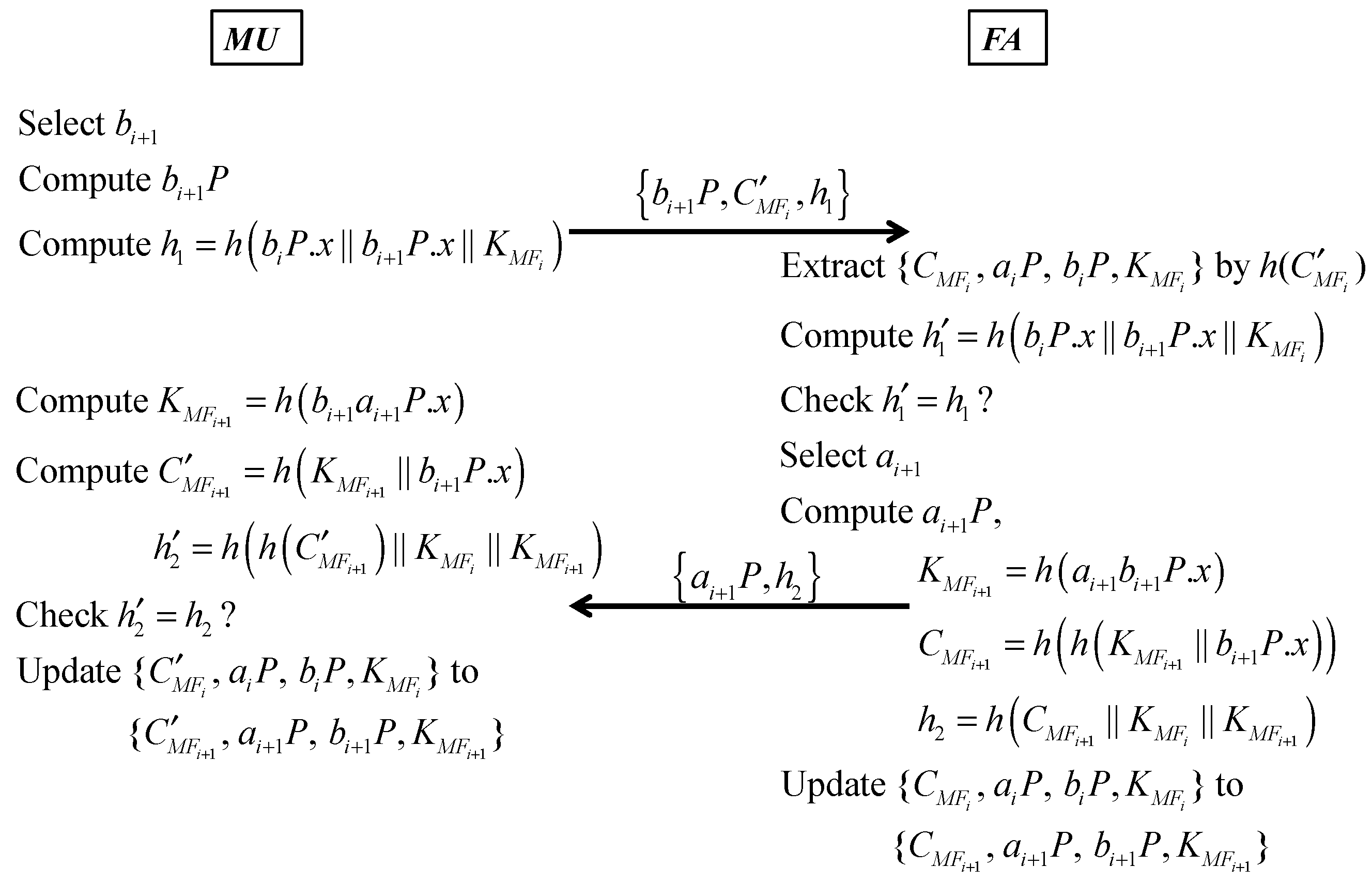1. Introduction
With the rapid growth of network technologies, users are used to accessing various services with their mobile devices. As a result, mobile devices and mobility networks play an important role in people’s daily lives. There are three entities in mobility networks; mobile user, home agent and foreign agent. Before being able to access mobile services, a mobile user needs to register with the home agent. After successful registration, the mobile user with a mobile device can access mobile services. These mobile services are provided by the home agent directly or a foreign agent. If the requested mobile service is provided by a foreign agent, the registered mobile user needs the home agent’s help to have himself/herself authenticated by the foreign agent. An illustration of mobility networks is shown in
Figure 1, where a mobile user with a mobile device can be regarded as a mobile node. Plenty of mobility network applications are proposed and utilized because they provide great convenience.
