Application of Blockchain in Education: GDPR-Compliant and Scalable Certification and Verification of Academic Information
Abstract
1. Introduction
- It analyzes the application of blockchain technologies to issue and verify educational data;
- It proposes an innovative model that supports the issuance, storage, and verification of different types of academic information under different scenarios that comply with the GDPR and tackles the scalability challenge present in almost every present blockchain initiative;
- It performs a security analysis of the described model;
- It proposes an implementation of the model as a constructive proof of concept with the objective of confirming the feasibility of the designed framework using available state-of-the-art technologies.
2. Preliminaries
| Initiative | Scalability Number of Blockchains | Right to Erasure | Data Modification | Grant/Remove Permissions | Data Portability | Data Access Accountability |
|---|---|---|---|---|---|---|
| Arenas and Fernández [40] | 1 bc Multichain | - | - | - | - | ✗ |
| Arndt and Guercio [53] | 1 bc | - | - | ✗ | ✗ | ✗ |
| Badyal and Chowdhary [30] | 1 bc | - | - | ✗ | ✗ | ✗ |
| Bandar et al. [52] | 1 bc | - | - | - | - | - |
| Blockcerts [47] | 1 blockchain Bitcoin/Eth | - | ✗ | ✗ | - | ✗ |
| Bore, et al. [36] | 1 bc HL Fabric | - | - | - | - | - |
| Cheng et al. [41] | 1 blockchain Ethereum | - | - | - | - | - |
| Cheng, et al. [48] | 1 bc (HLF) | - | - | - | - | - |
| Daraghmi et al. [17] | 1 bc Eth | - | - | ✓ | - | ✓ |
| Ghazali and Saleh [54] | 1 bc | - | - | - | - | ✗ |
| Gresch et al. [55] | 1 bc Eth | - | - | - | - | - |
| Han et al. [42] | 1 bc Eth | - | - | - | - | - |
| Jeong and Choi [51] | 1 bc Bitcoin/Eth | - | - | - | - | - |
| KARATAŞ [43] | 1 bc Eth | ✗ | ✗ | ✗ | ✗ | ✗ |
| Kuvshinov, et al. [32] | Several private bcs and 1 public | - | - | - | - | ✗ |
| Lam and Dongol [34] | 1 bc HL | - | ✓ | - | - | ✗ |
| Li and Han [35] | 1 bc Eth | - | - | - | - | ✗ |
| Li et al. [45] | 1 bc | - | - | - | - | ✗ |
| Lizcano et al. [38] | 1 bc Eth | - | - | - | - | ✗ |
| Nicosia [21] | 1 bc Bitcoin | - | - | - | - | - |
| Ocheja et al. [46] | 1 bc Eth | - | - | - | - | ✗ |
| Palma et al. [39] | 1 bc Eth | ✗ | - | - | - | ✗ |
| Prinz et al. [56] | 1 bc Eth | - | - | - | - | ✗ |
| Rooksby and Dimitrov [49] | 1 bc Eth | - | - | - | - | - |
| Saleh et al. [1] | 1 bc HL | - | - | - | - | - |
| Srivastava et al. [44] | 1 bc ARK | - | - | - | - | - |
| Sun et al. [50] | 1 bc | - | - | - | - | - |
| Turkanović et al. [31] | 1 bc ARK | - | - | - | - | ✗ |
| Wahab et al. [33] | 1 bc Tangle | - | - | - | - | ✗ |
| Xu et al. [37] | 1 bc | - | - | - | - | ✗ |
| This design | 1 consortium and n private bcs | ✓ | ✓ | ✓ | ✓ | ✓ |
| Initiative | Storage | Regenerate Data | Verification | Share Data Partially | Different Data Types | Data Encrypted | Flexible Format | QR/Web to Verify Data | Support for Learning Analytics | Data Available after Closure |
|---|---|---|---|---|---|---|---|---|---|---|
| Arenas and Fernández [40] | Off. + hash | ✓ | ✓ | ✗ | ✗ | - | - | ✗ | ✗ | ✗ |
| Arndt and Guercio [53] | Off./Bc | ✗ | ✓ | ✗ | - | - | - | ✗ | - | ✗ |
| Badyal and Chowdhary [30] | Bc | ✗ | ✓ | ✗ | - | ✗ | - | ✓ | - | ✗ |
| Bandar et al. [52] | Off. + hash + digital id | - | ✓ | ✗ | ✗ | - | - | - | ✓ | ✗ |
| Blockcerts [47] | Off. | ✗ | ✓ | ✗ | ✓ | - | ✓ | ✗ | ✗ | ✗ |
| Bore, et al. [36] | Off. + hash + pointer | - | ✓ | ✗ | ✓ | ✓ | - | - | - | ✗ |
| Cheng et al. [41] | Off. + hash + cert. id | ✓ | ✓ | ✗ | - | - | - | ✓ | - | ✗ |
| Cheng, et al. [48] | Off. | ✗ | ✓ | ✗ | ✓ | - | - | ✓ | - | ✗ |
| Daraghmi et al. [17] | Off./hash | - | ✓ | ✗ | - | ✓ | - | ✓ | - | ✗ |
| Ghazali and Saleh [54] | Off./hash | - | ✓ | ✗ | - | - | - | ✗ | - | ✗ |
| Gresch et al. [55] | File + hash | ✗ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| Han et al. [42] | Off. + pointer to data +hash | ✓ | ✓ | ✗ | - | - | - | - | - | ✗ |
| Jeong and Choi [51] | Off. | ✗ | ✓ | ✗ | ✗ | - | - | ✓ | ✗ | ✗ |
| KARATAŞ [43] | Eth | ✓ | ✓ | ✗ | ✓ | ✗ | ✗ | ✗ | - | ✓ |
| Kuvshinov, et al. [32] | On. in a private bc + hash | ✗ | ✓ | ✓ | ✓ | ✗ | - | ✗ | - | ✗ |
| Lam and Dongol [34] | HL + Access control | ✓ | ✓ | - | ✓ | ✗ | ✓ | ✗ | - | ✗ |
| Li and Han [35] | Off. | ✓ | ✓ | ✗ | ✓ | ✓ | - | - | - | ✓ |
| Li et al. [45] | Off. + OBE codes | ✗ | ✓ | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✓ |
