Abstract
Most Internet of Things (IoT) resources are exposed to security risks due to their essential functionality. IoT devices, such as smartphones and tablets, have a limited network, computation, and storage capacity, making them more vulnerable to attacks. In addition, the huge volume of data generated by IoT devices remains an open challenge for existing platforms to process, analyze, and discover underlying trends to create a convenient environment. As a result, to deliver acceptable services, a new solution is necessary to secure data accountability, increase data privacy and accessibility, and extract hidden patterns and usable knowledge. Moving the Internet of Things to a distributed ledger system might be the most effective way to solve these issues. One of the most well-known and extensively utilized distributed ledger systems is the blockchain. Due to its unique properties, such as privacy, accountability, immutability, and anonymity, blockchain technology has recently attracted a lot of interest. Using IoT in conjunction with blockchain technology can bring several benefits. This paper reviews the current state of the art different BIoT architectures, with a focus on current technologies, applications, challenges, and opportunities. The test findings prove that the decentralized authentication platform-based blockchain-based IoT (BIoT) device-to-device architecture has a significantly higher throughput than the gateway-based architecture. To encrypt the elliptical curve cryptographic (ECC) and to generate keys, the Chinese remainder theorem (CRT)-based scheme is proposed and compared with the secure hash algorithm (SHA-256). Finally, ECC-CRT is used to access system performance in terms of latency, throughput, and resource consumption, simulated through the Contiki Cooja (CC) simulator, and alter orderer and peer nodes for performance study in BIoT. A comprehensive analysis and simulation results show that the proposed scheme is secure against a variety of known attacks, including the man-in-the-middle (MiM) attack, and outperforms the SHA-256 cryptographic algorithm. Moreover, the significance of blockchain and IoT, as well as their analysis of proposed architecture, is discussed. This paper will help readers and researchers understand the IoT and its applicability to the real world.
1. Introduction
The Internet and technology have advanced so quickly that the entire world is experiencing the fourth industrial revolution (Industry 4.0) [1] in all aspects of humanity, with the Internet of Things (IoT) playing a significant role in its widespread adoption. The Internet of Things is a network of interconnected physical objects (e.g., devices, machines, and appliances) equipped with sensors, software, and electronics and assigned unique identifiers. IoT sensors can also exchange data over the Internet without the need for human intervention. The IoT can generate information about the associated objects, examine them, and make decisions. It has enormous potential to provide various elating services across a wide range of industries, including industry, healthcare, smart homes, smart cities, social media, and supply chains [2]. The IoT has made it possible for small, low-power devices to connect to the Internet and exchange massive amounts of data, enabling a new generation of services. Due to security concerns stemming from the sensitive nature of the data handled by such applications, the potential for IoT-based applications has not been fully realized to date. However, blockchains impose a significant computational demand, which is difficult to meet in a resource-constrained IoT scenario. Although IoT devices are currently unable to participate in a blockchain consensus protocol, it is anticipated that they will be required to do so in the future [3]. Hardware acceleration of the protocol’s most computationally intensive part, which typically consists of massive computation of the SHA-256 hash function, is one way to achieve this. Because SHA-256 is used in many security schemes, such as hash-based message authentication code [4] and the digital signature algorithm [5], the hardware acceleration of SHA-256 can benefit the capabilities of IoT applications in other ways. Indeed, SHA-256 is one of the most widely used cryptographic hash functions today, with applications in security-critical areas such as finance and cloud computing, in addition to the IoT.
Blockchain is a decentralized platform in which all parties keep a copy of each transaction [6]. The transactions are transparent, and any changes can be quickly identified. Consider a smart city where parking spaces are displayed in real-time to users. Sensors update the centralized database when they detect a free parking space. The database system administrator can reserve a parking space for himself without disclosing it to others. In this case, the data from the sensor integrity are compromised. The goal of a blockchain network of interconnected devices is to eliminate the need for a third party and, as a result, ensure that the sensor real-time data reach every node in the network without being tampered with. Furthermore, the blockchain enables IoT devices to communicate with one another and make decisions on their own.
Ethereum Blockchain is a platform for developing decentralized applications, in addition to digital currencies, by executing scripting language code known as smart contracts. Such code is run on a virtual machine known as the Ethereum Virtual Machine (EVM), which acts as an abstraction layer between the code and the machine itself [7]. While Bitcoin is considered a currency, Ethereum’s currency is Ether, which can be used by businesses to create decentralized applications (DApps), and changing the state of a smart contract in the blockchain requires transaction fees priced in Ether.
IoT implementations are currently largely centralized, which raises security concerns such as a single point of failure, trust, and privacy. Furthermore, it limits their scalability, highlighting the need for a decentralized trust mechanism in the IoT. Without the need for a central authority, the blockchain can provide trust through cryptographic techniques. Several blockchain-based IoT applications have recently gained traction due to their potential to improve security and privacy. According to a recent Juniper Research study [8], combining IoT and blockchain in the food industry can save billions of dollars by lowering retailer costs, simplifying regulatory compliance, and combating fraud.
This paper’s main contributions are:
- It discusses the latest papers investigating the intermingling of blockchain technology applications in the IoT.
- It discusses a summary of the blockchain infrastructure chosen and implemented for IoT in the literature.
- It analyses various problems of BIoT and how to address these issues using IoT inventions.
- It develops a novel energy-efficient and secure method for collecting and managing sensors’ data in BIoT applications.
- It develops a secure BIoT-device-only architecture that ensures data confidentiality, transparency, and authenticity.
- It proposes a new ECC-CRT algorithm to enhance performance in terms of latency, throughput, and resource consumption.
- It develops a BIoT-based architecture that achieves outstanding performance by meeting all the necessary security requirements.
- The proposed architecture for low-power IoT devices based on the Ethereum blockchain solves the power issue in IoT devices while communicating, validating transactions, and providing security.
2. Literature Survey
Following the presentation of the fundamentals of the IoT system and blockchain technology, a comprehensive review of integrating the blockchain with the IoT system will be presented, emphasizing the benefits of the integration and how the blockchain can resolve IoT system issues. Blockchain is a distributed database that can keep track of transactions in the form of blocks within peer-to-peer (P2P) network nodes. The cryptographic hash function is used to connect these blocks as a chain. As a result, attackers cannot alter these records because they are encrypted and distributed among P2P nodes. There are numerous blockchain platforms available that enable developers to create and program agreements, policies, and rules for users within a distributed blockchain network. These programs are known as smart contracts. The use of smart contracts eliminates the need for third-party judgment. Because of its numerous advantages, blockchain technology can be applied to domains other than cryptocurrencies, such as identity management, data storage management, data trading, and so on [9].
2.1. Background, Definitions, and Cryptographic Algorithms
The Internet of Things (IoT) has emerged as one of the most innovative technologies for connecting virtual and physical objects over the Internet, thus opening up a slew of new possibilities in a variety of fields. The unexpected growth of the Internet of Things system has opened up new opportunities in a variety of fields. However, there are still some issues with the IoT that act as a roadblock to the promised widespread adoption of IoT devices. The lack of trust and confidence is one of these issues. In the current IoT centralized model, a third-party central authority has complete control over data collection and processing from various IoT objects, with no clear restrictions on how the data are used. It is not easy to integrate blockchain into an IoT system. The first and most crucial step is to decide which blockchain platform will be used to combine IoT and blockchain technology. The most commonly used platforms for implementing blockchain with IoT are Ethereum, Hyperledger, and IOTA. They are not only open-source platforms, but they can also provide key capabilities such as block connectivity, and the cryptographically secure hashing of different transactions in single blocks, advanced marks, consensus, and smart contracts.
