Abstract
In this paper, we study the restricted singular-value decomposition (RSVD) for three quaternion tensors under the Einstein product, and give higher-order RSVD over the quaternion algebra, which can achieve simultaneous singular value decomposition of three quaternion tensors. Moreover, we give the algorithm for computing the RSVD of for quaternion tensors. What is more, we present a new blind color video watermarking scheme based on the forth-order RSVD over the quaternion algebra, and our numerical example demonstrates the effectiveness of the framework.
MSC:
15A69; 11R52; 15A18; 15A09
1. Introduction
Higher-order tensor decomposition has a wide range of applications, such as signal processing, data mining, genomic signals and so on. Kolda and Bader, [1] in 2009, provided theoretical developments and applications of tensor decomposition. Moreover, a lot of papers discussing tensor decomposition and other fields of tensor theory have been presented [2,3,4,5,6,7,8,9,10,11,12].
Tensor equations have high application values in engineering and science, for example, modeling the problems for continuum physics and engineering, isotropic and anisotropic flexibility, and reducing order modeling [13]. In addition, there are also some papers using different approaches to investigate tensor equation over fields [4,14].
W.R. Hamilton [15] in 1843 first introduced the concept of quaternions. Quaternion algebra is an associative and noncommutative division algebra over the real number field. Many scholars have applied it to quantum physics, signal, computer science, and color image processing, etc. [16]. In particular, applications for quaternion matrix factorization in color signal processing, image processing, and recognition are also prominent [17,18].
It is well known that matrix decomposition has a wide range of applications, and at the same time, due to the quaternion structure, the quaternion matrix retains more information, which is especially well applied in image processing. However, for video or higher-dimensional signals, the quaternion matrix can no longer meet the storage requirements. Therefore, research on quaternion tensors becomes necessary.
Multi-tensor factorization on quaternion algebra is currently underdeveloped compared to tensor factorization on traditional algebra. It is very challenging to generalize results of real or complex numbers to quaternions due to their non-commutative properties. Tensor decomposition and quaternion algebra all have wide applications [19,20], and the theory of quaternion tensor theory is also in urgent need of development. Therefore, in this paper, we propose the restricted singular value decomposition (higher-order RSVD) of quaternion tensor triples. Our contributions are as follows:
- We give the structure for higher-order RSVD on quaternion algebra as wells as two special cases: singular value decomposition for one quaternion tensor and quotient singular value decomposition for two quaternion tensors (higher-order QSVD) under the isomorphic group structures and the Einstein product (Definition 1).
- We present a blind color video watermarking scheme based on the forth-order RSVD over the quaternion algebra.
The rest of the paper is organized as follows. In Section 2, we introduce some basic knowledge of tensor quaternions. In Section 3, we investigate the restricted singular value decomposition for three quaternion tensors. In Section 4, we give the application for RSVD. We finally give the conclusion in Section 5.
2. Preliminaries
The number of dimensions of a tensor is called the order. Matrices (tensors of order two) are written as capitals, e.g., A. Higher-order tensors (order three or higher) are written as calligraphic letters, e.g., . An order N tensor is a multidimensional array with entries. Let and be, respectively, for the sets of the order N dimension tensors over the real number field , the complex number field and the quaternion algebra
As we all know, quaternion algebra is an associative and noncommutative division algebra. We refer the reader to the recent book [21] for more definitions and properties of quaternions. The symbol stands for the conjugate transpose of a quaternion where . Clearly,
For a quaternion tensor , let be the conjugate transpose of , where . The tensor is denoted by . A “square” tensor is said to be Hermitian if . A “square” tensor is called a diagonal tensor if all its entries are zero except for . If all the diagonal entries , then is a unit tensor, denoted by . The zero tensor with suitable order is denoted by 0. More detail regarding the basic definitions and properties of tensors are in [1].
The most common types of tensor multiplications are denoted by for the Einstein, for the n-mode, ⊗ for the Kronecker, ⊙ for the Khatri–Rao, and ⊛ for the Hadamard products. We refer the reader to the paper [22] for the latter four definitions.
We only focus on the Einstein product in this paper. First of all, the definition of the Einstein product is as following.
Definition 1
(Einstein product [23]). For and , the Einstein product of tensors and is defined by the operation via
where .
