A Review on Security of Smart Farming and Precision Agriculture: Security Aspects, Attacks, Threats and Countermeasures
Abstract
1. Introduction
- We itemize the security aspects of SF and PA and establish a map between attacks and security aspects.
- We use CKC [37] for the first time to present a systematic taxonomy on cyber-threats to SF and PA.
- We study the anatomy as well as the behavioral characteristics of APT.
- Finally, we develop a future road map to highlight some related emerging areas that still need to be studied in future research.
2. Existing Reviews
3. Cyber-Attacks on SF and PA
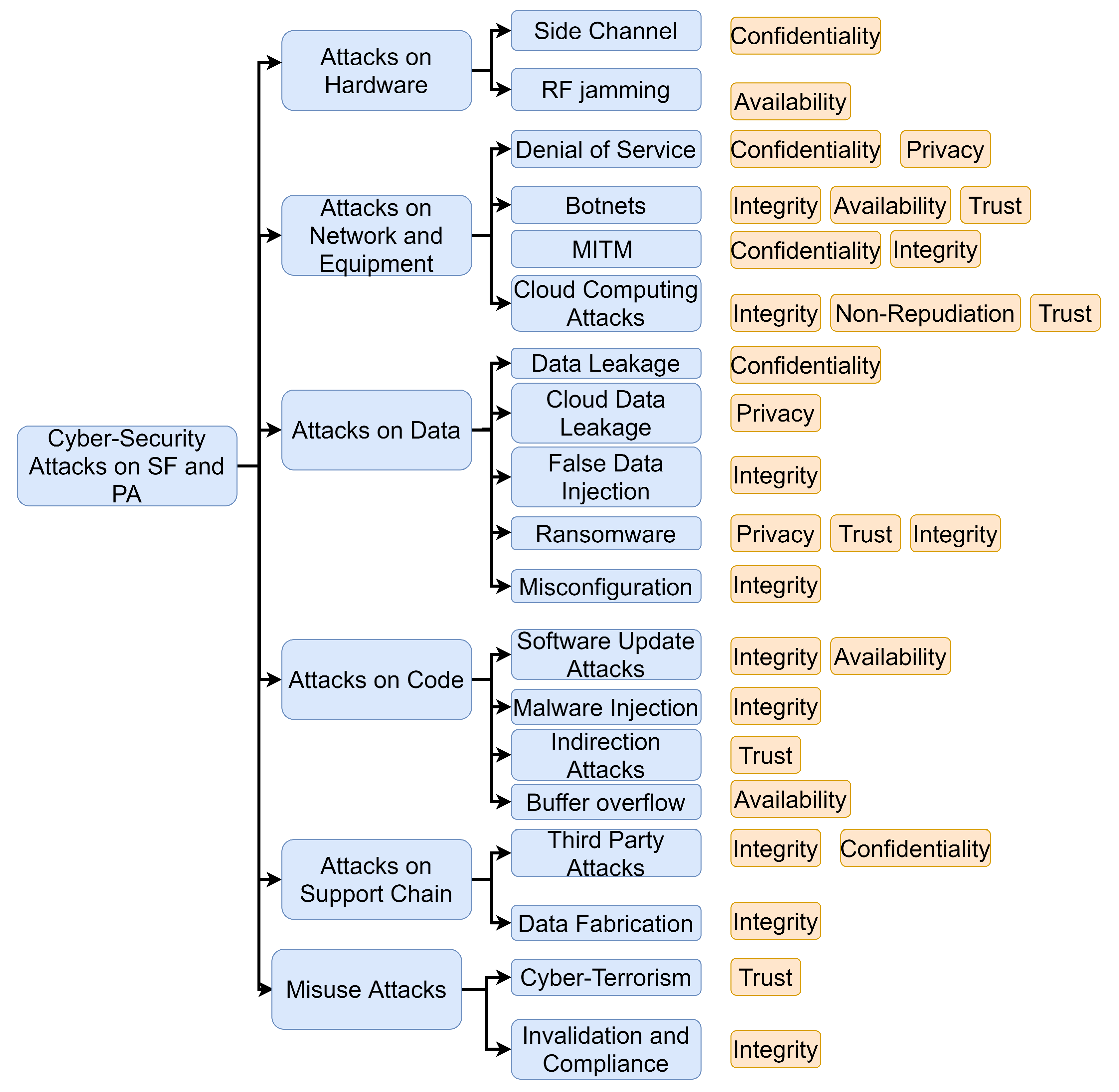
- Integrity: guarantees information not to be changed during storage or transmission. Integrity of PA and SF has been part of the topic in several research projects [62].
- Availability guarantees the continuity of the provided services. Some recent research works have focused on the availability of SF and PA [64].
- Non-Repudiation keeps users from repudiating what they have done in the system. The importance of non-repudiation in SF and PA has received attention form a few researchers [65].
- Trust: makes it impossible for a user to spoof another identity. The literature in this area comes with a few research projects focusing on authenticity of SF and PA [65].
- Attacks on Hardware: Unknown or unprotected vulnerabilities of IoT and cyber-physical devices (as well as other hardware components) may be exploited by professional attackers using specialised tools [66]. As good examples for this kind of attacks, we may refer to side channel and Radio frequency (RF) jamming attacks, which can violate privacy, confidentiality, or authenticity when they hit poorly-designed IoT and cyber-physical systems [2,66,67,68].
- -
- -
- Attacks on the Network and Related Equipment: target the network or the connected devices. This category of attacks can be further categorized as follows.
- -
- Denial of Service (DoS) [70,71] prevents users or devices from their authorized access to a resource such as a node, a server, or a communication link/network. For example, Radio Frequency (RF) Jamming [2,72] overwhelms the RF spectrum used by a network aiming to deny communication services to the connected nodes.
- -
- -
- Botnets [2,73,74] are groups of Internet-connected devices (remote sensors), each running one bot or more. Botnets can be used for many different purposes, including Distributed DoS (DDoS) attacks, information stealing, SPAM dissemination. They can be designed to violate availability, integrity, or trust.
- -
- Cloud Computing Attacks [2] misuse cloud features such as self-provisioning, on-demand services and auto-scaling to take advantage of cloud resources. For instance, an infected virtual machine can quickly spread the infecting malware to other virtual machines via the cloud. These attacks may target non-repudiation, trust, or integrity.
- Attacks on Data: hit the data while being stored, transmitted, or processed in the system. This category of attacks can be divided into the following subcategories [75].
- -
- -
- -
- -
- -
- Misconfiguration [2] is the action of configuring the SF or the PA reporting systems in a way that reflects invalid information regarding the managed farm, which can lead to costly, disruptive decisions and actions from the farmers. Misconfiguration attacks violate the integrity.
- Attacks on Code (applications):
- -
- Software Update Attacks [2] violate the integrity and the availability of the system via disrupting the update process of the installed software.
- -
- -
- -
- Attacks on Support Chain: are designed to hit different components of the support chain.
- -
- -
- Data Fabrication [82] involves the creation of malicious data or processes misusing an access provided for another purpose. It can lead to the violation of the system’s integrity.
- Misuse Attacks: include attacks that misuse SF and PA physical resources in order to conduct attacks on other entities such as people or institutes.
- -
- Cyber-Terrorism [2] may use IoT systems and cyber-physical devices to attack people or premises from afar. This can lead to the violation of trust in SF and PA systems.
