A Bi-Level Model for Detecting and Correcting Parameter Cyber-Attacks in Power System State Estimation
Abstract
:1. Introduction
- An explicit mathematical bi-level model for detecting and correcting cyber-attack pertaining state estimator static data.
- Using the temporal and spatio characteristics of the grid to eliminate non-linearity in parameter correction and providing a sliding-window for an online monitoring scheme of the measurement model parameters.
2. Background
2.1. State Estimation
2.2. Bi-Level Optimization
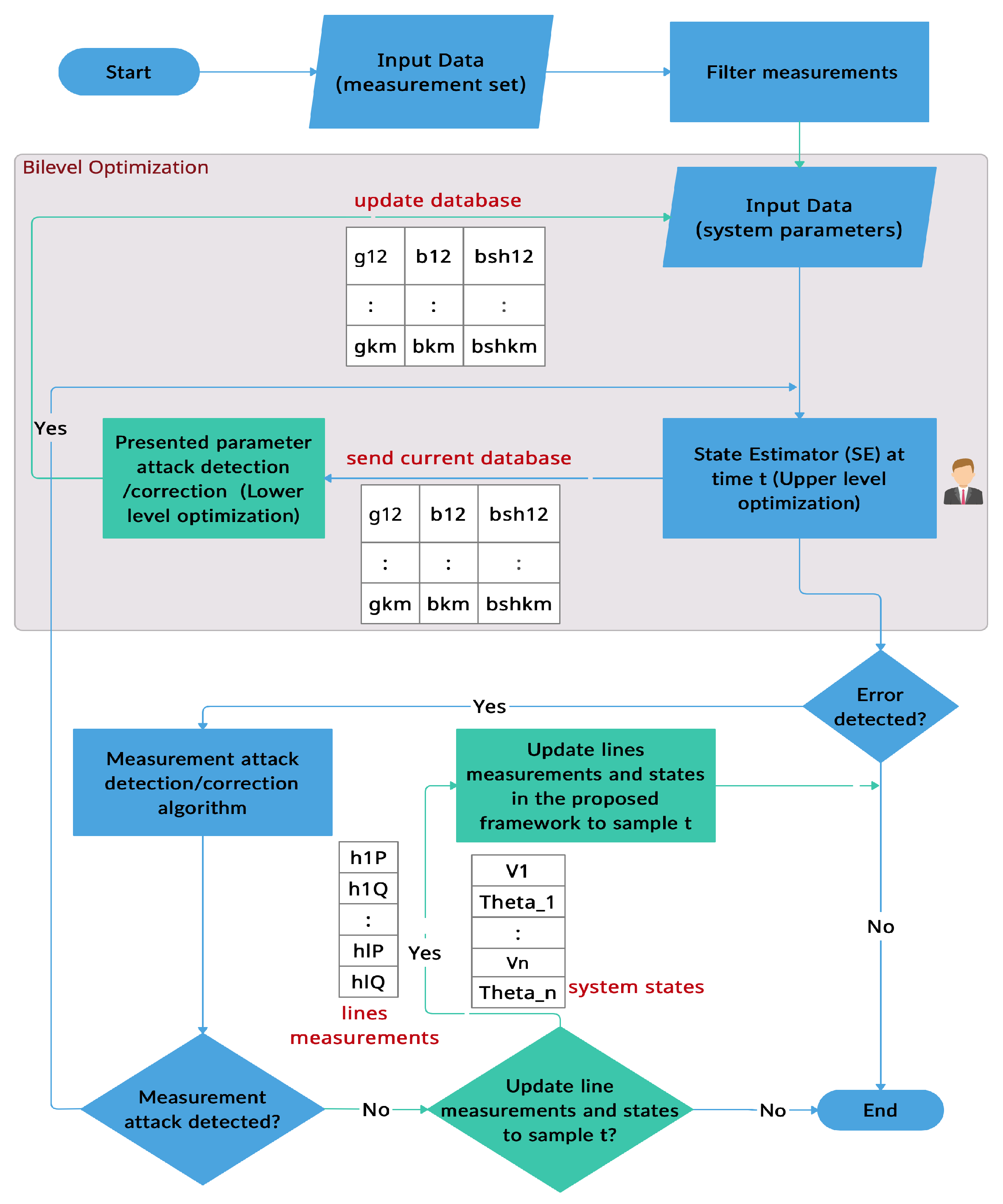