As a contracted product, the Einstein product has great applications for continuum mechanics [24] and the relativity theory [23]. The associative law of this tensor product is established. On the one hand, the Einstein product is the standard matrix multiplication. On the other hand, when specifying mode summation, the n-mode product is the Einstein product A more general definition of contraction can be seen in [25].
In 2013, Navasca et al. [4] introduced the transformation f between the tensor and matrix over real number field. We give the following definition for the transformation f between the tensor and matrix over the quaternion.
Definition 2
(transformation [4]). Define the transformation with defined component-wise as
where and . That is, the element has one-to-one correspondence between the quaternion matrix A and the quaternion tensor
Lemma 1.
Let , and f be the map defined in (2). Then the following properties hold:
- 1.
- The map f is a bijection. Moreover, there exists a bijective inverse map :
- 2.
- The map satisfies , where · refers to the usual matrix multiplication.
As can be seen from the Lemma 1, the Einstein product can be defined by the transformation:
Consequently, the inverse map satisfies
where A and B are quaternion matrices with appropriate sizes.
The following lemma appears in [4] over the real number field. In addition, we can extend it to the quaternion algebra by using similar methods.
Lemma 2
([4]). Suppose is a group. Let be any bijection. Then we can define a group structure on by defining
for all . Moreover, the mapping f is an isomorphism.
3. Restricted Singular-Value Decomposition for Three Quaternion Tensors
In this section, we investigate the restricted singular value decomposition of three quaternion tensors based on the isomorphic group structures and the Einstein product.
De Moor introduced the RSVD for a matrix triplet over real field, and Golub [26] and Zha [27] further developed and discussed by Chu and De Moor [28,29]. Moreover, Chu, De Lathauwer, and De Moor [30] presented the CSD-based QR-type method to compute the RSVD for a real matrix triplet. More recently, He, Wang, and De Moor [31] presented the RSVD for a matrix triplet over the quaternion.
Lemma 3
(RSVD for three quaternion matrices [26,31]). Let and be given. There exist unitary matrices and , and nonsingular matrices and such that
where
and is square nonsingular diagonal with positive diagonal elements, are defined to be the non-trivial restricted singular values of the matrix triplet Expressions for the integers are the following:
where the symbol stands for the rank of the quaternion matrix A.
Now we give the definitions of the unitary quaternion tensor and quaternion tensor inverse.
Definition 3 (unitary quaternion tensor).
A tensor is unitary if
Definition 4 (inverse of an even order tensor).
A tensor is called the inverse of if it satisfies It is denoted by
Now we give the higher-order RSVD over the quaternion in the following theorem.
Theorem 1.
(higher-order RSVD over the quaternion tensor) Given , and . Then there exist unitary tensors , and invertible tensors , such that
where the tensors , and have the following structures
where
are the non-trivial restricted singular values of the matrix triplet , and f is the transformation in (2). Expressions for the subscripts , , , and are given in Theorem 2.
Proof.
Let and
. Applying the RSVD (Lemma 3) on the matrix triplet , we obtain
where
and is square nonsingular diagonal with positive diagonal elements, are defined to be the non-trivial restricted singular values of the matrix triplet the expressions for are given by (13)–(17). The matrices and are unitary, and and are invertible.
From the property of f in (5) and Lemma 2, we have
where are invertible tensors, are unitary tensors, is a real tensor whose nonzero entries are 1, and the non-trivial restricted singular values of the matrix triplet , , and are real tensors whose nonzero entries are 1.
Now we consider the subscripts of nonzero entries in the tensors . Note that the subscripts of 1 and the non-trivial restricted singular values in are and , respectively, where
Suppose the subscripts of 1 and in the tensor are and
, respectively. Then, we have
Similarly, we can give the structures of tensors of and . □
The direct expressions for the subscripts of nonzero entries in the tensors , , will be given in the following theorem.
Theorem 2.
Consider the above higher-order RSVD for three tensors , and . The expressions for the subscripts , , , and are given by:
and is the greatest integer less than or equal to the real number a.
