Abstract
Establishing global secure networks is a potential implementation of continuous-variable quantum key distribution (CVQKD) but it is also challenged with respect to long-distance transmission. The discrete modulation (DM) can make up for the shortage of transmission distance in that it has a unique advantage against all side-channel attacks; however, its further performance improvement requires source preparation in the presence of noise and loss. Here, we consider the effects of photon catalysis (PC) on the DM-involved source preparation for improving the transmission distance. We address a zero-photon-catalysis (ZPC)-based source preparation for enhancing the DM–CVQKD system. The statistical fluctuation is taken into account for the practical security analysis. Numerical simulations show that the ZPC-based source preparation can not only achieve the long-distance transmission, but also contributes to the reasonable increase of the secret key rate.
1. Introduction
Quantum key distribution (QKD) [1,2,3,4] allows legal participants to share a secret key and enables theoretically information-secure communications [5,6,7]. Recently, it has spurred much interest, resulting in two approaches, i.e., discrete-variable (DV) QKD [8,9] and continuous-variable (CV) QKD [10,11,12,13,14,15,16,17,18,19,20]. A possible breakthrough may come from the practical implementation of CVQKD, which has an advantage of being practically implemented with modern telecommunications, thus allowing for the exploitation of the heritage of integrability in existing optical communication system.
At present, there are several mainstream modulations in CVQKD, such as Gaussian modulation (GM) [11,12,13,14,15] and discrete modulation (DM) [16,17,18,19,20]. In the former, the transmitter generates the key bits in the quadratures of the Gaussian modulated optical field, while the receiver recovers the secret key using a coherent detector [13]. It is GM–CVQKD that could achieve the potential high secret key rate. Unfortunately, it is still limited to the transmission distance, compared with its DVQKD counterpart. A challenge is that the resulting reconciliation efficiency [14,15] is still low, which is unsuitable for long-distance transmission, whereas in the latter, one can solve this problem by using a DM source for CVQKD [16], where it generates nonorthogonal coherent states, taking advantage of the randomly measured quadrature for information encoding rather than exploiting the fixed quadrature in source preparation [17]. Consequently, it results in a merit of both high reconciliation efficiency and high tolerance against the excess noise [11,12,13,14,15] such that it can extend the transmission distance of the CVQKD system [18]. Actually, GM–CVQKD is simpler for theoretical performance analysis than DM–CVQKD, and the secret key rates can approach the theoretical limits [17], whereas GM–CVQKD itself is alway approximated by the DM sources, which may be taken into account for security analysis [18]. Moreover, as GM–CVQKD usually requires more resources in terms of randomness and classical post-processing resources, DM–CVQKD can offer further simplified implementation in experiments. While theoretics and experiments of DM–CVQKD have suggested that we can achieve the above-mentioned goal, there are still some potential challenges while promoting its performances.
Currently, photon catalysis (PC) [21,22,23,24,25], which is a non-Gaussian operation with n-photon state input/output in essence, has been utilized for security improvement attributed to the photon catalyzing operation, which increases the entanglement degree of the two-participant system by increasing the correlation between the transmitter and the receiver [21]. In a certain low-squeezing parameter, the entanglement of the two-mode squeezed vacuum (TMSV) state can be enhanced by increasing the catalysis photon number [22]. Due to equivalence of the entanglement-based (EB) CVQKD system and the prepare-and-measure (PM) CVQKD system [11,12,13,14,15,16,17,18,19,20], the PC-involved DM–CVQKD system may be implemented with existing optical technologies. Motivated by the above advantages, we propose an improved DM–CVQKD system through photon catalyzing. The DM scheme is employed for the source preparation because it can tolerate a lower signal-to-noise ratio (SNR) well, resulting in the long-distance transmission of the CVQKD system. Meanwhile, a zero-photon catalysis (ZPC) operation with zero-photon state input/output is adopted in the DM-involved source preparation at the transmitter. The ZPC-based CVQKD protocol has been proven to be beneficial for tolerating lower reconciliation efficiency [24,25] and extending the maximal transmission distance, thus promoting its practical implementations with underlying technology.
