Abstract
Pervasive service composition is useful in many scenarios, for instance, in urban planning or controlled harvest. Currently, there is no standard to develop solutions using pervasive service composition. However, big companies propose their frameworks to develop complex services, but their frameworks are appropriate in specific applications, such as home automation and agriculture. On the other hand, there are different very well-grounded academic proposals for pervasive service composition. However, these do not solve the problems of traditional approaches that are appropriate to specific areas of application, and adaptation is needed to deal with the dynamism of the environment. This article presents a cognitive approach for pervasive service composition where InfoCom devices and the implementation of cognitive functions interact to create pervasive composite services. Our central hypothesis is that cognitive theory can help solve actual problems requiring pervasive service composition, as it addresses the above-mentioned problems. To test our approach, in this article we present a case of urban insecurity. Specifically, in different countries, street robbery using firearms is one of the problems with a high impact because of its frequency. This article proposes to compose a pervasive service for deterring criminals from committing their crimes. The results obtained by simulating our proposal in our case study are promising. However, more research needs to be achieved before applying the proposed approach to actual problems. The research needed ought to address various problems, some of which are discussed in this article.
1. Introduction
Currently, cities are becoming more complex environments to live in; for instance, we need to localize specific places, prevent some incidents, among many others. Fortunately, the technologies present in this kind of environment, including the ones humans wear, may help overcome some of our human problems. However, in order to use these technologies to help humans in dynamic environments, two problems must be solved. The first one is the autonomous pervasive service composition required by humans to deal with complex problems that a single service cannot solve. The second is how to deal with the volatility of available services in the environment. That is, how to ensure that the service is useful by the time it is created, and during the time it is required. In this article, we deal only with the first problem. Even though the second problem is quite essential, it is beyond the scope of this article. Thus, the objective of this article is to present a new way to create pervasive composite systems. The inspiration for our proposal is the way the human mind composes solutions using its cognitive functions.
To test our proposal, we used an urban security case study. Specifically, street robbery is of high interest because of its frequency. The pervasive service composition is a way to take advantage of the technologies already distributed throughout the environment to propose solutions to this growing problem.
There are different proposals to tackle the public insecurity problem using technology through artificial intelligence (AI) and pervasive applications [1,2,3]. These proposals come from different fields, such as smart spaces, Internet of Things (IoT) and ambient intelligence (AmI), among others. Such fields have in common that they are built upon concepts and technologies such as ubiquitous computing, context awareness, embedded systems and human-centric computer interaction design [4,5]. These kind of solutions are typically employed in home environments, but may also be employed for other kinds of purposes, such as healthcare [6], cognitive robotics [7], education [8] and public safety [1]. However, a common problem of the aforementioned proposals is the absence of a common framework for deploying the solutions.
The unified theories of cognition [9,10] provide some basis for the approach of general AI of cognitive architectures (CAs). The objective of this approach goes in the direction of proposing a theory working over the entire range of human cognition. That is, a CA is constituted by a group of cognitive components representing the human cognitive functions. Newell’s initial approach is based mainly on psychological evidence [11]. Currently, the components of some bioinspired CAs or BICAs, represent human cognitive functions grounded in different disciplines, for instance, psychology, neuroscience and philosophy, among others [12]. The appropriate work of these cognitive functions generates intelligent, human-like behavior [13]. The natural question is, why would we want to generate computer systems with human-like behavior? The answer is because we want computer systems that help us solve problems in an analogous way to how we solve our problems. That is, maybe not efficiently, but good enough to satisfy the current needs. Over the last 12 years, our research group has been developing a BICA named Cuâyôllôtl (which means brain in Nahuatl, a Mexican language). The objective of this BICA is to endow a cybernetic entity or system with human-like behavior. The resulting system ought to be able to engineer applications in which artificial and natural cognitive systems work together more effectively to solve a problem. In other words, we propose a CogInfoCom system with skills to engineer pervasive composed services using simple available services in the environment to solve actual complex human problems.
This proposal is the beginning of a study aiming to use the Cuâyôllôtl CA’s cognitive functions to create useful pervasive composite services to solve complex problems that humanity faces. The objective of this stage is to prove that it is possible to compose useful pervasive services using this approach. This objective is fulfilled by simulating the environmental conditions and the pervasive service composition in a simulated environment using Cuâyôllôtl’s cognitive functions. Subsequent stages go in the direction of obtaining more evidence to prove that the approach can be useful in actual scenarios. We assume that cognitive functions such as sensing, perception, memory, attention, emotions and motivation [14,15,16,17,18,19] can be abstracted as cognitive agents available in the city’s infrastructure, and that the city has enough useful infrastructure to create composite services. With these assumptions, the system starts by recognizing a specific need of a human and ends with the pervasive service composition able to solve that need. Our proposal’s originality is that it behaves similarly to the human way of detecting a need, and does not just create the needed composite service, but ensures its continuous appropriate behavior independently of the dynamism of the environment.
This article presents a study case of public security. That is, the Cuâyôllôtl BICA is used to simulate the creation of useful composite services to deal with the problem of public insecurity, more specifically, violent acts against a person that involve goods or property, also known as robbery or mugging [20]. The Cuâyôllôtl BICA’s work starts by detecting this crime using the resources available in the environment (different info-communication devices, including sensors such as cameras and microphones; and actuators such as drones and speakers) and ends by composing a service that helps to deter the aggressor from committing the crime.
This work is organized as follows: In Section 2, we review related concepts and analyze related works. In Section 3, we explain the methodologies we use during our research; after that we describe our proposal and present the case study and its formalization. In Section 4, we present the results obtained through a simulation of a case attached to reality. In Section 5 we discuss our thoughts, and the advantages and risks of our proposal. Finally, Section 6 presents our conclusions and work in progress.
2. Related Works
This section defines some necessary concepts for the proposal and analyzes related work.
2.1. Service Composition
In [21] a service is defined as an abstract entity that provides a consistent set of capabilities and has an interface to communicate with clients. We classify services as web services and pervasive services. Web services can be invoked independently of the place and do not consider user context. Pervasive services can provide services only to nearby clients, consider their context and use hardware devices to interact with the environment to satisfy users’ requirements. Unlike web services, pervasive services are focused on meeting user intentions, not just producing an output [21].
Frequently, users’ requirements are impossible to satisfy with a single service, mainly because of the requirements’ complexity. This situation generates the need to use multiple services working together to solve complex problems. The overall service delivers individual services that satisfy final user requirements [22]. Thus, service composition is the chaining of service interfaces syntactically or semantically. A service’s output is channeled as the next service(s)’s input while content filtering and format modification tasks are performed [23]. There are different service composition mechanisms; one of the most relevant for us is dynamic composition achieved using graph construction. This mechanism is important because it combines existing services to reach a complex solution [24], and because it is very close to the way the human brain constructs an action plan [25].
Service composition results are particularly useful in pervasive computing, also known as ubiquitous computing [26]. The main characteristic of pervasive computing is its dynamic complex environment, made up of many InfoCom devices supporting mobility and perceiving information regarding their environment [21]. Pervasive service composition is service composition performed using software services, using hardware and considering the context. Pervasive service composition is useful in open, dynamic environments where device and network availability cannot be ensured.
Pervasive service composition allows pervasive systems to exploit the capabilities of a variety of devices in the environment, allowing it to offer enriched functionality and serve as a basis for creating ambient intelligence or AmI. For this reason, service composition has become a topic of interest in fields such as IoT and AmI [22,27,28,29].
Before we can perform a service composition, we must be able to find the required services for the aforementioned composition: a process known as service discovery, and usually supported by protocols known as service discovery protocols (SDP). We use these protocols to detect devices and services in a network [21]. They are essential because the result of pervasive service composition depends on finding available and useful services in the user’s environment.
