Secure Outsourced Blockchain-Based Medical Data Sharing System Using Proxy Re-Encryption †
Abstract
:1. Introduction
- 1.
- We first propose a blockchain-based EHR management model. In each distributed ledger, the access information that reveals the user that can read the corresponding EHR and the hash value of the record are stored. Hence, only authorized users can download and retrieve the encrypted EHR;
- 2.
- In addition to the blockchain, we adopt a PRE scheme to enable secure and efficient EHR sharing. Moreover, the proxy is separated from the blockchain system, and the re-encryption key is generated and maintained by the system manager, not the outsourcing company. Hence, the company cannot open the encrypted EHRs;
- 3.
- We provide essential cyptography schemes to secure the EHRs, such as encryption/decryption and digital signature schemes. Hence, the confidentiality and integrity of the EHRs are guaranteed.
2. Related Works
2.1. Blockchain Implementations on Medical Data
2.2. Proxy Re-Encryption for Medical Data Using Blockchain
3. Preliminaries
3.1. Blockchain
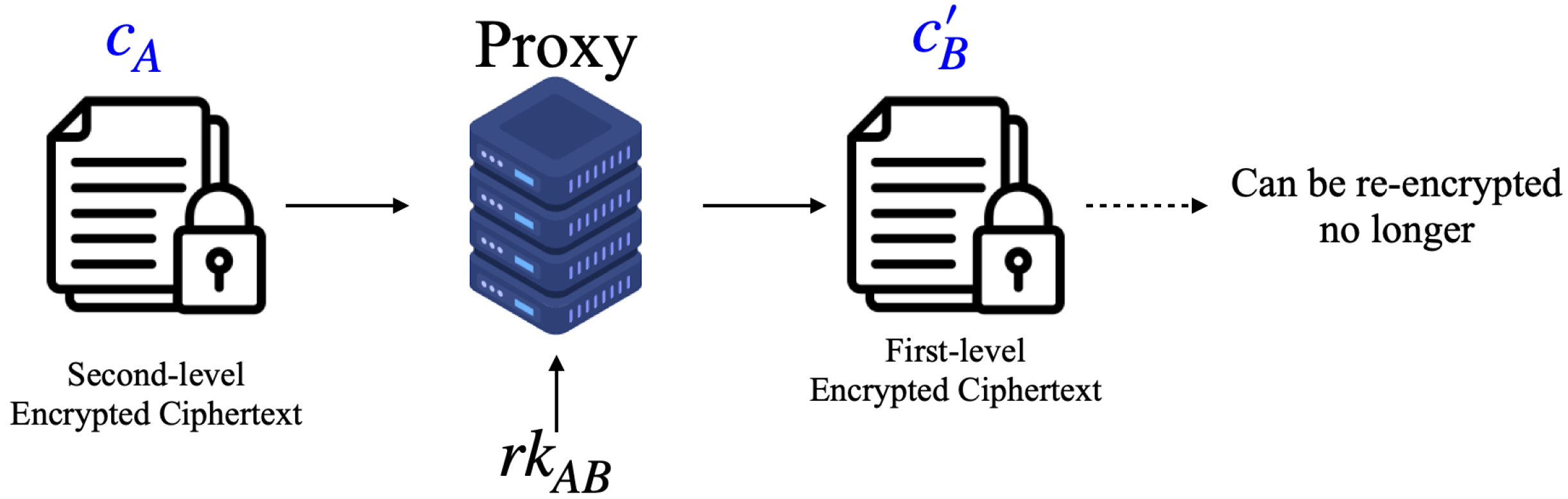
3.2. Proxy Re-Encryption
4. The Proposed Scheme
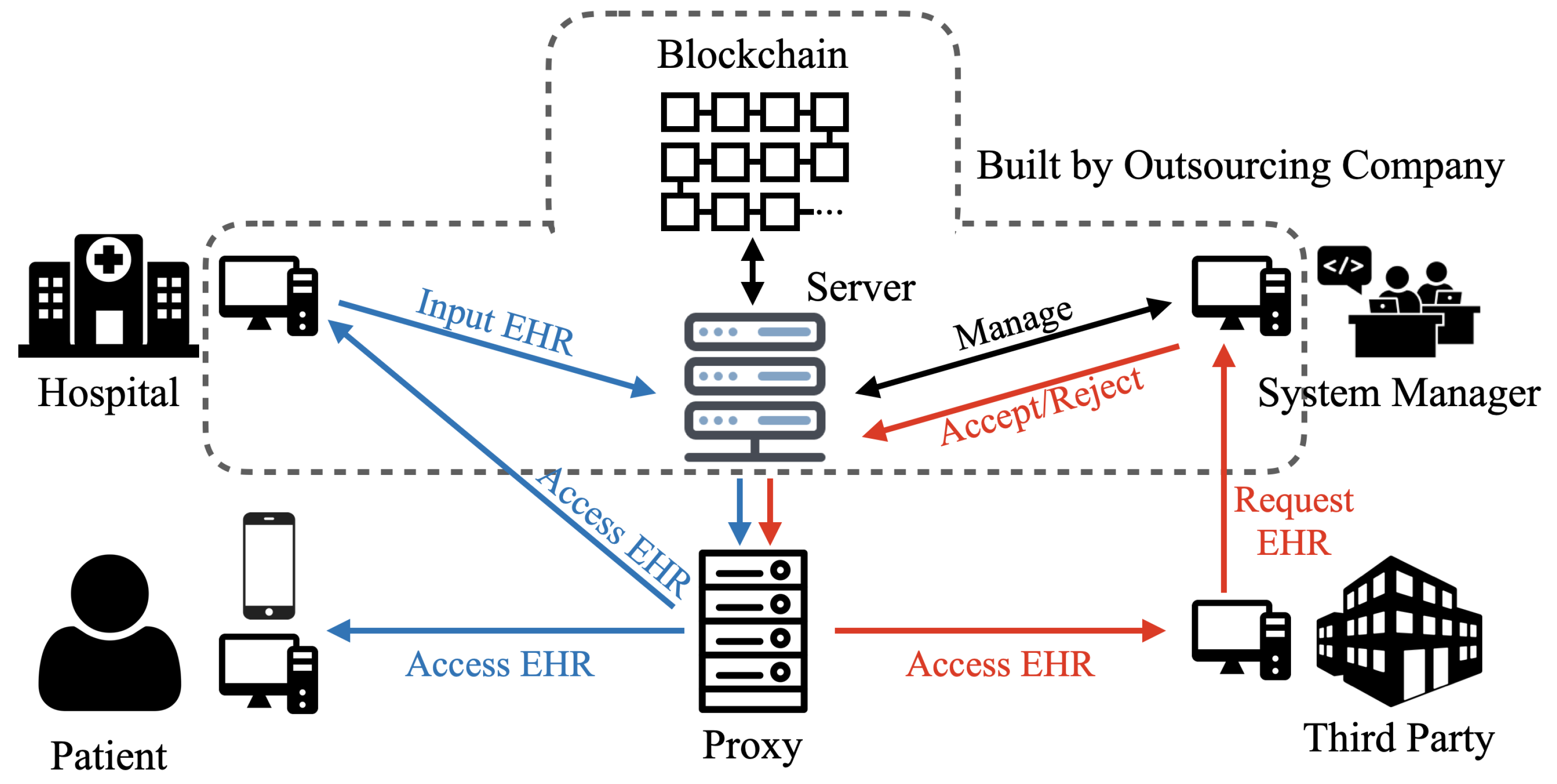
4.1. System Model
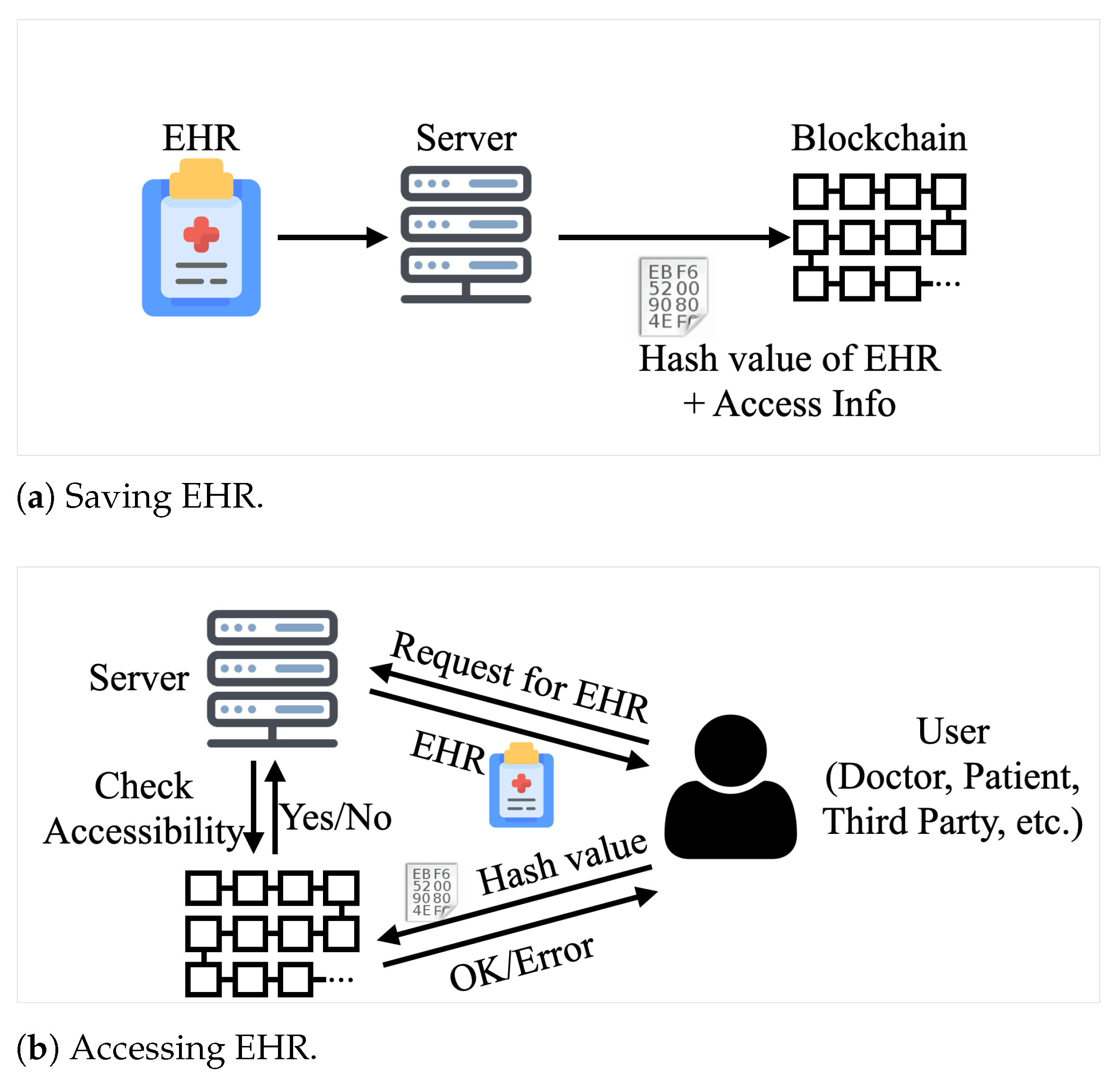
4.2. Blockchain in the System
4.3. The Re-Encryption Processes
4.3.1. System Initialization
- 1.
- The system manager selects two large primes p and q, where . Let the number of digits in q be , and let be a subgroup of with order q;
- 2.
- The manager selects four hash functions, , , , and . It is noteworthy that the security parameters and are determined by ;
- 3.
- The manager sets as .
4.3.2. User Registration
- 1.
- The system verifies the validity of user , who tries to register;
- 2.
- If the validity test is passed, then the system assigns to ;
- 3.
- User selects , and sets as ;
- 4.
- User calculates and , and sets public key as ;
- 5.
- User sends the public key to the system manager.
4.3.3. Data Storage
- 1.
- User signs M with one’s private key. Let S be ’s digital signature on M;
- 2.
- To encrypt both the message and the signature, user randomly creates a symmetric key K for the AES and encrypts with K. Let be the encrypted data, i.e., . In the next step, the second-level encryption of the PRE begins;
- 3.
- To encrypt K, user selects and randomly, and computes ;
- 4.
- User calculates the following:
- 5.