As for the performance analysis of the proposed DM–CVQKD system, we take into account the asymptotic case [17] where the secure key rate can be obtained via the covariance matrix approach. It is a theoretically calculated value without involving the finite-size effect. Unfortunately, the derived upper bound is difficult to obtain in practical implementations. Therefore, we have to consider the finite-size effects [26,27]. Though the secure key rate is still pessimistic, it approaches to the practical implementation. Its security analysis is based on the finite-size effects; hence, we can achieve the upper bound of the maximal transmission distance.
This paper is structured as follows. In Section 2, we propose the PC-based DM source for CVQKD, and then elaborate on the characteristics of the ZPC-based scheme for improving the DM–CVQKD system. In Section 3, we demonstrate the transmission distance improvement of the DM–CVQKD system via the ZPC-based source preparation scheme. Finally, we draw a conclusion in Section 4.
2. The DM Source Preparation via ZPC Operations
In what follows, we elaborate the ZPC-involved DM source preparation for performance improvement of the CVQKD system. To make the derivation self-contained, we suggest the ZPC-involved CVQKD system with the DM source preparation.
2.1. The CVQKD System with the DM Source Preparation
For the prepare-and-measure (PM) version of CVQKD that can be used for practical implementations, Alice randomly draws n quaternary or octal variables, each corresponding to a coherent state of , where is a real positive number related to the modulation variance of coherent state given by [16,17,18,19,20]. For and , we have the four-state DM source and the eight-state DM source, as shown in Figure 1 [28,29].
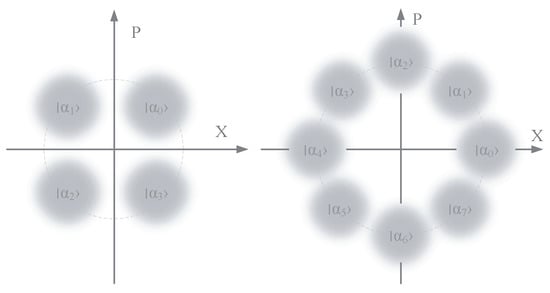
Figure 1.
The discrete-modulation (DM)-based sources for four states (left) and eight states (right).
Alice generates n coherent states, which are sent through quantum channel characterized by transmission T and excess noise . Then, for the received state, Bob measures one of quadratures (i.e., or ) by homodyne detector.
Theoretical analysis of CVQKD is considered through using its equivalent entanglement-based (EB) version. The transmitter Alice starts with a pure bipartite state with variance . Subsequently, she performs a projective measurement on the first half of this state, whereas the second half is sent to the receiver Bob. For the DM–CVQKD protocol, to apply the security analysis technique as the GM–CVQKD protocol [11,12,13,14,15], we therefore want to find a purification with a covariance matrix . This covariance matrix has the form given by [26,27]
where and . For example, taking into account, we have the four-state scheme given by
with the parameters and given by and [24].
We note that the DM source has a positive effect on CVQKD. For example, we have for and in the DM–CVQKD protocol, where represents the GM–CVQKD protocol. However, it is difficult to distinguish , and for , as shown in Figure 2. Therefore, we attempt to derive the security bounds of DM–CVQKD referring to that of GM–CVQKD.
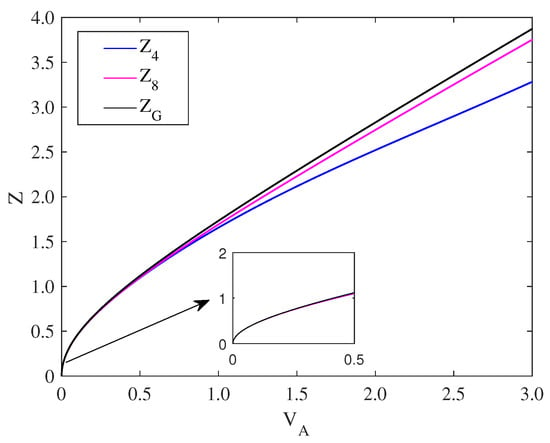
Figure 2.
The correlation comparison of , and .
2.2. The ZPC-Based DM Source Preparation
It is known that ZPC, which is a non-Gaussian operation with zero-photon state input/output [21,22], can enhance the correlation of the two-participant entangled quantum system [25,30]. In what follows, we suggest an improved CVQKD system with ZPC operation for the DM source preparation, as shown in Figure 3. In the auxiliary mode C, the zero-photon Fock state is injected at one input port of beam splitter (BS) with transmittance , and quantum state of the mode B is simultaneously injected at another input port. Subsequently, we detect the zero-photon Fock state at one of the output ports of the BS using a photon number resolving detector (PNRD), resulting in the ZPC-enhanced quantum state from another output port.
