Protected Network Architecture for Ensuring Consistency of Medical Data through Validation of User Behavior and DICOM Archive Integrity
Abstract
1. Introduction
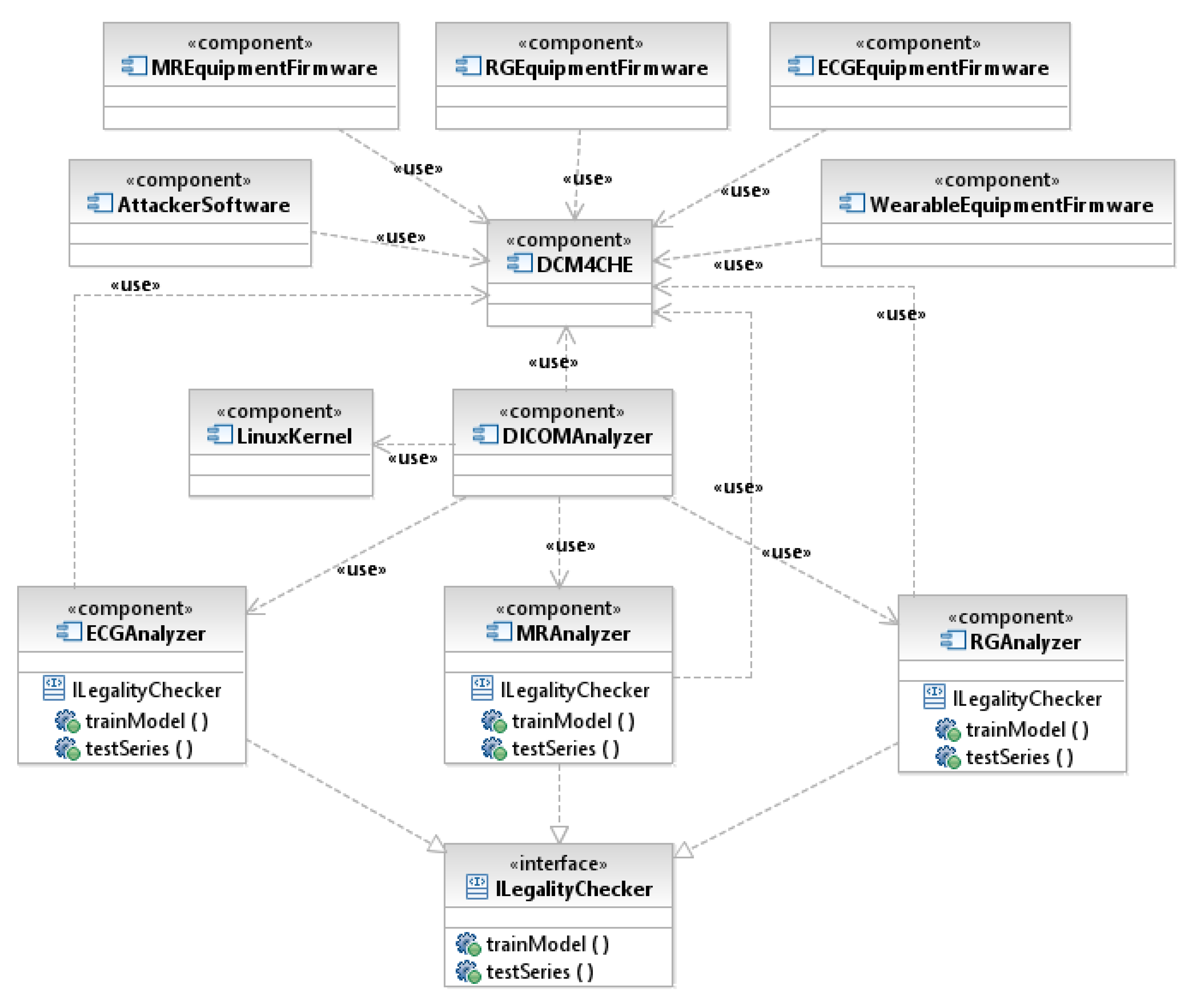
- Ensuring incoming data conformance with DICOM standards. This should be implemented on the server-side, the DICOM server or filtering component running as a front end for the DICOM server. The datum of interest is IOD (Information Objects Definition). An idea to propose a formal language to express IODs is not new [2]. Modern software like dcm4che [3] supports this validation.
- Watermarking medical images. The method proposed in [4], based on a reversible watermarking technique, provides authentication and self-correction by dividing an image into two regions: Region of Interest (ROI) and Region of Noninterest (RONI). Then, the ROI is embedded into the RONI so that any change of the image may be detected and can be self-restored back to the original image by extracting the ROI from the RONI. The work [5] proposes a security technique with patient authentication support, information confidentiality and integrity based on reversible watermarks. To provide integrity checking an MD5 (Message Digest 5) hash of the image is computed. Reversibility is achieved with compressed an R–S-Vector determined from the image (consists of bits indicating regular (1) or singular (0) state of a group of pixels). A watermark providing confidentiality and authentication services is constructed by aggregating the compressed R–S-Vector, the hash value and the patient ID. It is encrypted with AES (Advanced Encryption Standard) and embedded into medical images.
- Encryption of DICOM files. The work in [6] proposes the following algorithm for providing confidentiality, integrity and authenticity of the header and pixel data of DICOM images: an encryption and signature creation procedure, and a decryption and signature verification procedure. Singla and Singh [7] developed a framework proposing two different approaches to ensure cloud data security: the Extensible Authentication Protocol for authentication, and the Rijndael Encryption Algorithm used to encrypt sensitive data. Dorgham et al. [8] proposed a framework to secure transfer and storage of medical images on the cloud by using hybrid (a combination of symmetric and asymmetric) encryption algorithms. Their scheme consists of separate stages of hashing the DICOM header with SHA-3 (Secure Hash Algorithm 3) and encrypting pixel data with the result of the previous stage using an XTEA (eXtended Tiny Encryption Algorithm) algorithm.
- Application of artificial intelligence (AI) machinery to detect malicious tampering of medical data. Mirsky et al. [9] proposed an attack on the PACS network allowing changes in sensitive 3D imagery files using deep learning. They proposed a GAN (generative adversarial network) model helping to add or remove patterns related to lung cancer when editing 3D CT scans. The authors also mentioned use of digital signatures [10,11] as the best way to resist such attacks. They also noted that such a feature is implemented in actual PACS systems, but often is not configured in the proper way. Therefore, the supervised domain generic approach [12] is considered more robust in tampering detection.
- Application of User Behavior Analytics techniques [13] in Security Incident and Event Management systems. These systems contain all the data necessary to construct machine learning models, allowing discovery of patterns of abnormal activity in a dense event log, which often is considered as a big data stream [14,15,16,17]. Lee et al. [18] proposed methods to analyze security events, learn normal and threat patterns, construct event profiles and use common classification methods like Support Vector Machine, Random Forest and Naive Bayes, and proposed artificial neural network models to perform detection of malicious behavior in SIEM environments. The authors obtained accuracy near to 95% with an NSLKDD dataset [19] and 98–99% with a CICIDS2017 dataset [20]. Logical models are also applicable to model user behavior. Corapi et al. [21] proposed a model based on nonmonotonic learning allowing performance of revision of user behavior rules. They use Inductive Logic Programming machinery to train the model from examples.
