Credible Navigation Algorithm for GNSS Attack Detection Using Auxiliary Sensor System
Abstract
:1. Introduction
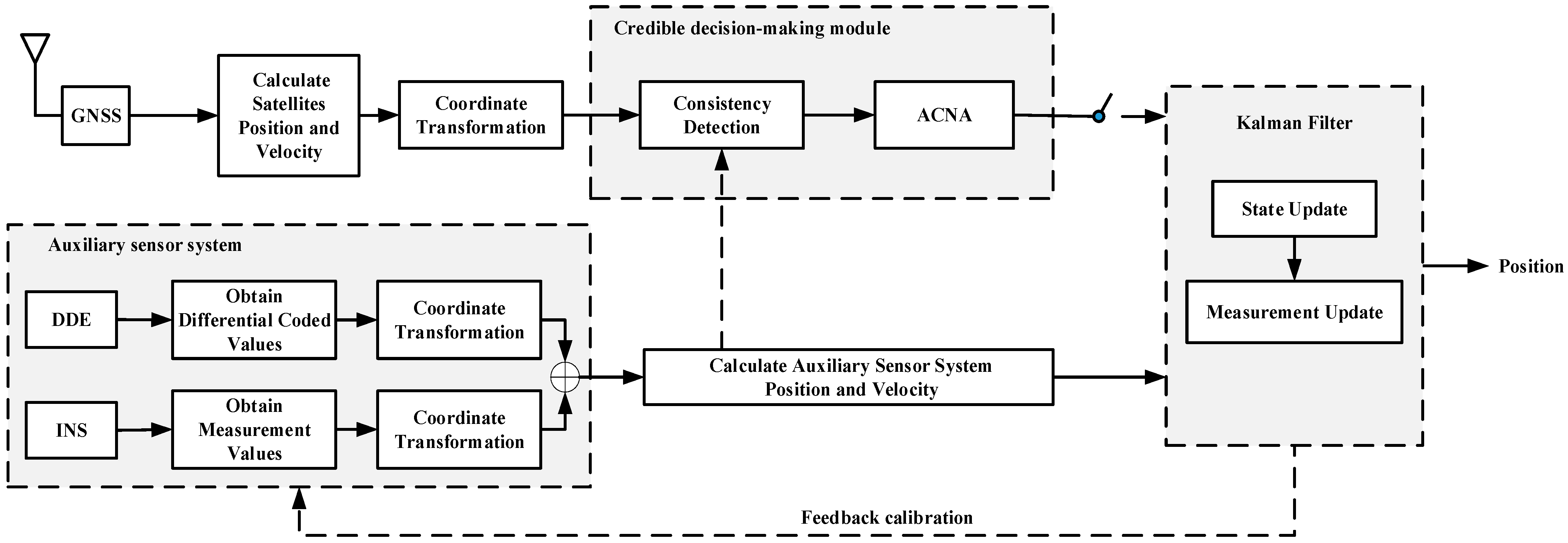
2. Credible Kalman Filter Model
2.1. Filter Model Description
2.2. GNSS Module
2.3. DDE/INS System Module
2.4. Credible Kalman Filter Model
3. Credible Navigation Algorithm
3.1. Algorithm Model
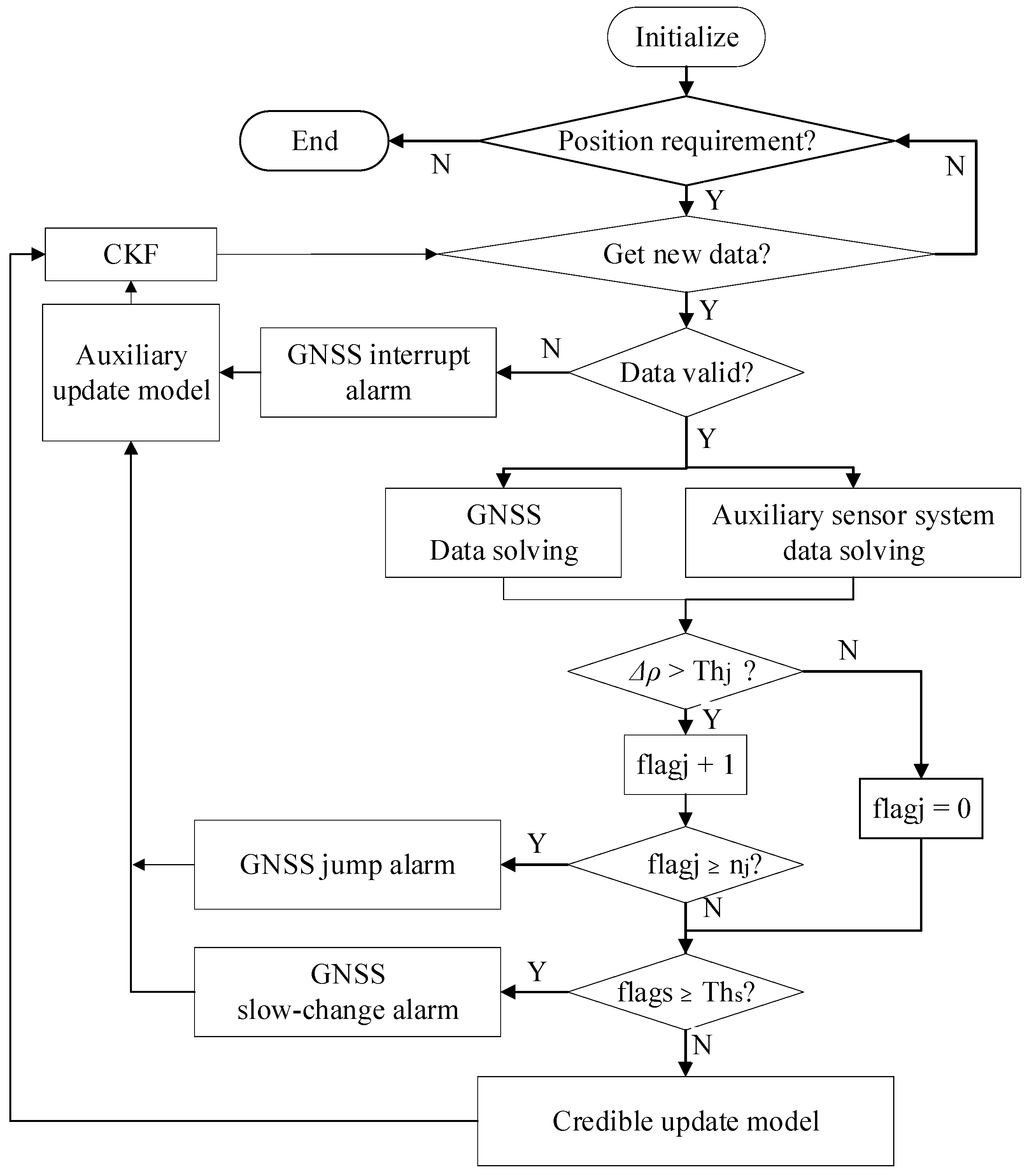
3.2. Algorithm Design
- Step 1: Initialization. Set the initial global position (converted to the navigation coordinate system) according to the GNSS signal acquired when the mobile terminal is initially at stationary. Initialize parameters , , , , and .
- Step 2: Decide whether there is a navigation and positioning requirement. If so, the GNSS receiver and auxiliary sensor will enter the working state and go to step 3; otherwise, go to step 8.
- Step 3: Determine whether the GNSS and auxiliary sensor system have new and valid input data. If the acquired information of GNSS and auxiliary sensor system is valid, the information of GNSS from global coordinates is converted to navigation coordinates, and the position unity with the auxiliary sensor system is realized to obtain and . Then, we go to step 4; if the effective information of the auxiliary navigation sensor system is obtained, and the GNSS positioning result is interrupted, the auxiliary update model is used to maintain the terminal position prediction, and we go to step 3 again; if no valid information is obtained, we go back to step 2.
- Step 4: Calculate GNSS drift at time k. If , then we have , and we go to step 5; otherwise, we have , and we go to step 6.
- Step 5: Determine the size of . If , we proceed to Step 6; if , it is determined that there is a GNSS jump attack, the GNSS is set as an untrusted navigation source, and the auxiliary update model is used to maintain the terminal position prediction at this time. If this happens, we reverse back to step 3.
