Contextual Evaluation of Risk Identification Techniques for Construction Projects: Comparative Insights and a Decision-Support Model
Abstract
1. Introduction
- Few comparative implementations of Delphi, NGT, HAZOP, and PHA in construction projects, particularly in developing contexts.
- Limited investigation of contextual determinants, such as project type, institutional maturity, and stakeholder dynamics.
- Lack of operational selection tools that can guide practitioners in choosing the most appropriate risk identification technique.
2. Background
2.1. Risk Management in Construction Projects
2.2. Classification of Risk Identification Techniques
- Conventional heuristic methods, such as checklists and brainstorming, are among the most frequently used tools in construction projects due to their ease of implementation and low resource requirements [27].
- The second category, group-based consensus techniques, includes structured expert judgment approaches such as the Delphi Method and the NGT. These methods aim to overcome the limitations of conventional tools by promoting systematic feedback, minimizing social bias, and enhancing group decision-making through iterative or structured procedures [28].
- The third category encompasses system-based analytical approaches, notably HAZOP and PHA. Originating from the chemical and process industries, these methods have been adapted for use in construction and infrastructure projects where technical complexity and safety concerns are prominent [29].
2.3. Risk Identification Methods
2.4. Research Gap
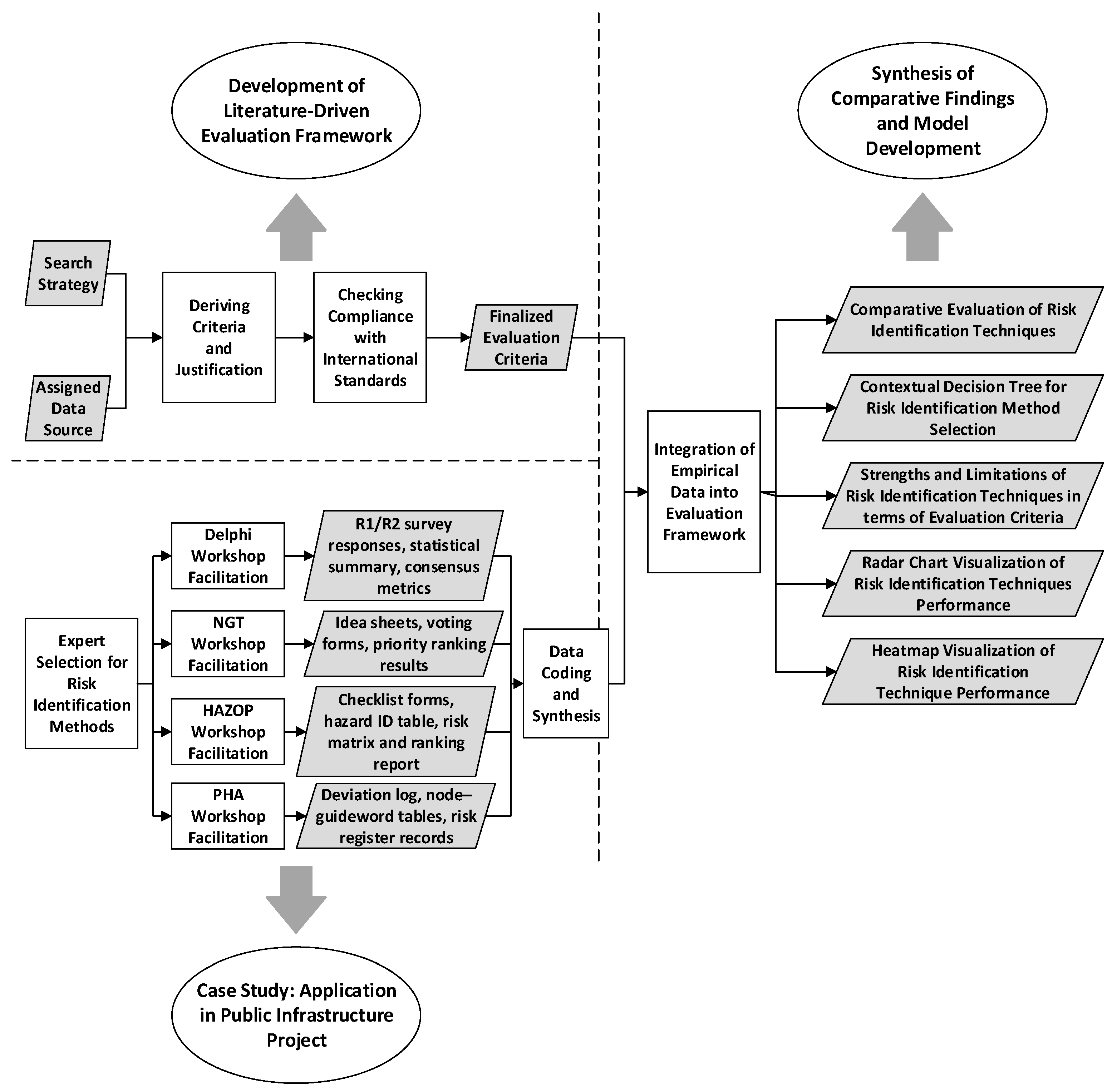
3. Materials and Methods
- (1)
- literature-driven development of evaluation criteria,
- (2)
- empirical data collection and synthesis through multiple structured techniques, and
- (3)
- comparative analysis and contextual model development (Figure 1).
3.1. Research Design
3.2. Literature-Driven Framework Development
3.2.1. Data Collection and Source Selection for Criteria Determination
3.2.2. Development of Evaluation Framework
- Triangulation across multiple data sources and literature domains was performed.
- Operational definitions were developed for each criterion to ensure clarity and consistency in assessment.
- Reflexivity was maintained throughout the case study application to address subjectivity and contextual variability.