- The user computes , outputs the ciphertext , and sends and to the server;
- 6.
- After the server receives and , it verifies if the following equation holds:If it does not hold, then the server rejects ;
- 7.
- The server finally stores , and writes the access information on the blockchain.
4.3.4. Data Retrieval by System Manager
- 1.
- The system manager requests the server to send the encrypted data and the encrypted key . Let be ;
- 2.
- The manager calculates . If no problem arises, then the result is two concatenated values; the first is the symmetric key K, and the second one is ;
- 3.
- The manager verifies whether is established. If it is not established, then the manager rejects and , and terminates the process;
- 4.
- The manager decrypts with K using the AES decryption algorithm. Subsequently, the manager obtains the original data M and its signature S;
- 5.
- The manager verifies the integrity of M via a verification procedure using the signature S. If the verification process is completed successfully, then data retrieval is terminated.
4.3.5. Data Sharing to a Third Party
- 1.
- When the server receives a request to access the stored EHR from the third party , the server verifies ’s accessibility from the blockchain. If does not have the right to access the EHR, then the server rejects ;
- 2.
- The server obtains the requested pair of the encrypted data and symmetric key , and sends to the third party and to the proxy server;
- 3.
- When the proxy server receives , it finds from its storage;
- 4.
- The proxy server calculates and sends to the third party.
4.3.6. Data Retrieval by a Third Party
- 1.
- The third party calculates . The following result can be obtained if no problem arises:
- 2.
- Using the result of Step 1, the third party derives K by calculating . If no problem arises, the following result can be obtained:
- 3.
- The third party verifies whether and hold. If they do not hold, then the third party rejects the received data and requests them again from the server;
- 4.
- Using the decrypted symmetric key K, the third party decrypts using the AES decryption scheme. Subsequently, is obtained, where M is the plaintext of the requested EHR, and S is its signature;
- 5.
- Finally, the third party verifies the integrity of M via the process to verify the digital signature using S. If the verification is successful, then the third party accepts M and terminates the process.
4.4. Data Management Processes
5. Discussion
5.1. Security Analysis
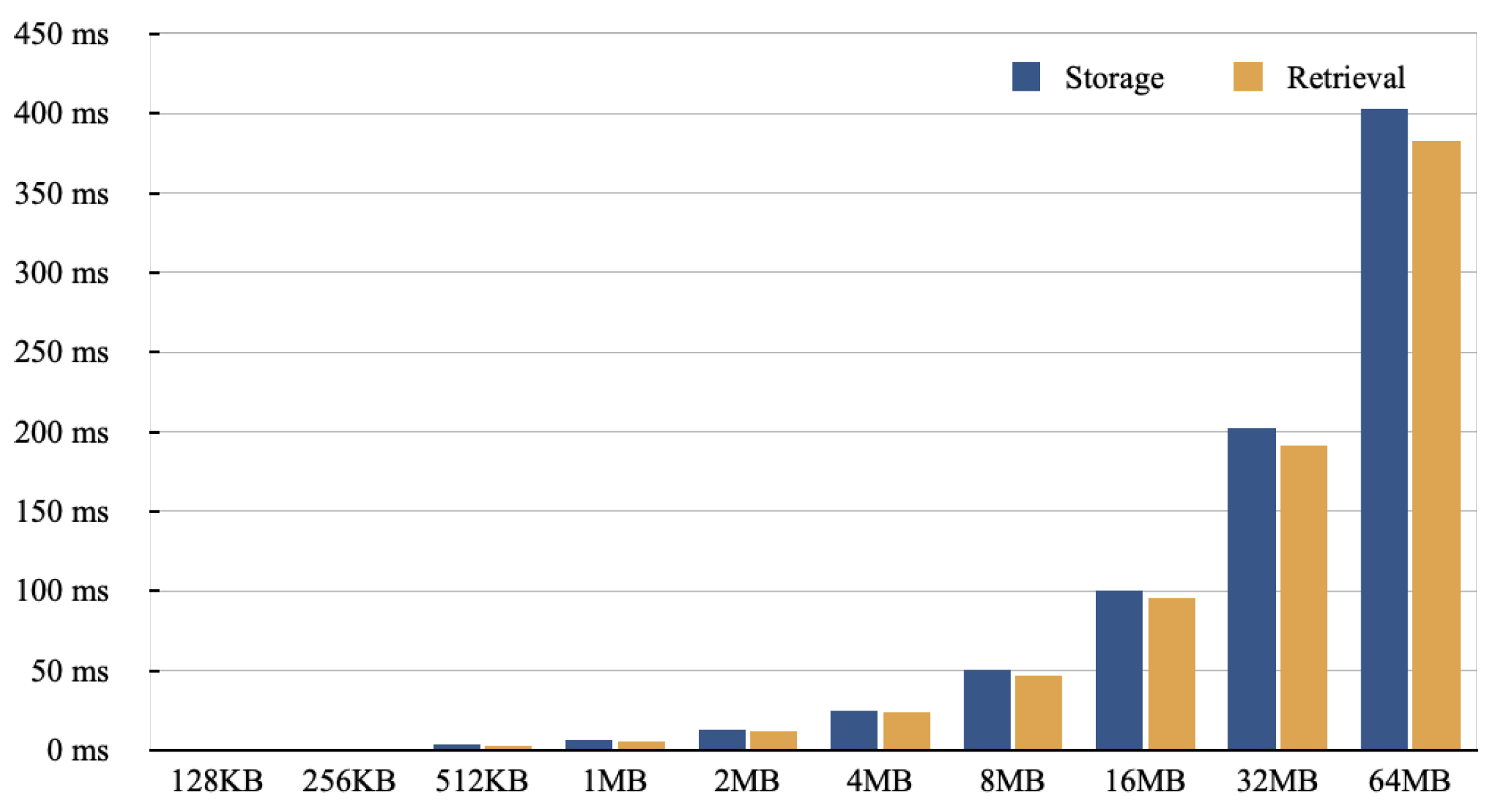
5.2. Experimental Results
6. Conclusions and Future Works