Given that we intend to develop a system that creates composite services without human intervention, we focus on automatic service composition [30], which is the name given to composition techniques with no human intervention. Automatic service composition approaches include AI planning, data integration, process synthesis and conversations [31]. The primary approach to achieving automatic service composition deals with it as a planning problem [32].
In an urban environment, all available devices and their network infrastructure constitute a pervasive system. It is possible to create a complex composite service with the capabilities of this infrastructure. The key is to plan and decide which of these services and devices are appropriate to create the required service.
2.2. Research Classification
To see what types of studies exist in fields closely related to pervasive service composition and how our proposal compares to them, we analyzed a group of studies that classify research related to pervasive systems and service composition. From this analysis, we outline the essential characteristics to classify the different approaches. We use these characteristics to compare our proposal with other approaches pointing out the main similarities and differences. Figure 1 shows visual representations of some of the classifications presented in this section.
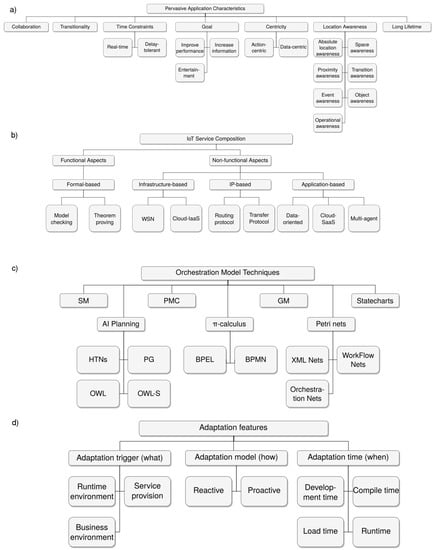
Figure 1.
Figures corresponding to the classifications of Dombroviak (a), Asghari (b), Petrova-Antonova (c) and Mutanu (d).
Dombroviak in [33], presents a pervasive application taxonomy, where the characteristics used to classify an application are: transitionality (usefulness over multiple environments), time constraints (real-time or delay-tolerant), goal (improve performance, increase information or entertainment), collaboration (degree of component cooperation in a single application instance), lifetime (how much time an instance ends up executing), centricity (data-centric or action-centric) and location awareness (an object’s knowledge of its location).
With this taxonomy in mind, a proposal classified as transitional, real-time, collaborative, long-lifetime, action-centric and location-aware would be the most desirable.
In [27], Asghari proposes a taxonomy for service composition on IoT platforms. The main classification considers functional and non-functional aspects of the composition, with functional ones being formal, such as model checking and theorem proving; and non-functional ones being infrastructure-based (such as wireless sensor networks or the cloud), IP-based (such as routing or transfer protocols) and application-based (such as data-oriented or multi-agent systems).
In the terms of this taxonomy, a non-functional solution would be preferable. Within the non-functional aspects, the multi-agent application-based approach closely matches service composition strategies.
Mutanu in [34] classifies service-oriented systems on the basis of their adaptation and validation features, the former including adaptation triggers (further divided into runtime environment, service provision and business environment triggers), the adaptation model (divided into strategy and implementation) and the application context; and the latter being technique or mechanism, involvement, the primary focus, the control mechanism and the strategy.
A proposal classified under runtime environment and service provision adaptation triggers, reactive embedded adaptation model and general application context would be preferable.
Petrova-Antonova in [35] offers a classification of web service composition approaches based on seven characteristics: component model, orchestration model, data and data access model, service selection model (static or dynamic), transactions, exception model and tool support. In turn, the work classifies orchestration models into different paradigms, such as AI planning, graph models, Petri nets, statecharts, -calculus, signature matching and planning as model checking.
Based on this classification, a dynamic service selection model and a AI planning orchestration model might be the most appropriate for our proposal.
Abdualrazak in [36] proposed a classification scheme for evaluating the performance of pervasive systems based on seven criteria: architecture, which is subdivided into infrastructure (centralized, mobile, ad hoc, personal range, local range, etc.) and design (application-based, service-oriented, component-oriented, etc.); application purpose (assistance, experience enhancement, etc.); autonomy (static, self-learning, re-programmable and re-configurable); integration (ad hoc, universal interface and plug-in); interaction (human-to-machine and machine-to-machine); intelligence (context-aware and not context-aware); and service availability (pervasive and non-pervasive).
Based on this taxonomy, an ad hoc, local range span, service-oriented, assistive, self-learning, human to machine, context-aware and pervasive proposal with ad hoc integration is the most adequate for us.
As we can see from these classifications, many focus either on service composition in general or web service composition in particular, or on pervasive applications. Even if these studies give us good insight into the requirements a pervasive service composition system must fulfill, there seems to be no single study that seeks to classify pervasive service composition approaches.
2.3. Related Service Composition Works
Service composition systems have been developed for well over a decade now. However, only in more recent times has the service composition community begun to tackle the challenges introduced by open, dynamic environments, such as those of pervasive systems. In this section, we present some studies focused on pervasive service composition in open, dynamic environments.
Cabrera et al. [37] proposed an IoT architecture for service composition, divided into five components: the request handler; the service registration engine; the service discovery engine; the service composition and execution engine; and the service providers. The architecture performs a semantic service classification by domain. However, it is unknown whether services obtain a semantic meaning beyond this classification. This proposal also lacks any learning capability. Additionally, the architecture seems to require all IoT gateways to have all architecture components loaded, which may not be feasible in some cases. Furthermore, the services used in this work are exclusively web services, so this proposal does not take into account pervasive service composition aspects such as locality and context-awareness.
The work of Baklouti, Le Sommer and Maheo [23] proposes a service composition system based on the opportunistic network approach to deal with pervasive network communication, and uses both orchestration and choreography strategies and a utility-based function to compare solutions. The main processes are the service discovery, guided by the hop-measured utility function, and the composition proper, done either by orchestration or by choreography. Whether the chaining is syntactical or semantic is not specified. This system lacks any capacity to learn from performed compositions, and has to start from scratch for similar scenarios. The system does not seem to have the capacity to adapt the yielded composite service, and tries to limit the impact of the open dynamic nature of pervasive systems by establishing a maximum distance () for participants to be considered in a composition process.
GoCoMo [38] is a service composition and adaptation model which uses an AI planning algorithm based on the backward-chaining technique. In order to exploit the goal-oriented approach used in this work, the authors focus on three main issues: goal-driven service discovery, handled by the establishment of a temporary overlay network; opportunistic service execution, handled via online adaptable reasoning; and heuristic discovery checking, handled via a hop-based heuristic discovery mechanism. In this model, service matchmaking is done syntactically; the authors justify this choice by arguing that maintaining a semantic dynamic overlay network for resource-constrained devices can be very expensive. GoCoMo does not seem to have a learning mechanism, so future composition tasks do not exploit the composition’s experienced solutions.
Cervantes et al. [39] proposed an adaptive pervasive service composition protocol based on the pervasive system of systems (PSoS) paradigm. It employs a distributed constraint satisfaction problem (disCSP) approach to ensure that user’s requirements are satisfied, and extends it to deal with the dynamism of pervasive environments. The composition process comprises three phases: identification of potential participants through a modified Contract Net Protocol, service composition through the PSCP algorithm for solving the disCSP and service adaptation based on a heuristic named DPS that seeks to dynamically add new participants into the system. This proposal lacks any learning mechanism, so experience from yielded solutions cannot be taken into account for similar future composition scenarios. Additionally, adaptation focuses on functional requirements, leaving aside QoS requirements that could affect user experience.