3.3. Empirical Data Collection and Case-Based Application
3.3.1. Participant Selection
3.3.2. Data Coding and Synthesis, and Integration with Evaluation Criteria
3.3.3. Evaluation Procedure, Member Checking and Reflexivity
3.3.4. Project Background and Context
3.3.5. Implementation of Risk Identification Techniques
4. Results
4.1. Quantitative Traceability of Risk Outputs
4.2. Risk Identification
4.3. Risk Categorization
5. Discussion
5.1. Validation Against Real-World Risk Data
5.2. Comparative Evaluation of Structured Risk Identification Techniques
5.3. Comparative Evaluation Matrix
5.4. Cognitive and Behavioral Dimensions of Method Deployment
5.5. Integration with Broader Risk Management Architecture
5.6. Empirical Validation Through Case Study
5.7. Comparative Reflections Based on Evaluation Criteria
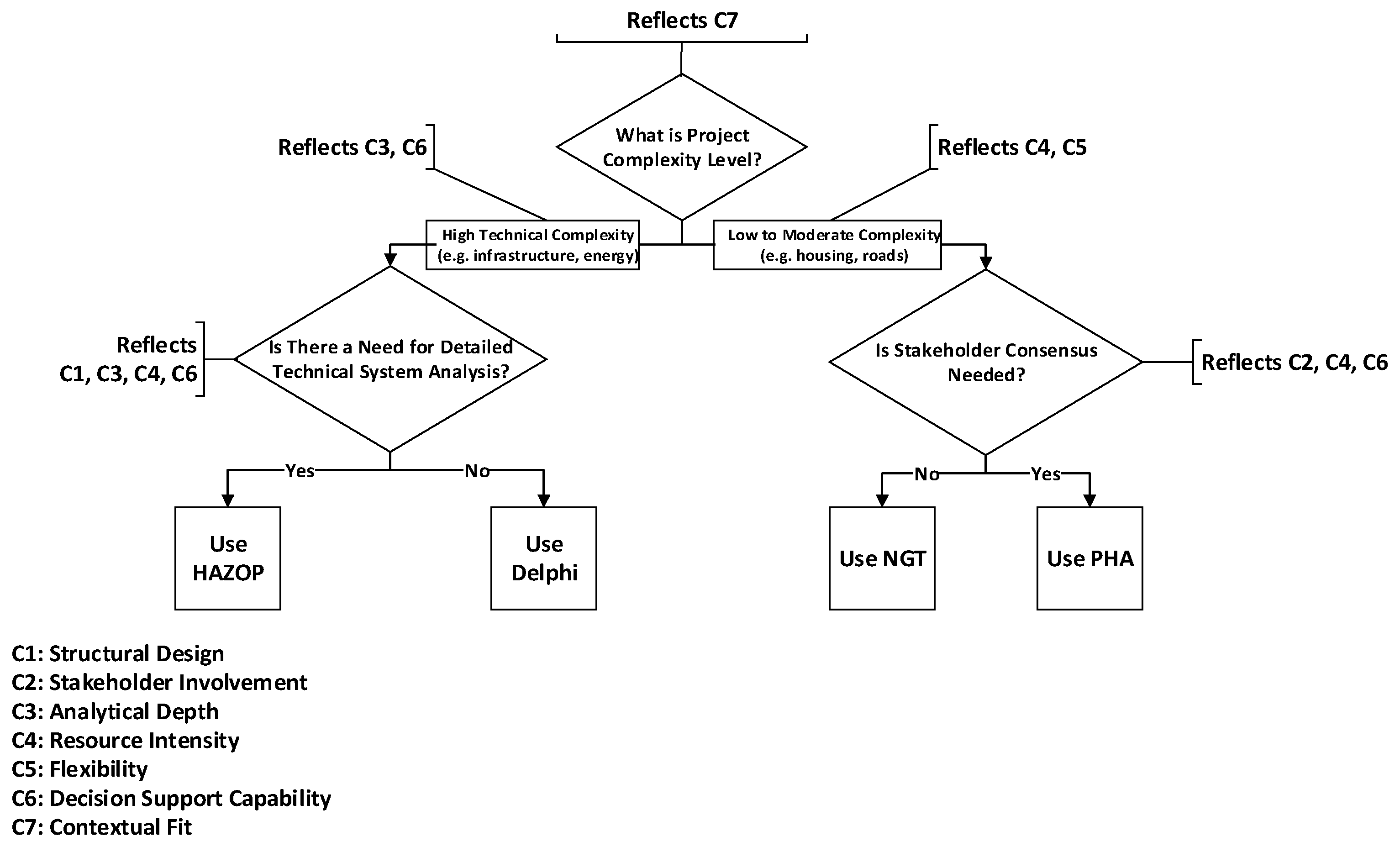
5.8. Contextual Decision Support Model for Risk Identification Method Selection
5.8.1. Worked Examples: Application of the Decision Model
5.8.2. Application Pathways: Owners, Contractors and Insurance Companies
5.8.3. Applicability in Developed and Global Construction Contexts
5.8.4. Positioning the Study Within Decision-Support Systems for Construction Risk Management
5.9. Comparative Contextual Evaluation of Risk Identification Techniques
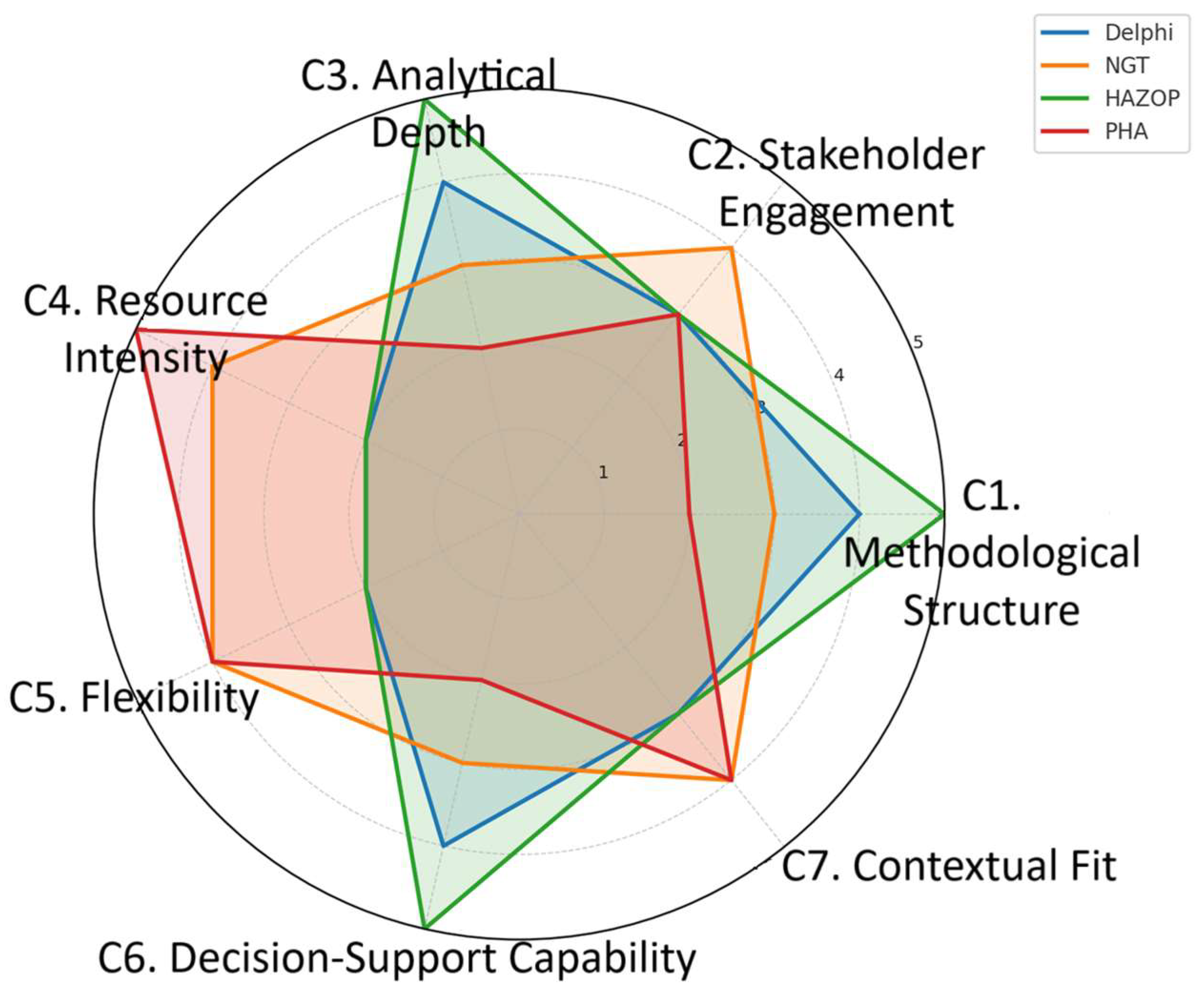
5.10. Radar Chart Visualization of Comparative Performance Across Risk Identification Techniques
5.11. Heatmap Visualization of Technique Performance by Evaluation Criteria
5.12. Summary and Implications
6. Research Limitations and Recommendations for Further Research
6.1. Limitations of Study
6.2. Directions for Future Research
6.2.1. Hybrid and Stepwise Applications of Risk Identification Techniques
6.2.2. Emerging Digital Approaches to Risk Identification
7. Conclusions
7.1. Theoretical Contributions
7.2. Practical Contributions
7.3. Methodological Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| AHP | Analytical Hierarchy Process |
| AI | Artificial Intelligence |
| APM | Association for Project Management |
| BoK | Body of Knowledge |
| BIM | Building Information Modeling |
| CDC | Centers for Disease Control and Prevention |
| CPWR | The Center for Construction Research and Training |
| HAZOP | Hazard and Operability Study |
| HSE | Health and Safety Executive |
| IQR | Interquartile Range |
| ISO | International Organization for Standardization |
| MCDM | Multi-Criteria Decision-Making |
| NGT | Nominal Group Technique |
| OHS | Occupational Health and Safety |
| OSHA | Occupational Safety and Health Administration |
| PHA | Preliminary Hazard Analysis |
| PMBOK | Project Management Body of Knowledge |
| PMI | Project Management Institute |
| PRISMA | Preferred Reporting Items for Systematic Reviews and Meta-Analyses |
| TOPSIS | Technique for Order Preference by Similarity to an Ideal Solution |
Appendix A. Delphi Template
Appendix A.1. General Design and Instructions
- Round 1 (R1): Exploration and initial rating, involving open risk listing, structured Likert-scale assessments, and justification of responses.