Although mobility networks bring people great convenience and advantages, security threats exist. First, the transmission medium is a public but insecure channel such that an attacker can easily eavesdrop or intercept the transmitted data. Second, when a mobile user enters a service domain dominated by a new foreign agent, the mobile user has to access services via the new foreign agent. In this condition, two issues raise: (1) how the mobile user determines whether the foreign agent is legal; and (2) how the foreign agent determines whether the mobile user is legal. That is, the mobile user and the foreign agent have to authenticate each other. Unfortunately, in the beginning, no secret is shared between them. Third, because the mobile user is a visitor, the foreign agent serves the mobile user when he continuously stays. The mobile user may continuously stay, but the mobile user may not request mobile services continuously. This denotes that the mobile user and the foreign agent do not always communicate with each other. In such a condition, it is a challenge for the mobile user and the foreign agent to ensure each other’s legality after they have already authenticated each other. Forth, a mobile user may roam. Because the transmission medium is public, anyone can eavesdrop. If an attacker wants to trace a mobile user, he can eavesdrop and use the intercepted messages to obtain required information.
To ensure security of mobility networks, many authentication protocols are proposed [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10]. In 2004, Zhu and Ma proposed an authentication scheme with anonymity for wireless environments based on the hash function and smart cards [
5]. Later, Lee et al. [
6] analyzed Zhu and Ma’s scheme and found that Zhu and Ma’s scheme does not provide mutual authentication and cannot resist forgery attack. In 2006, Lee et al. [
7] proposed an enhancement to improve Zhu and Ma’s authentication scheme for wireless networks. In 2009, Chang et al. [
8] analyzed Lee et al.’s scheme [
7] and pointed out that Lee et al.’s scheme still suffers from forgery attack and also proposed an improvement.
In 2014, Kuo et al. [
9] showed that Chang et al.’s scheme cannot ensure anonymity for mobile users and proposed an improvement. Kuo et al. claimed that their scheme could ensure efficiency and security in mobility networks and provide anonymity for mobile users. In 2015, Lu et al. [
10] showed that Kuo et al.’s scheme suffers from three drawbacks, vulnerability to insider attack, unfriendly password changes, and no local validation. They also proposed an authentication scheme to remedy these drawbacks. Later, Chang et al. [
11] found that Kuo et al.’s scheme [
9] is vulnerable to the other two weaknesses in 2016. First, Kuo et al.’s scheme cannot resist man-in-the-middle attacks when a mobile user and a foreign agent negotiate the session key. Via this security flaw, an attacker can impersonate a mobile user and negotiate the session key with the foreign agent. Second, Kuo et al.’s scheme cannot resist the synchronization problem. An attacker only needs to modify the transmitted data in password change phase such that a legal mobile user is unable to be authenticated by the home agent anymore. Lu et al. [
10] claimed that their scheme could defend against replay attack and provide mobile user anonymity.
After thoroughly analyzing Lu et al.’s scheme, Chang et al. found that it possesses three drawbacks [
12]. First, Lu et al.’s scheme is vulnerable to replay attack in authentication with key agreement phase. An attacker only needs to eavesdrop and resend the intercepted message with a new timestamp to cheat the foreign agent and the home agent. Second, user anonymity is not ensured as claimed because some transmitted parameters are fixed. Third, a random number chosen by the mobile user in registration phase is not stored in his/her smart card. As a result, the mobile user’s smart card cannot compute one essential parameter to have himself/herself authenticated by the home agent in authentication with key agreement phase.
In addition to mobility networks, privacy is also an important topic in different types of networks. To ensure privacy and security in different types of networks, related security mechanisms are proposed [
13,
14,
15,
16,
17,
18]. After analyzing the previous authentication schemes, the weaknesses that they suffer from and the security mechanisms of other networks, we propose a mobility network authentication scheme by considering the following four properties to ensure security and convenience.
Property 1: user anonymity
User anonymity needs to be ensured to prevent an unauthorized party from tracing a specific user. It denotes that only the authorized parties can know who the user is.
Property 2: resistance to common attacks
The proposed authentication scheme should be able to resist common attacks to ensure security.
Property 3: local password change
A mobile user should be able to change his/her password locally and at will without accessing the home agent to make the authentication scheme more convenient and user-friendly.
Property 4: mutual authentication between any two of a mobile user, a foreign agent and the home agent
In a mobility network authentication scheme, any two of a mobile user, a foreign agent and the home agent have to authenticate each other mutually to make sure that the other communication parties are legal.
