Age of Information and Success Probability Analysis in Hybrid Spectrum Access-Based Massive Cognitive Radio Networks
Abstract
1. Introduction
1.1. Hybrid Spectrum Access
1.2. Age of Information
1.3. Related Works
1.4. Contributions and Organisation
- By capturing the spatial distributions of users in both primary and secondary networks following two independent Poisson point processes (PPPs), we obtained tractable analysis for the conventional success probability (i.e., service/update delivery rate) in the considered hybrid spectrum access CRN. Since success probability is a location-dependent random variable, the analysis for the distribution of conditional success probability known as Meta distribution was further obtained.
- Using the analysis of the conventional success probability obtained, we derived expressions for the network throughput in the hybrid spectrum access CRN for both primary and secondary networks.
- Finally, based on the analysis of the conditional success probability, the expression for conditional average AoI was presented for the underlay, overlay and hybrid spectrum access CRN. To the best of our knowledge, this is the first work that investigates AoI in the hybrid spectrum access-based CRN.
2. Network Model
3. Analysis of Success Probability
3.1. Success Probability in Hybrid Cognitive Networks
3.1.1. Analysis in the Primary Network
- Underlay model: In the presence of at least one PT, STs coexist with active PTs as in the underlay mode, provided that its location is not within the exclusion region D of any active PT. Hence the PU outage probability at any typical PR is obtained from (5) asIn a simplified CRN, only a single PT transmits on any channel, thus . However, in a massive or large scale CRN considered in this paper, multiple PTs can co-exist within the same channel, hence [2]. is expressed aswhere is the large-scale path loss attenuation between the transmitter a and receiver b. Under Rayleigh fading assumption, is assumed to be independent and identically distributed exponential random variables with unit mean, i.e., . By applying the probability generating function of PPP to (6),where and . The