Now we give the following Algorithm 1 for computing the RSVD of three quaternion tensors.
| Algorithm 1: Computing the RSVD of quaternion tensors and . |
| Input: . |
| Output: , , |
| , and . |
| 1. , , . |
| 2. Give the RSVD of and C by the method in [30], |
| , |
| , |
| , |
| 3. , , , |
| , , . |
One numerical example is as following.
Example 1.
Consider the higher-order SVD for -quaternion tensor defined by
Then we have
where and are unitary tensors and
4. Some Applications
In this section, we give a watermarking scheme for blind color video based on the forth-order RSVD over the quaternion algebra. A fourth-order pure quaternion tensor can represent a color video with the even frames, where and denote the height and width of each frame, respectively, and is the frame number of the video.
Moreover, the fourth-order pure quaternion tensor will save more information than the traditional method because of the advantages of quaternions in color image processing. Now we embed three color video watermarks simultaneously into one color video based on RSVD over the quaternion tensor, and extract these three watermarks using two keys. Now we simultaneously insert three color video watermarks into one color video by RSVD on quaternion tensors, and extract the three watermarks with two keys.
denotes a color host video. , and denotes three color video watermarks (). Now we give the following procedures to plug three watermarks in the host video. Let , and . Then G is a pure quaternion matrix when is zero matrix.