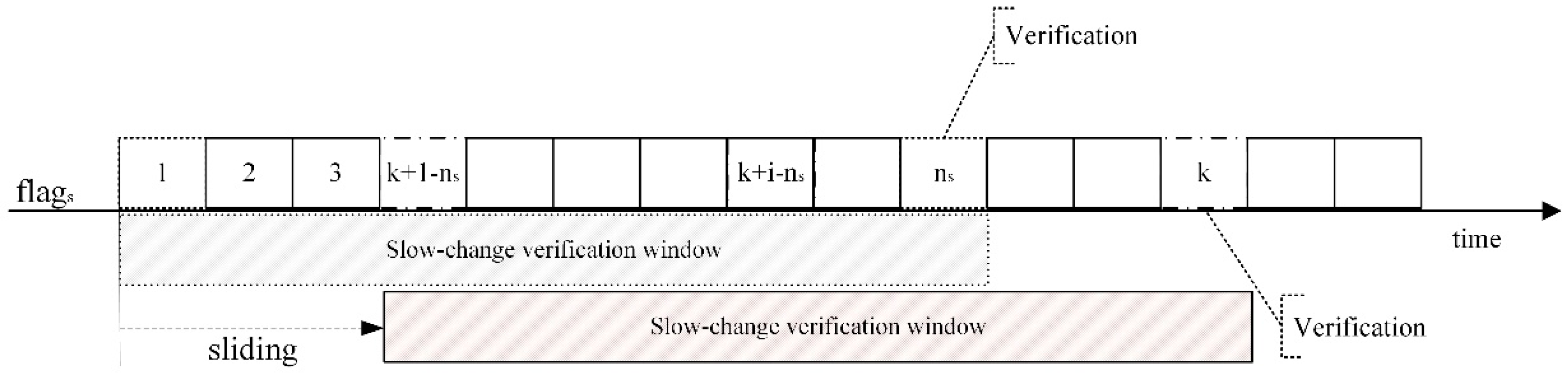
- Step 6: Calculate . If , it is determined that there is a GNSS slow-change attack, the GNSS is set as an untrusted navigation source, and the auxiliary update model is used to maintain the terminal position prediction. Then, we go back to step 3; otherwise, we continue to step 7.
- Step 7: GNSS is in a credible stage. The credible update model is used to maintain the terminal position output, and then we go to step 3 again.
- Step 8: End.
4. Performance Evaluation
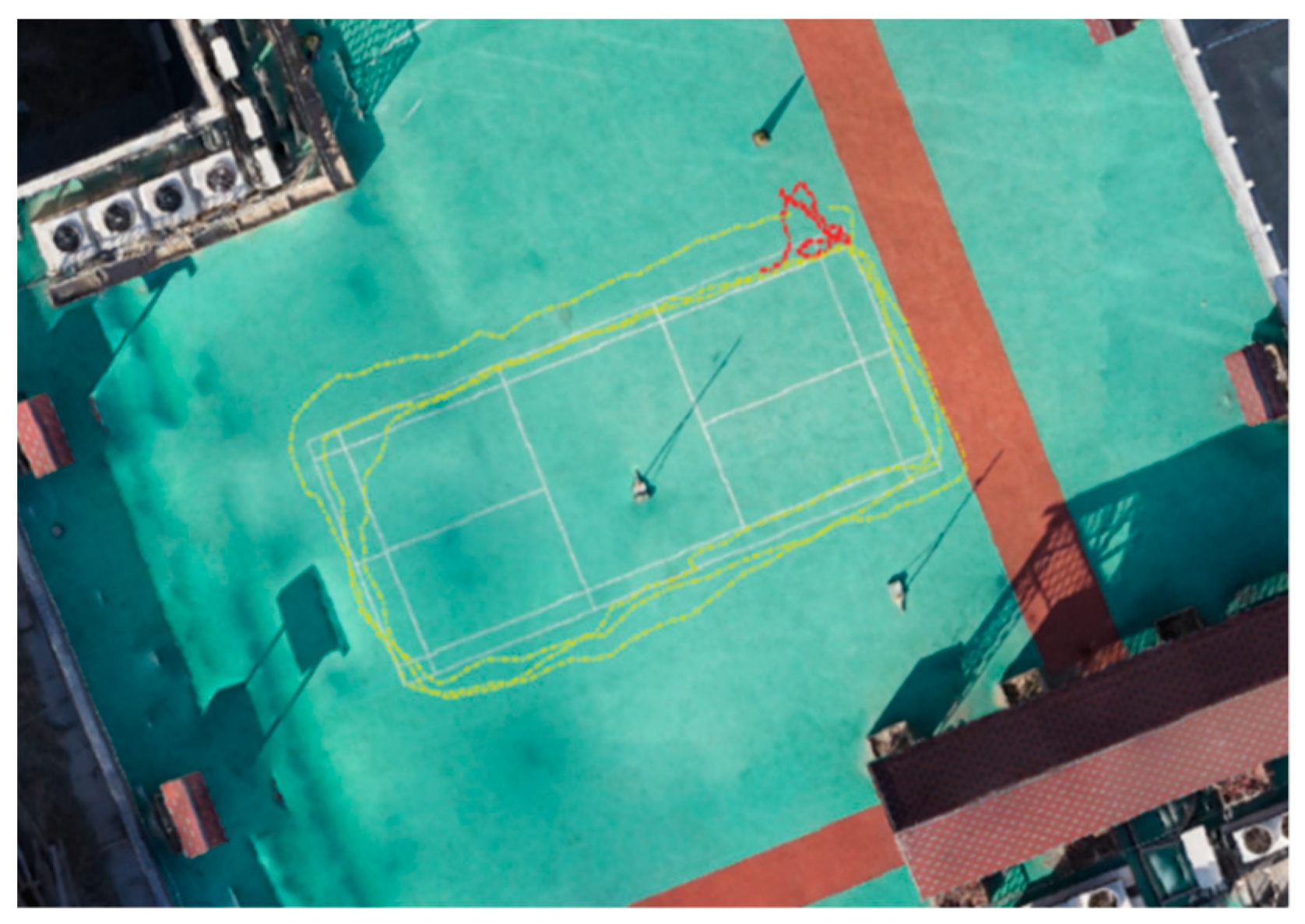
4.1. Experimental Platform and Data Set
4.2. Simulation Results
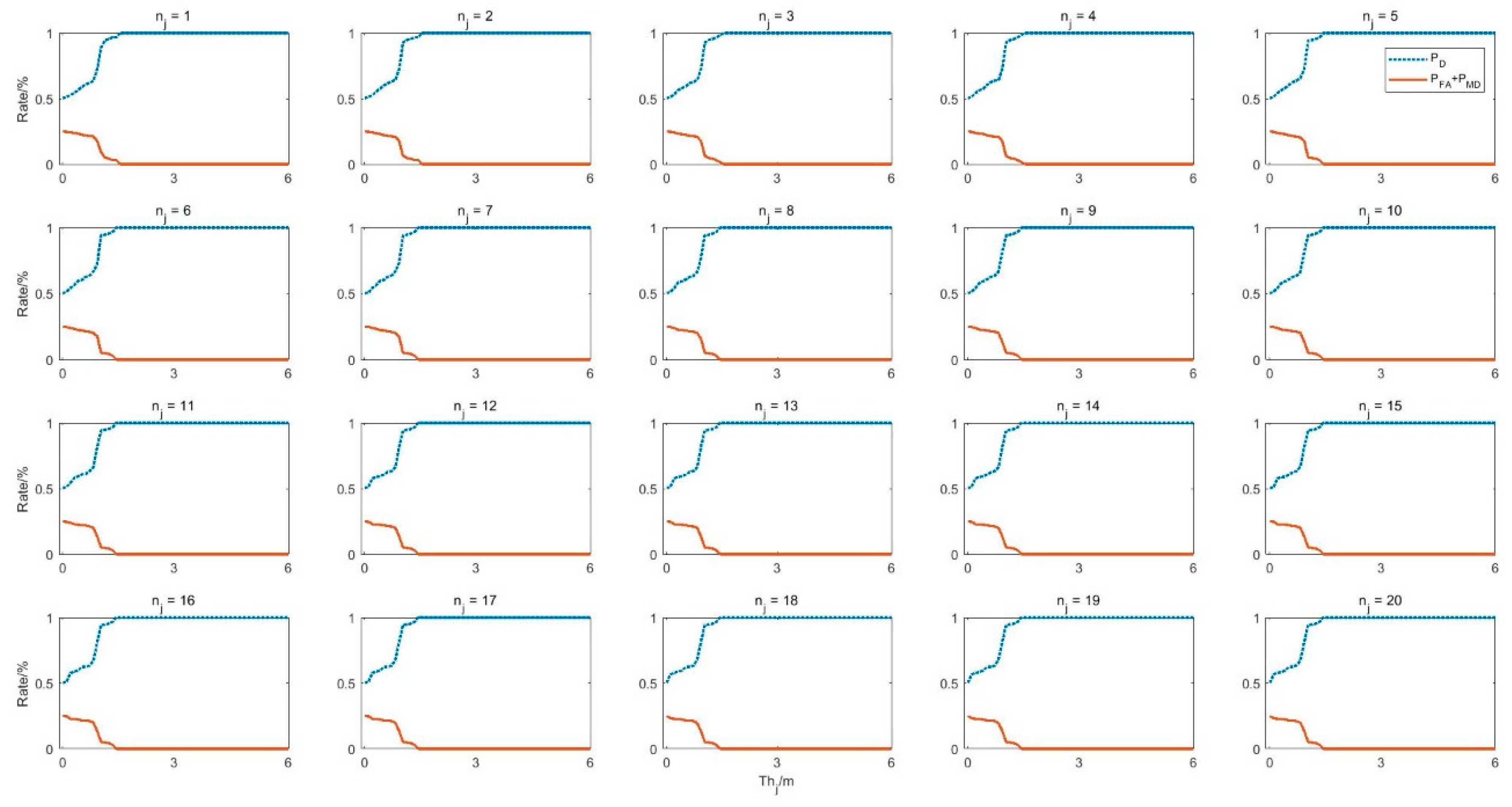
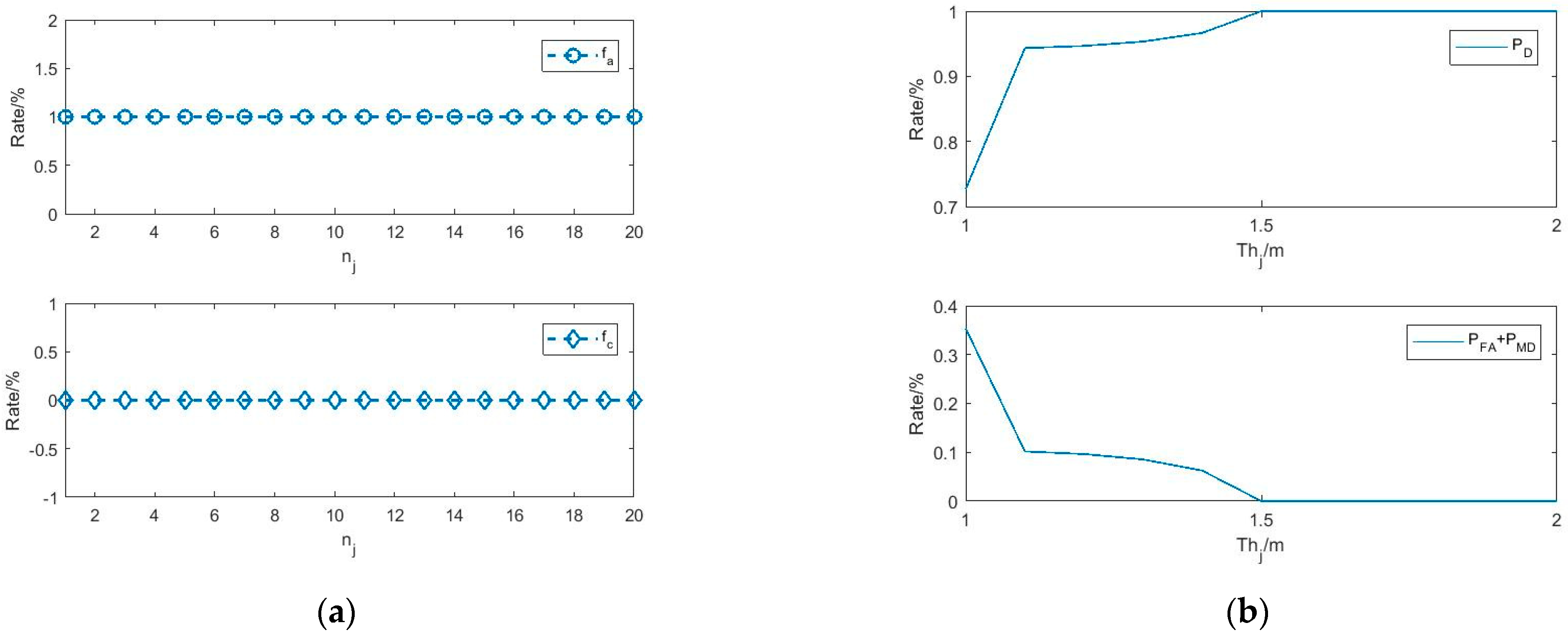
4.3. Parameter Analysis
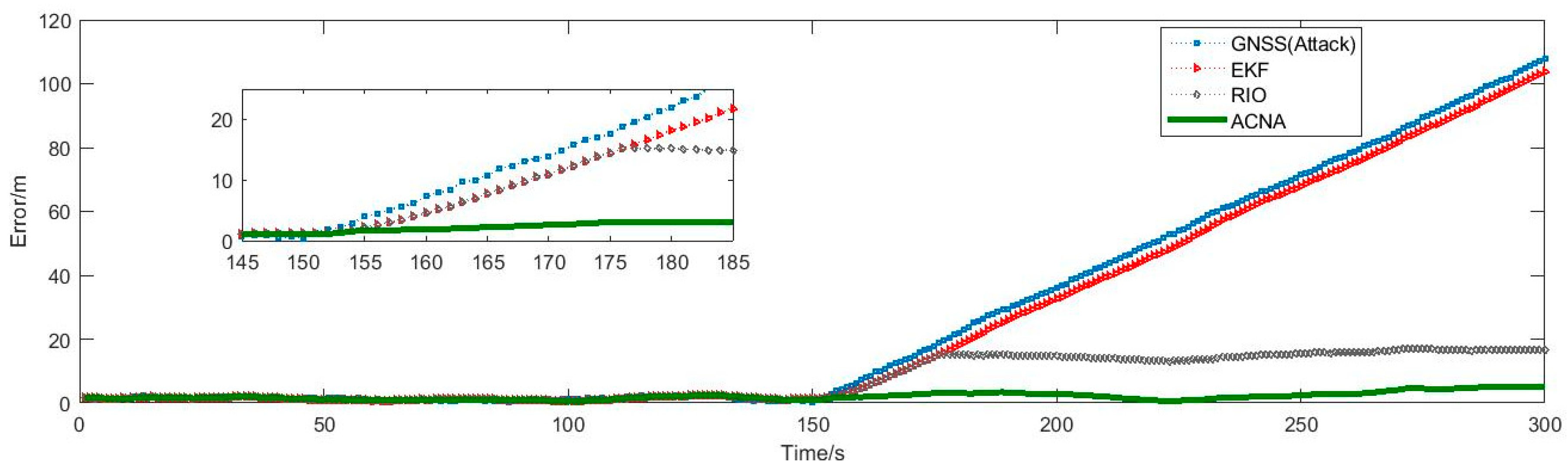
5. Experimental Analysis
5.1. Results of Data Set
5.2. Results of Data Set
5.3. Results of Data Set
5.4. Positioning Accuracy Deterioration Factor
5.5. Detection Latency