2. Materials and Methods
2.1. Formalization of the Problem
2.1.1. Periodicity Correctness Model
2.1.2. Legality of Medical Data
2.1.3. Legality of User Actions
2.2. New Server Roles to Ensure Medical Data Consistency
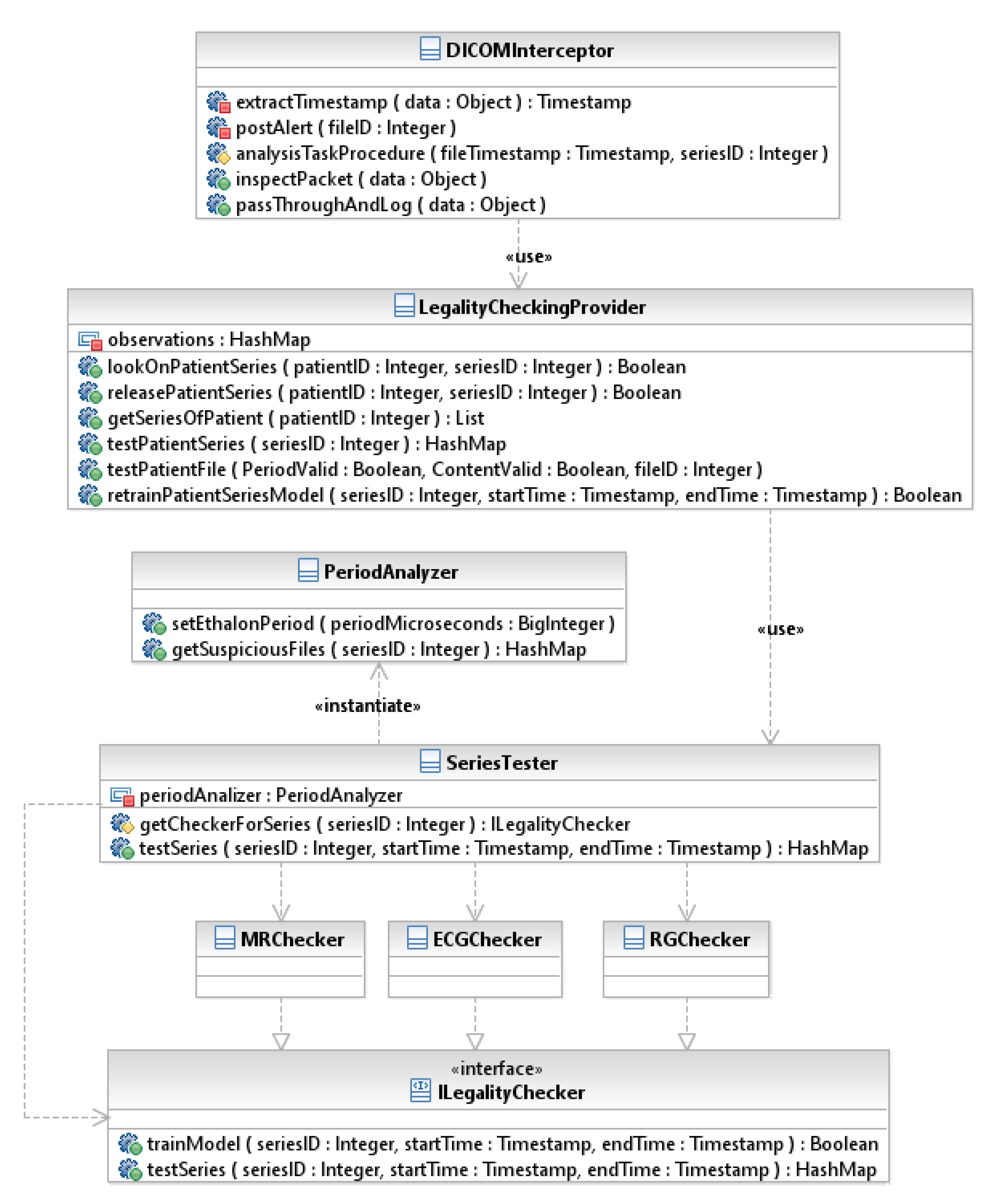
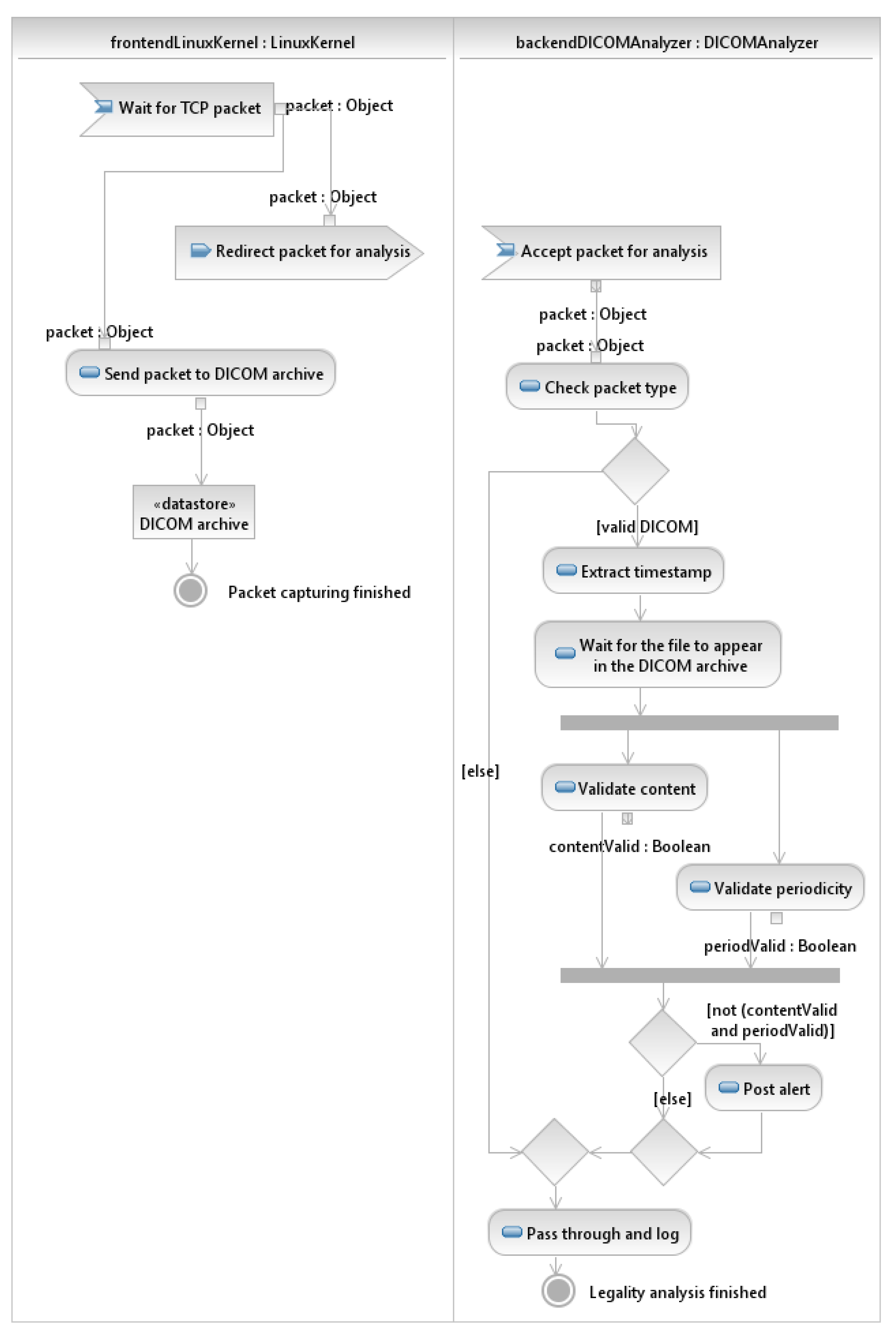
2.2.1. Validation of DICOM Archive Integrity
- DICOMInterceptor class is for inspecting DICOM packets, initiating content checking and generating alerts in case of detection of suspicious DICOM files. It is the main class interacting with LinuxKernel.