The inserting process is as following:
- Step 1.
- Decomposition three quaternion tensors , and by RSVD,where and are two keys, which are stored for the process of watermark extraction.
- Step 2.
- Transformation under map f:andwhere is a pure quaternion matrix.
- Step 3.
- Obtaining the principal component of each video:
- Step 4.
- Dividing into non-coinciding blocks and the size of the blocks is , where , . is the orthogonal transformed part for block position , of , which is saved for the extraction.
- Step 5.
- Getting the principal components , and in step 3 in the transformed blocks in step 4:where is a scale factor, which can control watermarking strength. In particular, the larger is, the stronger the robustness of watermark is, when the value of is confirmed.
- Step 6.
- The watermarked matrices , and are obtained by the inverse orthogonal transformation, and .
- Step 7.
- The inverse map gives the watermarked video
Next, the procedure of the extraction process is shown in the following.
- Step 1.
- Map the watermarked video into a quaternion matrix
- Step 2.
- Split matrices into blocks , which has size , of . In order to extract the video watermarks, save ,.
- Step 3.
- The extracted principal components for each video are obtained by the following:
- Step 4.
- The extracted color videos , , and are obtained by:Note that we use the quaternion singular value decomposition method in [32] to get the inverse of a nonsingular quaternion matrix.
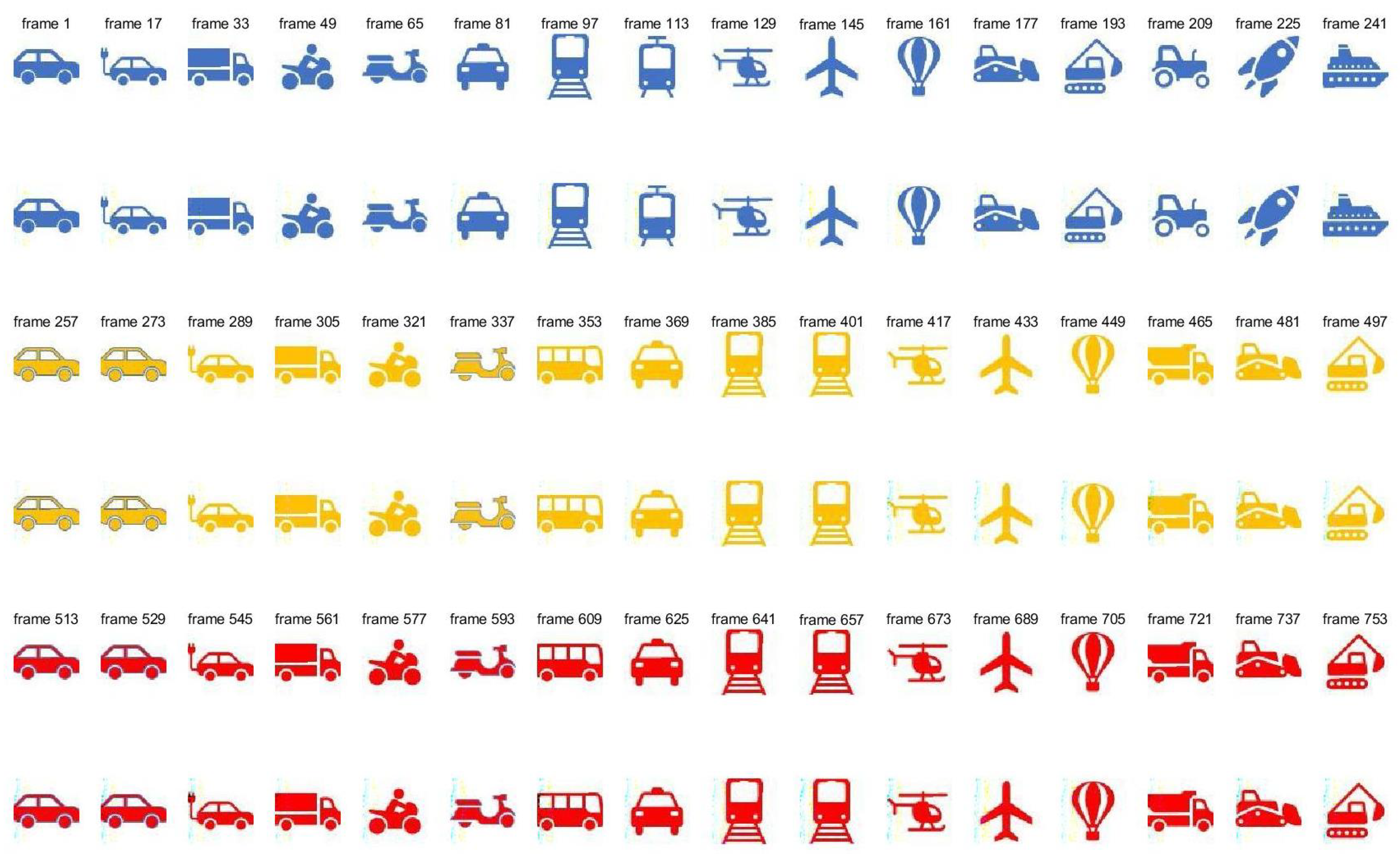
In the following experiment, our host video is the color video cars with 1024 frames and pixels, and watermarks are three color video with the same frame number 256 and the same size . Taking , we plug our watermarks into the host video, and extract them from the watermarked host video by the above frameworks based on the discrete wavelet transform (DWT) [33], and results are shown in Figure 1.

Figure 1.
Pictures of original host and watermarked host. Pictures in the first, third, and fifth lines are the frames of the original host video, and pictures in the second, fourth, and sixth lines are the frames of the watermarked video.
In Figure 1, we show some frames of original host video in the first, third and fifth lines, and the frames of the watermarked video in the second, fourth, and sixth lines. It can be seen visually that the original images and the watermarked images at the same number of frames are very similar. Therefore, we can conclude that the video watermarks are invisible in the watermarked video.
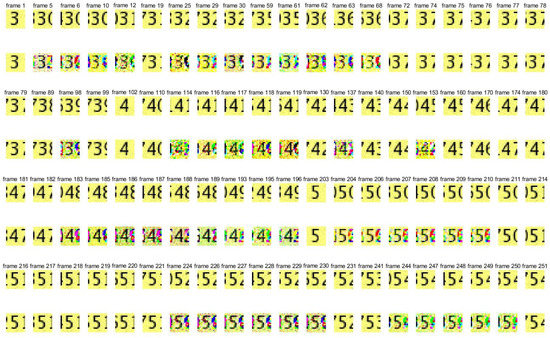
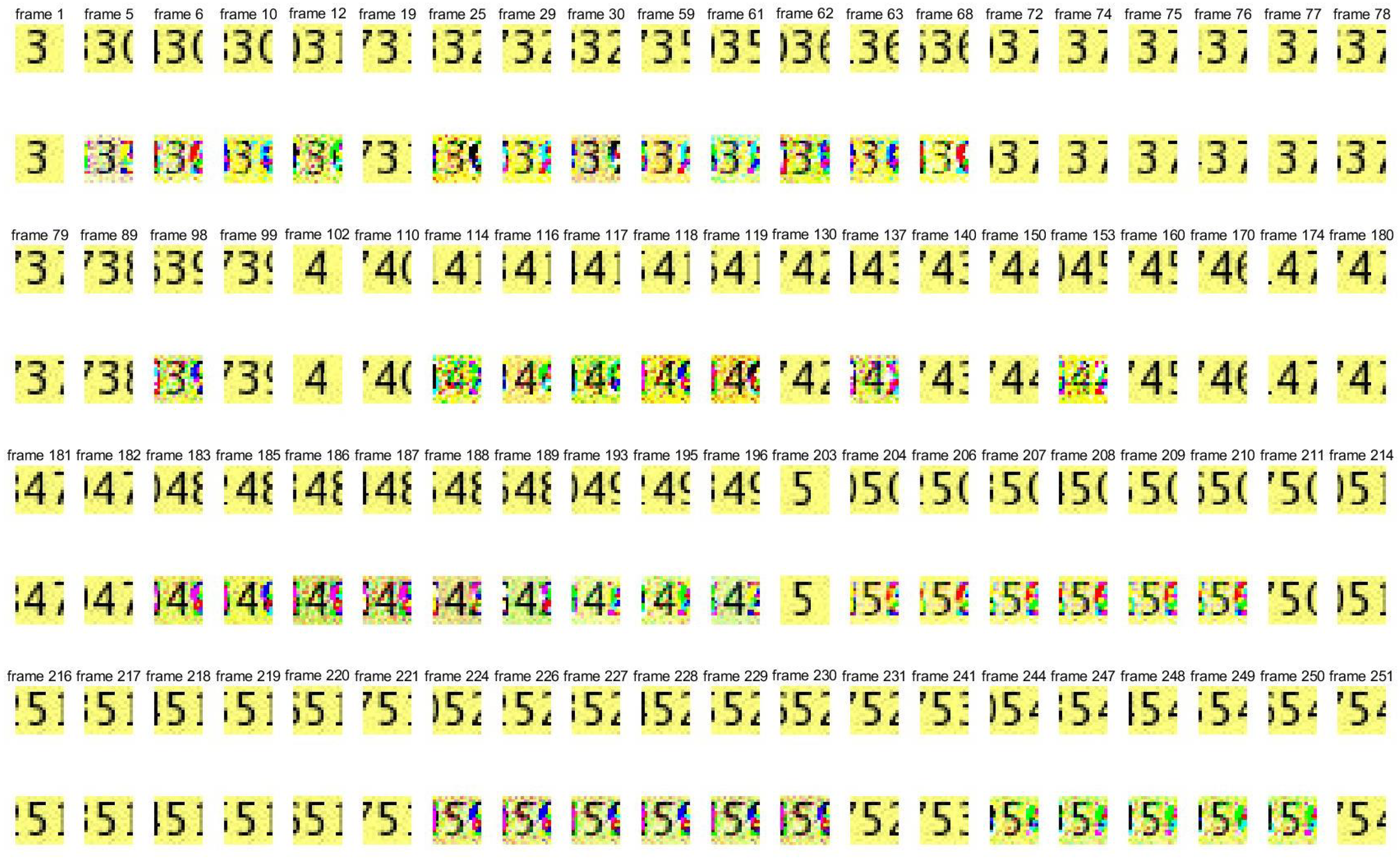
Figure 2.
Pictures of watermark 1 and extracted watermark 1. Pictures in the first, third, and fifth lines are the frames in the original watermark video 1, and pictures in the second, fourth, and sixth lines are the frames in the extracted watermark video 1.

