Attacks and Preventive Measures on Video Surveillance Systems: A Review
Abstract
1. Introduction
Motivation and Our Contribution
2. Attacks on VSS
2.1. Visual Layer Attacks
2.2. Covert Channel Attacks
- Manipulating CCTV/VSS infrared LEDs: by sending command/control data to the VSS cameras by using the infrared LED messages;
- A new type of optical covert channel named (VisisSploit) leaks data through a computer LCD display;
- Network-based covert channels can be created to coordinate distributed denial of service attacks, bypassing the user firewall. For example, the IPv4 header TTL field can be used to carry information into or out of a network domain.
2.3. Steganography Attacks
2.4. Pan–Tilt–Zoom Attacks
2.5. Denial of Service and Jamming Attacks
2.6. Malware Attack
2.7. Privilege Escalation Attack
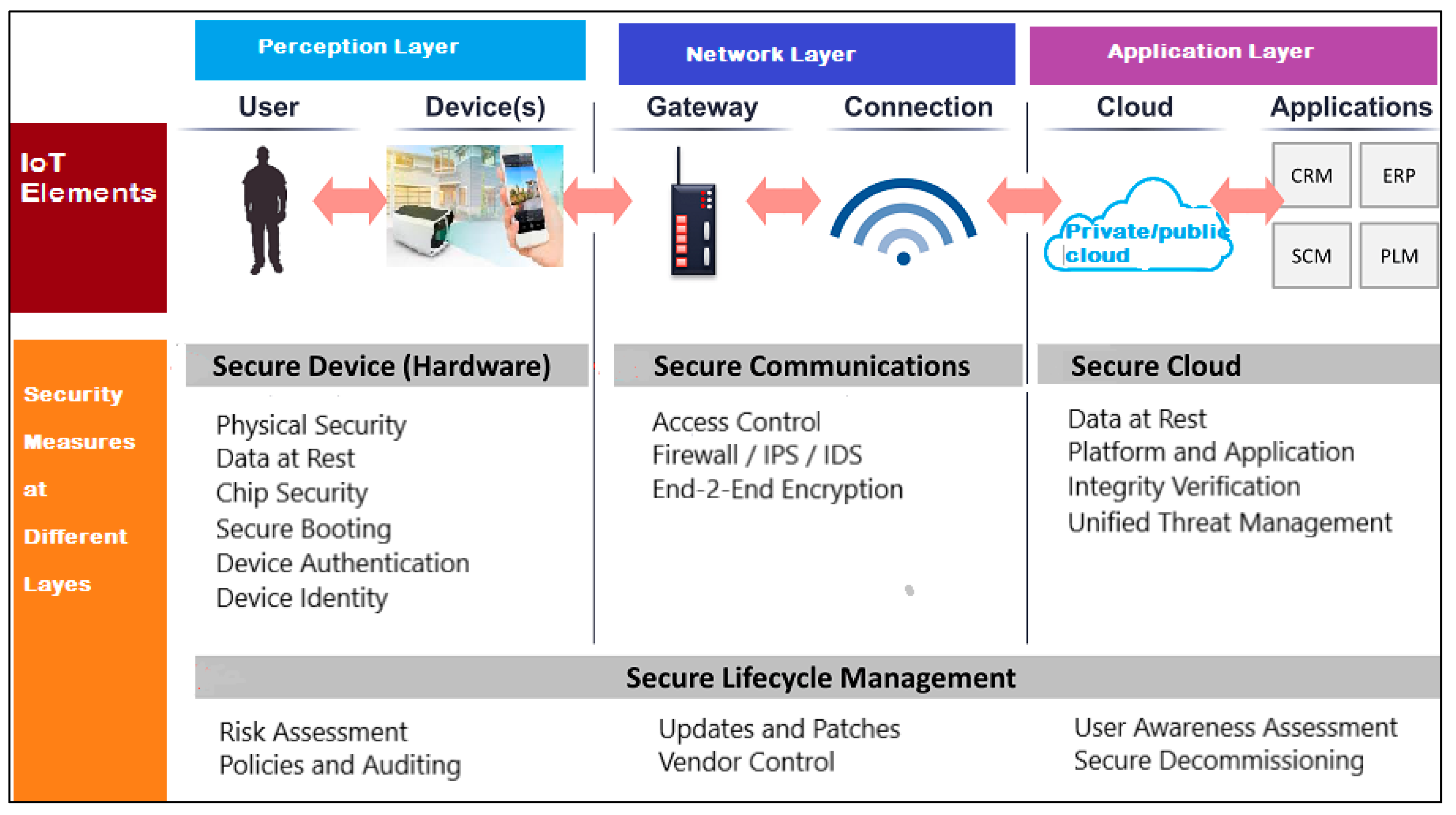
3. Security Measures for VSS
- Installation and regular updating of the anti-virus application is the foremost step to defend against malicious attacks.
- Network topology and configuration of a system is critical in maintaining the security of IP-based cameras, as there are multiple entry gateways through which it can be attacked. Configuration access is the key to provide security to the system. A local network system with a firewall and virtual private network (VPN) software for remote access is always safe. A secure, encrypted connection is a barrier for any attackers before they can go through a firewall.An alternative solution could be to use a cloud-connected IP security camera. In this type of locally connected system, rather than relying on a password to gain access to the firewall of a camera system, cloud-connected IP security cameras will communicate with a secured cloud-based server over an encrypted connection. Users can gain access by linking up their devices with those servers. Cloud-connected devices have the added advantage of continuous monitoring over locally connected systems.
- Using a unique, lengthy and unpredictable password for each camera is a good starting point. This is especially critical for a port forwarding system. However, if a system employs VPN, having a single secured password for all connected cameras is enough. As a rule, changing passwords every 90 days is recommended.
- Priority should be given to provide cybersecurity training to all employees who may have access to a central video surveillance system and all personnel must be made aware of cyber security guidelines.
- In case of security breaches, a cybersecurity incident response team can be constituted to respond to such emergencies.
- All latest software/firmware updates must be promptly applied as and when they are released by the manufacturers.
- If a cloud-based system is deployed, only authentic verified vendors should be chosen.