Asymmetric-key algorithms and hash functions are the two types of cryptographic algorithms used in blockchains. Hash functions are employed to give each participant the capability of a single view of the blockchain. The SHA-256 hashing method is commonly used as the hash function in blockchains. Each transaction is hashed before being bundled into a block on a blockchain. By storing a hash of the data in the previous block, hash pointers connect each block to the one before it. Data on the blockchain are immutable because each block is linked to the one before it. Because of the hashing function, any modification in a transaction generates a completely different hash, which affects the hashes of all the following blocks [10].
2.2. Related Work
IoT suggests that physical devices will have the alternative of participating and passing on through introduced structures. This will incite a passed-on arrangement of devices that can talk with the two individuals and each other. This will affect the influence of both family and business streams. One significant area of application is in masterminding the store’s organization. A store’s goal is to move a thing or help from a creator to a customer, and in an ideal world, this should be done as competently as is reasonable. A generation arrangement entails a business association that masterminds the movement of people, activities, information, and resources from one unit to the next [11]. Moving IoT components from the cloud to edge hosts reduces overall network traffic and, as a result, reduces latency. Provisioning IoT services on IoT edge devices, on the other hand, poses new challenges in terms of system design and maintenance. The use of software-defined IoT components in the form of virtual IoT resources is one option. As a result, the thing/device layer and the core IoT service layer can be exposed as collections of microservices that can be distributed to a diverse set of hosts [12].
Approaches to creating permission blockchain situations in which character and quality organization are worked on for both customers and devices are being proposed by the authors [13]. The proposed paradigm is intriguing; nevertheless, no implementation is currently underway. Overcoming the necessity of major blockchains’ time-consuming proof-of-work (PoW) architecture for shaping and incorporating data squares is a significant research problem not only for the IoT social order. Casper, a proof-of-stake (PoS) version of Ethereum, will be published, promising to be more powerful and secure over time [14]. To keep away from key altering by the administration supplier (which may be included) [15], two confirmations were performed before sending any message: different customers confirmed the collector open key when associating with the first client, and this key did not change unusually. Indistinguishable answers for BIoT gadgets have been demonstrated, utilizing blockchain innovation to reach executives and cultivate their personalities, demonstrating that the blockchain is protected from imitation assaults and Internet protocol (IP) mocking [16].
Declarations are likewise fundamental in guaranteeing security on the Internet. Therefore, specialists in authentication utilizing open keyframes must give trust to outsiders [17]. Nonetheless, such specialists have affirmed their disappointment with specific events and afterward, making recently exhibited endorsements invalid. Because of utilizing an appropriate framework dependent on Merkle, having a hash tree allows outsiders to confirm and review if a testament is legitimate [18]. The other privacy highlight is the accessibility, even though it is truly considered the least difficult to be accomplished by the blockchain, which is structured by configuration to be distributed in frameworks, enabling them to keep utilizing them in any event, when a few hubs are enduring an onslaught. In any case, accessibility might be undermined by different sorts of assaults [19]. The most dreaded threat is the 51% threat, where one excavator controls an entire blockchain and performs exchanges at will. In this situation, the information is accessible, but the accessibility for performing exchanges might be halted by the assailant that manages the blockchain. This kind of assault affects the honesty of information [20].
Blockchain clients are known by their hash or their open key. It suggests that name lessens are not accomplished because entire exchanges are shared; there is the potential for outsiders to break down and recognize these exchanges and induce the members’ characters [21]. Protection has become increasingly complicated in BIoT conditions because BIoT gadgets may discover extraordinary client information that can be saved in a blockchain whose security requirements differ from one country to the next [22]. As a result, in contrast to regular online installments, which were frequently only observed by executing parties and a go-between (for example, money-related governments and organizations), straightforward exchanges advanced by blockchain pose a security challenge. For example, multichain provides an explanation for arranging individual blockchains that ensures that the events on the blockchain can be checked by selected individuals [23]. Blending strategies may improve protection likewise. Such techniques may aggregate correspondence from various IoT procedures and generate activities or various exchanges with various targets that were not previously associated with unique systems. These strategies extend security, yet they are not finished. In this way, they might be deanonymized over numerical discovery assaults.
Furthermore, the blending office must be kept secret, as a malicious blender may delineate clients and, in the case of monetary exchanges, may prevent the taking of coins. An incredible administration framework was produced to liberate clients from dealing with the encryption key [24]. Protection can also be extended to any information-demonstrating systems, such as those used by Zerocoin, Zerocash, or Zcash [25]. Blockchain technology is being employed in a variety of non-financial industries, including by modum.io AG and several other non-financial start-ups [26]. A proposal was made to merge Ethereum-based Internet of Things networks into a blockchain-based decentralized framework. The platform will need a front-end application that can be defused with any web server, as well as a smart contract that will be deployed on a private blockchain network made up of connected IoT peer-to-peer (P2P) networks that operate as entire Ethereum nodes [27].
The goal is to provide blockchain-based applications and alternatives for conducting background checks using the Ethereum block circle [28]. For the testbed of networked, simulated Raspberry Pi devices, a unique way of simulating an IoT ecosystem was recommended using the network emulator for mobile universes (NEMU), which was based on the well-known quick emulator (QEMU) framework [29]. The transport layer security (TLS) protocol was tested by Rivest–Shamir–Adleman (RSA) in terms of security measures, scalability, power consumption, and data usage. The results were compared to ECC. Key length in ECC provides a reasonable security level. TLS is mostly applied at the transmission layer in wired and mobile networks and is used to provide secure communication. Its specific mechanisms aid in the maintenance of data confidentiality, integrity, and privacy [30].
The encryption scheme is based on ECC and is designed specifically for cloud services that provide storage. Because it is based on ECC, the results showed that it reduces the computational overhead associated with data encryption. Other traditional security schemes, such as RSA, are also compared to the proposed encryption scheme performance. In terms of the selected performance characteristics, the proposed scheme outperforms the other schemes [31]. RSA and data encryption standard (DES) encryption techniques are used for encrypting data frames. DES is a mathematical algorithm used for encrypting and decrypting coded information. It is computationally efficient and is executed by slow processors. The 64-bit data are encrypted and decrypted by 56-bit keys. RSA is used to improve cryptography and privacy [32]. The developers proposed a new system of updated blockchain models appropriate for IoT applications, based on their distributed existence and other network privacy and security features. The blockchain data flow is then linked to the IoT technology deployment based on the number of traceable resource units. Then, using consistent and reliable data for shelf life modification and fuzzy logic for quality degradation evaluation, decision support in the food supply chain may be established [33].
Software-defined blockchain architecture is proposed for the realization of complex blockchain configurations to fix this. A consensus feature virtualization technique of application-aware workflow is then proposed, which can abstract and handle several tools of consensus. Next, a smart transfer-learning-based system is designed to apply the study of the application-layer packet and to efficiently handle virtualized consensus services. The results of the experiment suggest the viability of the suggested regime. This work is essential to improving the flexibility and extensibility of blockchains in the IoT [34]. If blockchain functionality can be balanced to suit it, the IoT can offer several advantages. As such, several existing IoT issues can be overcome. However, several problems may also be imposed by the introduction of blockchains for the IoT. A study identified five major components that should be addressed while designing the blockchain architecture for the IoT [35]. This study focused on the possibilities of integrating blockchain and IoT technologies, resulting in the concept of BIoT, as well as the benefits and difficulties that such consolidation might offer [36]. Several current smart home Internet of Things automation systems provide a valid evaluation of the environment and analyze the feasibility of blockchain technologies for this case. Due to the vast amount of status, event, and usage data, another option anticipates private local blockchains being implemented in the home area network, although not necessarily for every appliance-generated transaction. A comparative analysis of BIoT technologies is shown in Table 1.