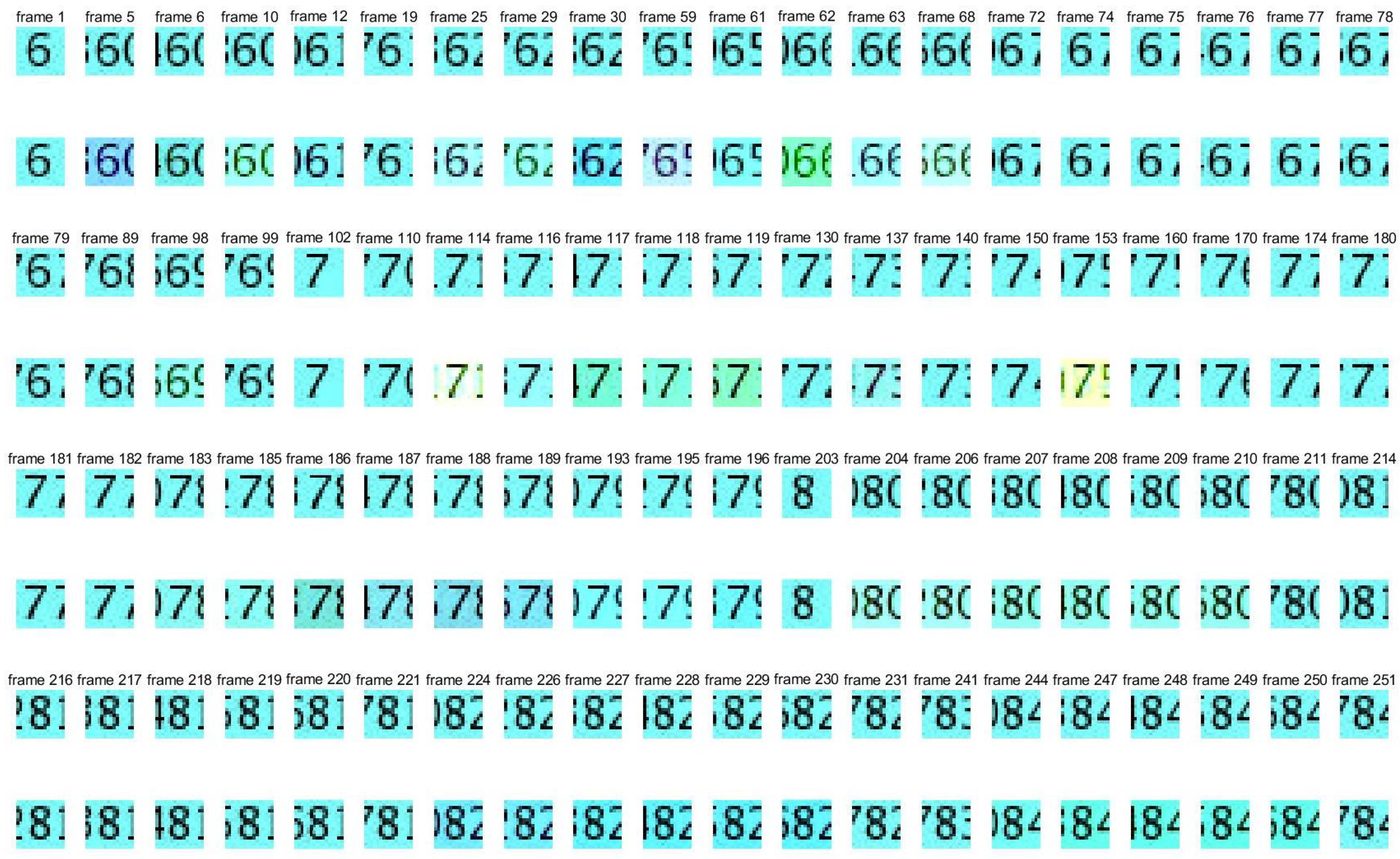
Figure 3.
Pictures of watermark 2 and extracted watermark 2. Pictures in the first, third, and fifth lines are the frames in the original watermark video 2, and pictures in the second, fourth, and sixth lines are the frames in the extracted watermark video 2.
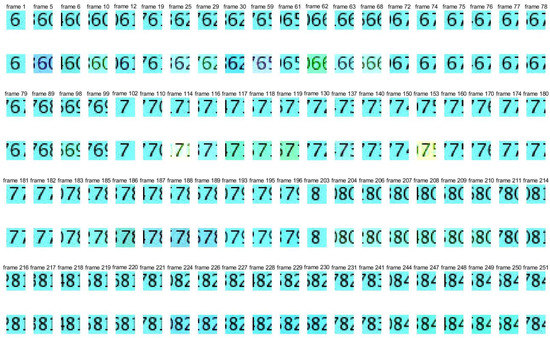
Figure 4.
