentCommandLine condition="is"> lazagne.exe mails</ParentCommandLine>
- 5
- <ParentCommandLine condition="is"> lazagne.exe project all</ParentCommandLine>
- 6
- </ProcessCreate>
7. Python_Evtx_Analyzer
- Memory mapping of massive Sysmon log files as inputs in .evtx form.
- Provision of basic arguments supporting a user-friendly command-line execution of the Python script’s source code.
- Parsing and transformation of the logs included in the .evtx file into an easily manipulated and analyzed .xml format.
- Custom header filtering of the .xml created file. This is based on pre-selected Sysmon’s Event ID tags, presented in tree-based form on the command line’s screen or stored externally to a .txt file.
- Manipulation of the tree-based .xml structure and filtering based on pre-configured features as enclosed in Sysmon’s config.xml.
- Enumeration of the identified LM events, alert message generation per attack denoting the number of identified malicious events and making an assumption of the type of potentially executed attack.
7.1. PeX Operation
| Algorithm 1 PeX’s arguments and folders initialization algorithm |
| Require: python install |
| Require: pip install , , , libraries |
| Require: import , , , , , |
| Require:, files in format |
| Require: Function def |
| 3: |
| if then |
| 6: else if then |
| end if |
| 9: for do |
| 12: |
| ▹ The header of every xml file is stored to the xmlHeaderOutput variable. |
| if then |
| 15: |
| else if then |
| 18: end if |
| end for |
| Algorithm 2 PeX’s evtx-to-xml transformation algorithm |
|
| Algorithm 3 PeX’s xml parsing and LM identification algorithm |
|
7.2. Dataset
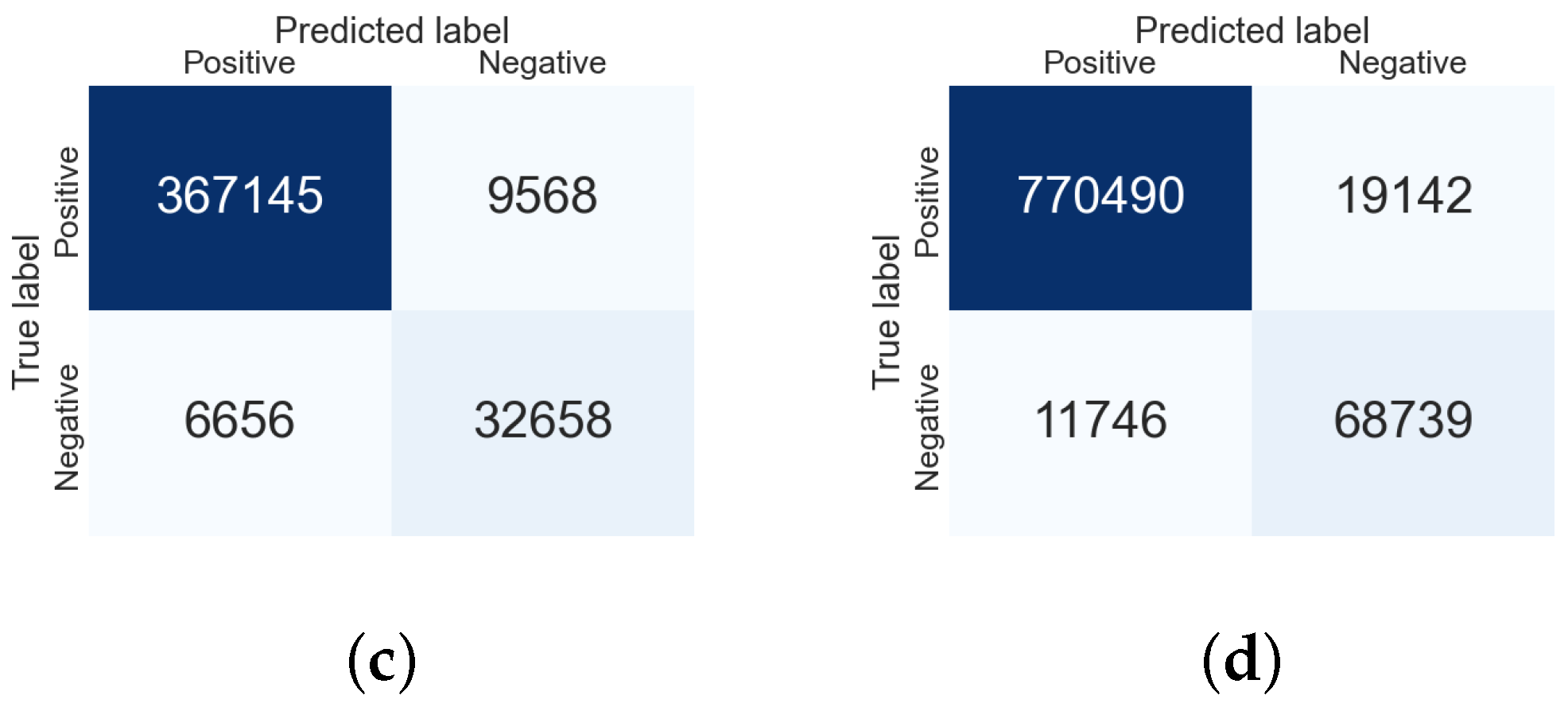
7.3. Evaluation
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| 5Ws | Who-When-Where-What-Why |
| Argparse | Argument Parser Python Library |
| API | Application Programming Interface |
| ARP | Address Resolution Protocol |
| CMD | Command Line |
| CME | CrackMapExec |
| CSIRT | Computer Security Incident Response Team |
| CSV | Comma-Separated Values |
| DLL | Dynamic Link Library |
| DOM | Document Object Model Interface |
| Domain SID | Domain Security Identifier |
| EDR System | Endpoint Detection and Response System |
| Event ID | Event Identification |
| evtx | Windows XML EventLog |
| FN | False Negative |
| FP | False Positive |
| GUID | Global Unique Identifier |
| I/O | Input/Output |
| IDE | Integrated Development Environment |
| IDS | Intrusion Detection System |
| IP | Internet Protocol |
| KDC | Kerberos Key Distribution Center |
| klist | Kerberos List |
| LSASS | Local Security Authority Subsystem Service |
| LTS | Long Time Support |
| MAC Address | Media Access Control Address |
| MMAP | Memory Mapped File Support Python Library |
| MSTSC | Microsoft Terminal Services Client |
| NMAP | Network Mapper |
| NTLM | Network Lan Manager |
| PeX | Python_Evtx_Analyzer |
| PtH | Pass the Hash |
| PtT | Pass the Ticket |
| RAM | Random Access Memory |
| RDP | Remote Desktop Protocol |
| SIEM | Security Information and Event Management |
| SMB | Service Message Block |
| SOHO | Small Office Home Office |
| STA | Station |
| Sysmon | System Monitoring |
| TN | True Negative |
| TP | True Positive |
| UAC | User Account Control |
| USB | Universal Serial Bus |
| VM | Virtual Machine |
| WIDS | Wireless Intrusion Detection Systems |