- One must be aware of all the latest cyber security standards being adopted as well as study all recent attacks to gain a better understanding of new techniques employed by attackers.
4. Review and Analysis of Existing VSS Frameworks
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Market Analysis Report. Available online: https://www.grandviewresearch.com/industry-analysis/smart-home-security-camera-market (accessed on 15 May 2021).
- Yan, W.Q.; Zhou, L.; Shu, Y.; Yu, J. CVSS: A Cloud-Based Visual Surveillance System. Int. J. Digit. Crime For. 2018, 10, 79–91. [Google Scholar]
- Shodan. Available online: https://www.shodan.io/ (accessed on 2 November 2020).
- The Mirai Botnet Explained: How Teen Scammers and CCTV Cameras almost Brought Down the Internet. Available online: https://www.csoonline.com/article/3258748/the-mirai-botnet-explained-how-teen-scammers-and-cctv-cameras-almost-brought-down-the-internet.html (accessed on 15 May 2021).
- CyberScoop. Available online: https://www.cyberscoop.com/washington-dc-ransomware-dc-police-department/ (accessed on 15 May 2021).
- Dozens of Canon Security Cameras Hacked in Japan. Available online: https://english.kyodonews.net/news/2018/05/91ec861ae24d-dozens-of-security-cameras-hacked-in-japan.html?phrase=ham%20fighters&words= (accessed on 15 May 2021).
- Bosch IP Camera Vulnerability (CVE-2018-19036). Available online: https://psirt.bosch.com/security-advisories/bosch-2018-1202.html (accessed on 15 May 2021).
- Vulners. Available online: https://vulners.com/talos/TALOS-2018-0565 (accessed on 15 May 2021).
- Your Smart Camera May Have Been Spying on You. Available online: https://www.cnet.com/home/smart-home/your-smart-camera-may-have-been-spying-on-you/ (accessed on 15 May 2021).
- Critical Flaw Lets Hackers Take Control of Samsung SmartCam Cameras. Available online: https://www.computerworld.com/article/3158204/critical-flaw-lets-hackers-take-control-of-samsung-smartcam-cameras.html (accessed on 15 May 2021).
- Major Vulnerabilities and Exploit in Foscam Cameras. Available online: https://www.vdoo.com/blog/vdoo-has-found-major-vulnerabilities-in-foscam-cameras (accessed on 15 May 2021).
- India Today. Available online: https://www.indiatoday.in/mail-today/story/installation-of-1-4-lakh-chinese-cctv-cameras-by-delhi-govt-sparks-row-1696032-2020-07-02 (accessed on 15 May 2021).
- Kao, I.-L. Securing Mobile Devices in the Business Environment; IBM Global Technology Services–Thought Leadership White Paper; IBM: Armonk, NY, USA, 2011. [Google Scholar]
- Becher, M.; Freiling, F.C.; Hoffmann, J.; Holz, T.; Uellenbeck, S.; Wolf, C. Mobile Security Catching Up? Revealing the Nuts and Bolts of the Security of Mobile Devices. In Proceedings of the 2011 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 22–25 May 2011; pp. 96–111. [Google Scholar]
- McAfee Labs. McAfee Threats Report: First Quarter 2013; McAffe Press: San Jose, CA, USA, 2013; Available online: http://www.mcafee.com/us/resources/re-ports/rpquarterly-threat-q (accessed on 15 May 2021).
- F-Secure Labs. Mobile Threat Report January-March 2013; F-Secure Labs: Helsinki, Finland, 2013; Available online: http://www.f-secure.com/static/doc/labs_global!Research/Mobile_Threat_Report_Q1_2013 (accessed on 15 May 2021).
- Stites, D.; Tadimla, A. A Survey of Mobile Device Security, Threats, Vulnerabilities and Defences. 2011. Available online: http//afewguys cod-ing.com/2011/12/survey-mobile-device-security-threats vulnerabilities-defences (accessed on 15 May 2021).
- Enck, W.; Gilbert, P.; Chun, B.G.; Cox, L.P.; Jung, J.; McDaniel, P.; Sheth, A.P.; Droid, T. An Information on Tracking System for Real Time Privacy Monitoring on Smart-Phones. In Proceedings of the 9th USENIX Conference on Operating Systems Design and Implementation, Vancouver, BC, Canada, 4–6 October 2010; USENIX Association: Berkeley, CA, USA, 2020; pp. 1–6. [Google Scholar]
- Franklin, J.; Brown, C.; Dog, S.; McNab, N.; Voss-Northrop, S.; Peck, M.; Stidham, B. Assessing Threats to Mobile Devices & Infrastructure NISTIR 8144. Available online: https://csrc.nist.gov/CSRC/media/Publications/nistir/8144/draft/documents/nistir8144_draft.pdf (accessed on 15 May 2021).
- Zheng, P.; Lionel, M.N. Spotlight: The rise of the smartphone. IEEE Distrib. Syst. Online 2006, 7, 3. [Google Scholar] [CrossRef]
- Liranzo, J.; Hayajneh, T. Security and Privacy Issues Affecting Cloud-Based IP camera. In Proceedings of the 2017 IEEE 8th Annual Ubiquitous Computing, Electronics and Mobile Communication Conference (UEMCON), New York, NY, USA, 19–21 October 2017; pp. 458–465. [Google Scholar]
- Hoque, N.; Bhuyan, M.H.; Baishya, R.C.; Bhattacharyya, D.K.; Kalita, J.K. Network attacks: Taxonomy, tools and systems. J. Netw. Comput. Appl. 2014, 40, 307–324. [Google Scholar] [CrossRef]
- Rytel, M.; Felkner, A.; Janiszewski, M. Towards a Safer Internet of Things—A Survey of IoT Vulnerability Data Sources. Sensors 2020, 20, 5969. [Google Scholar] [CrossRef]
- Costin, A. Poor Man’s Panopticon: Mass CCTV Surveillance for the Masses. Available online: http://andreicostin.com/papers/poc2013_andrei.slides.pdf (accessed on 15 May 2021).