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Chen, H.Y.; Wu, Z.Y.; Chen, T.L.; Huang, Y.M.; Liu, C.H. Security Privacy and Policy for Cryptographic Based Electronic Medical Information System. Sensors 2021, 21, 713. [Google Scholar] [CrossRef] [PubMed]
- Sharma, S.; Chen, K.; Sheth, A. Toward Practical Privacy-Preserving Analytics for IoT and Cloud-Based Healthcare Systems. IEEE Internet Comput. 2018, 22, 42–51. [Google Scholar] [CrossRef] [Green Version]
- Abbas, A.; Khan, S.U. A Review on the State-of-the-Art Privacy-Preserving Approaches in the e-Health Clouds. IEEE J. Biomed. Health Inform. 2014, 18, 1431–1441. [Google Scholar] [CrossRef] [PubMed]
- Jin, H.; Luo, Y.; Li, P.; Mathew, J. A Review of Secure and Privacy-Preserving Medical Data Sharing. IEEE Access 2019, 7, 61656–61669. [Google Scholar] [CrossRef]
- Zyskind, G.; Nathan, O.; Pentland, A.S. Decentralizing Privacy: Using Blockchain to Protect Personal Data. In Proceedings of the 2015 IEEE Security and Privacy Workshops, San Jose, CA, USA, 21–22 May 2015; pp. 180–184. [Google Scholar] [CrossRef]
- Zhang, J.; Sun, J.; Yang, Y.; Liang, C.; Yao, Y.; Cai, W.; Jin, J.; Zhang, G.; Sun, K. Image-Based Electronic Patient Records for Secured Collaborative Medical Applications. In Proceedings of the 2005 IEEE Engineering in Medicine and Biology 27th Annual Conference, Shanghai, China, 17–18 January 2006; pp. 3218–3220. [Google Scholar] [CrossRef]
- Lee, J.P.; Kim, Y.H.; Lee, J.K. SSL Application for Managed Security between the Mobile and HIS Biometric Information Collection Client. In Proceedings of the 2014 28th International Conference on Advanced Information Networking and Applications Workshops, Victoria, BC, Canada, 13–16 May 2014; pp. 55–60. [Google Scholar] [CrossRef]
- Park, Y.H.; Je, D.H.; Park, M.H.; Seo, S.W. Efficient Rekeying Framework for Secure Multicast with Diverse-Subscription-Period Mobile Users. IEEE Trans. Mob. Comput. 2014, 13, 783–796. [Google Scholar] [CrossRef]
- Korzun, D.G. Internet of Things Meets Mobile Health Systems in Smart Spaces: An Overview. In Internet of Things and Big Data Technologies for Next Generation Healthcare; Bhatt, C., Dey, N., Ashour, A.S., Eds.; Springer International Publishing: Cham, Switzerland, 2017; pp. 111–129. [Google Scholar] [CrossRef]
- Korzun, D.; Meigal, A. Multi-Source Data Sensing in Mobile Personalized Healthcare Systems: Semantic Linking and Data Mining. In Proceedings of the 2019 24th Conference of Open Innovations Association (FRUCT), Moscow, Russia, 8–12 April 2019; pp. 187–192. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Technical Report. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 9 October 2021).