| Lizcano et al. [38] | Off. + some data on | ✓ | ✓ | ✗ | ✗ | - | ✗ | ✗ | ✓ | ✓ |
| Nicosia [21] | Off. + hash | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ |
| Ocheja et al. [46] | Off. + hash +pointer | - | ✓ | ✗ | ✓ | - | ✓ | - | - | ✗ |
| Palma et al. [39] | Bc | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | - | ✗ | ✓ |
| Prinz et al. [56] | Off. | - | ✓ | ✗ | - | - | - | - | - | ✗ |
| Rooksby and Dimitrov [49] | Bc | - | ✓ | - | ✓ | - | - | ✗ | ✗ | ✗ |
| Saleh et al. [1] | Off.+hash | - | ✓ | - | - | ✓ | - | - | - | ✗ |
| Srivastava et al. [44] | On. (token) | ✓ | ✓ | ✗ | ✓ | - | - | - | - | ✓ |
| Sun et al. [50] | Bc + hash | - | ✓ | - | ✓ | - | - | - | - | - |
| Turkanović et al. [31] | On. (token) | ✓ | ✓ | ✗ | ✗ | ✗ | ✗ | ✗ | - | ✓ |
| Wahab et al. [33] | Off. + hash | ✗ | ✓ | ✗ | ✗ | - | - | - | - | - |
| Xu et al. [37] | On. | - | ✓ | ✗ | - | ✓ | - | - | - | ✗ |
| This design | Off. + hash + pointer to data | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ | ✓ |
- 1.
- Education is a discipline with a global dimension that encompasses many stakeholders who must exchange information despite the fact that their organizations are independent. Blockchain brings many applications to this field that require a new interconnection model [49] that is difficult to integrate into the proprietary systems of each entity. The system proposed in this research is adaptable and does not require different organizations to modify their information systems.
- 2.
- Achieving privacy in blockchain applications is a real challenge when personal information, protected by many regulations in different countries, is processed. Public blockchains should not be chosen to tamperproof store personal information, even encrypted [35], and consequently, private or consortium blockchains should be preferred [1]. However, from a privacy and regulatory point of view, in some countries (e.g., European Union countries under the scope of the GDPR), it may not be a valid solution [4]. Conscious of this issue, some proposals [1,17,38,46] store information offline but register the corresponding hash digests on the blockchain to ensure the integrity and traceability of information. Nonetheless, in some countries with more permissive regulations (e.g., Brazil [39]) personal information can be openly stored if related to public education. On the contrary, as pointed out above, the European GDPR forbids registering any personal data in unmodifiable permanent storage such as a blockchain [53], which must be anonymized. This is a relevant design constraint, and it is important to emphasize that hashing personal data, from the GDPR’s point of view, cannot be considered a completely valid anonymization technique [4]. Finally, the immutability feature of blockchain also makes it impossible to modify or delete data, even for legitimate reasons, which, in turn, collides with GDPR’s right to be forgotten. The model proposed in this research solves this challenge with a design that preserves the privacy of users and complies with the GDPR.
- 3.
- Storage, scalability, and performance of blockchain-based systems to issue, store, and verify academic information are also key challenges to be addressed in order to achieve its general adoption when the number of transactions containing academic information increases. Present-day blockchain frameworks (Bitcoin, Ethereum, …) have a very limited storage capacity, compared to other systems [35]. For example, the Bitcoin core protocol limits blocks to 1 MB in size [57], although there are specialized blockchain-based decentralized storage networks to store higher amounts of data (IPFS, Storj, Sia, Filecoin, Swarm, etc.) [58]. The current blockchain-based proposals present some issues related to their scalability, that is, the ability to handle large volumes of transactions at high speeds. In general, state-of-the-art blockchain implementations exhibit relatively low transaction efficiency and high confirmation delays. As an example, seven transactions per second (tps) are achieved in Bitcoin and 15 tps in Ethereum. In the case of Hyperledger, hundreds or even thousands of tps can be obtained depending on the actual configuration utilized. In contrast, centralized systems such as VISA can process a maximum of 24,000 tps [33,59].