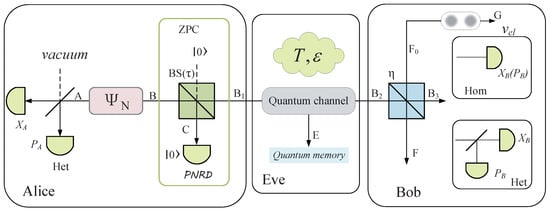
Figure 3.
Schematic diagram of continuous-variable quantum key distribution (CVQKD) with zero-photon-catalysis (ZPC)-based DM source preparation.
Similar to the traditional photon subtraction operation [30,31,32,33], the ZPC operation can be used for performance improvement of CVQKD. In order to describe the ZPC-based DM source preparation, the ZPC operation can be described as [22,25]
For an input , we have output given by
where denotes the success probability of the operation given by as function of parameters and , as shown in Figure 4. We find that the large and result in the high success probability. Note that we have for , indicating that there is no ZPC effect.
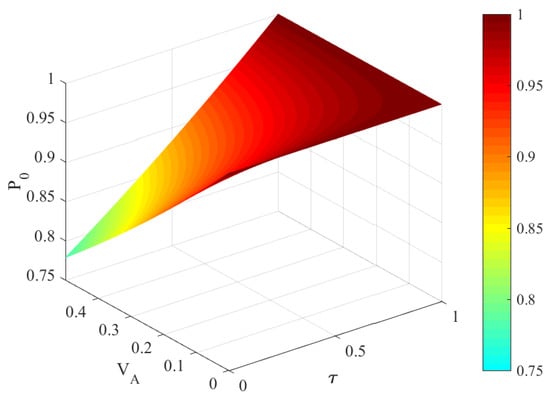
Figure 4.
Success probabilities of ZPC with transmittances and modulation variance .
In the PM version of CVQKD, Alice randomly draws n quaternary or octal variables, each corresponding to a coherent state of . Subsequently, Alice performs the ZPC operation on these n coherent states, which is modeled (BS) with transmittance , resulting in the catalyzed state
We note that the relationship of the transformed amplitudes can be written as . After that, the catalyzed quantum state is sent to Bob through the Eve-controlled channel. Bob may perform either homodyne (Hom) or heterodyne (Het) detection on the resulting quantum state. Finally, Alice and Bob distill the shared secret key after they conduct the classical post-processing procedure. In the EB version of the CVQKD system, as shown in Figure 3, Alice prepares for , and performs heterodyne detection (Het) on mode A. Mode B, which is performed with the ZPC operation, is sent to Bob. The role of the ZPC operation is for source-entanglement enhancement while promoting the mode transition between B and , resulting in the covariance matrix of the catalyzed state given by
with the parameters
where the calculation of is similar to that of in Equation (2), but note that is replaced by .
We note that we can obtain the effect of the ZPC operation on the DM source from the derived covariance matrix . The parameter , which can be calculated from modulation variances of the initially prepared coherent states, demonstrates the relation of the modes A and for source preparation. In what follows, we will show the effect of on the performance of the CVQKD system.
In addition, there are the other similar operations, such as local Gaussian operation [34], photon subtraction and addition operations [35], which can be used for improving entanglement of a two-mode state. These operations, whether they are Gaussian or not, may be similarly employed for source preparation while considering performance improvement of the CVQKD system. However, due to the elegant structure of the ZPC operation that can be conventionally integrated with the practical quantum system, in this paper, we consider the ZPC-based DM source preparation for extending the maximal transmission distance of the CVQKD system.
3. Security Analysis
In this section, we demonstrate the effect of the DM source preparation on CVQKD in both asymptotic [32,33] and finite-size cases [33] with numeric simulation results. For the detailed derivation of the secret key rate of the CVQKD system in asymptotic and finite-size cases, please see Appendices Appendix A and Appendix B, respectively.