- -
4. CKC-Based Taxonomy on Security Threats to SF and PA
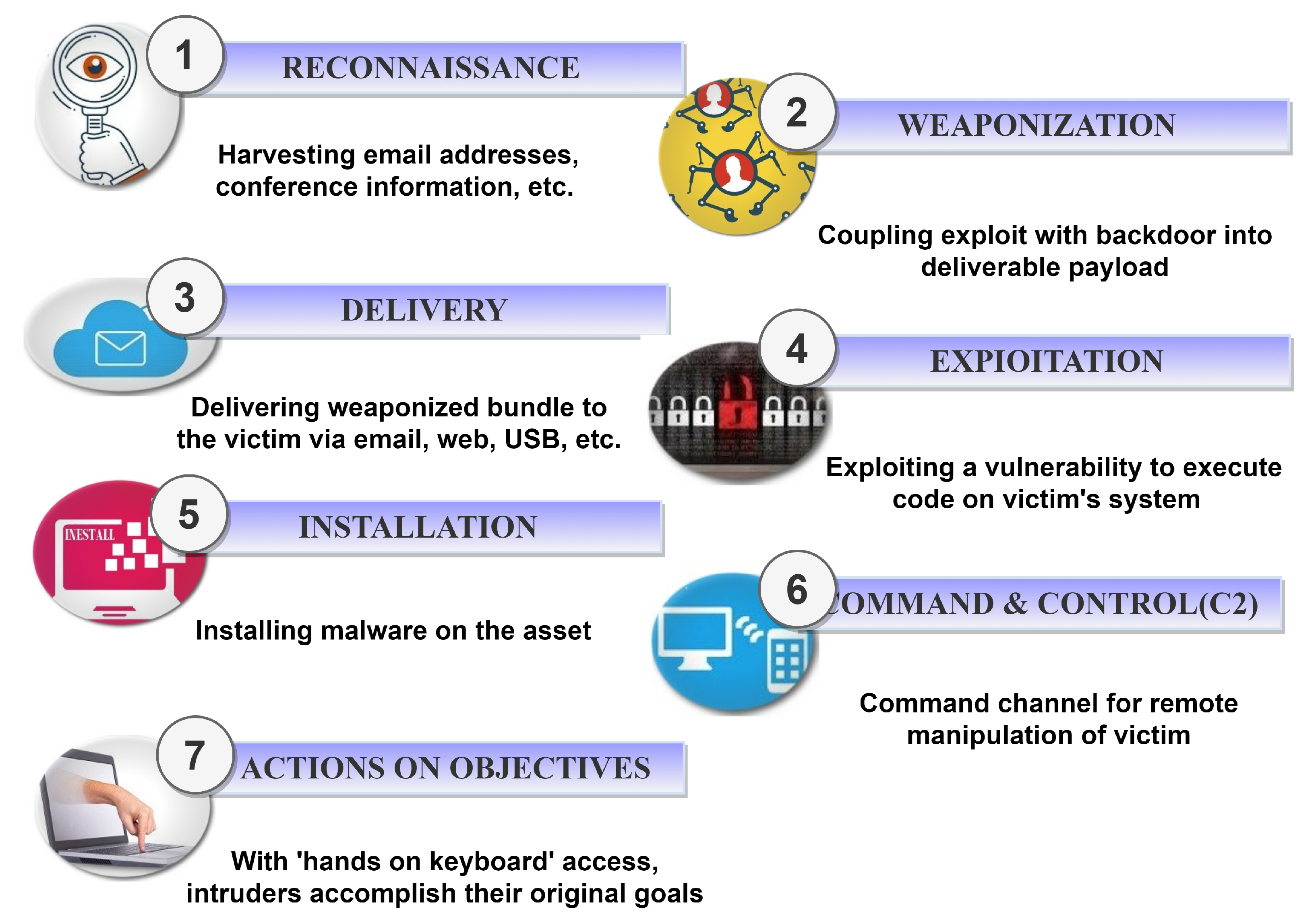
4.1. CKC
- Reconnaissance, where the attacker starts to identify and profile the victim via gathering as much information as possible. Any relevant information, such as email addresses, can be of interest in the reconnaissance stage. The primary goal of this stage is to discover the vulnerabilities of the victim. If properly accomplished, this stage can facilitate and accelerate a cyber-attack and make it difficult to detect via identifying the weak and strong points of the victim system. Moreover, the reconnaissance itself should not be suspicious to security mechanisms in the victim’s system. We can consider a passive and active approach for Reconnaissance. In the context of a cyberattack, passive Reconnaissance is known as footprinting. Active Reconnaissance is commonly referred to as scanning. An easy scan would be to ping every IP address owned by the destination network to see which ones went to real hosts. More sophisticated exploitation methods connect to every port number of the IP address to determine what services run on that host and which ports are open. In contrast to footprinting, scanning provides more specific information but is more intrusive. Additionally, the target may be alerted to a potential attack since scanning can trigger more abnormal connections, which must be avoided when scanning.
- Weaponization, wherein the attacker designs and implements the remote access malware (the weapon) e.g., the backdoor, virus or worm tailored to the vulnerabilities of the victim (discovered in the reconnaissance phase).
- Delivery, in which the attacker launches the remote access malware onto the victim (e.g., via a USB device, an e-mail attachment or a website).
- Exploitation, which triggers the remote access malware. In this stage, the attacker utilizes the remote access malware to action on the victim and the related network in order to exploit vulnerability.
- Installation, where the attacker tries to get permanent access to the victim via installing proper Command and Control (C2) servers.
- C2, wherein the attacker communicates with the C2 server in order to control the victim.
- Action on Target, where the attacker completes the attack scenario and achieves the final goal by compromising the victim.
4.2. The Taxonomy
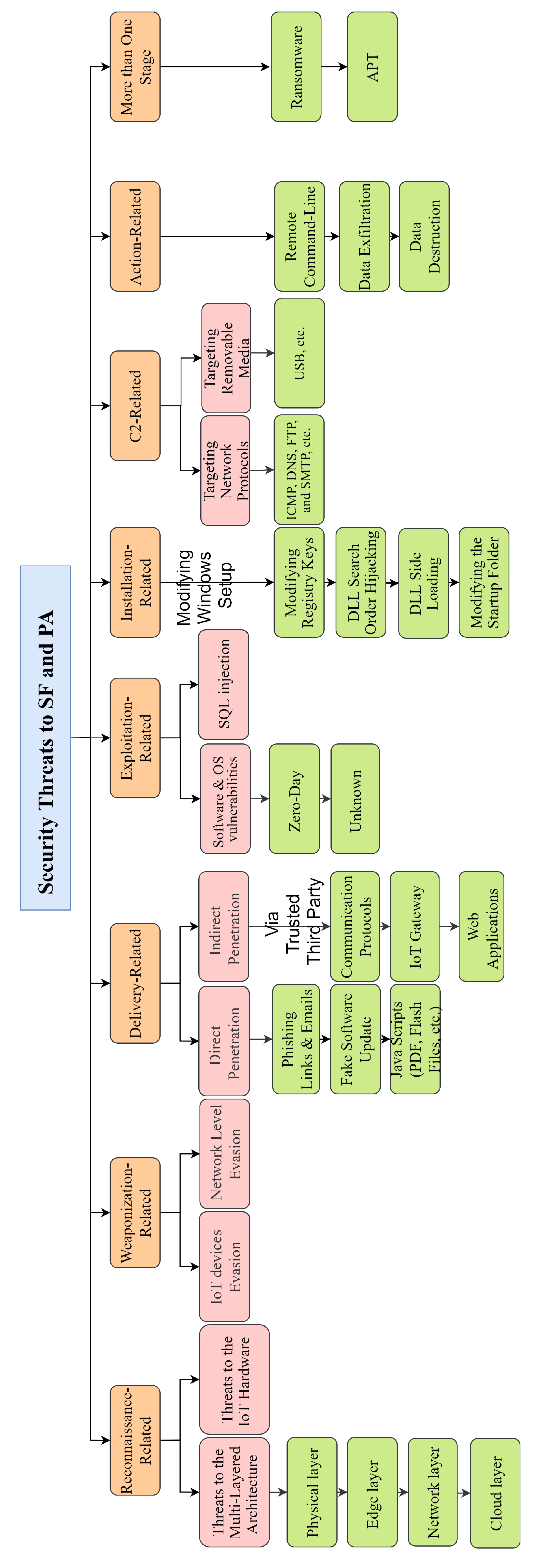
4.2.1. Threats Related to the Reconnaissance Stage
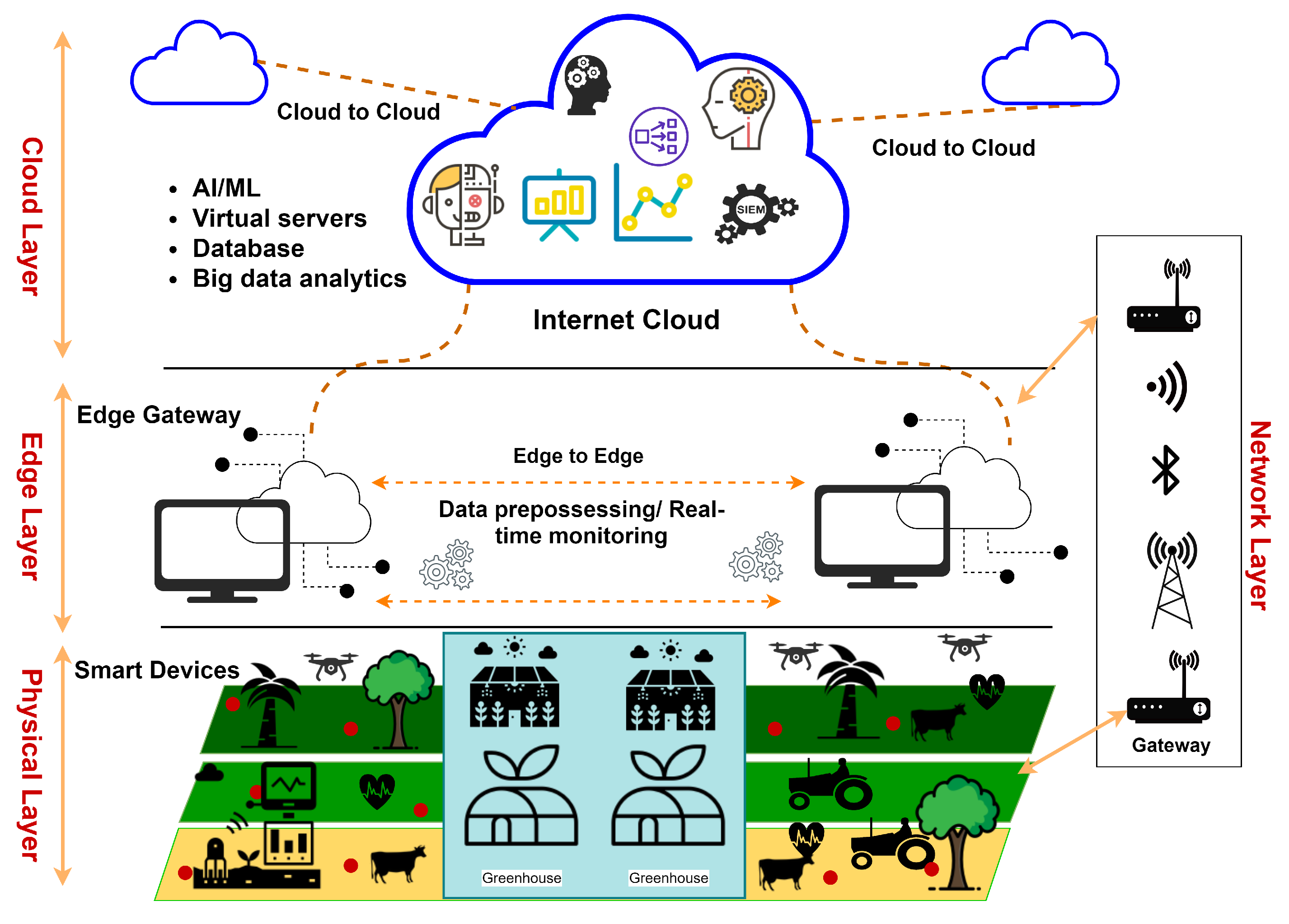
- Threats to the multi-layer architecture: These threats target different layers of the multi-layered architecture of Figure 1 as explained below.
