Abstract
Wireless communications are increasingly vulnerable to malicious jamming attacks due to the inherent openness and broadcast nature. In this regard, a novel anti-jamming scheme based on knowledge graph is proposed in this paper, where the knowledge graph which contains the prior knowledge of the commonly-used jamming patterns is utilized to make the fast anti-jamming decision with low complexity. Specifically, for the known jamming patterns, the anti-jamming strategy is directly extracted based on the search from the knowledge graph by using the sensing information. On the other hand, for the unknown jamming patterns, a time-frequency domain feature extraction method is first proposed to extract the jamming feature and match the jamming patterns in the knowledge graph. As such, multiple anti-jamming strategies can be obtained by the knowledge graph search. Finally, the optimal strategy can be achieved by the two communication decision criteria-based strategy fusion. The simulation results showed that the time-frequency domain feature extraction method can well extract the time-frequency domain feature of the jamming pattern, and the proposed algorithm has high decision accuracy and robustness.
1. Introduction
With the development of wireless communication technology, wireless communication systems are playing more and more important roles in many fields, such as in people’s daily life, economy and society. In recent years, traffic on wireless communications system and networks are increasing rapidly. Due to the openness of the wireless communication channel and the complicated electromagnetic environment that wireless communication systems are facing, today’s wireless communications systems are more vulnerable to the threats from all kinds of interference, including unintentional interference from other communication systems and malicious jamming from adversaries in the battlefield setting. Therefore, in order to ensure the reliability of wireless communication systems, reliable and robust anti-jamming measures are greatly need.
In the past a few decades, many technical measures were proposed to increase the anti-jamming performance of wireless communications systems, which mainly include direct sequence spread spectrum, frequency hopping (FH), time hopping, adopting ultra-wideband signals, and so on. These traditional measures have effectively improved the performance of wireless communication systems [1,2,3]. However, with the increasingly complex electromagnetic environment, the aforementioned anti-jamming technology has obvious shortcomings. Some of them cannot even ensure the reliable operation of wireless communication systems anymore. Therefore, enhancing the performance of anti-jamming measures and developing new and intelligent anti-jamming methods to improve the adaptability of wireless communication systems is becoming more and more prominent [4].
In recent years, researchers have combined traditional anti-jamming technologies with anti-jamming decision-making techniques, which greatly improved the performance of anti-jamming measures used in wireless communication systems.
The authors in [5] proposed a dynamic multi-domain communication anti-jamming decision-making method based on the combination of rough set theory and a genetic algorithm. In the proposed method, the decision-making rules were extracted based on the rough set theory. As a result, the convergence speed of the proposed algorithm has been improved without compromising the performance of the algorithm. In [6,7], a cognitive anti-jamming fast decision-making engine based on the artificial bee colony algorithm was proposed, which can make effective anti-jamming decisions under different jamming patterns, different jamming power, and different channel settings. However, it is inevitable that the multi-domain decision space is too large. In order to solve this problem, the authors in [8] proposed an anti-jamming decision method based on the artificial bee colony algorithm with a mutation search mechanism, which could compress the decision space before generating the initial population. In [9], the author proposed an anti-jamming decision-making technology based on the deep learning mechanism. By using the pattern classification function of convolutional networks, the high-order feature extraction process for input samples was optimized and the system’s performance in recognition decision-making accuracy was improved. The authors in [10] proposed a real-time anti-jamming decision model based on the back-propagation (BP) neural network, which can improve the system’s decision-making speed and has the ability of generalization and fault tolerance. Additionally, an intelligent anti-jamming decision method based on the neural network and an optimization algorithm was proposed, which can improve the spectral efficiency and reduce the transmission power for wireless communication systems, while still sustaining the required bit error rate performance.
With the continuous development of artificial intelligence technology, machine learning technology represented by reinforcement learning has also begun to be used in the field of communication anti-jamming [11,12]. A time-domain anti-pulse jamming algorithm (TDAA) based on reinforcement learning is proposed in [13]; this algorithm has a higher time utilization ratio and normalized throughput. The authors in [14] proposed a reinforcement learning-based mobile offload scheme for edge computing to counter jamming attacks, which has shorter computational delay, lower energy consumption, and higher utilization. To cope with the challenge of infinite state of spectrum waterfall, an anti-jamming deep reinforcement learning algorithm was proposed in [15]. The authors in [16] designed the Double Deep Q Network (Double DQN) to model the confrontation between the cognitive radio network and the jammer; the simulation results indicate that this approach can effectively defend against several kinds of jamming attacks.
The aforementioned literature mainly used heuristic algorithms to optimize the decision-making mechanism, such as machine learning and other technologies. These methods can improve the effectiveness and accuracy of the decision-making process for wireless communication anti-jamming to a certain extent, but they still face some challenges: first, those existing methods mainly achieved their optimized decision-making based on a few communication system parameters, such as communication frequency and transmission power. Therefore, the resultant optimizing results may not render the best results when more communication parameters need to be considered. Secondly, for those existing methods, historical experience or existing knowledge of the wireless communication systems and environment are difficult to be integrated into the decision-making process. On the one hand, when faced with known jamming patterns, prior knowledge cannot be used to achieve direct and fast decision-making. On the other hand, for unknown jamming patterns, it is difficult for those existing algorithms to connect the jamming features with existing decision-making knowledge. Therefore, when the jamming pattern changes, the system needs to relearn all the parameters from scratch, which will lead to more computational complexity and slower response.
