Segmented Embedded Rapid Defect Detection Method for Bearing Surface Defects
Abstract
1. Introduction
2. Methods
3. Algorithm Steps
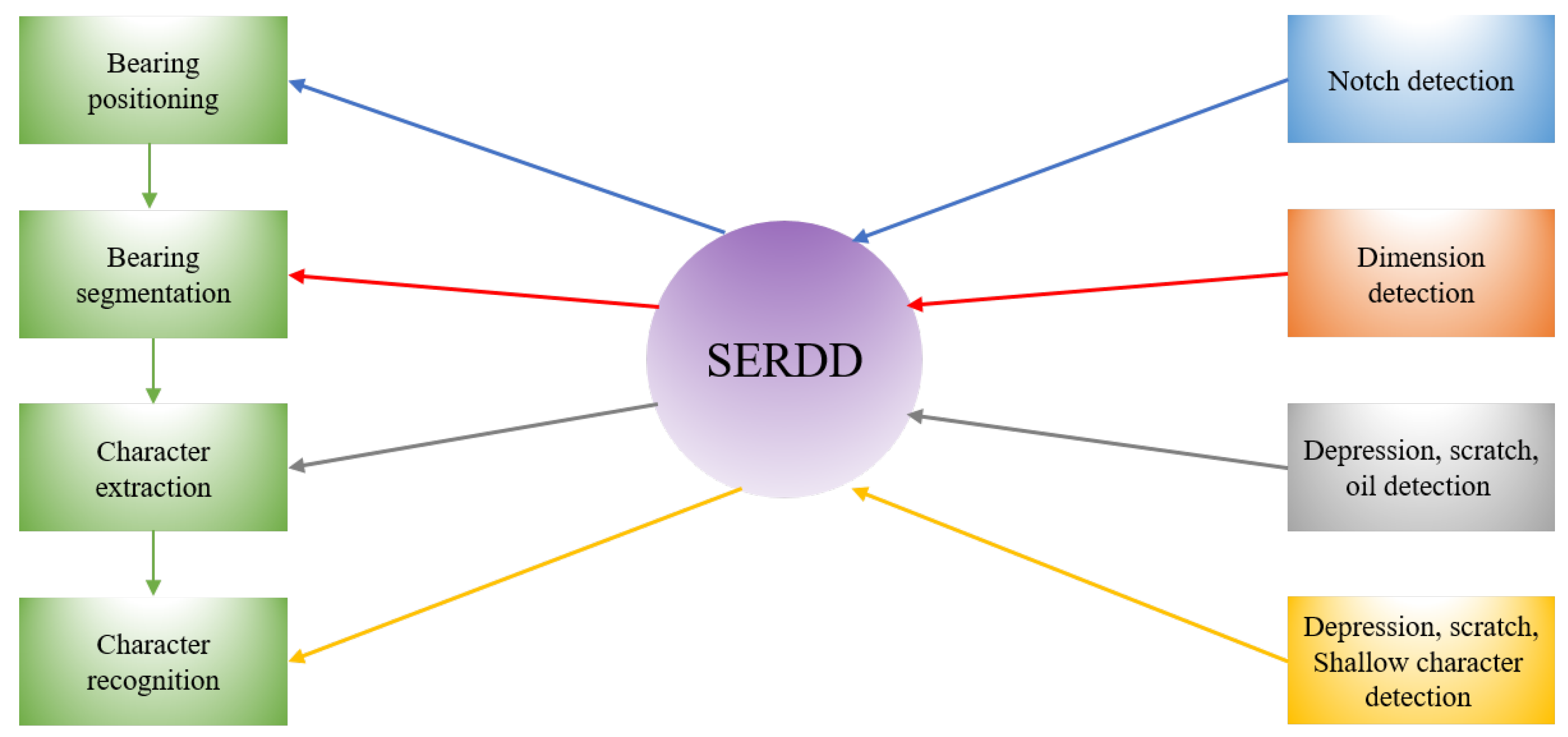
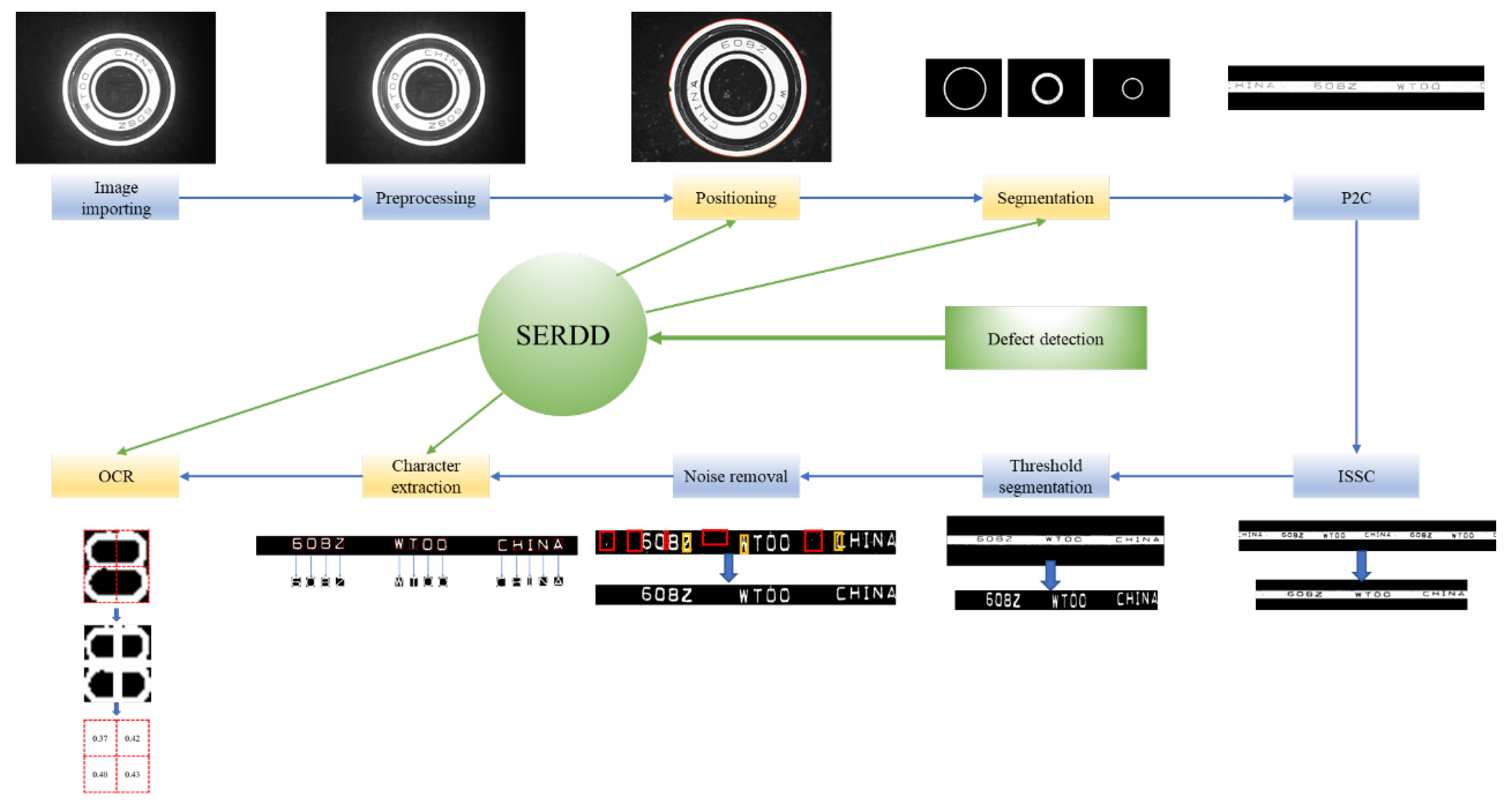
3.1. Algorithm Flow
3.2. Image Preprocessing
3.3. Bearing Positioning and Notch Detection
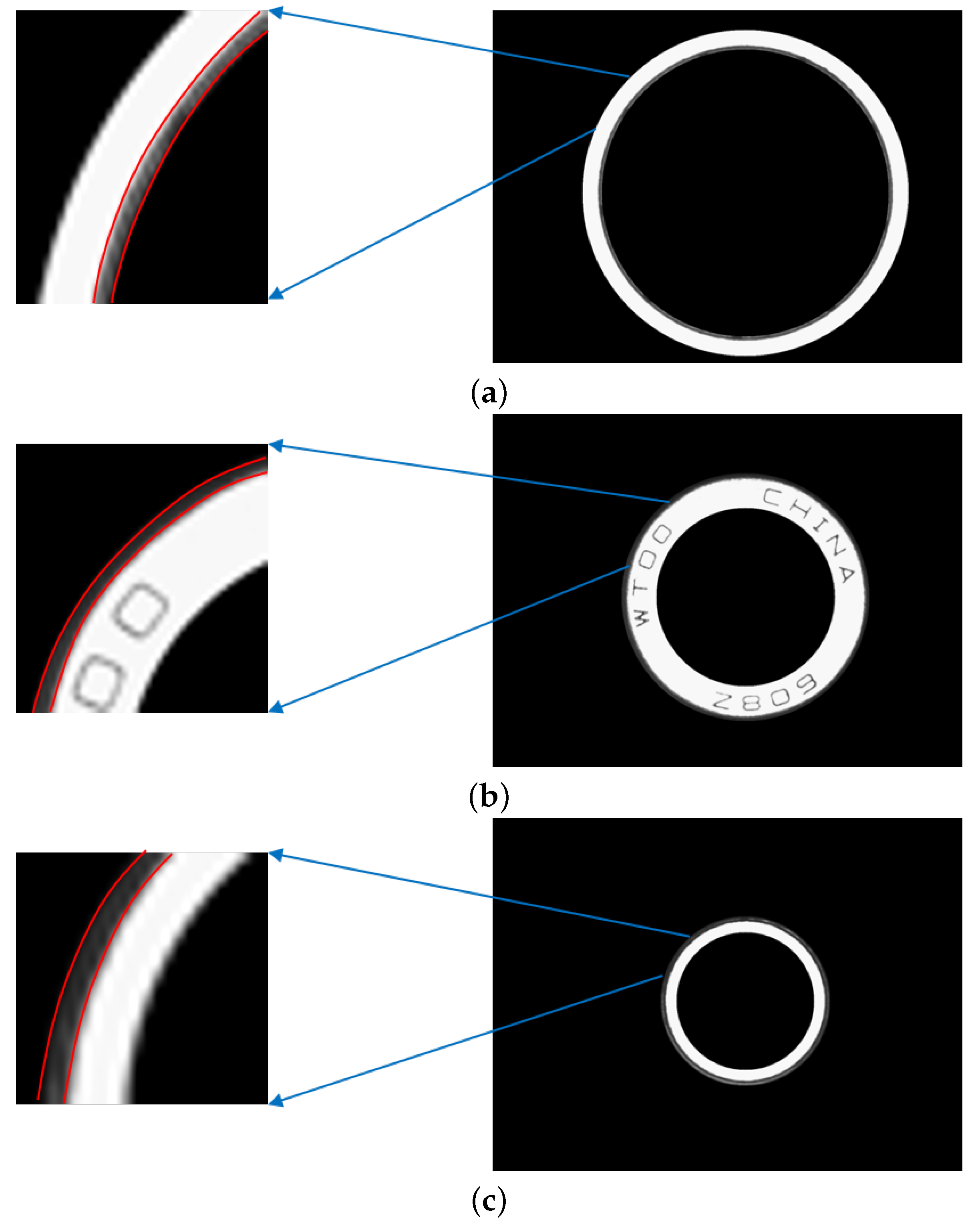
3.3.1. Bearing Positioning
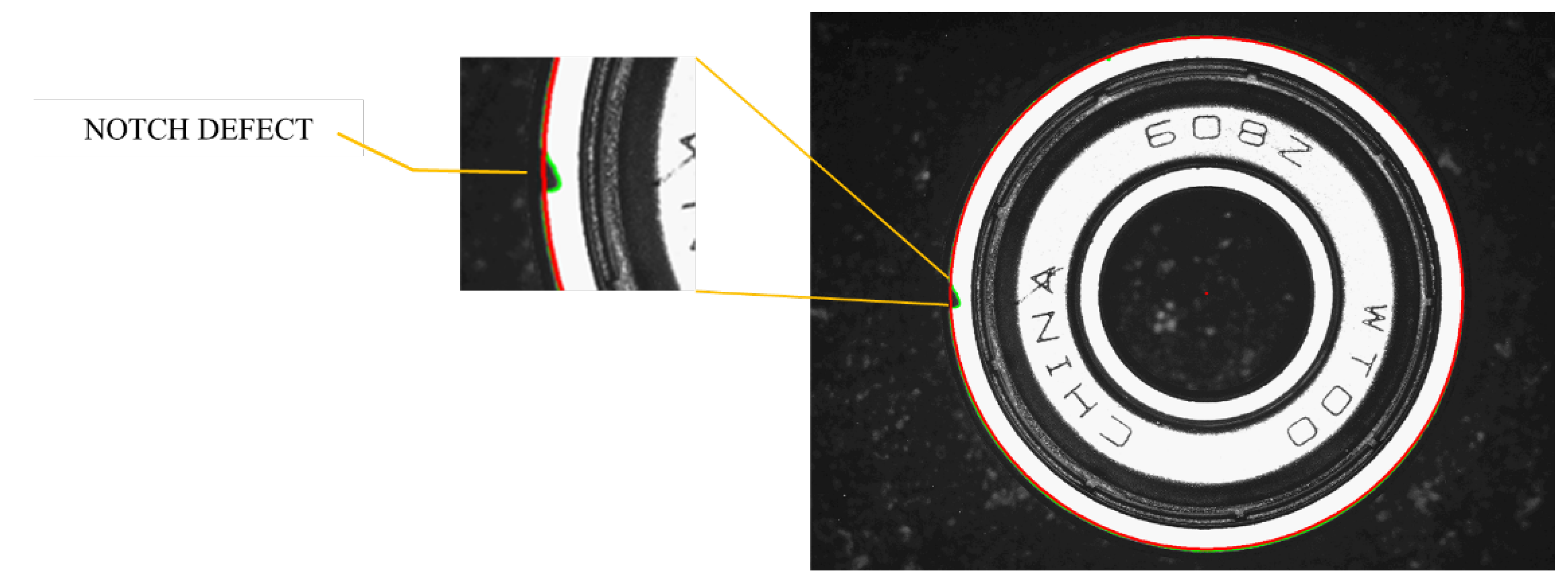