expression of can be obtained through the void probability technique, , which captures the repulsion between active PTs. The resulting point process can as well be approximated as a PPP of intensity . The derivation of (7) is straightforward from [29]. Similarly,where , knowing that an ST will only transmit when its location is outside the region of radius D of any active PTs. Hence, . The resulting point process in this case is better represented as hole processes. However, to avoid unnecessary complicated analysis, we approximated the distribution of active STs as independent PPP of equidense intensity .
- Overlay model: In the absence of active STs, PTs transmit in the overlay mode. Hence the interference from STs is normally assumed to be zero in the overlay mode provided that there is no inter-channel interference. With this, andFinally, when there is misdetection of PTs signal by SUs, active STs transmit with full transmit power thereby causing more interference in the primary network. Hence, at any typical PR,
3.1.2. Analysis of the Secondary Network
- Underlay model: In the presence of at least one PT, STs coexist with active PTs as in the conventional underlay mode, hence the SU’s outage probability at any typical SR at is given asFinally, when STs transmit in the underlay mode as a result of a false alarm, the only interference generated is from other active STs, hence,
- Overlay mode: In overlay mode, the interference from PTs can be assumed to be zero when there is no active PT on the channel. With this, andWhen there is misdetection of PTs signal, STs transmit with full transmit power thereby generating higher interference at any active PR, while also receiving interference from active PTs. Hence, at any typical SR,
3.2. Conditional Success Probability
3.2.1. Conditional Success Probability in Primary Network
3.2.2. Conditional Success Probability in Secondary Network
4. Analysis for Network Throughput and Average Age of Information
4.1. Network Throughput
4.2. Average Age of Information
5. Numerical Results and Simulation