COPERNIC [40] is service composition and adaptation middleware for pervasive systems. Its approach uses the modeling of a cognitive agent for performing service compositions. The pipeline of this agent consists of nine steps: sensing external and internal inputs, forwarding symbolic structures (percepts) to the memory, looking up related information, storing queued information, relevant information filtering, goal decomposition and service competition, service binding, service execution and output return. The middleware uses heuristics to adapt its behavior among goal-oriented vs. situation-oriented; proactive vs. reactive; maintaining ongoing plan vs. adapting it; and sensitivity to goal conflict. A problem with this cognitive pipeline is that, unlike what happens in human cognition, the COPERNIC agent indiscriminately senses its environment without attentional filtering, which can saturate the memory quickly.
As we can see from the proposals presented above, few of them can learn from successful service compositions to use the solutions in the event that a similar scenario arises in the future, which is something human beings know how to do very well. This feature could be handy to avoid creating composite services from scratch if an existing solution can be reused or even used as a template to be adapted, which would reduce composition times for those cases. Additionally, a notable quantity of proposals do not exploit semantic analysis of the involved services, which is a disadvantage. That prevents a service composition system from producing a composite service closer to the user’s expectations. The ability to learn from past experiences and to give things meaning via semantic analysis is very typical of human beings, so developing a service composition system that imitates the human cognition process could help tackle these challenges.
2.4. Crime
The term crime does not have a simple and universally accepted definition in modern criminal law. However, we adopted the following: crime is an act harmful not only for a victim but also for a community, society or state. Such acts are prohibited and punished by law [41]. According to some authors [20,42,43,44] there are two kinds of violence: affective violence and predatory violence. Affective violence refers to violence exercised because of fear or stress at an emotional level, and is mainly defensive, whereas predatory violence, is intentional, premeditated and looks for an advantage over the prey, as in the behavior of great carnivores. In this work, our efforts aim to propose the use of pervasive service composition to inhibit a specific type of predatory violence, specifically the crime of mugging. Our motivation is that the predatory behavior is standard among many crime modes. We can think of a pattern that generalizes these modes without defining them in a particular way, opening up the possibility to extending the range for dealing with different types of crimes with our proposal.
Figure 2 shows part of the crime classification presented in [45]. Due to its similarities, the crime of mugging may be considered as predatory violence.
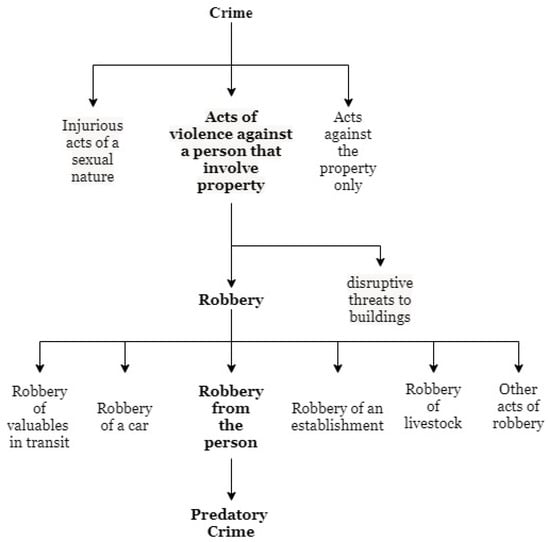
Figure 2.
Limited Taxonomy of Crimes.
One possibility for predatory crime detection and deterrence is creating a pervasive service for this purpose located in the urban environment. Next, we present our cognitive pervasive service composition applied to crime detection and deterrence inspired by human mental processes.
There are some studies focused on the use of IT for public safety, such as the work of Byun, Nasridinov and Park [1], which proposes a crime detection IoT system consisting of five modules: emotion sensing, emotion recording, crime detection, crime visualization and crime prediction. This proposal focuses on helping to notify alleged and potential crimes. However, it cannot deter an alleged criminal from committing the crime, as it relies entirely on the security forces. The use of CCTV cameras only identifies emotional states, thereby missing the chance to analyze other factors, such as the alleged criminal’s movement pattern or whether he is carrying a weapon, which could improve crime detection accuracy. Furthermore, the system relies exclusively on wearables and CCTV cameras; this means it cannot benefit from many other devices available in an urban environment.
3. Materials and Methods
3.1. Methodology
For the development of this work, we used a combination of methodologies. The first is the methodology for the construction of cognitive architectures [12] where we focus on the main flow. The first step is making a general definition of the system we want; this includes the context it is implemented, the applicability and the abilities desired for the system. The second step is the definition of functionalities within the scope of the problem, and the objectives and constraints. This leads to a preliminary study of the state of the art and a conceptualization.
At this point we blend the first methodology with the second one using the analysis and design of Gaia multi-agent systems [46], which helps us define and model our cognitive functions as agents with the research of sub-functionalities, subdivide the system into sub-organizations and define their requirements and their types of interaction with each other. At this point with Gaia we can define and model the role, interactions and environment for the agents of our system, which will guide us for the future implementation.
3.2. Pervasive Service Composition Proposal
Service composition may appear to be a novel topic in the field of pervasive systems, but in fact, it is a tool we as human beings employ on a daily basis. Humans constantly need to create services to interact with our environment and with other humans. Different cognitive functions constitute the human mind from the neuroscientific point of view. The fact that composition is a common task for the human mind is our primary motivation to propose a novel bioinspired approach to pervasive service composition. In this section, we present our proposal, objectives and hypotheses.
Objective and General Hypotheses
The objective of this proposal is to present a cognitive way to create pervasive composite services, in our case to inhibit predatory crime committed with a firearm; for this we need to merge the cognitive capabilities of artificial devices and humans towards engineering a specific application solving an actual problem [47,48]. In this first stage, we want to prove that our proposal is useful for creating pervasive composite services using a cognitive approach. The next stages will deal with quantitative measures to ensure that the proposal helps fulfill time and quality criteria to deal with actual problems.
Our general hypotheses for our proposal are:
- With our approach it is possible to build solutions to complex problems, such as the detection of a crime, in a way similar to how the human mind would produce them.
- We can make use of human cognitive functions abstracted as cognitive agents.
- The proposed cognitive agents are capable of dealing with information provided by other (agents) services in order to generate human-like behavior.
- The environment provides these cognitive agents, and they are omnipresent in the environment.
- Info-communication devices such as microphones, alarms, cameras and drones represent sensory and actuator services.
- The crime type we are dealing with for simplicity is predatory and involves a firearm, which is most likely to take place on the streets in the United States [49].
3.3. Proposal
As established previously, our proposal’s goal is the composition of pervasive services in a human-like way. For creating a pervasive composite service, the system performs the following steps: First, it determines the context through the cognitive functions of perception [14], memory [17,18] and attention [15]. Concurrently, the motivation agent sends pieces of information regarding the needs to be satisfied (pervasive services required) to the decision-making agent, who takes these inputs to determine by some evaluation the service or services to create. Then, the planning service checks whether it already knows something in its memory about the service required; if this is the case, it retrieves the information to create the composite service and executes the composition; otherwise, it tries to create the pervasive composite service from scratch. By the end of the composition, if the system knows the service, it updates the related information; otherwise, it stores useful information, such as context, services contacted for pervasive service composition and quality of the service obtained, for possible future use. In other words, our proposal creates a pervasive composite service based not just on the requirements of the service, but also on the context and its own experience in solving the current problem.
Figure 3 depicts the cognitive functions that make up Cuâyôllôtl, our cognitive architecture and their interactions to endow a cybernetic entity (system, avatar or robot) with human-like behavior.