- Mowery, K.; Wustrow, E.; Wypych, T.; Singleton, C.; Comfort, C.; Rescorla, E.; Halderman, J.A.; Shacham, H.; Checkoway, S. Security analysis of a full-body scanner. In 23rd USENIX Security Symposium USENIX Security 14; USENIX Association: San Diego, CA, USA, 2014; pp. 369–384. [Google Scholar]
- Jones, E.; Le Moigne, O.; Robert, J.-M. IP traceback solutions based on time to live covert channel. In Proceedings of the 2004 12th IEEE International Conference on Networks (ICON 2004) (IEEE Cat. No. 04EX955), Singapore, 19 November 2004; pp. 451–457. [Google Scholar]
- Alcaraz, C.; Bernieri, G.; Pascucci, F.; Lopez, J.; Setola, R. Covert Channels-Based Stealth Attacks in Industry 4.0. IEEE Syst. J. 2019, 13, 3980–3988. [Google Scholar] [CrossRef]
- Guri, M.; Hasson, O.; Kedma, G.; Elovici, Y. Visisploit: An optical covert-channel. arXiv 2016, arXiv:1607.03946. [Google Scholar]
- Sloan, T.; Hernandez-Castro, J. Forensic analysis of video steganography tools. PeerJ Comput. Sci. 2015, 1, e7. [Google Scholar] [CrossRef]
- Senthil, M. CCTV Surveillance System, attacks and design goals. Int. J. Electr. Comput. Eng. 2018, 8, 2072–2082. [Google Scholar] [CrossRef]
- Maharjan, R.; Shrestha, A.K.; Basnet, R. Image Steganography: Protection of Digital Properties against Eavesdrop-ping. arXiv 2019, arXiv:1909.04685. [Google Scholar]
- Yin, J.; Fen, G.; Mughal, F.; Iranmanesh, V. Internet of Things: Securing Data using Image Steganography. In Proceedings of the 2015 3rd International Conference on Artificial Intelligence, Modelling and Simulation (AIMS), Kota Kinabalu, Malaysia, 2–4 December 2015. [Google Scholar] [CrossRef]
- Zhang, Y.-Y.; Li, X.-Z.; Liu, Y.-A. The detection and defence of DoS attack for wireless sensor network. J. China Univ. Posts Telecommun. 2012, 19, 52–56. [Google Scholar] [CrossRef]
- Pan, J. Physical Integrity Attack Detection of Surveillance Camera with Deep Learning based Video Frame Interpolation. In Proceedings of the 2019 IEEE International Conference on Internet of Things and Intelligence System (IoTaIS), Bali, Indonesia, 5–7 November 2019; pp. 79–85. [Google Scholar]
- Blasing, T.; Batyuk, L.; Schmidt, A.-D.; Camtepe, S.; Albayrak, S. An Android Application Sandbox system for suspicious software detection. In Proceedings of the 2010 5th International Conference on Malicious and Unwanted Software, Nancy, France, 19–20 October 2010; pp. 55–62. [Google Scholar]
- Available online: https://www.cynet.com/network-attacks/privilege-escalation/ (accessed on 11 March 2021).
- Hur, J.B.; Shamsi, J.A. A survey on security issues, vulnerabilities and attacks in Android based smartphone. In Proceedings of the 2017 International Conference on Information and Communication Technologies (ICICT), Karachi, Pakistan, 30–31 December 2017; pp. 40–46. [Google Scholar]
- Cai, Y.; Tang, Y.; Li, H.; Yu, L.; Zhou, H.; Luo, X.; He, L.; Su, P. Resource Race Attacks on Android. In Proceedings of the 2020 IEEE 27th International Conference on Software Analysis, Evolution and Reengineering (SANER), London, ON, Canada, 18–21 February 2020; pp. 47–58. [Google Scholar]
- Raveendranath, R.; Rajamani, V.; Babu, A.J.; Datta, S.K. Android malware attacks and countermeasures: Cur-rent and future directions. In Proceedings of the 2014 International Conference on Control, Instrumentation, Communication and Computa-tional Technologies (ICCICCT), Kanyakumari, India, 10–11 July 2014; pp. 137–143. [Google Scholar]
- Wetherall, D.; ChoDnes, D.; Greenstein, B.; Han, S.; Homyack, P.; Jung, J.; Schechter, S.; Wang, X. Privacy revela-tions for web and mobile apps. In 13th Workshop on Hot Topics in Operating Systems HotOS XIII; USENIX Association: Napa, CA, USA, 2011. [Google Scholar]
- Jung, S.; Kwon, T. Automatic Smudge Attack Based on Machine Learning and Pattern Lock System Safety Analysis. J. Korea Inst. Inf. Secur. 2016, 26, 903–910. [Google Scholar]
- Prema, S.; Pramod, T.C. Key Establishment Scheme for Intra and Inter Cluster Communication in WSN. In Proceedings of the 2018 Second. International Conference on Computing Methodologies and Communication (ICCMC), Erode, India, 15–16 February 2018; pp. 942–944. [Google Scholar] [CrossRef]
- T.C., P.; G.S., T.; Iyengar, S.S.; Sunitha, N.R. CKMI: Comprehensive key management infrastructure design for Industrial Automation and Control Systems. Future Internet 2019, 11, 126. [Google Scholar] [CrossRef]
- Wang, S.; Bie, R.; Zhao, F.; Zhang, N.; Cheng, X.; Choi, H. Security in wearable communications. IEEE Netw. 2016, 30, 61–67. [Google Scholar] [CrossRef]
- Pramod, T.; Sunitha, N. Key pre-distribution schemes to support various architectural deployment models in WSN. Int. J. Inf. Comput. Secur. 2016, 8, 139. [Google Scholar] [CrossRef]
- Pramod, T.C.; Sunitha, N.R. An approach to detect malicious activities in SCADA systems. In Proceedings of the 2013 Fourth International Conference on Computing, Communications and Networking Technologies (ICCCNT), Tiruchengode, India, 4–6 July 2013; pp. 1–7. [Google Scholar]
- Kalbo, N.; Mirsky, Y.; Shabtai, A.; Elovici, Y. The Security of IP-Based Video Surveillance Systems. Sensors 2020, 20, 4806. [Google Scholar] [CrossRef] [PubMed]
- Android Camera Bug Under the Microscope. Available online: https://www.darkreading.com/vulnerabilities---threats/android-camera-bug-under-the-microscope/d/d-id/1339090 (accessed on 9 October 2020).