In order to reasonably utilize the historical experience and existing knowledge of anti-jamming, this paper introduces a knowledge graph in communication anti-jamming decision-making. Knowledge graphs, a branch of artificial intelligence technology, are a technique that uses graph models to describe knowledge and establish the relationship model among all the things in the world, which is an issue of great significance to explainable artificial intelligence [17]. Generally speaking, a knowledge graph consists of a set of nodes and edges, where the nodes are used to represent entities or abstract concepts (i.e., knowledge), and the edges are used to represent entity attributes or relationships between these entities [18]. Ever since Google Inc. used a knowledge graph for the first time in 2012 to improve the performance and user experience of their search engines, this technique has attracted extensive research interest from both academia and industry [19,20]. Different from the way traditional database store knowledge, knowledge graphs use nodes and edges to represent all the knowledge. Therefore, this novel knowledge management technology can effectively represent the relationship among different knowledge while storing the knowledge, which can lead to better and more efficient access to the stored knowledge. With the continuous development of knowledge graph technology, it has been more and more widely used in knowledge searches, intelligent answering systems [21,22], big data analysis [23], natural language processing [24,25] and auxiliary device interconnection.
This paper introduces the knowledge graph into the field of communication anti-jamming for the first time, and improves the intelligence level of anti-jamming decision-making from the perspective of knowledge utilization. The contributions of this paper are summarized as follows:
- Using the storage and representation capabilities of knowledge graphs, various parameters of decision-making elements are represented as entity attributes, so as to realize multi-parameter (including frequency domain, time domain, and power domain) decision-making for communication anti-jamming, and it has strong extensibility.
- The anti-jamming decision-making algorithm based on the knowledge graph can take advantage of prior knowledge, and directly extract anti-jamming strategies by searching the knowledge graph for known jamming patterns. For unknown jamming patterns, prior knowledge can also be used to effectively reduce decision complexity.
The rest of the article is organized as follows. The system model is presented in Section 2, at the mean time, the problem is formulated. Section 3 introduces the feature extraction and parameter decision-making methods of unknown jamming patterns; Section 4 presents the anti-jamming decision-making based on knowledge graph algorithm design; finally, the simulation results and analysis are given.
2. System Model
2.1. Block Diagram
An intelligent anti-jamming communication system model is shown in Figure 1. The main difference between this intelligent anti-jamming communication system and the traditional wireless communication system is that besides the transceiver signal processing module, a jamming cognition and anti-jamming decision-making model are introduced. Our work mainly studies the anti-jamming decision-making model.
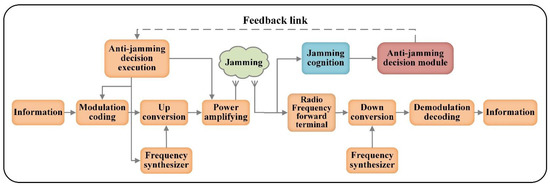
Figure 1.
The block diagram of an intelligent anti-jamming communication system model.
The anti-jamming decision-making module can also be further refined, as shown in Figure 2:
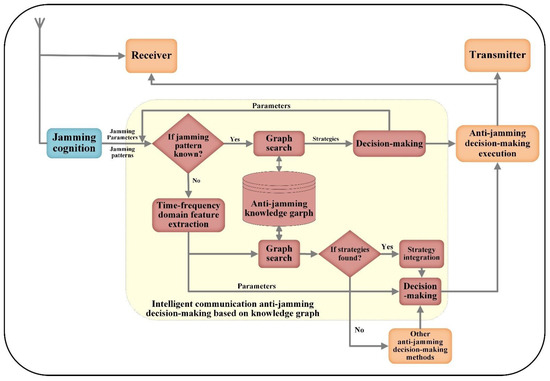
Figure 2.
The detailed block diagram of the anti-jamming decision-making module in Figure 1.
The intelligent communication anti-jamming decision-making module knowledge graph makes its anti-jamming decision following two different procedures: (1) if the jamming pattern is known, then the decision-making module will decide anti-jamming strategies by directly searching its knowledge graph based on the known jamming pattern and related parameters; (2) if the jamming pattern is unknown, then firstly the time-frequency domain features of unknown jamming pattern and its parameters need to be extracted, then the decision-making module will search its knowledge graph based on the acquired jamming pattern and its parameters for suitable anti-jamming strategies.
The decision-making module is implemented on the user equipment (UE) side by combining the anti-jamming knowledge graph and the proposed algorithm. One UE is considered in this paper; however, multiple UEs can also be realized due to the extensibility of the knowledge graph, which is also the advantage of the proposed approach.
Therefore, in the case of prior knowledge of communication jamming, the anti-jamming decision is made according to the search results of the knowledge graph, which effectively improves the speed and accuracy of the anti-jamming decision. When there is no prior knowledge about jamming in the knowledge graph, some jamming features stored in the knowledge graph can also be used to assist decision-making and improve the efficiency of decision-making.
2.2. Targeted Problems
2.2.1. Construction of Anti-Jamming Knowledge Graph
Since there is no research on the anti-jamming knowledge graph in existing literatures, how to construct a knowledge graph is the first problem to be solved. The prior knowledge of anti-conventional jamming patterns is abundant, and due to the small scale of data in anti-jamming field, knowledge is extracted mainly by manual methods in this paper, including jamming patterns, time-frequency domain features of jamming patterns, and anti-jamming strategies. Then, the knowledge is processed manually, and the relationship between jamming patterns, features and anti-jamming strategies is summarized to form Resource Description Framework (RDF) triplet data. Finally, the relational data are stored in the graph database Neo4j to form the anti-jamming knowledge graph of conventional jamming patterns. The detailed construction process and results of the anti-jamming knowledge map can be found in [26]. Based on this knowledge graph, all relations of an entity can be searched, or whether there is a correlation between the two entities can be judged, which provides the basis for the decision-making part.
2.2.2. The Search of Knowledge Graph for Unknown Jamming Patterns
There are no direct corresponding anti-jamming strategies for the unknown jamming patterns, and the factors determining the corresponding anti-jamming strategy are different with the difference of the unknown jamming patterns. How to use the anti-jamming knowledge graph to make anti-jamming decision for the unknown jamming patterns is an important problem. The processing method of unknown patterns in this paper is as follows: firstly, process the jamming parameters, and extract the time-frequency domain features of the jamming patterns; then, search the time-frequency domain features and match the corresponding anti-jamming strategies. The relationship from parameters to features can also be regarded as a triplet relationship, in which nodes are parameters and features, respectively, and edges are calculation rules. Since the Neo4j graph database cannot store calculation rules, the step from parameters to features needs to be realized through time-frequency domain feature extraction. The time-frequency domain feature extraction method will be studied in detail in Section 3.