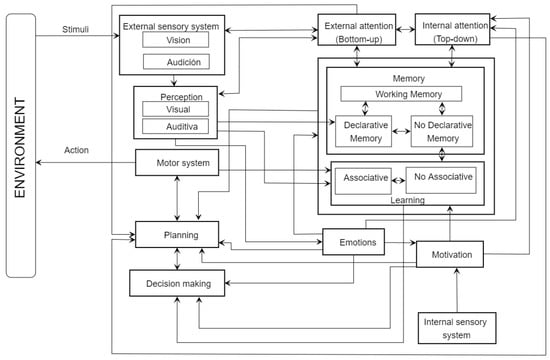
Figure 3.
Cognitive functions constituting the Cuâyôllôtl cognitive architecture and their interrelations according to neuroscientific evidence. Each function in this proposal is abstracted as an agent.
The cognitive functions and their interactions depicted in Figure 3 are available in the composition process. However, not all of them are useful in all cases. Their use depends on the context and task to be executed. Their use must be similar to that of humans who create a service based on the context’s and tasks’ characteristics. For instance, we inhibit the use of emotions in some motor tasks, and we do not use the visual function in listening tasks.
Next we briefly describe the behavior of each cognitive agent making up our proposal:
- Decision-making agent: This agent continually evaluates its inputs to determine the task to execute and communicates its decision to the planning agent. It also communicates any change regarding the execution of the current task; i.e., it can decide to change the entire workflow [50] of the task being executed. In a traditional composition, this agent plays a role similar to that of the orchestrator [51].
- Planning agent: The objective of this agent is to propose a plan to achieve a task. It takes as input the information coming from the decision-making agent, who determines the task to execute and inputs different agents, such as emotions and motivation, influencing how to achieve a plan. Before proposing a plan, it interacts with the memory agent to find out whether it has a plan to fulfill the objective. If the memory has the information, the planning agent retrieves all the information needed to achieve the plan; otherwise, it creates one from scratch.
- Motivation agent: In terms of neurosciences, motivation is a cognitive function that influences an objective’s determination in a human being. In our case, it bases its influences on the objective or objectives to be achieved. It sends its output to the decision-making agent, who will decide which task to undertake [52].
- Memory agent: In the human being, memory is responsible for the coding, storing, retrieving and forgetting of knowledge [53]. In our case, the, emory agent contains knowledge about available services, experienced plans and data such as object images and scenes. In this proposal, this agent helps to remember situations of interest, and associate situations with plans.
- Perception agent: In the human being, this cognitive function gives semantic meaning to information coming from different senses [54]. In our case, this agent processes information sensed by InfoCom devices to generate its semantic meaning and helps determine the context. The difference in perception between a human and our proposal is that human perception is limited to our known senses; in contrast, our proposal’s perception is limited only by the different InfoCom sensors available in the environment and the perception agent’s ability to give that information meaning.
- Attention agent: In humans, this function’s goal is to use resources available in the system [55] efficiently. In our system, this agent builds an attentional template from the attentional task established. Using this template, it recovers information from memory to assist the perception, memory, planning and decision-making agents in meeting their goals efficiently.
- Sensing agent: The sensory cognitive function’s goal is to extract the features of an object detected by the different sensors available to the human being [14]. In our proposal, the sensors are InfoCom devices, such as cameras that capture visual information, microphones and infrared sensors, among others. They send the captured information to the perception agent, which provides semantic meaning to the perceived information. This information helps to define the context.
- Motor agent: In human beings, the motor system helps them to interact with the environment to get information or modify the environment [56]. In our proposal, its objective is similar. InfoCom devices such as drones, speakers or robots constitute the motor system. These devices modify or help the overall system to interact with the physical environment. They help to execute the plans generated by the planning agent.
In our case, a framework developed by our research team offers the communication protocols used in our proposal [57,58]. This framework facilitates the distributed development of biologically inspired cognitive architectures or BICAs, abstracting the components and processes. It also performs encoding and decoding of the spikes (the structure of a message, inspired by the unit of communication in the brain) transferred among the components. Specifically, it solves the problems of integrating the implemented models of the different bio-inspired cognitive functions in a distributed way; i.e., the agents may be distributed in the environment. Based on biological evidence, the framework ensures the specific order of communications, the integration of transmitted information, coordination and synchronization among the different agents creating the pervasive service composition. The framework´s services include the validation of connections among the different agents making up the pervasive composite service, the correct behavior of the composed model (mechanisms of coordination and synchronization) and the provision of support for information processing. This means the framework will choose where the incoming information will be processed.
3.4. Case Study
To test our proposal, we decided to employ it to contribute to a public safety issue—specifically, to deter predatory crimes when the predator decides to commit the crime and is within the victim’s neighborhood.
The goal is the composition of a pervasive service applied to the detection and deterrence of robbery, because robbery is an act of violence involving firearms where the intention is to appropriate another’s personal goods. The use of firearms is vital in our case study to detect potential criminal situations. When a potential crime situation is detected, the system tries to inhibit it by creating a composite service, specifically, using a drone to make the criminal know that his act has been detected, and firing if possible an alarm to alert people that this criminal act is being committed, and some lights to locate the place of the possible crime. We expect that a composed service will prevent the criminal from performing the mugging. Some successful cases using these inhibitors were reported in public security systems using different approaches [59].
The way our study case behaves is as follows. Through different agents (sensors, cameras, etc.), the system senses the environment. When it identifies a potential threat, it starts the creation of a pervasive composite service to deter the crime using the capabilities of the different cognitive agents available in the environment. We describe the behavior of these agents specifically aimed at fulfilling this objective.
3.4.1. Description of the Agents
- Sensor agent: The goal of this agent is to obtain information from the environment to be analyzed. The sensors are distributed in the environment and are the cameras, heart sensors, accelerometers, gyroscopes and other useful sensors in our proposal. This agent sends the information obtained to the perception agent.
- Motivation agent: The motivation agent sends information to the decision-making agent, who determines the objective the system must satisfy. In our case of urban safety, the motivation is identifying a predatory crime using a firearm. In a general way, this agent will provide specific information about each kind of public safety to the decision-making agent.
- Decision-making agent: This agent must decide on one objective to fulfill from all the objectives received from the motivation agent. The decision-making agent uses a priority list to make a decision. Once it finishes its process, it communicates its decision to the planning agent. In a traditional composition, this agent plays the role of the orchestrator [51]. Besides this primary task, it also monitors the system state to modify the entire workflow when required, for instance, to detect when a particular task is no longer needed and then proceed to cancel it [50].
- Planning agent: This agent proposes a plan to fulfill the objective decided by the decision-making agent. To propose a plan, it first consults the memory agent to see whether it already knows a plan to reach the objective in the specific context; otherwise it must create one from scratch.
- Perception agent: This agent processes information sensed by InfoCom devices to generate its semantic meaning [54]. In our case, it assigns the meaning of crime to a scene involving a human with a weapon approaching another human in a specific context.
- Attention agent: The goal of this agent is to make efficient use of resources available in the system [55]. It builds an attentional template from the attentional task established by the decision-making agents. Using this template helps the perception, memory and decision-making agent agents to meet their goals efficiently. For instance, it filters the information coming from the sensor agent to the perception agent.
- Motor system agent: In the human being, the motor system interacts with the environment to get information or modify the environment [56]. In our case, the actuators, devices such as autonomous vehicles (drones, airplanes or robots) and speakers constitute the motor system. These actuators and devices are useful for executing a plan and modifying the system’s physical environment in accordance with the plans generated by the planning agent.
3.4.2. Workflow
Figure 4 illustrates the proposed flow of information and processing among the different agents previously described. The flow illustrates both cases: building a new plan and following up on a composed plan retrieved from memory.