- LegalityCheckingProvider class is for configuration management and providing functionality for medical data analysis (testPatientSeries, testPatientFile methods). The patient’s medical data in the DICOM archive is only analyzed if tracking is enabled for the respective patient and data series (lookOnPatientSeries method). In this case, the associated machine learning models must be initialized with a training sample of regular legal data specified by a time interval (retrainPatientSeriesModel method).
- SeriesTester class loads and uses various plugins to check legality of data for different modalities (types of data series). It also uses the instance of PeriodAnalyzer to test periodicity of incoming data.
- PeriodAnalyzer class is for analyzing the periodicity of data incomings in accordance with the proposed periodicity correctness model (getSuspiciousFiles method).
- ILegalityChecker is a common interface each modality-checking plugin must implement to provide functionality for initialization and utilization of the machine learning model intended for data legality checking (trainModel and testSeries methods).
- MRChecker, RGChecker, ECGChecker are MR (Magnetic resonance imaging), RG (Radiographic imaging), ECG (Electrocardiography) modality sample checking plugins implementing ILegalityChecker interface, respectively.
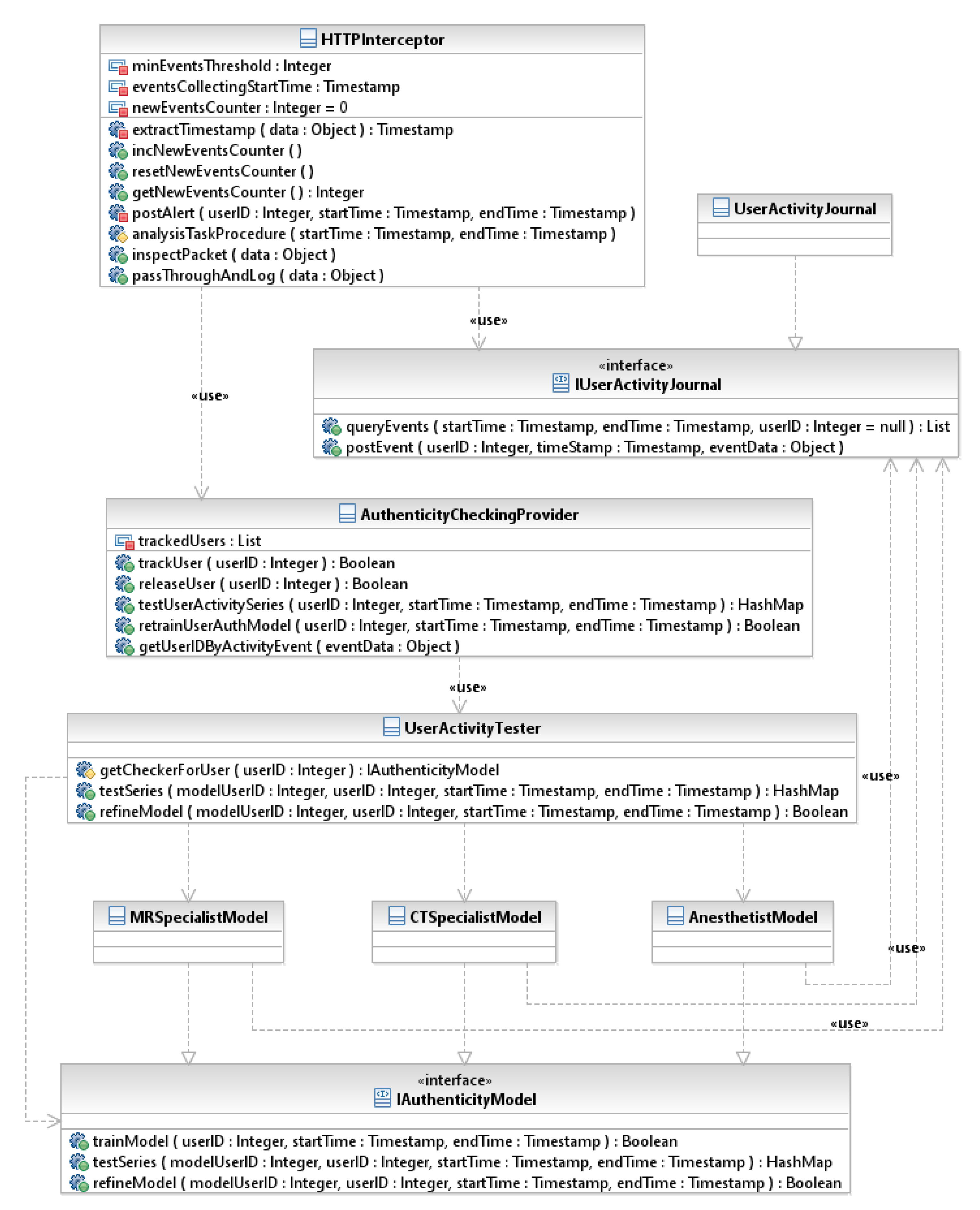
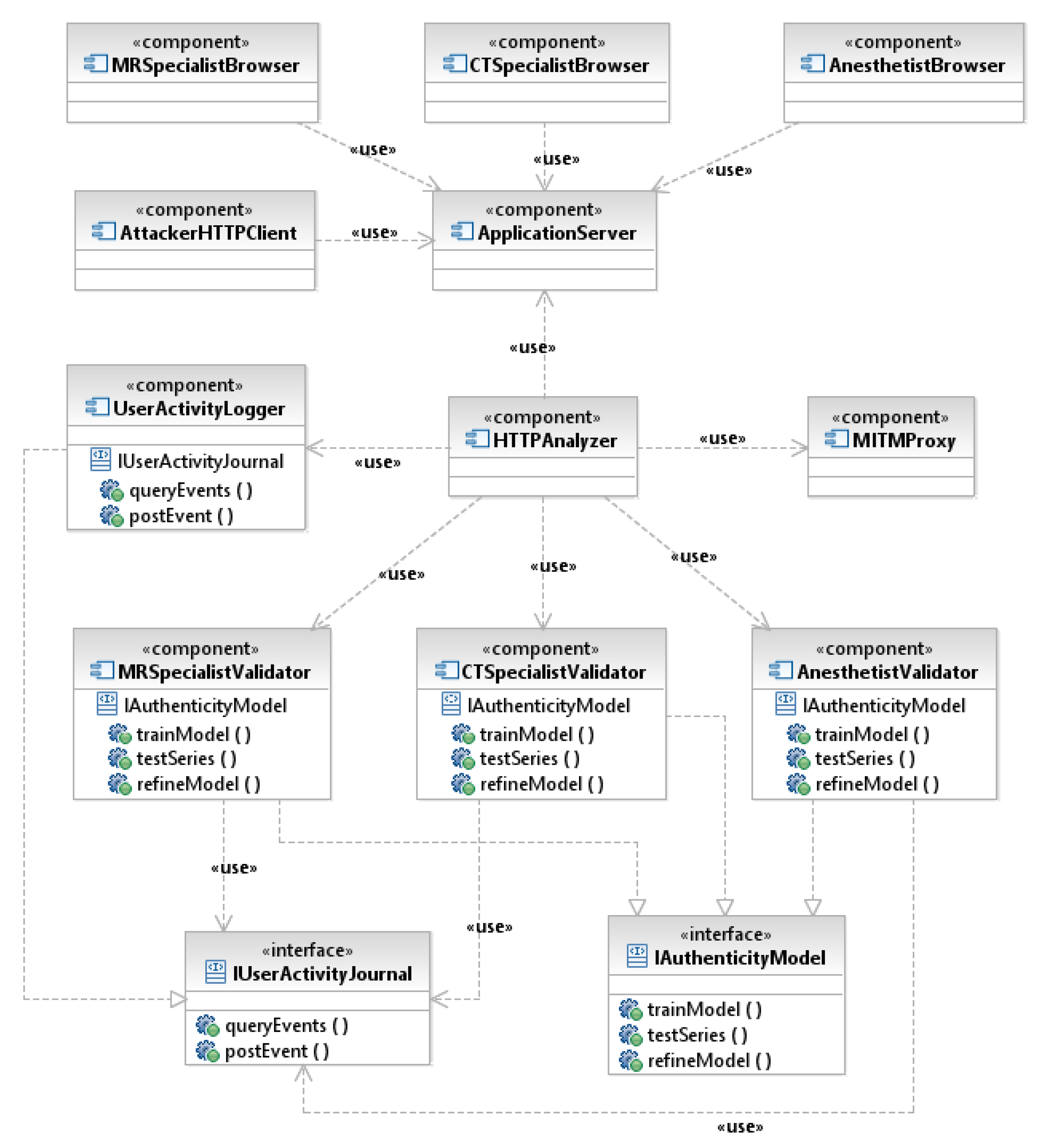
2.2.2. Validation of User Behavior
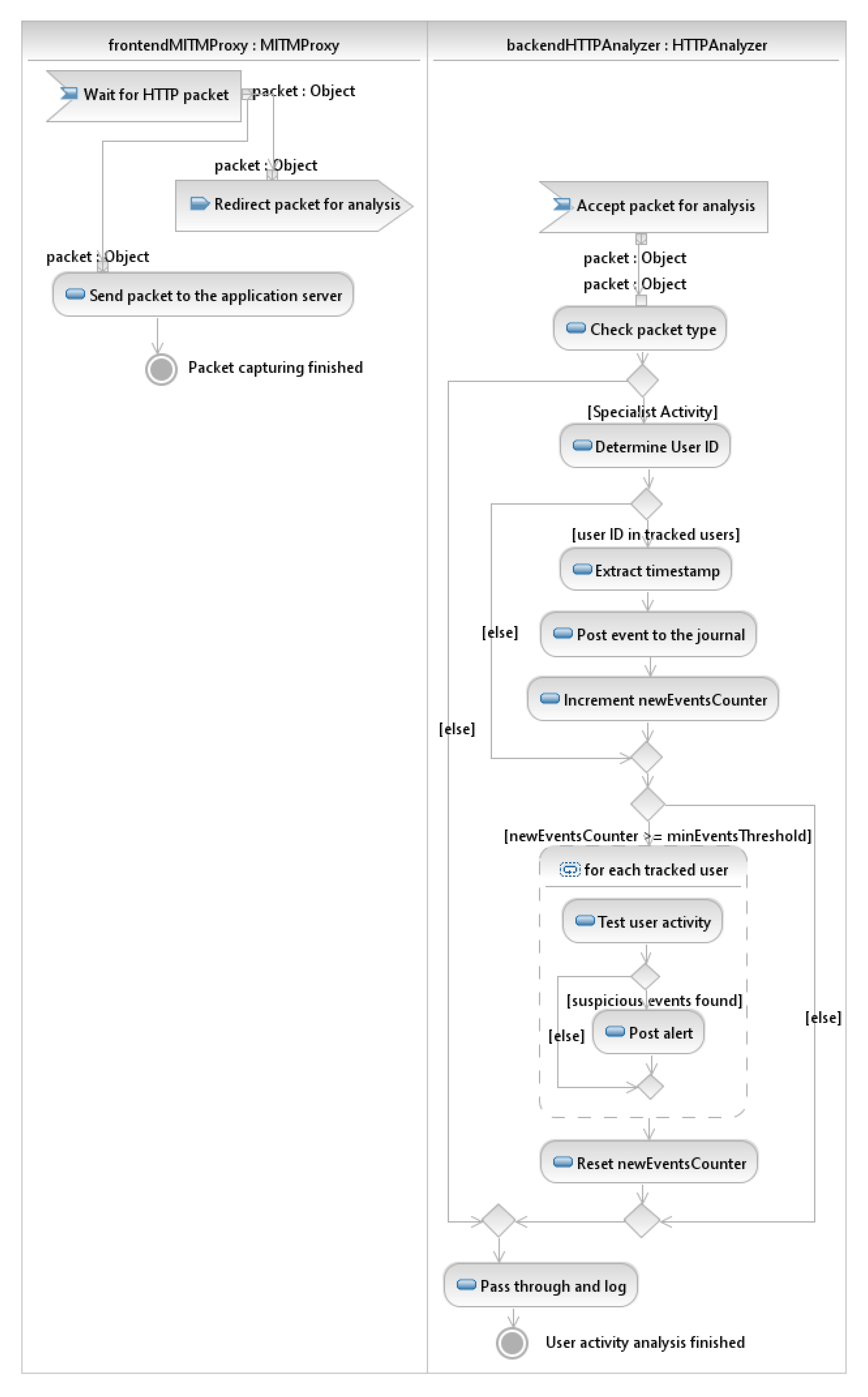
- HTTPInterceptor class is designed to parse HTTP packets, run content inspection and generate alerts in case of detection of dangerous user actions. This is the main class that interacts with mitmproxy.
- UserActivityJournal class is designed to manage user activity log and provide data to analytic components.
- IUserActivityJournal is an interface for working with the user activity log.
- AuthenticityCheckingProvider class is designed to manage configuration and provide compliance checking functionality for the User Behavior Analysis Component (HTTPAnalyzer). User activity data is only analyzed if tracking is enabled for the respective user (trackUser method). In this case, the associated machine learning models must be initialized with a training sample of regular legal data specified by a time interval (retrainUserAuthModel method).