2.2.3. Anti-Jamming Decision-Making Based on the Search of Knowledge Graph
Using the constructed anti-jamming knowledge graph to make search decisions, it is necessary to consider how to generate search results for diverse search requirements. Above all, since the knowledge graph stores knowledge relations rather than cases, for different parameters of the same jamming pattern, knowledge graph search results are the same, but the actual decision-making results may be different. This is because the knowledge graph stores all possible decision-making results of the patterns. Therefore, when the anti-jamming knowledge graph search is used to obtain anti-jamming decision-making, it is also necessary to integrate the strategies and select the optimal strategy. The main solution of this paper is to design a search decision-making algorithm, which can select the optimal strategy under different parameters and output anti-jamming strategies and corresponding decision parameters. The search decision-making algorithm and search sentence design will be carried out in Section 4.
3. Feature Extraction and Decision-Making Parameters
3.1. Time-Frequency Domain Features Extraction Method
3.1.1. Frequency Gap
We assume that the communication signal occupies the frequency range between and , and its bandwidth is . Additionally, the effective jamming signal shares the same frequency band with the communication signal, which is composed of single-frequency narrowband signals. At time , the central frequencies of all the jamming signals falling in the frequency range of are , , …, , respectively, and their bandwidths are , respectively. Frequency domain representations of the jamming signals are shown in Figure 3.
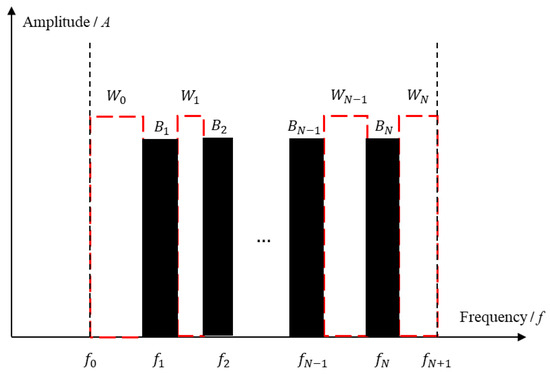
Figure 3.
Frequency domain representation of the jamming signals.
The frequency gap between any two adjacent jamming frequency points at time is
where . Defining , we can obtain that
If
the instantaneous frequency gap does not exist.
If
the instantaneous frequency gap exists.
The full-time frequency gap refers to a frequency gap that is not jammed at all times in the settings; namely, the intersection of all the instantaneous frequency gaps at different times. It can be calculated by using the above instantaneous frequency gaps. If the full-time frequency gap researches the bandwidth requirement threshold, then the system considers the full-time frequency gap as exists; otherwise, the system denies that there is a full-time frequency gap.
Deduction:
- Full-time frequency gap exists ► Instantaneous frequency gap exists
- Instantaneous frequency gap does not exist ► Full-time frequency gap does not exist
3.1.2. Power Margin
The expression of the jamming-to-signal ratio (JSR) is shown in Equation (6):
where is the input signal power reaching the receiver, and is the jamming power.
JSR can be used to measure the relationship between jamming power and target communication signal power, so as to study the influence of jamming on communication signal. To simplify the calculation, according to [27], we assume that jamming effects as long as reaches 0 dB.
The JSR that meets the jamming condition is the effective JSR threshold of jamming. If the jamming power can reach this threshold, the power margin does not exist; otherwise, the power margin exists.
3.1.3. Time Gap
During the time slot when there is no jamming signal and the power margin exists, transmission is almost not affected by jamming. If such a time slot exists, a time gap exists.
3.2. Communication Decision-Making Parameter
After obtaining the anti-jamming strategies according to the knowledge graph search results, it is necessary to assign proper parameters for each strategy. The anti-jamming strategies considered in this paper mainly include: adaptive frequency change, adaptive frequency hopping, power adaptive and adaptive time hopping.
In the time-frequency domain feature extraction process, the time-frequency parameters of the jamming are obtained, while in order to realize anti-jamming communication, the system needs to decide the optimized communication parameters under the jamming influence to acquire optimized communication parameters, so that the jamming signals will have minimum influences on the transmission of communication signals. Therefore, the purpose of anti-jamming parameter decision-making is to acquire the optimized communication parameters according to the time-frequency parameters of the jamming, to ensure the optimal communication signal transmission performance.
3.2.1. Frequency Domain Decision-Making Parameters
The frequency domain anti-jamming strategies include adaptive frequency change and adaptive frequency hopping.
The decision-making parameters for the adaptive frequency change strategy mainly include the available communication frequency gap within the communication time. The method for this decision-making is to calculate the available frequency gap with a duration satisfying the communication time according to the frequency domain parameters of the jamming pattern. According to the theory presented in Section 3.1, we can calculate the frequency gaps between any two adjacent jamming frequency points of the jamming signal. The gap which can last during the entire communication time and has the frequency gap bandwidth that meets the requirements of communication bandwidth will be selected for the communication signal transmission.
The decision-making parameters for adaptive frequency hopping strategy are its frequency hopping set and dwell time. The method for the decision-making is to calculate the available frequency gap satisfying the lasting time of communication.
The instantaneous frequency gaps can be calculated based on the process introduced in Section 3.1. Then, the instantaneous frequency gaps within each dwell time that meets the requirements of communication bandwidth are recorded to form the set of frequencies for adaptive frequency hopping. For specific jamming patterns, there is a simpler decision-making method. Taking the frequency hopping strategy against the linear sweep jamming as an example, the linear sweep jamming can be regarded as a narrow band jamming sweeping through the jamming frequency band in a sweep cycle. The sweep jamming is divided into two parts. In each part, the swept frequency band of each part of jamming is regarded as the whole. Linear sweep jamming can be regarded as two partial frequency jamming bands whose dwell time is a half sweep cycle. Then, the decision-making parameters can be acquired as follows: the frequency gaps swept are selected as the available frequency band, respectively, in the first and last half of the frequency sweep period, and the frequency hop set is divided according to the communication bandwidth.