3. Framework
3.1. Preliminaries
3.2. Cyber-Attack Model
3.3. Bi-Level Optimization Model
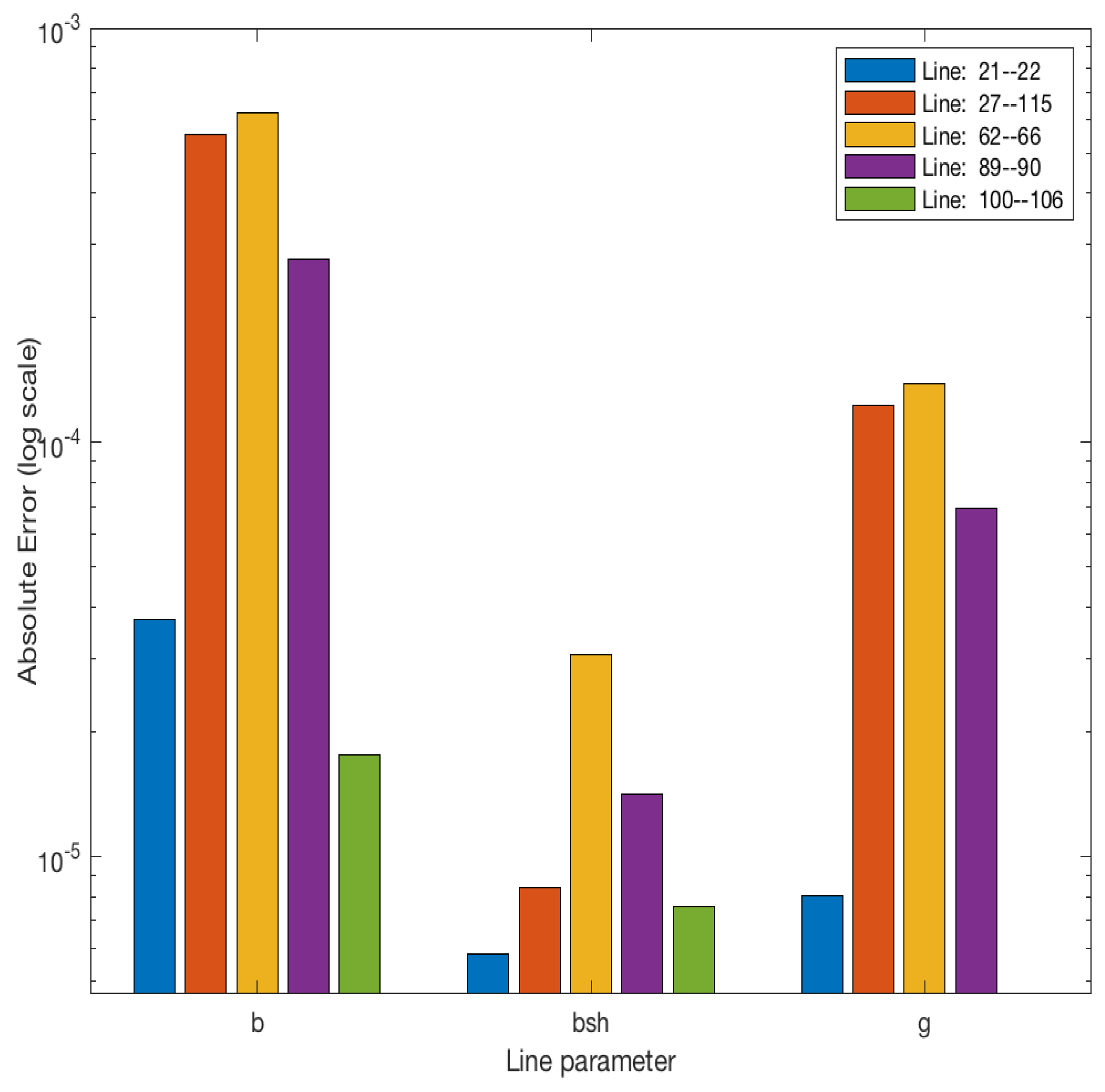
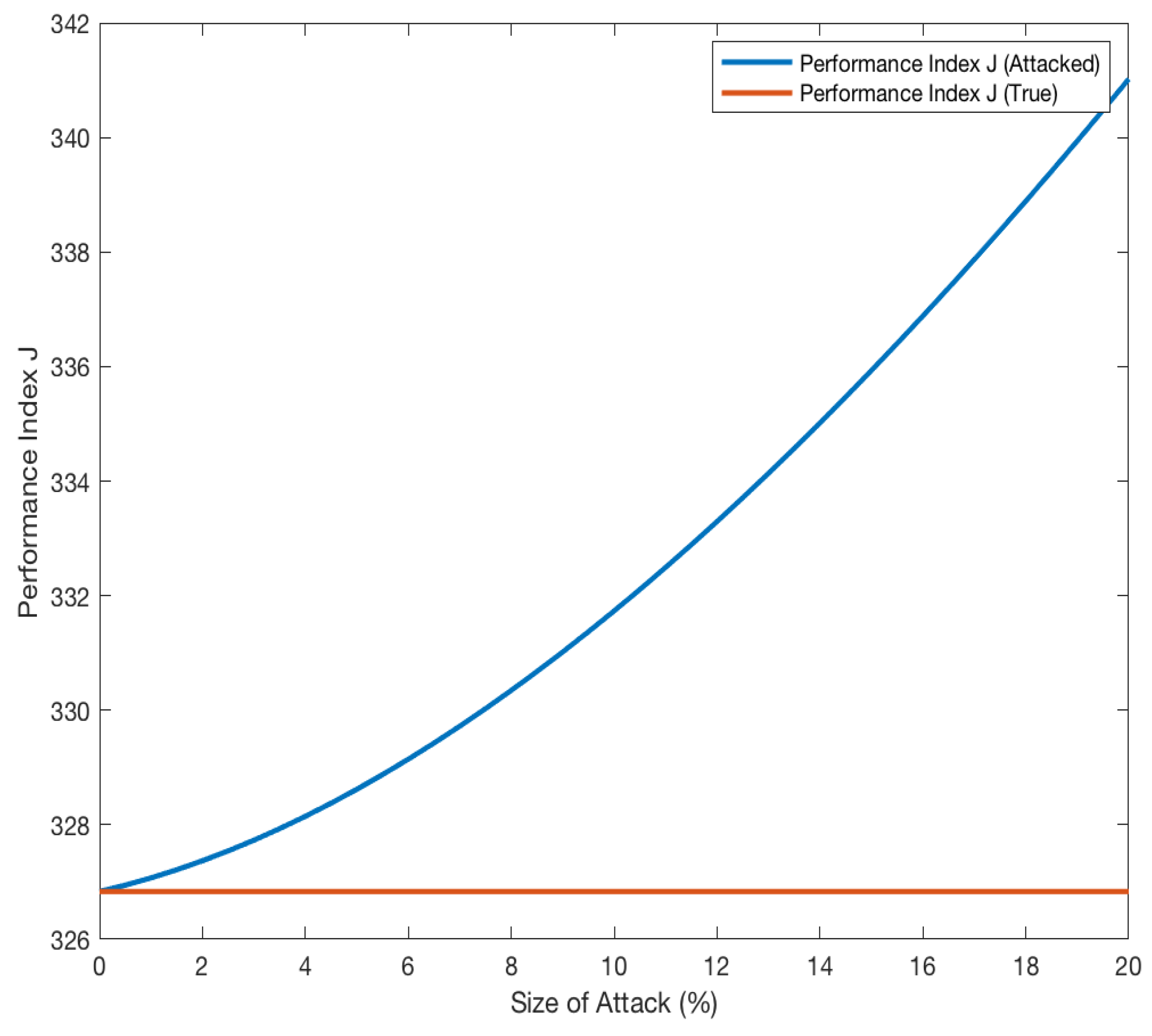
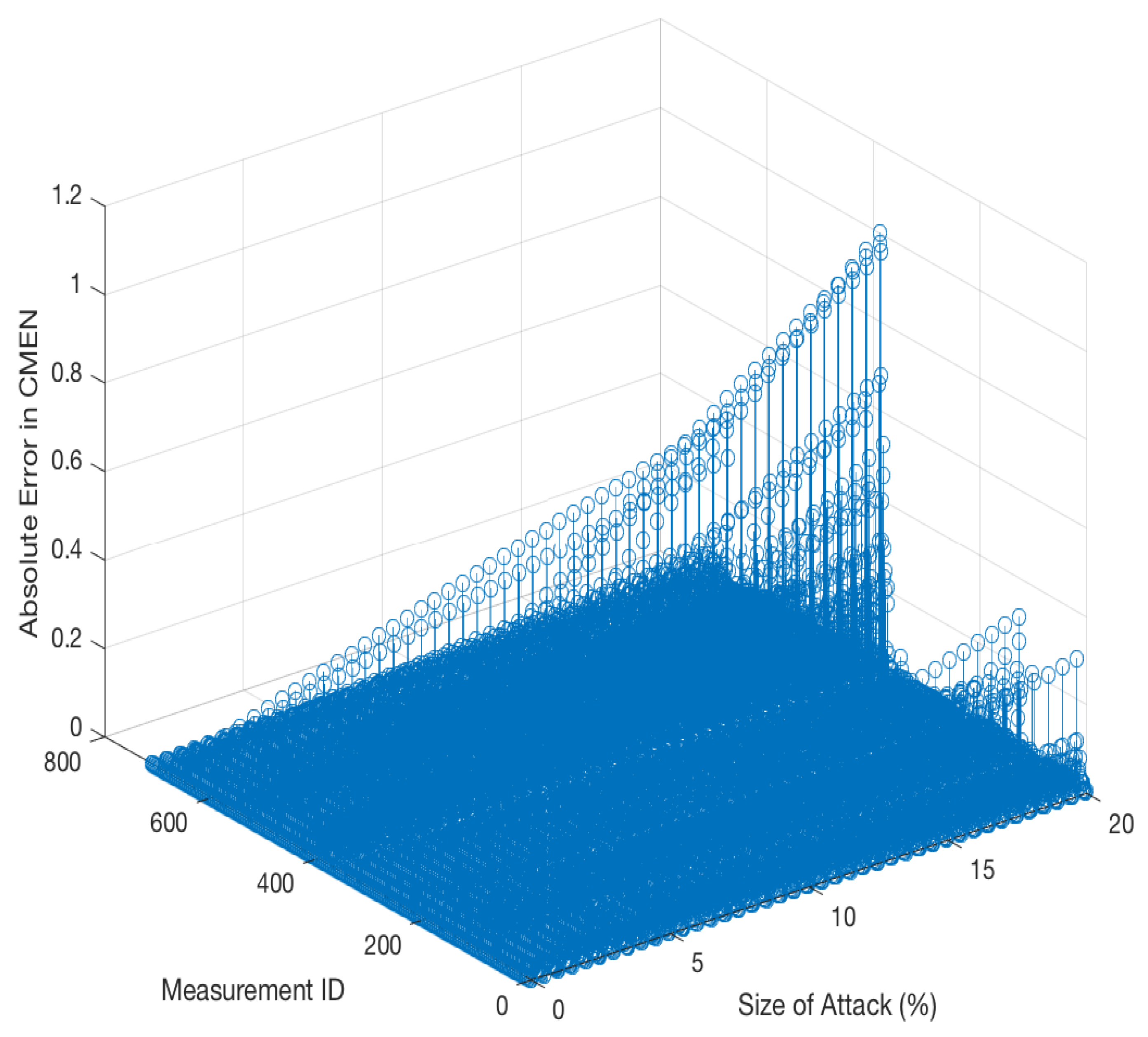
4. Case Study
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Raiyn, J. A survey of cyber attack detection strategies. Int. J. Secur. Its Appl. 2014, 8, 247–256. [Google Scholar] [CrossRef]
- Gupta, R.; Tanwar, S.; Tyagi, S.; Kumar, N. Machine learning models for secure data analytics: A taxonomy and threat model. Comput. Commun. 2020, 153, 406–440. [Google Scholar] [CrossRef]
- Sornsuwit, P.; Jaiyen, S. Intrusion detection model based on ensemble learning for U2R and R2L attacks. In Proceedings of the 2015 7th International Conference on Information Technology and Electrical Engineering (ICITEE), Chiang Mai, Thailand, 29–30 October 2015; pp. 354–359. [Google Scholar]
- Magalhaes, A.; Lewis, G. Modeling Malicious Network Packets with Generative Probabilistic Graphical Models. Available online: http://cs229.stanford.edu/proj2016spr/report/021.pdf (accessed on 13 July 2021).