3.3.2. Notch Detection of Bearing Outer Ring
3.4. Bearing Segmentation and Abnormal Dimension Detection
3.4.1. Bearing Segmentation
3.4.2. Abnormal Dimension Detection
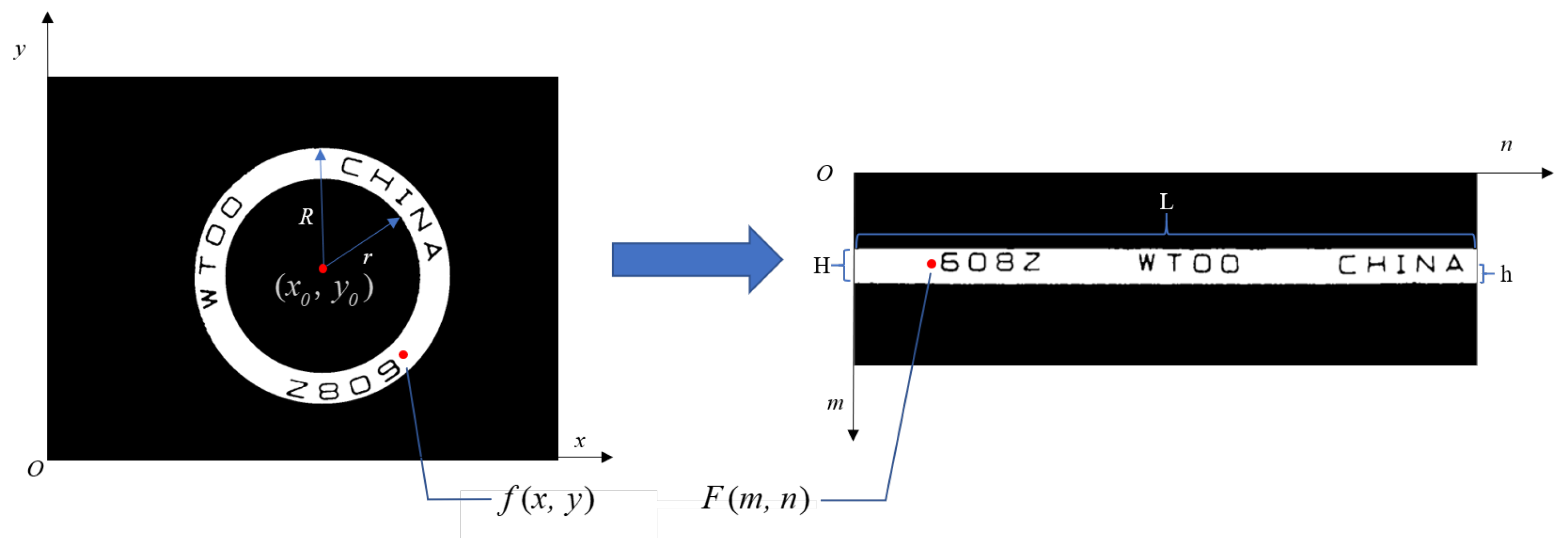
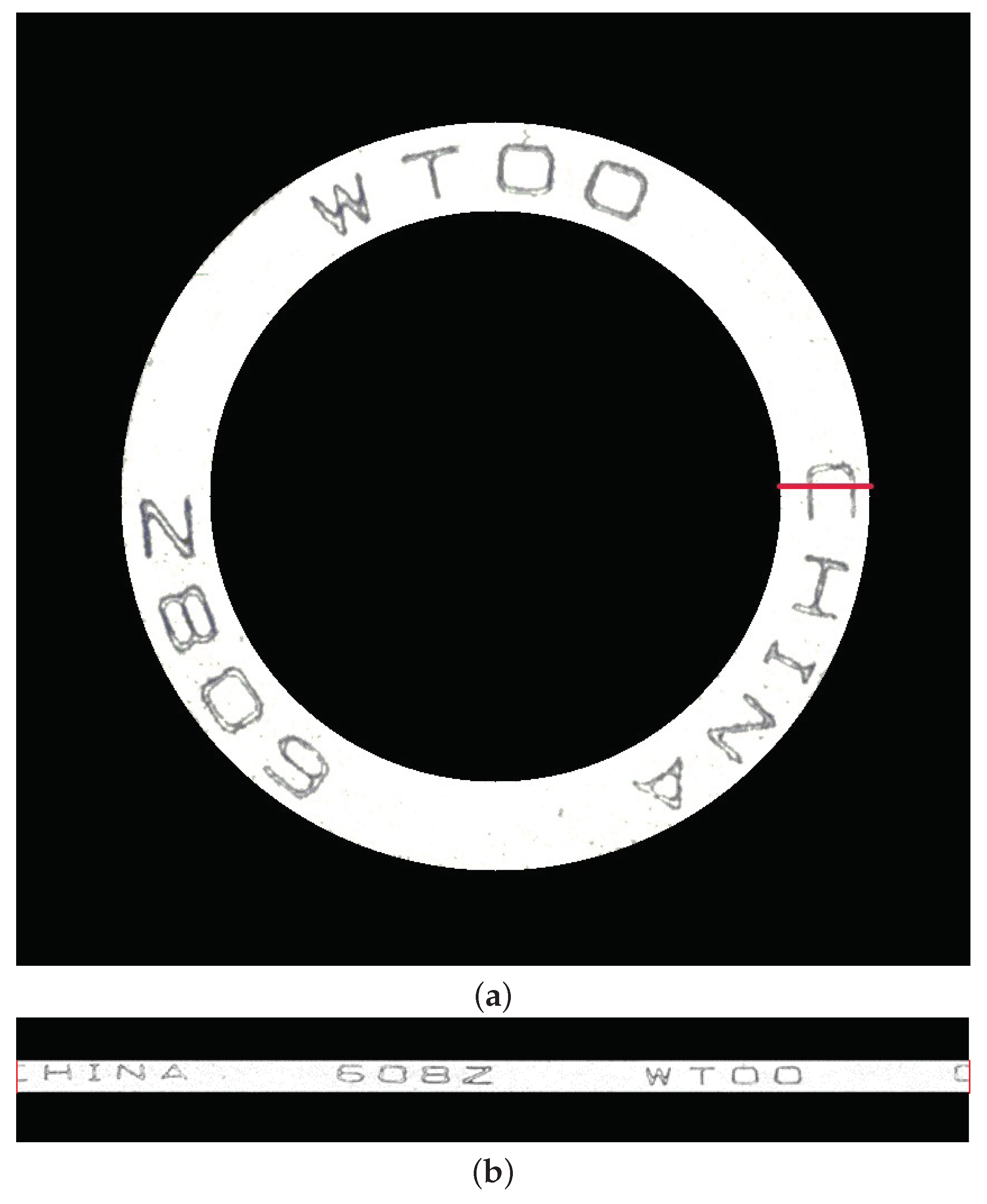
3.5. Polar to Cartesian (P2C) Coordinate Transformation
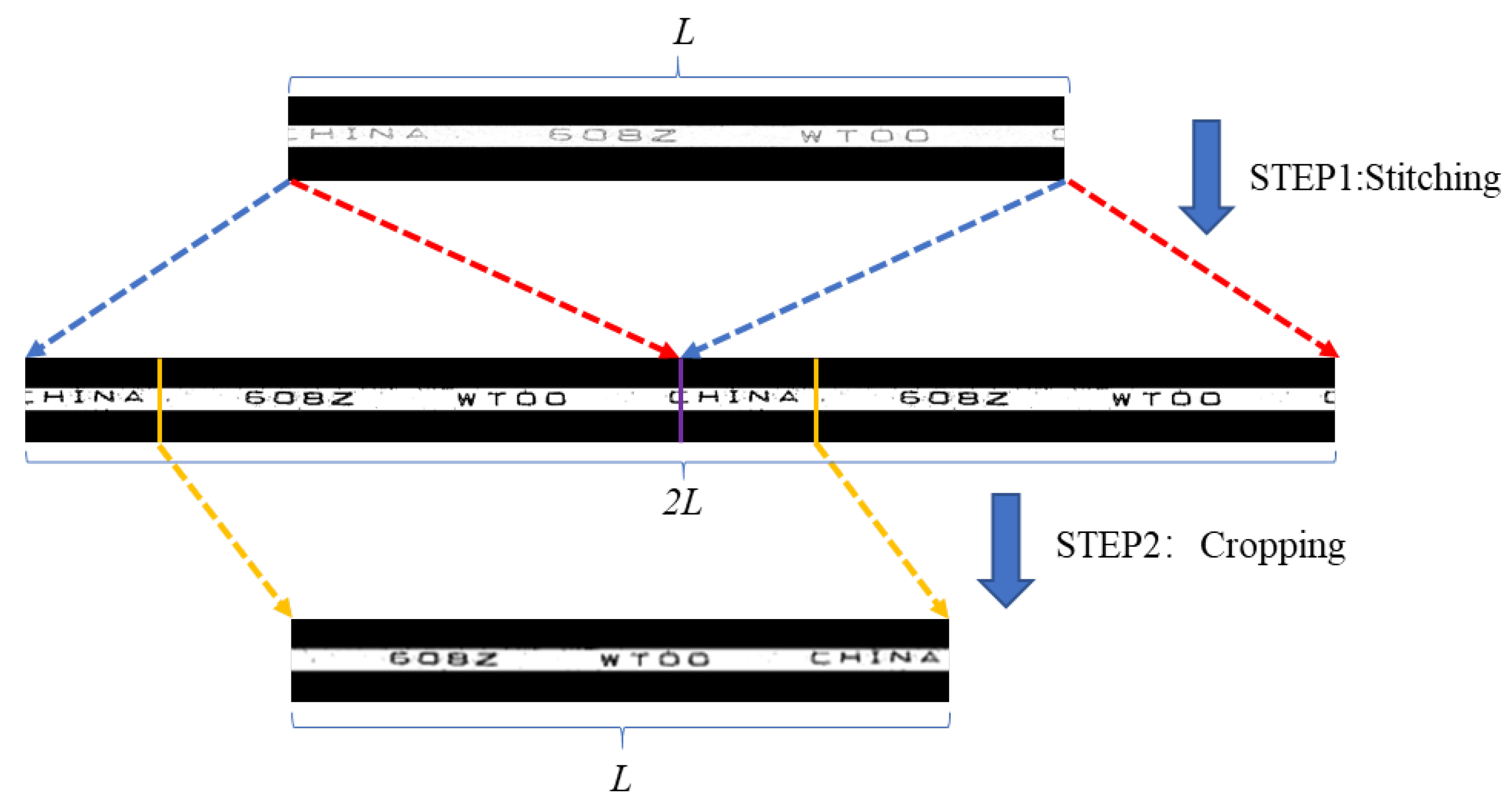
3.6. Image Self-Stitching-And-Cropping (ISSC)