- Round 2 (R2): Controlled feedback and re-rating, where participants were provided with group-level statistical summaries (median and interquartile range) and asked to reconsider their ratings, particularly if they diverged significantly from the panel consensus.
- IQR ≤ 1 interpreted as high consensus,
- 1 < IQR ≤ 1.5 as moderate consensus,
- IQR > 1.5 as low consensus
Appendix A.2. Round 1 Questionnaire (Exploration and Initial Rating)
| Risk ID | Risk Statement | Category | Median (L/I) | IQR (L/I) | Notes |
|---|---|---|---|---|---|
| R-03 | Unexpected groundwater inflows during excavation | Geotechnical | 4/5 | 1/1 | High consensus; safety & cost critical |
| R-07 | Critical equipment delivery delay (>8 weeks) | Supply Chain | 3/5 | 1/2 | Moderate consensus; major impact on schedule |
| R-12 | Design errors requiring rework during construction | Design/Quality | 4/4 | 1/1 | High consensus; recurring issue in past projects |
Appendix A.3. Round 2 Questionnaire (Controlled Feedback and Re-Rating)
| Risk ID | Risk Statement | R1 Median/IQR | R2 Median/IQR | Consensus Status | Revised Priority Rank | Notes |
|---|---|---|---|---|---|---|
| R-03 | Unexpected groundwater inflows during excavation | 4/5 (1/1) | 4/5 (1/0) | Improved to High Consensus | Top 3 | Consensus achieved after R2 re-rating |
| R-07 | Critical equipment delivery delay (>8 weeks) | 3/5 (1/2) | 4/5 (1/1) | Consensus improved | Top 5 | Stakeholder alignment after R2 feedback |
| R-12 | Design errors requiring rework during construction | 4/4 (1/1) | 4/4 (1/0) | Strong consensus | Top 4 | Remained critical risk across both rounds |
Appendix A.4. Scoring, Reporting, and Data Quality
Appendix A.5. Glossary for Respondents
Appendix B. NGT Template
Appendix B.1. General Design and Instructions
Appendix B.2. Step 1—Idea Generation and Clarification (R1)
| Risk ID | Risk Statement | Category | Clarification Notes |
|---|---|---|---|
| N-05 | Unsafe scaffolding setup | OHS | Clarified as ‘lack of inspection before use’. |
| N-09 | Delay in concrete delivery | Supply Chain | Clarified as ‘supplier reliability issue’. |
Appendix B.3. Step 2—Voting & Ranking (R2)
| Risk ID | Risk Statement | Individual Scores (P1–P6) | Total Score | Rank | Notes |
|---|---|---|---|---|---|
| N-05 | Unsafe scaffolding setup | 5, 4, 5, 4, 5, 5 | 28 | 1 | High consensus; safety-critical |
| N-09 | Delay in concrete delivery | 3, 2, 4, 3, 3, 4 | 19 | 2 | Moderate consensus |
Appendix B.4. Consensus
Appendix B.5. Glossary for Respondents
Appendix C. PHA Template
Appendix C.1. General Design and Instructions
Appendix C.2. Step 1—Hazard Identification
| Risk ID | Risk Statement | Category | Clarification Notes |
|---|---|---|---|
| P-02 | Unstable excavation slopes | Geotechnical | Risk of collapse during heavy rainfall. |
| P-06 | Improper storage of flammable materials | Safety | Potential fire hazard on site. |
Appendix C.3. Step 2—Hazard Evaluation
| Hazard ID | Hazard Statement | Severity (1–5) | Likelihood (1–5) | Matrix Position | Priority Rank |
|---|---|---|---|---|---|
| P-02 | Unstable excavation slopes | 5 | 4 | Critical (Red Zone) | 1 |
| P-06 | Improper storage of flammable materials | 4 | 3 | High (Orange Zone) | 2 |
Appendix C.4. Consensus
Appendix C.5. Glossary for Respondents
Appendix D. HAZOP Template
Appendix D.1. General Design and Instructions
Appendix D.2. Step 1—Node Selection and Guideword Application
| Node | Guideword | Deviation | Cause | Consequence | Safeguard/Recommendation |
|---|---|---|---|---|---|
| Excavation Phase | More | Excess water inflow | Unexpected groundwater table | Slope instability and delays | Install dewatering pumps; improve drainage design |
| Formwork System | Less | Insufficient concrete cover | Improper reinforcement placement | Reduced structural durability | Enhanced supervision; corrective rework procedure |
Appendix D.3. Step 2—Evaluation and Prioritization
| Deviation ID | Deviation | Severity (1–5) | Likelihood (1–5) | Risk Matrix Position | Priority Rank |
|---|---|---|---|---|---|
| H-03 | Excess water inflow | 4 | 3 | High (Orange Zone) | 2 |
| H-07 | Insufficient concrete cover | 3 | 2 | Medium (Yellow Zone) | 3 |
Appendix D.4. Reporting and Consensus
Appendix D.5. Glossary for Respondents
References
- Flyvbjerg, B. Survival of the unfittest: Why the worst infrastructure gets built—And what we can do about it. Oxf. Rev. Econ. Policy 2009, 25, 344–367. [Google Scholar] [CrossRef]
- Odeck, J. Cost overruns in road construction—What are their sizes and determinants? Transp. Policy 2004, 11, 43–53. [Google Scholar] [CrossRef]
- Hinze, J.; Godfrey, R. An evaluation of safety performance measures for construction projects. J. Constr. Res. 2003, 4, 5–15. [Google Scholar] [CrossRef]
- Zou, P.X.; Zhang, G.; Wang, J. Understanding the key risks in construction projects in China. Int. J. Proj. Manag. 2007, 25, 601–614. [Google Scholar] [CrossRef]
- Hwang, B.-G.; Zhao, X.; Toh, L.P. Risk management in small construction projects in Singapore: Status, barriers and impact. Int. J. Proj. Manag. 2014, 32, 116–124. [Google Scholar] [CrossRef]
- Research and Markets. 2024, Construction Market Report 2025. Available online: https://www.researchandmarkets.com/reports/5939618/construction-market-report (accessed on 11 August 2025).