- Malokar, N.K.; Subramanian, N.; Sriram, S.; Venkat, S.; Khan, Z.; Shrawne, S. Exploiting the Vulnerabilities of Android Camera API. IARJSET 2015, 2, 70–73. [Google Scholar] [CrossRef]
- Prasad, S.; Mahalakshmi, P.; Sunder, A.J.C.; Swathi, R. Smart Surveillance Monitoring System Using Raspberry PI and PIR Sensor. Int. J. Comput. Sci. Inf. Technol. 2014, 5, 7107–7109. [Google Scholar]
- Deypir, M. Entropy-based security risk measurement for Android mobile applications. Soft Comput. 2018, 23, 7303–7319. [Google Scholar] [CrossRef]
- Anagnostopoulos, M.; Kambourakis, G.; Gritzalis, S. New facets of mobile botnet: Architecture and evaluation. Int. J. Inf. Secur. 2016, 15, 455–473. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and Other Botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Wu, L.; Du, X.; Fu, X. Security threats to mobile multimedia applications: Camera-based attacks on mobile phones. IEEE Commun. Mag. 2014, 52, 80–87. [Google Scholar] [CrossRef]
- Jeong, J.; Kwon, S.; Hong, M.-P.; Kwak, J.; Shon, T. Adversarial attack-based security vulnerability verification using deep learning library for multimedia video surveillance. Multimed. Tools Appl. 2019, 79, 16077–16091. [Google Scholar] [CrossRef]
- Muhammad, K.; Hamza, R.; Ahmad, J.; Lloret, J.; Wang, H.H.G.; Baik, S.W. Secure Surveillance Framework for IoT Systems Using Probabilistic Image Encryption. IEEE Trans. Ind. Inform. 2018, 14, 3679–3689. [Google Scholar] [CrossRef]
- Hossain, M.A. Framework for a Cloud-Based Multimedia Surveillance System. Int. J. Distrib. Sens. Netw. 2014, 10, 1–11. [Google Scholar] [CrossRef]
- Staneková, L.; Stanek, M. Analysis of dictionary methods for PIN selection. Comput. Secur. 2013, 39, 289–298. [Google Scholar] [CrossRef]
- Alsmirat, M.A.; Obaidat, I.; Jararweh, Y.; Al-Saleh, M. A security framework for cloud-based video surveillance system. Multimed. Tools Appl. 2017, 76, 22787–22802. [Google Scholar] [CrossRef]
- Xu, Z.; Hu, C.; Mei, L. Video structured description technology based intelligence analysis of surveillance videos for public security applications. Multimed. Tools Appl. 2015, 75, 12155–12172. [Google Scholar] [CrossRef]
- Rahman, S.M.M.; Hossain, M.A.; Hassan, M.M.; Alamri, A.; Alghamdi, A.; Pathan, M. Secure privacy vault design for distributed multimedia surveillance system. Futur. Gener. Comput. Syst. 2016, 55, 344–352. [Google Scholar] [CrossRef]
- Gaj, S.; Patel, A.S.; Sur, A. Object based watermarking for H.264/AVC video resistant to rst attacks. Multimed. Tools Appl. 2015, 75, 3053–3080. [Google Scholar] [CrossRef]
- Fadl, S.M.; Han, Q.; Li, Q. Authentication of surveillance videos: Detecting frame duplication based on residual frame. J. Forensic Sci. 2018, 63, 1099–1109. [Google Scholar] [CrossRef]
- Lee, D.; Park, N. Blockchain based privacy preserving multimedia intelligent video surveillance using secure Merkle tree. Multimed. Tools Appl. 2020, 1–18. [Google Scholar] [CrossRef]
- Fitwi, A.; Chen, Y.; Zhu, S. A Lightweight Blockchain-Based Privacy Protection for Smart Surveillance at the Edge. In Proceedings of the 2019 IEEE International Conference on Blockchain (Blockchain), Atlanta, GA, USA, 14–17 July 2019; pp. 552–555. [Google Scholar]
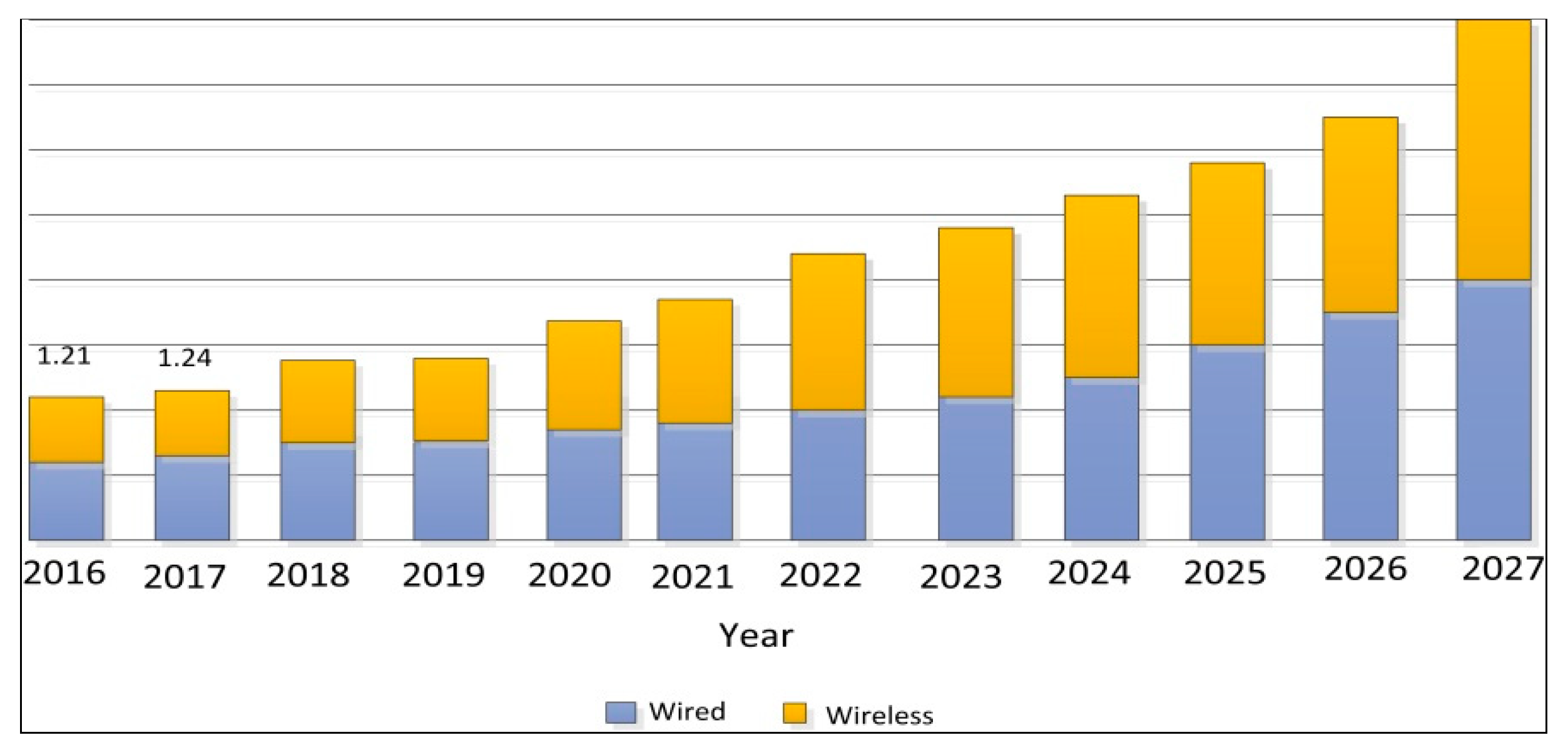
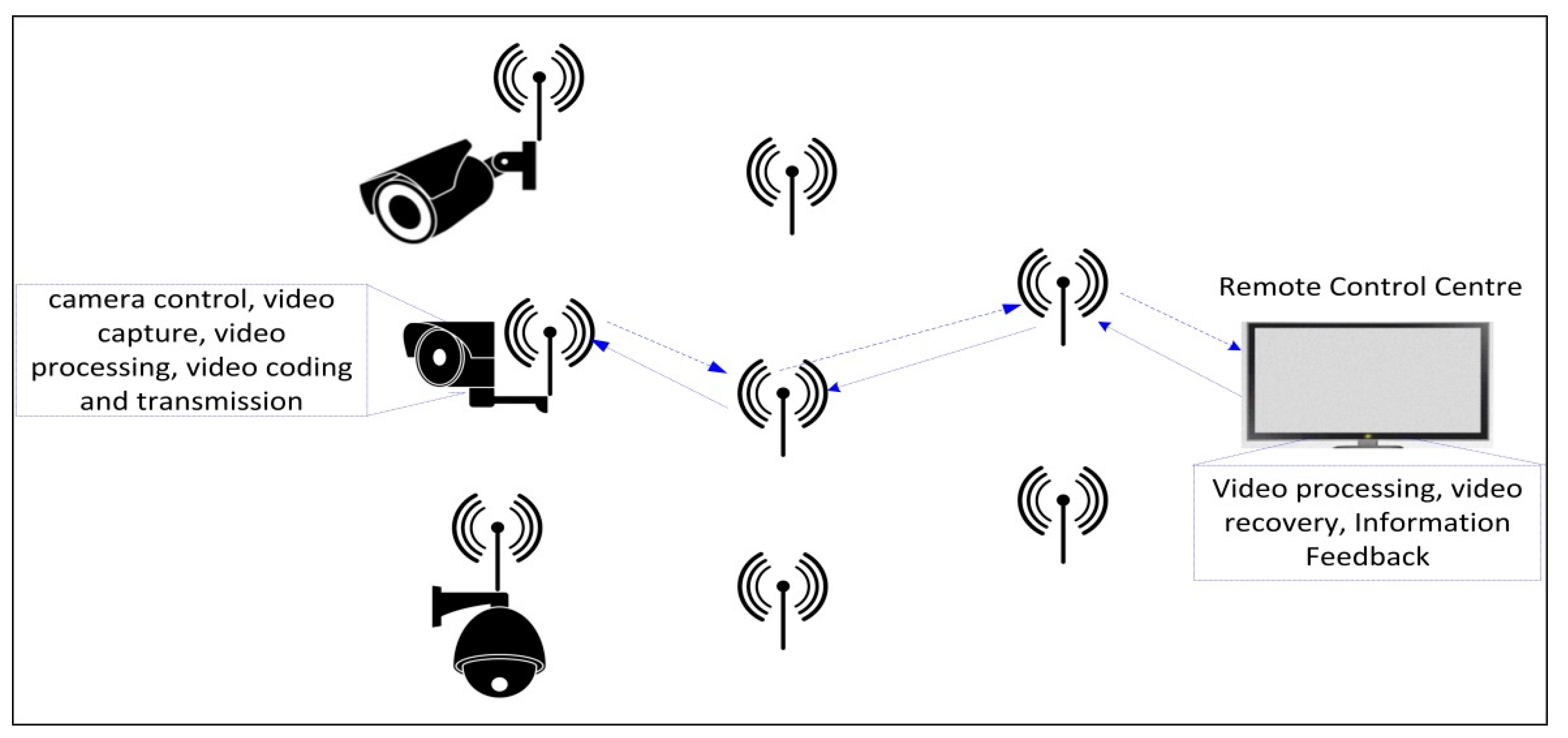