Pictures of watermark 3 and extracted watermark 3. Pictures in the first, third, and fifth lines are the frames in the original watermark video 3, and pictures in the second, fourth, and sixth lines are the frames in the extracted watermark video 3.
From Figure 2, Figure 3 and Figure 4, it can be seen that the quality of the extracted watermarks is very good, especially watermark 2, which is of particularly high quality.
The blind color video watermark processing framework based on RSVD over the quaternion tensor processes three color video waters simultaneously. In addition, only two keys are needed for the extraction process. Furthermore, it can be seen that the the reliable security of proposed blind color video watermarking scheme has been shown through numerical experiments.
5. Conclusions
In this paper, we have derived the restricted singular value decomposition for three quaternion tensors based on the isomorphic group structures and the Einstein product. As an application of RSVD, we present a blind color video watermarking scheme under the forth-order RSVD over the quaternion algebra. We plug three color video watermarks simultaneously into one host by the blind color video watermarking scheme, and extract the three watermarks by using two keys. Finally, numerical experiments show that the proposed blind color video watermarking scheme has reliable security. In the future, implementation algorithms based on quaternion tensors need to receive more attention. Due to the computational difficulty of quaternion and the high dimensionality of tensors, the design of a fast and effective quaternion tensor algorithm is a very meaningful research topic. This paper and future research content will provide new ideas and bring great improvements to video signal processing and high-dimensional signal processing.
Author Contributions
Methodology, W.-J.C.; software, W.-J.C.; writing-original draft preparation, W.-J.C.; writing-review and editing, W.-J.C. and S.-W.Y.; supervision, S.-W.Y.; project administration, S.-W.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Kolda, T.G.; Bader, B.W. Tensor decompositions and applications. SIAM Rev. 2009, 51, 455–500. [Google Scholar] [CrossRef]
- He, Z.H.; Qin, W.L.; Wang, X.X. Some applications of a decomposition for five quaternion matrices in control system and color image processing. Comput. Appl. Math. 2021, 40, 205. [Google Scholar] [CrossRef]
- He, Z.H.; Michael, K.N.; Zeng, C. Generalized Singular Value Decompositions for Tensors and Their Applications. Numer. Math. Theory Methods Appl. 2021, 14, 692–713. [Google Scholar] [CrossRef]
- Brazell, M.; Li, N.; Navasca, C.; Tamon, C. Solving multilinear systems via tensor inversion. SIAM J. Matrix Anal. Appl. 2013, 34, 542–570. [Google Scholar] [CrossRef]
- Yang, Q.Z.; Yang, Y.N. Further results for Perron Frobenius theorem for nonnegative tensors II. SIAM J. Matrix Anal. Appl. 2011, 32, 1236–1250. [Google Scholar] [CrossRef]
- He, Z.H.; Chen, C.; Wang, X.X. A simultaneous decomposition for three quaternion tensors with applications in color video signal processing. Anal. Appl. 2021, 19, 529–549. [Google Scholar] [CrossRef]
- Yang, Y.N.; Yang, Q.Z. A Study on Eigenvalues of Higher-Order Tensors and Related Polynomial Optimization Problems; Science Press: Beijing, China, 2015. [Google Scholar]
- He, Z.H.; Wang, X.X.; Zhao, Y.F. Eigenvalues of quaternion tensors with applications to color video processing. J. Sci. Comput. 2023, 94, 1. [Google Scholar] [CrossRef]
- He, Z.H.; Navasca, C.; Wang, X.X. Decomposition for a quaternion tensor triplet with applications. Adv. Appl. Clifford Algebr. 2022, 32, 9. [Google Scholar] [CrossRef]
- He, Z.H. Pure PSVD approach to Sylvester-type quaternion matrix equations. Electron. J. Linear Algebra 2019, 35, 266–284. [Google Scholar] [CrossRef]