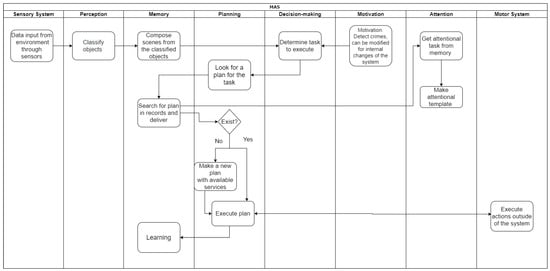
Figure 4.
Diagram of flow between functions.
The goal is to detect and inhibit predatory crimes. We consider a situation to be a potential crime of the type we want to deter when there are two persons in proximity (1–2 m) on a street, and one of them is carrying a firearm in his hand. In our case, the solution to this problem starts concurrently in the sensor, motivation and perception agents. The motivation agent establishes the need to detect this type of crime; the sensor agent (constituted by cameras and other sensors such as microphones) provides information from the environment to the perception agent. This agent and the memory agent identify the context, firearms and persons as a potential crime situation. When a potential crime situation arises, the decision-making agent is informed. This agent sends information to the planning agent, who concurrently asks the service directory for available agents offering their services and the memory agent for a list of plans applied successfully in a similar risk situation. Two different situations may arise: that the memory knows at least one plan to apply, or that it does not know a plan. In the first case, it sends the available option to the decision-making agent who, using the information retrieved from available agents (actuators) and an evaluation function, decides which plan to execute; in the second case, the planning agent must create a plan from scratch. We have already done some initial work on this case and have some early results. However, they are beyond the scope of this article and will be published later. Briefly, a new plan is created by constructing a graph made up of the different available services, similar to generating a map from beginning to end. There are many techniques, such as forward-chaining and backward-chaining [25] that we are using. In both cases, during the execution of a successful plan, the planning agent generates an execution report (including services used, time of composition, etc.). This information goes to the memory as metadata and is available for future use. In the case the applied plan is a new one, the agent also relays the need to store the plan as an option for similar cases in the future.
The motor agent executes the plan in our case study. A drone and other CogInfo devices represent the motor system. In our case study, once the risk situation is detected, the plan’s execution makes the drone approach the area of the potential crime, inhibiting the predator from committing the crime.
3.4.3. Assumptions and Limitations
Below we list some assumptions and limitations which we have considered for the implementation:
- Since it is not the goal of this work to describe the cognitive functions of the Cuâyôllôtl cognitive architecture, in this article they are represented as black boxes (the reader can consult [14,15,16,17,18,19]).
- In this case study, our environment is sensed only with cameras. Only cameras mean that we only consider the visual sensing system. In the ongoing work, we are considering hearing agents and other types of CogInfo sensors.
- The environment always contains the necessary services to deter the crime. However, in this case, we consider only drones. The ongoing work considers speakers, lights and some other CogInfo devices.
- At this moment, for the sake of simplicity, we only consider one type of crime. We are extending this work to different crime types.
- Taking the simulation tool’s (Gama) limitations into account, we can only simulate the system behavior and interactions between simulated cognitive agents, passersby and the aggressor.
4. Implementation and Results
This section describes the case study’s implementation used to test our proposal, conditions of execution and some results according to our initial objectives. With this case study, we tested our proposed method of coordination and message passing among the agents using Gama version 1.8.1 as the framework for agents [60].
Gama allowed us to simulate our cognitive agents as species with different characteristics and behaviors which control the simulation’s steps and coordination, passing the message in FIPA’s ACL format [61]. Gama allows us to simulate the interaction with the messages. The first message sent is the Contract Net; this binds the different agents to the decision-making and the planning agents. With this binding, they can use the agents’ functionalities to create the composite service. The Contract Net in Gama works as follows: The decision-making agent starts the conversation with a list of preloaded participants (the cognitive agents) with the protocol fipa-contract-net and the content is “Join my system”; then all agents respond with “agree”. After starting the simulation, the planning agent sends a request to the relevant agents to notify them that they will start the service. The sensor agent senses the environment and sends the information obtained to the perception agent, which, with the memory agent’s help, performs the scene recognition process. When the perception agent perceives the scene as risky, the perception agent notifies the decision-making agent that a crime might occur. The way all agents work inside Gama is with reflex; they react to certain changes within the environment and the messages that other agents send them, so every response in the simulation is controlled by the agents.
In our implementation, black boxes represent the cognitive agents playing the roles of the different cognitive functions. The motivation agent has pre-loaded mugging detection as motivation. The memory agent has previous training to match risk situations, specifically mugging with firearms; i.e., it contains information regarding the possible plans to apply when a mugging crime is detected.
Figure 5 shows the environment implemented. This environment shows the streets and circles, squares and arrows representing the different types of agents. Blue circles represent the passersby; green arrows represent the drones; red squares represent the criminals. For this simulation, we decided not to represent the other agents visually. However, these agents interact with the environment and are considered omnipresent for the sake of this simulation.
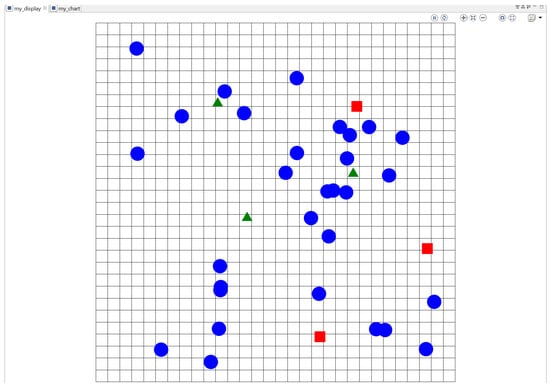
Figure 5.
Environment in Gama.
The motor agent controls the drone that appears once the perception agent identifies a crime situation. The behavior of the passersby and criminals is to wander randomly through the streets. However, the criminals have additional behavior: to perform a direct contact crime using a firearm, starting randomly. For the system, the criminal and the victim are indistinguishable until the aggressor tries to commit the crime by showing the firearm.
The simulation starts with the reflex “wandering” for all passersby. When one finds itself close to the aggressor (1–2 m), the criminal reveals his identity by exposing his firearm with the reflex “attack." At this moment, the system starts its work, identifying this perilous situation represented in the simulation’s snapshot as yellow tiles that surround the aggressor (see Figure 6); this action reflects perception’s reflex “detect." At this moment, the system starts its behavior to deter the aggressor, so we can see how the system deploys a composed service as a drone, represented as a green arrow. The control and deployment of the drone are the responsibility of the motor system agent and the reflex involved is “deter." This service (the drone) reaches the crime scene to deter the crime: if the drone arrives within a predefined time threshold, it “scares away” the aggressor just by its presence.
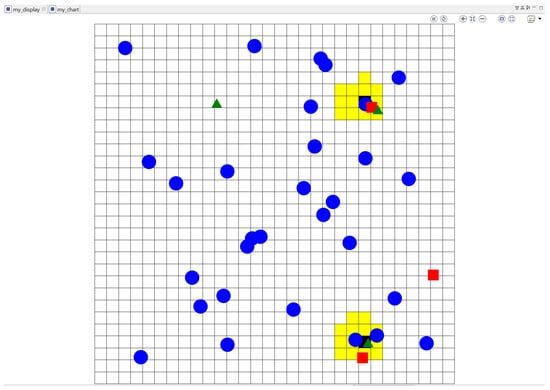
Figure 6.
Detection of a dangerous situation.
With this we successfully got our system to work and detect the situations as intended; more importantly, we can see that our system communicates and coordinates within itself and gets the work done. In Figure 7 we can see the number of messages sent by our system: at first it sent a high number of messages because of the initialization, the Contract Net and the agree messages and the start of the reflex for the agents to detect situations; after that, only when it detected a risky situation and it had to create a service did we get a rise of messages, as seen in the circles on the graph. With this simulation we confirm that our system will behave as we intended and have an impact on our lives. We can see that it can coordinate itself to meet the expectations using the FIPA messages. Still, there is work to be done, especially with-real-world data.