For the ZPC-based DM source preparation, we show the success probability of ZPC operation in Figure 4. We find that the success probability increases with the increased modulation variance, and simultaneously increases with the increased transmittance. In the security analysis, the transmittance is tunable to satisfy the optimality of the ZPC operation. Taking into account, no matter what the value of is, the success probability can remain more than 0.75. This is a feasible solution to improve the CVQKD system.
As usual, it is necessary to select an optimal modulation variance for the performance improvement of CVQKD involving the ZPC operation. As shown in Figure 5, solid lines denote the secret key rate of the eight state CVQKD system, while dashed lines represent that of the four-state CVQKD system. In addition, we let , and . We find that for , the secret key rate decreases as the transmission distance, while the inserted subgraph shows that the secret key rate decreases with the excess noise at the distance of 80km. Moreover, for the secret key rate can reach the optimal value, and hence we let in the subsequent simulations.
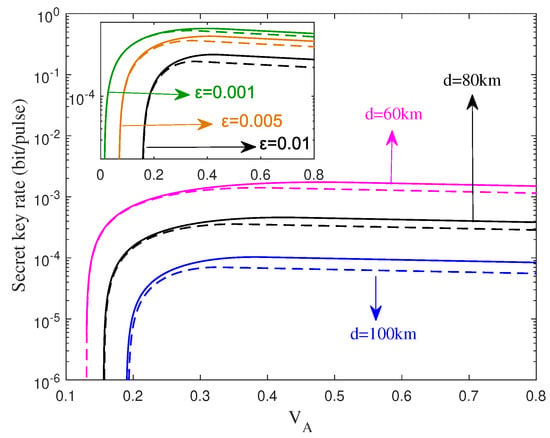
Figure 5.
Asymptotic secret key rate of the CVQKD system with the ZPC-based DM source preparation for , where solid lines denote the eight-state DM source preparation, while dashed lines represent the four-state DM source preparation. The inserted subgraph shows that asymptotic secret key rate of the CVQKD system for L = 80 km.
In Figure 6a, we show the asymptotic secret key rate of the ZPC-based CVQKD system, where solid lines denote homodyne detection and dashed lines represent heterodyne detection. It seems that performances of homodyne and heterodyne detectors are almost similar, and thus we employ the homodyne detector in security analysis. The performance of the ZPC-based CVQKD is better than that of the traditional CVQKD whether it is four-state modulation or not.
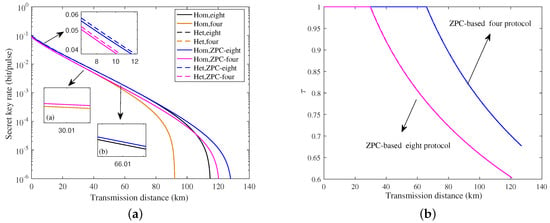
Figure 6.
(a) Asymptotic secret key rate of DM–CVQKD involving the ZPC operation for , where solid lines denote homodyne detection, while dashed lines heterodyne detection. (b) Corresponding to (a), the transmittance varies with the transmission distance.
The eight-state modulation scheme demonstrates better performance than the four-state modulation scheme in the traditional CVQKD system. However, after performing the ZPC operation, the performance of the ZPC-based four-state modulation scheme exceeds the eight-state modulation scheme. Therefore, the ZPC-based source preparation is an effective way to improve the DM–CVQKD system. We note that the effect of the ZPC operation does not work over the whole transmission distance. In the short distance range, there are few catalytic effects. As shown in Figure 6b, the performance of the ZPC-based system is almost similar to that of the traditional system for . For the four-state DM source preparation, the ZPC effect occurs at the distance of L = 60 km, whereas for the eight-state DM source preparation, it occurs at L = 30 km.
Usually, one assumes that the quantum channel is given in an asymptotic regime. However, one does not know the quantum channel in advance in the finite-size scenario. Therefore, we take into account effect of the finite-size on the ZPC-based CVQKD. As shown in Figure 7, the proposed CVQKD system in finite-size scenario performs worse than that in the asymptotic limit. As the number N of the exchanged signals is increased, the corresponding curves approach to the asymptotic scenario. The reason is that the large number of the exchanged signals results in the perfect signals parameter estimation. However, it is infeasible to achieve the infinite number of the exchanged signals in practice. Nonetheless, it still has resulted in an improvement, compared with the traditional system in the finite-size regime, as shown in Figure 8.