Table 1.
Comparative analysis of BIoT technologies.
Moreover, Table 1 categorizes recent studies which investigated the integration of blockchain with the IoT which can help researchers to track recent studies and publications that adopted a blockchain with the IoT in a certain domain. This paper proposed ECC-CRT to enhance performance in terms of latency, throughput, and resource consumption.
3. Proposed BIoT Architecture
Various researchers have proposed various architectures such as healthcare-based architecture, smart home-based architecture, fog computing (FC)-based architecture, and so on.
The IoT area would include a broad variety of technologies based on different architectures. Thus, it is impossible to use a single reference architecture as a blueprint for all possible concrete implementations. While it is acknowledged that a specific paradigm exists, other models with similar characteristics will coexist on the Internet. The architecture can be defined in this context as a framework for specifying physical components, functional arrangements, networking, and operational principles, procedures, and data formats used in its operation. As shown in Figure 1, the IoT design of patented protocols is also extremely scalable to support a variety of network implementations [36].
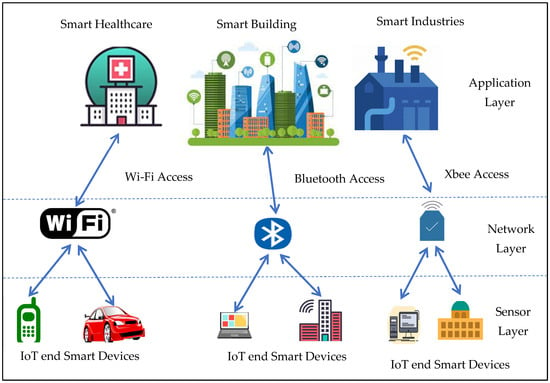
Figure 1.
IoT architecture [36].
In the gateway type of BIoT architecture, data generated from heterogeneous IoT devices in the smart home are transmitted to the smart home gateway consisting of various sizes and data types. The smart home gateway of the proposed architecture needs to accurately control IoT and process data according to the user’s request. A blockchain applied to smart home gateways is a crucial part of data transmission authentication with integrity and confidentiality between devices and other media. Although a smart home network has a centralized network form in each smart home, it was applied as a centralized to distributed network by using a blockchain at the cloud layer. However, that proposed network architecture has some limitations in terms of additional computational complexity by blockchain operation [37]. Figure 2 shows the proposed device-to-device BIoT architecture, which includes various BIoT devices and infrastructure applications that reduce computational complexity issues. In the proposed architecture, Ethereum Blockchain was chosen because it is the only platform available to date that is accessible to all public users, who are the customers in this case. Furthermore, the Ethereum Blockchain allows for blockchain programmability (via smart contracts) as well as cryptocurrency payment via the Ether token.
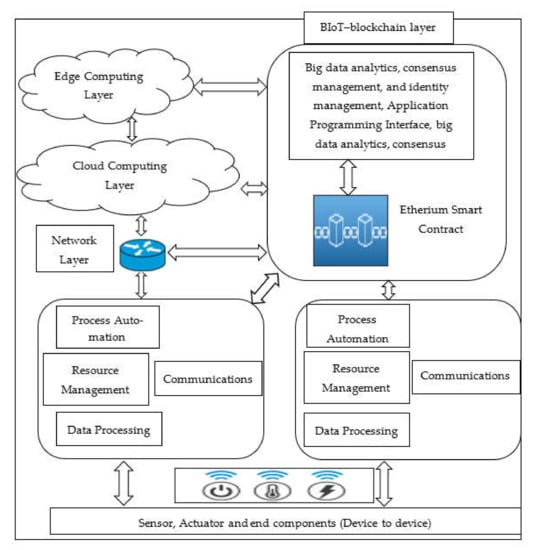
Figure 2.
Device-to- Device BIoT Architecture.
BIoT device integration involves cloud systems, edge computing, gateways, and various types of BIoT devices, ranging from basic sensors that can only communicate with neighbouring gateways to devices with computational and processing capabilities. It is fascinating to see how blockchains and edge computing are linked. Blockchain nodes can use edge computing and distributed computation architectures to store and validate transactions. On the other hand, the blockchain has the potential to create a completely open, distributed cloud marketplace. However, the way network designs are developed today is another factor contributing to blockchain network latency. To connect, blockchain nodes must send data across the entire network and back, much like cloud computing traffic. An edge computing network would allow for new server-to-server data flows, removing the need for data to travel through the core network. Industry professionals and academics are interested in cloud computing, blockchain, and the Internet of Things [38].
The emphasis is on the advantages of employing such technology to do more with less, i.e., improve work routines, better resource use, and lower expenses. However, due to the contradictory nature of these developing technologies, various obstacles arise when interest in integrating the three technologies emerges.
The IoT physical layer is made up of numerous interconnected devices that may communicate, compute, and store data. The network layer’s primary job is route management, as self-organization is essential due to the lack of global Internet protocols on physical devices. This layer includes additional service-providing modules such as network administration, security administration, and message brokerage. The IoT blockchain service layer includes all modules that combine common services to allow different technical characteristics, including identity management, consensus, and peer-to-peer communication (P2P).
BIoT–blockchain layer is a new layer that includes all modules that may be incorporated into a BIoT system using different elements of blockchain technology. The features given include peer-to-peer communication, distributed ledger, smart contracts, API, large data analysis, consensus management, and identity management. To allow for decentralized communication between different BIoT devices, P2P protocols are required [39]. In addition, each BIoT device has a copy of the distributed ledger that allows the IoT network modifications to be updated in minutes or even seconds. As IoT devices produce large volumes of data that cannot be managed using traditional methods, blockchain can provide effective online data storage and processing through the big data analytics module.
Moreover, an extra data analysis is required because several transactions are recorded in structured ledges. Another key component of blockchain technology is smart contracts, which enable autonomous decisions based on preset parameters. If specific criteria are met or validated, an intelligent agreement is a component of the software running on the blockchain and carries out several measures [40]. Consensus administration is another key component of the blockchain and BIoT combination. It is the central server of the network that ensures the integrity of all connected nodes. To govern and identify various nodes, the BIoT network identity management system is employed. BIoT apps may also access blockchain services via the API interface. The top layer is the application layer, consisting of various BIoT applications and data visualization operations that enable decision-makers to evaluate accurately and correctly based on data from real BIoT devices.
The edge layer of the BIoT workload consists of the physical hardware of your devices, the embedded operating system that manages the processes on your device, and the device firmware, which is the software and instructions programmed onto your BIoT devices. The cloud computing layer allows the organization to significantly exceed the normally available storage, without having to host extra servers on site. Data can also be collected from multiple sites and devices, accessible anytime, anywhere.
4. Proposed Methodology and Simulation Scenarios
At their core, blockchains are a time stamped (or other unique identifiers) ledger of transactions. The system will shine in the transactions involved in the Internet of Things (IoT) ecosystem. Because an Ethereum account message can trigger computation or another code action, an IoT device can be controlled if it is connected to an Ethereum-based network. Work on developing a comprehensive IoT control system with Ethereum as a component has already begun. The most difficult challenge, however, is not simply creating a decentralized IoT, but creating one that can scale globally while maintaining private, secure, and trustless transactions. In other words, the Internet of Things is a case of billions of players, not all of whom can be trusted—some of whom are even malicious—and who require some form of validation and consensus.