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Junzhi, L.; Wanqing, L.; Qixiang, F.; Beidianet, L. Research progress of GNSS spoofing and spoofing detection technology. In Proceedings of the 19th International Conference on Communication Technology (ICCT), Xi’an, China, 16–19 October 2019; pp. 1360–1369. [Google Scholar]
- Kerns, A.J.; Shepard, D.P.; Bhatti, J.A.; Humphreys, T.E. Unmanned aircraft capture and control via GPS spoofing. J. Field Robot. 2014, 31, 617–636. [Google Scholar] [CrossRef]
- Ruegamer, A.; Kowalewski, D. Jamming and spoofing of GNSS signals—An underestimated risk?! Proc. Wisdom Ages Chall. Mod. World 2015, 3, 17–21. [Google Scholar]
- Jafarnia-Jahromi, A.; Fadaei, N.; Daneshmand, S.; Broumandan, A.; Lachapelle, G. A review of pre-despreading GNSS interference detection techniques. In Proceedings of the 5th International Colloquium on Scientific and Fundamental Aspects of the Galileo Programme, Braunschweig, Germany, 27–29 October 2015; pp. 1–8. [Google Scholar]
- Parkinson, S.; Ward, P.; Wilson, K.; Miller, J. Cyber threats facing autonomous and connected vehicles: Future challenges. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2898–2915. [Google Scholar] [CrossRef]