3.2.2. Power, Modulation and Code Decision-Making Parameters
The power adaptive decision-making parameter is transmitted power. Modulation and code decision-making parameters are modulation order and channel coding rate. In practical applications, we first select modulation order and channel coding rate according to the requirements, and then determine the reliable transmission power. Therefore, these two decision-making parameters can be discussed together.
Communication transmission requirements can be divided into two categories: minimum transmission power consumption and maximum transmission rate. For minimum transmission power consumption, we adopt the lowest-order modulation and the minimum channel coding rate. For maximum transmission rate, we adopt maximum order modulation and maximum channel coding rate. The transmitted power is determined according to the following formula:
where is the jamming signal power, is the communication signal power, is the signal-to-interference ratio threshold of the receiver under modulation and coding, and is the part where the JSR exceeds the threshold. According to [27], the jamming effects when the JSR is less than 0 dB. With the purpose of reliable communication transmission, it is necessary to make more than 0 dB.
3.2.3. Time Domain Decision-Making Parameters
The decision-making parameter of adaptive time hopping is dwell time. The determination method is as follows: choose transmission in time slot with no jamming; choose silence in time with jamming.
4. Decision-Making Algorithm Based on Anti-Jamming Knowledge Graph
4.1. Decision-Making Algorithm
4.1.1. Algorithm Description
The anti-jamming knowledge graph can be regarded as a combination of several triples. Each node in the graph represents an entity of communication anti-jamming knowledge, and the edge represents the relationship between two nodes. If a triple is regarded as a one-way relationship, the initial node is called the head node. The head node points to the tail node in the triple through the relation edge. The search process of anti-jamming knowledge graph is to utilize two entities in a triplet relation to search the other entities.
In this paper, the communication anti-jamming decision-making algorithm based on knowledge graph is divided into two steps: strategy extraction and strategy fusion.
Strategy extraction is the process of obtaining the anti-jamming strategies corresponding to the jamming pattern by searching the anti-jamming knowledge graph. Specifically, we take the jamming patterns as the head node and take the anti-jamming relation (i.e., head node and relational edge) to search the anti-jamming strategies (i.e., tail nodes) when the jamming patterns are known. However, if the jamming patterns are unknown, we first obtain the time-frequency domain features of the unknown jamming patterns by the time-frequency domain feature extraction method. Then, we take the time-frequency domain features as the head node and the anti-jamming relation as the relational edge, search the tail node, and obtain the anti-jamming strategies corresponding to the time-frequency domain features. Finally, we obtain the corresponding parameters of each anti-jamming strategy by the communication parameter decision method described in Section 3.2. Each strategy-parameter set can be expressed as , where represents an anti-jamming strategy, and represents the corresponding decision-making parameters of the anti-jamming strategy.
Multiple anti-jamming strategies may be obtained in the search process, and strategy fusion is to integrate the possible anti-jamming strategies after strategy extraction to obtain the optimal strategy. Firstly, taking the intersection of the anti-jamming strategies in the same domain and the union set of anti-jamming strategies in different domains, we obtain the anti-jamming strategy set of preliminary fusion, where represents the strategy set and represents the set of each strategy parameter set. Then, we further optimize the strategy set after strategy fusion according to the communication requirements and select the strategy with the lowest communication cost which can ensure the communication transmission to improve the communication transmission efficiency. Finally, the anti-jamming decision-making is formed. Assuming that the extracted anti-jamming strategy includes the frequency domain and the power domain, when the purpose of the anti-jamming can be achieved by adopting only the frequency domain strategy, the communication cost is lower at the same time. In this regard, the power domain strategy can be discarded, and the frequency domain strategy can be the final optimal strategy.
The specific process of the decision-making algorithm is shown in Algorithm 1. It is assumed that we can extract the characteristics of the jamming signal at the current moment and search for the strategy in each communication time slot. After initialization, first obtain the information of the jamming signal (line 2). According to the information, determine whether the jamming pattern is known (line 3). Directly search for strategies in the anti-jamming knowledge graph for known jamming patterns (line 4). To unknown jamming patterns, the jamming period should be divided into multiple time slots. In each time slot, use the time-frequency domain feature extraction method to extract the time-frequency domain features of jamming patterns (line 6), and then search for strategies in the current time slot according to the features by the knowledge graph (line 7). Then, calculate the corresponding parameters of strategies to form the ‘strategy-parameter’ set in the time slot (line 8) by the communication parameter decision-making method. Finally, fuse strategies in each time slot (line 9), where is the fusion symbol.
| Algorithm1 Communication anti-jamming decision-making algorithm based on the knowledge graph |
| 1: Initialization: 2: The receiver obtains the jamming patterns and parameters from the jamming sensing module; 3: if jamming pattern is known 4: The receiver directly obtains the strategy set by anti-jamming knowledge graph; else 5: for t = 1, 2, …, T do 6: The receiver obtains the time-frequency features by time-frequency domain features extraction method; 7: The receiver searches for the strategy set according to the features by anti-jamming knowledge graph; 8: The receiver calculates the corresponding parameters of strategies according to the communication parameter decision method and obtains set ; 9: The receiver fuses strategies, ; 10: t = t + 1; end for |
4.1.2. Strategy Fusion Method
The proposed strategy fusion method optimizes and prioritizes the strategies according to the communication requirements to reduce the communication cost.
Common communication decision criterion mainly includes the minimum power consumption criterion and the maximum transmission rate criterion.
- After selecting the best communication channel under the minimum power criterion, we preferentially adopt the lowest order modulation coding mode. The transmission power corresponding to the channel environment and bit error rate is the minimum consumption power.
- After selecting the best communication channel under the maximum transmission rate criterion, we preferentially adopt the highest order modulation coding mode, and the corresponding transmission power is the maximum rate power.