Security is a crucial challenge in BIoT-based systems because they include databases, information files, and interconnected sensors and devices. This paper proposes a secure scheme for the BIoT environment in any smart system using ECC-CRT algorithms. CC is a low-power Internet of Things working framework. Cooja is a Contiki organization emulator. It is a well-known, independent, and open-source IoT programming framework based on the C programming language and available under the Berkeley Software Distribution (BSD) license [41]. The current revolution in Internet, mobile, and machine-to-machine (M2M) technologies can be viewed as the IoT first phase. Radio frequency identification (RFID) technology is one of the core technologies of IoT deployments in the smart environment. Contiki is an operating system designed for low-power IoT devices [42]. Figure 3 shows a Cooja window, which is filled with the primary simulation tools. Here is a quick rundown of each tool’s functionality:
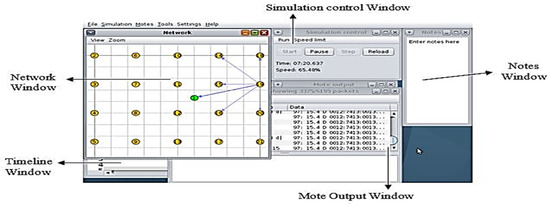
Figure 3.
Cooja’s window.
This paper evaluates the performance of both the BIoT-device-only architecture and the gateway-based design using the Contiki operating system. The Z-motes were placed at random locations and are used by us. Networks with 6, 12, 24, and 48 Z-motes were simulated as shown in Figure 4. The simulation parameters are given in Table 2. The nodes communicate using IPv6 over low-power personal area networks (6LoWPAN). Indeed, 6LoWPAN technology is used in a variety of applications, including the Internet of Things and wireless sensor networks [43].
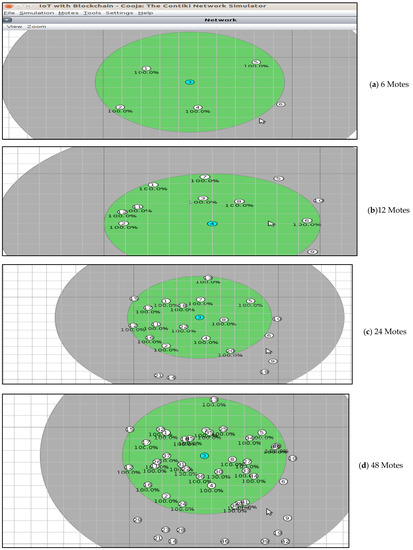
Figure 4.
Networks with 6, 12, 24, and 48 Z-motes. (a) 6 Motes, (b) 12 Motes, (c) 24 Motes, (d) 48 Motes.

Table 2.
Simulation parameters.
IPv6 is the name used for a wireless sensor network of this type that delivers data in packets and utilizes IPv6. Furthermore, 6LoWPAN permits the transmission of IPv6 packet data over IEEE 802.15.4 and other networks. It offers IPv6 connectivity end-to-end to a wide range of networks, including the Internet. IEEE 802.15.4 is used for this low-energy wireless network system in the 6LoWPAN technology [44].
While the IPv6 and IEEE 802.15.4 standards might seem to be an easy way to create , a data-package wireless system, or a network of wireless sensors, the system may be applied as layers at the top of the standard (802.15.4) using 6LoWPAN.
Authentication, cipher key generation, integrity, and radio link privacy are all provided to users on BIoT networks using a variety of security techniques. The ECC-CRT and SHA-256 algorithms are described in detail below, along with how to obtain them.
4.1. SHA-256 Algorithm
The SHA-256 approach was developed by the National Security Agency as a successor to the SHA-1 (2001) [45] and SHA-2 [46,47,48,49]. The SHA-256 algorithm is a proprietary cryptographic hash technique that produces a 256-bit output. The process of hacking is to change hashed data to make them entirely illegible. The aforementioned 256-bit hash could hardly be converted back to its original 512-bit form. The most common cause is that the sensitive material is checked twice. Hashing, for example, serves to check the completeness of safe messages and data. A hash (or cryptographic hash) is a long number that acts as a digital fingerprint of any collection of data. In IoT devices, the SHA256 hashing function is used, which generates a 64-digit hexadecimal number. For example, the cryptographic hash of the words in this paragraph is:
C019286295F2CDEC9958BEE25B9603B5F94C76B2CCC69A59CE54872ED26DC479
Data stored in the block and the hash of the previous block are put into the SHA256 function to get the value of the current block hash:
SHA256(Block Number, Data, Previous Block Hash) Hash
Now we can see how the blocks are linked. Not only does each block reference the previous block’s cryptographic hash, but, in fact, that hash directly affects the value of the current block’s hash.
The timestamp is also included in the SHA256 calculation for the hash of the current block that is being mined:
SHA256(Block Number, Timestamp, Nonce, Data, Prev. Block Hash) -> Hash
In addition, since the timestamp is constantly refreshing (until the block is successfully mined), this effectively resets the Nonce range every second. SHA-256 hash function reference implementation is discussed below.
SHA-256 hash function reference implementation:
* (a) Generates SHA-256 hash of a string.
* @param {string} msg - (Unicode) string to be hashed.
* import Sha256 from ‘./sha256.js’;
*consthash=Sha256.hash(‘abc’); ‘ba7816bf8f01cfea414140de5dae2223b00361a396177a9cb410ff61f20015ad’
*/
(b) Preprocessing
msg += String.fromCharCode(0x80); //add trailing ‘1’ bit (+ 0’s padding) to string [§5.1.1]
const lenHi = ((msg.length − 1)*8) / Math.pow(2, 32);
(c) Hash computation
for (let i = 0; i < N; i++) {
const W = new Array(64);
}
return (x >>> n) | (x << (32 − n));
}
(d) Logical functions
* @private
*/
static Σ0(x) { return Sha256.ROTR(2, x) ^ Sha256.ROTR(13, x) ^ Sha256.ROTR(22, x); }
}
4.2. ECC-CRT Algorithm
Observation suggests that any legal but malicious IoT device can reveal the identity of other users. As a result, their method is susceptible to both server spoofing and offline password-guessing attacks. Furthermore, if the malicious patient registers at the same time as other users, she can successfully carry out impersonation, man-in-the-middle, modification, replay, and powerful replay attacks. This paper proposes an improved ECC-based authenticated key agreement mechanism to address these flaws. An ECC is an elliptical curve theory based on a public key encryption technique that can be used to create cryptographic keys that are faster, smaller, and more effective. To obtain exceptionally high primary numbers, the ECC uses the functions of the elliptic curve equation to construct keys rather than the traditional method. This technology supports most public-key encryption algorithms, including SHA and Diffie-Hellman [44]. According to some researchers, ECC can provide the same level of security as other methods that need a 1024-bit key with a 164-bit key. The proposed approach uses ECC methods, which depend on the algebraic structure of the elliptical curves over finite fields, to overcome these limitations, as shown in Figure 5. Internal and public keys are the primary applications of elliptic curves with this method. They are also used when the messages are encrypted and decrypted. This alternative approach used this method to decrease computing power since the key size of the method is the least of many cryptographic algorithms in contrast.