- UserActivityTester class loads and uses various plugins to authenticate user activity to various medical professionals.
- IAuthenticityModel is a common interface that every behavior validation plugin for any medical specialization must implement to provide functionality for initialization and utilization of machine learning model intended for data legality checking (trainModel, refineModel and testSeries methods).
- MRSpecialistModel, CTSpecialistModel, AnesthetistModel are MR, CT (Computed tomography imaging), anesthesiologist specialist behavior validator plugins that implement the IAuthenticityModel interface, respectively.
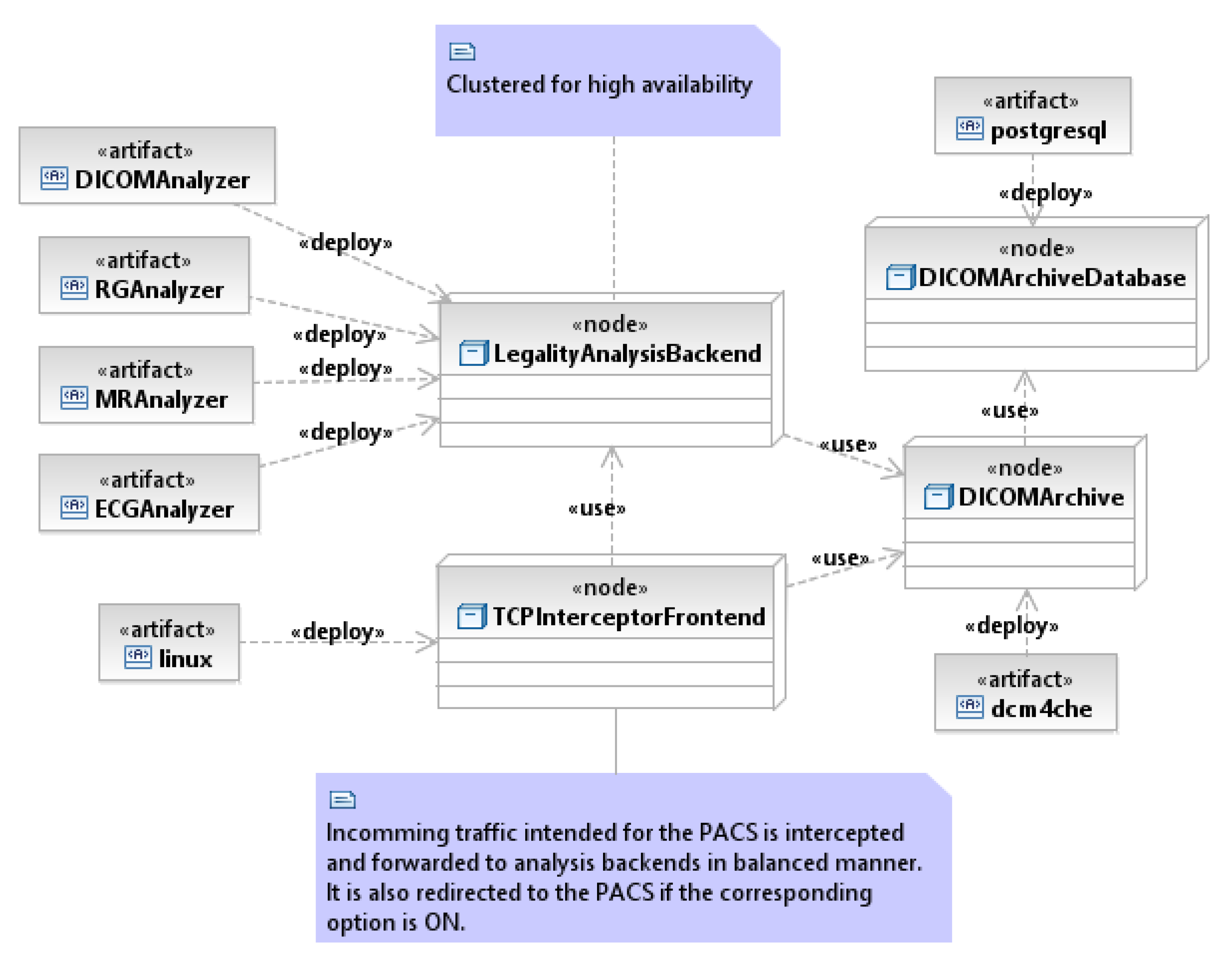
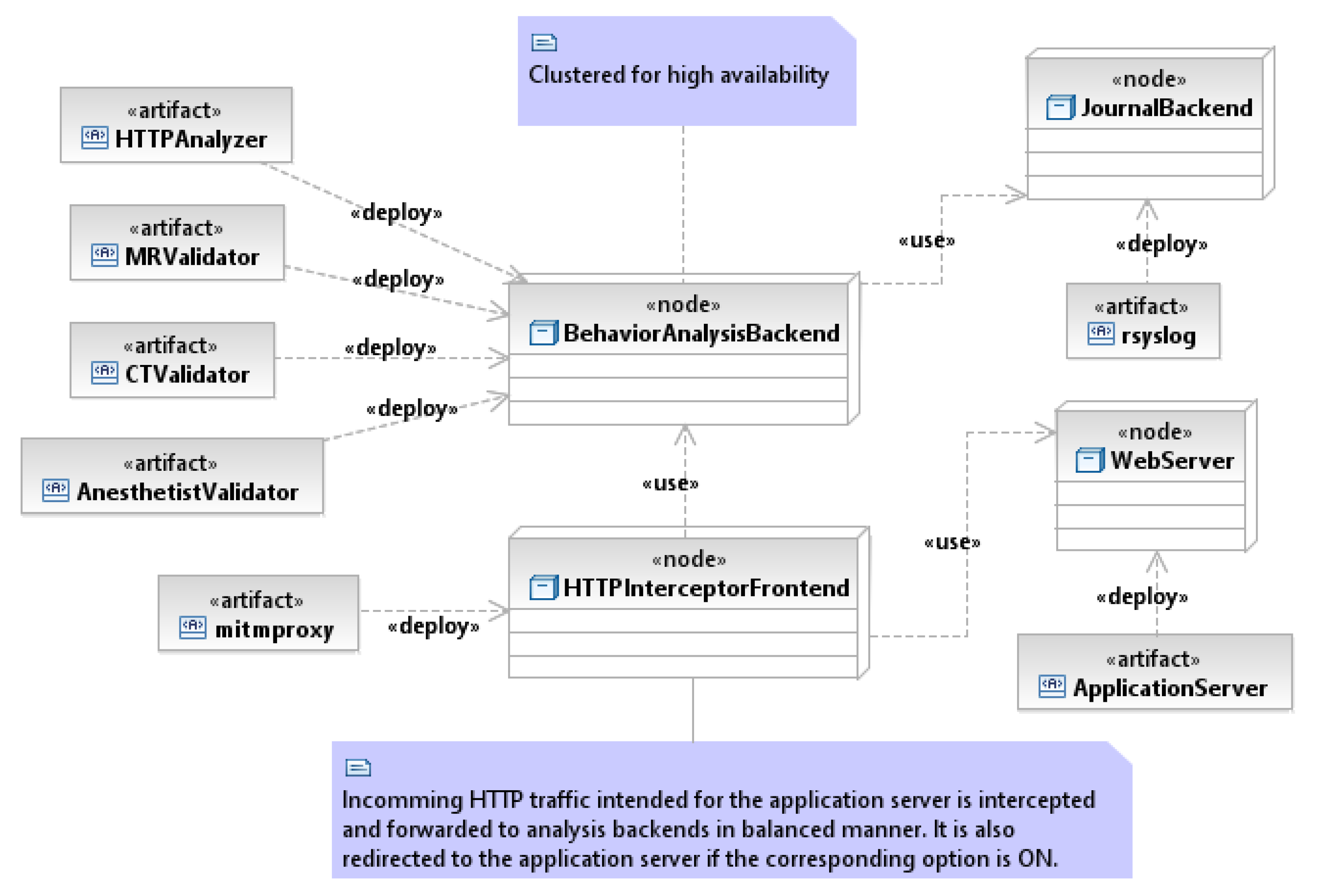
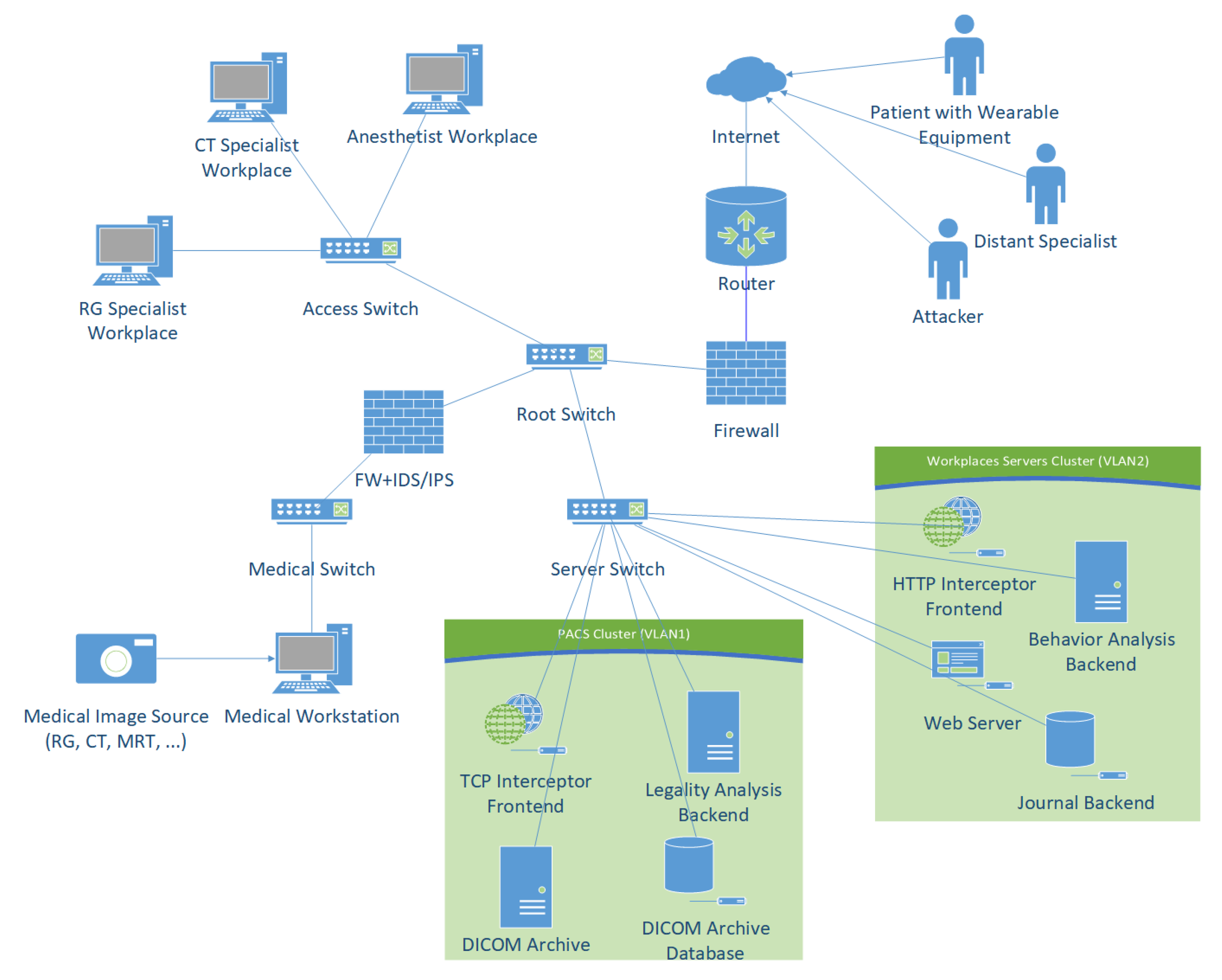
2.2.3. Place of Server Roles in Network Infrastructure
3. Discussion
4. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Appendix A. Classes for Validation of DICOM Archive Integrity
| Member Name | Member Purpose |
|---|---|
| inspectPacket | 1. Extracts timestamp from the data packet. 2. If data is valid DICOM file with timestamp, run the analyzing task asynchronously. |
| passThroughAndLog | Passes the packet through and logs this event. |
| extractTimestamp | Extracts timestamp from DICOM file. |
| postAlert | Posts alert for specifiled DICOM file. |
| analysisTaskProceduce | 1. Waits for the file with the specified timestamp appears in the DICOM archive. 2. Runs the analysis of this file. 3. If there are violations, posts alerts. |
| Member Name | Member Purpose |
|---|---|
| retrainPatientSeriesModel | Retrain ML model for specified series with specified data interval for training. |
| testPatientSeries | Returns hashmap with samples IDs as keys and their legality as <boolean, boolean> values. The first boolean in the tuple is period legality, the second boolean in the tuple is content legality. |
| testPatientFile | Returns period and content legality of the single specified patient file. |
| getSeriesOfPatient | Return observed series IDs for the patient. |
| releasePatientSeries | Remove the patient’s series from the observation list. |
| lookOnPatientSeries | Add a series of a patient to the observation list. |
| observations | Hashmap with patient IDs as keys and lists of series IDs as values. |
| Member Name | Member Purpose |
|---|---|
| testSeries | Returns hashmap with samples IDs as keys and their legality as <boolean, boolean> values. The first boolean in the tuple is period legality, the second boolean in the tuple is content legality. |
| getCheckerForSeries | Get the entry point in the appropriate plugin for specified data series. |
| periodAnalyzer | An instance of PeriodAnalyzer. |
| Member Name | Member Purpose |
|---|---|
| setEthalonPeriod | Sets the value of the period to check conformance of the time series with it. |
| getSuspiciousFiles | Returns hashmap with samples IDs as keys and their legality as boolean values. |
| Method Name | Method Purpose |
|---|---|
| trainModel | Train ML model for specified series with specified data interval for training. |