- Mit, R.; Zangvil, Y.; Katalan, D. Analyzing Tesla’s level 2 autonomous driving system under different GNSS spoofing scenarios and implementing connected services for authentication and reliability of GNSS data. In Proceedings of the 33rd International Technical Meeting of the Satellite Division of The Institute of Navigation (ION GNSS+ 2020), Online, 22–25 September 2020; pp. 621–646. [Google Scholar]
- Fabio, D. (Ed.) GNSS Interference Threats and Countermeasures; Artech House: Norwood, MA, USA, 2015. [Google Scholar]
- Zhou, M.; Li, H.; Wang, C.; Ma, T.; Lu, M. Induced spoofing detection of global navigation satellite system. J. Natl. Univ. Def. Technol. 2019, 41, 129–135. [Google Scholar]
- Psiaki, M.L.; Humphreys, T.E. GNSS spoofing and detection. Proc. IEEE 2016, 104, 1258–1270. [Google Scholar] [CrossRef]
- Huang, J.; Presti, L.L.; Motella, B.; Pini, M. GNSS spoofing detection: Theoretical analysis and performance of the Ratio Test metric in open sky. Ict Express 2016, 2, 37–40. [Google Scholar] [CrossRef] [Green Version]
- Yuan, D.; Li, H.; Wang, F. A GNSS acquisition method with the capability of spoofing detection and mitigation. Chin. J. Electron. 2018, 27, 213–222. [Google Scholar] [CrossRef]
- Bian, S.F.; Hu, Y.F.; Ji, B. Research status and prospect of GNSS anti-spoofing technology. Sci. Sin. Inf. 2017, 47, 275–287. (In Chinese) [Google Scholar] [CrossRef]
- Wesson, K.; Rothlisberger, M.; Humphreys, T. Practical cryptographic civil GNSS signal authentication. Navig. J. Inst. Navig. 2012, 59, 177–193. [Google Scholar] [CrossRef]
- Kerns, A.J.; Wesson, K.D.; Humphreys, T.E. A blueprint for civil GNSS navigation message authentication. In Proceedings of the 2014 IEEE/ION Position, Location and Navigation Symposium—PLANS 2014, Monterey, CA, USA, 5–8 May 2014; pp. 262–269. [Google Scholar]
- O’Driscoll, C. What is navigation message authentication? Inside GNSS. 1 January 2018. Available online: https://insidegnss.com/what-is-navigation-message-authentication/ (accessed on 2 June 2021).