3. Proposed Model
- Certificate issuance and management of academic information. This application is further discussed below to illustrate the solution proposed. For this use case, an academic institution issues a certificate, transcript, or diploma and records information on the blockchain so it can be verified for authenticity or recovered, even by authorized third parties;
- Registration of learning paths. In this use case, student’s achievements are registered by the educational institutions on the blockchain for both formal and informal studies so they can also be verified. Academic data managed in this case extend the certificates and diplomas mentioned in the previous point.
- Tracking of competence values. Diplomas and certificates are not the only alternatives to provide evidence about the competences acquired by a student since their grades can be converted into competence values that can be issued by the academic institution to be verified by authorized third parties.
- Recording of academic credits. Another application of this solution is to record learners’ credits achieved for successfully completed courses. This type of academic information would be generated by the educational organization according to the proposed model.
- An indirect use case of the proposed model in this section, as it will be discussed later, corresponds to the enrichment of the academic information managed in the previous use cases with additional public nonsensitive personal data, such as the type of academic information, degree, or category of a certificate. This could be used to anonymously generate statistics, learning analytics data, or trends relevant to the education domain.
3.1. Issuance of Academic Information
3.2. Verification of Academic Information
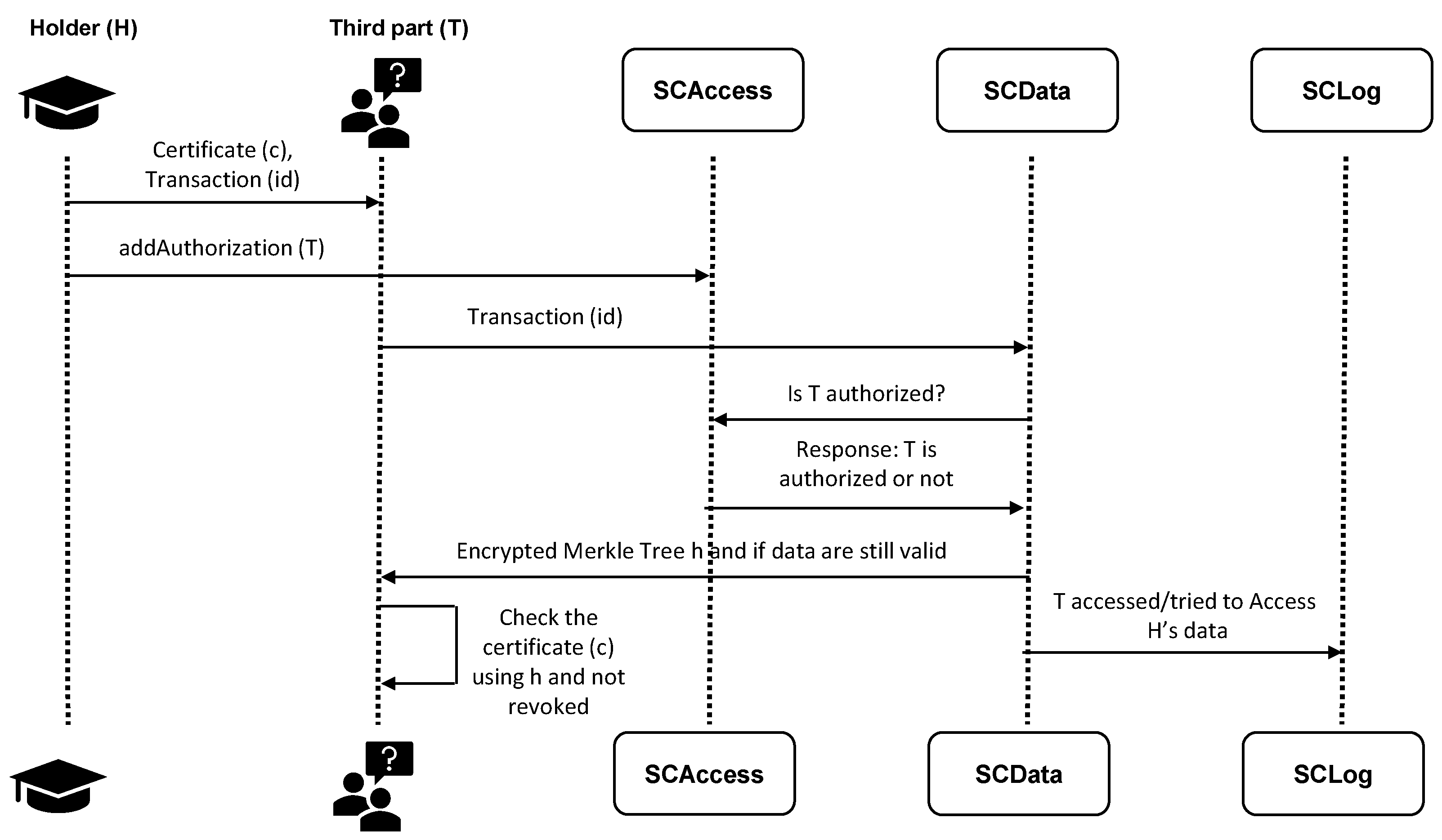
3.2.1. Case 1: The Holder Sends a Third Party the Certificate and Allows Its Verification