- Gundes, S. Trends in global infrastructure investment and financial consequences. Eur. J. Sustain. Dev. Ment 2022, 11, 66. [Google Scholar] [CrossRef]
- Kaplan, R.S.; Mikes, A.; Simons, R.; Tufano, P.; Hofmann, M., Jr. Managing risk in the new world. Harv. Bus. Rev. 2009, 87, 68–75. [Google Scholar]
- Kishk, M.; Ukaga, C. The impact of effective risk management on project success. In Proceedings of the 24th Annual ARCOM Conference, Cardiff, UK, 1–3 September 2008. [Google Scholar]
- Merna, T.; Al-Thani, F.F. Corporate Risk Management; John Wiley Sons: Hoboken, NJ, USA, 2008. [Google Scholar]
- Zhang, L.; Li, X. How to reduce the negative impacts of knowledge heterogeneity in engineering design team: Exploring the role of knowledge reuse. Int. J. Proj. Manag. 2016, 34, 1138–1149. [Google Scholar] [CrossRef]
- Song, J.; Munyinda, M.; Sarfo, P.A. Examining the impact of risk management practices on sustainable project performance in the construction industry: The role of stakeholder engagement. Front. Built Environ. 2025, 11, 1575827. [Google Scholar] [CrossRef]
- Alexandra, L. Collaborative Risk Management in IPD Projects: Challenges and Opportunities. 2025. Available online: https://www.researchgate.net/publication/393165314_Collaborative_Risk_Management_in_IPD_Projects_Challenges_and_Opportunities (accessed on 11 August 2025).
- Raz, T.; Michael, E. Use and benefits of tools for project risk management. Int. J. Proj. Manag. 2001, 19, 9–17. [Google Scholar] [CrossRef]
- Albasyouni, W.; Kamara, J.; Heidrich, O. Key Challenges and Opportunities to Improve Risk Assessments in the Construction Industry. Buildings 2025, 15, 1832. [Google Scholar] [CrossRef]
- Kiral, I.A.; Kural, Z.; Comu, S. Risk identification in construction projects: Using the Delphi method. In Proceedings of the 11th International Congress on Advances in Civil Engineering, Istanbul, Turkey, 21–25 October 2014; pp. 21–25. [Google Scholar]
- George, C. The essence of risk identification in project risk management: An overview. Int. J. Sci. Res. IJSR 2020, 9, 973–978. [Google Scholar] [CrossRef]
- Zwikael, O.; Ahn, M. The effectiveness of risk management: An analysis of project risk planning across industries and countries. Risk Anal. Int. J. 2010, 31, 25–37. [Google Scholar] [CrossRef]
- Abdulwahab, A.; Isa, R.B.; Bello, A.O. Barriers to Adoption of BIM-Based Risk Management in the Construction Industry: A Systematic Literature Review and Bibliometric Analysis. In Proceedings of the Selçuk Scientific Research Congress, Konya, Turkey, 9 July 2023. [Google Scholar]
- Lehtiranta, L. Risk perceptions and approaches in multi-organizations: A research review 2000–2012. Int. J. Proj. Manag. 2014, 32, 640–653. [Google Scholar] [CrossRef]
- Project Management Institute (PMI). A Guide to the Project Management Body of Knowledge (PMBOK® Guide)—Seventh Edition and The Standard for Project Management; Project Management Institute: Newtown Square, PA, USA, 2021. [Google Scholar]
- Aven, T. Risk assessment and risk management: Review of recent advances on their foundation. Eur. J. Oper. Res. 2016, 253, 1–13. [Google Scholar] [CrossRef]
- Hopkin, P. Fundamentals of Risk Management: Understanding, Evaluating and Implementing Effective Risk Management; Kogan Page Publishers: London, UK, 2018. [Google Scholar]
- Ökmen, Ö.; Öztaş, A. Construction cost analysis under uncertainty with correlated cost risk analysis model. Constr. Manag. Econ. 2010, 28, 203–212. [Google Scholar] [CrossRef]
- Erfani, A.; Ma, Z.; Cui, Q.; Baecher, G.B. Ex post project risk assessment: Method and empirical study. J. Constr. Eng. Manag. 2023, 149, 04022174. [Google Scholar] [CrossRef]
- Tixier, J.; Dusserre, G.; Salvi, O.; Gaston, D. Review of 62 risk analysis methodologies of industrial plants. J. Loss Prev. Process Ind. 2002, 15, 291–303. [Google Scholar] [CrossRef]
- Chapman, R.J. The effectiveness of working group risk identification and assessment techniques. Int. J. Proj. Manag. 1998, 16, 333–343. [Google Scholar] [CrossRef]
- Humphrey-Murto, S.; Lee, S.H.; Gottlieb, M.; Horsley, T.; Shea, B.; Fournier, K.; Tran, C.; Chan, T.; Wood, T.J.; Cate, O.T. Protocol for an extended scoping review on the use of virtual nominal group technique in research. PLoS ONE 2023, 18, e0280764. [Google Scholar] [CrossRef]
- Elhosary, E.; Moselhi, O. Automation for HAZOP study: A state-of-the-art review and future research directions. J. Inf. Technol. Constr. ITcon 2024, 29, 750–777. [Google Scholar] [CrossRef]
- Linstone, H.; Turoff, M. The Delphi Method; Addison-Wesley Publishing Company: Reading, MA, USA, 1995. [Google Scholar]
- Okoli, C.; Pawlowski, S.D. The Delphi method as a research tool: An example, design considerations and applications. Inf. Manag. 2004, 42, 15–29. [Google Scholar] [CrossRef]
- Rowe, G.; Wright, G. The Delphi technique as a forecasting tool: Issues and analysis. Int. J. Forecast 1999, 15, 353–375. [Google Scholar]
- McMillan, S.S.; King, M.; Tully, M.P. How to use the nominal group and Delphi techniques. Int. J. Clin. Pharm. 2016, 38, 655–662. [Google Scholar] [CrossRef] [PubMed]
- Hallowell, M.R.; Gambatese, J.A. Construction safety risk mitigation. J. Constr. Eng. Manag. 2009, 135, 1316–1323. [Google Scholar] [CrossRef]
- Forbes, D.; Smith, S.; Horner, M. Tools for selecting appropriate risk management techniques in the built environment. Constr. Manag. Econ. 2008, 26, 1241–1250. [Google Scholar] [CrossRef]
- Fang, H.; Duan, M. Offshore Operation Facilities: Equipment and Procedures; Gulf Professional Publishing: Houston, TX, USA, 2014. [Google Scholar]
- Lincoln, Y.S.; Guba, E.G. Naturalistic Inquiry (Volume 75); Sage Publications, International Educational and Professional Publisher: London, UK; New Delhi, India, 1985. [Google Scholar]
- Creswell, J.W.; Poth, C.N. Qualitative Inquiry and Research Design: Choosing Among Five Approaches; Sage Publications: Thousand Oaks, CA, USA, 2016. [Google Scholar]