| Wi-Fi | Wireless Fidelity |
| xml | Extensible Markup Language |
Appendix A
Appendix A.1
| Tool | Tool Attack Utilization | COM Port | Sysmon-Event Log |
|---|---|---|---|
| PsExec | Remote command execution on clients and servers within a domain. | 135/tcp, 445/tcp, or a random high port | Event IDs 1,5 (ProcessCreate, ProcessTerminate), path: “%SystemRoot%/PSEXESVC.exe”, Images: “C:/Windows/PSEXESVC.exe”, “C:/Windows/services.exe”, “C:/Windows/wmiprsv.exe” User: “SYSTEM”, Additional Info: date, UtcTime the “Image: “C:/Windows/PSEXESVC.exe” was executed”. |
| WinRM | Target enumeration-investigation on the remote host via command execution. | 5985/tcp (HTTP) or 5986/tcp (HTTPS) | Event IDs 1,5 (ProcessCreate, ProcessTerminate), Images: “C:/Windows/System32/cscript.exe”, “C:/Windows/System32/svchost.exe”, “C:/Windows/System32/wsmprovhost.exe” |
| “C:/Windows/System32/mmc.exe” Additional Info: ProcessID, UtcTime, CommandLine, User. | |||
| smbexec | Execution of applications that are normally controlled by the bypassed User Account Control (UAC) as a user with administrator privileges. | - | Event IDs 1,5 (ProcessCreate, ProcessTerminate), Images: “C:/Windows/System32/smbexec.py”, “C:/Windows/System32/sdbinst.py” User: “SYSTEM”, Additional Info: “Process Start/End Time and Date (UTC), Process CommandLine, ProcessID, SDB File Used”. |
| smb_login (Metasploit) | Privilege Escalation within host or domain. | 445/tcp | Event IDs 1,5 (ProcessCreate, ProcessTerminate), path: “%SystemRoot%/PSEXESVC.exe”, Images: “C:/Windows/PSEXESVC.exe”, “C:/Windows/System32/cmd.exe”, “C:/Windows/System32/powershell.exe”, “C:/Windows/System32/net.exe”, “C:/Windows/System32/whoami.exe” |
| , Additional Info: Administrative privileges “//*/IPC$”, “//*/admin$”, “//*/c$” | |||
| Images - CommandLine-CurrentDirectory-Hashes-ParentImage-ParentCommandLine related to net.exe and whoami.exe. | |||
| Wannacry malware | Malware infection to leverage MS17-010 EternalBlue vulnerability on SMB file-sharing services. | 139/tcp, 445/tcp, 137–138/udp | Event IDs 1,2,5 (ProcessCreate, ProcessChange, ProcessTerminate), path: “%SystemRoot%/Wcry.exe”, “%SystemRoot%/taskce.exe” Images: “C:/Windows/Users/Desktop/Wcry.exe”, “C:/Windows/Users/Desktop/tasksche.exe”, “C:/Windows/Users/Desktop/r.wnry.exe”, “C:/Windows/Users/Desktop/s.wnry.exe”, “C:/Windows/Users/Desktop/t.wnry.exe”, “C:/Windows/Users/Desktop/u.wnry.exe”, “C:/Windows/Users/Desktop/taskse.exe”, “C:/Windows/Users/Desktop/taskdl.exe”, “C:/.../attrib.exe”, “C:/.../icacls.exe” |
| Additional Info:ProcessID: 3024, Files with extension “.WNCRYT” or “C://Users//...//Desktop//Eula.txt.WNCRYT” objects which denote ransomware’s expansion, CommandLine: “attrib +h”, “icacls . /grant Everyone:F /T /C /Q”. | |||
| BlueKeep (CVE-2019-0708) | Worm-like (Wannacry similiral) cybersecurity vulnerability of Windows Remote Desktop Protocol (RDP) and Services (RDS) which allows the remote execution of arbitrary malicious code. | 3389/tcp | Event IDs 1,2,5 (ProcessCreate, ProcessChange, ProcessTerminate) as in –, Event ID 3 (NetworkConnection), path: “%SystemRoot%/”, Images: “C:/Windows/System32/rdpv.exe”, “C:/Windows/System32/mstsc.exe”, “C:/Windows/System32/RTSApp.exe”, “C:/Windows/System32/ws_TunnelService.exe.exe”, “C:/Windows/System32/RemoteDesktopManagerFree.exe”, “C:/Windows/System32/RemoteDesktopManager.exe”, “C:/Windows/System32/RemoteDesktopManager64.exe”, “C:/Windows/System32/mRemote.exe”, “C:/Windows/System32/Terminals.exe”, “C:/Windows/System32/spiceworks-finder.exe”, “C:/Windows/System32/thor.exe”, “C:/Windows/System32/thor64.exe”, “C:/Windows/System32/reg.exe”, “C:/Windows/System32/chrome.exe” |