3.2.2. Case 2: The Holder Only Wants to Share Parts of the Academic Information
3.2.3. Case 3: The Holder Allows a Third Party to Receive the Certificate Directly from the Academic Institution
3.3. Modification of Academic Information
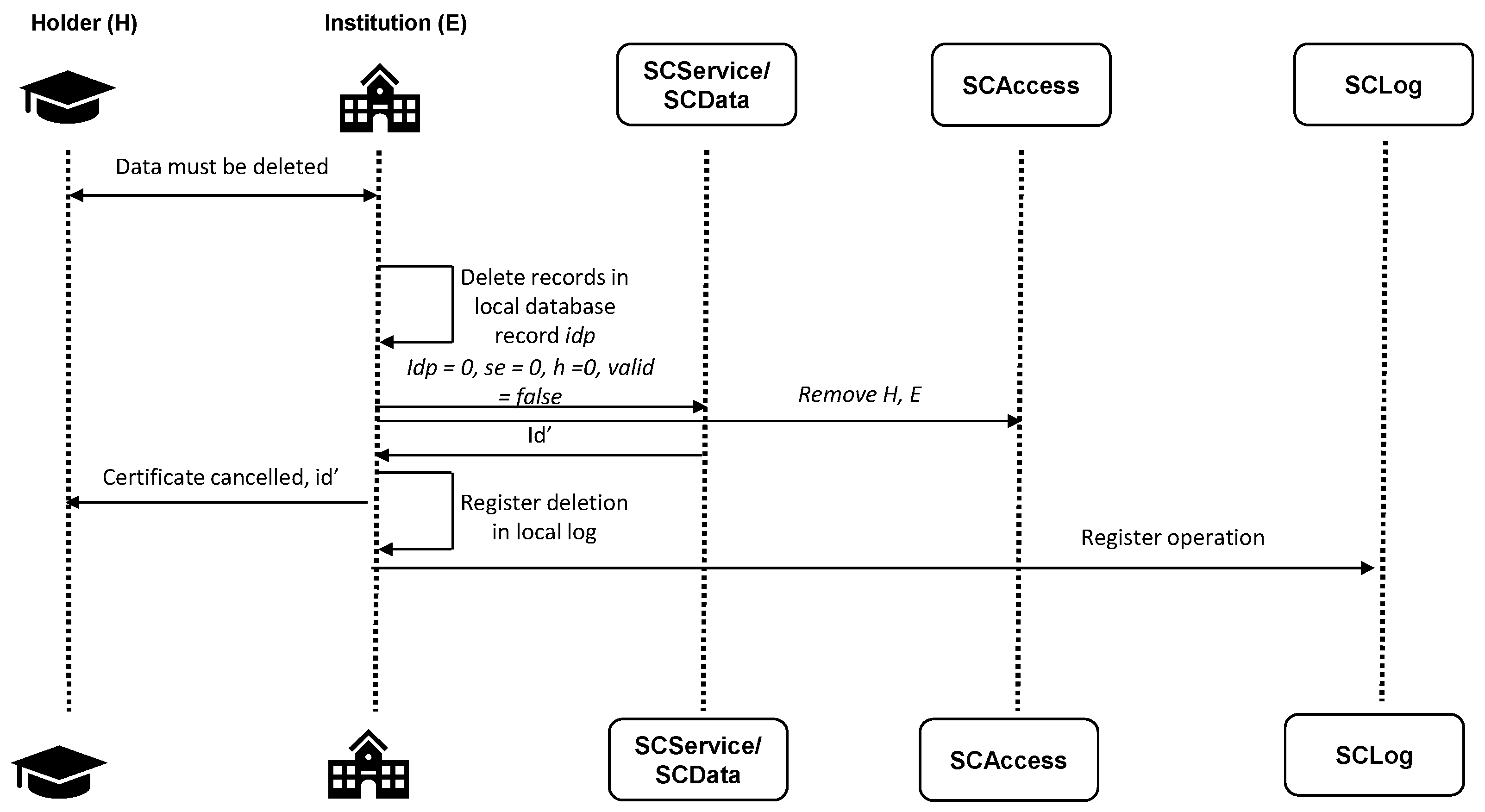
3.4. Revocation/Deletion of Academic Information
3.5. How to Verify or Recover Any Academic Information in Cases Where the Issuing Institution Disappears
- The institution E, before discontinuing its educational activities, should publish the affected educational data in their final form as stored in its databases (encrypted with a key shared with each holder as described in this model) in a distributed file system such as a private IPFS connected to a private blockchain that can only be used and accessed by some trustful, prestigious selected organizations. Although these entities have direct access to the records, their contents cannot be read since they are originally encrypted. Associated with each protected academic information in IPFS, a private blockchain will exist in which the pointer to the information in the distributed file system and the same information it was recorded on the private and consortium blockchain will be stored.
- If a holder H would like to recover their certificate (case 3), the system should relocate the database access point to a new location, where a smart contract should check if H is allowed in SCAccess to access the Information. If it has the proper permissions, it should make it encrypted, but since H has the secret shared key with the discontinued institution E, it could recover the original information.
- Under this scenario, if the holder H deletes their secret key, as the encrypted information is only stored on a private distributed storage with limited access, the “right to be forgotten” should be achieved since the GDPR considers deleting the decrypting keys to be a valid option.