| Algorithm 1: ISSC |
 |
3.7. Threshold Segmentation
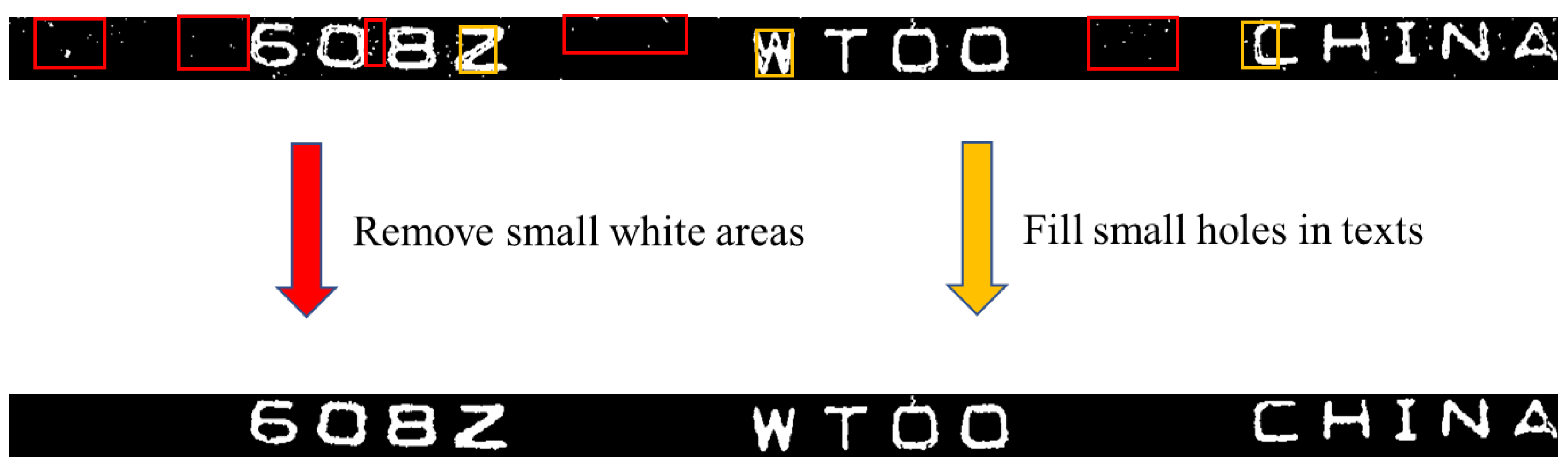
3.8. The Removal of Small Connected Domains and Holes
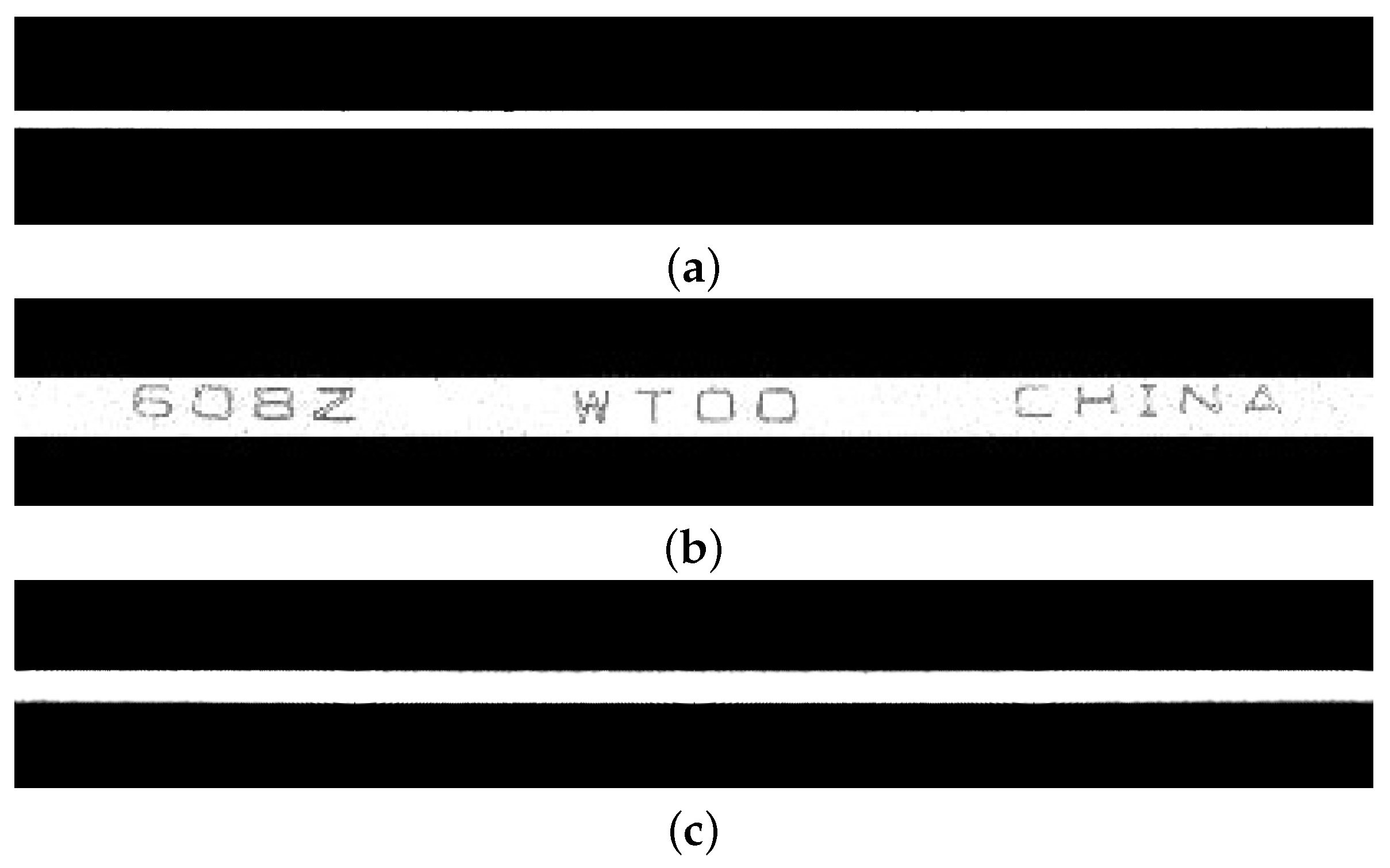
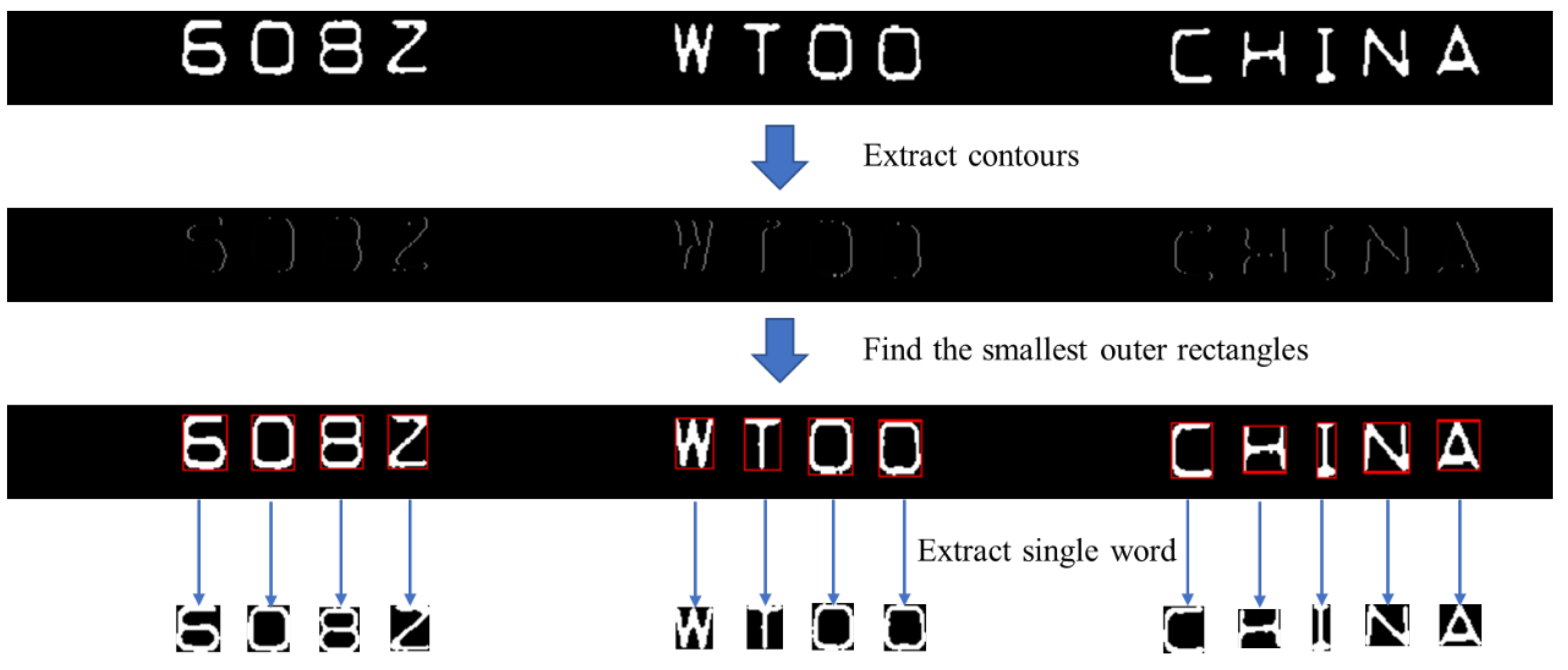
3.9. Character Extraction and Defect Detection of Non-Character Regions
3.9.1. Character Extraction
3.9.2. Defect Detection of Non-Character Regions
3.10. Character Recognition and Defect Detection of Characters