| testSeries | Returns hashmap with samples IDs as keys and their legality as boolean values. |

Appendix B. Classes for Validation of User Behavior
| Member Name | Member Purpose |
|---|---|
| minEventsThreshold | A minimum threshold of new events count to start analysis. |
| eventsCollectingStartTime | A timestamp when collecting new events has started. |
| newEventsCounter | A counter of new incoming user activity events to be analyzed further. |
| extractTimestamp | Extracts timestamp from HTTP headers. |
| incNewEventsCounter | Increments the counter of the new user activity events. |
| resetNewEventsCounter | Resets the counter of new user activity events to zero. Sets events collecting start time to current time. |
| getNewEventsCounter | Returns value of the counter of new user activity events. |
| postAlert | Posts alert for specified user activity time interval. |
| analysisTaskProcedure | 1. Runs the analysis of new events. 2. If there are suspicions, posts alerts. |
| inspectPacket | 1. Extracts timestamp from the data packet. 2. If data is valid HTTP with user action, increment counter of new events, and if it reaches minEventsThreshols, runs the analyzing task asynchronously. |
| passThroughAndLog | Passes the packet through and logs this event. |
| Member Name | Member Purpose |
|---|---|
| trackedUsers | List of IDs of tracked users. |
| trackUser | Add user identified by userID to tracking list. True is returned if the appropriate behavior model plugin is accessible and entry is not added yet. |
| releaseUser | Do not track user identified with userID anymore. True is returned if entry exists in the tracking list. |
| testUserActivitySeries | Returns hashmap with event timestamps as keys and their authenticity estimation as boolean values. ML model source is defined automatically by userID. |
| retrainUserAuthModel | Retrain ML model for specified user with specified data interval for training. |
| getUserIDByActivityEvent | Returns user ID by its activity event. |
| Member Name | Member Purpose |
|---|---|
| getCheckerForUser | Get the entry point in the appropriate plugin for specified user behavior model. |
| testSeries | Returns hashmap with event timestamps as keys and their authenticity estimation as boolean values. ML model source is defined by user identified by modelUserID, test data is defined by activity of the user identified by userID. If users identified by modelUserID and userID have incompatible ML model types, an exception is raised. |
| refineModel | Refine model for user identified by modelUserID with data associated with activity of the user identified by userID. If users identified by modelUserID and userID have incompatible ML model types, an exception is raised. |
| Method Name | Method Purpose |
|---|---|
| trainModel | Train ML model for a user specified with userID with specified data interval for training. The model is saved elsewhere to be used by testSeries and refineModel methods. |