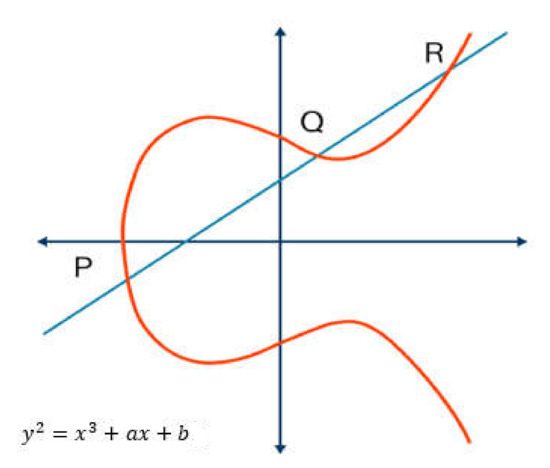
Figure 5.
Elliptical curves over finite fields.
ECC generates two keys: the private key and the public key. The resource directory (RD) public key will be used to encrypt each service agent (SA) sender node post. The RD, in turn, will use its private key to decrypt the message.
A random number R in a range (n) is then chosen. The following Equation (1) is then used to produce the public key:
If R is a random number between 1 and n − 1, P is the point in the curve produced by the next Equation (2). Furthermore, PU refers to the public key, and n to the private key.
Here, the ECC algorithm key generation is given as (shown in Figure 5):
For Encryption
- s is message
- K is random number
C1 = K × P & C2 = S + K × PU
For Decryption
- Received encrypted message
S = C2 − d × C1
- received original message
The Chinese remainder theorem is a theorem which gives a unique solution to simultaneous linear congruences with coprime moduli. In its basic form, the Chinese remainder theorem will determine a number p that, when divided by some given divisors, leaves given remainders. Many ancient problems involved linear congruences. Such a problem concerned the removal of eggs from a basket 2, 3, 4, 5, and 6 at a time, whereupon 1 egg remained. However, when they were removed 7 at a time, none remained. This may be stated in terms of congruences as follows: x ≡ 1(mod 2), x ≡ 1(mod 3), …, x ≡ 1(mod 6), x ≡ 0(mod 7). These are equivalent to the two congruences x ≡ 1(mod 60) and x ≡ 0(mod 7), which have the solution x ≡ 301(mod 420).
Problems of this type are found in the works of the Chinese mathematician Sun-Tse. When each pair of moduli is relatively prime, the solution is found in the following theorem.
Chinese Remainder Theorem.
Given the simultaneous congruences )) for i = 1, 2, 3, …, n, where ( = 1 for all i, j, let M = . If for each i the congruence is solved, then the original set of congruences has the solution.
The Chinese remainder theorem asserts that if one knows the remainder of the Euclidean division of an integer n by multiple integers, one can uniquely identify the remainder of the division of n by the product of these integers if the divisors are pairwise coprime.
Figure 6 shows a mesh that wraps around every 6 steps horizontally and every 5 steps vertically. In this mesh, the leftover pairs arising from division by 6 and 5 are illustrated. The values outside the mesh are the horizontal and vertical coordinates, which are the corresponding remainders from dividing by 6 and 5. From (0,0), a ray, shown by the red line, transitions forward 1 step in both the horizontal and vertical directions regularly. This ray denotes the sequence of remaining pairs as the payout increases in steps of one. On each red stripe, a number represents each wrap-around of the ray. Working of ECC-CRT algorithm is shown below.
| // working of ECC-CRT #include<bits/stdc++.h> using namespace std; // k is size of num[] and rem[]. Returns the smallest // number x such that: // x % num(0) = rem(0), // x % num(1) = rem(1), // .................. // x % num(k – 2) = rem(k – 1) // Assumption: Numbers in num() are pairwise coprime // (gcd for every pair is 1) int findMinX(int num[], int rem[], int k) { int x = 1; // Initialize result // As per the Chinese remainder theorem, // this loop will always break. while (true) { // Check if remainder of x % num(j) is // rem[j] or not (for all j from 0 to k − 1) int j; for (j = 0; j < k; j++ ) if (x%num(j) != rem(j)) break; // If all remainders matched, found x if (j == k) return x; // Else try next number x++; } return x; } // Driver method int main(void) { int num() = {3, 4, 5}; int rem() = {2, 3, 1}; int k = sizeof(num)/sizeof(num[0]); cout << “x is ” << findMinX(num, rem, k); return 0; } |
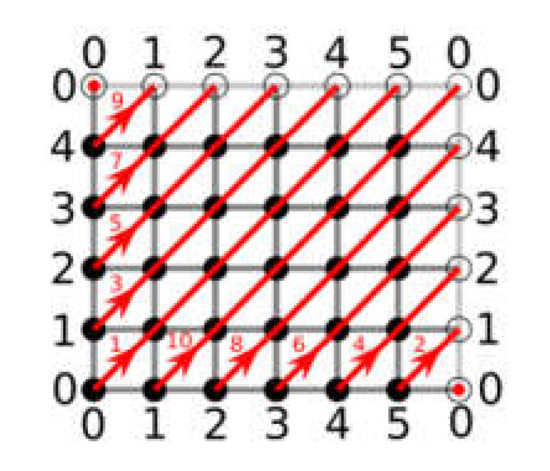
Figure 6.
Mesh Chinese remainder theorem.
5. Results and Discussion
These simulation processing and storage mechanisms, as well as the communication process, will be examined. The elliptic curve signature is 72 bytes long, the SHA-256 hash function is 32 bytes long, and the typical transaction is 77 bytes long. This paper only compared the average connection time between blockchain nodes in an IoT-only and a gateway-only configuration. A graph was produced based on the results received throughout the process. The number of nodes is represented on the X-axis, while the number of transactions cost (gas) is represented on the Y-axis. The value of the gas units is converted to eth. The price of gas is set at 33 Gwei. Furthermore, the cost of Gwei is calculated by multiplying the number of gas units by the current gas price. The total is then divided by the unit of single Ether, i.e., 1 Ether = 1,000,000,000 Gwei, between 6 and 12 s, counting the number of transactions. With the rapid evolution of the technological, economic, and regulatory landscapes, it is almost certain that modern blockchain platforms will undergo significant changes. As a result, the applications that rely on them must eventually migrate from one blockchain instance to another to remain competitive and secure. Additionally, data migration would be required to improve business processes, performance, cost efficiency, privacy, and regulatory compliance. The differences in data and smart contract representations, modes of hosting, transaction fees, and the need to preserve consistency, immutability, and data provenance, on the other hand, present unique challenges in database migration.
The cost of sending a smart contract code to the Ethereum Blockchain for a smart network is referred to as the transaction cost [50,51,52]. It is determined by the size of the smart contract. The computational tasks performed by a smart contract determine its size. For example, if the smart contract contains a high number of computational tasks, it will be large in size and have a high transaction cost. Furthermore, the transaction cost includes the following components: transaction cost, contract deployment cost, and transaction data cost. Figure 7 and Figure 8, respectively, depict the transaction cost of BIoT-device-only architecture and gateway-type BIoT architecture. The figure clearly shows that the transaction cost of BIoT-device-only architecture is significantly higher than that of gateway-type BIoT architecture. It manages the system’s overall access control and has more functions than other smart contracts. As a result, the cost increases in proportion to the size of the smart contract. The transaction cost of the BIoT-device-only architecture is 160 gas units which are equal to 0.0528 eth. The transaction cost of gateway-type BIoT architecture is 80 gas units which are equal to 0.0000026 eth. The gateway-type BIoT architecture has a low cost because it only performs user registration operations and creates a user registration table.
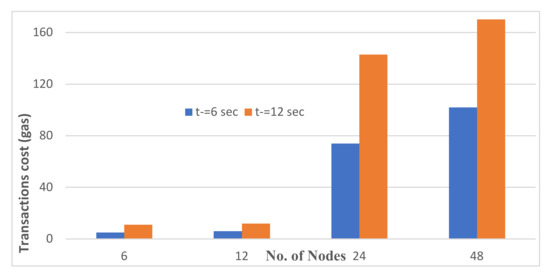
Figure 7.