- Jeya, P.G.; Ravichandran, M.; Ravichandran, C. Efficient classifier for R2L and U2R attacks. Int. J. Comput. Appl. 2012, 45, 28–32. [Google Scholar]
- Liu, Y.; Ning, P.; Reiter, M.K. False data injection attacks against state estimation in electric power grids. ACM Trans. Inf. Syst. Secur. 2011, 14, 1–33. [Google Scholar] [CrossRef]
- Hug, G.; Giampapa, J.A. Vulnerability assessment of AC state estimation with respect to false data injection cyber-attacks. IEEE Trans. Smart Grid 2012, 3, 1362–1370. [Google Scholar] [CrossRef] [Green Version]
- Sridhar, S.; Manimaran, G. Data integrity attacks and their impacts on SCADA control system. In Proceedings of the IEEE PES General Meeting, Minneapolis, MI, USA, 25–29 July 2010; pp. 1–6. [Google Scholar]
- Bi, S.; Zhang, Y.J.A. Graph-based cyber security analysis of state estimation in smart power grid. IEEE Commun. Mag. 2017, 55, 176–183. [Google Scholar] [CrossRef]
- Ozay, M.; Esnaola, I.; Vural, F.T.Y.; Kulkarni, S.R.; Poor, H.V. Sparse attack construction and state estimation in the smart grid: Centralized and distributed models. IEEE J. Sel. Areas Commun. 2013, 31, 1306–1318. [Google Scholar] [CrossRef] [Green Version]
- Kosut, O.; Jia, L.; Thomas, R.J.; Tong, L. Malicious data attacks on the smart grid. IEEE Trans. Smart Grid 2011, 2, 645–658. [Google Scholar] [CrossRef] [Green Version]
- Teixeira, A.; Sou, K.C.; Sandberg, H.; Johansson, K.H. Secure control systems: A quantitative risk management approach. IEEE Control Syst. Mag. 2015, 35, 24–45. [Google Scholar]