The rest of this paper is organized as follows. The proposed scheme is shown in
Section 2. The corresponding analysis is given in
Section 3. Further discussions including comparisons and authentication proof using Burrows-Abadi-Needham logic (BAN logic) [
19] are made in
Section 4. Finally, some conclusions are given in
Section 5.
3. Property Analysis
In this section, we analyze our proposed scheme’s security and convenience by taking the following four properties into consideration: (1) user anonymity; (2) resistance to common attacks; (3) local password change; and (4) mutual authentication. In the following, we discuss our scheme to show that it possesses these properties.
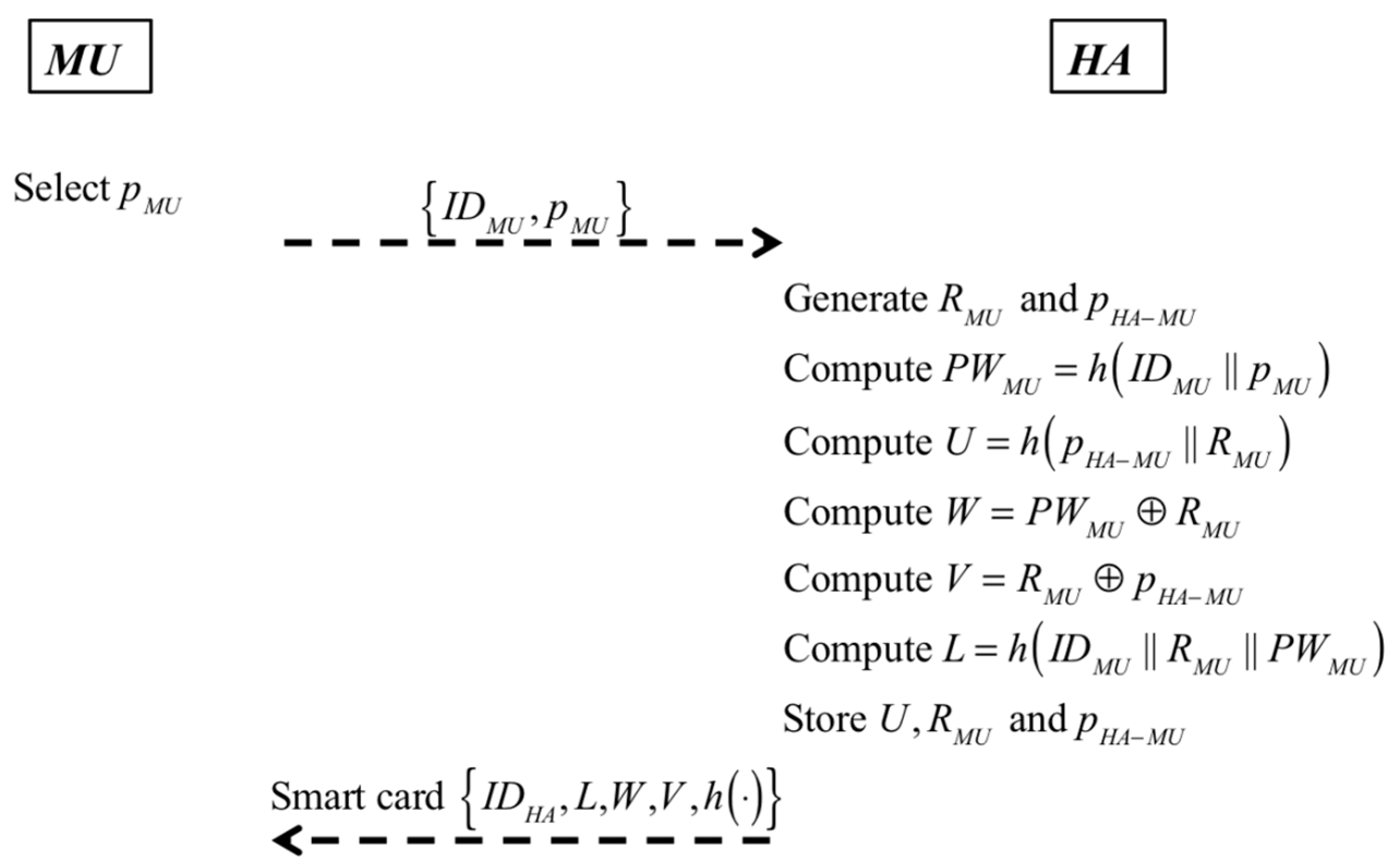
3.1. User Anonymity
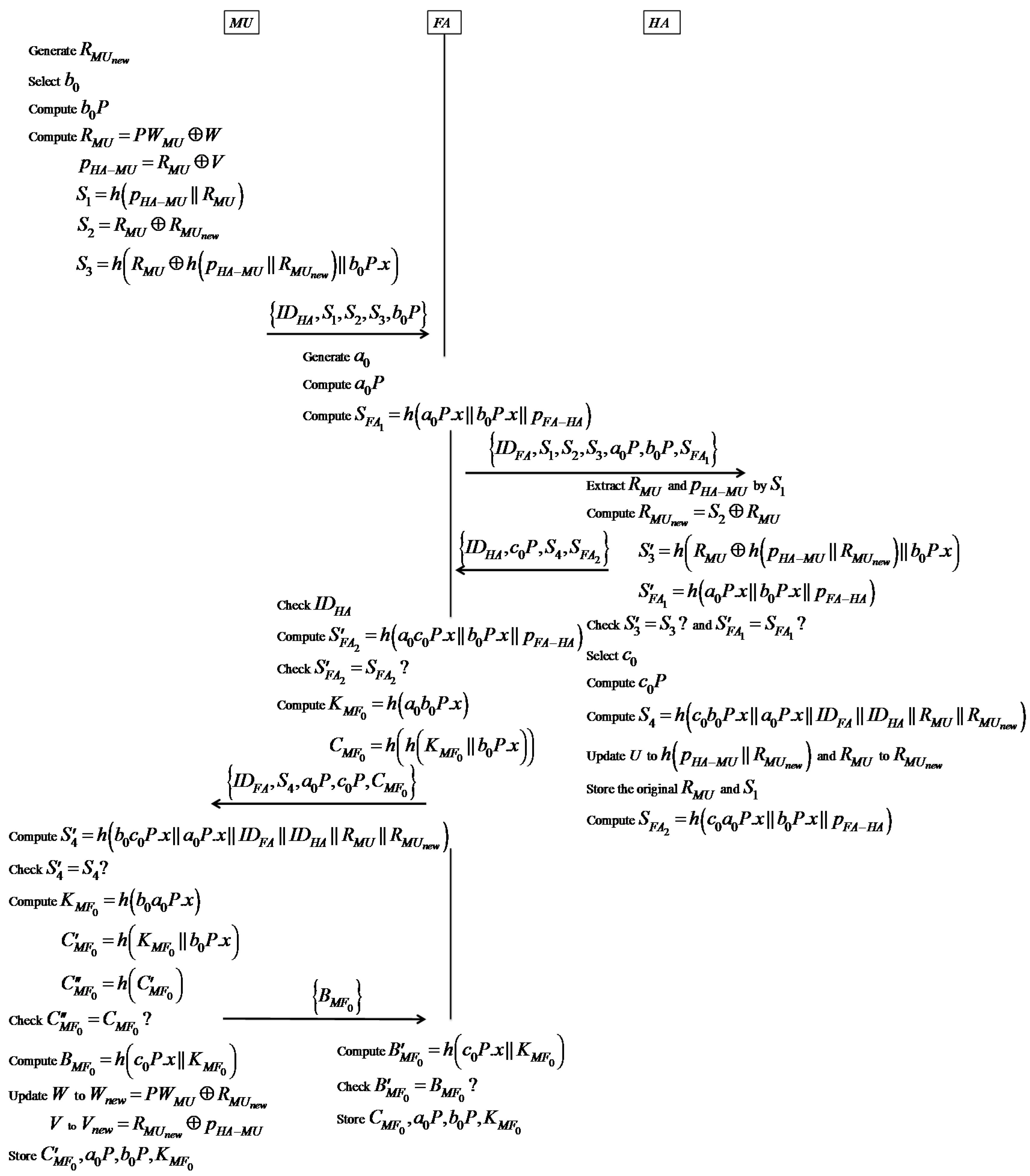
In our proposed scheme, MU’s real identifier is concealed in PWMU = h(IDMU || pMU) and is never transmitted when MU wants to access the roaming service. In authentication and establishment of the session key phase, MU sends {IDHA, S1, S2, S3, b0P} to FA, where S1 = h(pHA-MU || RMU), S2 = RMU ⊕ , and S3 = h(RMU ⊕ h(pHA-MU || ) || b0P.x). After authenticating MU and FA successfully, HA sends {IDHA, c0P, S4, } to FA, where S4 = h(c0b0P.x || a0P.x || IDFA || IDHA || RMU || ). Parameters S1, S2, S3, and S4 contain MU’s specific information RMU and and are transmitted via public channels. Because RMU and will be updated in each session, it denotes that S1, S2, S3, and S4 in one session differ from those in other sessions. That is, no constant parameter is transmitted for MU in different sessions, and our scheme ensures user anonymity.