Transaction cost for BIoT-device-only type of architecture.
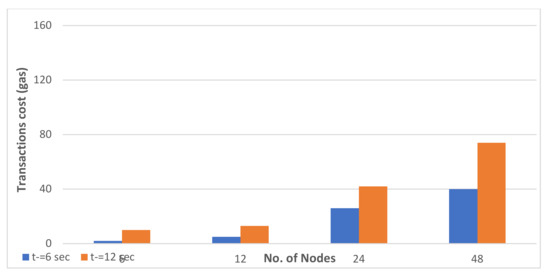
Figure 8.
Transaction cost for gateway-type BIoT architecture.
The paper compares the performance of two security algorithms, ECC-CRT and SHA-256, in the proposed device-to-device BIoT architecture. The higher the network traffic, the higher the energy consumption, and vice versa. There are a vast number of parameters that need to be looked at during the IoT simulation, including low power management (LPM), the central processing unit (CPU), radio listening, and radio transmitting. The findings are compatible with the above-described graph, and the low-power mode is in honesty mode. Furthermore, the parameters for radio listening are also consistent. The LPM CPU radio listens and the radio transmits. These are different parameters for the processing calculation, and this parameter is used for the calculation of the average power of network motes.
When the key sizes for both algorithms vary, the following graph compares the power usage of the proposed ECC and SHA-256. The proposed ECC consumes less power than SHA-256, which consumes a large amount of power as the main size increases, as seen in the graph. As the main size exceeds 512 bits, the power consumption using SHA-256 becomes linear as shown in Figure 9.
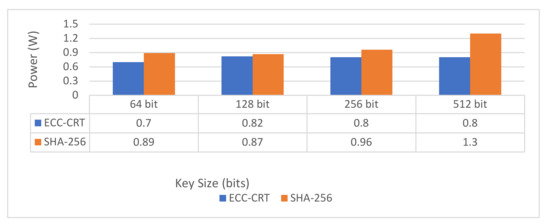
Figure 9.
Power consumption of ECC-CRT and SHA-256.
The optimization seen in this work aims to increase the overall network performance and extend the network’s lifetime. IoT nodes typically use batteries; the energy supply of these nodes is thus an important element in their continuous life and operation in the network environment. In this regard, the energy consumption of the network is measured in a way, namely real energy consumption, and the estimation method for the energy consumption rate is modeled on a milli-joul scale.
where LPM is low power management, CPU is central processing unit, radio listens, and radio transmit.
Now compare the performance of two security algorithms, ECC and SHA-256, in the proposed device-to-device BIoT architecture. Figure 10 depicts the Contiki OS simulation results for the average battery level for all nodes from the start of the simulation to the end. As can be shown, the proposed ECC saves 49% more energy than SHA-256. Furthermore, when using SHA-256, the battery absorbed more energy than when using the proposed stable ECC.
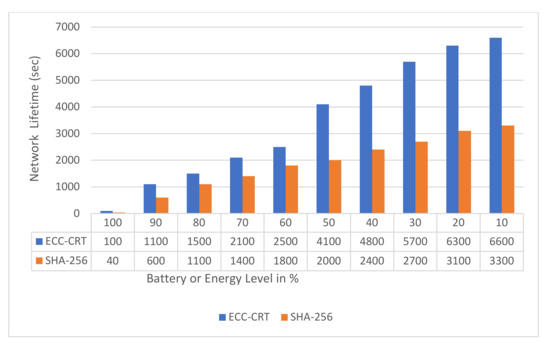
Figure 10.
Network lifetime in various battery or energy levels for ECC-CRT and SHA-256.
Figure 11 depicts the SHA 256 and proposed ECC-CRT storage spaces. The files are represented on the x-axis, and the storage space in megabytes is represented on the y-axis (MB). When the file size is 30 kb, SHA 256 and the suggested ECC-CRT require 300 and 350 MB of storage capacity, respectively. In comparison to SHA 256, the suggested ECC-CRT method requires less storage space. Table 3 provides a performance comparison between ECC-CRT and SHA-256.
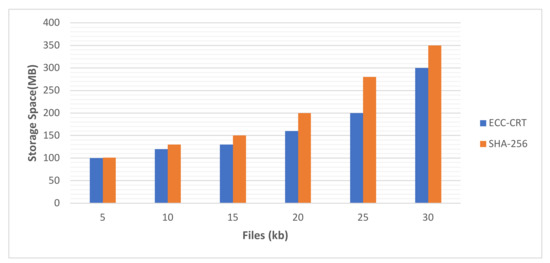
Figure 11.
Storage space for ECC-CRT and SHA-256.

Table 3.
Comparison between ECC-CRT and SHA-256.
As a result, the ECC-CRT approach is ideal since it is extremely safe and has no flaws that allow its keys to be broken. For the suggested scenario, network efficiency and high securities are key exchange requirements and ECC-CRT is the best choice due to its speedy key generation and reduced key length as compared with SHA-256. The combination of blockchain and IoT will recommend a powerful approach that can greatly direct and spread innovative market approaches.
6. Conclusions
This paper presented the secure data sharing and increased security of BIoT networks. The existing capabilities of IoT devices are insufficient to protect themselves against attackers. Device security, communication protocols, and different layers must all be considered in an IoT ecosystem. Unfortunately, a large number of IoT devices contain security flaws and are vulnerable, allowing hackers and bad individuals to harm and disrupt the operation of these devices, as well as compromise the privacy of their users. This is due to resource constraints in IoT devices, as well as immature standards, a lack of secure hardware, and software architectures. This work proposes an enhanced IoT-device-only architecture in blockchain networks. Due to the simulation results, we may conclude that ECC outperforms the SHA-256 algorithm for networks with limited computational, power, and storage resources. As a result, ECC-CRT becomes a cost-effective option for IoT-based BIoT networks. The paper proposed using ECC-CRT to calculate the intended platform performance in terms of throughput, latency, resource consumption, and variable network characteristics. Experimentation has shown that ECC-CRT improves system performance in terms of throughput and resource consumption. This paper also evaluated the performance of the IoT-device-only architecture and the gateway-based design using the Contiki operating system in the BIoT network. The transaction costs of BIoT-device-only architecture and gateway-type BIoT architecture are depicted in the results. The simulation results clearly show that the transaction cost of BIoT-device-only architecture is significantly higher than the transaction cost of gateway-type BIoT architecture. It manages the overall access control of the system and has more functions than other smart contracts. As a result, the price rises in direct proportion to the size of the smart contract. This work may be used in a variety of fields, including healthcare and smart businesses. The interoperability of the suggested service model with different IoT frameworks is a potential future direction for this study. Future work will focus on evaluating and refining the proposed scheme to make it applicable to the real BIoT system.
Author Contributions
Conceptualization, A.R. and S.S.; methodology, S.D. and A.R.; validation, K.N. and S.S.; formal analysis, A.A.A.I. and B.C.; data curation, A.R., K.N. and A.A.A.I.; writing—original draft preparation, N.G., K.N., A.A.A.I. and A.R.; writing—review and editing, S.H., A.R. and K.N.; supervision, K.N. and A.A.A.I.; project administration, K.N. and A.A.A.I. funding acquisition. All authors have read and agreed to the published version of the manuscript.