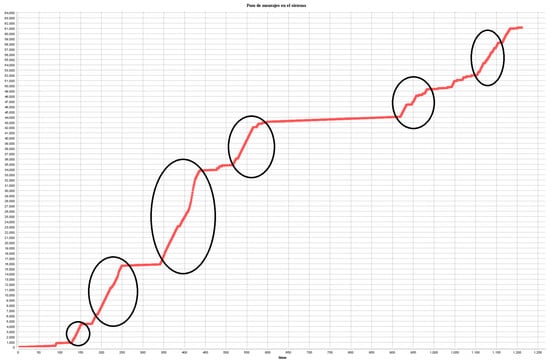
Figure 7.
Passing of messages within the system.
5. Discussion
In this section we discuss two aspects of the proposal presented that we consider important. The first is that the proposal presented in this article must be considered as multidisciplinary, because the modeling and implementation depend to a certain extent on advances in related sciences for the PSC needed. For instance, in the specific case presented in this article, in order to deal with different types of crimes, more maturity in the criminal sciences is needed to have a suitable taxonomy to identify (define specific characteristics for different type of crimes) and deal with different types of crimes. From psychology, results are needed about how to inhibit specific types of crimes; from image processing and machine learning, how to distinguish between a crime of direct contact and two persons dancing on the street; from AI, how to endow synthetic systems with human-like behavior. In our proposal we use cognitive architecture as a specific approach to endow this type of entity with the capacity to deal with a general approach for PSC.
The second very important aspect is that, in spite of our promising results obtained through simulations, we consider that before our proposal is applied in actual scenarios, there are different points that need attention. Some of them are: Security—the system needs to ensure the security of the information obtained from all of us by a public system. Cost—even though our environment currently contains many technologies, how much money is required to endow our environment with the technology needed to compose any kind of useful pervasive services? Ethics—our society is ruled by norms; thus, PSC must consider norms for PSC; for instance, how correct is it to provide a service to a person if the service may harm other persons? All these points are beyond the scope of this article; however, they must be considered when this approach is applied to a specific problem.
Furthermore, our proposal raises a number of questions that must be addressed. What are the limits of cognitive architectures? Could more fields of research benefit from using a bio-inspired approach? Should we entrust our safety to autonomous systems? Where is the line that technology should not cross? What does the population prefer, a human looking over them or a computer? These questions are very important: security and privacy are things that should be taken seriously because our existence may be at stake. As computer scientists, we can entrust our personal information to a computer system only if cybersecurity standards are applied so that our private information can not be used with malicious intent.
6. Conclusions
This proposal for pervasive service composition, or PSC, is motivated mainly by two facts: the evident increase of technology in our daily lives, and the lack of an appropriate way to compose pervasive services dealing with problems that involve the dynamism of the environment. For the first, everywhere we look we see the use of cameras, speakers, drones in the streets, factories and controlled harvest environments, not to mention the use of more and more powerful technology on people through wearables such as mobile phones, glucometers and many other types of sensors.
Regarding the second fact, the current state of the art in pervasive service composition includes multiple proposals for PSC. However, most of the time, the solutions lack memory (do not consider experience), do not propose a general way to create pervasive composite services and fail to propose a solution to novel problems arising from the environment’s dynamism, for instance, reconfiguring a pervasive service by analyzing the environment’s resources rather than composing it from scratch once one of the services fails.
The proposal presented in this article has the advantage of composing a pervasive service by using its experience in solving similar problems, thereby dealing with the dynamism of the environment the way we humans do.
The presented results obtained from simulation validate the proposed strategy for PSC. Both of the simulated case studies focused on an actual problem that is difficult to deal with: a predatorial crime. The first case study presents two scenarios: the first considers the use of an existing plan; the second considers the creation of a new one considering the context and services available at the time of the crime. The first scenario considers that the system has the experience (the memory system contains a plan to fulfill the objective). In this scenario the system ought to perform better than the second scenario when there is no experience with the crime. What is important in this case is the ability of our proposal to deal with a problem and update the information regarding the PSC, such as any modification regarding the services used and the quality of the service; the details necessary for adaptation. The interaction with other cognitive functions allows the adaptation of the composed service at any time while the PSC is required. The second scenario shows the behavior of our proposal when the system has no experience dealing with the crime: the motivation cognitive function guides the behavior to detect the crime; once it is detected, the system uses a task set to start the composition of a plan, which may or may not be useful. Some limitations of this implementation that affect the obtained results include the fact that we only consider a single type of crime, and that our system analyzes on an image-by image basis while the perception agent will have the capability to analyze video in real-time.
With this work, using simulations, we validated our proposal’s capability to create complex services much as we humans do. The results obtained from the simulation show that by using our proposal, the system may solve different problems. Currently, we are working to obtain quantitative metrics to clarify the utility of this proposal and compare our approach with more traditional ones. However before this proposal is applied in actual scenarios, different technical and non technical problems must be addressed, and some questions also must be answered. Some of these problems and questions were described in the Section 5.
Author Contributions
Conceptualization, F.F.R.C. and A.C.L.F.; methodology, F.F.R.C. and A.C.L.F.; software, A.C.L.F.; validation, A.C.L.F., and R.S.S.; formal analysis, F.F.R.C.; investigation, R.S.S., M.A.R.C.; resources, F.F.R.C.; writing—original draft preparation, F.F.R.C., A.C.L.F., R.S.S.; writing—review and editing, F.F.R.C. and M.A.R.C.; visualization, O.B.M.; supervision, F.F.R.C.; project administration, F.F.R.C.; funding acquisition, F.F.R.C. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Secretaría de Innovación, Ciencia y Tecnología de Jalisco, Mexico, and the Centro de Investigación y de Estudios Avanzados del IPN, México grant number 8053.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Acknowledgments
This research was supported by the Consejo Estatal de Ciencia y Tecnología de Jalisco, Mexico, and the Centro de Investigación y de Estudios Avanzados del IPN of México grant.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Byun, J.Y.; Nasridinov, A.; Park, Y.H. Internet of things for smart crime detection. Contemp. Eng. Sci. 2014, 7, 749–754. [Google Scholar] [CrossRef]
- Jeon, J.-H.; Jeong, S.R. Designing a Crime-Prevention System by Converging Big Data and IoT. J. Internet Comput. Serv. 2016, 17, 115–128. [Google Scholar] [CrossRef]
- Cabri, G.; Ferrari, L.; Leonardi, L.; Zambonelli, F. The LAICA project: Supporting Ambient Intelligence via agents and ad-hoc middleware. In Proceedings of the 14th IEEE International Workshops on Enabling Technologies: Infrastructure for Collaborative Enterprise (WETICE’05), Linkoping, Sweden, 13–15 June 2005; IEEE: Piscataway, NJ, USA, 2005; pp. 39–44. [Google Scholar] [CrossRef]
- Bandyopadhyay, S.; Sengupta, M.; Maiti, S.; Dutta, S. A Survey of Middleware for Internet of Things. In Recent Trends in Wireless and Mobile Networks; Özcan, A., Zizka, J., Nagamalai, D., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 288–296. [Google Scholar]
- Cerny, T.; Donahoo, M.J.; Trnka, M. Contextual understanding of microservice architecture. ACM SIGAPP Appl. Comput. Rev. 2018, 17, 29–45. [Google Scholar] [CrossRef]
- Enler, E.; Pentek, I.; Adamko, A. Healthcare Framework for Smarter Cities with bio-sensory data. In Proceedings of the 2020 11th IEEE International Conference on Cognitive Infocommunications (CogInfoCom), Mariehamn, Finland, 23–25 September 2020; pp. 000337–000342. [Google Scholar] [CrossRef]
- Demeter, R.; Kovari, A.; Katona, J.; Heldal, I.; Costescu, C.; Rosan, A.; Thill, S.; Stefanut, T. Cognitive robotics software development aspects based on experiments of future software engineers. In Proceedings of the 2020 11th IEEE International Conference on Cognitive Infocommunications (CogInfoCom), Mariehamn, Finland, 23–25 September 2020; pp. 000459–000464. [Google Scholar] [CrossRef]
- Katona, J.; Kovari, A.; Heldal, I.; Costescu, C.; Rosan, A.; Demeter, R.; Thill, S.; Stefanut, T. Using Eye- Tracking to Examine Query Syntax and Method Syntax Comprehension in LINQ. In Proceedings of the 2020 11th IEEE International Conference on Cognitive Infocommunications (CogInfoCom), Mariehamn, Finland, 23–25 September 2020; pp. 000437–000444. [Google Scholar] [CrossRef]
- Gobet, F. Individual Data Analysis and Unified Theories of Cognition: A Methodological Proposal; Universal Press: Veenendaal, The Netherlands, 2000. [Google Scholar]
- Newell, A. Unified Theories of Cognition; Harvard University Press: Cambridge, MA, USA; London, UK, 1994. [Google Scholar]
- Précis of Unified Theories of Cognition; Cambridge University Press: Cambridge, UK, 1992.
