Novel Implementation of Audio Encryption Using Pseudorandom Byte Generator
Abstract
:1. Introduction
- We applied the pseudo-random number generator based on the Ikeda map [16] to a novel audio encryption scheme;
- We examined the proposed algorithm and the results show that it has a very good sample change rate number, desirable signal-to-noise and peak signal-to-noise ratios as well as strong key sensitivity that is able to resist most common theoretical and statistical attacks;
- We allow ourselves to make the assumption that the proposed audio encryption is suitable for ensuring the security of different byte-oriented multimedia sources such as images and video files.
2. Ikeda Map Used as a Basis for a Pseudo-Random Generator
2.1. Description of the Ikeda Map
2.2. Description of the Pseudo-Random Byte Algorithm
- The initial values and parameters forming the key set for the two Ikeda functions were obtained—, , , , and ;
- More than 100 iterations of the Ikeda maps were made without retrieving any results;
- The work of the algorithm continues with more iterations of the Ikeda maps to calculate and post-process the four real values—, , , . They are calculated as follows:where returns the integer part of z—truncating the value at the decimal point— returns the absolute value of z, and returns the reminder after division;
- Output byte is generated when XOR operations are performed between and d: ;
- Perform Step 3 until the output stream is reached.
3. Novel Implementation of Audio Encryption Scheme
Proposed Encryption and Decryption Algorithm
- In file A’, the header bytes of a input audio file A are moved without cryptographic modifications;
- Using logical XOR operation with the same amount of bytes as the bytes in the sample produced by the pseudo-random generator described above the bytes in the sample are encrypted;
- Encrypted sample from Step 2 is processed into file A’;
- Repeat Steps 2–3 until the end of input file A is reached;
- The produced output file A’ is the final encrypted audio file.
4. Cryptographic Analysis
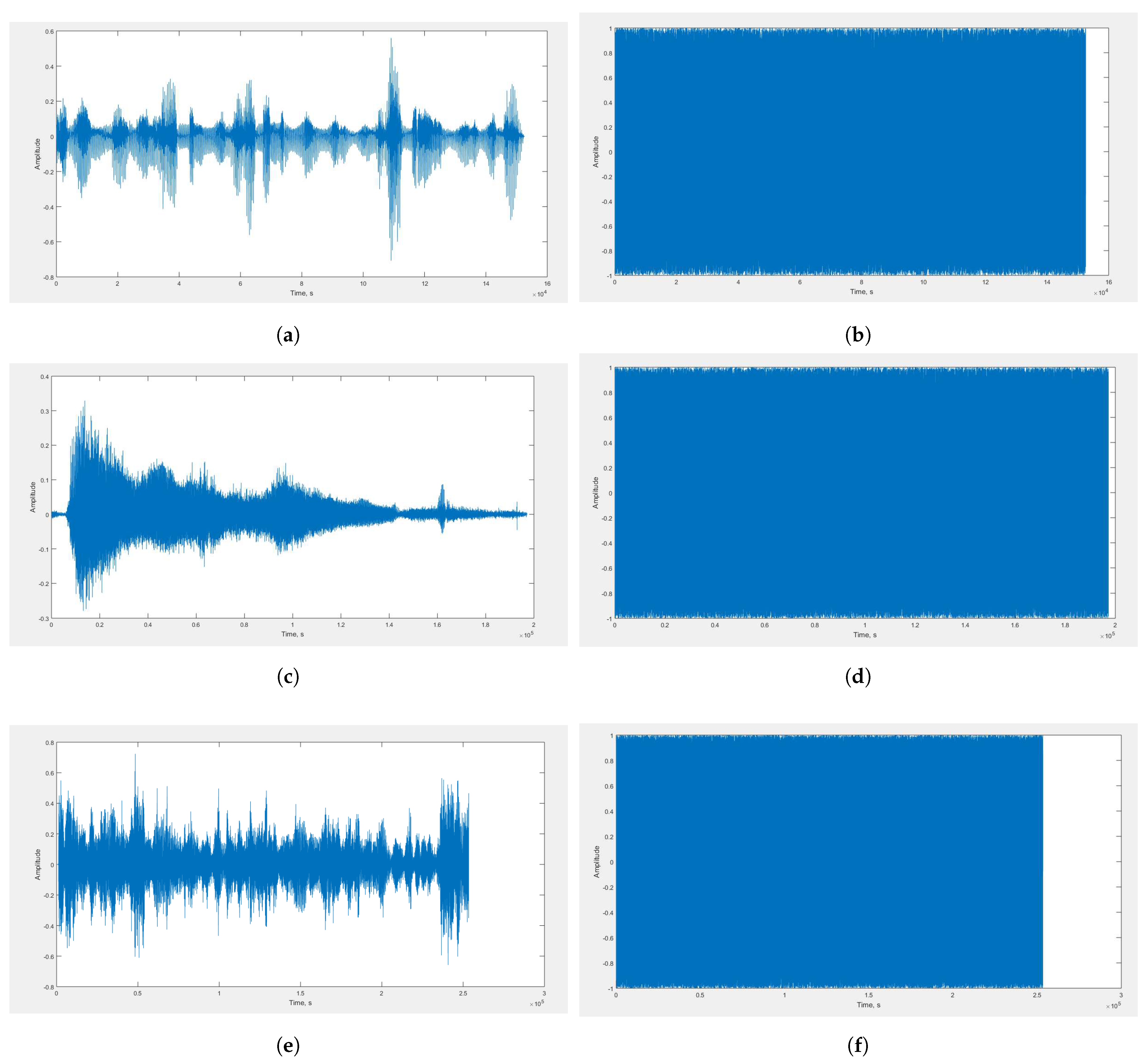
4.1. Waveform Plotting
4.2. Correlation Analysis
4.3. Number of Sample Change Rate
4.4. Signal-to-Noise Ratio
4.5. Peak Signal-to-Noise Ratio
4.6. Speed Performance
4.7. Encryption/Decryption Key Sensitivity
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Rivest, R.L.; Shamir, A.; Adleman, L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems. Commun. ACM 1978, 21, 120–126. [Google Scholar] [CrossRef]
- Rijmen, V.; Daemen, J. Advanced encryption standard (AES). In Federal Information Processing Standards Publications 197; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2001. Available online: https://csrc.nist.gov/publications/detail/fips/197/final (accessed on 1 September 2021).