- Association for Project Management. Project Risk Analysis and Management (PRAM) Guide; APM: Princes Risborough, UK, 2004. [Google Scholar]
- Page, M.J.; McKenzie, J.E.; Bossuyt, P.M.; Boutron, I.; Hoffmann, T.C.; Mulrow, C.D.; Shamseer, L.; Tetzlaff, J.M.; Akl, E.A.; Brennan, S.E.; et al. The PRISMA 2020 statement: An updated guideline for reporting systematic reviews. BMJ 2021, 372, 71. [Google Scholar] [CrossRef]
- Nawaz, A.; Waqar, A.; Shah, S.A.R.; Sajid, M.; Khalid, M.I. An innovative framework for risk management in construction projects in developing countries: Evidence from Pakistan. Risks 2019, 7, 24. [Google Scholar] [CrossRef]
- Cooper, D.F.; Grey, S.; Raymond, G.; Walker, P. Project Risk Management Guidelines: Managing Risk in Large Projects and Complex Procurements; Wiley: Hoboken, NJ, USA, 2017. [Google Scholar]
- Albert, A.; Hallowell, M.R.; Kleiner, B.; Chen, A.; Golparvar-Fard, M. Enhancing construction hazard recognition with high-fidelity augmented virtuality. J. Constr. Eng. Manag. 2014, 140, 04014024. [Google Scholar] [CrossRef]
- Hillson, D.; Simon, P. Practical Project Risk Management: The ATOM Methodology, 2nd ed.; Management Concepts Press: Tysons Corner, VA, USA, 2012. [Google Scholar]
- Valis, D. Selected overview of risk assessment techniques. Trans. VŠB Tech. Univ. Ostrav. Saf. Eng. Ser. 2009, 4, 19–32. [Google Scholar]
- De los Pinos, A.J.C.; García, M.d.L.N.G. Critical analysis of risk assessment methods applied to construction works. Rev. de la Construcción J. Constr. 2017, 16, 104–114. [Google Scholar] [CrossRef]
- Hillson, D.; Murray-Webster, R. Understanding and Managing Risk Attitude; Routledge: London, UK, 2017. [Google Scholar]
- Ling, F.Y.Y.; Hoi, L. Risks faced by Singapore firms when undertaking construction projects in India. Int. J. Proj. Manag. 2006, 24, 261–270. [Google Scholar] [CrossRef]
- Smith, N.J.; Merna, T.; Jobling, P. Managing Risk in Construction Projects; John Wiley Sons: Hoboken, NJ, USA, 2014. [Google Scholar]
- Hutchins, G. ISO 31000: 2018 Enterprise Risk Management; Greg Hutchins: Portland, OR, USA, 2018. [Google Scholar]
- OSHA Occupational Safety and Health Administration. Construction Industry: Safety and Health Regulations for Construction 29 CFR 1926; U.S. Department of Labor: Washington, DC, USA, 2011.
- CDC Centers for Disease Control and Prevention. National Occupational Research Agenda (NORA): Construction Sector Council; U.S. Department of Health and Human Services: Atlanta, GA, USA, 2022.
- HSE Health and Safety Executive. Annual Health and Safety Statistics for Great Britain: 2024/25; Health and Safety Executive: London, UK, 2025.
- Cantarelli, C.C.; Flyvbjerg, B.; Molin, E.J.; Van Wee, B. Cost overruns in large-scale transportation infrastructure pro-jects: Explanations and their theoretical embeddedness. Eur. J. Transp. Infrastruct. Res. 2010, 10, 5–18. [Google Scholar]
- Crawley, F.; Tyler, B. HAZOP: Guide to Best Practice; Elsevier: Amsterdam, The Netherlands, 2015. [Google Scholar]
- Hsu, C.C.; Sandford, B.A. The Delphi technique: Making sense of consensus. Pract. Assess. Res. Eval. 2007, 121, 10. [Google Scholar]
- Delbecq, A.L.; Van de Ven, A.H.; Gustafson, D.H. Group Techniques for Program Planning: A Guide to Nominal Group and Delphi Processes; Scott, Foresman and Company: Glenview, IL, USA, 1975. [Google Scholar]
- Garrido, M.V.; Kristensen, F.B.; Nielsen, C.P.; Busse, R.; Kramme, R. Health Technology Assessment and Health Policy-Making in Europe: Current Status, Challenges and Potential; European Observatory on Health Systems and Policies: Brussels, Belgium, 2011. [Google Scholar]
- Shen, L.Y.; Wu, G.W.C.; Ng, C.S.K. Risk assessment for construction joint ventures in China. J. Constr. Engi-Neering Manag. 2001, 127, 76–81. [Google Scholar] [CrossRef]
- Hasson, F.; Keeney, S.; McKenna, H. Research guidelines for the Delphi survey technique. J. Adv. Nurs. 2000, 32, 1008–1015. [Google Scholar] [CrossRef]
- King, M.F.; Bruner, G.C. Social desirability bias: A neglected aspect of validity testing. Psychol. Mark. 2000, 17, 79–103. [Google Scholar] [CrossRef]
- Shang, Z.M. Use of Delphi in health sciences research: A narrative review. Medicine 2023, 102, e32829. [Google Scholar] [CrossRef]
- Veugelers, R.; Gaakeer, M.I.; Patka, P.; Huijsman, R. Improving design choices in Delphi studies in medicine: The case of an exemplary physician multi-round panel study with 100% response. BMC Med. Res. Methodol. 2020, 20, 156. [Google Scholar] [CrossRef]
- Kletz, T.A. Hazop Hazan: Identifying and Assessing Process Industry Hazards; CRC Press: Boca Raton, FL, USA, 2018. [Google Scholar]
- Ericson, C.A. Hazard Analysis Techniques for System Safety; John Wiley Sons: Hoboken, NJ, USA, 2015. [Google Scholar]
- Khan, F.I.; Abbasi, S. Techniques and methodologies for risk analysis in chemical process industries. J. Loss Prev. Process Ind. 1998, 11, 261–277. [Google Scholar] [CrossRef]
- Hillson, D. Managing Risk in Projects; Routledge: London, UK, 2024. [Google Scholar]
- Nasa, P.; Jain, R.; Juneja, D. Delphi methodology in healthcare research: How to decide its appropriateness. World J. Methodol. 2021, 11, 116–129. [Google Scholar] [CrossRef]
- Winch, G.M. Managing Construction Projects, 2nd ed.; Wiley-Blackwell: Hoboken, NJ, USA, 2010. [Google Scholar]
- Osipova, E.; Eriksson, P.E. Balancing control and flexibility in joint risk management: Lessons learned from two construction projects. Int. J. Proj. Manag. 2013, 31, 391–399. [Google Scholar] [CrossRef]
- Lingard, H.; Cooke, T.; Blismas, N. Do perceptions of supervisors’ safety responses mediate the relationship between perceptions of the organizational safety climate and incident rates in the construction supply chain? J. Constr. Eng. Manag. 2012, 138, 234–241. [Google Scholar] [CrossRef]