- Wood, G. Ethereum: A secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 2014, 151, 1–32. [Google Scholar]
- Piedrahita Castillo, D.; Regidor, F.M.; Higuera, J.B.; Higuera, J.R.B.; Montalvo, J.A.S. A New Mail System for Secure Data Transmission in Cyber Physical Systems. Int. J. Uncertain. Fuzziness Knowl.-Based Syst. 2020, 28, 23–48. [Google Scholar] [CrossRef]
- Sharma, A.; Sarishma; Tomar, R.; Chilamkurti, N.; Kim, B.G. Blockchain Based Smart Contracts for Internet of Medical Things in e-Healthcare. Electronics 2020, 9, 1609. [Google Scholar] [CrossRef]
- Agbo, C.C.; Mahmoud, Q.H.; Eklund, J.M. Blockchain Technology in Healthcare: A Systematic Review. Healthcare 2019, 7, 56. [Google Scholar] [CrossRef] [Green Version]
- Azaria, A.; Ekblaw, A.; Vieira, T.; Lippman, A. MedRec: Using Blockchain for Medical Data Access and Permission Management. In Proceedings of the 2016 2nd International Conference on Open and Big Data (OBD), Vienna, Austria, 22–24 August 2016; pp. 25–30. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Asamoah, K.O.; Gao, J.; Du, X.; Guizani, M. MeDShare: Trust-Less Medical Data Sharing among Cloud Service Providers via Blockchain. IEEE Access 2017, 5, 14757–14767. [Google Scholar] [CrossRef]
- Yang, H.; Yang, B. A Blockchain-Based Approach to the Secure Sharing of Healthcare Data. In Proceedings of the Norwegian Information Security Conference 2017 (NISK2017), Oslo, Norway, 27–29 November 2017; pp. 100–111. [Google Scholar]
- Xia, Q.; Sifah, E.B.; Smahi, A.; Amofa, S.; Zhang, X. BBDS: Blockchain-Based Data Sharing for Electronic Medical Records in Cloud Environments. Information 2017, 8, 44. [Google Scholar] [CrossRef]
- Li, M.; Yu, S.; Zheng, Y.; Ren, K.; Lou, W. Scalable and Secure Sharing of Personal Health Records in Cloud Computing Using Attribute-Based Encryption. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 131–143. [Google Scholar] [CrossRef] [Green Version]
- Liu, J.; Huang, X.; Liu, J.K. Secure sharing of Personal Health Records in cloud computing: Ciphertext-Policy Attribute-Based Signcryption. Future Gener. Comput. Syst. 2015, 52, 67–76. [Google Scholar] [CrossRef]
- Li, F.; Liu, K.; Zhang, L.; Huang, S.; Wu, Q. EHRChain: A Blockchain-based EHR System Using Attribute-Based and Homomorphic Cryptosystem. IEEE Trans. Serv. Comput. 2021, 1. [Google Scholar] [CrossRef]
- Fu, J.; Wang, N.; Cai, Y. Privacy-Preserving in Healthcare Blockchain Systems Based on Lightweight Message Sharing. Sensors 2020, 20, 1898. [Google Scholar] [CrossRef] [Green Version]
- Hao, K.; Xin, J.; Wang, Z.; Cao, K.; Wang, G. Blockchain-Based Outsourced Storage Schema in Untrusted Environment. IEEE Access 2019, 7, 122707–122721. [Google Scholar] [CrossRef]
- Yang, Y.; Zheng, X.; Guo, W.; Liu, X.; Chang, V. Privacy-preserving smart IoT-based healthcare big data storage and self-adaptive access control system. Inf. Sci. 2019, 479, 567–592. [Google Scholar] [CrossRef]
- Blaze, M.; Bleumer, G.; Strauss, M. Divertible protocols and atomic proxy cryptography. In Advances in Cryptology—EUROCRYPT’98, Proceedings of the International Conference on the Theory and Application of Cryptographic Techniques Espoo, Finland, 31 May–4 June 1998; Nyberg, K., Ed.; Springer: Berlin/Heidelberg, Germany, 1998; pp. 127–144. [Google Scholar]