| Sysmon’s Additional Info: Administrative privileges “//*/IPC$”, “//*/admin$”, “//*/c$”, Images-CommandLine-CurrentDirectory - Hashes-ParentImage-ParentCommandLine-ProcessID-UtcTime, User related to the identified Images. |
Appendix A.2
| Tool | Tool Attack Utilization | COM Port | Sysmon-Event Log |
|---|---|---|---|
| PtH (PowerShell Invoke-Mimikatz) | Credential theft and Lateral Movement technique in which the adversary leverages Windows NTLM hash without cracking it to authenticate as legit. | 445/tcp | Event IDs 1,2,5 (ProcessCreate, ProcessChange, ProcessTerminate) as in – of Table A1, Event ID 3 (NetworkConnection), Event ID 10 (ProcessAccess), Event ID 11 (FileCreate), Event ID 22 (DNSEvent (DNS query)), Event ID 13 (RegistryEvent (Value Set)), path: “%SystemRoot%/”, “%SystemRoot%/PSEXESVC.exe”, ParentImage: “C:/Users/Administrator/Desktop/mimikatz_trunk /x64/mimikatz.exe”, “C:/Windows/system32/sppsvc.exe” TargetImage: “C:/Windows/System32/lsass.exe”, “C:/Windows/System32/lsass.exe”, “C:/Windows/System32/reg.exe”, “C:/Windows/System32/svchost.exe”, “C:/Windows/PSEXESVC.exe”, “C:/Windows/services.exe”, “C:/Windows/wmiprsv.exe” GrantedAccess: “0 × 1010”, “0 × 1410”, “×1438”, “×1438a”, “0 × 1FFFFF”, “0 × 143a”, CommandLine: “sekurlsa”, “mimikatz”, “reg SAVE”, “dumpcr”, Sysmon’s Additional Info: Administrative privileges “//*/IPC$”, “//*/admin$”, “//*/c$”, Images-CommandLine-CurrentDirectory-Hashes-ParentImage- ParentCommandLine-ProcessID-UtcTime, User related to the identified Images, TargetFilename: “C:/Users/Administrator/Desktop/.../filename.kirbi”, DNS QueryName: “sysmon_set (or the desired name of the targeted domain)” |
| PtT, Golden Ticket, Silver Ticket | Capturing the Domain Administrator Privilege and Account Credentials. Leverages an unauthorized Kerberos ticket that is valid for an arbitrary period and grants access without additional authentication. | 445/tcp | Event IDs 1,2,5 (ProcessCreate, ProcessChange, ProcessTerminate), Event ID 3 (NetworkConnection), Event ID 10 (ProcessAccess), Event ID 11 (FileCreate), Event ID 22 (DNSEvent (DNS query)), Event ID 13 (RegistryEvent (Value Set)), path: “%SystemRoot%/”,“%SystemRoot%/PSEXESVC.exe”, as in – of Table A1, ParentImage: as in –, plus, C:/Windows/System32/klist.exe, C:/Windows/mimikatz.exe, “C:/Windows/PSEXESVC.exe”, CommandLine: “sekurlsa”, “mimikatz”, “reg SAVE”, “dumpcr”, “Get-Keystrokes”, “Get-TimedScreenshot”, “Get-VaultCredential”, “Invoke-CredentialInjection”, “Invoke-CredentialInjection” |
| LaZagne | Open source application used for passwords exploitation which are stored on a local targeted host. | 3389/tcp | Event IDs 1,2,5 (ProcessCreate, ProcessChange, ProcessTerminate), Event ID 10 (ProcessAccess), path: “%SystemRoot%/”,“%SystemRoot%/PSEXESVC.exe”, ParentImage: “C:/Windows/System32/lazagne.exe”, CommandLine: “lazagne.exe windows”, “... sysadmin, mail, project mail, project databases, project windows, project all” |