- -
- -
- Edge Layer: SF and PA environments rely on the edge layer devices for their real-time or near real-time computations and services. In some scenarios, attackers may be able to shutdown the function of these devices, causing disruption, delay, customer dissatisfaction, and financial loss [2].
- -
- -
4.2.2. Threats Related to the Weaponization Stage
- IoT Device Level Evasion: It has been observed that defence in IoT device level mainly relies on anti-viruses and end-point security solutions embedded in or installed on devices, which detect well-known virus signatures or anomalies in behaviors. Well-designed attacks on SF and PA try to hide themselves from these mechanisms. As an example, one may refer to hollowing technique or heap spraying, which may successfully embed a malicious code inside an application even in the case the anti-virus includes the related signature [90,91,92,93].
- Network Level Evasion: Firewalls and Intrusion Detection/Prevention Systems (IDSs/IPSs) are the most common tools for in-network protection [94,95]. A key point to be reiterated here is that there is no completely secure solution, including firewalls and IDS/IPS. Although these tools can detect a malicious executable file, they may be unable to detect a malicious file attached to an email. Thus, they are not considered as completely-secure mechanisms in SF and PA. To evade these mechanisms, SF and PA attacks depend on a wide range of techniques, among which we can mention illegal use of well-known protocols (HTTPS, DNS, HTTP, etc.) [37] or ports (53, 80, 443, etc.) [37] as well as network spoofing [89].
4.2.3. Threats Related to the Delivery Stage
- Indirect Penetration: In the indirection penetration scenario, a communication protocol, a gateway or a web application may play the role of the trusted third party. Trusted third parties can help attackers gather information via TCP/UDP port scan, spoofing and sniffing, or launch a pre-designed backdoor [1,3].
4.2.4. Threats Related to the Exploitation Stage
- Exploiting Software and OS Vulnerabilities: Zero-day exploits are good examples for this kind of threat [103]. They are not detectable by common software vulnerability protection mechanisms. They exploit unknown software vulnerabilities for which no patch or fix is available. Moreover, viruses, worms, Trojan horses, and backdoors are common threats related to OS vulnerabilities in smart devices and consequently in SF and PA [104,105].
- SQL injection: In recent years, SQL injection has frequently hit data-driven applications using code injection techniques [37]. It can potentially hit SF and PA databases as well.
4.2.5. Threats Related to the Installation Stage
- Modifying registry keys [111]
- DLL Search Order Hijacking [112]
- DLL side loading [113]
- Startup Folder Modification [37]
4.2.6. Threats Related to the C2 Stage
- C2s using Network Protocols: Many common attacks on SF and PA use HTTP/HTTPS, ICMP, DNS, FTP, SMTP and other standard network protocols for their communications in the C2 stage [119,120]. For example, in many scenarios, when direct connection to an external mail server or an agriculture database server is not possible, hackers rely on backdoors that use protocols such as FTP or SMTP to penetrate into the server via sending files or emails [37,101]. Moreover, to bypass common network security mechanisms, hackers may perturb DNS packets, which makes the attack more difficult to trace [121].
- C2s using Removable Media: Given the features of removable media (such as USB storage), they are commonly used to bypass networks for the exfiltration of data. For example, when a disk is formatted for decreasing the size of a partition, hundreds of megabytes of data (including malicious files) can be stored at the last addresses of the disk without being lost [37].
4.2.7. Threats Related to the Action Stage
4.2.8. Threats Related to More Than One Stage
4.3. Case Study
4.3.1. The Target Environment
4.3.2. Anatomy of the Attack
Reconnaissance:
Weaponization:
Delivery:
Exploitation:
Installation:
C2:
Action on Target:
5. APTs in SF and PA
5.1. An Introduction to APT Attacks
5.2. APT Attacks on SF and PA
- Theft of IP (patents, etc.)
- Stealth of critical data related to food chain, control, genetics, etc.
- Damage to important agricultural infrastructure (change to database entries or control parameters)
The Anatomy of an APT Attack on SF or PA
- Penetration (Infiltration):This step can be mapped to the first three stages in CKC. Social engineering can be mentioned as a common reconnaissance technique used in this step [129]. This phase may involve vulnerability exploiting and malicious code uploading (SQL Injection). Penetration may lead to the installation of backdoors, which can provide the attacker with further access to the network.This step is composed of the following phases.
- Testing the target for detection
- Deployment
- White noise attack
- Initial infiltration
- Outbound connection initiation
- Further Access (Expansion):This step may be mapped stages 4 through 6 in CKC. In this step, the attacker tries to gain longer access to the network or access to more strategic resources. The goal is getting control of critical functions and manipulating them to pave the way for the final step. This step is composed of the following phases. The following two functions can be run in this step.
- Expanding access and stealing credentials using phishing and similar techniques
- Broadening the presence
- Information Stealth and Sabotage (Exploitation):We can compare the final step to the last stage in CKC. In this step, APT groups may steal valuable information, shut down a strategic function, or cause damage to the system.Critical business information regarding the production value or cultivation process of livestock or crops may be of interest to APT groups in this step. These kinds of information can be sold to a rival or used to undermine the production process. The stolen data may be stored somewhere inside the victim network for covert transportation in the future.APT attacks commonly use white noise techniques (maybe in the form of a DDoS attack) to evade detection systems [131].This step is typically composed of the following phases.
- White noise attack
- Extra data collection
- Covering tracks
5.3. Some Behavioral Characteristics of APT Attacks on SF or PA
- Unusual and suspicious activities in security and control systems (especially the high-level access systems)
- Widespread use of backdoor tools (Most of them can be detected by common IDSs.
- Suspicious and unusual activities occurring in the databases
- Evidences for data and information stealth
6. Risk Mitigation Strategies and Countermeasure
| Strategy | IoT Layer | Related Security Aspect |
|---|---|---|
| User Authentication [136,137,138,139,140,141,142,143] | Middleware | Privacy, Confidentially, Authenticity |
| Secure Passwords [137,138,139,140,141,142,143,144] | Middleware | Privacy, Confidentially, Authenticity |
| Device-Level Encryption [136,137,138,139,140,143,144] | Edge layer | Privacy, Integrity Middleware |
| Communication-Level Encryption (SSL/TLS) [65,137,138,139,140,141,142,143,144] | Access Gateway | Confidentially, Integrity, Authenticity |
| Port Hardening [3,65,137,139,140,141,142] | Internet, Clould | Privacy, Authenticity, Non-Repudiation |
| Remote Login Deactivation [137,138,139,140,141,142,143] | Internet, Clould | Privacy, Authenticity, Non-Repudiation |
| Regular Firmware Update [3,138,139,140,141,142,144,145] | Application | Privacy, Confidentially, Availability |
| Measure | IoT Layer | Related Security Aspect |
|---|---|---|
| Password Recovery Made Safe [65,137,138,139,140,141,144] | Middleware | Privacy, Confidentially, Authenticity |
| Unauthorized Account Deactivation [138,139,140,142,144] | Edge layer | Privacy, Confidentially, Authenticity |
| Periodic Device Evaluation [65,137,139,140,141,143,144] | Edge layer | Privacy, Availability |
7. Future Roadmap
- Access Control from a Security Perspective:Dealing with hired labor and livestock, the owners of farms, greenhouses, etc. are traditionally concerned about access control. However, they need to adopt a security perspective for their property. Authentication, authorization, and accounting should be incorporated to prevent unauthorized access, which is the stepping stone in many severe attacks on SF and PA. Although the literature in this area comes with some relevant research reports [1,2,3,41,50], there is still opportunities for systematic research.