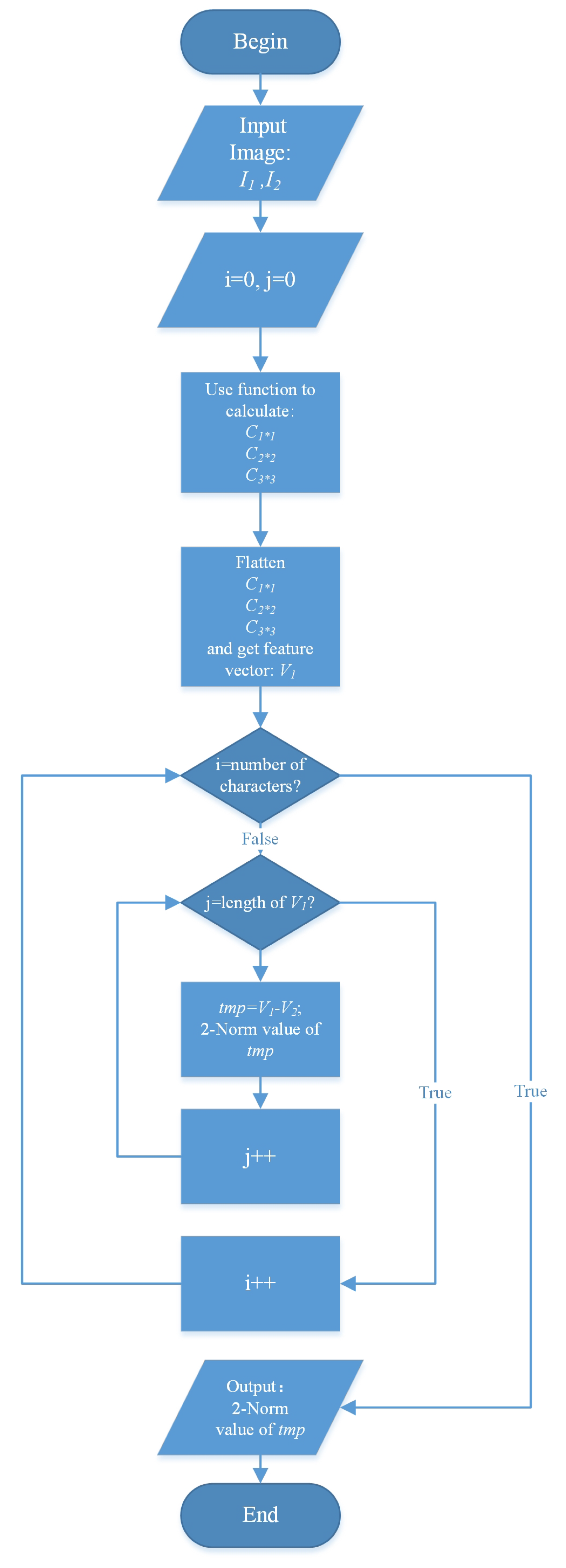
3.10.1. Character Recognition
| Algorithm 2: SPCPM |
 |
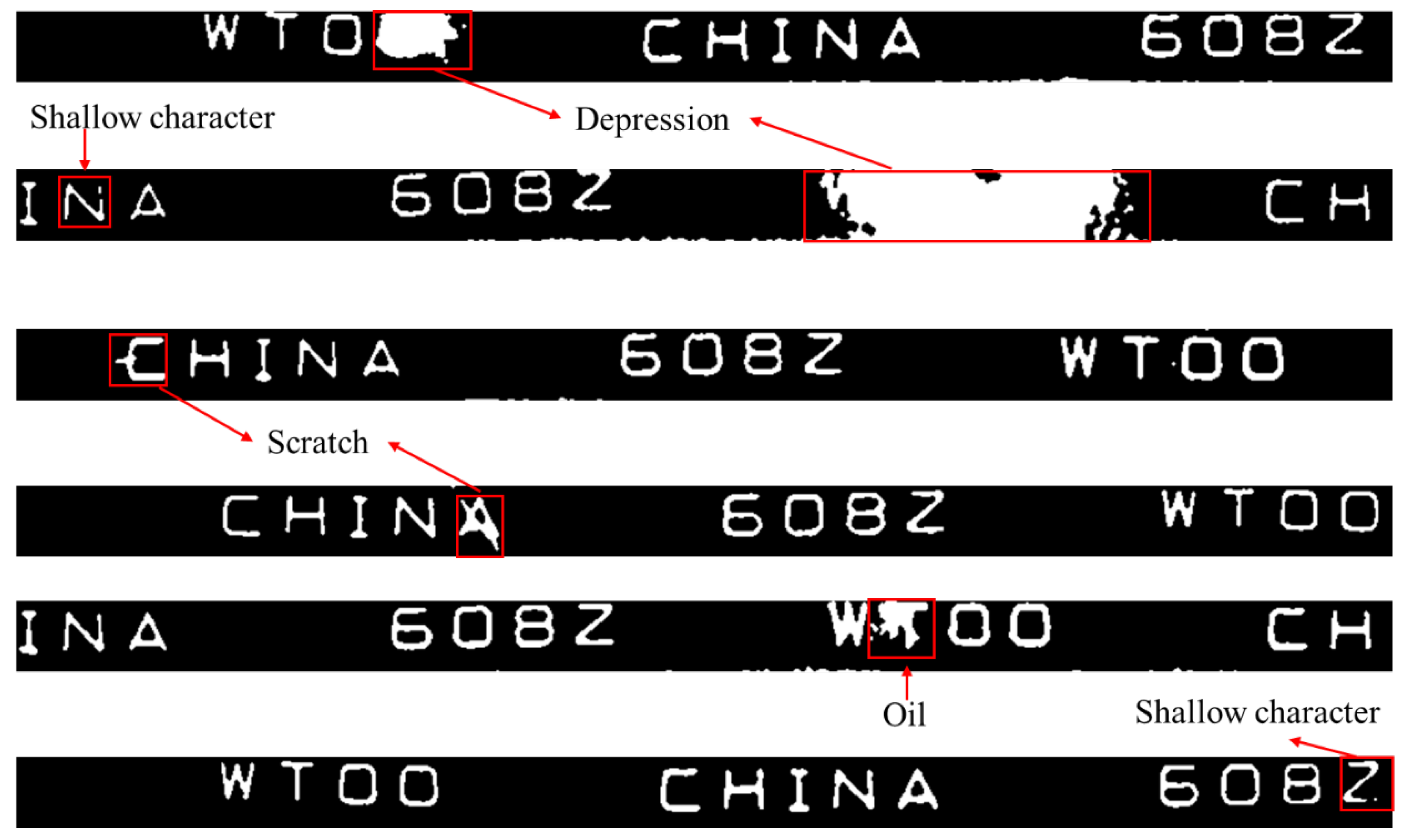
3.10.2. Defect Detection of Characters
4. Experimental Results
4.1. Experimental Setup
4.2. Results and Analysis of Defect Detection
4.3. Experimental Results and Analysis of Character Recognition
5. Conclusions
- Improve the accuracy of SPCPM.