| Privilege Escalation | The basis of each Lateral Movement attack. Target acquisition, weak points enumeration, access gained within the security perimeter of a domain, gradual escalation of privileges and extension of the Lateral Movement of the adversary. | 80, 53, 25, 110, 143, 139, 445, 3389, 6000/TCP | Event IDs 1,2,5 (ProcessCreate, ProcessChange, ProcessTerminate), CommandLine: “Get-Keystrokes”, “Get-TimedScreenshot”, “Get-VaultCredential”, “Invoke-CredentialInjection”, “mimikatz” |
References
- MITRE. Lateral Movement-The Adversary Is Trying to Move through Your Environment. Mitre, 12 July 2019. [Google Scholar]
- Smiliotopoulos, C.; Barmpatsalou, K.; Kambourakis, G. Python_Evtx_Analyzer (PeX-v1). Available online: https://github.com/ChristosSmiliotopoulos/Python_Evtx_Analyzer.git (accessed on 25 June 2022).
- Coordination, J. Detecting Lateral Movement through Tracking Event Logs; JPCERT Coordination Center: Tokyo, Japan, June 2017. [Google Scholar]
- Russinovich, M.; Garnier, T. Sysmon v13. 22. Available online: https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=90022 (accessed on 25 June 2022).
- Coordination, J. Detecting Lateral Movement through Tracking Event Logs (Ver. 2); JPCERT Coordination Center: Tokyo, Japan, December 2017. [Google Scholar]
- Viasat. KaSat-Network Cyber Attack Overview. Available online: https://www.viasat.com/about/newsroom/blog/ka-sat-network-cyber-attack-overview/ (accessed on 4 April 2022).
- Mavroeidis, V.; Jøsang, A. Data-driven threat hunting using sysmon. In Proceedings of the 2nd International Conference on Cryptography, Security and Privacy, Guiyang, China, 16–19 March 2018; pp. 82–88. [Google Scholar]
- Mavroeidis, V.; Bromander, S. Cyber Threat Intelligence Model: An Evaluation of Taxonomies, Sharing Standards, and Ontologies within Cyber Threat Intelligence. In Proceedings of the 2017 European Intelligence and Security Informatics Conference (EISIC), Athens, Greece, 11–13 September 2017; pp. 91–98. [Google Scholar] [CrossRef] [Green Version]
- Berady, A.; Jaume, M.; Tong, V.V.T.; Guette, G. From TTP to IoC: Advanced Persistent Graphs for Threat Hunting. IEEE Trans. Netw. Serv. Manag. 2021, 18, 1321–1333. [Google Scholar] [CrossRef]
- Matsuda, W.; Fujimoto, M.; Mitsunaga, T. Real-Time Detection System Against Malicious Tools by Monitoring DLL on Client Computers. In Proceedings of the 2019 IEEE Conference on Application, Information and Network Security (AINS), Penang, Malaysia, 19–21 March 2019; pp. 36–41. [Google Scholar] [CrossRef]
- Juwono, J.T.; Lim, C.; Erwin, A. A comparative study of behavior analysis sandboxes in malware detection. In Proceedings of the International Conference on New Media (CONMEDIA), Jakarta, Indonesia, 27 November 2015; pp. 73–78. [Google Scholar]
- Narouei, M.; Ahmadi, M.; Giacinto, G.; Takabi, H.; Sami, A. DLLMiner: Structural mining for malware detection. Secur. Commun. Netw. 2015, 8, 3311–3322. [Google Scholar] [CrossRef]
- Rajesh, P.; Ismail. Ismail. B, M.; Alam, M.; Tahernezhadi, M. Network Forensics Investigation in Virtual Data Centers Using ELK. In Proceedings of the 2021 International Symposium on Electrical, Electronics and Information Engineering, Online, 19–21 February 2021; pp. 175–179. [Google Scholar]
- Jain, U. Lateral Movement Detection Using ELK Stack. Ph.D. Thesis, University of Houston, Houston, MA, USA, 2018. [Google Scholar]