Under the requirements of these two criteria, JSR threshold of the receiver in Formula (7) need to be determined according to the bit error rate requirements of different modulation coding modes.
Strategy priorities are classified as follows:
Frequency domain strategy: adaptive frequency change > adaptive frequency hopping.
Power domain policy: Adopt the lowest power strategy with the lowest modulation order under the minimum power criterion; Adopt the lowest power strategy with the highest modulation order under the maximum transmission rate criterion.
Among different domain policies, frequency domain strategy > power domain strategy > time domain strategy.
4.2. Anti-Jamming Knowledge Graph Search Statement Design
The process of extracting anti-jamming strategies from the anti-jamming knowledge graph is as follows: first, input different jamming patterns into the anti-jamming knowledge graph to determine/select/calculate the corresponding anti-jamming strategies and parameters. This input and output mode are similar to the knowledge graph question answering system. The difference is that the transmission and execution of anti-jamming decision-making are mostly carried out by machine language, which can save the semantic analysis step of the question answering system. The effective search can be realized only by matching the common input and output types in practical application to the search statement template, namely the “question answering template” used in the graph database.
4.2.1. Question Answering Template Design
The question answering (Q&A) template is essentially a sub-graph of the anti-jamming knowledge graph. For example, the template ‘entity + attribute’ represents nodes and an edge in the graph. Because the large-scale data set for the anti-jamming knowledge questions is not sufficient, this paper constructs the question template manually based on the constructed anti-jamming knowledge graph, and designs the type template of the anti-jamming knowledge question, as listed in Table 1.

Table 1.
Anti-jamming knowledge question answering (Q&A) template.
4.2.2. Question Classification
In the process of question answering module design, we classify questions and combine/match them with the corresponding query template. In practical application, the proposed method utilizes the machine language as the inputs of the anti-jamming knowledge graph, and its question directivity is obvious. Moreover, because of the small scale of the anti-jamming problem template, questions can be manually classified. The question and the corresponding query template are listed in Table 2.

Table 2.
Questions and corresponding query template examples.
For example, in Table 2, the question ‘How to counter sweep jamming?’, we take the frequency sweep jamming as the query condition, fill the query template, and then map it into a complete Cypher query statement. The query result is returned after the query in the Neo4j graph database.
5. Simulation Results and Discussion
5.1. Simulation of Time-Frequency Domain Feature Extraction
The purpose of the time-frequency domain feature extraction of the unknown jamming pattern is to obtain the head node of the unknown jamming pattern in the anti-jamming knowledge graph. We adopt the recall of the time-frequency domain features extracted to verify the performance of the proposed algorithm.
Recall is a metric widely used in the field of information retrieval and statistics to evaluate the quality of the search results. The formula of recall can be expressed as:
where is the recall, is the number of positive samples recognized, and is the number of the unrecognized positive samples. Recall can well demonstrate the ability and effect of positive sample recognition. In our simulations, recall is computed as a measure for the quality of feature extraction, where represents the count of successful time-frequency domain feature extraction, and represents the count of the failed ones.
The validation process is: firstly, adopt the algorithm to extract the time-frequency domain features of the input jamming patterns with known parameters; then, the recall of feature extraction in different domains are computed and analyzed. We initialize sensing parameters to simulate the real data from the jamming cognition module for the simulation experiment. The sensing parameters details are shown in Table 3. Here, we only take frequency domain feature extraction as an example considering the paper length limit.

Table 3.
Sensing parameters of time-frequency domain feature extraction.
Related parameters used in our simulations are set as follows: the available communication frequency band is set to be 30 MHz~2.5 GHz, namely the communication bandwidth 5 MHz. The starting and stopping frequency range of the jamming pattern is set to be 30 MHz~2.5 GHz; the bandwidth of partial frequency band jamming and multi-tone jamming range is set to be 500 kHz~300 MHz; the instantaneous bandwidth of high-speed collision jamming and sweep jamming range is set to be 500 kHz~300 MHz. Perception error rate is the ratio of the perceived frequency deviation to the true value from the jamming sensing module. The simulation results are shown in Figure 4.
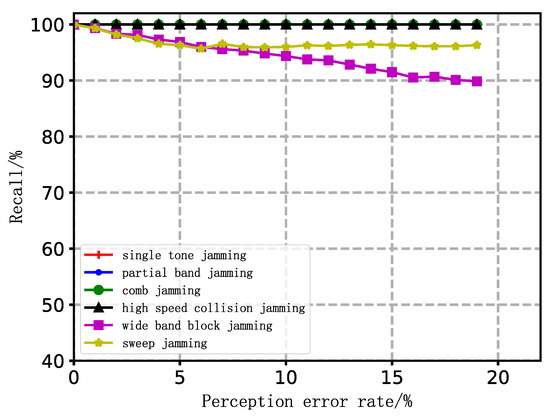
Figure 4.
Frequency domain feature extraction recall.
The simulation result shows that the recall of frequency domain feature extraction is higher when the jamming pattern is narrowband or instantaneous narrowband. It is also proved that the proposed feature extraction method has strong robustness against perception error. Our analysis suggests that when the bandwidth of the jamming signal is relatively narrow compared with the communication frequency band, the jamming cannot cover the available frequency band, and the jamming parameters perceived under a certain error cannot cover the available frequency band. Thus, the original frequency domain features are still maintained, and the feature extraction algorithm can recognize and extract in this case. Compared with narrowband or instantaneous narrowband jamming patterns, the recall of frequency domain feature extraction of wideband block jamming patterns decreases slowly with growing perception error because the bandwidth of the jamming signal is relatively wider than the communication frequency band, which is consistent with our analysis. It is indicated that the proposed frequency domain feature extraction method has the ability to effectively extract jamming features.