- Schneier, B. Description of a new variable-length key, 64-bit block cipher (Blowfish). In Fast Software Encryption; Anderson, R., Ed.; Springer: Berlin/Heidelberg, Germany, 1994; pp. 191–204. [Google Scholar] [CrossRef] [Green Version]
- Ghasemzadeh, A.; Esmaeili, E. A novel method in audio message encryption based on a mixture of chaos function. Int. J. Speech Technol. 2017, 20, 829–837. [Google Scholar] [CrossRef]
- Sathiyamurthi, P.; Ramakrishnan, S. Speech encryption using chaotic shift keying for secured speech communication. EURASIP J. Audio Speech Music Process. 2017, 2017, 1–11. [Google Scholar] [CrossRef]
- Wang, X.; Su, Y. An Audio Encryption Algorithm Based on DNA Coding and Chaotic System. IEEE Access 2020, 8, 9260–9270. [Google Scholar] [CrossRef]
- Moreno-Alvarado, R.; Rivera-Jaramillo, E.; Nakano, M.; Perez-Meana, H. Simultaneous Audio Encryption and Compression Using Compressive Sensing Techniques. Electronics 2020, 9, 863. [Google Scholar] [CrossRef]
- Kordov, K. A Novel Audio Encryption Algorithm with Permutation-Substitution Architecture. Electronics 2019, 8, 530. [Google Scholar] [CrossRef] [Green Version]
- Adhikari, S.; Karforma, S. A novel audio encryption method using Henon–Tent chaotic pseudo random number sequence. Int. J. Inf. Technol. 2021, 13, 1463–1471. [Google Scholar] [CrossRef]
- Aziz, H.; Gilani, S.M.M.; Hussain, I.; Janjua, A.K.; Khurram, S. A Noise-Tolerant Audio Encryption Framework Designed by the Application of S8 Symmetric Group and Chaotic Systems. Math. Problems Eng. 2021, 2021, 5554707. [Google Scholar] [CrossRef]
- Roy, A.; Misra, A. Audio signal encryption using chaotic Hénon map and lifting wavelet transforms. Eur. Phys. J. Plus 2017, 132, 1–10. [Google Scholar] [CrossRef] [Green Version]
- Shah, D.; Shah, T.; Ahamad, I.; Haider, M.I.; Khalid, I. A three-dimensional chaotic map and their applications to digital audio security. Multimedia Tools Appl. 2021, 80, 22251–22273. [Google Scholar] [CrossRef]
- Tutueva, A.V.; Karimov, T.I.; Moysis, L.; Nepomuceno, E.G.; Volos, C.; Butusov, D.N. Improving chaos-based pseudo-random generators in finite-precision arithmetic. Nonlinear Dyn. 2021, 104, 727–737. [Google Scholar] [CrossRef]
- Hato, E.; Shihab, D. Lorenz and rossler chaotic system for speech signal encryption. Int. J. Comput. Appl. 2015, 128, 25–33. [Google Scholar] [CrossRef]
- Liu, H.; Kadir, A.; Li, Y. Audio encryption scheme by confusion and diffusion based on multi-scroll chaotic system and one-time keys. Optik 2016, 127, 7431–7438. [Google Scholar] [CrossRef]
- Stoyanov, B.; Ivanova, T. CHAOSA: Chaotic map based random number generator on Arduino platform. AIP Conf. Proc. 2019, 2172, 090001. [Google Scholar] [CrossRef]
- Ikeda, K. Multiple-valued stationary state and its instability of the transmitted light by a ring cavity system. Opt. Commun. 1979, 30, 257–261. [Google Scholar] [CrossRef]