3.6. Compliance with Security Requirements
4. Proof-of-Concept Implementation
- It is a private, efficient processing blockchain, enabling parallel processing with thousands of transactions per second depending on the topology and configuration [74];
- It provides a membership identity service that manages user ID and authenticates all participants in the network, allowing the creation of access control lists to provide different levels of permission depending on the role;
- It enables the creation of private channels to assure privacy and confidentiality; hence, information cannot be accessed without proper permissions to the network participant;
- It allows the creation of smart contracts called “chaincode” in the Hyperledger Fabric network required by the proposed design;
- It implements a modular architecture with pluggable components for different types of identity, consensus mechanisms, or encryption algorithms.
4.1. Holder and Third-Party Users
4.2. Educational Institution
4.3. Private Blockchains
4.4. Consortium Blockchain
4.5. Private Blockchain Connected to IPFS to Store Academic Information from Disappeared Institutions
5. Discussion
6. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
References
- Saleh, O.S.; Ghazali, O.; Rana, M.E. Blockchain based framework for educational certificates verification. J. Crit. Rev. 2020, 7, 79–84. [Google Scholar] [CrossRef]
- Muzammil, M. Corrupt schools, corrupt universities: What can be done? Comp. A J. Comp. Int. Educ. 2010, 40, 385–387. [Google Scholar] [CrossRef]
- Creating Pathways to Careers in IT. Available online: https://services.google.com/fh/files/misc/it_cert_impactreport_booklet_rgb_digital_version.pdf. (accessed on 16 March 2021).
- Lyons, T.; Courcelas, L.; Timsit, K. Blockchain and the GDPR; The European Union Blockchain Observatory and Forum, European Commission: Brussels, Belgium, 2018. [Google Scholar]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008. Available online: https://www.bitcoin.org/bitcoin.pdf. (accessed on 17 January 2021).
- Andoni, M.; Robu, V.; Flynn, D.; Abram, S.; Geach, D.; Jenkins, D.; McCallum, P.; Peacock, A. Blockchain technology in the energy sector: A systematic review of challenges and opportunities. Renew. Sustain. Energy Rev. 2019, 100, 143–174. [Google Scholar] [CrossRef]
- Mirabelli, G.; Solina, V. Blockchain and agricultural supply chains traceability: Research trends and future challenges. Procedia Manuf. 2020, 42, 414–421. [Google Scholar] [CrossRef]
- Khezr, S.; Moniruzzaman, M.; Yassine, A.; Benlamri, R. Blockchain Technology in Healthcare: A Comprehensive Review and Directions for Future Research. Appl. Sci. 2019, 9, 1736. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y.; Ma, M.; He, J. BlocHIE: A BLOCkchain-Based Platform for Healthcare Information Exchange. In Proceedings of the 2018 IEEE International Conference on Smart Computing (SMARTCOMP), Taormina, Sicily, Italy, 18–20 June 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2018; pp. 49–56. [Google Scholar] [CrossRef]
- Pournader, M.; Shi, Y.; Seuring, S.; Koh, S.L. Blockchain applications in supply chains, transport and logistics: A systematic review of the literature. Int. J. Prod. Res. 2019, 58, 2063–2081. [Google Scholar] [CrossRef]
- Conoscenti, M.; Vetro, A.; de Martin, J.C. Blockchain for the Internet of Things: A systematic literature review. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2016; pp. 1–6. [Google Scholar] [CrossRef]
- Jiang, S.; Cao, J.; Wu, H.; Yang, Y. Fairness-based Packing of Industrial IoT Data in Permissioned Blockchains. IEEE Trans. Ind. Inform. 2020, 1. [Google Scholar] [CrossRef]
- Konstantinidis, I.; Siaminos, G.; Timplalexis, C.; Zervas, P.; Peristeras, V.; Decker, S. Blockchain for Business Applications: A Systematic Literature Review; Abramowicz, W., Paschke, A., Eds.; Springer International Publishing: Cham, Switzerland, 2018; Volume 320, pp. 384–399. [Google Scholar]
- Butijn, B.-J.; Tamburri, D.A.; Heuvel, W.-J.V.D. Blockchains. ACM Comput. Surv. 2020, 53, 1–37. [Google Scholar] [CrossRef]
- Casino, F.; Dasaklis, T.K.; Patsakis, C.F. A systematic literature review of blockchain-based applications: Current status, classification and open issues. In Telematics and Informatics; Elsevier Ltd: Amsterdam, The Netherlands, 2019; Volume 36, pp. 55–81. [Google Scholar] [CrossRef]
- Kiayias, A.; Russell, A.; David, B.; Oliynykov, R. Ouroboros: A Provably Secure Proof-of-Stake Blockchain Protocol; Katz, J., Shacham, H., Eds.; Springer International Publishing: Cham, Switzerland, 2017; Volume 10401, pp. 357–388. [Google Scholar]