- Alexopoulos, T.A.; Korres, G.N.; Manousakis, N.M. Complementarity reformulations for false data injection attacks on PMU-only state estimation. Electr. Power Syst. Res. 2020, 189, 106796. [Google Scholar] [CrossRef]
- Hao, J.; Piechocki, R.J.; Kaleshi, D.; Chin, W.H.; Fan, Z. Sparse malicious false data injection attacks and defense mechanisms in smart grids. IEEE Trans. Ind. Inform. 2015, 11, 1–12. [Google Scholar] [CrossRef] [Green Version]
- Jin, M.; Lavaei, J.; Johansson, K.H. Power grid AC-based state estimation: Vulnerability analysis against cyber attacks. IEEE Trans. Autom. Control 2018, 64, 1784–1799. [Google Scholar] [CrossRef]
- He, Y.; Mendis, G.J.; Wei, J. Real-time detection of false data injection attacks in smart grid: A deep learning-based intelligent mechanism. IEEE Trans. Smart Grid 2017, 8, 2505–2516. [Google Scholar] [CrossRef]
- Ruben, C.; Dhulipala, S.; Nagaraj, K.; Zou, S.; Starke, A.; Bretas, A.; Zare, A.; McNair, J. Hybrid data-driven physics model-based framework for enhanced cyber-physical smart grid security. IET Smart Grid 2020, 3, 445–453. [Google Scholar] [CrossRef]
- Nagaraj, K.; Zou, S.; Ruben, C.; Dhulipala, S.; Starke, A.; Bretas, A.; Zare, A.; McNair, J. Ensemble CorrDet with adaptive statistics for bad data detection. IET Smart Grid 2020, 3, 572–580. [Google Scholar] [CrossRef]