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Oh, J.; Choi, W. A hybrid cognitive radio system: A combination of underlay and overlay approaches. In Proceedings of the IEEE Vehicular Technology Conference-Fall, Ottawa, OT, Canada, 6–9 September 2010; pp. 1–5. [Google Scholar]
- Okegbile, S.D.; Maharaj, B.T.; Alfa, A.S. Interference characterization in underlay cognitive networks with intra-network and inter-network dependence. IEEE Trans. Mobile Comput. 2020. [Google Scholar] [CrossRef]
- Zhao, Y.; Peng, M.; Liu, J. A Hybrid Spectrum Access Strategy with Channel Bonding and Classified Secondary User Mechanism in Multichannel Cognitive Radio Networks. Sensors 2019, 19, 4398. [Google Scholar] [CrossRef]
- Zou, J.; Xiong, H.; Wang, D.; Chen, C.W. Optimal power allocation for hybrid overlay/underlay spectrum sharing in multiband cognitive radio networks. IEEE Trans. Veh. Technol. 2012, 62, 1827–1837. [Google Scholar] [CrossRef]
- Song, H.; Hong, J.P.; Choi, W. On the optimal switching probability for a hybrid cognitive radio system. IEEE Trans. Wirel. Commun. 2013, 12, 1594–1605. [Google Scholar] [CrossRef]
- Kaul, S.; Yates, R.; Gruteser, M. Real-time status: How often should one update? In Proceedings of the IEEE INFOCOM, Orlando, FL, USA, 25–30 March 2012; pp. 2731–2735. [Google Scholar]
- Gu, Y.; Chen, H.; Zhai, C.; Li, Y.; Vucetic, B. Minimizing age of information in cognitive radio-based IoT systems: Underlay or overlay? IEEE Internet Things J. 2019, 6, 10273–10288. [Google Scholar] [CrossRef]
- Leng, S.; Ni, X.; Yener, A. Age of information for wireless energy harvesting secondary users in cognitive radio networks. In Proceedings of the IEEE International Conference on Mobile Ad Hoc and Sensor Systems, Monterey, CA, USA, 4–7 November 2019; pp. 353–361. [Google Scholar]
- Kosta, A.; Pappas, N.; Ephremides, A.; Angelakis, V. Age of information and throughput in a shared access network with heterogeneous traffic. In Proceedings of the IEEE Global Communications Conference, Abu Dhabi, UAE, 9–13 December 2018; pp. 1–6. [Google Scholar]
- Mankar, P.D.; Abd-Elmagid, M.A.; Dhillon, H.S. Spatial distribution of the mean peak age of information in wireless networks. arXiv 2020, arXiv:2006.00290. [Google Scholar]