- Ikeda, K.; Daido, H.; Akimoto, O. Optical Turbulence: Chaotic Behavior of Transmitted Light from a Ring Cavity. Phys. Rev. Lett. 1980, 45, 709–712. [Google Scholar] [CrossRef]
- Buscarino, A.; Fortuna, L.; Frasca, M. Essentials of Nonlinear Circuit Dynamics with MATLAB® and Laboratory Experiments; CRC Press: Taylor and Francis Group: Boca Raton, FL, USA, 2017. [Google Scholar]
- Mohammadi, S. LYAPROSEN: MATLAB Function to Calculate Lyapunov Exponent; Boston College, Department of Economics: Boston, MA, USA, 2009; Available online: https://EconPapers.repec.org/RePEc:boc:bocode:t741502 (accessed on 1 September 2021).
- Li, S.; Chen, G.; Mou, X. On the dynamical degradation of digital piecewise linear chaotic maps. Int. J. Bifurcation Chaos 2005, 15, 3119–3151. [Google Scholar] [CrossRef] [Green Version]
- Patidar, V.; Sud, K.K.; Pareek, N.K. A pseudo random bit generator based on chaotic logistic map and its statistical testing. Informatica 2009, 33, 441–452. [Google Scholar]
- Tutueva, A.; Pesterev, D.; Karimov, A.; Butusov, D.; Ostrovskii, V. Adaptive Chirikov Map for Pseudo-random Number Generation in Chaos-based Stream Encryption. In Proceedings of the 2019 25th Conference of Open Innovations Association (FRUCT), Helsinki, Finland, 5–8 November 2019; pp. 333–338. [Google Scholar] [CrossRef]
- IEEE Standard for Floating-Point Arithmetic. In IEEE Std 754-2019 (Revision of IEEE 754-2008); IEEE: Piscatway, NJ, USA; New York, NY, USA, 2019; pp. 1–84. [CrossRef]
- Jozwiak, M.; Monnet, X.; Teboul, J.L. Pressure waveform analysis. Anesth. Analg. 2018, 126, 1930–1933. [Google Scholar] [CrossRef] [PubMed]
- Taylor, R. Interpretation of the correlation coefficient: A basic review. J. Diagnost. Med. Sonogr. 1990, 6, 35–39. [Google Scholar] [CrossRef]
- Farsana, F.; Devi, V.; Gopakumar, K. An audio encryption scheme based on Fast Walsh Hadamard Transform and mixed chaotic keystreams. Appl. Comput. Inform. 2019. [Google Scholar] [CrossRef]
- Johnson, D.H. Signal-to-noise ratio. Scholarpedia 2006, 1, 2088. [Google Scholar] [CrossRef]
- Korhonen, J.; You, J. Peak signal-to-noise ratio revisited: Is simple beautiful? In Proceedings of the 2012 Fourth International Workshop on Quality of Multimedia Experience, Melbourne, Australia, 5–7 July 2012; pp. 37–38. [Google Scholar] [CrossRef]
- Poobathy, D.; Chezian, R.M. Edge detection operators: Peak signal to noise ratio based comparison. Int. J. Image Graph. Signal Process. 2014, 10, 55–61. [Google Scholar] [CrossRef] [Green Version]
- Ahamad, M.M.; Abdullah, M.I. Comparison of encryption algorithms for multimedia. Rajshahi Univ. J. Sci. Eng. 2016, 44, 131–139. [Google Scholar] [CrossRef]




| Audio File | File Size | File Length | Corellation Coefficient |
|---|---|---|---|
| usb-headset-weird | 200 kb | 2.32 s | −0.0248023 |
| cartoon-mumble-speak | 298.1 kb | 3.45 s | 0.0008942 |
| grito-wav | 385.3 kb | 4.47 s | 0.0167187 |
| a-strange-dream | 495 kb | 5.74 s | −0.0376280 |