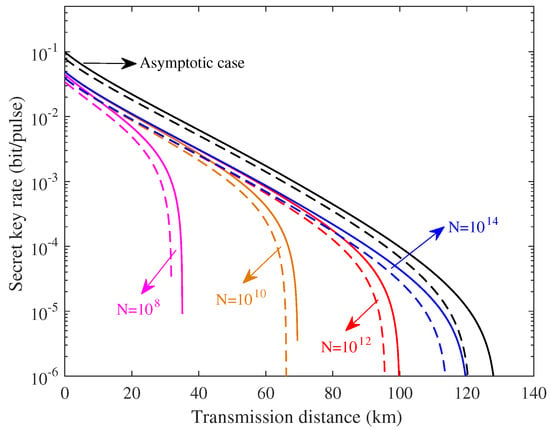
Figure 7.
Finite-size key rate of CVQKD involving the ZPC operation for , where solid lines represent the eight-state DM source preparation and dotted lines represent the four-state DM source preparation, respectively.
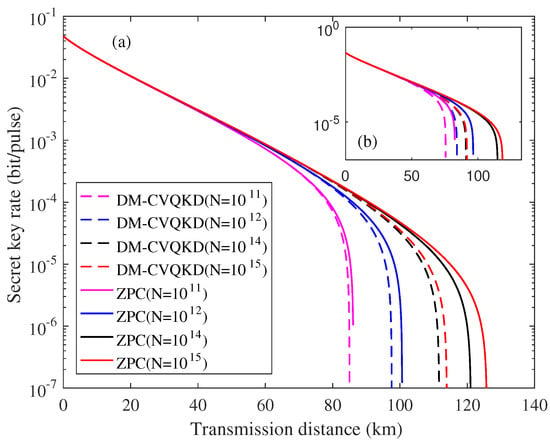
Figure 8.
Finite-size key rate of CVQKD involving the ZPC operation for , where the (a) represents eight-state DM source preparation, and inset (b) represents four-state DM source preparation.
In addition, we show the effect of the ZPC-involved source on the tolerable excess noise of CVQKD, as shown in Figure 9. We find that CVQKD involving the ZPC-involved source performs better than the traditional system in terms of maximal transmission distance.
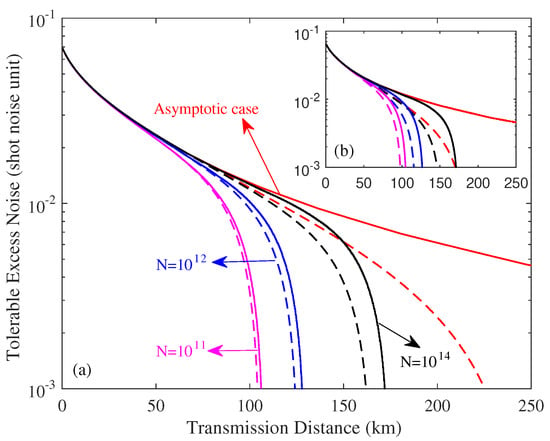
Figure 9.
The maximal tolerable excess noise of CVQKD involving the ZPC operation (dotted lines and solid lines) for the traditional CVQKD (dotted lines) and the ZPC-based CVQKD (solid lines), where (a) represents eight-state DM source preparation, and inset (b) represents four-state DM source preparation.
Moreover, reconciliation efficiency is the other important parameter that has an effect on the performance of CVQKD. Figure 10 suggests the effect of the ZPC-based source on the secret key rate of CVQKD related to the reconciliation efficiency. We find that the ZPC-based source can tolerate low reconciliation efficiency. Therefore, the ZPC-based source preparation can reduce the requirements for reconciliation efficiency, thereby reducing costs of practical implementation of the high-rate long-distance quantum communications.