- Data Protection:Given, the abilities of smart devices and IoT, enormous data acquisition, communication and processing is a well-known characteristic of SF and PA [1,2]. This raises the need for efficient data protection mechanisms, which has been of interest to a few researchers [1,2]. However, data protection can still be considered as an open research challenge in this area.
- Network Infrastructure and Physical Layer Protection:
- Education as Risk Reduction: The social elements of reducing cyber-risks, such as education, has received relatively little attention by scholars [146]. Not only are farmers are interested in education regarding security threats to their operations, but education is regarded as a vital tool for reducing security risk [132,147,148]. Future research opportunities exist in assessing what cyber-safe behaviours farmers currently utilize. From this, there can be investigation of what educational formats, content, and dispersion would be most effective and appreciated by these vital stakeholders.
- Specific Secure Communication Protocols for SF and PA:In SF and PA, where sensors, actuators, drones, autonomous tractors and other smart devices are spread out in various locations, communication protocols are of critical importance. Although several network, Machine-to-Machine (M2M) and IoT protocols such as Bluetooth, NFC, WiFi, SSL, TCP, UDP and 6loWPA have been adopted from other technologies [3,121,149], there is still room for research on secure protocols specifically designed and standardized for SF and PA.
- Secure Smart Devices: Given the threats to smart devices used in SF and PA (studied in previous sections), security needs to be taken into consideration in design and implementation phases of these devices.
- Secure AI Adoption: In recent years, some researchers have been concerned about the application of AI in SF and PA [2,3]. Thus, the security threats to AI such as adversarial attacks [1,2] can motivate future research on secure AI in SF and PA. Informed by this taxonomy of cyber-threats, strengthening policy regarding cyber-security in PA is an important consideration for future research. Legal frameworks designed to protect private data and ensure privacy are key to addressing the challenge of cyber-security arising from new farming technologies [150]. Reviews on the social science of PA have highlighted that future research needs to address how policy-makers should respond to cyber-attacks on agri-food systems [151].
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Roopaei, M.; Rad, P.; Choo, K.K.R. Cloud of things in smart agriculture: Intelligent irrigation monitoring by thermal imaging. IEEE Cloud Comput. 2017, 4, 10–15. [Google Scholar] [CrossRef]
- Gupta, M.; Abdelsalam, M.; Khorsandroo, S.; Mittal, S. Security and privacy in smart farming: Challenges and opportunities. IEEE Access 2020, 8, 34564–34584. [Google Scholar] [CrossRef]
- Demestichas, K.; Peppes, N.; Alexakis, T. Survey on Security Threats in Agricultural IoT and Smart Farming. Sensors 2020, 20, 6458. [Google Scholar] [CrossRef] [PubMed]
- Lin, J.; Shen, Z.; Zhang, A.; Chai, Y. Blockchain and IoT based food traceability system. Int. J. Inf. Technol. 2018, 24, 1–16. [Google Scholar]
- Gia, T.N.; Qingqing, L.; Queralta, J.P.; Zou, Z.; Tenhunen, H.; Westerlund, T. Edge AI in smart farming IoT: CNNs at the edge and fog computing with LoRa. In Proceedings of the IEEE AFRICON, Accra, Ghana, 25 September 2019. [Google Scholar]
- Jahn, M.M.; Oemichen, W.L.; Treverton, G.F. Cyber Risk and Security Implications in Smart Agriculture and Food Systems; Technical Report; College of Agricultureand Life Sciences, University of Wisconsin: Madison, WI, USA, 2019. [Google Scholar]
- Kasten, J. Blockchain on the Farm: A Systematic Literature Review. J. Strateg. Innov. Sustain. 2020, 15, 129–153. [Google Scholar]
- Abuan, D.D.; Abad, A.C.; Lazaro, J.B., Jr.; Dadios, E.P. Security systems for remote farm. J. Autom. Control Eng. 2014, 2, 1–4. [Google Scholar] [CrossRef][Green Version]
- Vangala, A.; Sutrala, A.K.; Das, A.K.; Jo, M. Smart Contract-Based Blockchain-Envisioned Authentication Scheme for Smart Farming. IEEE Internet Things J. 2021, 8, 10792–10806. [Google Scholar] [CrossRef]
- Sa, I.; Chen, Z.; Popović, M.; Khanna, R.; Liebisch, F.; Nieto, J.; Siegwart, R. weedNet: Dense Semantic Weed Classification Using Multispectral Images and MAV for Smart Farming. IEEE Robot. Autom. Lett. 2018, 3, 588–595. [Google Scholar] [CrossRef]
- Su, J.; Yi, D.; Su, B.; Mi, Z.; Liu, C.; Hu, X.; Xu, X.; Guo, L.; Chen, W.H. Aerial Visual Perception in Smart Farming: Field Study of Wheat Yellow Rust Monitoring. IEEE Trans. Ind. Inf. 2021, 17, 2242–2249. [Google Scholar] [CrossRef]
- Shadrin, D.; Menshchikov, A.; Somov, A.; Bornemann, G.; Hauslage, J.; Fedorov, M. Enabling Precision Agriculture Through Embedded Sensing With Artificial Intelligence. IEEE Trans. Instrum. Meas. 2020, 69, 4103–4113. [Google Scholar] [CrossRef]
- Sambo, D.W.; Forster, A.; Yenke, B.O.; Sarr, I.; Gueye, B.; Dayang, P. Wireless Underground Sensor Networks Path Loss Model for Precision Agriculture (WUSN-PLM). IEEE Sens. J. 2020, 20, 5298–5313. [Google Scholar] [CrossRef]
- Gigli, M.; Koo, S. Internet of things: Services and applications categorization. Adv. Internet Things 2011, 1, 27–31. [Google Scholar] [CrossRef]
- Al-Fuqaha, A.; Guizani, M.; Mohammadi, M.; Aledhari, M.; Ayyash, M. Internet of things: A survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 2015, 17, 2347–2376. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of Things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- Kamienski, C.; Soininen, J.P.; Taumberger, M.; Fernandes, S.; Toscano, A.; Cinotti, T.S.; Maia, R.F.; Neto, A.T. Swamp: An iot-based smart water management platform for precision irrigation in agriculture. In Proceedings of the Global Internet of Things Summit (GIoTS), Bilbao, Spain, 4–7 June 2018. [Google Scholar]
- Hu, X.; Qian, S. IoT application system with crop growth models in facility agriculture. In Proceedings of the 6th International Conference on Computer Sciences and Convergence Information Technology (ICCIT), Seogwipo, Korea, 29 November 2011. [Google Scholar]
- Stovces, M.; Vanvek, J.; Masner, J.; Pavlik, J. Internet of things (iot) in agriculture-selected aspects. Agris On-line Pap. Econ. Inf. 2016, 8, 8388. [Google Scholar]
- Burton, L.; Dave, N.; Fernandez, R.; Jayachandran, K.; Bhansali, S. Smart gardening IoT soil sheets for real-time nutrient analysis. J. Electr. Soc. 2018, 165, B3156–B3162. [Google Scholar] [CrossRef]
- Malik, A.W.; Rahman, A.U.; Qayyum, T.; Ravana, S.D. Leveraging Fog Computing for Sustainable Smart Farming Using Distributed Simulation. IEEE Internet Things J. 2020, 7, 3300–3309. [Google Scholar] [CrossRef]