| testSeries | Returns hashmap with event timestamps as keys and their estimation as boolean values. «True» stands for authentic, «False» stands for illegal. ML model used is associated with the user identified by modelUserID, data series are defined by activity of user identified by userID. Users identified by modelUserID and userID must be associated with the same ML model type. |
| refineModel | Refine model for user identified by modelUserID with data associated with activity of the user identified by userID. Users identified by modelUserID and userID must be associated with the same ML model type. |
| Method Name | Method Purpose |
|---|---|
| trainModel | Query events from journal for specified time interval and user identifier. |
| testSeries | Record event data to journal with specified timestamp and user identifier. |

References
- Magomedov, S.G. Security analysis of computer networks and applications of the healthcare organizations information processes. Cloud Sci. 2020, 7, 685–704. [Google Scholar]
- Hewett, A.J.; Grevemeyer, H.; Barth, A.; Eichelberg, M.; Jensch, P.F. Conformance testing of DICOM image objects. In Medical Imaging 1997: PACS Design and Evaluation: Engineering and Clinical Issues; International Society for Optics and Photonics: Bellingham, WA, USA, 1997; Volume 3035, pp. 480–487. [Google Scholar]
- Open-Source Clinical Image and Object Management. Available online: https://www.dcm4che.org/ (accessed on 13 January 2021).
- Coatrieux, G.; Montagner, J.; Huang, H.; Roux, C. Mixed reversible and RONI watermarking for medical image reliability protection. In Proceedings of the 2007 29th Annual International Conference of the IEEE Engineering in Medicine and Biology Society IEEE, Lyon, France, 22–26 August 2007; pp. 5653–5656. [Google Scholar]
- Abd-Eldayem, M.M. A proposed security technique based on watermarking and encryption for digital imaging and communications in medicine. Egypt. Inform. J. 2013, 14, 1–13. [Google Scholar] [CrossRef]
- Al-Haj, A. Providing integrity, authenticity, and confidentiality for header and pixel data of DICOM images. J. Digit. Imaging 2015, 28, 179–187. [Google Scholar] [CrossRef]
- Singla, S.; Singh, J. Cloud data security using authentication and encryption technique. Global J. Comput. Sci. Technol. 2013, 13, 2232–2235. [Google Scholar]
- Dorgham, O.; Al-Rahamneh, B.; Almomani, A.; Khatatneh, K.F. Enhancing the security of exchanging and storing DICOM medical images on the cloud. Int. J. Cloud Appl. Comput. 2018, 8, 154–172. [Google Scholar] [CrossRef]
- Mirsky, Y.; Mahler, T.; Shelef, I.; Elovici, Y. CT-GAN: Malicious tampering of 3D medical imagery using deep learning. In Proceedings of the 28th {USENIX} Security Symposium ({USENIX} Security 19), Santa Clara, CA, USA, 14–16 August 2019; pp. 461–478. [Google Scholar]
- Cao, F.; Huang, H.K.; Zhou, X.Q. Medical image security in a HIPAA mandated PACS environment. Comput. Med. Imaging Graph. 2003, 27, 185–196. [Google Scholar] [CrossRef]
- Digital Imaging and Communications in Medicine (DICOM). Available online: https://www.dicomstandard.org/ (accessed on 22 January 2020).