Funding
This research work is fully supported by the Faculty of Computing and Informatics, University Malaysia Sabah Jalan UMS, 88400 Kota Kinabalu Sabah, Malaysia.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Bhushan, B.; Sahoo, C.; Sinha, P.; Khamparia, A. Unification of Blockchain and Internet of Things (BIoT): Requirements, working model, challenges and future directions. Wirel. Netw. 2021, 27, 55–90. [Google Scholar] [CrossRef]
- Christidis, K.; Devetsikiotis, M. Blockchains and smart contracts for the internet of things. IEEE Access 2016, 4, 2292–2303. [Google Scholar] [CrossRef]
- Wang, X.; Zha, X.; Ni, W.; Liu, R.P.; Guo, Y.J.; Niu, X.; Zheng, K. Survey on blockchain for Internet of Things. Comput. Commun. 2019, 136, 10–29. [Google Scholar] [CrossRef]
- Haque, M.R.; Tan, S.C.; Yusoff, Z.; Nisar, K.; Lee, C.K.; Chowdhry, B.S.; Ali, S.; Memona, S.K.; Kaspin, R. SDN architecture for UAVs and EVs using satellite: A hypothetical model and new challenges for future. In Proceedings of the 2021 IEEE 18th Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, NV, USA, 9–12 January 2021; IEEE: New York, NY, USA, 2021; pp. 1–6. [Google Scholar]
- Abdelmaboud, A.; Ahmed, A.I.A.; Abaker, M.; Eisa, T.A.E.; Albasheer, H.; Ghorashi, S.A.; Karim, F.K. Blockchain for IoT Applications: Taxonomy, Platforms, Recent Advances, Challenges and Future Research Directions. Electronics 2022, 11, 630. [Google Scholar] [CrossRef]
- Dai, H.N.; Zheng, Z.; Zhang, Y. Blockchain for Internet of Things: A survey. IEEE Internet Things J. 2019, 6, 8076–8094. [Google Scholar] [CrossRef] [Green Version]
- Rana, A.; Chakraborty, C.; Sharma, S.; Dhawan, S.; Pani, S.K.; Ashraf, I. Internet of Medical Things-Based Secure and Energy-Efficient Framework for Health Care. Big Data 2022, 10, 18–33. [Google Scholar] [CrossRef]
- Harada, S.; Yan, Z.; Park, Y.J.; Nisar, K.; Ibrahim, A.A.A. Data aggregation in named data networking. In Proceedings of the TENCON 2017—2017 IEEE Region 10 Conference, Penang, Malaysia, 5–8 November 2017; IEEE: New York, NY, USA, 2017; pp. 1839–1842. [Google Scholar]
- Rana, A.K.; Sharma, S. Enhanced energy-efficient heterogeneous routing protocols in WSNs for IoT application. IJEAT 2019, 9, 4415–4418. [Google Scholar] [CrossRef]
- Rao, A.R.; Clarke, D. Perspectives on emerging directions in using IoT devices in blockchain applications. Internet Things 2020, 10, 100079. [Google Scholar] [CrossRef]
- Rana, A.K.; Sharma, S. Industry 4.0 manufacturing based on IoT, cloud computing, and big data: Manufacturing purpose scenario. In Advances in Communication and Computational Technology; Springer: Singapore, 2021; pp. 1109–1119. [Google Scholar]
- Samaniego, M.; Deters, R. Using blockchain to push software-defined IoT components onto edge hosts. In Proceedings of the International Conference on Big Data and Advanced Wireless Technologies, Blagoevgrad, Bulgaria, 10–11 November 2016; pp. 1–9. [Google Scholar]
- Kravitz, D.W.; Cooper, J. Securing user identity and transactions symbiotically: IoT meets blockchain. In Proceedings of the 2017 Global Internet of Things Summit (GIoTS), Geneva, Switzerland, 6–9 June 2017; IEEE: New York, NY, USA, 2017; pp. 1–6. [Google Scholar]
- Dua, D.; Taniskidou, E.K. UCI Machine Learning Repository; School of Information and Computer Sciences, University of California: Irvine, CA, USA, 2018; Available online: http://archive.ics.uci.edu/ml (accessed on 10 June 2021).
- Lawal, I.A.; Said, A.M.; Nisar, K.; Mu’azu, A.A.; Shah, P.A. Throughput enhancement for fixed WiMAX network using distributed model. In Proceedings of the 2014 International Conference on Computer and Information Sciences (ICCOINS), Kuala Lumpur, Malaysia, 3–5 June 2014; pp. 1–6. [Google Scholar] [CrossRef]
- Hammi, M.T.; Hammi, B.; Bellot, P.; Serhrouchni, A. Bubbles of Trust: A decentralized blockchain-based authentication system for IoT. Comput. Secur. 2018, 78, 126–142. [Google Scholar] [CrossRef]
- Lawal, I.A.; Said, A.M.; Nisar, K.; Mu’azu, A.A.; Shah, P.A. A Distributed QoS-Oriented Model to Improve Network Performance for Fixed WiMAX. Int. J. Recent Trends Eng. Technol. 2014, 10, 186–202. [Google Scholar]
- Nauman, M.; Tanveer, T.A.; Khan, S.; Syed, T.A. Deep neural architectures for large scale android malware analysis. Clust. Comput. 2018, 21, 569–588. [Google Scholar] [CrossRef]
- Nisar, K.; Amphawan, A.; Hassan, S.B. Comprehensive structure of novel voice priority queue scheduling system model for VoIP over WLANs. Int. J. Adv. Pervasive Ubiquitous Comput. (IJAPUC) 2011, 3, 50–70. [Google Scholar] [CrossRef] [Green Version]
- Wee, X.L.; Yan, Z.; Park, Y.J.; Leau, Y.-B.; Nisar, K.; Ibrahim, A.A.A. Rom-p: Route optimization management of producer mobility in information-centric networking. In First International Conference on Intelligent Transport Systems; Springer: Cham, Switzerland, 2018; pp. 81–91. [Google Scholar]
- Wang, Q.; Zhu, X.; Ni, Y.; Gu, L.; Zhu, H. Blockchain for the IoT and industrial IoT: A review. Internet Things 2020, 10, 100081. [Google Scholar] [CrossRef]
- Kaplan, A. How Alibaba Is Championing the Application of Blockchain Technology in China and Beyond. 2018. Available online: https://smartereum.com/7630/how-alibaba-is-championing-the-application-of-blockchain-technology-in-china-and-beyond-sun-jun-09/ (accessed on 22 June 2018).
- Huang, Z. China’s Crackdown on Crypto Hasn’t Stopped Its Tech Giants from Flirting with Blockchain. 2018. Available online: https://twitter.com/qz/status/987179394966982656 (accessed on 30 March 2018).
- Levy, A. Why Mark Zuckerberg Just Put Some of His Best Execs on Blockchain. 2018. Available online: https://finance.yahoo.com/news/why-mark-zuckerberg-just-put-130100695.html (accessed on 10 May 2018).