- Zhang, X.; Pang, J.; Su, Y.; Ou, G. Spoofing detection technique on antenna array carrier phase double difference. J. Natl. Univ. Def. Technol. 2014, 36, 55–60. [Google Scholar]
- Jafarnia Jahromi, A.; Broumandan, A.; Nielsen, J.; Lachapelle, G. GNSS spoofer countermeasure effectiveness based on signal strength, noise power, and C/N0 measurements. Int. J. Satell. Commun. Netw. 2012, 30, 181–191. [Google Scholar] [CrossRef]
- Dehghanian, V.; Nielsen, J.; Lachapelle, G. GNSS spoofing detection based on signal power measurements: Statistical analysis. Int. J. Navig. Obs. 2012, 2012, 313527. [Google Scholar] [CrossRef] [Green Version]
- Sharifi-Tehrani, O.; Sabahi, M.F.; Danaee, M.R. Low-complexity framework for GNSS jamming and spoofing detection on moving platforms. IET Radar Sonar Navig. 2020, 14, 2027–2038. [Google Scholar] [CrossRef]
- Li, J.; Li, H.; Lu, M. One-dimensional traversal receiver autonomous integrity monitoring method based on maximum likelihood estimation for GNSS anti-spoofing applications. IET Radar Sonar Navig. 2020, 14, 1888–1896. [Google Scholar] [CrossRef]
- Lai, Q.; Yuan, H.; Wei, D.; Wang, N.; Li, Z.; Ji, X. A Multi-Sensor Tight Fusion Method Designed for Vehicle Navigation. Sensors 2020, 20, 2551. [Google Scholar] [CrossRef] [PubMed]
- Lee, J.H.; Kwon, K.C.; An, D.S.; Shim, D.S. GPS spoofing detection using accelerometers and performance analysis with probability of detection. Int. J. Control. Autom. Syst. 2015, 13, 951–959. [Google Scholar] [CrossRef]
- Broumandan, A.; Lachapelle, G. Spoofing detection using GNSS/INS/odometer coupling for vehicular navigation. Sensors 2018, 18, 1305. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Melendez-Pastor, C.; Ruiz-Gonzalez, R.; Gomez-Gil, J. A data fusion system of GNSS data and on-vehicle sensors data for improving car positioning precision in urban environments. Expert Syst. Appl. 2017, 80, 28–38. [Google Scholar] [CrossRef]
- Majidi, M.; Erfanian, A.; Khaloozadeh, H. Prediction-discrepancy based on innovative particle filter for estimating UAV true position in the presence of the GPS spoofing attacks. IET Radar Sonar Navig. 2020, 14, 887–897. [Google Scholar] [CrossRef]
- Yimin, W.; Hong, L.; Mingquan, L. Spoofing profile estimation based GNSS spoofing identification method for tightly coupled MEMS INS/GNSS integrated navigation system. IET Radar Sonar Navig. 2019, 14, 216–225. [Google Scholar] [CrossRef]
- Nebot, E.; Sukkarieh, S.; Durrant-Whyte, H. Inertial navigation aided with GPS information. In Proceedings of the 4th Annual Conference on Mechatronics and Machine Vision in Practice, Toowoomba, Australia, 22–24 September 1997; pp. 169–174. [Google Scholar]
- Rapoport, L.; Gribkov, M.; Khvalkov, A.; Pesterev, A.; Tkachenko, M. Control of wheeled robots using GNSS and inertial navigation: Control law synthesis and experimental results. Constraints 2006, 10, 2. [Google Scholar]
- Feng, S.; Ochieng, W.Y.; Walsh, D.; Ioannides, R. A measurement domain receiver autonomous integrity monitoring algorithm. GPS Solut. 2006, 10, 85–96. [Google Scholar] [CrossRef]