| radio | 691 kb | 8.02 s | 0.0222683 |
| insult | 832 kb | 9.66 s | 0.0157122 |
| sharpening-blade-long-blade | 1228.8 kb | 14.48 s | −0.0211372 |
| airport-security-message | 1740.8 kb | 20.28 s | −0.0335765 |
| shakuhachi-grave-5 | 2048 kb | 23.41 s | −0.0068954 |
| Ref. [5] | - | 7 s | 0.0233000 |
| Ref. [8] | 2.33 mb | 13.85 s | 0.0004710 |
| Ref. [27] | - | - | 0.0000900 |
| AES [27] | - | - | 0.0097100 |
| Audio File | NSCR |
|---|---|
| usb-headset-weird | 99.994% |
| cartoon-mumble-speak | 100.000% |
| grito-wav | 99.998% |
| a-strange-dream | 99.996% |
| radio | 99.999% |
| insult | 99.999% |
| sharpening-blade-long-blade | 99.998% |
| airport-security-message | 99.998% |
| shakuhachi-grave-5 | 99.998% |
| Ref. [5] | 99.998% |
| Ref. [8] | 99.998% |
| Ref. [27] | 99.998% |
| AES [27] | 99.603% |
| Audio File | SNR | PSNR |
|---|---|---|
| usb-headset-weird | −42.3697 dB | 4.6583 dB |
| cartoon-mumble-speak | −44.6930 dB | 4.7036 dB |
| grito-wav | −43.0053 dB | 4.7551 dB |
| a-strange-dream | −44.8190 dB | 4.6431 dB |
| radio | −40.7581 dB | 4.6431 dB |
| insult | −43.2195 dB | 4.7109 dB |
| sharpening-blade-long-blade | −28.5052 dB | 4.7690 dB |
| airport-security-message | −44.7026 dB | 4.6590 dB |
| shakuhachi-grave-5 | −43.3945 dB | 4.6990 dB |
| Ref. [5] | 33.7464 dB | 59.7989 dB |
| Ref. [8] | −16.0483 dB | 1.4524 dB |
| Ref. [27] | −133.0000 dB | - |
| AES [27] | −1.4461 dB | - |
| Audio File | File Size | File Length | Encryption Time |
|---|---|---|---|
| usb-headset-weird | 200 kb | 2.32 s | 0.865 s |
| cartoon-mumble-speak | 298.1 kb | 3.45 s | 1.284 s |
| grito-wav | 385.3 kb | 4.47 s | 1.676 s |
| a-strange-dream | 495 kb | 5.74 s | 2.188 s |
| radio | 691 kb | 8.02 s | 3.195 s |
| insult | 832 kb | 9.66 s | 3.691 s |
| sharpening-blade-long-blade | 1228.8 kb | 14.48 s | 5.651 s |
| airport-security-message | 1740.8 kb | 20.28 s | 8.193 s |
| shakuhachi-grave-5 | 2048 kb | 23.41 s | 8.831 s |
| Ref. [5] | - | 7 s | 0.012 s |
| Ref. [8] | 2.33 mb | 13.85 s | 5.767 s |
| AES [31] | 800 kb | - | 0.003 s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Stoyanov, B.; Ivanova, T. Novel Implementation of Audio Encryption Using Pseudorandom Byte Generator. Appl. Sci. 2021, 11, 10190. https://doi.org/10.3390/app112110190
Stoyanov B, Ivanova T. Novel Implementation of Audio Encryption Using Pseudorandom Byte Generator. Applied Sciences. 2021; 11(21):10190. https://doi.org/10.3390/app112110190
Chicago/Turabian StyleStoyanov, Borislav, and Tsvetelina Ivanova. 2021. "Novel Implementation of Audio Encryption Using Pseudorandom Byte Generator" Applied Sciences 11, no. 21: 10190. https://doi.org/10.3390/app112110190
APA StyleStoyanov, B., & Ivanova, T. (2021). Novel Implementation of Audio Encryption Using Pseudorandom Byte Generator. Applied Sciences, 11(21), 10190. https://doi.org/10.3390/app112110190