- Bretas, A.S.; Bretas, N.G.; Carvalho, B.E. Further contributions to smart grids cyber-physical security as a malicious data attack: Proof and properties of the parameter error spreading out to the measurements and a relaxed correction model. Int. J. Electr. Power Energy Syst. 2019, 104, 43–51. [Google Scholar] [CrossRef]
- Zou, T.; Bretas, A.S.; Ruben, C.; Dhulipala, S.C.; Bretas, N. Smart grids cyber-physical security: Parameter correction model against unbalanced false data injection attacks. Electr. Power Syst. Res. 2020, 187, 106490. [Google Scholar] [CrossRef]
- Bretas, N.G.; Bretas, A.S. A two steps procedure in state estimation gross error detection, identification, and correction. Int. J. Electr. Power Energy Syst. 2015, 73, 484–490. [Google Scholar] [CrossRef]
- Lin, Y.; Abur, A. Fast Correction of Network Parameter Errors. IEEE Trans. Power Syst. 2018, 33, 1095–1096. [Google Scholar] [CrossRef]
- Abur, A.; Zhu, J. Identification of parameter errors. In Proceedings of the IEEE PES General Meeting, Minneapolis, MI, USA, 25–29 July 2010; pp. 1–4. [Google Scholar]
- Carvalho, B.; Bretas, N.; Bretas, A. A local state vector augmentation technique for processing network parameters errors. In Proceedings of the 2017 IEEE Power Energy Society General Meeting, Chicago, IL, USA, 16–20 July 2017; pp. 1–5. [Google Scholar]
- Bretas, A.; Bretas, N.; Braunstein, S.; Rossoni, A.; Trevizan, R. Multiple gross errors detection, identification and correction in three-phase distribution systems WLS state estimation: A per-phase measurement error approach. Electr. Power Syst. Res. 2017, 151, 174–185. [Google Scholar] [CrossRef]