- Deal with some possible situations of particular defects.
- Set up the related execution equipment to build a defect detection system for bearing surface defects.
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Wang, H.; Yang, J.; Hu, Z. Current Status and Prospect of Roller Bearing Surface Defect Detection. Procedia Eng. 2011, 15, 4331–4336. [Google Scholar] [CrossRef][Green Version]
- Shah, D.S.; Patel, V.N. A Review of Dynamic Modeling and Fault Identifications Methods for Rolling Element Bearing. Procedia Technol. 2014, 14, 447–456. [Google Scholar] [CrossRef]
- El-Thalji, I.; Jantunen, E. A summary of fault modelling and predictive health monitoring of rolling element bearings. Mech. Syst. Signal Process. 2015, 60–61, 252–272. [Google Scholar] [CrossRef]
- Randall, R.B.; Antoni, J. Rolling element bearing diagnostics—A tutorial. Mech. Syst. Signal Process. 2011, 25, 485–520. [Google Scholar] [CrossRef]
- Peng, Z.; Tse, P.W.; Chu, F. A comparison study of improved Hilbert–Huang transform and wavelet transform: Application to fault diagnosis for rolling bearing. Mech. Syst. Signal Process. 2005, 19, 974–988. [Google Scholar] [CrossRef]
- Randall, R.; Antoni, J.; Chobsaard, S. The relationship between spectral correlation and envelope analysis in the diagnostics of bearing faults and other cyclostationary machine signals. Mech. Syst. Signal Process. 2001, 15, 945–962. [Google Scholar] [CrossRef]
- Lou, X.; Loparo, K.A. Bearing fault diagnosis based on wavelet transform and fuzzy inference. Mech. Syst. Signal Process. 2004, 18, 1077–1095. [Google Scholar] [CrossRef]
- Li, B.; Chow, M.; Tipsuwan, Y.; Hung, J. Neural-network-based motor rolling bearing fault diagnosis. IEEE Trans. Ind. Electron. 2000, 47, 1060–1069. [Google Scholar] [CrossRef]
- Samanta, B.; Al-Balushi, K. Artificial neural network based fault diagnostics of rolling element bearings using time-domain features. Mech. Syst. Signal Process. 2003, 17, 317–328. [Google Scholar] [CrossRef]
- Lei, Y.; Jia, F.; Lin, J.; Xing, S.; Ding, S. An Intelligent Fault Diagnosis Method Using Unsupervised Feature Learning Towards Mechanical Big Data. IEEE Trans. Ind. Electron. 2016, 63, 3137–3147. [Google Scholar] [CrossRef]
- Cao, H.; Li, D.; Yue, Y. Root Cause Identification of Machining Error Based on Statistical Process Control and Fault Diagnosis of Machine Tools. Machines 2017, 5, 20. [Google Scholar] [CrossRef]
- Zenzen, R.; Khatir, S.; Belaidi, I.; Le Thanh, C.; Abdel Wahab, M. A modified transmissibility indicator and Artificial Neural Network for damage identification and quantification in laminated composite structures. Compos. Struct. 2020, 248, 112497. [Google Scholar] [CrossRef]
- Khatir, S.; Boutchicha, D.; Le Thanh, C.; Tran, H.; Nguyen, N.; Abdel Wahab, M. Improved ANN technique combined with Jaya algorithm for crack identification in plates using XIGA and experimental analysis. Theor. Appl. Fract. Mech. 2020, 107, 102554. [Google Scholar] [CrossRef]
- Jiang, Y.; Tang, C.; Zhang, X.; Jiao, W.; Huang, T. A novel rolling bearing defect detection method based on bispectrum analysis and cloud model-improved EEMD. IEEE Access 2020, 8, 24323–24333. [Google Scholar] [CrossRef]