- El-Hadidi, M.G.; Azer, M.A. Detecting Mimikatz in Lateral Movements Using Mutex. In Proceedings of the 2020 15th International Conference on Computer Engineering and Systems (ICCES), Cairo, Egypt, 15–16 December 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Ki, Y.; Kim, E.; Kim, H.K. A Novel Approach to Detect Malware Based on API Call Sequence Analysis. Int. J. Distrib. Sens. Netw. 2015, 11, 659101. [Google Scholar] [CrossRef] [Green Version]
- Ho, G.; Dhiman, M.; Akhawe, D.; Paxson, V.; Savage, S.; Voelker, G.M.; Wagner, D. Hopper: Modeling and Detecting Lateral Movement. In Proceedings of the 30th USENIX Security Symposium (USENIX Security 21); USENIX Association: Berkeley, CA, USA, 2021; pp. 3093–3110. [Google Scholar]
- Bhasin, H.P.S.; Ramsdell, E.; Alva, A.; Sreedhar, R.; Bhadkamkar, M. Data center application security: Lateral movement detection of malware using behavioral models. SMU Data Sci. Rev. 2018, 1, 10. [Google Scholar]
- Coffey, K.; Smith, R.; Maglaras, L.; Janicke, H. Vulnerability analysis of network scanning on SCADA systems. Secur. Commun. Netw. 2018, 2018, 3794603. [Google Scholar] [CrossRef]
- Mulder, J.; Stingley, M. Mimikatz Overview, Defenses and Detection. SANS Institute, February 2016; p. 1–18. Available online: https://www.sans.org/white-papers/36780/ (accessed on 15 April 2022).
- Ussath, M.; Jaeger, D.; Cheng, F.; Meinel, C. Advanced persistent threats: Behind the scenes. In Proceedings of the IEEE 2016 Annual Conference on Information Science and Systems (CISS), Princeton, NJ, USA, 15–18 March 2016; pp. 181–186. [Google Scholar]
- Kazanciyan, R.; Hastings, M. Investigating Powershell Attacks; Black Hat: San Francisco, CA, USA, 2014; pp. 1–25. [Google Scholar]
- Steven, F. Revisiting Remote Desktop Lateral Movement. Medium. 2022. Available online: https://posts.specterops.io/ (accessed on 12 April 2022).
- logPoint. MITRE ATT&CK Analytics—Alert Rules Latest Documentation. 2022. Available online: https://docs.logpoint.com/docs/alert-rules/en/latest/MITRE.html (accessed on 15 April 2022).
- Goet, M. Protect Yourself against #BlueKeep Using Azure Sentinel and Defender ATP. Medium. 2022. Available online: https://medium.com/@maarten.goet/protect-yourself-against-bluekeep-using-azure-sentinel-and-defender-atp-d308f566d5cf (accessed on 12 April 2022).
- SandBoxCloud, J. Windows Analysis Report. SandBoxCloud. 2022. Available online: https://www.joesandbox.com/analysis (accessed on 24 May 2022).
- Sandbox, F. Free Automated Malware Analysis Service, “RemoteDesktopManagerFree.exe”. Sandbox. 2022. Available online: https://www.hybrid-analysis.com/sample/b26ede46a0be62f361b4a28d2e67fa2e2f35c9bbc995ae84a2c0c7f4141f65b0?environmentId=100 (accessed on 17 April 2022).
- Sorensen, S. Remote Desktop Manager Free. LO4D.com. 2022. Available online: https://remote-desktop-manager-free.en.lo4d.com/windows (accessed on 18 May 2022).
- Bezverkhyi, A. Proactive Detection Content: CVE-2019-0708 vs ATT&CK, Sigma, Elastic and ArcSight-SOC Prime. SOC Prime. 2022. Available online: https://socprime.com/blog/proactive-detection-content-cve-2019-0708-vs-attck-sigma-elastic-and-arcsight (accessed on 15 May 2022).
- s0i37—HackMag. Lateral Movement Guide: Remote Code Execution in Windows. Available online: https://hackmag.com/security/lateral-guide/ (accessed on 26 May 2022).