- Zou, P.X.W.; Couani, P. Managing risks in green building supply chain. Archit. Eng. Des. Manag. 2012, 8, 143–158. [Google Scholar] [CrossRef]
- Khodabakhshian, A.; Puolitaival, T.; Kestle, L. Deterministic and probabilistic risk management approaches in construction projects: A systematic literature review and comparative analysis. Buildings 2023, 13, 1312. [Google Scholar] [CrossRef]
- Taroun, A. Towards a better modelling and assessment of construction risk: Insights from a literature review. Int. J. Proj. Manag. 2014, 32, 101–115. [Google Scholar] [CrossRef]
- Yazdi, M.; Zarei, E.; Adumene, S.; Beheshti, A. Navigating the power of artificial intelligence in risk management: A comparative analysis. Safety 2024, 10, 42. [Google Scholar] [CrossRef]
- Zhang, X.; Mao, X.; AbouRizk, S.M. Developing a knowledge management system for improved value engineering practices in the construction industry. Autom. Constr. 2009, 18, 777–789. [Google Scholar] [CrossRef]
- Dikmen, I.; Atasoy, G.; Erol, H.; Kaya, H.D.; Birgonul, M.T. A decision-support tool for risk and complexity assessment and visualization in construction projects. Comput. Ind. 2022, 141, 103694. [Google Scholar] [CrossRef]
- Anshuka, A.; Shenoy, U.; Banerjee, S.; Wajekar, P.; Vasvani, V. Large or small panel in the Delphi study? Application of bootstrap technique. J. Evol. Med. Dent. Sci. 2020, 9, 1267–1271. [Google Scholar] [CrossRef]
- Harvey, N.; Holmes, C.A. Nominal group technique: An effective method for obtaining group consensus. Int. J. Nurs. Pract. 2012, 18, 188–194. [Google Scholar] [CrossRef]
- Vahedian-Shahroodi, M.; Mansourzadeh, A.; Shariat Moghani, S.; Saeidi, M. Using the nominal group technique in group decision-making: A review. Med. Educ. Bull. 2023, 4, 837–845. [Google Scholar]
- Khan, F.I.; Abbasi, S.A. Multivariate hazard identification and ranking system. Process Saf. Prog. 1998, 17, 157–170. [Google Scholar] [CrossRef]
- Rathnayaka, S.; Khan, F.; Amyotte, P. SHIPP methodology: Predictive accident modeling approach. Part I: Methodology and model description. Process Saf. Environ. Prot. 2011, 89, 151–164. [Google Scholar] [CrossRef]
- Wang, L.; Li, W.; Feng, W.; Yang, R. Fire risk assessment for building operation and maintenance based on BIM technology. Build. Environ. 2021, 205, 108188. [Google Scholar] [CrossRef]


| Method | Key Studies | Context (Project/Domain) | Sample Characteristics | Outputs | Reported Limitations |
|---|---|---|---|---|---|
| Delphi | [16,30,31,32] | Early-stage, large-scale or innovative construction projects (high uncertainty, scarce empirical data) | Expert panels (domain-specific, iterative rounds) | Identification of latent/uncertain risks; refinement of expert judgments | Time-consuming; requires carefully designed questionnaires; dependent on expert availability |
| NGT | [33,34] | Multi-stakeholder construction projects (e.g., contractor–consultant–client workshops) | Small groups (6–10 participants, structured facilitation) | Rapid consensus on prioritized risks | Limited scalability; facilitator skill critical; potential bias if not well moderated |
| HAZOP | [29,35] | Technically complex projects (tunnels, petrochemical, healthcare infrastructure) | Multidisciplinary teams (designers, engineers, safety experts) | Systematic identification of deviations from intended design/operation | High resource and documentation demand; requires specialized training; often underutilized in general construction |
| PHA | [10,36] | Conceptual design or feasibility phases of construction projects | Small teams, often managers/engineers | Broad hazard screening across safety, environmental, and operational categories | Provides limited depth; mainly preparatory for advanced techniques (e.g., HAZOP) |
| Inclusion Criteria | Exclusion Criteria |
|---|---|
|
|
| Criterion | ISO 31000 [50] | Key References |
|---|---|---|
| C1. Methodological Structure | Refers to the degree to which a technique is governed by a formalized process, structured steps, and predefined logic. A robust methodological structure improves repeatability and transparency of risk identification efforts. | [27,41,42] |
| C2. Stakeholder Participation | Measures the technique’s capacity to incorporate inputs from diverse stakeholders, enhancing comprehensiveness and legitimacy of identified risks. Particularly important in collaborative and multidisciplinary construction environments. | [31,34,43] |
| C3. Analytical Depth | Assesses the level of detail, causality, and interdependencies captured by the technique. High analytical depth is crucial for uncovering complex, latent, or systemic risks in large-scale projects. | [22,23,26] |
| C4. Resource Intensity | Captures the demands imposed by the technique in terms of time, cost, expertise, and logistical support. Critical for method feasibility in resource-constrained environments. | [26,27,34] |
| C5. Flexibility & Adaptability | Refers to the technique’s ability to accommodate variations in project size, phase, scope, and context. More adaptable techniques are applicable across a broader range of projects. | [39,44,45,46] |
| C6. Decision Support Value | Indicates the extent to which the outputs of the technique facilitate actionable decision-making. A substantial decision-support value enhances the integration of risk outputs into project planning and control. | [22,42,47] |
| C7. Contextual Fit | Evaluates how well the technique aligns with institutional norms, cultural dynamics, and sector-specific constraints in local countries’ construction industry. Ensures local relevance and implementation feasibility. | [4,48,49] |
| Criterion | ISO 31000 [50] | PMBOK Guide [21] | Explanation |
|---|---|---|---|
| C1. Methodological Structure | Clause 6.3—Risk Assessment Process | Tailoring Considerations | Emphasizes structured steps in method selection |