- Daraghmi, Y.-A.; Yuan, S.-M. UniChain: A Design of Blockchain-Based System for Electronic Academic Records Access and Permissions Management. Appl. Sci. 2019, 9, 4966. [Google Scholar] [CrossRef]
- Marjit, U.; Kumar, P. Towards a Decentralized and Distributed Framework for Open Educational Resources based on IPFS and Blockchain. In Proceedings of the 2020 International Conference on Computer Science, Engineering and Applications (ICCSEA), Gunupur, India, 13–14 March 2020; pp. 1–6. [Google Scholar] [CrossRef]
- Szabo, N. Formalizing and Securing Relationships on Public Networks. First Monday 1997, 2. [Google Scholar] [CrossRef]
- Swan, M. Blockchain: Blueprint for a New Economy, 1st ed.; O’Reilly Media, Inc.: Sebastopol, CA, USA, 2015. [Google Scholar]
- Grech, A.; Camilleri, A.F. Blockchain in Education; Publications Office of the European Union: Luxembourg City, Luxembourg, 2017. [Google Scholar]
- AlAmmary, A.; Alhazmi, S.; Almasri, M.; Gillani, S. Blockchain-Based Applications in Education: A Systematic Review. Appl. Sci. 2019, 9, 2400. [Google Scholar] [CrossRef]
- Yumna, H.; Khan, M.M.; Ikram, M.; Ilyas, S. Use of Blockchain in Education: A Systematic Literature Review; Nguyen, N.T., Gaol, F.L., Hong, T.-P., Trawiński, B., Eds.; Springer: Cham, Switzerland, 2019; Volume 11432, pp. 191–202. [Google Scholar]
- Malibari, N.A. A Survey on Blockchain-based Applications in Education. In Proceedings of the 2020 7th International Conference on Computing for Sustainable Global Development (INDIACom), New Delhi, India, 12–14 March 2020; IEEE: Piscataway, NJ, USA, 2020; pp. 266–270. [Google Scholar] [CrossRef]
- Bhaskar, P.; Tiwari, C.K.; Joshi, A. Blockchain in education management: Present and future applications. Interact. Technol. Smart Educ. 2020. ahead of print. [Google Scholar] [CrossRef]
- Caldarelli, G.; Ellul, J. Trusted Academic Transcripts on the Blockchain: A Systematic Literature Review. Appl. Sci. 2021, 11, 1842. [Google Scholar] [CrossRef]
- Raimundo, R.; Rosário, A. Blockchain System in the Higher Education. Eur. J. Investig. Heal. Psychol. Educ. 2021, 11, 21. [Google Scholar] [CrossRef]
- Fernández-Caramés, T.M.; Fraga-Lamas, P. Towards Next Generation Teaching, Learning, and Context-Aware Applications for Higher Education: A Review on Blockchain, IoT, Fog and Edge Computing Enabled Smart Campuses and Universities. Appl. Sci. 2019, 9, 4479. [Google Scholar] [CrossRef]
- Hameed, B.; Murad, M.; Noman, A.; Javed, M.; Ramzan, M.; Ashfaq, F.; Usman, H.; Yousaf, M. A Review of Blockchain based Educational Projects. Int. J. Adv. Comput. Sci. Appl. 2019, 10. [Google Scholar] [CrossRef]
- Badyal, S.; Chowdhary, A. Alumnichain: Blockchain based records verification service. Int. J. Innov. Technol. Explor. Eng. 2019, 8, 4296–4299. [Google Scholar] [CrossRef]
- Turkanovic, M.; Holbl, M.; Kosic, K.; Hericko, M.; Kamisalic, A. EduCTX: A Blockchain-Based Higher Education Credit Platform. IEEE Access 2018, 6, 5112–5127. [Google Scholar] [CrossRef]
- Kuvshinov, K.; Nikiforov, I.; Mostovoy, J.; Mukhutdinov, D. Disciplina: Blockchain for Education. 2018. Available online: https://www.disciplina.io/yellowpaper.pdf (accessed on 21 February 2021).
- Wahab, A.; Barlas, M.; Mahmood, W. Zenith Certifier: A Framework to Authenticate Academic Verifications Using Tangle. J. Softw. Syst. Dev. 2018, 2018. [Google Scholar] [CrossRef]
- Lam, T.Y.; Dongol, B. A blockchain-enabled e-learning platform. Interact. Learn. Environ. 2020, 1–23. [Google Scholar] [CrossRef]
- Li, H.; Han, D. EduRSS: A Blockchain-Based Educational Records Secure Storage and Sharing Scheme. IEEE Access 2019, 7, 179273–179289. [Google Scholar] [CrossRef]
- Bore, N.; Karumba, S.; Mutahi, J.; Darnell, S.S.; Wayua, C.; Weldemariam, K. Towards Blockchain-enabled School Information Hub. In Proceedings of the Ninth International Conference on Information and Communication Technologies and Development—ICTD, Lahore, Pakistan, 16–19 November 2017; ACM: New York, NY, USA, 2017; pp. 1–36. [Google Scholar] [CrossRef]
- Xu, Y.; Zhao, S.; Kong, L.; Zheng, Y.; Zhang, S.; Li, Q. ECBC: A High Performance Educational Certificate Blockchain with Efficient Query, in Theoretical Aspects of Computing—ICTAC 2017. Lect. Notes Comput. Sci. 2017, 10580, 288–304. [Google Scholar] [CrossRef]
- Lizcano, D.; Lara, J.A.; White, B.; Aljawarneh, S. Blockchain-based approach to create a model of trust in open and ubiquitous higher education. J. Comput. High. Educ. 2020, 32, 109–134. [Google Scholar] [CrossRef]
- Palma, L.M.; Vigil, M.A.G.; Pereira, F.L.; Martina, J.E. Blockchain and smart contracts for higher education registry in Brazil. Int. J. Netw. Manag. 2019, 29, e2061. [Google Scholar] [CrossRef]