- Okegbile, S.D.; Maharaj, B.T.; Alfa, A.S. Outage and throughput analysis of cognitive users in underlay cognitive radio networks with handover. IEEE Access 2020, 8, 208045–208057. [Google Scholar] [CrossRef]
- Okegbile, S.D.; Ogunranti, O.I. Users emulation attack management in massive internet of things enabled environment. ICT Express 2020, 6, 353–356. [Google Scholar] [CrossRef]
- Okegbile, S.; Maharaj, B.; Alfa, A. Malicious users control and management in cognitive radio networks with priority queues. In Proceedings of the IEEE VTC Conference, Victoria, BC, Canada, 18 November–16 December 2020. [Google Scholar]
- Okegbile, S.D.; Maharaj, B.T.; Alfa, A.S. Stochastic geometry approach towards interference management and control in cognitive radio network: A survey. Comput. Commun. 2021, 166, 174–195. [Google Scholar] [CrossRef]
- Mankar, P.D.; Chen, Z.; Abd-Elmagid, M.A.; Pappas, N.; Dhillon, H.S. Throughput and Age of Information in a Cellular-based IoT Network. arXiv 2020, arXiv:2005.09547. [Google Scholar]
- Hu, Y.; Zhong, Y.; Zhang, W. Age of information in Poisson networks. In Proceedings of the IEEE International Conference on Wireless Communications and Signal Processing, Hangzhou, China, 29–31 July 2018; pp. 1–6. [Google Scholar]
- Usman, M.; Koo, I. Access strategy for hybrid underlay-overlay cognitive radios with energy harvesting. IEEE Sen. J. 2014, 14, 3164–3173. [Google Scholar] [CrossRef]
- Shaker, R.; Khakzad, H.; Taherpour, A.; Khattab, T.; Hasna, M.O. Hybrid underlay/overlay cognitive radio system with hierarchical modulation in the presence of channel estimation error. In Proceedings of the IEEE Global Communications Conference, Austin, TX, USA, 8–12 December 2014; pp. 967–972. [Google Scholar]
- Jiang, X.; Wong, K.K.; Zhang, Y.; Edwards, D. On hybrid overlay–underlay dynamic spectrum access: Double-threshold energy detection and Markov model. IEEE Trans. Veh. Technol. 2013, 62, 4078–4083. [Google Scholar] [CrossRef]
- Chen, Y.; Lei, Q.; Yuan, X. Resource allocation based on dynamic hybrid overlay/underlay for heterogeneous services of cognitive radio networks. Wirel. Pers. Commun. 2014, 79, 164–1664. [Google Scholar] [CrossRef]