- Li, C.; Sanchez, V.; Zurita, G.; Cerrada Lozada, M.; Cabrera, D. Rolling element bearing defect detection using the generalized synchrosqueezing transform guided by time–frequency ridge enhancement. Isa Trans. 2016, 60, 274–284. [Google Scholar] [CrossRef]
- Wang, J.; He, Q.; Kong, F. A new synthetic detection technique for trackside acoustic identification of railroad roller bearing defects. Appl. Acoust. 2014, 85, 69–81. [Google Scholar] [CrossRef]
- Anil, K.; Yuqing, Z.; Gandhi, C.P.; Rajesh, K.; Jiawei, X. Bearing defect size assessment using wavelet transform based Deep Convolutional Neural Network (DCNN). Alex. Eng. J. 2020, 59, 999–1012. [Google Scholar]
- Udmale, S.S.; Singh, S.K.; Bhirud, S.G. A bearing data analysis based on kurtogram and deep learning sequence models. Measurement 2019, 145, 665–677. [Google Scholar] [CrossRef]
- Fu, X.; Li, K.; Liu, J.; Li, K.; Chen, C. A Two-Stage Attention Aware Method for Train Bearing Shed Oil Inspection Based on Convolutional Neural Networks. Neurocomputing 2019, 380, 212–224. [Google Scholar] [CrossRef]
- Liu, B.; Yang, Y.; Wang, S.; Bai, Y.; Yang, Y.; Zhang, J. An automatic system for bearing surface tiny defect detection based on multi-angle illuminations. Optik 2020, 208, 164517. [Google Scholar] [CrossRef]
- Shen, H.; Li, S.; Gu, D.; Chang, H. Bearing defect inspection based on machine vision. Measurement 2012, 45, 719–733. [Google Scholar] [CrossRef]
- Xiangwei, C.; Xuejun, Z.; Shan, G. Inspection of Surface Defect of Micro Bearing Based on Computer Vision. Mach. Tool Hydraul. 2009, 37, 130–132. [Google Scholar]
- Deng, S.; Cai, W.; Xu, Q.; Liang, B. Defect detection of bearing surfaces based on machine vision technique. In Proceedings of the 2010 International Conference on Computer Application and System Modeling (ICCASM 2010), Taiyuan, China, 22–24 October 2010; pp. 548–554. [Google Scholar] [CrossRef]
- Li, Z.; Zhang, J.; Zhuang, T.; Wang, Q. Metal surface defect detection based on MATLAB. In Proceedings of the 2018 IEEE 3rd Advanced Information Technology, Electronic and Automation Control Conference (IAEAC), Chongqing, China, 1 October 2018; pp. 2365–2371. [Google Scholar]
- Peng, G.; Zhang, Z.; Li, W. Computer vision algorithm for measurement and inspection of O-rings. Measurement 2016, 94, 828–836. [Google Scholar] [CrossRef]
- Kong, H.; Yang, J.; Chen, Z. Accurate and efficient inspection of speckle and scratch defects on surfaces of planar products. IEEE Trans. Ind. Inform. 2017, 13, 1855–1865. [Google Scholar] [CrossRef]
- Chiou, Y.C.; Li, W.C. Flaw detection of cylindrical surfaces in PU-packing by using machine vision technique. Measurement 2009, 42, 989–1000. [Google Scholar] [CrossRef]
- Chiou, Y.C.; Li, W.C. Bearing shield surface defect detection based on machine vision. Comput. Eng. Appl. 2014, 50, 250–254. [Google Scholar] [CrossRef]
- Level Otsu, N. A threshold selection method from gray-level histogram. IEEE Trans. Syst. Man. Cybern. 1979, 9, 62–66. [Google Scholar] [CrossRef]
- TAO, Q.P.; WU, X.S. Rapid Detection Method of the Bearing Surface Defects. Microelectron. Comput. 2011, 10, 98–100, 104. [Google Scholar]
- Ng, H.F. Automatic thresholding for defect detection. Pattern Recognit. Lett. 2006, 27, 1644–1649. [Google Scholar] [CrossRef]