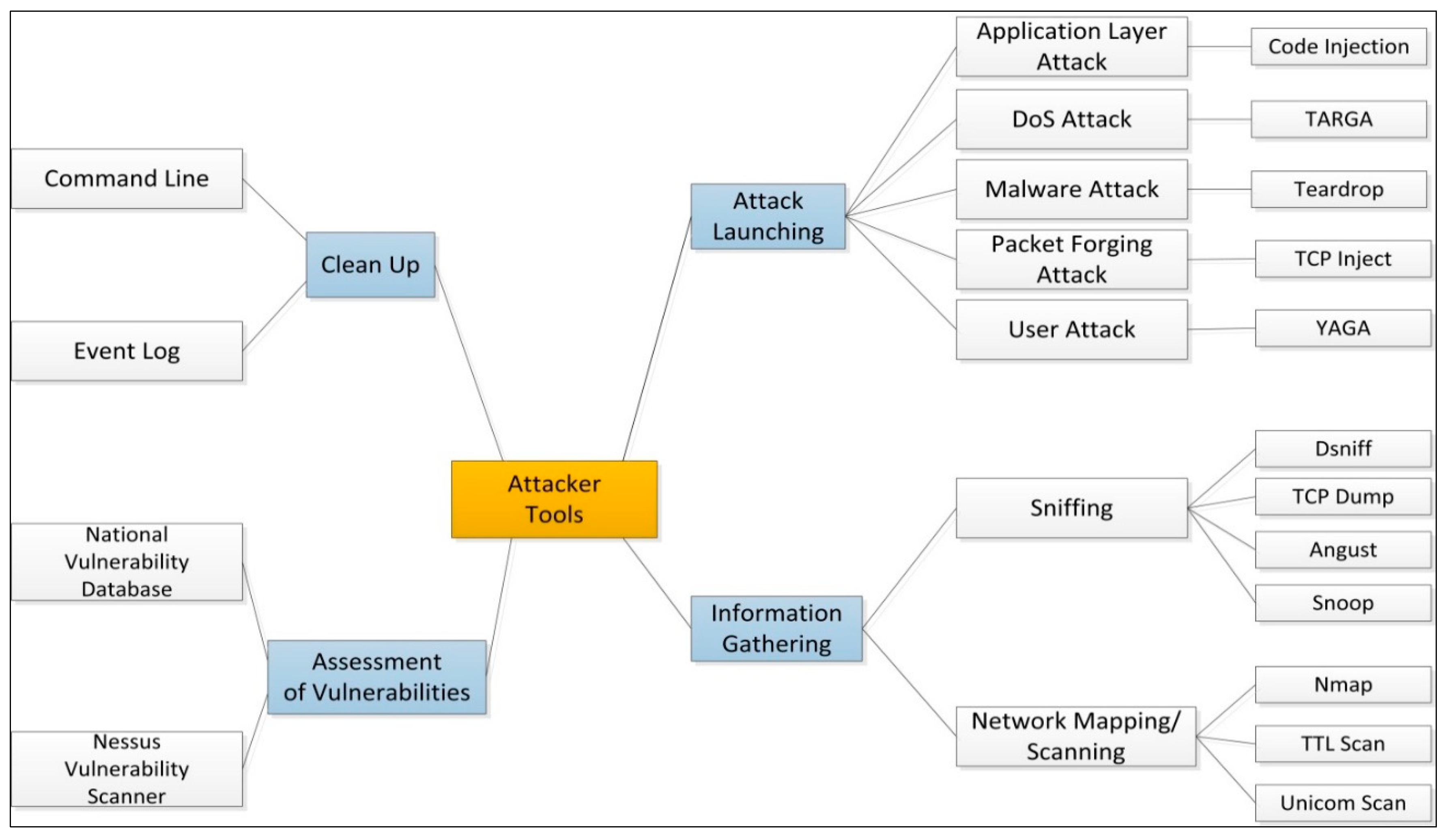
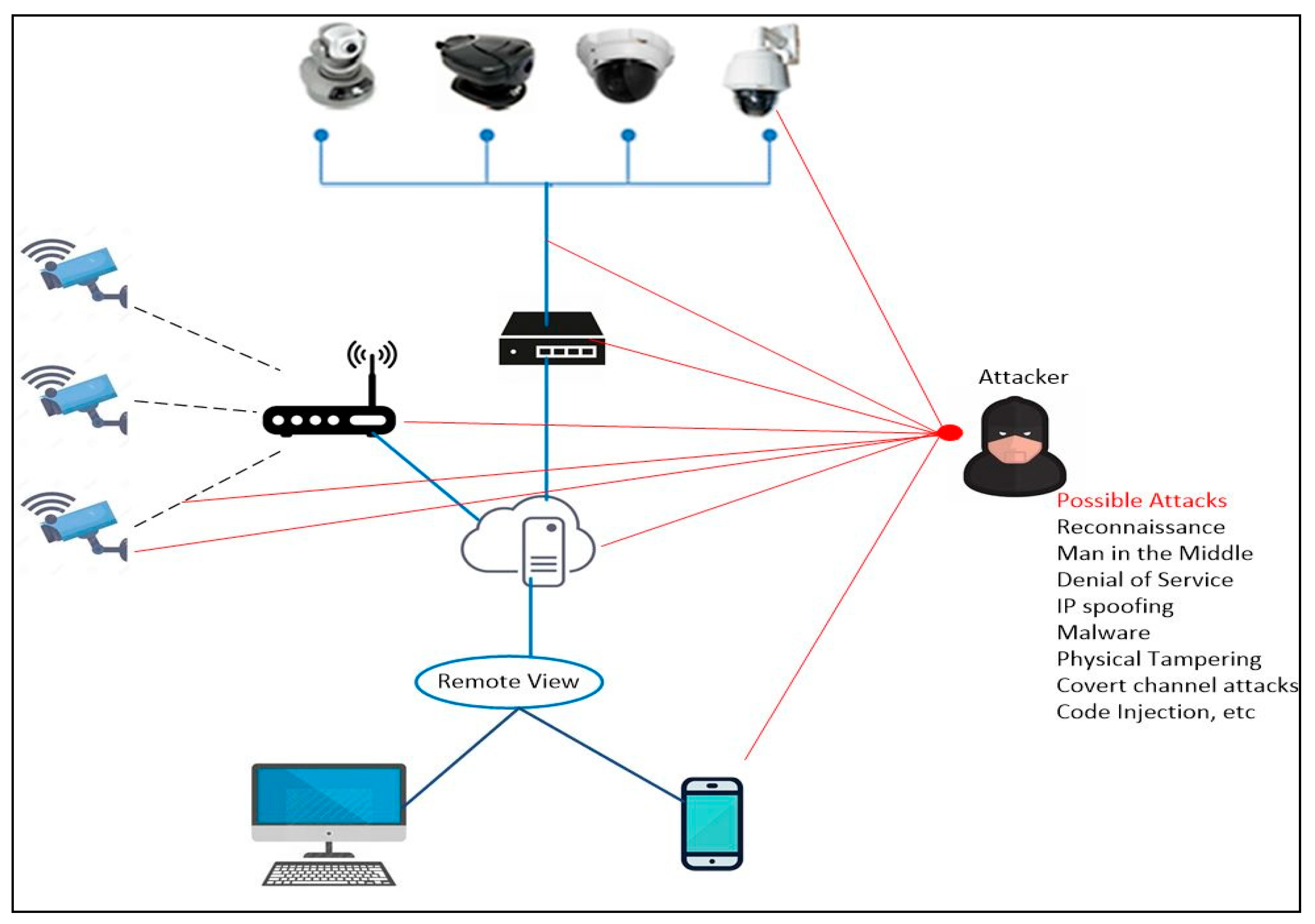
| Attack and Vulnerability Events | Year | Place/Device Manufacturer | Remarks |
|---|---|---|---|
| DDoS attack—Mirai [4] | September, 2016 | French web host OVH | It was the largest DDoS attack ever recorded at over 600 Gbps in size targeting IoT devices, including routers, IP cameras and digital video recorders. |
| Ransomware [5] | January, 2017 | USA | The ransomware attack affected 123 of 187 network video recorders in a closed-circuit TV system for public spaces across Washington, D.C. |
| Privacy hack and defacing [6] | May, 2018 | Yachiyo and Ageo, Japan | Hackers disabled more than 60 Canon security cameras officially. |
| DoS attack [7] | December, 2018 | Bosch IP cameras (firmware versions: 6.32 and higher) | It is classified as “buffer overflow” vulnerability, situated in the RCP and parser of the web server. This would enable an attacker to reactivate disabled features (e.g., telnet) or bypass access credentials (username/password). |
| Command injection [8] | October, 2018 | Yi Technology, a renowned Chinese organization closely connected with Xiaomi | Issues streamed from a data exposure vulnerability which existed in the mobile-to-camera communications of Yi Home Camera. |
| Brute-force attack [9] | March, 2018 | South Korean firm Hanwha Techwin | Kapersky recognized almost 2000 vulnerable cameras that were accessible by means of open IP addresses on the internet. |
| Privilege escalation attacks [10] | March, 2018 | Hanwha SmartCam | Due to a fault in the design, an interloper could obtain entrance through the cloud to all cameras and control them. The primary issue for this is the cloud architecture depended on the XMPP communications protocol. |
| Command and control attack [11] | June, 2018 | Foscam security cameras | The attacker utilized stack-based buffer overflow vulnerability to crash the webService procedure and gain administrative access. |
| Command and control attack [12] | July, 2019 | Delhi, India | Remote hacking and backdoor access to CCTV cameras. |
| Privacy attack—ransomware [13] | March, 2021 | USA | 150,000 security cameras at banks, jails, schools, carmaker Tesla, and other sites were hacked to expose “the surveillance state”. |
| Layer | Attacks | Threats | Description | Examples |
|---|---|---|---|---|
| Perception Layer | Device attack | Physical Attacks, impersonation, malicious code injection | Someone takes advantage of a bug or inherent vulnerability to gain access to the infrastructure. | Physical access to a security surveillance camera and modifying the design settings. |
| IoT botnet | DoS attacks, routing attacks | Group of hacked computers, smart devices, and appliances connected to the Internet are known as an IoT botnet. | The Mirai malware is seen as a milestone in the threat landscape and exploits security holes in IoT devices and launches attacks. | |
| Network Layer | Attacks on Wifi/Ethernet | Routing attacks, data transit attacks | Numerous malicious activities can be performed on devices if an attacker gains physical access to the local network wirelessly. | In the network level attacks, cybercriminals are able to redirect network traffic; for example, Address Resolution Protocol poisoning (ARP) or by changing the Domain Name System (DNS) settings. |