- Jiménez, J.P.; Martin, L.; Dounce, I.A.; Ávila Contreras, C.; Ramos, F. Methodological aspects for cognitive architectures construction: A study and proposal. Artif. Intell. Rev. 2020. [Google Scholar] [CrossRef]
- Ruiz Sánchez de León, J.; Fernández-Blázquez, M. Arquitecturas cognitivas y cerebro: Hacia una teoría unificada de la cognición. Int. J. Psychol. Res. 2011, 4, 38–47. [Google Scholar] [CrossRef]
- Gonz’alez-Casillas, A.; Parra, L.; Martin, L.; Avila-Contreras, C.; Ramirez-Pedraza, R.; Vargas, N.; del Valle-Padilla, J.L.; Ramos, F. Towards a model of visual recognition based on neurosciences. Procedia Comput. Sci. 2018, 145, 214–231. [Google Scholar] [CrossRef]
- Avila-Contreras, C.; Medina, O.; Jaime, K.; Ramos, F. An agent cognitive model for visual attention and response to novelty. In Agent and Multi-Agent Systems: Technologies and Applications; Springer: Cham, Switzerland, 2014; pp. 27–36. [Google Scholar]
- Torres, G.; Jaime, K.; Ramos, F.; Garcia, G. Brain architecture for visual object identification. In Proceedings of the IEEE 10th International Conference on Cognitive Informatics and Cognitive Computing (ICCI-CC’11), Banff, AB, Canada, 18–20 August 2011; pp. 33–40. [Google Scholar]
- Jaime, K.; Torres, G.; Ramos, F.; Garcia-Aguilar, G. A cognitive architecture for visual memory identification. Int. J. Softw. Sci. Comput. Intell. (IJSSCI) 2014, 6, 63–77. [Google Scholar] [CrossRef][Green Version]
- Martin, L.; Torres, G.; L’opez-Tolsa, G. Bio-inspired cognitive model for sustained attention. In Proceedings of the 2016 IEEE 15th International Conference on Cognitive Informatics & Cognitive Computing (ICCI*CC), Palo Alto, CA, USA, 22–23 August 2016; pp. 551–557. [Google Scholar]
- Rosales, J.H.; Zamarripa, M.S.; Ramos, F.; Ramos, M. Automatic reward system for virtual creatures, emergent processes of emotions and physiological motivation. Biol. Inspir. Cognit. Archit. 2017, 22, 51–66. [Google Scholar] [CrossRef]
- McEllistrem, J.E. Affective and predatory violence: A bimodal classification system of human aggression and violence. Aggress. Violent Behav. 2004, 10, 1–30. [Google Scholar] [CrossRef]
- Bouain, A.; El Fazziki, A.; Sadgal, M. Pervasive services vs. Web services: Survey and comparison. In Proceedings of the 2014 International Conference on Multimedia Computing and Systems (ICMCS), Marrakech, Morocco, 14–16 April 2014; IEEE: Piscataway, NJ, USA, 2014; pp. 552–557. [Google Scholar] [CrossRef]
- Aoudia, I.; Benharzallah, S.; Kahloul, L.; Kazar, O. Service composition approaches for internet of things: A review. Int. J. Commun. Netw. Distrib. Syst. 2019, 23, 194–230. [Google Scholar] [CrossRef]
- Baklouti, F.; Le Sommer, N.; Maheo, Y. Choreography-based vs orchestration-based service composition in opportunistic networks. In Proceedings of the 2017 IEEE 13th International Conference on Wireless and Mobile Computing, Networking and Communications (WiMob), Rome, Italy, 9–11 October 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–8. [Google Scholar] [CrossRef]
- Kalasapur, S.; Kumar, M.; Shirazi, B.A. Dynamic Service Composition in Pervasive Computing. IEEE Trans. Parallel Distrib. Syst. 2007, 18, 907–918. [Google Scholar] [CrossRef]
- Fink, E.; Veloso, M. Formalizing the PRODIGY Planning Algorithm. 1995. Available online: http://www-cgi.cs.cmu.edu/afs/cs.cmu.edu/Web/People/eugene/research/full/formalizing-prodigy.pdf (accessed on 22 June 2020).