Then, the wideband blocking jamming scenario is considered: in our simulations, the available communication frequency band is set as 30 MHz~2.5 GHz, then the communication bandwidth is 5 MHz; the bandwidth of wideband blocking jamming is set to be 30 MHz~300 MHz (narrow), 300 MHz~1 GHz (medium), and 1 GHz~2.5 GHz (wide), respectively. Simulation results are shown in Figure 5.
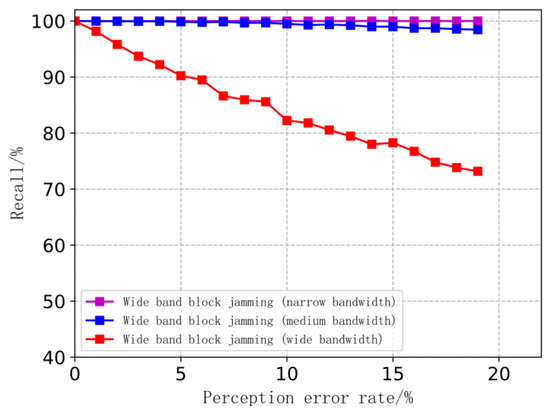
Figure 5.
Recall of frequency domain feature extraction of broadband blocking jamming.
5.2. Simulation of Decision-Making Result
In this section, the anti-jamming decision-making is under the conditions of known jamming patterns and unknown jamming patterns. We utilize the py2neo package to invoke the existing knowledge graph database which is relevant to the anti-jamming, and then perform the simulation experiment by Python. The simulation parameters details are shown in Table 4.

Table 4.
Simulation parameters of the decision-making algorithm.
The computational complexity of the proposed scheme is calculated by the communication timeslot, knowledge graph search time (about 60 ms per search), total number of timeslots and number of jamming patterns (i.e., 100 × 0 × 3000 × number of jamming patterns).
5.2.1. Simulation of the Decision-Making Result of Known Jamming Patterns
In this section, we mainly simulate the conventional jamming patterns. Assuming that the jamming sensing module can give the jamming patterns and parameters, we compare whether the anti-jamming strategies and decision-making parameters derived from the communication anti-jamming decision-making algorithm based on the knowledge graph match the prior anti-jamming strategies and parameters to check the accuracy of the decision-making algorithm. The simulation results are shown in Figure 6.
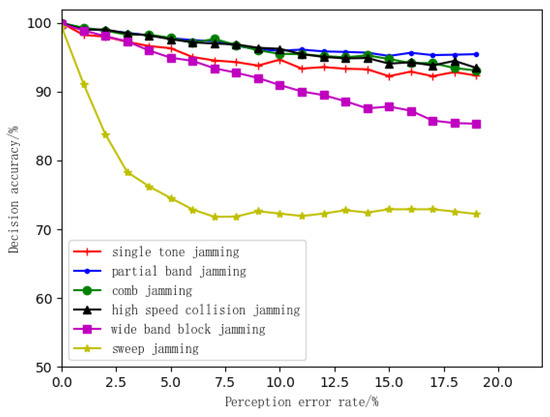
Figure 6.
Decision accuracy curves of known jamming patterns under perception errors.
As seen from the results in Figure 6, the reliability of the decision-making algorithm is less affected by perception error when the jamming patterns have a narrow bandwidth and limited jamming frequency coverage characters (i.e., single-tone jamming, partial band jamming, comb jamming and high-speed collision jamming). It also confirmed that the proposed algorithm has good robustness.
On the other hand, the jamming bandwidth is so wide that it covers the whole communication frequency band for wideband block jamming. Once there is a large error in the jamming bandwidth perception and the starting and stopping frequency, the probability that the decision-making result is jammed will increase.
Besides, for sweep jamming patterns, the FH pattern generated by the decision-making algorithm can induce serious errors when the perception of sweep starting and stopping frequency and its period contain error. Thus, the algorithm accuracy is vulnerable even if the perception error is small.
In this paper, we assume that the starting and stopping frequencies of sweep jamming are randomly generated. When the starting and stopping frequencies of sweep jamming do not cover the communication frequency band completely, the frequency change strategy will be adopted. In this regard, when the perception error rate is large, the decision-making algorithm might choose the frequency change strategy, and the decision is wrong. On the other hand, if the starting frequency of the sweep jamming is high, the jamming will not completely cover the communication frequency band, and then the proposed algorithm will choose the correct strategy, namely the frequency change strategy. Therefore, the decision accuracy of the algorithm only depends on whether the randomly selected frequency point is covered by the jamming or not. As a result, the decision accuracy curve shows a steady trend.
5.2.2. Simulation of the Decision-Making Result of Unknown Jamming Patterns
In this section, we assume that the perception module of the system fails to provide the parameters of the jamming patterns, but still successfully provides the jamming time-frequency domain parameters. After extracting the time-frequency domain features of the unknown jamming patterns, the algorithm searches the corresponding strategies based on the acquired time-frequency domain features, then outputs the decision.
The method to verify the accuracy of the decision-making algorithm of unknown jamming patterns is to input the parameters of the generated jamming pattern but set the pattern as unknown (the jamming patterns generated by this method are called pseudo-unknown patterns of the original jamming). Then, the simulations verify whether the decision result of this pseudo-unknown jamming pattern is accurate or not. The simulation results are shown in Figure 7.
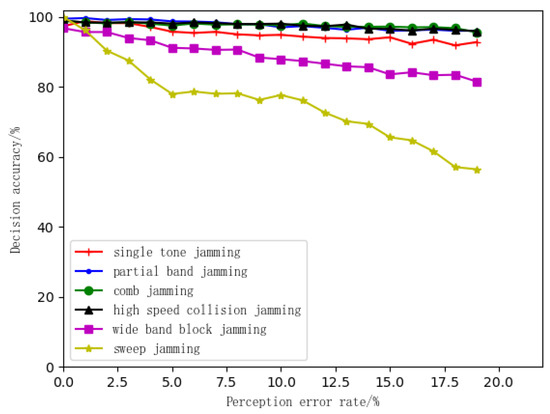
Figure 7.
Decision accuracy curves of unknown jamming patterns under perception errors.