3.2. Resistance to Common Attacks
To show that the proposed authentication scheme can resist common attacks to ensure security, common attacks, man-in-the-middle attack, desynchronization attack, insider attack, replay attack, and offline secret key guessing attack are taken into consideration. These attacks are chosen for security analysis because of the following reasons. First, HA, MU, and FA transmit data via public channels. It is essential to protect all communication parties from being threatened by an attacker without being detected when the authentication scheme is in progress. This denotes that the proposed scheme has to resist man-in-the-middle attack. Second, in authentication and establishment of the session key phase of the proposed scheme, the random nonce RMU kept by HA will be updated to after MU is authenticated successfully, and MU will update W to Wnew = PWMU ⊕ and V to Vnew = ⊕ pHA-MU after MU is assured that . If only HA updates U to h(pHA-MU || ) and RMU to while W and V are not updated, MU may be regarded as an illegal user. That is, the proposed scheme has to resist desynchronization attacks to ensure that an authorized mobile user can access the service even when the new authentication parameters are modified by an attacker. Third, the proposed scheme has to resist insider attacks such that no one can impersonate a legal mobile user even when a malicious insider with privileges can access the home agent’s database. Forth, the proposed scheme has to resist replay attack such that no one can impersonate MU to cheat FA and HA by sending the intercepted data transmitted in previous sessions. Fifth, because the computational capacities of computers progress rapidly, an attacker can eavesdrop to get transmitted messages and analyze them offline. That is, an attacker may attempt to retrieve the secrets pHA-MU and pFA-HA by mounting an offline secret key guessing attack. The corresponding analysis is given as follows.
In authentication and establishment of the session key phase, an attacker may mount a man-in-the-middle attack by impersonating a communication party to establish the session key with another innocent communication party. First, we assume an attacker tries to impersonate MU and establish the session key with FA by modifying b0P. However, this approach will never succeed because MU computes S3 = h(RMU ⊕ h(pHA-MU || ) || b0P.x) for HA and HA verifies b0P by checking whether S3 = S′3. FA can also verify b0P by checking whether . On the other hand, if the attacker tries to impersonate FA and establish the session key with MU by modifying a0P, this approach will never succeed because HA can verify a0P by checking whether and MU can verify a0P by checking whether S4 = S′4. In the update session key phase, FA authenticates MU by checking if h1 = h′1 and MU authenticates FA by checking if h2 = h′2 Because of the above reasons, our scheme can resist man-in-the-middle attacks.
In the authentication and establishment of the session key phase, an attacker may attempt to mount a desynchronization attack by disturbing the authentication process after HA updates U to h(pHA-MU || ) and RMU to in its database. Although MU does not update W and V in his/her smart card, MU still can be authenticated by HA successfully because HA stores the original RMU and the original U. Because of the above reasons, our scheme can resist desynchronization attack.
Assume that a malicious insider with privileges tries to get MU’s private data in HA’s database to impersonate MU. In our proposed scheme, this attack cannot be mounted successfully because HA does not store a user’s password and his/her real identifier. No insider can obtain pMU and IDMU to compute MU’s secret PWMU, where PWMU = h(IDMU || pMU). Therefore, our scheme can resist insider attack.
In authentication and establishment of the session key phase, anyone can eavesdrop to intercept the transmitted data because the channel is public. In Step 3, MU sends {IDHA, S1, S2, S3, b0P} to FA and stores , where S1 = h(pHA-MU || RMU), S2 = RMU ⊕ , and S3 = h(RMU ⊕ h(pHA-MU || ) || b0P.x). In Step 10, FA sends {IDFA, S4, a0P, c0P, } to MU, where = h(h( || b0P.x)) = h(h(h(a0b0P.x) || b0P.x)). In Step 12, MU sends {} to FA, where = h(c0P.x || ). In Step 13, FA computes = h(c0P.x || ) and checks if = to determine whether MU is legal. After an attacker eavesdrops, he may use the intercepted data to cheat HA and FA to access services. However, the attacker cannot mount a reply attack successfully because of the following. = h(a0b0P.x) and = h(c0P.x || ) = h(c0P.x || h(a0b0P.x)). If the attacker wants to cheat, he has to obtain a0b0P. Although a0P and b0P are available, the attacker knows neither a0 nor b0 because of the difficulty of solving the elliptic curve discrete logarithm problem (ECDLP). As a result, the attacker cannot compute a0b0P to obtain . Since cannot be obtained by the attacker, he cannot be authenticated by FA successfully by retransmitting the intercepted data. Therefore, our scheme can resist replay attack.