- Lin, Y.; Abur, A. Robust state estimation against measurement and network parameter errors. IEEE Trans. Power Syst. 2018, 33, 4751–4759. [Google Scholar] [CrossRef]
- Arturo, B.; Newton, G.; Bretas, J.L.J.; Carvalho, B.E. Cyber-Physical Power Systems State Estimation; Elsevier: Amsterdam, The Netherlands, 2021; Volume 1. [Google Scholar]
- Bretas, N.G.; Bretas, A.S. The Extension of the Gauss Approach for the Solution of an Overdetermined Set of Algebraic Non Linear Equations. IEEE Trans. Circuits Syst. II Express Briefs 2018, 65, 1269–1273. [Google Scholar] [CrossRef]
- Sinha, A.; Malo, P.; Deb, K. A review on bilevel optimization: From classical to evolutionary approaches and applications. IEEE Trans. Evol. Comput. 2017, 22, 276–295. [Google Scholar] [CrossRef]
- Bretas, A.S.; Bretas, N.G.; Carvalho, B.; Baeyens, E.; Khargonekar, P.P. Smart grids cyber-physical security as a malicious data attack: An innovation approach. Electr. Power Syst. Res. 2017, 149, 210–219. [Google Scholar] [CrossRef]
- Zimmerman, R.D.; Murillo-Sanchez, C.E.; Thomas, R.J. MATPOWER: Steady-State Operations, Planning, and Analysis Tools for Power Systems Research and Education. IEEE Trans. Power Syst. 2011, 26, 12–19. [Google Scholar] [CrossRef] [Green Version]
- Gurobi Optimization, LLC. Gurobi Optimizer Reference Manual; Gurobi Optimization, LLC: Beaverton, OR, USA, 2021. [Google Scholar]
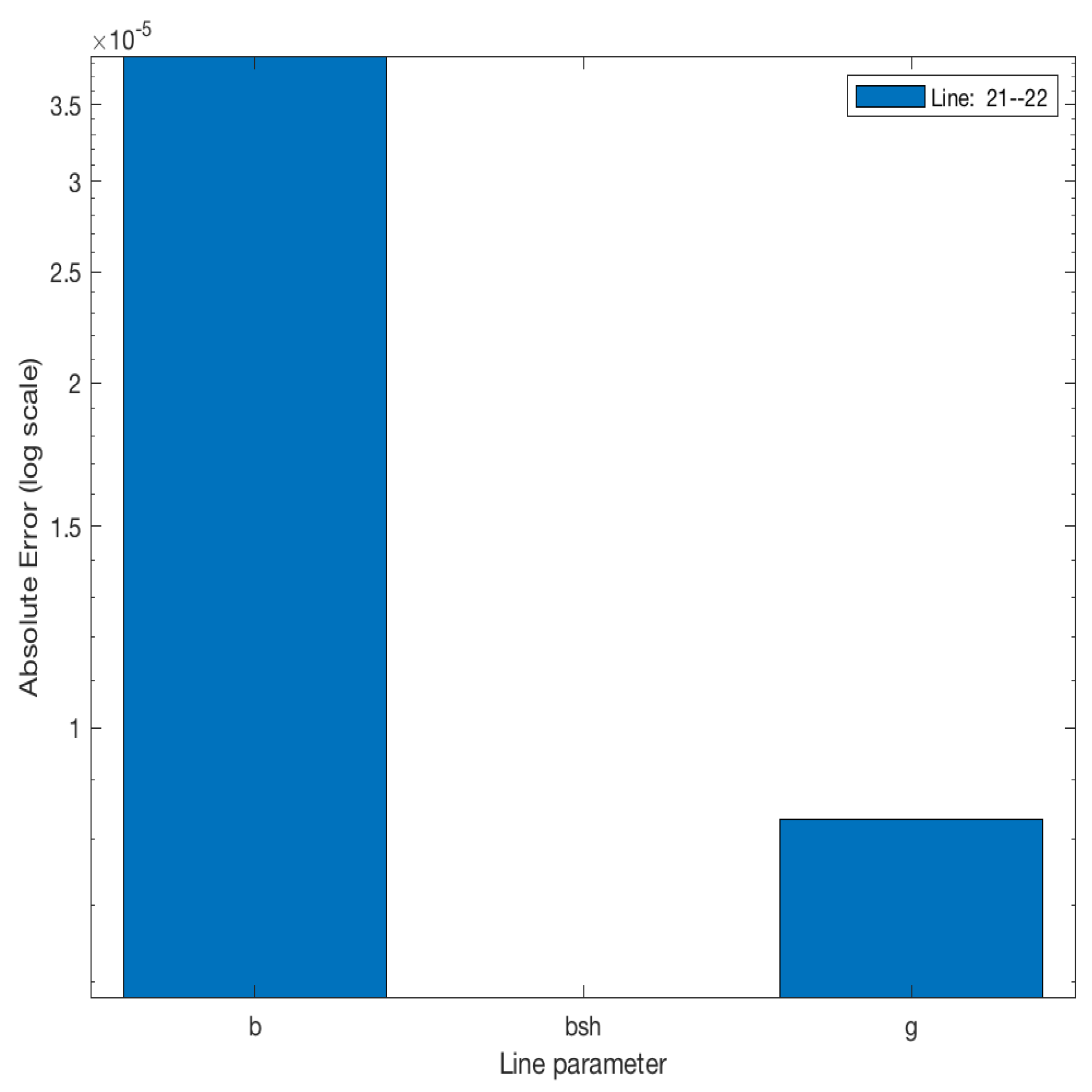
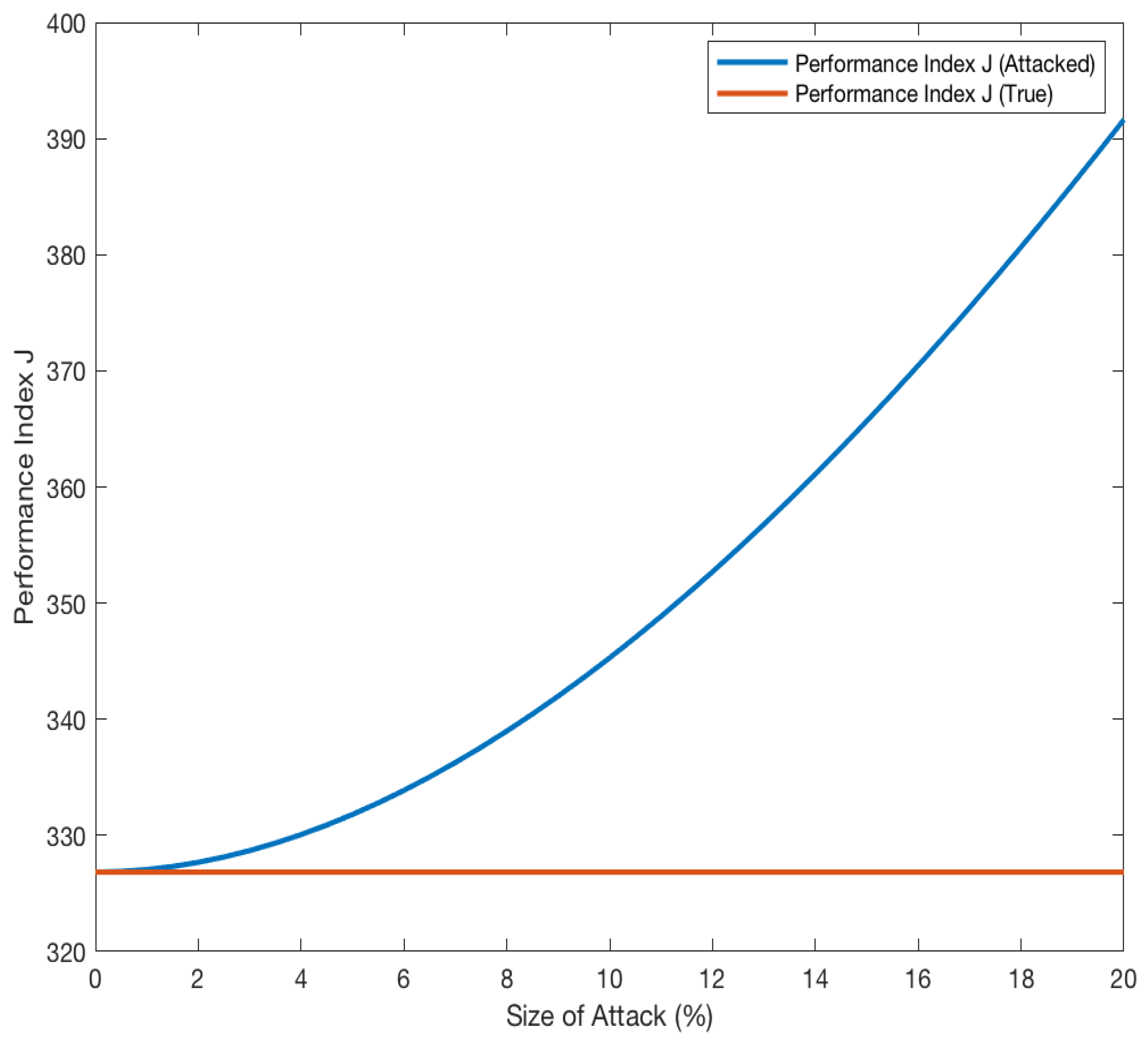
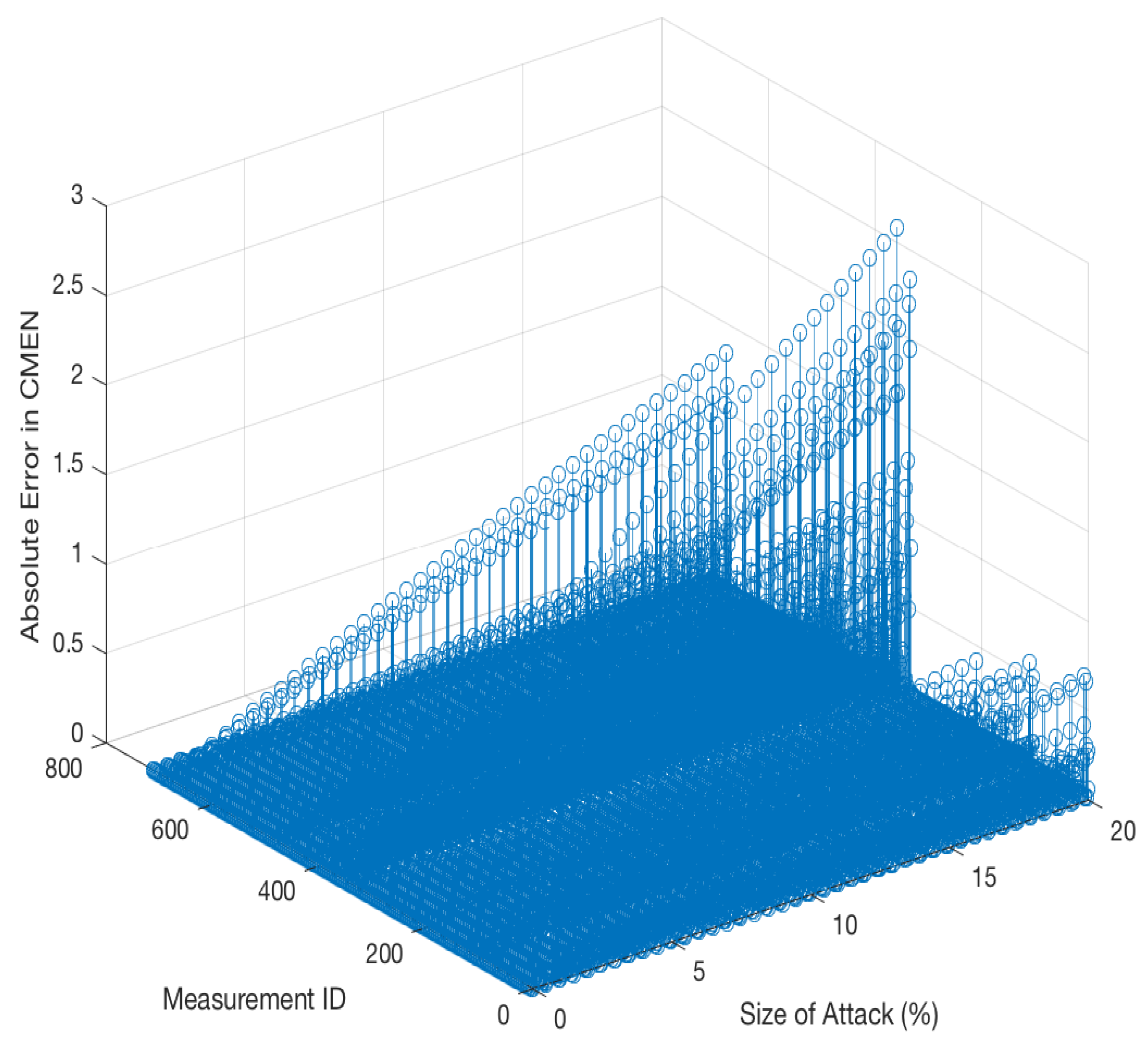