- Lin, H.Y.; Jiang, Y.R. A Multi-User Ciphertext Policy Attribute-Based Encryption Scheme with Keyword Search for Medical Cloud System. Appl. Sci. 2021, 11, 63. [Google Scholar] [CrossRef]
- Chow, S.S.M.; Weng, J.; Yang, Y.; Deng, R.H. Efficient Unidirectional Proxy Re-Encryption. In Progress in Cryptology—AFRICACRYPT 2010, Proceedings of the International Conference on Cryptology in Africa, Stellenbosch, South Africa, 3–6 May 2010; Bernstein, D.J., Lange, T., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 316–332. [Google Scholar]
- Lee, S.O.; Ko, K.; Park, Y.H. Blockchain-based Medical Data Management System Using Proxy Re-encryption. In Proceedings of the International Conference on Green and Human Information Technology 2021 (ICGHIT 2021), Jeju Island, Korea, 13–15 January 2021. [Google Scholar]
- Chelladurai, M.U.; Pandian, D.S.; Ramasamy, D.K. A blockchain based patient centric electronic health record storage and integrity management for e-Health systems. Health Policy Technol. 2021, 100513. [Google Scholar] [CrossRef]
- Dubovitskaya, A.; Xu, Z.; Ryu, S.; Schumacher, M.; Wang, F. Secure and trustable electronic medical records sharing using blockchain. AMIA Annu. Symp. Proc. 2017, 2017, 650. [Google Scholar]
- Yang, X.; Li, T.; Pei, X.; Wen, L.; Wang, C. Medical Data Sharing Scheme Based on Attribute Cryptosystem and Blockchain Technology. IEEE Access 2020, 8, 45468–45476. [Google Scholar] [CrossRef]
- Wang, Y.; Zhang, A.; Zhang, P.; Wang, H. Cloud-assisted EHR sharing with security and privacy preservation via consortium blockchain. IEEE Access 2019, 7, 136704–136719. [Google Scholar] [CrossRef]
- Yang, M.; Margheri, A.; Hu, R.; Sassone, V. Differentially private data sharing in a cloud federation with blockchain. IEEE Cloud Comput. 2018, 5, 69–79. [Google Scholar] [CrossRef] [Green Version]
- Liu, X.; Wang, Z.; Jin, C.; Li, F.; Li, G. A blockchain-based medical data sharing and protection scheme. IEEE Access 2019, 7, 118943–118953. [Google Scholar] [CrossRef]
- Thwin, T.T.; Vasupongayya, S. Blockchain based secret-data sharing model for personal health record system. In Proceedings of the 2018 5th International Conference on Advanced Informatics: Concept Theory and Applications (ICAICTA), Krabi, Thailand, 14–17 August 2018; pp. 196–201. [Google Scholar]
- Thwin, T.T.; Vasupongayya, S. Blockchain-based access control model to preserve privacy for personal health record systems. Secur. Commun. Netw. 2019, 2019, 8315614. [Google Scholar] [CrossRef]
- Dagher, G.G.; Mohler, J.; Milojkovic, M.; Marella, P.B. Ancile: Privacy-preserving framework for access control and interoperability of electronic health records using blockchain technology. Sustain. Cities Soc. 2018, 39, 283–297. [Google Scholar] [CrossRef]
- Gao, J.; Asamoah, K.O.; Sifah, E.B.; Smahi, A.; Xia, Q.; Xia, H.; Zhang, X.; Dong, G. Gridmonitoring: Secured sovereign blockchain based monitoring on smart grid. IEEE Access 2018, 6, 9917–9925. [Google Scholar] [CrossRef]
- Xia, Q.; Sifah, E.B.; Huang, K.; Chen, R.; Du, X.; Gao, J. Secure Payment Routing Protocol for Economic Systems Based on Blockchain. In Proceedings of the 2018 International Conference on Computing, Networking and Communications (ICNC), Maui, HI, USA, 5–8 March 2018; pp. 177–181. [Google Scholar]