| Related Work | ||
|---|---|---|
| Title | Year | Summary |
| A novel approach for detecting malware based on API call sequence analysis [16] | 2015 | Detection of malware API call patterns towards the identification of behavioral anomaly signatures |
| Detecting lateral movement through tracking event logs (v1 & 2) [3,5] | 2017 | Execution of LM through well-known penetration testing tools. Collection of logs with Sysmon and MS Windows Audit Policy. Categorization of logs per attack and proposition of optimal MS Windows infiltration settings for effective identification of LM activity. |
| Data-driven threat hunting using Sysmon [7] | 2018 | Data-driven threat classification methodology based on aggregated logs created by Sysmon. Proposed a threat analysis system, which is based on the developed by the authors CTI ontology. |
| Lateral movement detection using ELK stack [14] | 2018 | A way to generate event logs with Sysmon related to the execution of various LM attacks and the associated malicious tools on MS Windows-based environments. Implementation of ELK stack towards the analysis of possible abnormalities in the collected logs due to the existence of LM. |
| Real-time detection system against malicious tools by monitoring DLL on client computers [10] | 2019 | Proposed a DLL-oriented method for malicious file detection through logs collected by Sysmon [4]. Common DLL list per malicious tool, independent of MS Windows OS version. |
| Detecting Mimikatz in lateral movements using Mutex [15] | 2020 | APT detection of Mimikatz while utilized in LM. Implementation of Mutex memory objects in conjunction with DLL files analysis. Mimikatz’s misidentification while deliberately obfuscated. |
| From TTP to IoC: Advanced persistent graphs for threat hunting [9] | 2021 | Threat hunting model which evaluates Sysmon’s logs from both an offender’s and defender’s perspective. Based on indicators of compromise, proactive threat detection is possibly enhanced. A high rate of false positives due to the absence of rule-based Sysmon’s configuration. |
| Hopper: Modeling and detecting lateral movement [17] | 2021 | System for LM attack detection based on real-life generated logs. Login activity is tracked and outlined through a graph of interrelated logins among the implicated hosts to conclude in the detection of anomalies among logins referring to LM. |