- Weiser, M. The Computer for the 21st Century. SIGMOBILE Mob. Comput. Commun. Rev. 1999, 3, 3–11. [Google Scholar] [CrossRef]
- Asghari, P.; Rahmani, A.M.; Javadi, H.H.S. Service composition approaches in IoT: A systematic review. J. Netw. Comput. Appl. 2018, 120, 61–77. [Google Scholar] [CrossRef]
- Stavropoulos, T.G.; Vrakas, D.; Vlahavas, I. A survey of service composition in ambient intelligence environments. Artif. Intell. Rev. 2013, 40, 247–270. [Google Scholar] [CrossRef]
- Urbieta, A.; Barrutieta, G.; Parra, J.; Uribarren, A. A survey of dynamic service composition approaches for ambient systems. In Proceedings of the 2008 Ambi-Sys Workshop on Software Organisation and MonIToring of Ambient Systems (SOMITAS 2008), Quebec City, QC, Canada, 11–14 February 2008; ICST: Brussels, Belgium, 2008. [Google Scholar] [CrossRef]
- Berardi, D.; Calvanese, D.; De Giacomo, G.; Lenzerini, M.; Mecella, M. Automatic Service Composition Based on Behavioral Descriptions. Int. J. Coop. Inf. Syst. 2005, 14, 333–376. [Google Scholar] [CrossRef]
- Berardi, D.; Cheikh, F.; De Giacomo, G.; Patrizi, F. Automatic Service Composition via Simulation. Int. J. Found. Comput. Sci. 2008, 19, 429–451. [Google Scholar] [CrossRef]
- Küster, U.; König-Ries, B.; Stern, M.; Klein, M. DIANE: An Integrated Approach to Automated Service Discovery, Matchmaking and Composition. In Proceedings of the 16th International Conference on World Wide Web (WWW ’07), Banff, AB, Canada, 8–12 May 2007; Association for Computing Machinery: New York, NY, USA, 2007; pp. 1033–1042. [Google Scholar] [CrossRef]
- Dombroviak, K.M.; Ramnath, R. A taxonomy of mobile and pervasive applications. In Proceedings of the 2007 ACM Symposium on Applied Computing, Seoul, Korea, 22–26 March 2007; ACM: New York, NY, USA, 2007; pp. 1609–1615. [Google Scholar] [CrossRef]
- Mutanu, L.; Kotonya, G. State of runtime adaptation in service-oriented systems: What, where, when, how and right. IET Softw. 2019, 13, 14–24. [Google Scholar] [CrossRef]
- Petrova-Antonova, D.; Dimov, A. Towards a taxonomy of web service composition approaches. Scalable Comput. 2011, 12, 377–384. [Google Scholar] [CrossRef]
- Abdualrazak, B.; Malik, Y.; Yang, H. A Taxonomy Driven Approach towards Evaluating Pervasive Computing System. In Aging Friendly Technology for Health and Independence; Lee, Y., Bien, Z.Z., Mokhtari, M., Kim, J.T., Park, M., Kim, J., Lee, H., Khalil, I., Eds.; Springer: Berlin/Heidelberg, Germany; Seoul, Korea, 2010; pp. 32–42. [Google Scholar] [CrossRef]
- Cabrera, C.; Li, F.; Nallur, V.; Palade, A.; Razzaque, M.A.; White, G.; Clarke, S. Implementing heterogeneous, autonomous, and resilient services in IoT: An experience report. In Proceedings of the 2017 IEEE 18th International Symposium on A World of Wireless, Mobile and Multimedia Networks (WoWMoM), Macau, China, 12–15 June 2017; IEEE: Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar] [CrossRef]
- Chen, N.; Cardozo, N.; Clarke, S. Goal-Driven Service Composition in Mobile and Pervasive Computing. IEEE Trans. Serv. Comput. 2018, 11, 49–62. [Google Scholar] [CrossRef]
- Cervantes, F.; Ramos, F.; Gutiérrez, L.F.; Occello, M.; Jamont, J.P. A New Approach for the Composition of Adaptive Pervasive Systems. IEEE Syst. J. 2018, 12, 1709–1721. [Google Scholar] [CrossRef]
- Romero, O.J. Cognitively-Inspired Agent-Based Service Composition for Mobile and Pervasive Computing. In Proceedings of the 8th International Conference, Held as Part of the Services Conference Federation (SCF 2019), Artificial Intelligence and Mobile Services (AIMS 2019), San Diego, CA, USA, 20–25 June 2019; Springer: Cham, Switzerland, 2019; pp. 101–117. [Google Scholar] [CrossRef]
- Martin, E.A. Oxford Dictionary of Law; Oxford University Press: Oxford, UK, 2003. [Google Scholar]
- Felson, M.; Cohen, L.E. Human ecology and crime: A routine activity approach. Hum. Ecol. 1980, 8, 389–406. [Google Scholar] [CrossRef]
- Meloy, J.R. Predatory violence and psychopathy. In Psychopathy and Law; Wiley: London, UK, 2012. [Google Scholar]
- Rossmo, D.K.; Summers, L. Routine activity theory in crime investigation. In The Criminal Act; Palgrave Macmillan: London, UK, 2015; pp. 19–32. [Google Scholar]
- National Academies of Sciences, Engineering, and Medicine. Modernizing Crime Statistics: Report 1: Defining and Classifying Crime; Lauritsen, J., Cork, D., Eds.; The National Academies Press: Washington, DC, USA, 2016. [Google Scholar] [CrossRef]
- Wooldridge, M.; Jennings, N.R.; Kinny, D. The Gaia Methodology for Agent-Oriented Analysis and Design. Auton. Agents Multi-Agent Syst. 2000, 3, 285–312. [Google Scholar] [CrossRef]
- Baranyi, P.; Csapo, A.; Sallai, G. Cognitive Infocomunications (CogInfoCom); Springer: Cham, Switzerland, 2015; ISBN 978-3-319-19608-4. [Google Scholar]
- Baranyi, P.; Csapó, Á. Definition and synergies of cognitive infocommunications. Acta Polytech. Hung. 2012, 9, 67–83. [Google Scholar]
- Number of Robberies in the United States in 2018, by Weapon Used. Available online: https://www.statista.com/statistics/251914/number-of-robberies-in-the-us-by-weapon (accessed on 22 June 2020).
- Ramirez-Pedraza, R.; Vargas, N.; Sandoval, C.; del Valle-Padilla, J.L.; Ramos, F. A bio-inspired model of behavior considering decision-making and planning, spatial attention and basic motor commands processes. Cognit. Syst. Res. 2020, 59, 293–303. [Google Scholar] [CrossRef]
- Surianarayanan, C.; Ganapathy, G.; Chelliah, P.R. Service Orchestration and Choreography. In Essentials of Microservices Architecture, 1st ed.; Taylor & Francis: Boca Raton, FL, USA, 2019; pp. 175–197. [Google Scholar] [CrossRef]
- Gómez-Martínez, D.G.; Ramos, M.; del Valle-Padilla, J.L.; Rosales, J.-H.; Robles, F.; Ramos, F. Bioinspired model of short-term satiety of hunger influenced by food properties in virtual creatures. Cognit. Syst. Res. 2021, 66, 46–66. [Google Scholar] [CrossRef]
- Martin, L.; Jaime, K.; Ramos, F.; Robles, F. Declarative Working Memory: A Bio-Inspired Cognitive Architecture Proposal. Cognit. Syst. Res. 2021, 66, 30–45. [Google Scholar] [CrossRef]
- Dounce, I.A.; Ramos, F. An expanded model for perceptual visual single object recognition system using expectation priming following neuroscientific evidence. Cognit. Syst. Res. 2021, 66, 150–161. [Google Scholar] [CrossRef]
- Vargas, N.; del Valle-Padilla, J.L.; Jimenez, J.P.; Ramos, F. A model of top-down attentional control for visual search based on neurosciences. In Biologically Inspired Cognitive Architectures Meeting; Springer: Cham, Switzerland, 2020; pp. 541–546. [Google Scholar]
- Sandoval, C.J.; Ramos, F.F. A proposal of bioinspired motor-system cognitive architecture focused on feedforward-control movements. Cognit. Syst. Res. 2021, 67, 50–59. [Google Scholar] [CrossRef]
- Jaime, K.; Cervantes, A.; Medina, O.; Ramos, F.; Rosales, J.-H.; Torres, G.; Ramos, M. A middleware for integrating cognitive architectures. In Proceedings of the 8th International Conference on Brain Informatics and Health (BIH 2015), London, UK, 30 August–2 September 2015; Springer: Cham, Switzerland, 2015; pp. 435–444. [Google Scholar]
- Cervantes, A. Modelo Bio-Inspirado de Comunicaci’øn y Soporte Para Arquitecturas Cognitivas. Ph.D. Thesis, CINVESTAV del IPN Unidad Guadalajara, Zapopan, Jalisco, Mexico, 2020. [Google Scholar]
- A Single Drone Helped Mexican Police Drop Crime 10 Percent. Available online: https://www.wired.com/story/ensenada-mexico-police-drone (accessed on 22 June 2020).
- Taillandier, P.; Gaudou, B.; Grignard, A.; Huynh, Q.-N.; Marilleau, N.; Caillou, P.; Philippon, D.; Drogoul, A. Building, composing and experimenting complex spatial models with the GAMA platform. GeoInformatica 2019, 23, 299–322. [Google Scholar] [CrossRef]
- Poslad, S. Specifying Protocols for Multi-Agent Systems Interaction. ACM Trans. Auton. Adapt. Syst. 2007, 2. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).