- Chukkapalli, S.S.L.; Mittal, S.; Gupta, M.; Abdelsalam, M.; Joshi, A.; Sandhu, R.; Joshi, K. Ontologies and Artificial Intelligence Systems for the Cooperative Smart Farming Ecosystem. IEEE Access 2020, 8, 164045–164064. [Google Scholar] [CrossRef]
- Bacco, M.; Berton, A.; Gotta, A.; Caviglione, L. IEEE 802.15.4 Air-Ground UAV Communications in Smart Farming Scenarios. IEEE Commun. Lett. 2018, 22, 1910–1913. [Google Scholar] [CrossRef]
- Chebrolu, N.; Läbe, T.; Stachniss, C. Robust Long-Term Registration of UAV Images of Crop Fields for Precision Agriculture. IEEE Robot. Autom. Lett. 2018, 3, 3097–3104. [Google Scholar] [CrossRef]
- Bayrakdar, M.E. A Smart Insect Pest Detection Technique With Qualified Underground Wireless Sensor Nodes for Precision Agriculture. IEEE Sens. J. 2019, 19, 10892–10897. [Google Scholar] [CrossRef]
- Huang, K.; Shu, L.; Li, K.; Yang, F.; Han, G.; Wang, X.; Pearson, S. Photovoltaic Agricultural Internet of Things Towards Realizing the Next Generation of Smart Farming. IEEE Access 2020, 8, 76300–76312. [Google Scholar] [CrossRef]
- Verdouw, C.; Tekinerdogan, B.; Beulens, A.; Wolfert, S. Digital twins in smart farming. Agric. Syst. 2021, 189, 103046. [Google Scholar] [CrossRef]
- Shabadi, L.S.; Biradar, H.B. Design and implementation of IOT based smart security and monitoring for connected smart farming. Int. J. Comput. Appl. 2018, 179, 1–4. [Google Scholar]
- Ahmed, N.; De, D.; Hussain, I. Internet of Things (IoT) for Smart Precision Agriculture and Farming in Rural Areas. IEEE Internet Things J. 2018, 5, 4890–4899. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Karimipour, H. Federated learning for drone authentication. Ad Hoc Netw. 2021, 120, 102574. [Google Scholar] [CrossRef]
- Chae, C.J.; Cho, H.J. Enhanced secure device authentication algorithm in P2P-based smart farm system. Peer-to-Peer Netw. Appl. 2018, 11, 1230–1239. [Google Scholar] [CrossRef]
- West, J. A prediction model framework for cyber-attacks to precision agriculture technologies. J. Agric. Food Inf. 2018, 19, 307–330. [Google Scholar] [CrossRef]
- Window, M. Security in Precision Agriculture: Vulnerabilities and Risks of Agricultural Systems. Master’s Thesis, Department of Computer Science, Lulea University of Technology, Lulea, Sweden, 2019. [Google Scholar]
- Grgic, K.; Zagar, D.; Krizanovic, V. Security in IPv6-based wireless sensor network—Precision agriculture example. In Proceedings of the 12th International Conference on Telecommunications, Zagreb, Croatia, 26 June 2013. [Google Scholar]
- Chi, H.; Welch, S.; Vasserman, E.; Kalaimannan, E. A framework of cybersecurity approaches in precision agriculture. In Proceedings of the ICMLG2017 5th International Conference on Management Leadership and Governance, Johannesburg, South Africa, 16 March 2017. [Google Scholar]
- Bahrami, P.N.; Dehghantanha, A.; Dargahi, T.; Parizi, R.M.; Choo, K.K.R.; Javadi, H.H. Cyber kill chain-based taxonomy of advanced persistent threat actors: Analogy of tactics, techniques, and procedures. J. Inf. Process. Syst. 2019, 15, 865–889. [Google Scholar]
- Sharma, A.; Jain, A.; Gupta, P.; Chowdary, V. Machine Learning Applications for Precision Agriculture: A Comprehensive Review. IEEE Access 2020, 9, 4843–4873. [Google Scholar] [CrossRef]
- Janrao, P.; Palivela, H. Management zone delineation in Precision agriculture using data mining: A review. In Proceedings of the International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), Coimbatore, India, 19–20 March 2015. [Google Scholar]
- Savla, A.; Israni, N.; Dhawan, P.; Mandholia, A.; Bhadada, H.; Bhardwaj, S. Survey of classification algorithms for formulating yield prediction accuracy in precision agriculture. In Proceedings of the International Conference on Innovations in Information, Embedded and Communication Systems (ICIIECS), Coimbatore, India, 19–20 March 2015. [Google Scholar]
- Kumar, S.; Kumar, N.; Saini, R.K. Energy-Saving Sensors for Precision Agriculture in Wireless Sensor Network: A Review. In Proceedings of the Women Institute of Technology Conference on Electrical and Computer Engineering (WITCON ECE), Piscataway, NJ, USA, 22–23 November 2019. [Google Scholar]
- Deepika, G.; Rajapirian, P. Wireless sensor network in precision agriculture: A survey. In Proceedings of the International Conference on Emerging Trends in Engineering, Technology and Science (ICETETS), Pudukkottai, India, 24–26 February 2016. [Google Scholar]
- Goel, K.; Bindal, A.K. Wireless Sensor Network in Precision Agriculture: A Survey Report. In Proceedings of the Fifth International Conference on Parallel, Distributed and Grid Computing (PDGC), Solan, India, 20–22 December 2018. [Google Scholar]
- Huerta, M.; Garcia, A.; Guillermo, J.C.; Martinez, R.C. Wireless Sensor Networks Applied to Precision Agriculture: A worldwide literature review with emphasis on Latin America. IEEE Geosci. Remote Sens. Mag. 2021. [Google Scholar] [CrossRef]
- Imam, S.A.; Choudhary, A.; Sachan, V.K. Design issues for wireless sensor networks and smart humidity sensors for precision agriculture: A review. In Proceedings of the International Conference on Soft Computing Techniques and Implementations (ICSCTI), Faridabad, India, 8–10 October 2015. [Google Scholar]
- Jawad, H.M.; Nordin, R.; Gharghan, S.K.; Ismail, A.M.J.M. Energy-Efficient Wireless Sensor Networks for Precision Agriculture: A Review. Sensors 2017, 17, 1781. [Google Scholar] [CrossRef]
- Kamath, R.; Balachandra, M.; Prabhu, S. Raspberry Pi as Visual Sensor Nodes in Precision Agriculture: A Study. IEEE Access 2019, 7, 45110–45122. [Google Scholar] [CrossRef]
- Narvaez, F.Y.; Reina, G.; Torres-Torriti, M.; Kantor, G.; Cheein, F.A. A Survey of Ranging and Imaging Techniques for Precision Agriculture Phenotyping. IEEE/ASME Trans. Mechatron. 2017, 22, 2428–2439. [Google Scholar] [CrossRef]
- Deroussi, A.; Alihamidi, I.; Charaf, L.A.; Madi, A.A.; Addaim, A. Routing Protocols for WSN: A Survey Precision Agriculture Case Study. In Proceedings of the IEEE 2nd International Conference on Electronics, Control, Optimization and Computer Science (ICECOCS), Kenitra, Morocco, 2–3 December 2020. [Google Scholar]
- Lakshmi, T.A.; Hariharan, B.; Rekha, P. A Survey on Energy Efficient Routing Protocol for IoT Based Precision Agriculture. In Proceedings of the International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 17–19 July 2019. [Google Scholar]
- Boghossian, A.; Linsky, S.; Mutschler, P.; Ulicny, B.; Barrett, L.; Bethel, G.; Matson, M.; Strang, T.; Ramsdell, K.W.; Koehler, S. Threats to Precision Agriculture; Technical Report; United States Department of Homeland Security and Office of Intelligence and Analysis: Washington, DC, USA, 2018.