- Zhao, L.; Ochieng, W.Y.; Quddus, M.A.; Noland, R.B. An extended Kalman filter algorithm for integrating GPS and low-cost dead reckoning system data for vehicle performance and emissions monitoring. J. Navig. 2003, 56, 257–275. [Google Scholar] [CrossRef] [Green Version]











| Sensor | Model | Sensor Error | Sample Rate |
|---|---|---|---|
| RTK | MXT906A | Horizontal position accuracy RTK 0.025 m | 1 Hz |
| GNSS | NEO-6M | Horizontal position accuracy GPS 2.5 m | 1 Hz |
| Accelerometer | MPU9250 | Noise power Spectral Density | 10 Hz |
| Gyroscope | MPU9250 | Rate Noise Spectral Density | 10 Hz |
| Magnetometer | MPU9250 | Sensitivity Scale Factor | 10 Hz |
| DDE | JGB37-520 | Max Encoder 495 | 10 Hz |
| Type | Initial State of the Trajectory |
|---|---|
| Lan/Lon/Height | 40.0702° N/116.2747° E/54.63 m |
| Heading/Roll/Yaw | 0°, 0°, 248° |
| Algorithm | ||||||
|---|---|---|---|---|---|---|
| GNSS | 10.17 | 9.88 | 13.47 | 21.11 | 20.83 | 29.42 |
| EKF | 9.92 | 9.80 | 13.24 | 21.08 | 20.83 | 28.89 |
| RIO | 1.21 | 1.86 | 1.39 | 2.48 | 5.79 | 5.80 |
| ACNA | 1.06 | 1.63 | 1.14 | 2.01 | 4.94 | 5.02 |
| Algorithm | ||||||
|---|---|---|---|---|---|---|
| GNSS | 24.69 | 24.55 | 34.27 | 76.39 | 75.97 | 107.73 |
| EKF | 23.56 | 23.52 | 32.76 | 73.33 | 73.52 | 103.84 |
| RIO | 5.14 | 5.44 | 6.77 | 11.76 | 13.75 | 17.06 |
| ACNA | 1.07 | 1.66 | 1.17 | 2.01 | 5.05 | 5.12 |
| Algorithm | ||||||
|---|---|---|---|---|---|---|
| GNSS | 8.67 | 8.78 | 11.80 | 25.34 | 24.70 | 35.39 |
| EKF | 7.80 | 8.04 | 10.65 | 22.89 | 22.41 | 32.03 |
| RIO | 5.11 | 5.40 | 6.75 | 12.01 | 13.93 | 17.37 |
| ACNA | 0.78 | 0.97 | 0.81 | 2.01 | 3.38 | 3.38 |
| Algorithm | ||||
|---|---|---|---|---|
| GNSS | 0.59 | 11.80 | 20.01 | / |
| EKF | 0.53 | 10.65 | 20.16 | −0.74% |
| RIO | 0.53 | 6.75 | 12.77 | 36.19% |
| ACNA | 0.54 | 0.81 | 1.49 | 92.53% |
| Algorithm | After GNSS Jump Attacks | After GNSSS low-Change Attacks |
|---|---|---|
| EKF | / | / |
| RIO | 1 s | 27 s |
| ACNA | 2 s | 5 s |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, J.; Wu, H.; Guo, X.; Li, S.; Gong, Y.; Zhang, Y.; Li, Y. Credible Navigation Algorithm for GNSS Attack Detection Using Auxiliary Sensor System. Appl. Sci. 2021, 11, 6321. https://doi.org/10.3390/app11146321
Song J, Wu H, Guo X, Li S, Gong Y, Zhang Y, Li Y. Credible Navigation Algorithm for GNSS Attack Detection Using Auxiliary Sensor System. Applied Sciences. 2021; 11(14):6321. https://doi.org/10.3390/app11146321
Chicago/Turabian StyleSong, Jiahui, Haitao Wu, Xuqiang Guo, Siyuan Li, Yingkui Gong, Yang Zhang, and Yaping Li. 2021. "Credible Navigation Algorithm for GNSS Attack Detection Using Auxiliary Sensor System" Applied Sciences 11, no. 14: 6321. https://doi.org/10.3390/app11146321
APA StyleSong, J., Wu, H., Guo, X., Li, S., Gong, Y., Zhang, Y., & Li, Y. (2021). Credible Navigation Algorithm for GNSS Attack Detection Using Auxiliary Sensor System. Applied Sciences, 11(14), 6321. https://doi.org/10.3390/app11146321