| Reconnaissance | DoS attacks, routing attacks | The aim is to collect data about an infrastructure, including the network services and devices that are running. | This can be achieved by scanning network ports and packet sniffers. | |
| Man-in-the-middle attack | Data transit attacks | It is a type of eavesdropping attack. This attack could permit the attacker to secretly relay and possibly alter the communications between two IoT devices. | Attackers can use a network packet analyzer, i.e., Wireshark for analyzing network traffic. If communications are not encrypted or authenticated, an attacker can easily steal the data. | |
| Application Layer | Cloud infrastructure | Data leakage, DoS attacks, malicious code injection | An IoT device interconnects with back-end cloud services. IoT cloud services might permit the client to select simple passwords. | A lot of cloud services have a logical weakness, which is actually the permission of cloud to a cybercriminal to obtain sensitive information of the customer and also access to the device without any authentication. |
| Privilege escalation | Data leakage, malicious code injection | The attacker takes advantage of programming errors or software flaws to permit cybercriminals to elevate access to an IoT infrastructure. | Grant the cybercriminal elevated access to the IoT ecosystem and its associated data and applications. | |
| Server-side denial of service (DoS) | DoS attacks, Malicious Code Injection | Electronic devices and its connected devices are deactivated or changed by a cybercriminal, via physical or remote access to the IoT sensors. | An attacker can deny the sensors to send and receive communications. Another example could be battery abuse, device disabling, or device bricking. |
| Type of Attacks | Mechanisms that Help to Prevent Attacks | Description |
|---|---|---|
| Spyware and malware | Anti-virus solution | Commercially available anti-virus solutions can scan system and cache files, messages and emails as well as website URLs. They can also prevent spyware and malware by preventing access to a suspected phishing website. |
| IP spoofing | Firewall | Firewall stops unauthorized inward or outward connections. It can prevent various types of network attacks by blocking unauthenticated wireless networks. |
| Man-in-the-middle, visual layer attacks. | Secure API | Cryptography-based API can provide various secure functionalities to the application developer. |
| Malware, DoS, covert channel attacks. | Access control | Access control not only limits the access of processes but also limits the user to resources and/or services, thus limiting risk from malicious applications. |
| Covert channel attacks, DoS, spyware, cross-site scripting attack. | Authentication | The user can login to a device only after being authenticated to prevent its unauthorized use. |
| Covert channel attack, spyware. | Spam filter | Spam filtering applications block unwanted calls, messages and emails. They can also prevent spam from reaching to the user’s inbox. |
| Covert channel attacks, malware attacks, privilege escalation attack. | Pre-testing | Pre-testing can ensure application security by preventing malware. It can also validate applications and give proper access authority to application developers. |