Figure 7 shows results of algorithm performance when different pseudo-unknown jamming patterns are considered, including single-tone jamming, partial frequency band jamming, comb jamming, high-speed collision jamming, wideband block jamming and sweep jamming. It can be seen from the simulation results that for single-tone jamming, partial frequency band jamming, comb jamming, high-speed collision jamming and wideband block jamming, the decision-making method has good robustness, the decision accuracy is around 90%, and the reliability is less affected by the perception error.
Different from the case where the known pattern is sweep jamming, the accuracy of the decision-making algorithm gradually becomes stable when the perceptual error rate increases. For the pseudo-unknown pattern of sweep jamming, the decision-making accuracy is affected by the perceptual error to a certain extent. The analysis believes that this is because the anti-jamming strategy is obtained by searching the anti-jamming knowledge graph in the case of known styles, the possible range of the anti-jamming strategy is smaller, and the curve of the decision accuracy is rather smooth.
In the case of an unknown pattern, the time-frequency domain features of the jamming pattern are obtained by the time-frequency domain feature extraction algorithm, and the anti-jamming strategy can be selected in a large range, which leads to a certain decrease in the accuracy due to the influence of the perception error.
As can be seen from the above simulation results, the proposed anti-jamming decision-making algorithm has great advantages over the existing methods in terms of the number of jamming patterns and decision-making time. The specific comparison is given in the Table 5.

Table 5.
Comparison with existing work.
Existing methods mainly achieved their optimized decision-making for a particular jamming pattern based on a few communication system parameters, such as communication frequency and transmission power. The resultant optimizing results may not render the best results when more communication parameters need to be considered. By comparison, the proposed decision-making algorithm based on the anti-jamming knowledge graph can not only deal with multiple jamming patterns, but can also consider multiple communication parameters simultaneously. The anti-jamming knowledge graph has strong extensibility that can add anti-jamming communication parameters in later work.
When the jamming pattern changes, the reinforcement learning methods need to relearn all the parameters from scratch, which will lead to more computational complexity and slower response. The proposed decision-making algorithm directly extracts the anti-jamming strategy by utilizing the advantage of prior knowledge for known jamming patterns. For unknown jamming patterns, prior knowledge can also be utilized to effectively reduce decision complexity.
6. Conclusions
To reduce the complexity of the communication anti-jamming decision-making process, make full use of domain prior knowledge, and improve the intelligent decision-making level, a communication anti-jamming decision-making algorithm based on knowledge graph is proposed. The proposed algorithm is based on the anti-jamming knowledge graph, and separately processes the jamming cognitive data. For known jamming patterns, the anti-jamming strategy is directly obtained by searching the graph; for unknown jamming patterns, the proposed feature extraction method of the time-frequency domain is used to calculate the time-frequency domain characteristic parameters of the jamming pattern, and the time-frequency domain of the feature is judged. Then, the anti-jamming strategy corresponding to the time-frequency domain features is searched in the knowledge graph. Anti-jamming strategy fusion is performed, and the final anti-jamming decision-making results are outputted. The simulation results show that the time-frequency domain feature extraction method can accurately extract the time-frequency domain features of unknown jamming patterns, and it is still robust in the presence of errors in jamming sensing. The communication anti-jamming decision-making algorithm based on the knowledge graph can deal with multiple different jamming patterns, and the decision-making results are robust to jamming sensing errors, which can achieve accurate anti-jamming decision-making results under the complex and changeable electromagnetic environment and inaccurate interference cognition.
The principal theoretical implication of this study is that utilization of a domain knowledge graph can reduce algorithm complexity. The major limitation of this study is that new jamming patterns are constantly emerging and the anti-jamming knowledge graph is difficult to complete. A further study could usefully explore how combining existing knowledge graphs with reinforcement learning could improve the convergence speed of the algorithm. This would be a fruitful area for further work.
Author Contributions
Conceptualization, Y.N. and X.F.; methodology, S.K.; software, S.K.; validation, X.F. and S.K.; formal analysis, Y.N.; investigation, Y.N.; resources, Y.N.; data curation, X.F.; writing—original draft preparation, S.K.; writing—review and editing, X.F. and P.X.; visualization, X.F.; supervision, Y.N. and X.F.; project administration, X.F.; funding acquisition, Y.N. All authors have read and agreed to the published version of the manuscript.