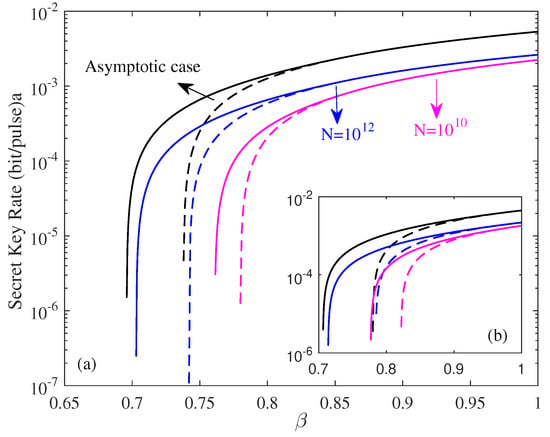
Figure 10.
The secret key rate of the CVQKD system involving the ZPC operation with L = 50 km and for the traditional CVQKD system (dotted lines) and the ZPC-based CVQKD system (solid lines), where (a) represents eight-state DM source preparation, and inset (b) represents four-state DM source preparation.
4. Conclusions
We have suggested a ZPC-based source preparation scheme for improving the DM–CVQKD system in metropolitan areas. The PC operation, which is non-Gaussian, has been deployed for the source preparation at the transmitter. We consider the effect of the ZPC-based DM source on the performance of CVQKD. Numerical simulations show that the ZPC-involved DM source can extend the maximal transmission distance of the CVQKD system. Moreover, it can tolerate high excess noise and low reconciliation efficiency, compared with the traditional CVQKD system. Taking the finite-size effect into account, we obtain the tight bound of the maximal transmission distance, which can be experimentally achieved with state-of-the-art technologies.
Author Contributions
Writing–original draft preparation, Z.Z. and Y.G.; software, S.Z.; validation and formal analysis, T.H.; supervision, Y.G. All authors have read and agreed to the published version of the manuscript.
Funding
This work was supported by the National Natural Science Foundation of China (Grant No. 61871407).
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A. Calculation of Asymptotic Secret Key Rate
We assume that Eve performs the Gaussian collective attack to achieve the useful results, and the information obtained is limited to the Holevo range . The definition of secret key rate in the case of reverse reconciliation under collective attacks can be given by
where is the reconciliation efficiency, is the Shannon mutual information between Alice and Bob, and is the Holevo bound of the mutual information between Eve and Bob. The mutual information for homodyne detection is derived as
where represents the total noise given by and represents the total channel-added noise given by . The transmission efficiency T is calculated as , where dB/km is the loss coefficient for the standard optical fibers and L is the length of the fiber optics. For homodyne detection, the detection-added noise referred to Bob’s input can be given by
Note that in the case of heterodyne detection, we have,
After Bob applies homodyne or heterodyne measurement, Eve purifies the whole system so that the mutual information between Eve and Bob can be expressed as
where the first term is a function of the symplectic eigenvalues of , which is given by
where and are symplectic eigenvalues of covariance matrix
Consequently, we have
where A and B are parameters given by
The second term is a function of the symplectic eigenvalues of the convariance matrix of Alice’s mode after Bob performs homodyne (heterodyne) detection, which is given by
with the symplectic eigenvalues
For homodyne detection, we have
with . For heterodyne detection, we have
Appendix B. Secret Key Rate in the Finite-Size Scenario
In the following, let the notation N represent the total number of signals exchanged by Alice and Bob during the protocol. The x and y represent the classical data of Alice and Bob after they have measured their quantum states, and E refers to the quantum state of the eavesdropper. In the case of the CVQKD system, the secret key rate obtained for a finite size analysis can be given by
where represents n signals are used for the establishment of the key, out of the N signals exchanged. The notation is defined as the maximum of the Holevo information compatible with the statistics except with probability , where is the failure probability of parameter estimation. The parameter is related to the security of the privacy amplification given by
where is the Hilbert space corresponding to the variable y used in the raw key. Since the raw key is usually encoded on binary bits, we have . In addition, is a smoothing parameter, and is the failure probability of the privacy amplification procedure. Both the smoothing parameter and are intermediate parameters which should be optimized numerically. One needs to fix an overall security parameter e for the performance analysis of the CVQKD system. Compared with the unconditional security in the case of asymptotic scenario, the CVQKD system is limited to e-security in a finite-size setting. The parameter e corresponds to the failure probability of the whole protocol, meaning that the protocol is assured to performed as it is supposed to except with a probability at most e. The failure probability e can be computed from the various parameters as follows
where is the probability that the reconciliation fails. The above-mentioned error probabilities can be set to .