- He, Z.H. Some new results on a system of Sylvester-type quaternion matrix equations. Linear Multilinear Algebra 2021, 69, 3069–3091. [Google Scholar] [CrossRef]
- He, Z.H.; Wang, Q.W.; Zhang, Y. A simultaneous decomposition for seven matrices with applications. J. Comput. Appl. Math. 2019, 349, 93–113. [Google Scholar] [CrossRef]
- Antoulas, A.C.; Beattie, C.A.; Gugercin, S. Interpolatory Methods for Model Reduction; SIAM: Philadelphia, PA, USA, 2020. [Google Scholar]
- Sun, L.Z.; Zheng, B.D.; Bu, C.J.; Wei, Y.M. Moore-Penrose inverse of tensors via Einstein product. Linear Multilinear Algebra 2016, 64, 686–698. [Google Scholar] [CrossRef]
- Hamilton, W.R. Elements of Quaternions; Longmans Green and Co.: London, UK, 1866. [Google Scholar]
- Took, C.C.; Mandic, D.P. Augmented second-order statistics of quaternion random signals. Signal Process. 2011, 91, 214–224. [Google Scholar] [CrossRef]
- Bihan, N.L.; Mars, J. Singular value decomposition of quaternion matrices: A new tool for vector-sensor signal processing. Signal Process. 2004, 84, 1177–1199. [Google Scholar] [CrossRef]
- Zhang, Y.; Wang, R.H. The exact solution of a system of quaternion matrix equations involving η-Hermicity. Appl. Math. Comput. 2013, 222, 201–209. [Google Scholar] [CrossRef]
- Jukl, M.; Juklová, L. On decomposition problems on manifolds with a special differential operator. Miskolc Math. 2013, 14, 591–599. [Google Scholar]
- Mike?, J. Differential Geometry of Special Mappings; Palacky University: Olomouc, Czech Republic, 2015. [Google Scholar]
- Rodman, L. Topics in Quaternion Linear Algebra; Princeton University Press: Princeton, NJ, USA, 2014. [Google Scholar]
- Cichocki, A. Era of big data processing: A new approach via tensor networks and tensor decompositions. arXiv 2014, arXiv:1403.2048. [Google Scholar]
- Einstein, A. The foundation of the general theory of relativity. In The Collected Papers of Albert Einstein 6; Kox, A.J., Klein, M.J., Schulmann, R., Eds.; Princeton University Press: Princeton, NJ, USA, 2007; pp. 146–200. [Google Scholar]
- Lai, W.M.; Rubin, D.; Krempl, E. Introduction to Continuum Mechanics; Butterworth-Heinemann: Oxford, UK, 2009. [Google Scholar]
- De Lathauwer, L. Signal Processing Based on Multilinear Algebra. Ph.D Thesis, Katholike Universiteit Leuven, Leuven, Belgium, 1997. [Google Scholar]
- De Moor, B.; Golub, G.H. The restricted singular value decomposition: Properties and applications. SIAM J. Matrix Anal. Appl. 1991, 12, 401–425. [Google Scholar] [CrossRef]
- Zha, H. The restricted singular value decomposition of matrix triplets. SIAM J. Matrix Anal. Appl. 1991, 12, 172–194. [Google Scholar] [CrossRef]
- Chu, D.; De Lathauwer, L.; De Moor, B. A QR-type reduction for computing the SVD of a general matrix product/quotient. Numer. Math. 2003, 95, 101–121. [Google Scholar] [CrossRef]
- Chu, D.; De Moor, B. On the nonuniqueness of the factorization factors in the product singular value decomposition. Linear Algebra Appl. 2000, 314, 191–203. [Google Scholar] [CrossRef]
- Chu, D.; De Lathauwer, L.; De Moor, B. On the computation of the restricted singular value decomposition via the Cosine-Sine decomposition. SIAM J. Matrix Anal. Appl. 2000, 22, 580–601. [Google Scholar] [CrossRef]
- He, Z.H.; Agudelo, O.M.; Wang, Q.W.; De Moor, B. Two-sided coupled generalized Sylvester matrix equations solving using a simultaneous decomposition for fifteen matrices. Linear Algebra Appl. 2016, 496, 549–593. [Google Scholar] [CrossRef]
- Li, Y.; Wei, M.; Zhang, F.; Zhao, J. A Fast Structure-Preserving Method for Computing the Singular Value Decomposition of Quaternion Matrix. Appl. Math. Comput. 2014, 235, 157–167. [Google Scholar]
- Lai, C.C.; Tsai, C.C. Digital image watermarking using discrete wavelet transform and singular value decomposition. IEEE Trans. Instrum. Meas. 2010, 59, 3060–3063. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).