In the authentication and establishment of the session key phase, HA authenticates FA by checking whether , and FA authenticates HA by checking whether , where = h(a0P.x || b0P.x || pFA-HA) and = h(c0a0P.x || b0P.x || pFA-HA). The secret pFA-HA shared between FA and HA is contained in both and . Although a0P, b0P and c0P are available, an attacker cannot compute c0a0P because of the difficulty of solving ECDLP. On the other hand, MU authenticates HA by checking whether S4 = S′4 and HA authenticates MU by checking whether S3 = S′3, where S4 = h(c0b0P.x || a0P.x || IDFA || IDHA || RMU || ) and S3 = h(RMU ⊕ h(pHA-MU || ) || b0P.x). The secret pHA-MU shared between MU and HA is contained in the transmitted parameters S1 and S3, where S1 = h(pHA-MU || RMU). If an attacker wants to obtain pHA-MU, he has to guess RMU at the same time. This makes retrieving pHA-MU hard. Because of the above, offline secret key guessing attacks cannot be mounted on the proposed scheme.
3.3. Local Password Change
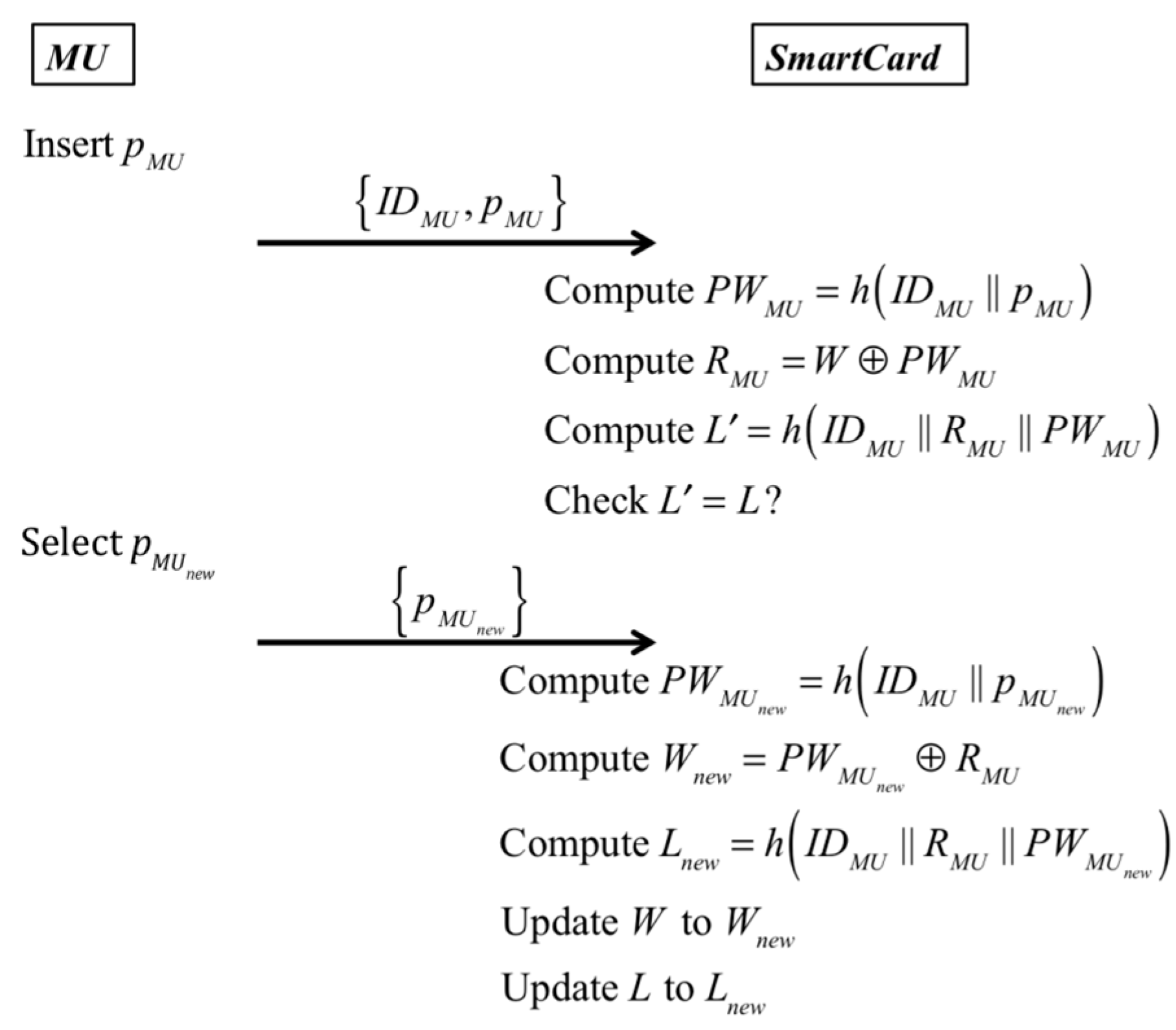
In our proposed scheme, MU can locally update his/her password. When MU wants to change his/her password PWMU to the new password , he/she does not need to connect to HA. This means a user can change his/her password at will.