In the finite-size scenario, needs to be calculated in parameter estimation procedure where one can find a covariance matrix , which minimizes the secret key rate with a probability of at least . The estimation of can be calculated by couples of correlated variables in the following form
where and correspond respectively to the minimal value of t and the maximal value of compatible with the sampled data, except with probability . With the maximum likelihood estimators, we have
where is such that and is the error function given by
References
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145. [Google Scholar] [CrossRef]
- Zhou, J.; Huang, D.; Guo, Y. Long-distance continuous-variable quantum key distribution using separable Gaussian states. Phys. Rev. A 2018, 98, 042303. [Google Scholar] [CrossRef]
- Guo, Y.; Xie, C.; Huang, P.; Li, J.; Zhang, L.; Huang, D.; Zeng, G. Channel-parameter estimation for satellite-to-submarine continuous-variable quantum key distribution. Phys. Rev. A 2018, 97, 052326. [Google Scholar] [CrossRef]
- Liao, Q.; Wang, Y.; Huang, D.; Guo, Y. Dual-phase-modulated plug-and-play measurement-device-independent continuous-variable quantum key distribution. Opt. Express 2018, 26, 19907–19920. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Tamaki, K. Secure quantum key distribution. Nat. Photon 2014, 8, 595. [Google Scholar] [CrossRef]
- Wootters, W.K.; Zurek, W.H. A single quantum cannot be cloned. Nature 1982, 299, 802. [Google Scholar] [CrossRef]
- Bang, J.Y.; Berger, M.S. Quantum mechanics and the generalized uncertainty principle. Phys. Rev. D 2006, 74, 125012. [Google Scholar] [CrossRef]
- Shor, P.W.; Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 2000, 85, 441. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef]
- Soh, D.B.S.; Brif, C.; Coles, P.J.; Lutkenhaus, N.; Camacho, R.M.; Urayama, J.; Sarovar, M. Self-referenced continuous-variable quantum key distribution protocol. Phys. Rev. X 2015, 5, 041010. [Google Scholar] [CrossRef]
- Grosshans, F.; Grangier, P. Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 2002, 88, 057902. [Google Scholar] [CrossRef]
- Grosshans, F.; van Assche, G.; Wenger, J.; Brouri, R.; Cerf, N.J.; Grangier, P. Quantum key distribution using gaussian-modulated coherent states. Nature 2003, 421, 238. [Google Scholar] [CrossRef]
- Liao, Q.; Guo, Y.; Huang, D.; Huang, P.; Zeng, G. Long-distance continuous-variable quantum key distribution using non-Gaussian state-discrimination detection. New. J. Phys. 2018, 023015. [Google Scholar] [CrossRef]
- Braunstein, S.L.; van Loock, P. Quantum information with continuous variables. Rev. Mod. Phys. 2005, 77, 513. [Google Scholar] [CrossRef]
- Ma, X.C.; Sun, S.H.; Jiang, M.S.; Gui, M.; Liang, L.M. Gaussian-modulated coherent-state measurement-device-independent quantum key distribution. Phys. Rev. A 2014, 89, 042335. [Google Scholar] [CrossRef]
- Leverrier, A.; Grangier, P. Unconditional security proof of long-distance continuous-variable quantum key distribution with discrete modulation. Phys. Rev. Lett. 2009, 102, 180504. [Google Scholar] [CrossRef]
- Takeoka, M.; Guha, S.; Wilde, M.M. Fundamental rate-loss tradeoff for optical quantum key distribution. Nat. Commun. 2014, 5, 5235. [Google Scholar] [CrossRef]
- Furrer, F.; Franz, T.; Berta, M.; Leverrier, A.; Scholz, V.B.; Tomamichel, M.; Werner, R.F. Continuous variable quantum key distribution: Finite-key analysis of composable security against coherent attacks. Phys. Rev. Lett. 2012, 109, 100502. [Google Scholar] [CrossRef]