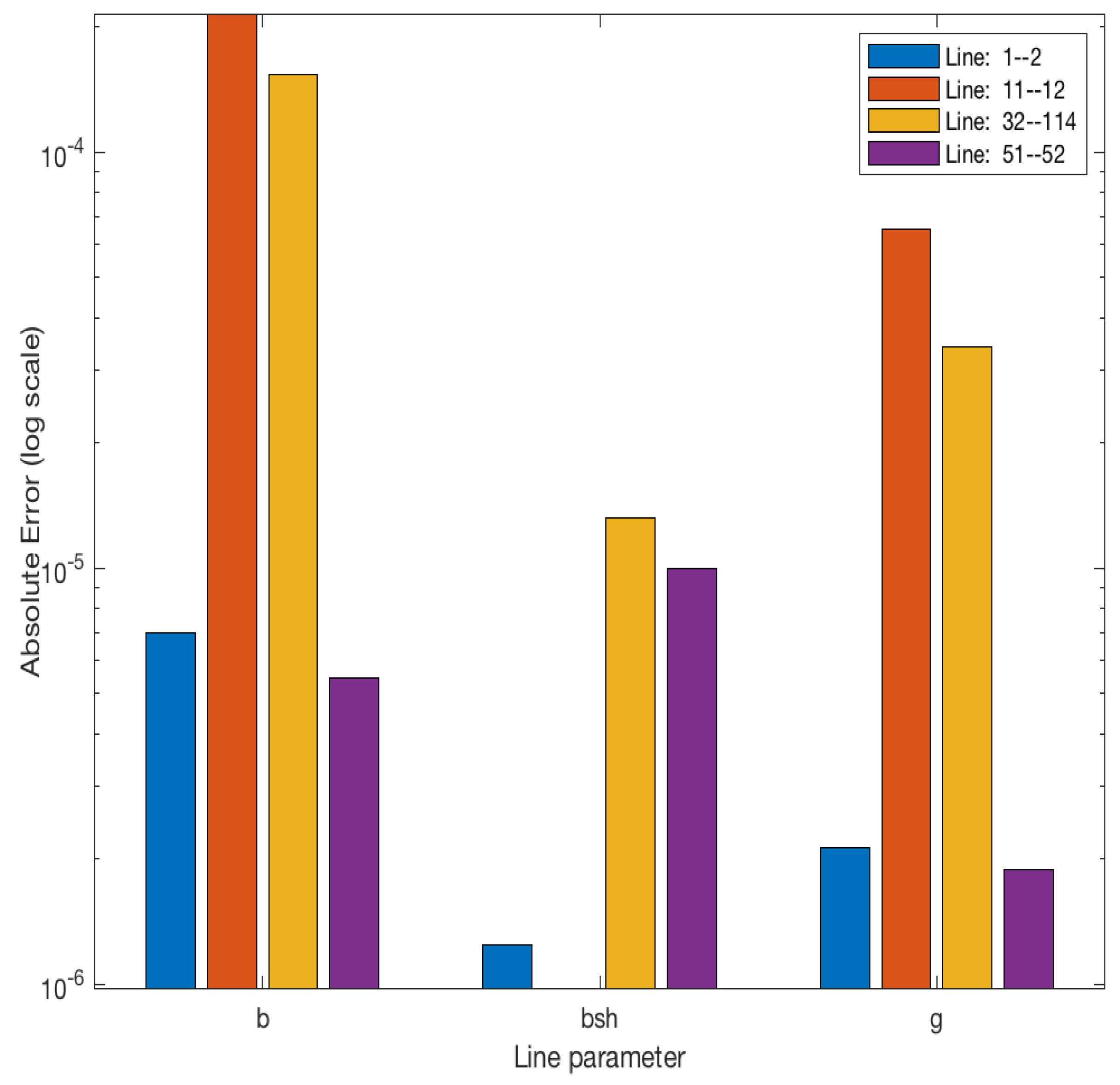
| Prediction Outcome | ||||
|---|---|---|---|---|
| Actual value | Normal | Anomaly | ||
| Normal | 17336 | 0 | Normal | |
| sample | sample | |||
| Anomaly | 3252 | 1012 | Anomaly | |
| sample | sample | |||
| Normal | Anomaly | |||
| Measurement | From Bus | To Bus | |
|---|---|---|---|
| Real Power Flow | 96 | 95 | 10.093 |
| Reactive Power Flow | 95 | 96 | 9.5299 |
| Reactive Power Flow | 94 | 95 | 7.9748 |
| Reactive Power Flow | 94 | 96 | 7.7034 |
| Real Power Flow | 94 | 95 | 6.3127 |
| Real Power Flow | 94 | 96 | 5.8595 |
| Real Power Injection | 95 | 95 | 4.0285 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Aljohani, N.; Bretas, A. A Bi-Level Model for Detecting and Correcting Parameter Cyber-Attacks in Power System State Estimation. Appl. Sci. 2021, 11, 6540. https://doi.org/10.3390/app11146540
Aljohani N, Bretas A. A Bi-Level Model for Detecting and Correcting Parameter Cyber-Attacks in Power System State Estimation. Applied Sciences. 2021; 11(14):6540. https://doi.org/10.3390/app11146540
Chicago/Turabian StyleAljohani, Nader, and Arturo Bretas. 2021. "A Bi-Level Model for Detecting and Correcting Parameter Cyber-Attacks in Power System State Estimation" Applied Sciences 11, no. 14: 6540. https://doi.org/10.3390/app11146540
APA StyleAljohani, N., & Bretas, A. (2021). A Bi-Level Model for Detecting and Correcting Parameter Cyber-Attacks in Power System State Estimation. Applied Sciences, 11(14), 6540. https://doi.org/10.3390/app11146540