| All types of attacks. | Regular update | Smartphone applications can prevent various types of attacks by regularly updating from various manufacturer-provided platforms. |
| Author(s) | Methodology | Issues Addressed | Advantages | Disadvantages |
|---|---|---|---|---|
| Wu et al. [54] | The background bootstrapping method is applied, which eliminates background motion and the need to precisely estimate the salient motion. | Visual attack | Proposed a randomized capturing approach, which makes it impossible for attackers to extract informative data or original data from the decoded frames. | Deals with large amount of surveillance data to decide about abnormal and suspicious activity detection. |
| Jeong et al. [55] | The adversarial attack method is used for finding vulnerability by employing a deep learning library for multimedia VSS. | Visual layer attack | The proposed experimental method measures the detected accuracy of the model and verifies the effect of adversarial samples. | Both the models used have a significant reduction in classification accuracy by using adversarial samples. |
| Rafik Hamza et al. [56] | Proposed a secured surveillance framework based on the Internet of Things (IoT) system with intelligent integration of video summarization using key frames extraction algorithm and image encryption algorithm. | Visual attack | High speed and lightweight probabilistic key frames encryption algorithm is proposed for encrypting the key frames before they are transmitted about an event alert. | The final decision is based on event identification of encoded key frames. |
| Hossain et al. [57] | Summarizes several distinct issues of a cloud-based multimedia surveillance system and discusses the different design choices. | DoS attack and covert channel attacks | Presents significant issues related to cloud deployment architecture, media acquisition strategy, cloud storage, media processing, resource allocation, notification and sharing, big data analytics, security and privacy, and cloud-based system performance. | The device should be authenticated to each other before data transfer takes place. |
| Lubica et al. [58] | Analysis of the dictionary-based techniques for selecting the PIN (personal identification number). | Privilege escalation attack | The technique of the mitigated dictionary is useful for the selection of a secured PIN which is not prone to guessing attacks. | Application only works if a uniform PIN word is selected. |
| Alsmirat et al. [59] | Provides an end-to-end security framework for a cloud-based video surveillance system supported by a Mobile Edge Computing (MEC) server. | Visual layer attack | The proposed cloud-based VSS supports large number of cameras. An end-to-end security framework provides mutual authentication, data integrity as well as confidentiality and key management. | Key exchange is the major problem in proposed method. |
| Xu et al. [60] | A new model named video structural description (VSD) carries out the parsing of video content into text information by segmenting spatial and temporal data, selecting features, recognizing objects based on a semantic model. | Covert channel attack | Embedding video content into the text information reduces redundant frames processing. | The proposed approach is not tested with the attack model to check side-channel attacks. |