- Arenas, R.; Fernandez, P. CredenceLedger: A Permissioned Blockchain for Verifiable Academic Credentials. In Proceedings of the 2018 IEEE International Conference on Engineering, Technology and Innovation (ICE/ITMC), Stuttgart, Germany, 17–20 June 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2018; pp. 1–6. [Google Scholar]
- Cheng, J.-C.; Lee, N.-Y.; Chi, C.; Chen, Y.-H. Blockchain and smart contract for digital certificate. In Proceedings of the 2018 IEEE International Conference on Applied System Invention (ICASI), Taiwan, China, 13–17 April 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2018; pp. 1046–1051. [Google Scholar]
- Han, M.; Li, Z.; He, J.; Wu, D.; Xie, Y.; Baba, A. A Novel Blockchain-based Education Records Verification Solution. In Proceedings of the 19th Annual SIG Conference on Information Technology Education, Fort Lauderdale, FL, USA, 3–6 October 2018; Association for Computing Machinery (ACM): New York, NY, USA, 2018; pp. 178–183. [Google Scholar]
- Karataş, E. Developing Ethereum Blockchain-Based Document Verification Smart Contract for Moodle Learning Management System. Int. J. Inform. Technol. 2018, 11, 399–406. [Google Scholar] [CrossRef]
- Srivastava, A.; Bhattacharya, P.; Singh, A.; Mathur, A.; Prakash, O.; Pradhan, R. A Distributed Credit Transfer Educational Framework based on Blockchain. In Proceedings of the 2018 Second International Conference on Advances in Computing, Control and Communication Technology (IAC3T), Allahabad, India, 21–23 September 2018; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2018; pp. 54–59. [Google Scholar]
- Li, T. Design of Outcome-based Education Blockchain. IJPE 2018, 14, 2403. [Google Scholar] [CrossRef]
- Ocheja, P.; Flanagan, B.; Ueda, H.; Ogata, H. Managing lifelong learning records through blockchain. Res. Pr. Technol. Enhanc. Learn. 2019, 14, 4. [Google Scholar] [CrossRef]
- Baldi, M.; Chiaraluce, F.; Kodra, M.; Spalazzi, L. Security analysis of a blockchain-based protocol for the certification of academic credentials. arXiv 2019, arXiv:1910.04622. [Google Scholar]
- Cheng, H.; Lu, J.; Xiang, Z.; Song, B. A Permissioned Blockchain-Based Platform for Education Certificate Verification. Commun. Comput. Inf. Sci. 2020, 3, 456–471. [Google Scholar]
- Rooksby, J.; Dimitrov, K. Trustless education? A blockchain system for university grades1. Ubiquity J. Pervasive Media 2020, 6, 83–88. [Google Scholar] [CrossRef]
- Sun, H.; Wang, X.; Wang, X. Application of Blockchain Technology in Online Education. Int. J. Emerg. Technol. Learn. 2018, 13, 252–259. [Google Scholar] [CrossRef]
- Jeong, W.-Y.; Choi, M. Design of recruitment management platform using digital certificate on blockchain. J. Inf. Process. Syst. 2019, 15, 707–716. [Google Scholar] [CrossRef]
- Bandara, I.; Ioraş, F.; Arraiza, M.P. The Emerging Trend of Blockchain for Validating Degree Apprenticeship Certification in Cybersecurity Education. INTED2018 Proc. 2018, 1, 7677–7683. [Google Scholar] [CrossRef]
- Arndt, T.; Guercio, A. Blockchain-Based Transcripts for Mobile Higher-Education. Int. J. Inf. Educ. Technol. 2020, 10, 84–89. [Google Scholar] [CrossRef]
- Ghazal, O.; Saleh, O.S. A graduation certificate verification model via utilization of the blockchain technology. J. Telecommun. Electron. Comput. Eng. 2018, 10, 29–34. [Google Scholar]
- Gresch, J.; Rodrigues, B.; Scheid, E.; Kanhere, S.S.; Stiller, B. The Proposal of a Blockchain-Based Architecture for Transparent Certificate Handling. In Business Information Systems; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2019; Volume 339, pp. 185–196. [Google Scholar]
- Prinz, W.; Kolvenbach, S.; Ruland, R. Blockchain for Education: Lifelong Learning Passport. ERCIM News 2020, 120, 15–16. [Google Scholar]
- Göbel, J.; Krzesinski, A. Increased block size and Bitcoin blockchain dynamics. In Proceedings of the 2017 27th International Telecommunication Networks and Applications Conference (ITNAC), Melbourne, Australia, 22–24 November 2017; Institute of Electrical and Electronics Engineers (IEEE): Piscataway, NJ, USA, 2017; pp. 1–6. [Google Scholar]
- Benisi, N.Z.; Aminian, M.; Javadi, B. Blockchain-based decentralized storage networks: A survey. J. Netw. Comput. Appl. 2020, 162, 102656. [Google Scholar] [CrossRef]
- Lyons, T.; Courcelas, L.; Timsit, K. Scalability, Interoperability and Sustainability of Blockchains; The European Union Block-chain Observatory and Forum, European Commission: Brussels, Belgium, 2019. [Google Scholar]
- Eter Project. European Tertiary Education Register 2021. Available online: https://ec.europa.eu/education/european-tertiary-education-register_en (accessed on 11 February 2021).