| Network forensics investigation in virtual data centers using ELK [13] | 2021 | Generating log records with Logstash. Network forensic analysis via the implementation of Elastic Search and towards the identification of RDP LM-related attacks, Ransomware, Data Exfiltration, etc., as part of a criminal investigation. |
| Technical Characteristics and Utilization of Each STA (Physical and VM) | |||||||
|---|---|---|---|---|---|---|---|
| Station | Type | Operating System | Kernel_Version | CPU/RAM | IP_Address | MAC_Address | Username |
| AP | Wireless_AP | SERCOM_Firmware | 09022001.00.031 OTE2 | - | 80.107.57.231, 192.168.1.1 | 7C:8F:DE:46:66:11 | N/A |
| Client STA 1 | VM | Ubuntu 20.0.4 | 5.8.0-53-generic-x64 | VM dual_core, 2 GB | 192.168.1.6 | 08:00:27:4e:4e:e6 | adminchr |
| Client STA 2 | VM | Kali 2021.1 | 5.10.0-kali7-amd64 | VM dual_core, 2 GB | 192.168.1.11 | 08:00:27:3e:b5:a7 | nicksaitas |
| Client STA 3 | VM | Win10 Eval. x64 | 2004 | VM dual_core, 2 GB | 192.168.1.7 | 08:00:27:3d:c5:a9 | chr.smilio |
| Client STA 4 | Laptop | Win10 Home x64 | 2004 | i7-9750H CPU, 16 GB DDR4 | 192.168.1.28 | 98:AF:65:32:E8:21 | laptop-ropr18ak_chrsm |
| Windows 2019 Server | VM | Win2019 Server x64 | 1809 | VM dual_core, 2 GB VM RAM | 192.168.1.8 | 08:00:27:4f:d3:32 | christossmiliotopoulos |
| Client STA 5 | Smartphone | iOS 15.0 | 14.4.2 | Hexa-core, 64GB RAM | 192.168.1.3 | 06:16:EC:81:F9:68 | iPhone-Christos |
| Client STA 6 | Smartphone | Android 9 | Knoxx 3.3 | Exynos 7 Octa 7885 | 192.168.1.13 | 3C:DC:BC:7F:73:B7 | A8-Maraki |
| No. | Event ID | Description | Subsection |
|---|---|---|---|
| 1 | Event ID 1 | Process creation | Section 6.1 and Section 6.2 |
| 2 | Event ID 2 | A process changed a file creation time | Section 6.1.3, Section 6.1.4 and Section 6.2 |
| 3 | Event ID 3 | Network connection | Section 6.1.4, Section 6.2.1, Section 6.2.2 and Section 6.2.3 |
| 4 | Event ID 5 | Process terminated | Section 6.1 and Section 6.2 |
| 5 | Event ID 10 | Process Access | Section 6.2.1, Section 6.2.2, Section 6.2.3 and Section 6.2.5 |
| 6 | Event ID 11 | FileCreate | Section 6.2.1, Section 6.2.2 and Section 6.2.3 |