- Lin, I.C.; Liao, T.C. A survey of blockchain security issues and challenges. Int. J. Netw. Secur. 2017, 19, 653–659. [Google Scholar]
- Zhang, Y.; Xu, C.; Lin, X.; Shen, X.S. Blockchain-based public integrity verification for cloud storage against procrastinating auditors. IEEE Trans. Cloud Comput. 2019, 9, 923–937. [Google Scholar] [CrossRef] [Green Version]
- Mohanta, B.K.; Panda, S.S.; Jena, D. An overview of smart contract and use cases in blockchain technology. In Proceedings of the 2018 9th International Conference on Computing, Communication and Networking Technologies (ICCCNT), Bengaluru, India, 10–12 July 2018; pp. 1–4. [Google Scholar]
- Bahga, A.; Madisetti, V.K. Blockchain platform for industrial internet of things. J. Softw. Eng. Appl. 2016, 9, 533–546. [Google Scholar] [CrossRef] [Green Version]
- Mambo, M.; Usuda, K.; Okamoto, E. Proxy Signatures for Delegating Signing Operation. In Proceedings of the 3rd ACM Conference on Computer and Communications Security, CCS ’96, New Delhi, India, 14–16 March 1996; Association for Computing Machinery: New York, NY, USA, 1996; pp. 48–57. [Google Scholar] [CrossRef]
- Zhou, L.; Marsh, M.; Schneider, F.; Redz, A. Distributed Blinding for Distributed ElGamal Re-Encryption. In Proceedings of the 25th IEEE International Conference on Distributed Computing Systems (ICDCS’05), Columbus, OH, USA, 6–10 June 2005; p. 824. [Google Scholar] [CrossRef] [Green Version]
- Canetti, R.; Hohenberger, S. Chosen-Ciphertext Secure Proxy Re-Encryption. In Proceedings of the 14th ACM Conference on Computer and Communications Security, CCS ’07, Alexandria, VA, USA, 29 October–2 November 2014; Association for Computing Machinery: New York, NY, USA, 2007; pp. 185–194. [Google Scholar] [CrossRef] [Green Version]
- Applied Cryptography Group PBC Library—Pairing-Based Cryptography. Available online: https://crypto.stanford.edu/pbc/ (accessed on 9 October 2021).


| Symbols | Meaning |
|---|---|
| , , | Security parameters |
| p and q | Large primes satisfy , where length of q is |
| Subgroup of | |
| , , , and | Hash functions |
| Generator | |
| , | Manager’s private and public keys |
| , | User ’s private and public keys |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Park, Y.-H.; Kim, Y.; Lee, S.-O.; Ko, K. Secure Outsourced Blockchain-Based Medical Data Sharing System Using Proxy Re-Encryption. Appl. Sci. 2021, 11, 9422. https://doi.org/10.3390/app11209422
Park Y-H, Kim Y, Lee S-O, Ko K. Secure Outsourced Blockchain-Based Medical Data Sharing System Using Proxy Re-Encryption. Applied Sciences. 2021; 11(20):9422. https://doi.org/10.3390/app11209422
Chicago/Turabian StylePark, Young-Hoon, Yejin Kim, Shin-Ok Lee, and Kwangman Ko. 2021. "Secure Outsourced Blockchain-Based Medical Data Sharing System Using Proxy Re-Encryption" Applied Sciences 11, no. 20: 9422. https://doi.org/10.3390/app11209422
APA StylePark, Y.-H., Kim, Y., Lee, S.-O., & Ko, K. (2021). Secure Outsourced Blockchain-Based Medical Data Sharing System Using Proxy Re-Encryption. Applied Sciences, 11(20), 9422. https://doi.org/10.3390/app11209422