- UNESCO Institute for Statistics. Enrolment by Level of Education (Both Sexes) 2018. Available online: http://data.uis.unesco.org/ (accessed on 14 February 2021).
- Wood, G. Polkadot: Vision for a Heterogeneous Multi-Chain Framework. 2016. Available online: https://polkadot.network/PolkaDotPaper.pdf (accessed on 17 January 2021).
- Ethereum. Ethereum 2.0 (Eth2) 2021. Available online: https://ethereum.org/en/eth2/ (accessed on 21 February 2021).
- Cachin, C. Architecture of the Hyperledger Blockchain Fabric. Work. Distrib. Cryptocurrencies Consens. Ledgers 2016, 310, 4. [Google Scholar]
- Longo, R.; Podda, A.S.; Saia, R. Analysis of a Consensus Protocol for Extending Consistent Subchains on the Bitcoin Blockchain. Computation 2020, 8, 67. [Google Scholar] [CrossRef]
- Sun, T.; Yu, W. A Formal Verification Framework for Security Issues of Blockchain Smart Contracts. Electronics 2020, 9, 255. [Google Scholar] [CrossRef]
- Andola, N.; Gogoi, M.; Venkatesan, S.; Verma, S. Vulnerabilities on Hyperledger Fabric. Pervasive Mob. Comput. 2019, 59, 101050. [Google Scholar] [CrossRef]
- Lin, I.-C.; Liao, T.-C. A Survey of Blockchain Security Issues and Challenges. Int. J. Netw. Secur. 2017, 19, 653–659. [Google Scholar] [CrossRef]
- Lyons, T.; Courcelas, L. Blockchain and cyber security; The European Union Blockchain Observatory and Forum, European Commission: Brussels, Belgium, 2020. [Google Scholar]
- Li, X.; Jiang, P.; Chen, T.; Luo, X.; Wen, Q. A survey on the security of blockchain systems. Futur. Gener. Comput. Syst. 2020, 107, 841–853. [Google Scholar] [CrossRef]
- Iqbal, M.; Matulevičius, R. Blockchain-Based Application Security Risks: A Systematic Literature Review; Proper, H.A., Stirna, J., Eds.; Springer International Publishing: Cham, Switzerland, 2019; Volume 349, pp. 176–188. [Google Scholar]
- Nabil, A.; Nafil, K.; Mounir, F. Blockchain Security and Privacy in Education: A Systematic Mapping Study. In Advances in Intelligent Systems and Computing; Springer Science and Business Media LLC: Berlin/Heidelberg, Germany, 2020; pp. 253–262. [Google Scholar]
- Androulaki, E.; Bortnikov, V.; Cachin, C.; de Caro, A.; Enyeart, D.; Muralidharan, S.; Murthy, C.; Smith, K.; Sorniotti, A.; Cocco, S.W.; et al. Hyperledger Fabric: A Distributed Operating System for Permissioned Blockchains. arXiv 2018, arXiv:1801.10228. [Google Scholar] [CrossRef]
- Nasir, Q.; Qasse, I.A.; Abu Talib, M.; Nassif, A.B. Performance Analysis of Hyperledger Fabric Platforms. Secur. Commun. Netw. 2018, 2018, 1–14. [Google Scholar] [CrossRef]
- Popov, S. The Tangle. Available online: https://assets.ctfassets.net/r1dr6vzfxhev/2t4uxvsIqk0EUau6g2sw0g/45eae33637ca92f85dd9f4a3a218e1ec/iota1_4_3.pdf (accessed on 2 April 2021).









Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Delgado-von-Eitzen, C.; Anido-Rifón, L.; Fernández-Iglesias, M.J. Application of Blockchain in Education: GDPR-Compliant and Scalable Certification and Verification of Academic Information. Appl. Sci. 2021, 11, 4537. https://doi.org/10.3390/app11104537
Delgado-von-Eitzen C, Anido-Rifón L, Fernández-Iglesias MJ. Application of Blockchain in Education: GDPR-Compliant and Scalable Certification and Verification of Academic Information. Applied Sciences. 2021; 11(10):4537. https://doi.org/10.3390/app11104537
Chicago/Turabian StyleDelgado-von-Eitzen, Christian, Luis Anido-Rifón, and Manuel J. Fernández-Iglesias. 2021. "Application of Blockchain in Education: GDPR-Compliant and Scalable Certification and Verification of Academic Information" Applied Sciences 11, no. 10: 4537. https://doi.org/10.3390/app11104537
APA StyleDelgado-von-Eitzen, C., Anido-Rifón, L., & Fernández-Iglesias, M. J. (2021). Application of Blockchain in Education: GDPR-Compliant and Scalable Certification and Verification of Academic Information. Applied Sciences, 11(10), 4537. https://doi.org/10.3390/app11104537