- Ahmed, B.K.I.; Prakash, A.; Husna, M.S.; Prakash, A. A Review on Smart Farming with Zinc-Fortified Sprouts. In Proceedings of the Fourth World Conference on Smart Trends in Systems, Security and Sustainability (WorldS4), London, UK, 27 July 2020. [Google Scholar]
- Sreedevi, T.R.; Kumar, M.S. Digital Twin in Smart Farming: A Categorical Literature Review and Exploring Possibilities in Hydroponics. In Proceedings of the Advanced Computing and Communication Technologies for High Performance Applications (ACCTHPA), Kerala, India, 2 July 2020. [Google Scholar]
- Bhagat, M.; Kumar, D.; Kumar, D. Role of Internet of Things (IoT) in Smart Farming: A Brief Survey. In Proceedings of the 2019 Devices for Integrated Circuit (DevIC), Kalyani, India, 23 March 2019. [Google Scholar]
- Farooq, M.S.; Riaz, S.; Abid, A.; Abid, K.; Naeem, M.A. A Survey on the Role of IoT in Agriculture for the Implementation of Smart Farming. IEEE Access 2019, 7, 156237–156271. [Google Scholar] [CrossRef]
- Biradar, H.B.; Shabadi, L. Review on IOT based multidisciplinary models for smart farming. In Proceedings of the 2nd IEEE International Conference on Recent Trends in Electronics, Information & Communication Technology (RTEICT), Bangalore, India, 19 May 2017. [Google Scholar]
- Ünal, Z. Smart Farming Becomes Even Smarter With Deep Learning—A Bibliographical Analysis. IEEE Access 2020, 8, 105587–105609. [Google Scholar] [CrossRef]
- Barreto, L.; Amaral, A. Smart farming: Cyber security challenges. In Proceedings of the International Conference on Intelligent Systems (IS), Phuket, Thailand, 28 September 2018. [Google Scholar]
- Idoje, G.; Dagiuklas, T.; Iqbal, M. Survey for smart farming technologies: Challenges and issues. Comput. Electr. Eng. 2021, 92, 107104. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Shu, L.; Yang, X.; Derhab, A.; Maglaras, L. Security and privacy for green IoT-based agriculture: Review, blockchain solutions, and challenges. IEEE Access 2020, 8, 32031–32053. [Google Scholar] [CrossRef]
- Ametepe, A.F.X.; Ahouandjinou, S.A.R.; Ezin, E.C. Secure encryption by combining asymmetric and symmetric cryptographic method for data collection WSN in smart agriculture. In Proceedings of the IEEE International Smart Cities Conference (ISC2), Casablanca, Morocco, 19 October 2019. [Google Scholar]
- Chamarajnagar, R.; Ashok, A. Integrity threat identification for distributed IoT in precision agriculture. In Proceedings of the 16th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Boston, MA, USA, 10 June 2019. [Google Scholar]
- Zhang, N.; Wu, R.; Yuan, S.; Yuan, C.; Chen, D. RAV: Relay aided vectorized secure transmission in physical layer security for Internet of Things under active attacks. IEEE Internet Things J. 2019, 6, 8496–8506. [Google Scholar] [CrossRef]
- Bisogni, F.; Cavallini, S.; Di Trocchio, S. Cybersecurity at European level: The role of information availability. Commun. Strateg. 2011, 81, 105–124. [Google Scholar]
- Nesarani, A.; Ramar, R.; Pandian, S. An efficient approach for rice prediction from authenticated Block chain node using machine learning technique. Environ. Technol. Innov. 2020, 20, 101064. [Google Scholar] [CrossRef]
- Xue, M.; Gu, C.; Liu, W.; Yu, S.; O’Neill, M. Ten years of hardware Trojans: A survey from the attacker’s perspective. IET Comput. Digit. Tech. 2020, 14, 231–246. [Google Scholar] [CrossRef]
- Alrajhi, A.M. A survey of Artificial Intelligence techniques for cybersecurity improvement. Int. J. Cyber-Secur. Digit. Forensic 2020, 9, 34–41. [Google Scholar] [CrossRef]
- Jahromi, A.N.; Karimipour, H.; Dehghantanha, A.; Choo, K.K.R. Toward Detection and Attribution of Cyber-Attacks in IoT-enabled Cyber-physical Systems. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Ukil, A.; Sen, J.; Koilakonda, S. Embedded security for Internet of Things. In Proceedings of the 2011 2nd National Conference on Emerging Trends and Applications in Computer Science, Shillong, India, 4 May 2011; pp. 1–6. [Google Scholar]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Antonakakis, M.; April, T.; Bailey, M.; Bernhard, M.; Bursztein, E.; Cochran, J.; Durumeric, Z.; Halderman, J.A.; Invernizzi, L.; Kallitsis, M.; et al. Understanding the mirai botnet. In Proceedings of the 26th USENIX Security Symposium, Vancouver, BC, Canada, 16 August 2017; pp. 1093–1110. [Google Scholar]
- Ye, D.; Zhang, T.Y. Summation detector for false data-injection attack in cyber-physical systems. IEEE Trans. Cybern. 2019, 50, 2338–2345. [Google Scholar] [CrossRef] [PubMed]
- Al Shorman, A.; Faris, H.; Aljarah, I. Unsupervised intelligent system based on one class support vector machine and Grey Wolf optimization for IoT botnet detection. J. Ambient Intell. Humaniz. Comput. 2020, 11, 2809–2825. [Google Scholar] [CrossRef]
- What Is a Botnet Attack Work? Available online: https://www.akamai.com/us/en/resources/what-is-a-botnet.jsp (accessed on 5 December 2017).
- Fard, S.M.H.; Karimimpour, H.; Dehghantanha, A.; Jahromi, A.N.; Srivastava, G. Ensemble sparse representation-based cyber threat hunting for security of smart cities. Comput. Electr. Eng. 2020, 88, 106825. [Google Scholar] [CrossRef]
- Purohit, B.; Singh, P.P. Data leakage analysis on cloud computing. Int. J. Eng. Res. Appl. 2013, 3, 1311–1316. [Google Scholar]
- Dovom, E.M.; Azmoodeh, A.; Dehghantanha, A.; Newton, D.E.; Parizi, R.M.; Karimipour, H. Fuzzy pattern tree for edge malware detection and categorization in IoT. J. Syst. Arch. 2019, 97, 1–7. [Google Scholar] [CrossRef]
- Priebe, C.; Muthukumaran, D.; O’Keeffe, D.; Eyers, D.; Shand, B.; Kapitza, R.; Pietzuch, P. Cloudsafetynet: Detecting data leakage between cloud tenants. In Proceedings of the 6th edition of the ACM Workshop on Cloud Computing Security, New York, NY, USA, 7 November 2014; pp. 117–128. [Google Scholar]
- Musleh, A.S.; Chen, G.; Dong, Z.Y. A survey on the detection algorithms for false data injection attacks in smart grids. IEEE Transac. Smart Grid 2019, 11, 2218–2234. [Google Scholar] [CrossRef]
- Gruschka, N.; Jensen, M. Attack surfaces: A taxonomy for attacks on cloud services. In Proceedings of the 2010 IEEE 3rd International Conference on Cloud Computing, Miami, FL, USA, 5 July 2010; pp. 276–279. [Google Scholar]
- Stoica, I.; Adkins, D.; Zhuang, S.; Shenker, S.; Surana, S. Internet indirection infrastructure. IEEE/ACM Trans. Netw. 2004, 12, 205–218. [Google Scholar] [CrossRef]
- Khan, S.; Bagiwa, M.A.; Wahab, A.W.A.; Gani, A.; Abdelaziz, A. Understanding link fabrication attack in software defined network using formal methods. In Proceedings of the 2020 IEEE International Conference on Informatics, IoT, and Enabling Technologies (ICIoT), Doha, Qatar, 2 February 2020; pp. 555–562. [Google Scholar]
- Cuker, B.E. Livestock and Poultry: Other Colonists Who Changed the Food System of the Chesapeake Bay. In Diet for a Sustainable Ecosystem; Springer: Berlin/Heidelberg, Germany, 2020; pp. 219–244. [Google Scholar]
- The Cyber Kill Chain. Available online: https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html (accessed on 5 March 2021).
- Hutchins, E.M.; Cloppert, M.J.; Amin, R.M. Intelligence-driven computer network defense informed by analysis of adversary campaigns and intrusion kill chains. Lead. Issues Inf. Warf. Secur. Res. 2011, 1, 80. [Google Scholar]
- Meyers, C.A.; Powers, S.; Faissol, D.M. Taxonomies of Cyber Adversaries and Attacks: A Survey of Incidents and Approaches; Technical Report; Lawrence Livermore National Laboratory (LLNL): Livermore, CA, USA, 2009. [Google Scholar]
- Sidhu, S.; Mohd, B.J.; Hayajneh, T. Hardware security in IoT devices with emphasis on hardware Trojans. J. Sens. Actuator Netw. 2019, 8, 42. [Google Scholar] [CrossRef]
- Vasisht, D.; Kapetanovic, Z.; Won, J.; Jin, X.; Chandra, R.; Sinha, S.; Kapoor, A.; Sudarshan, M.; Stratman, S. Farmbeats: An iot platform for data-driven agriculture. In Proceedings of the 14th USENIX Symposium on Networked Systems Design and Implementation, Boston, MA, USA, 27 March 2017. [Google Scholar]
- Yazdinejadna, A.; Parizi, R.M.; Dehghantanha, A.; Khan, M.S. A kangaroo-based intrusion detection system on software-defined networks. Comput. Netw. 2021, 184, 107688. [Google Scholar] [CrossRef]
- Lengyel, T.K.; Maresca, S.; Payne, B.D.; Webster, G.D.; Vogl, S.; Kiayias, A. Scalability, fidelity and stealth in the drakvuf dynamic malware analysis system. In Proceedings of the 30th Annual Computer Security Applications Conference, New York, NY, USA, 8 December 2014. [Google Scholar]
- Lengyel, T.K. Malware Collection and Analysis via Hardware Virtualization. Ph.D. Thesis, University of Connecticut, Graduate School, Mansfield, CT, USA, 2015. [Google Scholar]
- Process Hollowing. Available online: http://www.autosectools.com/process-hollowing.pdf (accessed on 4 March 2021).
- HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Aledhari, M.; Karimipour, H. A survey on internet of things security: Requirements, challenges, and solutions. Internet Things 2019, 14, 100129. [Google Scholar] [CrossRef]
- Nissim, N.; Cohen, A.; Elovici, Y. Boosting the detection of malicious documents using designated active learning methods. In Proceedings of the 2015 IEEE 14th International Conference on Machine Learning and Applications (ICMLA), Miami, FL, USA, 9 December 2015. [Google Scholar]
- Shafiq, M.Z.; Khayam, S.A.; Farooq, M. Embedded malware detection using markov n-grams. In Proceedings of the International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, Paris, France, 10 July 2008. [Google Scholar]
- Sood, A.K.; Zeadally, S. A taxonomy of domain-generation algorithms. IEEE Secur. Priv. 2016, 14, 46–53. [Google Scholar] [CrossRef]
- Karim, A.; Salleh, R.B.; Shiraz, M.; Shah, S.A.A.; Awan, I.; Anuar, N.B. Botnet detection techniques: Review, future trends, and issues. J. Zhejiang Univ. Sci. C 2014, 15, 943–983. [Google Scholar] [CrossRef]
- Al-Taharwa, I.A.; Lee, H.M.; Jeng, A.B.; Wu, K.P.; Mao, C.H.; Wei, T.E.; Chen, S.M. Redjsod: A readable javascript obfuscation detector using semantic-based analysis. In Proceedings of the IEEE 11th International Conference on Trust, Security and Privacy in Computing and Communications, Liverpool, UK, 25 June 2012. [Google Scholar]
- Cosovan, D.; Benchea, R.; Gavrilut, D. A practical guide for detecting the java script-based malware using hidden markov models and linear classifiers. In Proceedings of the 16th International Symposium on Symbolic and Numeric Algorithms for Scientific Computing, Timisoara, Romania, 22 September 2014. [Google Scholar]
- Subrahmanian, V.; Ovelgonne, M.; Dumitras, T.; Prakash, B.A. The Global Cyber-Vulnerability Report; Springer: Berlin/Heidelberg, Germany, 2015. [Google Scholar]
- Singh, V.K.; Govindarasu, M. Cyber Kill Chain-Based Hybrid Intrusion Detection System for Smart Grid. In Wide Area Power Systems Stability, Protection, and Security; Springer: Cham, Switzerland, 2021; pp. 571–599. [Google Scholar]
- Yadav, T.; Rao, A.M. Technical aspects of cyber kill chain. In Proceedings of the International Symposium on Security in Computing and Communication, Kochi, India, 10 August 2015. [Google Scholar]
- Ablon, L.; Bogart, A. Zero Days, Thousands of Nights: The Life and Times of Zero-Day Vulnerabilities and Their Exploits; Rand Corporation: Santa Monica, CA, USA, 2017. [Google Scholar]
- Singh, J.; Sharmila, V.C. Detecting Trojan Attacks on Deep Neural Networks. In Proceedings of the 4th International Conference on Computer, Communication and Signal Processing (ICCCSP), Chennai, India, 28 September 2020. [Google Scholar]
- Zhang, Z.; Jia, J.; Wang, B.; Gong, N.Z. Backdoor attacks to graph neural networks. arXiv 2020, arXiv:2006.11165. [Google Scholar]
- Operation Ephemeral Hydra: Ie Zero-Day Linked to Deputydog Uses Diskless Method. Available online: https://www.fireeye.com/blog/threat-research/2013/11/operation-ephemeral-hydra-ie-zero-day-linked-to-deputydog-uses-diskless-method.html (accessed on 5 March 2021).
- Guri, M.; Poliak, Y.; Shapira, B.; Elovici, Y. JoKER: Trusted Detection of Kernel Rootkits in Android Devices via JTAG Interface. In Proceedings of the IEEE Trustcom/BigDataSE/ISPA, Helsinki, Finland, 20 August 2015. [Google Scholar]
- Martin, E.D.; Kargaard, J.; Sutherland, I. Raspberry Pi Malware: An analysis of cyberattacks towards IoT devices. In Proceedings of the 10h IEEE International Conference on Dependable Systems, Services and Technologies, Leeds, UK, 5 June 2019. [Google Scholar]
- Schmidt, A.D.; Clausen, J.H.; Camtepe, A.; Albayrak, S. Detecting symbian os malware through static function call analysis. In Proceedings of the IEEE International Conference on Malicious and Unwanted Software (MALWARE), Montreal, QC, Canada, 13 October 2009. [Google Scholar]
- You, D.H.; Noh, B.N. Android platform based linux kernel rootkit. In Proceedings of the 6th International Conference on Malicious and Unwanted Software, Washington, DC, USA, 18 October 2011. [Google Scholar]
- Park, W.H.; Park, K.C.; il Heo, K.; Kook, K.H. Agent Attacks Using a TTL Transformation of Windows Registry. In Proceedings of the International Conference on Information Science and Applications, Seoul, Korea, 10 April 2010. [Google Scholar]
- Diogenes, Y.; Ozkaya, E. Cybersecurity—Attack and Defense Strategies; Packt Publishing: Birmingham, UK, 2018. [Google Scholar]
- DLL Side-Loading Technique Used in the Recent Kaseya Ransomware Attack. Available online: https://www.fortinet.com/blog/threat-research/dll-side-loading-technique-used-in-recent-kaseya-ransomware-attack (accessed on 26 July 2021).
- Hu, C. Backdoor detection in embedded system firmware without file system. J. Commun. 2013, 34, 140–145. [Google Scholar]
- Vulnerable Embedded Systems, CVE-2019-17666. Available online: https://nvd.nist.gov/vuln/detail/CVE-2019-17666 (accessed on 16 October 2019).
- Park, C.S.; Lee, J.H.; Seo, S.C.; Kim, B.K. Assuring software security against buffer overflow attacks in embedded software development life cycle. In Proceedings of the 12th International Conference on Advanced Communication Technology (ICACT), Gangwon-Do, Korea, 7 February 2010. [Google Scholar]
- Android Mobile Security Threats. Available online: https://www.kaspersky.com/resource-center/threats/android-mobile-threats (accessed on 10 December 2013).
- Unit 42 Technical Analysis: Seaduke. Available online: https://unit42.paloaltonetworks.com/unit-42-technical-analysis-seaduke/ (accessed on 5 March 2021).
- Yazdinejad, A.; Bohlooli, A.; Jamshidi, K. P4 to SDNet: Automatic generation of an efficient protocol-independent packet parser on reconfigurable hardware. In Proceedings of the 8th International Conference on Computer and Knowledge Engineering (ICCKE), Mashhad, Iran, 25 October 2018. [Google Scholar]
- Yazdinejad, A.; Kavei, S.; Razaghi Karizno, S. Increasing the Performance of Reactive Routing Protocol using the Load Balancing and Congestion Control Mechanism in MANET. Comput. Knowl. Eng. 2019, 2, 33–42. [Google Scholar]
- Das, A.K.; Zeadally, S.; He, D. Taxonomy and analysis of security protocols for Internet of Things. Future Gener. Comput. Syst. 2018, 89, 110–125. [Google Scholar] [CrossRef]
- Yazdinejad, A.; HaddadPajouh, H.; Dehghantanha, A.; Parizi, R.M.; Srivastava, G.; Chen, M.Y. Cryptocurrency malware hunting: A deep recurrent neural network approach. Appl. Soft Comput. 2020, 96, 106630. [Google Scholar] [CrossRef]
- Microsoft Security Intelligence Report (Volume 19). Available online: https://download.microsoft.com/download/4/4/C/44CDEF0E-7924-4787-A56A-16261691ACE3/Microsoft_Security_Intelligence_Report_Volume_19_English.pdf (accessed on 5 March 2021).
- Sontowski, S.; Gupta, M.; Chukkapalli, S.S.L.; Abdelsalam, M.; Mittal, S.; Joshi, A.; Sandhu, R. Cyber Attacks on Smart Farming Infrastructure. In Proceedings of the IEEE 6th International Conference on Collaboration and Internet Computing (CIC), Atlanta, GA, USA, 1 December 2020. [Google Scholar]
- FarmBeats for Students. Available online: https://education.microsoft.com/en-us/lesson/5d991297 (accessed on 27 July 2021).
- Weaknesses in Wireless LAN Session Containment. Available online: http://i.cmpnet.com/nc/1612/graphics/SessionContainment_file.pdf (accessed on 27 July 2021).
- Quintero-Bonilla, S.; Martín del Rey, A. A New Proposal on the Advanced Persistent Threat: A Survey. Appl. Sci. 2020, 10, 3874. [Google Scholar] [CrossRef]
- Zulkefli, Z.; Singh, M.M. Sentient-based Access Control model: A mitigation technique for Advanced Persistent Threats in Smartphones. J. Inf. Secur. Appl. 2020, 51, 1–11. [Google Scholar] [CrossRef]
- Hejase, H.J. Advanced Persistent ThreatS (APT): An Awareness Review. J. Econ. Econ. Educ. Res. 2020, 21, 1–8. [Google Scholar]
- Advanced Persistent Threat (APT) Progression. Available online: https://www.imperva.com/learn/application-security/apt-advanced-persistent-threat/ (accessed on 16 August 2021).
- Cyber ThreatScape Report. Available online: https://www.accenture.com/_acnmedia/PDF-136/Accenture-2020-Cyber-Threatscape-Full-Report.pdf (accessed on 17 May 2021).
- FBI Investigation. Smart Farming May Increase Cyber Targeting against US Food and Agriculture Sector. Available online: https://info.publicintelligence.net/FBI-SmartFarmHacking.pdf (accessed on 31 March 2016).