- Bei, L. One improved scan line seed-filling algorithm. In Proceedings of the China-ireland International Conference on Information & Communications Technologies, Dublin, Ireland, 28–29 August 2007. [Google Scholar]
- Suzuki, S.; be, K. Topological structural analysis of digitized binary images by border following. Comput. Vis. Graph. Image Process. 1985, 29, 396. [Google Scholar] [CrossRef]
- Hengdi, W.; Yang, Z.; Sier, D.; Erdong, S.; Yong, W. Bearing characters recognition system based on LabVIEW. In Proceedings of the 2011 International Conference on Consumer Electronics, Communications and Networks (CECNet), Xianning, China, 16–18 April 2011; pp. 118–122. [Google Scholar]
- Dalal, N.; Triggs, B. Histograms of oriented gradients for human detection. In Proceedings of the 2005 IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR’05), San Diego, CA, USA, 20–25 June 2005; pp. 886–893. [Google Scholar]
- Bosch, A.; Zisserman, A.; Munoz, X. Image classification using random forests and ferns. In Proceedings of the 2007 IEEE 11th International Conference on Computer Vision, Rio de Janeiro, Brazil, 14–21 October 2007; pp. 1–8. [Google Scholar]
- Bosch, A.; Zisserman, A.; Munoz, X. Representing shape with a spatial pyramid kernel. In Proceedings of the 6th ACM International Conference on Image and Video Retrieval, Amsterdam, The Netherlands, 9–11 July 2007; pp. 401–408. [Google Scholar]
- Lazebnik, S.; Schmid, C.; Ponce, J. Beyond bags of features: Spatial pyramid matching for recognizing natural scene categories. In Proceedings of the 2006 IEEE Computer Society Conference on Computer Vision and Pattern Recognition (CVPR’06), New York, NY, USA, 17–22 June 2006; pp. 2169–2178. [Google Scholar]
- Cao, Y.; Wang, C.; Li, Z.; Zhang, L.; Zhang, L. Spatial-bag-of-features. In Proceedings of the 2010 IEEE Computer Society Conference on Computer Vision and Pattern Recognition, San Francisco, CA, USA, 13–18 June 2010; pp. 3352–3359. [Google Scholar]
- Smith, R. An overview of the Tesseract OCR engine. In Proceedings of the Ninth International Conference on Document Analysis and Recognition (ICDAR 2007), Curitiba, Brazil, 23–26 September 2007; pp. 629–633. [Google Scholar]



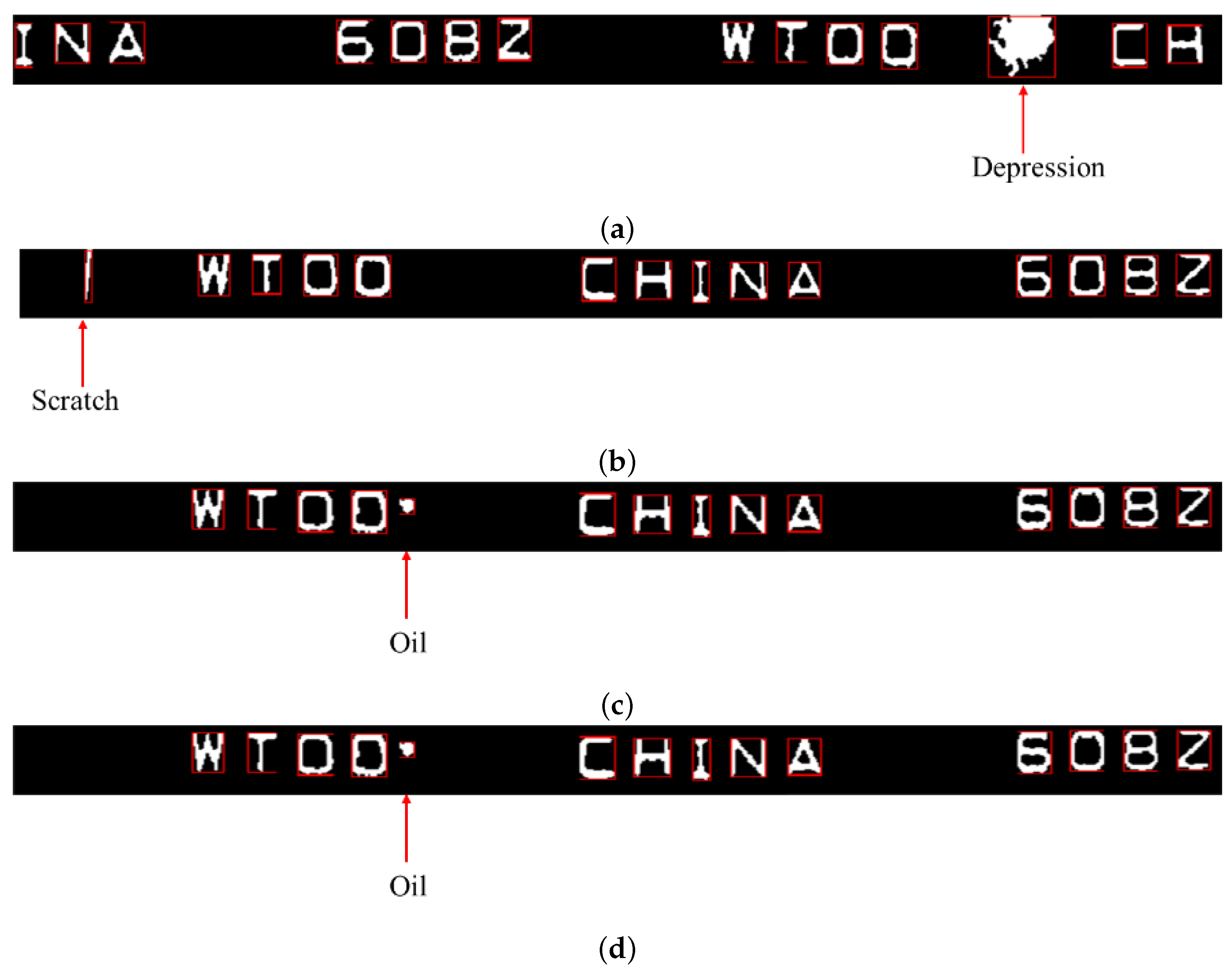
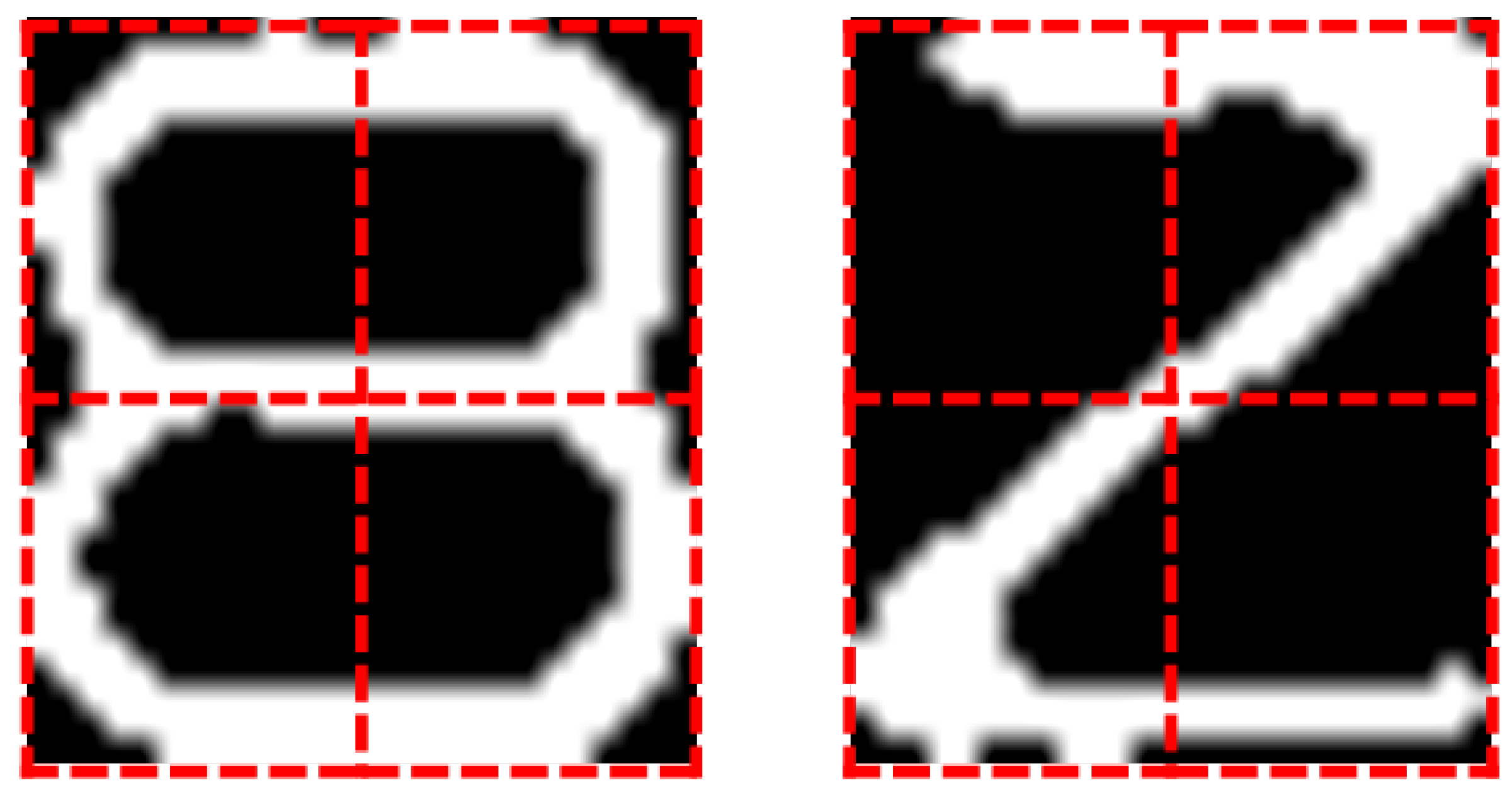
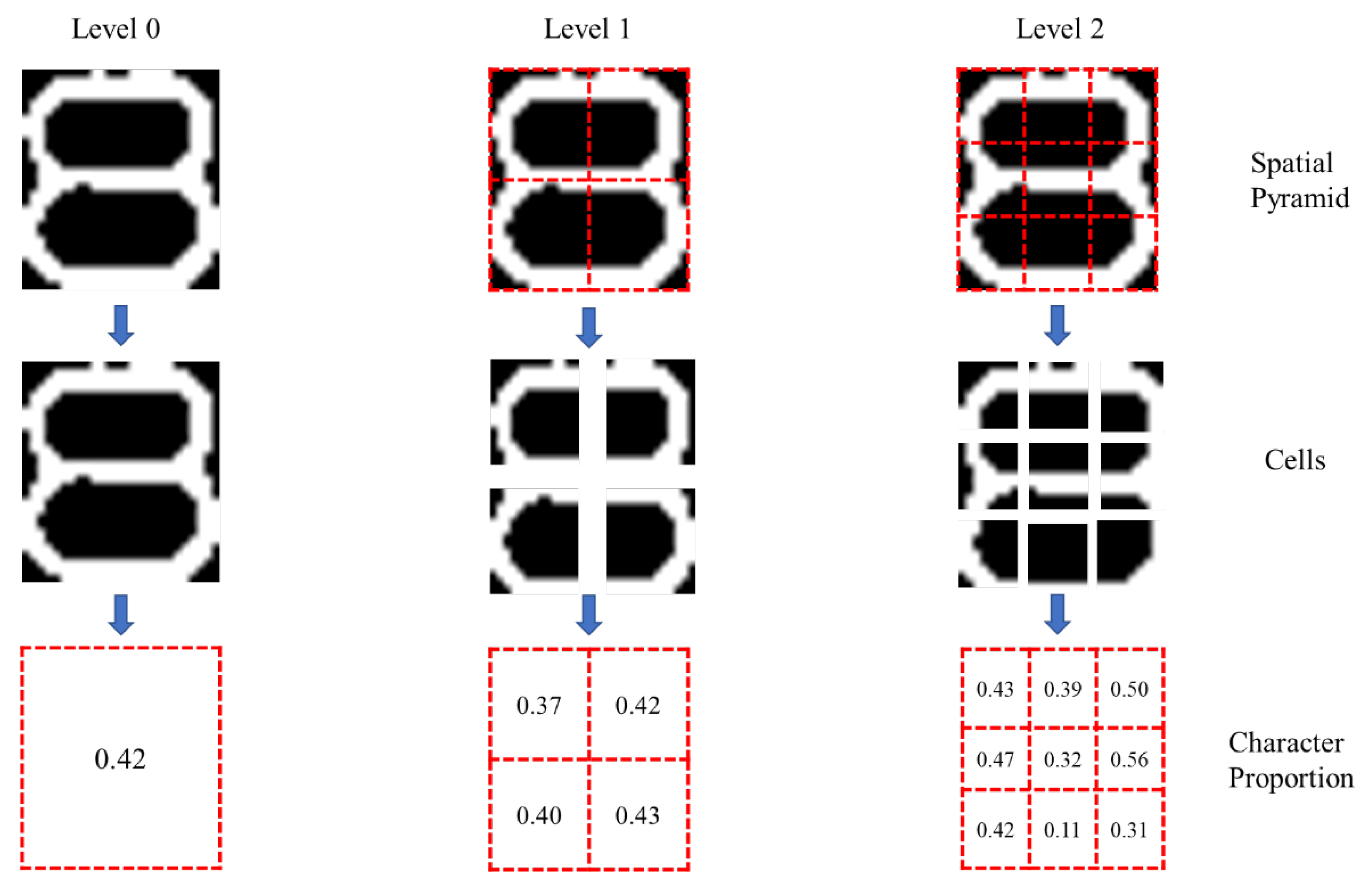
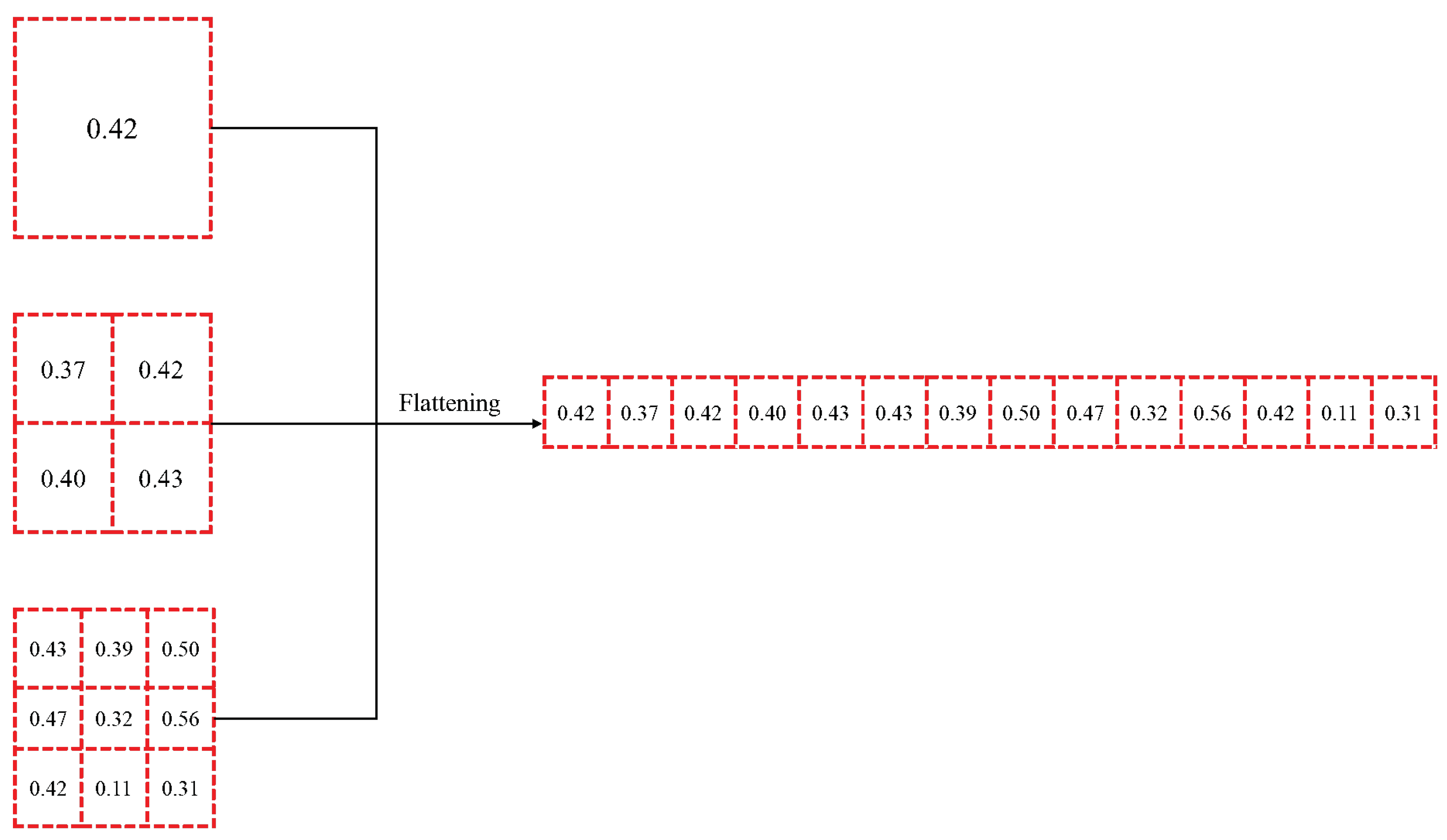
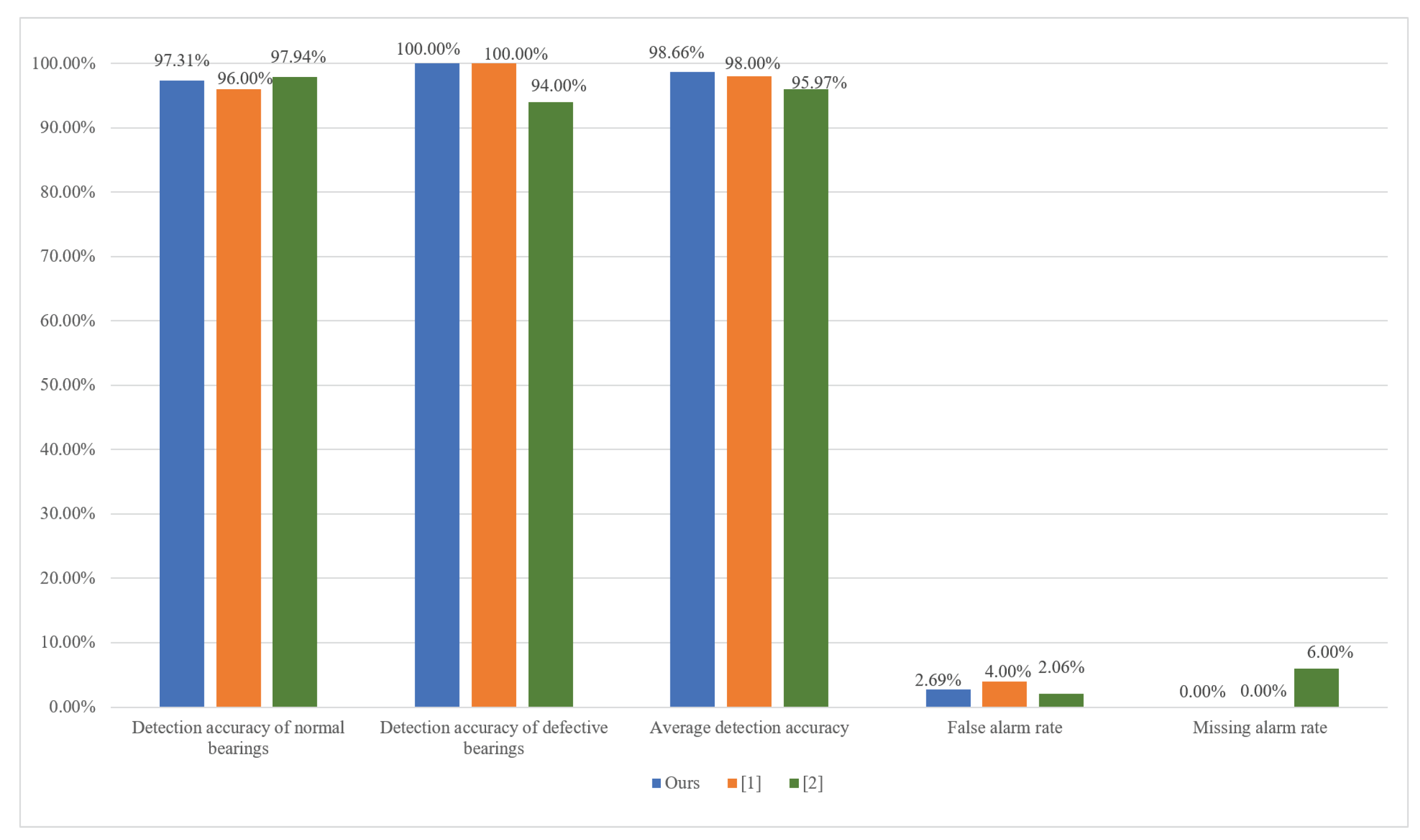
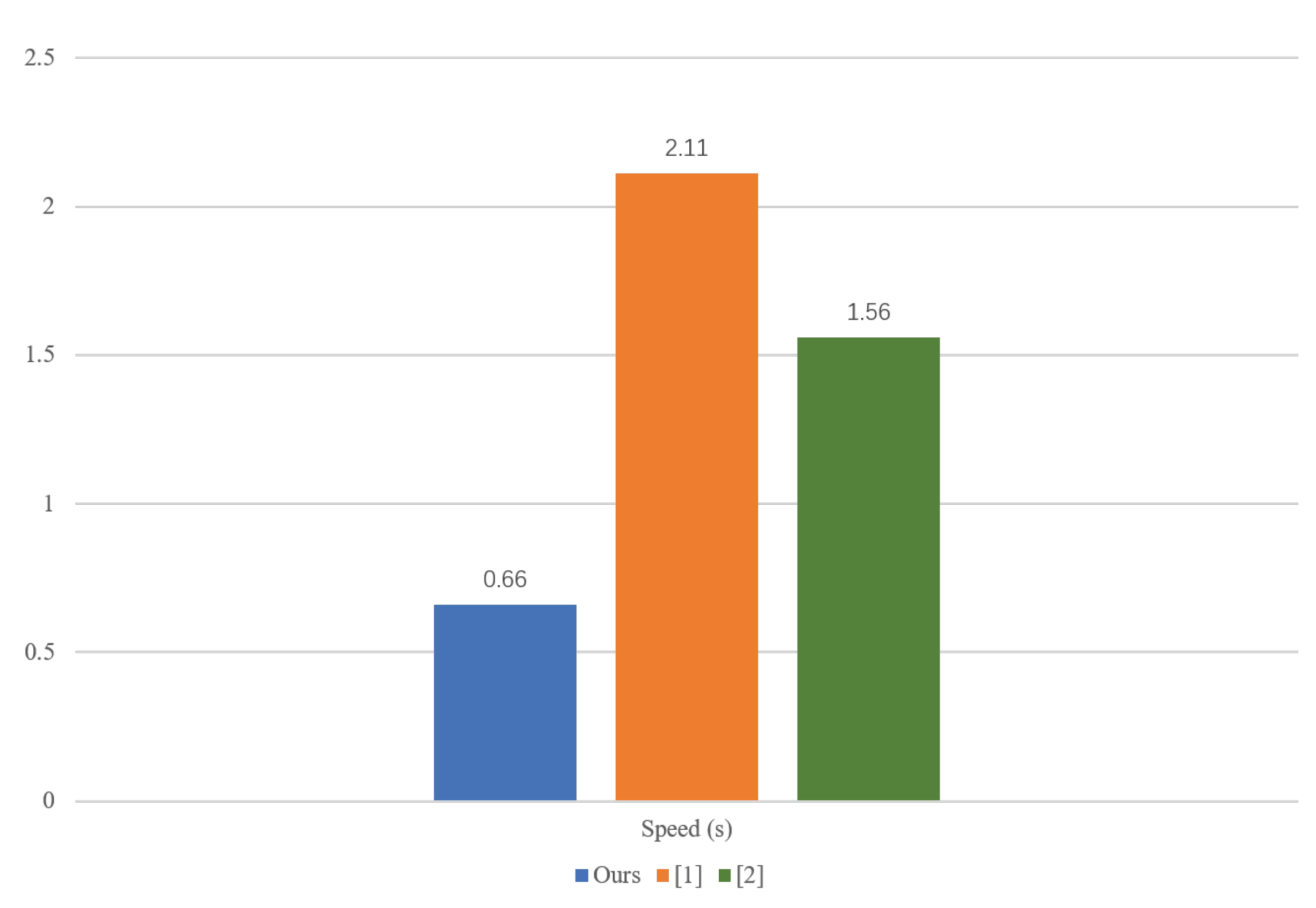
| Number of Normal Bearings | Number of Detected Normal Bearings | Number of Defective Bearings | Number of Detected Defective Bearings | |
| 965 | 939 | 320 | 320 | |
| Detection Accuracy of Normal Bearings | Detection Accuracy of Defective Bearings | Average Detection Accuracy | False Alarm Rate | Missing Alarm Rate |
| 97.31% | 100.00% | 98.66% | 2.69% | 0.00% |
| Number of Normal Bearings | Number of Detected Normal Bearings | Number of Notched Bearings | Number of Detected Notched Bearings |
|---|---|---|---|
| 64 | 64 | 36 | 36 |
| Detection Accuracy of Normal Bearings | Detection Accuracy of Notched Bearings | False Alarm Rate | Missing Alarm Rate |
| 100.00% | 100.00% | 0.00% | 0.00% |
| Number of Normal Bearings | Number of Detected Normal Bearings | Number of Bearings with Abnormal Dimension | Number of Detected Bearings with Abnormal Dimension |