3.4. Mutual Authentication
First, we make discussions on communication parties MU, FA and HA in authentication and establishment of the session key phase by the following three cases.
Case 1: Mutual authentication between FA and HA
HA authenticates FA by checking whether , and FA authenticates HA by checking whether , where = h(a0P.x || b0P.x || pFA-HA) and = h(c0a0P.x || b0P.x || pFA-HA). Because pFA-HA is only known to FA and HA, it denotes that only FA and HA can compute the correct parameters to be authenticated successfully. That is, our proposed scheme provides mutual authentication between FA and HA.
Case 2: Mutual authentication between MU and HA
MU authenticates HA by checking whether S4 = S′4, and HA authenticates MU by checking whether S3 = S′3, where S4 = h(c0b0P.x || a0P.x || IDFA || IDHA || RMU || ) and S3 = h(RMU ⊕ h(pHA-MU || ) || b0P.x). Only MU and HA can compute the correct parameters to be authenticated successfully because pHA-MU, and RMU are only known to MU and HA. As the result, our proposed scheme provides mutual authentication between MU and HA.
Case 3: Mutual authentication between MU and FA
In authentication and establishment of the session key phase, MU authenticates HA by checking if S4 = S′4, where S4 = h(c0b0P.x || a0P.x || IDFA || IDHA || RMU || ). Because only HA and MU know pHA-MU, and RMU, only HA can compute c0b0P and S4. If S4 = S′4, it denotes (1) a0P is valid because S4 contains a0P.x and (2) FA has been already authenticated by HA. Then, MU computes the session key = h(b0a0P.x), = h( || b0P.x), and = h() and checks if . If , it denotes that FA really knows = h(a0b0P.x). Because MU has already authenticated HA, MU is assured that only FA knows a0 to compute . As a result, FA is authenticated successfully by MU. Thereupon, MU computes = h(c0P.x || ) and sends it to FA. After obtaining {}, FA computes = h(c0P.x || ) and checks if . If , FA is assured that MU knows b0 to compute . FA has authenticated HA by checking if , where = h(c0a0P.x || b0P.x || pFA-HA). It denotes (1) b0P is valid because contains b0P.x and (2) MU has been already authenticated by HA. As a result, MU is authenticated successfully by FA. Therefore, our proposed scheme provides mutual authentication between MU and FA.
Second, we make discussions on communication parties MU and FA in the update session key phase. Because MU and FA have already shared the session key = h(aibiP.x) in the previous session, they can use and the stored data to authenticate each other. At the moment, FA stores {, aiP, biP, } and MU stores {, aiP, biP, }, where = h( || b0P.x) and = h(h( || b0P.x)) = h(). MU selects r bi+1, computes bi+1P and h1 = h(biP.x || bi+1P.x || ), and sends {bi+1P, , h1} to FA. After receiving {bi+1P, , h1}, FA checks if exists in its database, where = . Because it is hard to find the input of the hash function with a known hash value, this search approach protects MU from being traced even he stays in FA’s service domain and implies MU‘s legality. After finding the matched , FA extracts {, aiP, biP, } from its database and selects ai+1. FA computes h′1 = h(biP.x || bi+1P.x || ) and checks if h′1 = h1. If h′1 = h1, it denotes (1) MU indeed knows and (2) bi+1P is valid. FA authenticates MU successfully. Then, FA computes ai+1P, = h(ai+1bi+1P.x), = h(h( || bi+1P.x)) and h2 = h(). FA updates {, aiP, biP, } to {, ai+1P, bi+1P, } in its database and sends {ai+1P, h2} to MU. After receiving {ai+1P, h2}, MU computes = h(bi+1ai+1P.x), = h( || bi+1P.x), and h′2 = h(h() || ). Then, MU checks if h′2 = h2. If h′2 = h2, it denotes that FA indeed knows and . MU authenticates FA successfully. As a result, mutual authentication is ensured in update session key phase.