Funding
This research is supported by the National Science Foundation of China under contract No. U19B2014.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
The data presented in this study are available from the author, X.F., upon reasonable request.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Grover, K.; Lim, A.; Yang, Q. Jamming and anti-jamming techniques in wireless networks: A survey. Int. J. Ad Hoc Ubiquitous Comput. 2014, 17, 197–215. [Google Scholar] [CrossRef] [Green Version]
- Torrieri, D. Principles of Spread-Spectrum Communication Systems, 4th ed.; Springer Science & Business Media: New York, NY, USA, 2018. [Google Scholar]
- Lichtman, M.; Poston, J.D.; Amuru, S.; Shahriar, C.; Clancy, T.C.; Buehrer, R.M.; Reed, J.H. A communications jamming taxonomy. IEEE Secur. Priv. 2016, 14, 47–54. [Google Scholar] [CrossRef]
- Pirayesh, H.; Zeng, H. Jamming Attacks and Anti-Jamming Strategies in Wireless Networks: A Comprehensive Survey. IEEE Commun. Surv. Tutor. 2022. [Google Scholar] [CrossRef]
- Miao, W.; Song, X.; Niu, Y.; Tong, T. Anti-jamming decision-making in wireless communication based on Rough Sets Theory. In Proceedings of the International Conference on Mechatronic Sciences, Electric Engineering and Computer (MEC), Shengyang, China, 20–22 December 2013; pp. 2535–2539. [Google Scholar]
- Hui, X.; Niu, Y.; Mi, Y. Decision method of anti-jamming communication based on binary artificial bee colony algorithm. In Proceedings of the 4th International Conference on Computer Science and Network Technology (ICCSNT), Harbin, China, 19–20 December 2015; pp. 987–991. [Google Scholar]
- Li, J.; Tang, X.; Gao, L.; Chen, L. Satellite communication anti-jamming based on artificial bee colony blind source separation. In Proceedings of the 6th International Conference on Communication, Image and Signal Processing (CCISP), Chengdu, China, 17 December 2021; pp. 240–244. [Google Scholar]
- Ye, F.; Zhou, Z.; Tian, H.; Sun, Q.; Li, Y.; Jiang, T. Intelligent Anti-Jamming Decision Method Based on the Mutation Search Artificial Bee Colony Algorithm for Wireless Systems. In Proceedings of the International Conference on Computer Science & Education (ICCSE), Atlanta, GA, USA, 7–12 July 2019. [Google Scholar] [CrossRef]
- Liu, M.; Wang, J.; Liu, L. Research on Intelligent Anti-jamming Communication with Transform Domain Communication System. In Proceedings of the International Conference in Communications, Signal Proccessing, and Systems, Singapore, 4 May 2019; pp. 949–955. [Google Scholar] [CrossRef]
- Ran, Y.; Cheng, Y.; Chen, D.; Wang, X. Intelligent Anti-jamming Decision Engine Based on BP Neural Network. J. Signal Process. 2019, 35, 1350–1357. [Google Scholar]
- Yang, H.; Xiong, Z.; Zhao, J.; Niyato, D.; Wu, Q.; Poor, H.V.; Tornatore, M. Intelligent Reflecting Surface Assisted Anti-Jamming Communications: A Fast Reinforcement Learning Approach. IEEE Trans. Wirel. Commun. 2020, 20, 1963–1974. [Google Scholar] [CrossRef]
- Han, H.; Xu, Y.; Jin, Z.; Li, W.; Chen, X.; Fang, G.; Xu, Y. Primary-User-Friendly Dynamic Spectrum Anti-Jamming Access: A GAN-Enhanced Deep Reinforcement Learning Approach. IEEE Wirel. Commun. Lett. 2021, 11, 258–262. [Google Scholar] [CrossRef]
- Zhou, Q.; Li, Y.; Niu, Y. A Countermeasure Against Random Pulse Jamming in Time Domain Based on Reinforcement Learning. IEEE Access 2020, 8, 97164–97174. [Google Scholar] [CrossRef]
- Xiao, L.; Lu, X.; Xu, T.; Wan, X.; Ji, W.; Zhang, Y. Reinforcement Learning-Based Mobile Offloading for Edge Computing Against Jamming and Interference. IEEE Trans. Commun. 2020, 68, 6114–6126. [Google Scholar] [CrossRef]
- Liu, X.; Xu, Y.; Jia, L.; Wu, Q.; Anpalagan, A. Anti-Jamming Communications Using Spectrum Waterfall: A Deep Reinforcement Learning Approach. IEEE Commun. Lett. 2018, 22, 998–1001. [Google Scholar] [CrossRef] [Green Version]
- Xu, J.; Lou, H.; Zhang, W.; Sang, G. An Intelligent Anti-Jamming Scheme for Cognitive Radio Based on Deep Reinforcement Learning. IEEE Access 2020, 8, 202563–202572. [Google Scholar] [CrossRef]
- Pujara, J.; Miao, H.; Getoor, L.; Cohen, W. Knowledge Graph Identification. In Proceedings of the International Semantic Web Conference, Sydney, Australia, 21–25 October 2013; pp. 542–557. [Google Scholar] [CrossRef] [Green Version]
- Oezsu, M.T. A survey of RDF data management systems. Front. Comput. Sci. 2016, 10, 418–432. [Google Scholar] [CrossRef] [Green Version]
- Bollacker, K. Freebase: A collaboratively created graph database for structuring human knowledge. In Proceedings of the ACM SIGMOD International Conference on Management of Data, Vancouver, BC, Canada, 10–12 June 2008; ACM: New York, NY, USA, 2008; pp. 1247–1250. [Google Scholar]
- Auer, S.; Bizer, C.; Kobilarov, G.; Lehmann, G.; Lehmann, J.; Cyganiak, R.; Ives, Z. DBpedia: A Nucleus for a Web of Open Data. In Proceedings of the Semantic Web, Busan, Korea, 11–15 November 2007; pp. 722–735. [Google Scholar]
- Abacha, A.B.; Zweigenbaum, P. MEANS: A medical question-answering system combining NLP techniques and semantic Web technologies. Inf. Process. Manag. 2015, 51, 570–594. [Google Scholar] [CrossRef]
- Tong, R.; Sun, C.L.; Wang, H.F.; Fang, Z.J.; Yin, Y.C. Construction of Traditional Chinese Medicine Knowledge Graph and Its Application. J. Med. Inform. 2016, 37, 8–13. [Google Scholar]
- Zhang, R.; Peng, J.; Yang, W.; Liang, L. The Semantic Knowledge Embedded Deep Representation Learning and Its Applications on Visual Understanding. J. Comput. Res. Dev. 2017, 54, 1251–1266. [Google Scholar]
- Lample, G.; Ballesteros, M.; Subramanian, S.; Kawakami, K.; Dyer, C. Neural Architectures for Named Entity Recognition; Association for Computational Linguistics: San Diego, CA, USA, 2016. [Google Scholar] [CrossRef]
- Ma, X.; Hovy, E. End-to-End Sequence Labeling via Bi-Directional LSTM-CNNs-CRF; Association for Computational Linguistics: Berlin, Germany, 2016. [Google Scholar] [CrossRef] [Green Version]
- Kou, S.; Niu, Y.; Zhang, H. Construction of knowledge graph based on conventional jamming patterns. In Proceedings of the EAI International Conference on Wireless and Satellite Systems, Harbin, China, 31 July–2 August 2021. [Google Scholar]
- David L, A. EW104: EW against a New Generation of Threats; Artech House: Fitchburg, MA, USA, 2015. [Google Scholar]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).