| 7 | Event ID 13 | RegistryEvent (Value Set) | Section 6.2.1, Section 6.2.2 and Section 6.2.3 |
| 8 | Event ID 22 | DNSEvent (DNS query) | Section 6.2.1, Section 6.2.2 and Section 6.2.3 |
| 9 | Event ID 23 | FileDelete (File Delete archived) | Section 7.2 * |
| 10 | Event ID 255 | Event ID 255: Error | Section 7.2 * |
| Tested Subsets | Sysmon Event IDs (Logs) |
|---|---|
| Normal | ≈80,000 |
| NormalVsMalicious01 | ≈290,000 |
| NormalVsMalicious02 | ≈415,000 |
| FullSet | ≈870,000 |
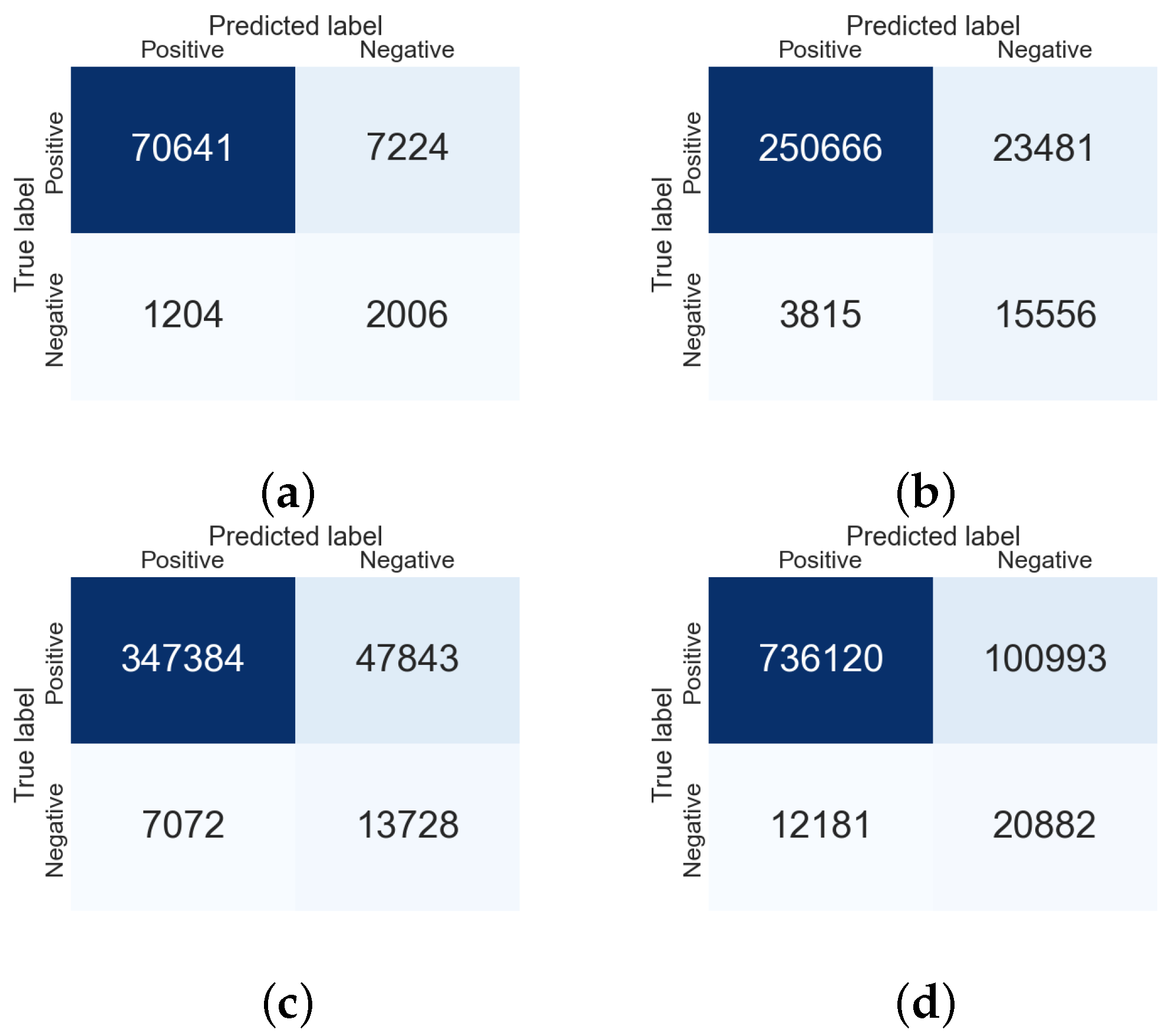
| Attack Vector | Subset | No. of Logs | TP (%) | TN (%) | FP (%) | FN (%) |
|---|---|---|---|---|---|---|
| Normal Network Traffic | Normal | 80,274 | 88.0% | 2.5% | 9.0% | 1.5% |
| Remote Services Exploitation + Normal Net Traffic | NormalVsMalicious01 | 293,520 | 85.4% | 5.3% | 8.0% | 1.3% |
| Hashing Pass Exploitation + Normal Net Traffic | NormalVsMalicious02 | 416,029 | 83.5% | 3.3% | 11.5% | 1.7% |
| Total Attacking Vector + Normal Net Traffic | FullSet | 870,119 | 84.6% | 2.4% | 11.6% | 1.4% |
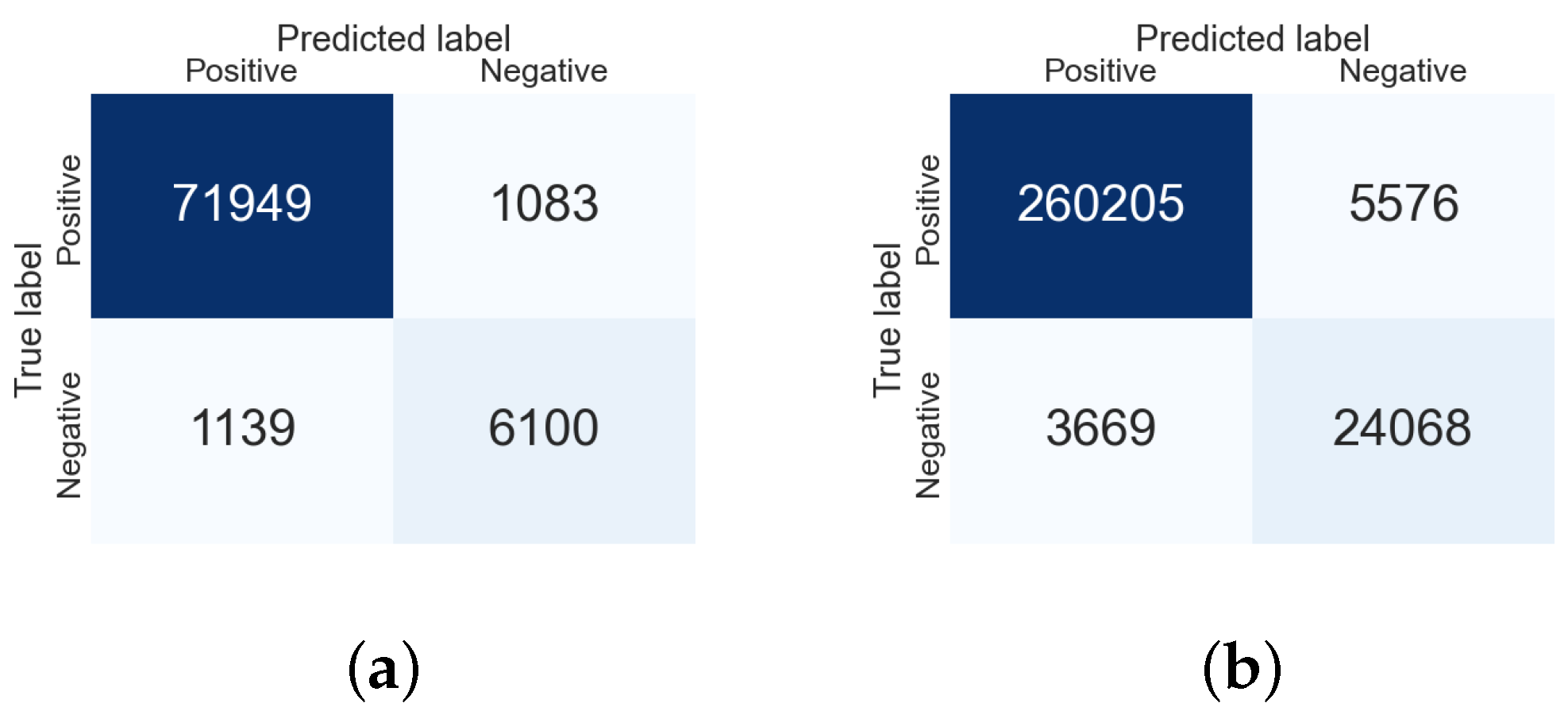
| Subset | No. of Logs | TP (%) | TN (%) | FP (%) | FN (%) |
|---|---|---|---|---|---|
| Normal | 80,274 | 89.63% | 7.60% | 1.35% | 1.42% |
| NormalVsMalicious01 | 293,520 | 88.65% | 8.20% | 1.90% | 1.25% |
| NormalVsMalicious02 | 416,029 | 88.25% | 7.85% | 2.30% | 1.60% |
| FullSet | 870,119 | 88.55% | 7.90% | 2.20% | 1.35% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Smiliotopoulos, C.; Barmpatsalou , K.; Kambourakis, G. Revisiting the Detection of Lateral Movement through Sysmon. Appl. Sci. 2022, 12, 7746. https://doi.org/10.3390/app12157746
Smiliotopoulos C, Barmpatsalou K, Kambourakis G. Revisiting the Detection of Lateral Movement through Sysmon. Applied Sciences. 2022; 12(15):7746. https://doi.org/10.3390/app12157746
Chicago/Turabian StyleSmiliotopoulos, Christos, Konstantia Barmpatsalou , and Georgios Kambourakis. 2022. "Revisiting the Detection of Lateral Movement through Sysmon" Applied Sciences 12, no. 15: 7746. https://doi.org/10.3390/app12157746
APA StyleSmiliotopoulos, C., Barmpatsalou , K., & Kambourakis, G. (2022). Revisiting the Detection of Lateral Movement through Sysmon. Applied Sciences, 12(15), 7746. https://doi.org/10.3390/app12157746