- Bocek, T.; Rodrigues, B.B.; Strasser, T.; Stiller, B. Blockchains everywhere-a use-case of blockchains in the pharma supply-chain. In Proceedings of the 2017 IFIP/IEEE Symposium on Integrated Network and Service Management (IM), Lisbon, Portugal, 8–12 May 2017; IEEE: New York, NY, USA, 2017; pp. 772–777. [Google Scholar]
- Ahmad, A. Integration of IoT Devices via a Blockchain-Based Decentralized Application. Master’s Thesis, University of Stuttgart, Stuttgart, Germany, 2018. [Google Scholar]
- Orenge, A.O. Blockchain-Based Provenance Solution for Handcrafted Jewellery. Ph.D. Thesis, University of Tartu, Tartu, Estonia, 2018. [Google Scholar]
- Brady, S.; Hava, A.; Perry, P.; Murphy, J.; Magoni, D.; Portillo-Dominguez, A.O. Towards an emulated IoT test environment for anomaly detection using NEMU. In Proceedings of the 2017 Global Internet of Things Summit (GIoTS), Geneva, Switzerland, 6–9 June 2017; IEEE: New York, NY, USA, 2017; pp. 8–21. [Google Scholar]
- Suárez-Albela, M.; Fernández-Caramés, T.M.; Fraga-Lamas, P.; Castedo, L. A practical performance comparison of ECC and RSA for resource-constrained IoT devices. In Proceedings of the 2018 Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4–7 June 2018; IEEE: New York, NY, USA, 2018; pp. 1–6. [Google Scholar]
- Chhabra, A.; Arora, S. An elliptic curve cryptography based encryption scheme for securing the cloud against eavesdropping attacks. In Proceedings of the 2017 IEEE 3rd International Conference on Collaboration and Internet Computing (CIC), San Jose, CA, USA, 15–17 October 2017; IEEE: New York, NY, USA, 2017; pp. 243–246. [Google Scholar]
- Hussain, I.; Negi, M.C.; Pandey, N. A secure IoT-based power plant control using RSA and DES encryption techniques in data link layer. In Proceedings of the 2017 International Conference on Infocom Technologies and Unmanned Systems (Trends and Future Directions) (ICTUS), Dubai, United Arab Emirates, 18–20 December 2017; IEEE: New York, NY, USA, 2017; pp. 464–470. [Google Scholar]
- Tsang, Y.P.; Choy, K.L.; Wu, C.H.; Ho, G.T.; Lam, H.Y. Blockchain-driven IoT for food traceability with an integrated consensus mechanism. IEEE Access 2019, 7, 129000–129017. [Google Scholar] [CrossRef]
- Wu, J.; Dong, M.; Ota, K.; Li, J.; Yang, W. Application-aware consensus management for software-defined intelligent blockchain in IoT. IEEE Netw. 2020, 34, 69–75. [Google Scholar] [CrossRef]
- Pavithran, D.; Shaalan, K.; Al-Karaki, J.N.; Gawanmeh, A. Towards building a blockchain framework for IoT. Clust. Comput. 2020, 23, 2089–2103. [Google Scholar] [CrossRef]
- Miraz Mahdi, H. Blockchain of Things (blockchainoT): The Fusion of Blockchain and IoT Technologies. In Advanced Applications of Blockchain Technology; Springer: Singapore, 2020; pp. 141–159. [Google Scholar]
- Rana, A.K.; Krishna, R.; Dhwan, S.; Sharma, S.; Gupta, R. Review on artificial intelligence with internet of things-problems, challenges and opportunities. In Proceedings of the 2019 2nd International Conference on Power Energy, Environment and Intelligent Control (PEEIC), Greater Noida, India, 18–19 October 2019; IEEE: New York, NY, USA, 2019; pp. 383–387. [Google Scholar]
- Kharif, O.; Bergen, M. Google Is Working on Its Own Blockchain-Related Technology. 2018. Available online: https://www.bloomberg.com/news/articles/2018-03-21/google-is-said-to-work-on-its-own-Blockchain-related-technology (accessed on 22 June 2021).
- Kumar, A.; Sharma, S.; Goyal, N.; Singh, A.; Cheng, X.; Singh, P. Secure and energy-efficient smart building architecture with emerging technology IoT. Comput. Commun. 2021, 176, 207–217. [Google Scholar] [CrossRef]
- Shoker, A. Sustainable blockchain through proof of exercise. In Proceedings of the 2017 IEEE 16th International Symposium on Network Computing and Applications (NCA), Cambridge, MA, USA, 30 October–1 November 2017; IEEE: New York, NY, USA, 2017; pp. 1–9. [Google Scholar]
- Kumar, A.; Sharma, S. IFTTT rely based a semantic web approach to simplifying trigger-action programming for end-user application with IoT applications. In Semantic IoT: Theory and Applications; Springer: Cham, Switzerland, 2021; pp. 385–397. [Google Scholar]
- Zhang, Y.; Wen, J. An IoT electric business model based on the protocol of bitcoin. In Proceedings of the 2015 18th International Conference on Intelligence in Next Generation Networks, Paris, France, 17–19 February 2015; IEEE: New York, NY, USA, 2015; pp. 184–191. [Google Scholar]
- Kumar, A.; Sharma, S.; Singh, A.; Alwadain, A.; Choi, B.-J.; Manual-Brenosa, J.; Ortega-Mansilla, A.; Goyal, N. Revolutionary Strategies Analysis and Proposed System for Future Infrastructure in Internet of Things. Sustainability 2022, 14, 71. [Google Scholar] [CrossRef]
- Ateniese, G.; Goodrich, M.; Lekakis, V.; Papamanthou, C.; Paraskevas, E.; Tamassia, R. Accountable Storage. In Proceedings of the International Conference on Applied Cryptography and Network Security, Kanazawa, Japan, 10–12 July 2017. [Google Scholar]
- Jimson, E.R.; Nisar, K.; Hijazi, M.H.A. The state of the art of software defined networking (SDN) issues in current network architecture and a solution for network management using the SDN. Int. J. Technol. Diffus. (IJTD) 2019, 10, 33–48. [Google Scholar] [CrossRef] [Green Version]
- Huang, X.; Dong, Y.; Zhu, H.; Ye, G. Visually asymmetric image encryption algorithm based on SHA-3 and compressive sensing by embedding encrypted image. Alex. Eng. J. 2022, 61, 7637–7647. [Google Scholar] [CrossRef]
- Suman, R.R.; Mondal, B.; Mandal, T. A secure encryption scheme using a Composite Logistic Sine Map (CLSM) and SHA-256. Multimed. Tools Appl. 2022, 22, 1–22. [Google Scholar] [CrossRef]
- Esai Malar, E.; Paramasivan, B. Enhancing Security and Privacy Preserving of Data in Cloud Using SHA and Genetic Algorithm. In Computational Intelligence in Pattern Recognition; Springer: Singapore, 2022; pp. 401–411. [Google Scholar]
- Rana, S.K.; Kim, H.C.; Pani, S.K.; Rana, S.K.; Joo, M.I.; Rana, A.K.; Aich, S. Blockchain-Based Model to Improve the Performance of the Next-Generation Digital Supply Chain. Sustainability 2021, 13, 10008. [Google Scholar] [CrossRef]
- Sultana, T.; Almogren, A.; Akbar, M.; Zuair, M.; Ullah, I.; Javaid, N. Data sharing system integrating access control mechanism using blockchain-based smart contracts for IoT devices. Appl. Sci. 2020, 10, 488. [Google Scholar] [CrossRef] [Green Version]
- Laurent, A.; Brotcorne, L.; Fortz, B. Transactions fees optimization in the Ethereum blockchain. Blockchain Res. Appl. 2022, 100074. [Google Scholar] [CrossRef]
- Dhawan, S.; Chakraborty, C.; Frnda, J.; Gupta, R.; Rana, A.K.; Pani, S.K. SSII: Secured and high-quality steganography using intelligent hybrid optimization algorithms for IoT. IEEE Access 2021, 9, 87563–87578. [Google Scholar] [CrossRef]
- Thai, Q.T.; Ko, N.; Byun, S.H.; Kim, S.M. Design and implementation of NDN-based Ethereum blockchain. J. Netw. Comput. Appl. 2022, 200, 103329. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