- Karmokar, A.K.; Senthuran, S.; Anpalagan, A. Physical layer-optimal and cross-layer channel access policies for hybrid overlay–underlay cognitive radio networks. IET Commun. 2014, 8, 266–2675. [Google Scholar] [CrossRef]
- Bhowmick, A.; Prasad, B.; Roy, S.D.; Kundu, S. Performance of cognitive radio network with novel hybrid spectrum access schemes. Wirel. Pers. Commun. 2016, 91, 541–560. [Google Scholar] [CrossRef]
- Duy, T.T.; Thanh, T.L.; Bao, V.N. A hybrid spectrum sharing approach in cognitive radio networks. In Proceedings of the IEEE International Conference on Computing, Management and Telecommunications, Da Nang, Vietnam, 27–29 April 2014; pp. 19–23. [Google Scholar]
- Tefek, U.; Lim, T. Interference management through exclusion zones in two-tier cognitive networks. IEEE Trans. Wirel. Commun. 2016, 15, 2292–2302. [Google Scholar] [CrossRef]
- Baccelli, F.; Blaszczyszyn, B. Stochastic Geometry and Wireless Networks, Volume I—Theory; Now Publishers: Boston, MA, USA, 2010. [Google Scholar]
- Okegbile, S.D.; Maharaj, B.T.; Alfa, A.S. Relaying techniques based outage analysis for mobile users in cognitive radio networks. In Proceedings of the IEEE Vehicular Technology Conference, Antwerp, Belgium, 25–28 May 2020; pp. 1–5. [Google Scholar]
- Yang, H.H.; Arafa, A.; Quek, T.Q.; Poor, H.V. Locally adaptive scheduling policy for optimizing information freshness in wireless networks. In Proceedings of the IEEE Global Communications Conference, Waikoloa, HI, USA, 9–13 December 2019; pp. 1–6. [Google Scholar]
- Okegbile, S.D.; Maharaj, B.T.; Alfa, A.S. Spatiotemporal Characterization of Users’ Experience in Massive Cognitive Radio Networks. IEEE Access 2020, 8, 57114–57125. [Google Scholar] [CrossRef]
- Haenggi, M.; Ganti, R.K. Interference in large wireless networks. Found. Trends Netw. 2008, 3, 127–248. [Google Scholar] [CrossRef]
- Haenggi, M. The meta distribution of the SIR in Poisson bipolar and cellular networks. IEEE Trans. Wirel. Commun. 2015, 15, 2577–2589. [Google Scholar] [CrossRef]
- Yang, H.H.; Quek, T.Q. Spatio-temporal analysis for SINR coverage in small cell networks. IEEE Trans. Commun. 2019, 67, 5520–5531. [Google Scholar] [CrossRef]