- Cozzolino, D.; Thies, J.; Rössler, A.; Riess, C.; Nießner, M.; Verdoliva, L. Forensictransfer: Weakly-supervised domain adaptation for forgery detection. arXiv Preprint 2018, arXiv:1812.02510. [Google Scholar]
- Csaba, K.; Péter, H.B. Analysis of Cyberattack Patterns by User Behavior Analytics. AARMS–Acad. Appl. Res. Mil. Sci. 2018, 17, 101–114. [Google Scholar]
- Veeramachaneni, K.; Arnaldo, I.; Korrapati, V.; Bassias, C.; Li, K. AI^ 2: Training a big data machine to defend. In Proceedings of the 2016 IEEE 2nd International Conference on Big Data Security on Cloud (BigDataSecurity), IEEE International Conference on High Performance and Smart Computing (HPSC), and IEEE International Conference on Intelligent Data and Security (IDS), New York, NY, USA, 9–10 April 2016; pp. 49–54. [Google Scholar]
- Magomedov, S.; Ilin, D.; Silaeva, A.; Nikulchev, E. Dataset of User Reactions When Filling Out Web Questionnaires. Data 2020, 5, 108. [Google Scholar] [CrossRef]
- Nikulchev, E.; Ilin, D.; Silaeva, A.; Kolyasnikov, P.; Belov, V.; Runtov, A.; Pushkin, P.; Laptev, N.; Alexeenko, A.; Magomedov, S. Digital Psychological Platform for Mass Web-Surveys. Data 2020, 5, 95. [Google Scholar] [CrossRef]
- Magomedov, S.G.; Kolyasnikov, P.V.; Nikulchev, E.V. Development of technology for controlling access to digital portals and platforms based on estimates of user reaction time built into the interface. Russ. Technol. J. 2020, 8, 34–46. (In Russian) [Google Scholar] [CrossRef]
- Lee, J.; Kim, J.; Kim, I.; Han, K. Cyber Threat Detection Based on Artificial Neural Networks Using Event Profiles. IEEE Access 2019, 7, 165607–165626. [Google Scholar] [CrossRef]
- Tavallaee, M.; Bagheri, E.; Lu, W.; Ghorbani, A.A. A detailed analysis of the KDD CUP 99 data set. In Proceedings of the 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications, Ottawa, ON, Canada, 8–10 July 2009; pp. 1–6. [Google Scholar]
- Sharafaldin, I.; Lashkari, A.H.; Ghorbani, A.A. Toward generating a new intrusion detection dataset and intrusion traffic characterization. ICISSP 2018, 1, 108–116. [Google Scholar]
- Corapi, D.; Ray, O.; Russo, A.; Bandara, A.; Lupu, E. Learning rules from user behaviour. In IFIP International Conference on Artificial Intelligence Applications and Innovations; Springer: Boston, MA, USA, 2009; pp. 459–468. [Google Scholar]
- Dehlinger, J.; Dixon, J. Mobile application software engineering: Challenges and research directions. Workshop Mob. Softw. Eng. 2011, 2, 29–32. [Google Scholar]
- Kassinen, O.; Harjula, E.; Koskela, T.; Ylianttila, M. Guidelines for the implementation of cross-platform mobile middleware. Int. J. Softw. Eng. Appl. 2010, 4, 43–58. [Google Scholar]
- Petrov, A.V.; Bolshakov, O.S.; Lebedev, A.S.; Golubeva, N.E. Application template method to increase mobility of distributed systems for collecting and relaying information from biomedical sensors. J. Radio Electron. 2013, 5, 7. Available online: http://jre.cplire.ru/iso/may13/5/text.pdf (accessed on 22 January 2020). (In Russian).
- Lebedev, A.S.; Bolshakov, O.S.; Petrov, A.V. Designing distributed retransmission system with the mobile clients based on cross-platform software development methods. Curr. Probl. Sci. Educ. 2014, 1, 227. Available online: https://science-engineering.ru/pdf/2014/1/352.pdf (accessed on 22 January 2020). (In Russian).
- Karpov, O.E.; Akatkin, Y.M.; Konyavsky, V.A.; Shishkanov, D.V.; Yasinovskaya, E.D. Digital health in a digital society. Ecosyst. Clust. 2017, 220, 48. [Google Scholar]
- Komisaruk, O.V.; Nikulchev, E.V.; Malykh, S.B. Neural network model for artifacts marking in EEG signals. Cloud Sci. 2020, 7, 631–654. Available online: https://www.researchgate.net/publication/341882969_Razrabotka_nejrosetevoj_modeli_vyavlenia_artefaktov_v_elektroencefalogramme_mozga (accessed on 22 January 2020). (In Russian).
- Benssalah, M.; Rhaskali, Y. A Secure DICOM Image Encryption Scheme Based on ECC, Linear Cryptography and Chaos. In Proceedings of the 2020 1st International Conference on Communications, Control Systems and Signal Processing (CCSSP), El-Oued, Algeria, 16–17 March 2020; pp. 131–136. [Google Scholar]
- Mortajez, S.; Tahmasbi, M.; Zarei, J.; Jamshidnezhad, A. A novel chaotic encryption scheme based on efficient secret keys and confusion technique for confidential of DICOM images. Inform. Med. Unlocked 2020, 20, 100396. [Google Scholar] [CrossRef]
- Shini, S.G.; Thomas, T.; Chithraranjan, K. Cloud based medical image exchange-security challenges. Procedia Eng. 2012, 38, 3454–3461. [Google Scholar] [CrossRef]
- TCPDUMP/LIBPCAP Public Repository. Available online: https://www.tcpdump.org/ (accessed on 22 January 2020).
- Mitmproxy—An Interactive HTTPS Proxy. Available online: https://mitmproxy.org/ (accessed on 22 January 2020).
- IBM QRadar SIEM – Overview. Available online: https://www.ibm.com/products/qradar-siem (accessed on 22 January 2020).
- IBM Technology Partners. Available online: https://www.ibm.com/support/pages/technology-partners (accessed on 22 January 2020).
- IBM QRadar User Behavior Analytics (UBA) app: User Guide. Available online: https://www.ibm.com/support/knowledgecenter/SS42VS_SHR/com.ibm.UBAapp.doc/b_Qapps_UBA.pdf (accessed on 22 January 2020).
- IBM QRadar: Architecture and Deployment Guide. Available online: https://www.ibm.com/support/knowledgecenter/en/SS42VS_7.3.3/com.ibm.qradar.doc/b_siem_deployment.pdf (accessed on 22 January 2020).
- Gartner Magic Quadrant for Security Information and Event Management. Available online: https://www.gartner.com/en/documents/3981040/magic-quadrant-for-security-information-and-event-manage (accessed on 22 January 2020).
- About USM Appliance. Available online: https://cybersecurity.att.com/documentation/usm-appliance/system-overview/about-usm-solution.htm (accessed on 22 January 2020).
- USM Appliance. Develop New Plugins from Scratch. Available online: https://cybersecurity.att.com/documentation/usm-appliance/plugin-management/developing-new-plugins.htm (accessed on 22 January 2020).
- Configuring High Availability in USM Appliance Enterprise Systems. Available online: https://cybersecurity.att.com/documentation/usm-appliance/configuring-ha/deploying-ha-in-usm-enterprise-prods.htm (accessed on 22 January 2020).
- Apache Hadoop. Available online: https://hadoop.apache.org/ (accessed on 22 January 2020).
- MLlib. Apache Spark. Available online: https://spark.apache.org/mllib/ (accessed on 22 January 2020).
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Magomedov, S.; Lebedev, A. Protected Network Architecture for Ensuring Consistency of Medical Data through Validation of User Behavior and DICOM Archive Integrity. Appl. Sci. 2021, 11, 2072. https://doi.org/10.3390/app11052072
Magomedov S, Lebedev A. Protected Network Architecture for Ensuring Consistency of Medical Data through Validation of User Behavior and DICOM Archive Integrity. Applied Sciences. 2021; 11(5):2072. https://doi.org/10.3390/app11052072
Chicago/Turabian StyleMagomedov, Shamil, and Artem Lebedev. 2021. "Protected Network Architecture for Ensuring Consistency of Medical Data through Validation of User Behavior and DICOM Archive Integrity" Applied Sciences 11, no. 5: 2072. https://doi.org/10.3390/app11052072
APA StyleMagomedov, S., & Lebedev, A. (2021). Protected Network Architecture for Ensuring Consistency of Medical Data through Validation of User Behavior and DICOM Archive Integrity. Applied Sciences, 11(5), 2072. https://doi.org/10.3390/app11052072