- Leverrier, A.; Grangier, P. Continuous-variable quantum-key-distribution protocols with a non-Gaussian modulation. Phys. Rev. A 2011, 83, 042312. [Google Scholar] [CrossRef]
- Mao, Y.; Wang, Y.; Huang, W.; Zhong, H.; Qin, H.; Guo, Y.; Huang, D. Detecting quantum attacks: A machine learning based defense strategy for practical continuous-variable quantum key distribution. New J. Phys. 2020, 22, 083073. [Google Scholar] [CrossRef]
- Guo, Y.; Ye, W.; Zhong, H.; Liao, Q. Continuous-variable quantum key distribution with non-Gaussian quantum catalysis. Phys. Rev. A 2019, 99, 032327. [Google Scholar] [CrossRef]
- Ye, W.; Zhong, H.; Liao, Q.; Huang, D.; Hu, L.; Guo, Y. Improvement of self-referenced continuous-variable quantum key distribution with quantum photon catalysis. Opt. Express 2019, 27, 17186–17198. [Google Scholar] [CrossRef]
- Xu, X. Enhancing quantum entanglement and quantum teleportation for two-mode squeezed vacuum state by local quantum-optical catalysis. Phys. Rev. A 2015, 92, 012318. [Google Scholar] [CrossRef]
- Guo, Y.; Ding, J.Z.; Mao, Y.; Ye, W.; Liao, Q.; Huang, D. Quantum catalysis-based discrete modulation continuous variable quantum key distribution with eight states. Phys. Lett. A 2020, 384, 126340. [Google Scholar] [CrossRef]
- Ye, W.; Guo, Y.; Xia, Y.; Zbinden, H.; Zhang, H.; Ding, J.Z.; Hu, L.Y. Discrete modulation continuous-variable quantum key distribution based on quantum catalysis. Acta Phys. Sinica 2020, 69, 060301. [Google Scholar]
- Leverrier, A.; Grosshans, F.; Grangier, P. Finite-size analysis of a continuous-variable quantum key distribution. Phys. Rev. A 2010, 81, 062343. [Google Scholar] [CrossRef]
- Guo, Y.; Li, R.J.; Liao, Q.; Zhou, J.; Huang, D. Performance improvement of eight-state continuous-variable quantum key distribution with an optical amplifier. Phys. Lett. A 2018, 382, 372–381. [Google Scholar] [CrossRef]
- Mao, Y.; Wang, Y.; Huang, W.; Qin, H.; Huang, D.; Guo, Y. Hidden-Markov-model-based calibration-attack recognition for continuous-variable quantum key distribution. Phys. Rev. A 2020, 101, 062320. [Google Scholar] [CrossRef]
- Wang, Y.; Mao, Y.; Huang, W.; Huang, D.; Guo, Y. Optical frequency comb-based multichannel parallel continuous-variable quantum key distribution. Opt. Express 2019, 27, 25314–25329. [Google Scholar] [CrossRef] [PubMed]
- Li, Z.; Zhang, Y.; Wang, X.; Xu, B.; Peng, X.; Guo, H. Non-Gaussian postselection and virtual photon subtraction in continuous-variable quantum key distribution. Phys. Rev. A 2016, 93, 012310. [Google Scholar] [CrossRef]
- He, Y.Q.; Mao, Y.; Zhong, H.; Huang, D.; Guo, Y. Hybrid linear amplifier-involved detection for continuous variable quantum key distribution with thermal states. Chin. Phys. B 2020, 29, 050309. [Google Scholar] [CrossRef]
- Guo, Y.; Liao, Q.; Wang, Y.; Huang, D.; Huang, P.; Zeng, G. Performance improvement of continuous-variable quantum key distribution with an entangled source in the middle via photon subtraction. Phys. Rev. A 2017, 95, 032304. [Google Scholar] [CrossRef]
- Wu, X.; Wang, Y.; Zhong, H.; Ye, W.; Huang, D.; Guo, Y. Continuous-variable measurement-device-independent quantum key distribution via quantum catalysis. Quantum Infor. Process. 2020, 19, 234. [Google Scholar] [CrossRef]
- Ryu, J.; Lim, J.; Lee, C.; Lee, J. Nonlocality for continuous variable system with local symplectic operation. J. Mod. Opt. 2010, 57, 1550–1554. [Google Scholar] [CrossRef]
- Lee, S.-Y.; Ji, S.-W.; Kim, H.-J.; Nha, H. Enhancing quantum entanglement for continuous variables by a coherent superposition of photon subtraction and addition. Phys. Rev. A 2011, 84, 012302. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).