- Wass, S.; Pournouri, S.; Ibbotson, G. Prediction of Cyber Attacks During Coronavirus Pandemic by Classification Techniques and Open Source Intelligence. In Cybersecurity, Privacy and Freedom Protection in the Connected World; Springer: Cham, Switzerland, 2021. [Google Scholar]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Choo, K.K.R. Blockchain-enabled authentication handover with efficient privacy protection in SDN-based 5G networks. IEEE Trans. Netw. Sci. Eng. 2019, 8, 1–12. [Google Scholar] [CrossRef]
- Yazdinejad, A.; Parizi, R.M.; Dehghantanha, A.; Karimipour, H.; Srivastava, G.; Aledhari, M. Enabling Drones in the Internet of Things with Decentralized Blockchain-based Security. IEEE Internet Things J. 2020, 8, 6406–6415. [Google Scholar] [CrossRef]
- Khanna, A.; Kaur, S. Evolution of Internet of Things (IoT) and its significant impact in the field of Precision Agriculture. Comput. Electr. Agric. 2019, 157, 218–231. [Google Scholar] [CrossRef]
- Das, S.K.; Kant, K.; Zhang, N. Handbook on Securing Cyber-Physical Critical Infrastructure; Elsevier: Amsterdam, The Netherlands, 2012. [Google Scholar]
- Zhang, H.; Wei, X.; Zou, T.; Li, Z.; Yang, G. Agriculture Big Data: Research status, challenges and countermeasures. In Proceedings of the International Conference on Computer and Computing Technologies in Agriculture, Beijing, China, 16 September 2014. [Google Scholar]
- Daoliang, L. Internet of things and wisdom agriculture. Agric. Eng. 2012, 2, 1–6. [Google Scholar]
- Butun, I.; Österberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, attacks, and countermeasures. IEEE Commun. Surv. Tutor. 2019, 22, 616–644. [Google Scholar] [CrossRef]
- Ghadeer, H. Cybersecurity issues in Internet of Things and countermeasures. In Proceedings of the IEEE International Conference on Industrial Internet (ICII), Bellevue, WA, USA, 21 October 2018. [Google Scholar]
- Pfleeger, C.P.; Pfleeger, S.L. Analyzing Computer Security: A Threat/Vulnerability/Countermeasure Approach, 1st ed.; Pearson: London, UK, 18 August 2011. [Google Scholar]
- Whitacre, P. Authenticity, Integrity, and Security in a Digital World: Proceedings of a Workshop—In Brief; National Academies Press: Washington, DC, USA, 2019. [Google Scholar]
- Mentsiev, A.U.; Magomaev, T.R. Security threats of NB-IoT and countermeasures. In Proceedings of the IOP Conference Series: Materials Science and Engineering, London, UK, 1 May 2020. [Google Scholar]
- Mekala, M.S.; Viswanathan, P. A Survey: Smart agriculture IoT with cloud computing. In Proceedings of the International Conference on Microelectronic Devices, Circuits and Systems (ICMDCS), Vellore, India, 10 August 2017. [Google Scholar]
- Bronson, K.; Knezevic, I. Big Data in food and agriculture. Big Data Soc. 2016, 3. [Google Scholar] [CrossRef]
- Geil, A.; Sagers, G.; Spaulding, A.D.; Wolf, J.R. Cyber Security on the Farm: An Assessment of Cyber Security Practices in the United States Agricultural Industry. Int. Food Agribus. Manag. Rev. 2018, 21, 317–334. [Google Scholar] [CrossRef]
- Homeland Security. Threats to Precision Agriculture. Public-Private Analytic Exchange Program. Available online: https://www.dhs.gov/sites/default/files/publications/2018%20AEP_Threats_to_Precision_Agriculture.pdf (accessed on 26 July 2018).
- Yazdinejad, A.; Parizi, R.M.; Srivastava, G.; Dehghantanha, A. Making Sense of Blockchain for AI Deepfakes Technology. In Proceedings of the 2020 IEEE Globecom Workshops, Taipei, Taiwan, 7 December 2020; pp. 1–6. [Google Scholar]
- Trendov, N.M.; Varas, S.; Zeng, M. Digital technologies in agriculture and rural areas: Status report. Digit. Technol. Agric. Rural Areas 2019, 3, 152. [Google Scholar]
- Klerkx, L.; Jakku, E.; Labarthe, P. A review of social science on digital agriculture, smart farming and agriculture 4.0: New contributions and a future research agenda. NJAS Wageningen J. Life Sci. 2019, 90, 100315. [Google Scholar] [CrossRef]

| Reviews | Objective & Contribution | Considering Technology |
|---|---|---|
| [2] | Study on security and privacy in SF ecosystems Elaborates on potential cyber-attack scenarios Open research challenges and future directions | IoT, Wireless Sensor Network (WSN), Blockchain, AI, Machine Learning (ML) |
| [3] | Study on security threats in SF and agricultural IoT Highlights the innovations, techniques, and threats in SF | IoT, Blockchain, AI, ML |
| [38] | Applying ML methods for PA Demonstrates the impact of ML in improving the quality of the product | IoT, AI, ML |
| [39] | Studies the data mining approaches for the management of PA Applying Fuzzy, DBSCAN, SVM, algorithms | AI, ML |
| [40] | Using AI algorithms for formulating yield prediction in PA Finding the best classification algorithm, bagging, in crops | AI, ML |
| [41] | Designing energy-saving sensors for PA Measures temperature, soil moisture, and humidity by sensors in SF | WSN |
| [42] | Study WSN methods in PA and SF Plant monitoring with the image processing using field-programmable gate array (FPGA) | WSN, FPGA |
| [43] | Presents the importance of PA over traditional agriculture techniques Applying WSN for obtaining parameters of land | IoT, WSN |
| [44] | Reviews WSN applications in SF and PA | IoT, WSN |
| [45] | Design WSNs and smart humidity sensors for PA Comparative review of research in the field of agriculture | WSN, Very large-scale integration (VLSI) |
| [46] | The review outlines the applications of WSNs in agriculture Provides a taxonomy of energy-efficient techniques for WSNs in agriculture Shows opportunities for processing IoT data | IoT, WSN |
| [47] | Considers Raspberry Pi as visual sensor nodes in PA Applying random forest and support vector machine classifiers to classify crops | WSN, AI, ML |
| [48] | Studies ranging and imaging techniques for PA Develops sensing techniques to provide information about crop growth Presents innovative sensing methods in pesticide management and crop monitoring | AI, ML |
| [49] | Studies Routing Protocols for WSN in PA Applies Ad-Hoc, MANET, VANET and WSN to facilitate control of PA | MANET, VANET, WSN |
| [50] | Studies energy efficient routing protocol for IoT Based PA | IoT, WSN |
| [52] | Review on SF with Zinc-Fortified sprouts Considers robotic solutions with AI in agricultural techniques | IoT, AI |
| [54] | Review on role of IoT in SF Discusses different tools, hardware, and software used in SF | IoT |
| [55] | Studies the IoT effect when implementing SF Highlights security issues in IoT in agriculture Presents open research issues and challenges in IoT agriculture | IoT, WSN, AI, ML |
| [56] | Review on IoT-based Multidisciplinary models for SF Considers Cyber-Physical systems role in PA Applies cloud computing technologies for better production of crops | IoT, WSN, Cloud computing |
| [57] | Explores the advantages of using deep learning in SF Provides a bibliography containing 120 papers in SF and PA | IoT, AI, ML |
| [58] | Studies cyber-security challenges in SF using an empirical methodology to highlight security threats in SF systems | IoT, ICT |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Yazdinejad, A.; Zolfaghari, B.; Azmoodeh, A.; Dehghantanha, A.; Karimipour, H.; Fraser, E.; Green, A.G.; Russell, C.; Duncan, E. A Review on Security of Smart Farming and Precision Agriculture: Security Aspects, Attacks, Threats and Countermeasures. Appl. Sci. 2021, 11, 7518. https://doi.org/10.3390/app11167518
Yazdinejad A, Zolfaghari B, Azmoodeh A, Dehghantanha A, Karimipour H, Fraser E, Green AG, Russell C, Duncan E. A Review on Security of Smart Farming and Precision Agriculture: Security Aspects, Attacks, Threats and Countermeasures. Applied Sciences. 2021; 11(16):7518. https://doi.org/10.3390/app11167518
Chicago/Turabian StyleYazdinejad, Abbas, Behrouz Zolfaghari, Amin Azmoodeh, Ali Dehghantanha, Hadis Karimipour, Evan Fraser, Arthur G. Green, Conor Russell, and Emily Duncan. 2021. "A Review on Security of Smart Farming and Precision Agriculture: Security Aspects, Attacks, Threats and Countermeasures" Applied Sciences 11, no. 16: 7518. https://doi.org/10.3390/app11167518
APA StyleYazdinejad, A., Zolfaghari, B., Azmoodeh, A., Dehghantanha, A., Karimipour, H., Fraser, E., Green, A. G., Russell, C., & Duncan, E. (2021). A Review on Security of Smart Farming and Precision Agriculture: Security Aspects, Attacks, Threats and Countermeasures. Applied Sciences, 11(16), 7518. https://doi.org/10.3390/app11167518