| C2. Stakeholder Participation | Clause 5.4—Communication & Consultation | Stakeholder Engagement Principle | Encourages participatory identification processes |
| C3. Analytical Depth | Clause 6.4—Risk Analysis | Risk Performance Domain | Depth of analysis in identifying risk sources and consequences |
| C4. Resource Intensity | Clause 4.3—Integration with Governance | Constraints and Resource Allocation | Considers the time, cost, and personnel demands of each technique |
| C5. Flexibility & Adaptability | Clause 4.2 & Principle 6—Continual Improvement | Tailoring, Complexity Dimensions | Methods’ ability to adjust to context or project scale |
| C6. Decision Support Value | Clause 6.5—Risk Evaluation | Decision-Making Environment and Data Models | Methods’ contribution to prioritization and actionability |
| C7. Contextual Fit | Clause 4.2—Understanding the Organization | Organizational Systems and Environment Fit | Compatibility with institutional, cultural, and regulatory context |
| Technique | Participants/Roles | Experience | Application Procedure | Session Duration | Artifacts Used |
|---|---|---|---|---|---|
| Delphi | 2 Senior Geotechnical Engineers, 2 Project Managers, 1 Safety Consultant | >10 years each | Two iterative rounds; Round 1: anonymized questionnaires; Round 2: aggregated feedback for re-evaluation | Two rounds conducted over ~4 weeks | Structured R1/R2 questionnaires |
| NGT | 1 Site Engineer, 1 Safety Supervisor, 4 Crew Leaders (Excavation, Formwork, Mechanical, Logistics) | 10–12 years | 90 min structured workshop; silent listing → round-robin sharing → clarification → anonymous voting | Full-day facilitated workshop | Idea sheets, voting forms, priority ranking |
| HAZOP | 1 Civil Engineer, 1 Geotechnical Engineer, 1 Safety Coordinator, 1 Mechanical Systems Designer | 10–15 years | Multidisciplinary team review; process flow diagram analyzed with guidewords (“more,” “less,” “reverse”) | One-day team session during detailed design | Guideword tables, deviation logs |
| PHA | 1 Project Manager, 1 Safety Consultant | 10–15 years | Semi-structured session using an adapted checklist across lifecycle phases | 3 h session during the conceptual stage | Hazard checklists |
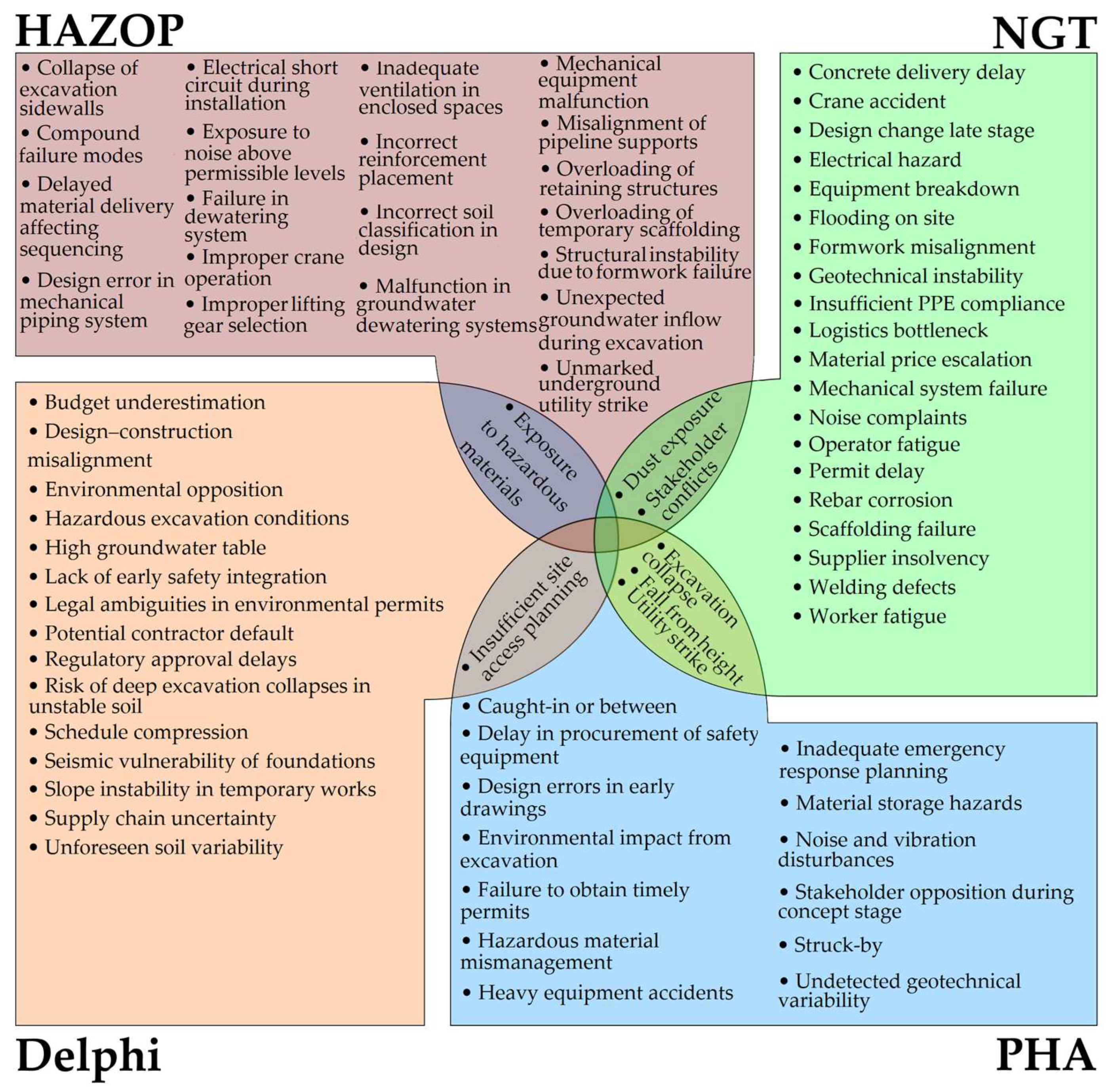
| Method | Total Risks Identified | Unique Risks | Overlaps with Other Methods |
|---|---|---|---|
| Delphi | 17 | 15 | 2 |
| HAZOP | 23 | 20 | 3 |
| NGT | 25 | 20 | 5 |
| PHA | 17 | 13 | 4 |
| Total (Overlapped Risks Excluded) | 75 |
| Method | Contextual/Project Management | Occupational Health and Safety |
|---|---|---|
| Delphi | Budget underestimation, Design–construction misalignment, Environmental opposition, High groundwater table, Insufficient site planning, Lack of early safety integration, Legal ambiguities in environmental permits, Potential contractor default, Regulatory approval delays, Schedule compression, Supply chain uncertainty, Unforeseen soil variability | Exposure to hazardous materials, Hazardous excavation conditions, Risk of deep excavation collapses in unstable soil, Seismic vulnerability of foundations, Slope instability in temporary works |
| HAZOP | Delayed material delivery affecting sequencing, Design error in mechanical piping system, Incorrect soil classification in design, Stakeholder conflicts | Collapse of excavation sidewalls, Compound failure modes, Dust exposure, Electrical short circuit during installation, Exposure to hazardous materials, Exposure to noise above permissible levels, Failure in dewatering system, Improper crane operation, Improper lifting gear selection, Inadequate ventilation in enclosed spaces, Incorrect reinforcement placement, Malfunction in groundwater dewatering systems, Mechanical equipment malfunction, Misalignment of pipeline supports, Overloading of retaining structures, Overloading of temporary scaffolding, Structural instability due to formwork failure, Unexpected groundwater inflow during excavation, Unmarked underground utility strike |
| NGT | Concrete delivery delay, Design change late stage, Logistics bottleneck, Material price escalation, Permit delay, Stakeholder conflicts, Supplier insolvency, Utility strike | Crane accident, Dust exposure, Electrical hazard, Equipment breakdown, Excavation collapse, Flooding on site, Formwork misalignment, Geotechnical instability, Mechanical system failure, Noise complaints, Rebar corrosion, Scaffolding failure, Welding defects, Worker fall from height, Worker fatigue |
| PHA | Caught-in or between, Delay in procurement of safety equipment, Design errors in early drawings, Environmental impact from excavation, Failure to obtain timely permits, Insufficient site planning, Stakeholder opposition during concept stage, Utility strike | Excavation collapse, Fall from height, Hazardous material mismanagement, Heavy equipment accidents, Inadequate emergency response planning, Material storage hazards, Noise and vibration disturbances, Undetected geotechnical variability, Struck-by |
| Criterion | Delphi Method | NGT | HAZOP | PHA |
|---|---|---|---|---|
| C1. Methodological Structure | High—Iterative, formal, structured questionnaire | Medium—Structured steps, less iterative | Very High—Guideword-based, standardized process | Medium—Checklist-style structure |
| C2. Stakeholder Participation | Moderate—Limited to selected experts | High—Interactive, inclusive of all participants | Moderate—Technical team focused | Moderate—Early-stage multidisciplinary teams |
| C3. Analytical Depth | High—Aggregates expert judgment and refinement | Medium—Focused on idea generation and ranking | Very High—Identifies design deviations and hazards | Low to Medium—Identifies broad categories only |
| C4. Resource Intensity | High—Time-consuming, requires multiple rounds | Low—Quick sessions, minimal prep | Very High—Requires technical documents and facilitation | Low—Fast, minimal documentation required |