| Rahman et al. [61] | Sensitive data generated from visual sensors is secured by designing a system which identifies various privacy leakage channels in the distributed VSS. | Covert channel attack | Privacy-related problems of the leakage channels are mitigated at different levels. | When a secured privacy vault (obtained from distributed visual sensors) is stolen, information may be compromised. |
| Gaj et al. [62] | Geometric attacks are countered by using a compressed domain video watermarking scheme which embeds the watermark in the homogeneously moving object of a video sequence. | Visual layer attack | It can resist an RST (rotation, scaling and translation) attack without sacrificing the visual quality. | Not applicable for non-stationary backgrounds. |
| Fadl et al. [63] | A new duplication detection algorithm is employed based on the standard deviation of residual inter frames. | Visual layer attack/ steganography attack | It is relatively effective in identifying inter-frame duplication forgery within an acceptable time. | It detects attacks in residual frames and is not possible for all types of intra-frame. |
| Lee et al. [64] | Blockchain technology is used to securely synchronize the CCTV video using the Secure Merkle-Tree method in all the authorized nodes of the system. | Malware attack | It enables deduplication to reduce storage costs. Additionally, the proposed method can synchronize CCTV video data safely without exposing the privacy of the object in the course of synchronization | It can have privacy violation due to the leakage of personal information from an object in a video, which may cause serious social issues. |
| Fitwi et al. [65] | The Lib-Pri system uses the blockchain technique for integrity checking, blurring mechanisms, and video access permissions. | Visual layer modification | Privacy-sensitive objects are detected and masked or blurred in the block chain network. Access permission for users is mentioned in a smart contract document. It ensures the regeneration of a masked image in an isolation storage if required for legal purposes. | The Lib-Pri system accuracy is crucial and applying a reversible mask to preserve privacy is an issue of concern. |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Vennam, P.; T. C., P.; B. M., T.; Kim, Y.-G.; B. N., P.K. Attacks and Preventive Measures on Video Surveillance Systems: A Review. Appl. Sci. 2021, 11, 5571. https://doi.org/10.3390/app11125571
Vennam P, T. C. P, B. M. T, Kim Y-G, B. N. PK. Attacks and Preventive Measures on Video Surveillance Systems: A Review. Applied Sciences. 2021; 11(12):5571. https://doi.org/10.3390/app11125571
Chicago/Turabian StyleVennam, Preethi, Pramod T. C., Thippeswamy B. M., Yong-Guk Kim, and Pavan Kumar B. N. 2021. "Attacks and Preventive Measures on Video Surveillance Systems: A Review" Applied Sciences 11, no. 12: 5571. https://doi.org/10.3390/app11125571
APA StyleVennam, P., T. C., P., B. M., T., Kim, Y.-G., & B. N., P. K. (2021). Attacks and Preventive Measures on Video Surveillance Systems: A Review. Applied Sciences, 11(12), 5571. https://doi.org/10.3390/app11125571