- Yates, R.D.; Kaul, S.K. The age of information: Real-time status updating by multiple sources. IEEE Trans. Inf. Theory 2019, 65, 1807–1827. [Google Scholar] [CrossRef]
- Chen, Z.; Pappas, N.; Bjornson, E.; Larsson, E.G. Age of information in a multiple access channel with heterogeneous traffic and an energy harvesting node. In Proceedings of the IEEE INFOCOM Workshops, Paris, France, 29 April–2 May 2019; pp. 662–667. [Google Scholar]





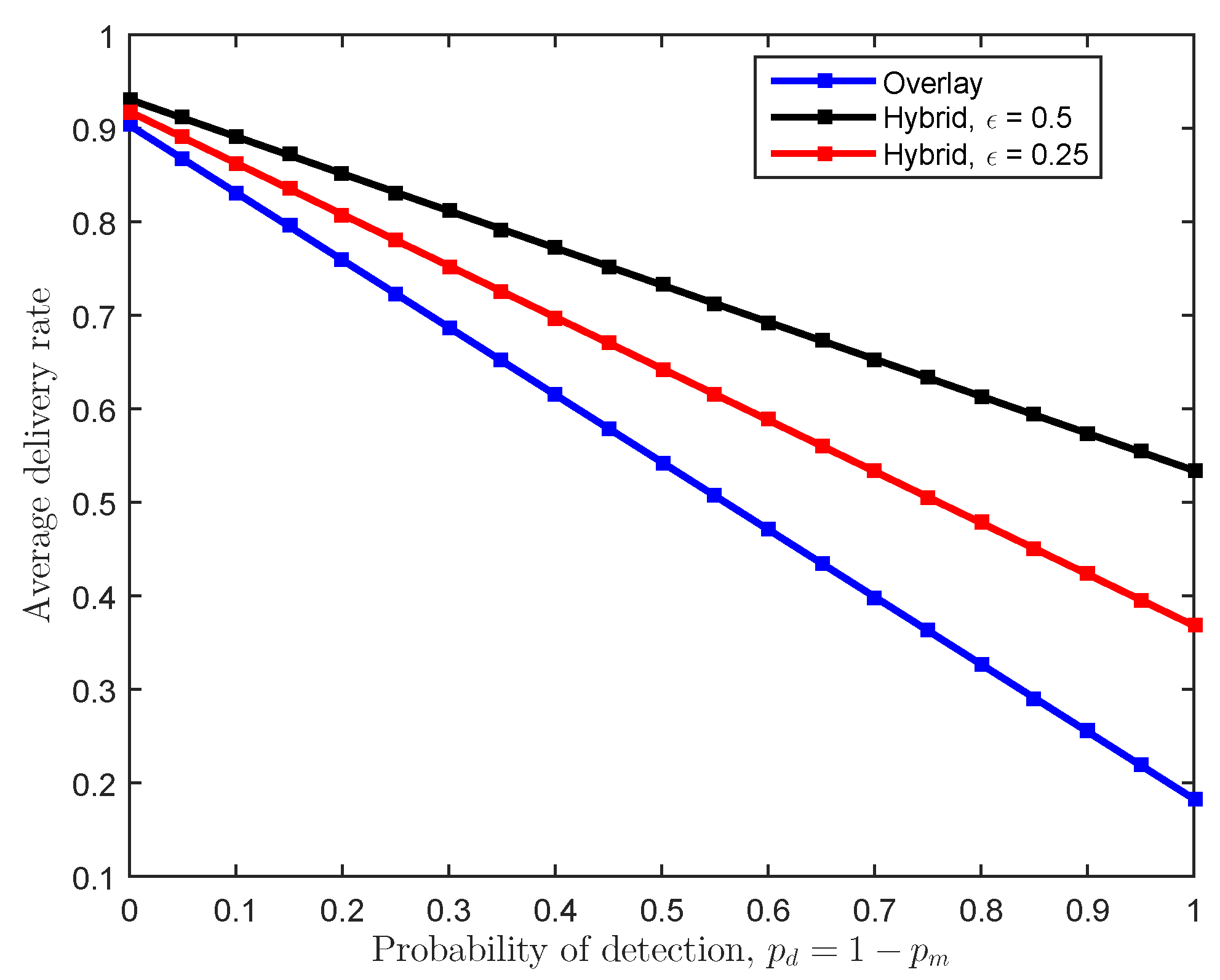
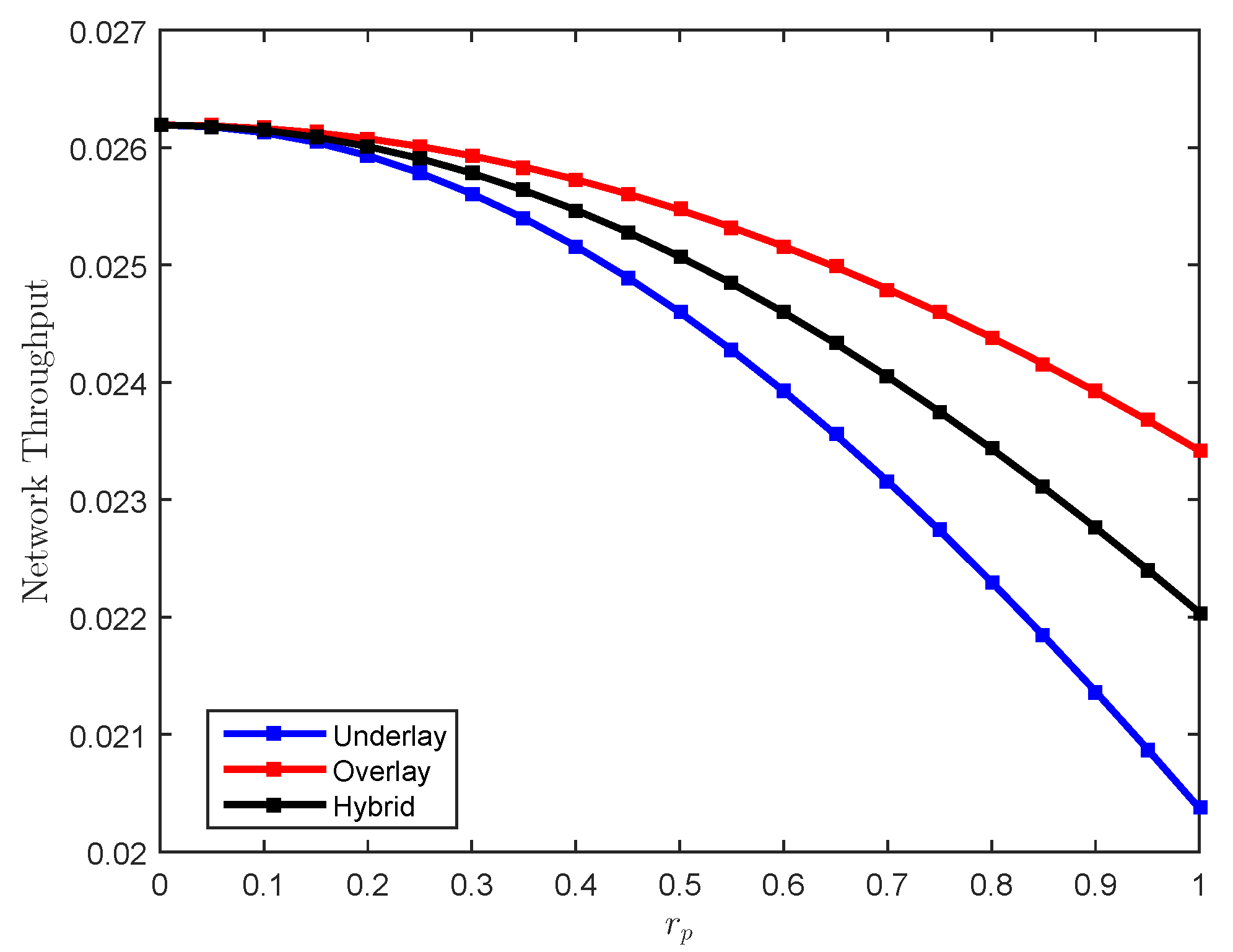
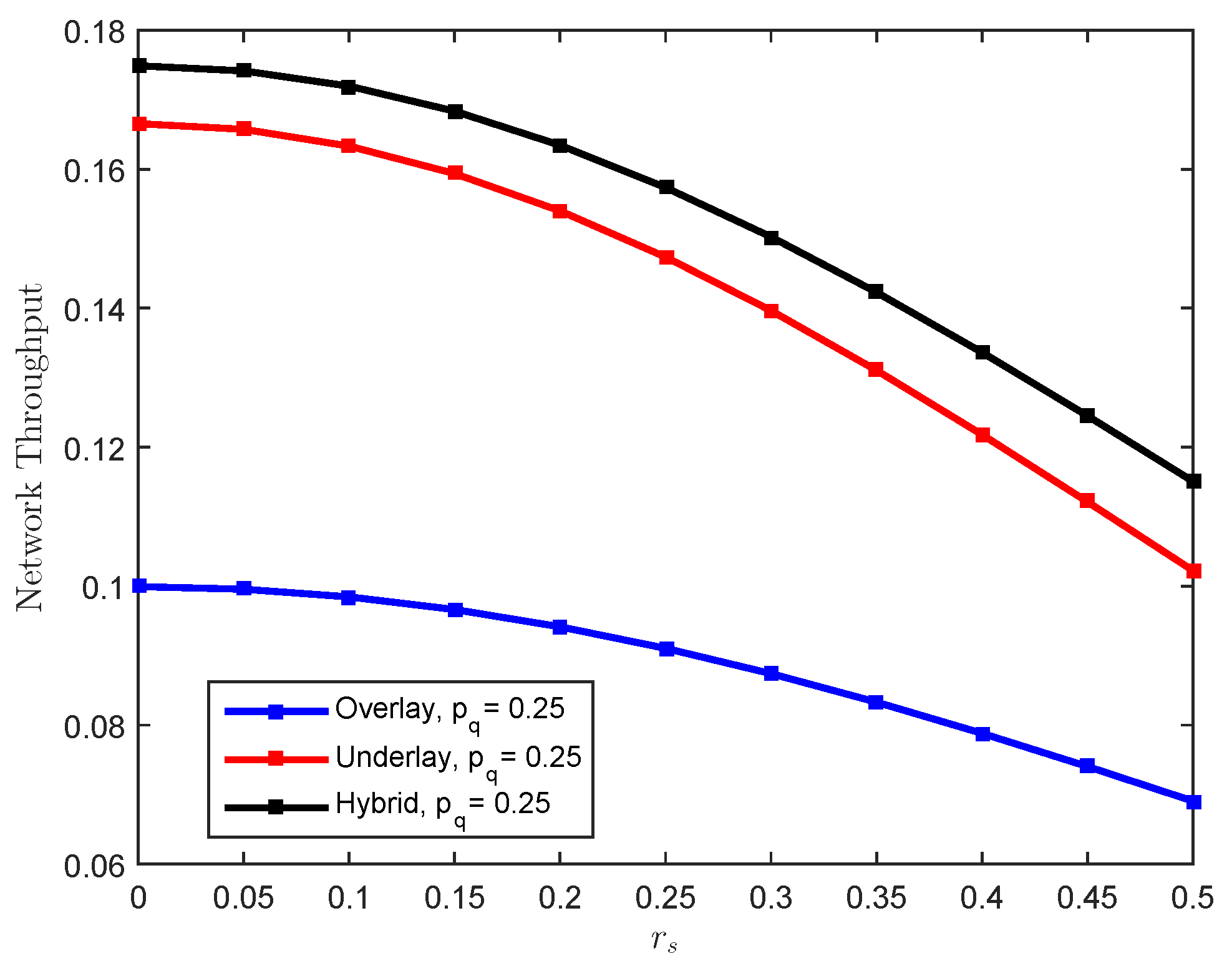


| Parameter | Definition | Value |
|---|---|---|
| Distribution of secondary transmitter-receiver pairs | 0.3 | |
| Distribution of primary transmitter-receiver pairs | 0.03 | |
| Distance between any tagged primary transmitter-receiver pair | 0.5 m | |
| Distance between any tagged secondary transmitter-receiver | 0.1 m | |
| PT’s transmission power signal | 0 dB | |
| ST’s transmission power signal in the overlay mode | −32 dB | |
| ST’s transmission power signal in the underlay mode | −36 dB | |
| Path-loss exponent | 4 | |
| D | Coverage region of any PT | 1.2 m |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Okegbile, S.D.; Maharaj, B.T. Age of Information and Success Probability Analysis in Hybrid Spectrum Access-Based Massive Cognitive Radio Networks. Appl. Sci. 2021, 11, 1940. https://doi.org/10.3390/app11041940
Okegbile SD, Maharaj BT. Age of Information and Success Probability Analysis in Hybrid Spectrum Access-Based Massive Cognitive Radio Networks. Applied Sciences. 2021; 11(4):1940. https://doi.org/10.3390/app11041940
Chicago/Turabian StyleOkegbile, Samuel D., and Bodhaswar T. Maharaj. 2021. "Age of Information and Success Probability Analysis in Hybrid Spectrum Access-Based Massive Cognitive Radio Networks" Applied Sciences 11, no. 4: 1940. https://doi.org/10.3390/app11041940
APA StyleOkegbile, S. D., & Maharaj, B. T. (2021). Age of Information and Success Probability Analysis in Hybrid Spectrum Access-Based Massive Cognitive Radio Networks. Applied Sciences, 11(4), 1940. https://doi.org/10.3390/app11041940