| C5. Flexibility & Adaptability | High—Can be customized across domains | High—Easily modified based on scope | Low to Medium—Suited for detailed designs only | High—Flexible for early-phase application |
| C6. Decision Support Value | High—Informed by expert convergence | Medium—Group consensus but less analytical | Very High—Detailed outputs for design-level decisions | Medium—Used for early-stage screening |
| C7. Contextual Fit | Medium—Requires expert availability | High—Works well in workshops or training groups | Low—Demands high technical maturity | High—Suitable for low-resource, early-stage use |
| Method | Main Strengths | Limitations | Dominant Risk Focus | Overlap with Others |
|---|---|---|---|---|
| Delphi | Deep expert elicitation; accommodates tacit knowledge; systematic consensus-building | Time-consuming; risk of participant fatigue; requires experienced facilitators | Contextual/PM risks (budget underestimation, regulatory delays, design–construction misalignment); some OHS (hazardous excavation, seismic risks) | Overlaps with PHA (permits, site planning) and NGT (stakeholder conflicts) |
| NGT | Highly participatory; inclusive; transparent prioritization | Lack of anonymity; potential social desirability bias in hierarchical settings | OHS risks (crane accidents, scaffolding failures, equipment breakdowns, fatigue) and contextual risks (logistics bottlenecks, supplier insolvency) | Overlaps with Delphi (stakeholder conflicts) and HAZOP (dust exposure, utility strikes) |
| HAZOP | Rigorous, system-based; detailed node analysis; strong for technical hazards | Resource-intensive; requires detailed documentation; not suited for early project phases | OHS risks (incorrect reinforcement, electrical hazards, ventilation issues, equipment malfunctions) | Overlaps with Delphi (utility conflicts, hazardous excavation) and PHA (early excavation collapse, material exposure) |
| PHA | Lightweight, rapid screening; efficient for early stages | Generalized outputs; lacks detail for task-level planning | Early-stage OHS risks (falls from height, emergency response gaps, material mismanagement) and contextual risks (permits, site planning, environmental impacts) | Overlaps with Delphi (permits, site planning) and HAZOP (excavation collapse, dust/noise exposures) |
| Criterion | Delphi Method | NGT | HAZOP | PHA |
|---|---|---|---|---|
| C1. Methodological Structure | (+) Highly structured, systematic, and iterative process (−) Long implementation time | (+) Clear procedural steps, easy to implement (−) Lack of anonymity may create conformity pressure | (+) Highly detailed and technically robust procedure (−) Limited applicability at early project stages | (+) Simple and quick structure (−) Does not provide in-depth analysis |
| C2. Stakeholder Participation | (+) Deepens expert insights through multiple rounds (−) Limited participant interaction (no face-to-face) | (+) Encourages active and equal participation (−) Diversity of views may decline in high power-distance contexts | (+) Intensive interaction among multidisciplinary teams (−) Limited contribution from non-experts | (+) Can quickly gather input from different stakeholder groups (−) Engagement may remain superficial |
| C3. Analytical Depth | (+) Enables deep analysis and synthesis of ideas (−) Requires substantial time and data | (+) Provides moderate analytical depth in practice (−) Limited systematic technical analysis | (+) Highest level of technical analytical depth (−) Cannot be applied without sufficient documentation and data | (+) Conducts basic risk screening (−) Does not offer detailed analysis |
| C4. Resource Intensity | (−) High demand for time, coordination, and human resources | (+) Low cost and time requirements | (−) High technical expertise and preparation needed | (+) Lowest resource requirements |
| C5. Flexibility & Adaptability | (−) Rigid process, difficult to change (+) Adjustable by varying the number of rounds | (+) Easily adaptable to different project types | (−) High dependence on documentation | (+) Quickly integrates into early-stage projects |
| C6. Decision Support Value | (+) Strong, data-driven insights for decision-making | (±) Strong for short-term decisions, weaker for long-term | (+) Directly linkable to risk mitigation planning | (−) Weak decision support, requires additional analysis |
| C7. Contextual Fit | (±) Strong where expert access is easy and there is no time pressure (−) Challenging under time constraints or with a limited expert pool | (+) Ideal for environments with low documentation and rapid decision needs | (±) Effective in projects with high documentation and technical maturity (−) Difficult to apply in developing sectors | (+) Suitable for contexts with limited resources and quick decision-making needs |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kiral, I.A. Contextual Evaluation of Risk Identification Techniques for Construction Projects: Comparative Insights and a Decision-Support Model. Buildings 2025, 15, 3806. https://doi.org/10.3390/buildings15203806
Kiral IA. Contextual Evaluation of Risk Identification Techniques for Construction Projects: Comparative Insights and a Decision-Support Model. Buildings. 2025; 15(20):3806. https://doi.org/10.3390/buildings15203806
Chicago/Turabian StyleKiral, Isik Ates. 2025. "Contextual Evaluation of Risk Identification Techniques for Construction Projects: Comparative Insights and a Decision-Support Model" Buildings 15, no. 20: 3806. https://doi.org/10.3390/buildings15203806
APA StyleKiral, I. A. (2025). Contextual Evaluation of Risk Identification Techniques for Construction Projects: Comparative Insights and a Decision-Support Model. Buildings, 15(20), 3806. https://doi.org/10.3390/buildings15203806