|---|---|---|---|
| 55 | 55 | 45 | 45 |
| Detection Accuracy of Normal Bearings | Detection Accuracy of Bearings with Abnormal Dimension | False Alarm Rate | Missing Alarm Rate |
| 100.00% | 100.00% | 0.00% | 0.00% |
| Number of Normal Bearings | Number of Detected Normal Bearings | Number of Bearings with Depressions | Number of Detected Bearings with Depressions |
|---|---|---|---|
| 52 | 52 | 16 | 16 |
| Number of Bearings with Scratches | Number of Detected Bearings with Scratches | Number of Bearings with Oil | Number of Detected Bearings with Oil |
| 20 | 20 | 12 | 12 |
| Detection Accuracy of Normal Bearings | Detection Accuracy of Bearings with Depressions | Detection Accuracy of Bearings with Scratches | Detection Accuracy of Bearings with Oil |
| 100.00% | 100.00% | 100.00% | 100.00% |
| False Alarm Rate | Missing Alarm Rate | ||
| 0.00% | 0.00% |
| Number of Normal Bearings | Number of Detected Normal Bearings | Number of Bearings with Character Depressions | Number of Detected Bearings with Character Depressions |
|---|---|---|---|
| 51 | 49 | 24 | 24 |
| Number of Bearings with Character Scratches | Number of Detected Bearings with Character Scratches | Number of Bearings with Shallow Characters | Number of Detected Bearings with Shallow Characters |
| 12 | 12 | 13 | 13 |
| Detection Accuracy of Normal Bearings | Detection Accuracy of Bearings with Character Depressions | Detection Accuracy of Bearings with Character Scratches | Detection Accuracy of Bearings with Shallow Characters |
| 96.08% | 100.00% | 100.00% | 100.00% |
| False Alarm Rate | Missing Alarm Rate | ||
| 3.92% | 0.00% |
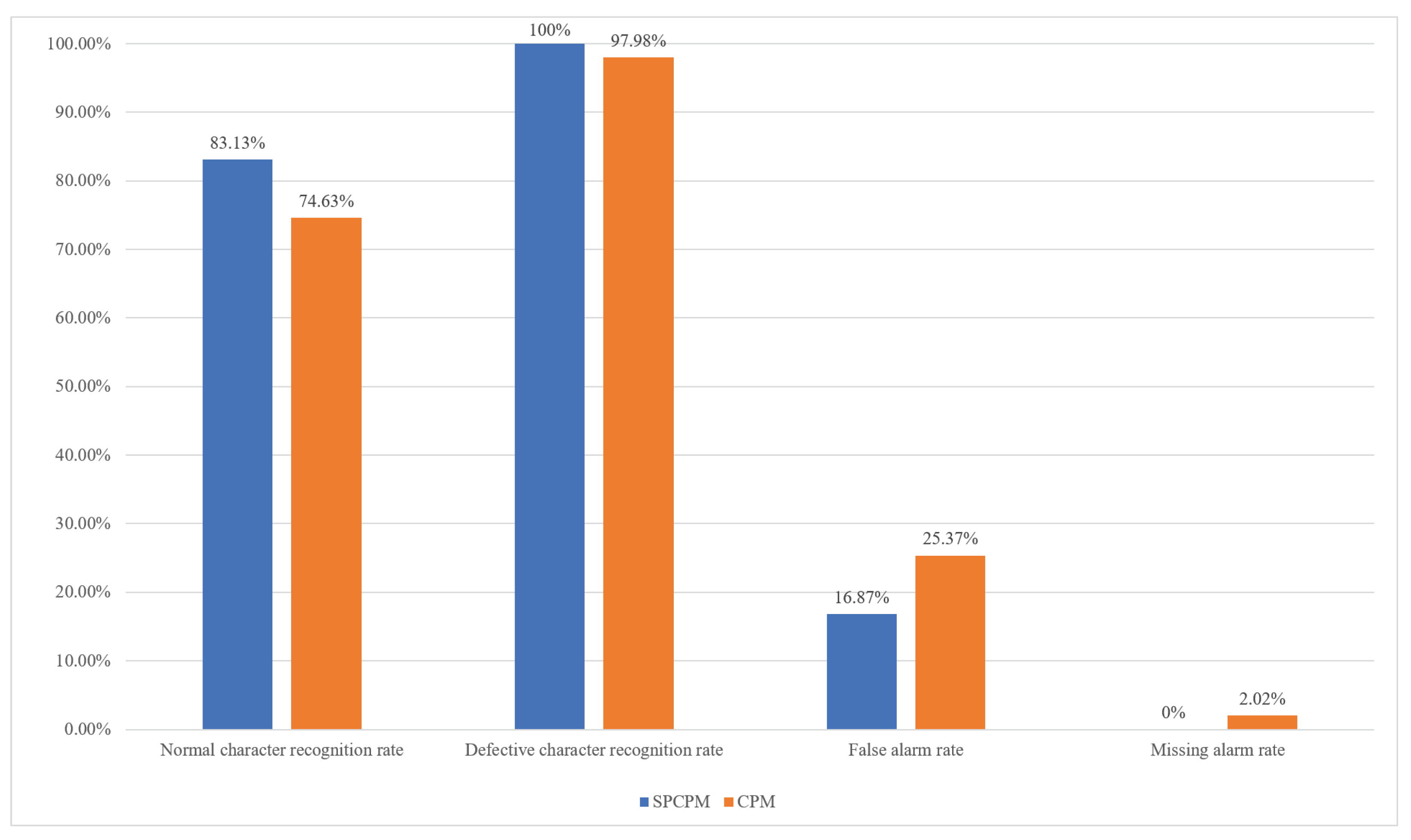
| Number of Normal Characters | Number of Detected Normal Characters | Number of Defective Characters | Number of Detected Defective Characters |
|---|---|---|---|
| 753 | 626 | 247 | 247 |
| Recognition Accuracy of Normal Characters | Recognition Accuracy of Defective Characters | False Alarm Rate | Missing Alarm Rate |
| 83.13% | 100.00% | 16.87% | 0.00% |
| Number of Normal Characters | Number of Detected Normal Characters | Number of Defective Characters | Number of Detected Defective Characters |
|---|---|---|---|
| 753 | 562 | 247 | 242 |
| Recognition Accuracy of Normal Characters | Recognition Accuracy of Defective Characters | False Alarm Rate | Missing Alarm Rate |
| 74.63% | 97.98% | 25.37% | 2.02% |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Lei, L.; Sun, S.; Zhang, Y.; Liu, H.; Xie, H. Segmented Embedded Rapid Defect Detection Method for Bearing Surface Defects. Machines 2021, 9, 40. https://doi.org/10.3390/machines9020040
Lei L, Sun S, Zhang Y, Liu H, Xie H. Segmented Embedded Rapid Defect Detection Method for Bearing Surface Defects. Machines. 2021; 9(2):40. https://doi.org/10.3390/machines9020040
Chicago/Turabian StyleLei, Linjian, Shengli Sun, Yue Zhang, Huikai Liu, and Hui Xie. 2021. "Segmented Embedded Rapid Defect Detection Method for Bearing Surface Defects" Machines 9, no. 2: 40. https://doi.org/10.3390/machines9020040
APA StyleLei, L., Sun, S., Zhang, Y., Liu, H., & Xie, H. (2021). Segmented Embedded Rapid Defect Detection Method for Bearing Surface Defects. Machines, 9(2), 40. https://doi.org/10.3390/machines9020040