4. Further Discussions
In this section, we first make comparisons between the proposed scheme and the related works, and BAN logic is then used to deduce the completeness of the proposed authentication scheme.
4.1. Comparisons
In the following, we present a discussion of the properties of the proposed scheme and the related works. The term “Local password change” denotes whether the mobile user can locally change his password without the home agent’s help in the corresponding scheme. The term “Anonymity” denotes whether the corresponding scheme can ensure user anonymity. The term “Insider attack resistance” denotes whether the corresponding scheme can resist insider attack. The term “Man-in-the-middle attack resistance” denotes whether the corresponding scheme can resist man-in-the-middle attack. The term “The synchronization problem resistance” denotes whether the corresponding scheme can resist the synchronization problem. “Replay attack resistance” denotes whether the corresponding scheme can resist replay attack. The comparisons between our scheme and the related works are given in
Table 2. According to the comparisons, it is assured that our scheme can resist common attacks and ensure security and convenience at the same time while others cannot.
4.2. BAN Logic-Based Authentication Proof
In the following, BAN logic is used to deduce the completeness of the proposed authentication scheme. Notations used in BAN logic are listed in
Table 3.
Fundamental rules for BAN logic analysis are listed as follows:
RBL1 (Message Meaning Rule 1): .
RBL2 (Message Meaning Rule 2): .
RBL3 (Nonce Verification Rule): .
RBL4 (Jurisdiction Rule): .
RBL5 (Freshness Conjunction Rule): .
RBL6 (Belief Rule): .
RBL7 (Session Key Rule): .
The following goals must be satisfied by using the above rules to ensure the security of the proposed authentication scheme under BAN logic.
- Goal 1:
.
- Goal 2:
.
- Goal 3:
.
- Goal 4:
.
- Goal 5:
.
- Goal 6:
.
- Goal 7:
.
- Goal 8:
.
- Goal 9:
.
- Goal 10:
.
- Goal 11:
.
- Goal 12:
.
Idealized transformation of the proposed scheme is as follows:
IM1:
MU →
FA:
IDHA,
S1,
S2,
S3,
b0P:
IM2:
FA →
HA:
IDFA,
S1,
S2,
S3,
a0P,
b0P,
:
IM3: HA → FA:
IDHA,
c0P,
S4,
:
IM4: FA → MU:
IDFA,
S4,
a0P,
c0P,
:
To evaluate the proposed scheme, assumptions regarding the preliminary state are shown as follows:
- A1:
.
- A2:
.
- A3:
.
- A4:
.
- A5:
.
- A6:
.
- A7:
.
- A8:
.
- A9:
.
- A10:
.
- A11:
.
- A12:
.
- A13:
.
Considering IM1 and IM2 of the idealized forms:
IM1:
MU →
FA:
IDHA,
S1,
S2,
S3,
b0P:
IM2:
FA →
HA:
IDFA,
S1,
S2,
S3,
a0P,
b0P,
:
By applying seeing rule, we have
S1:
FAIDHA,
S1,
S2,
S3,
b0P:
S2:
HAIDFA,
S1,
S2,
S3,
a0P,
b0P,
:
By S2, A2, and RBL1, we have
| S3: | {h(pHA-MU || RMU),, , b0P}. | |
By S3, A5, A8, RBL3, RBL4, and RBL7, we have
| S4: | . | Goal 1 |
By S4, A7, A12, and RBL4, we have
| S5: | . | Goal 2 |
By S2, A4, and RBL2, we have
| S6: | {IDFA, a0P, }. | |
By S6, A6, A11, RBL3, RBL4, and RBL7, we have
| S7: | | Goal 5 |
By S7, A7, A13, and RBL4, we have
| S8: | . | Goal 6 |
Considering IM3 of the idealized form:
IM3: HA → FA:
IDHA,
c0P,
S4,
:
By applying seeing rule, we have
S9:
FAIDHA,
c0P,
S4,
:
By S9, A3, A7, A13, RBL2, RBL3, RBL4, and RBL7, we have
| S10: | {IDHA, c0P, }, |
| S11: | , | Goal 7 |
| S12: | , and | Goal 8 |
| S13: | . |
By S13, A5, and A9, we have
| S14: | and | Goal 11 |
| S15: | | Goal 12 |
Considering IM4 of the idealized form:
IM4: FA → MU:
IDFA,
S4,
a0P,
c0P,
:
By applying seeing rule, we have
S16:
MUIDFA,
S4,
a0P,
c0P,
:
By S16, A1, and RBL1, we have
| S17: | {, a0P, c0P}. | |
By S17, A7, A12, RBL3, RBL4, and RBL7, we have
| S18: | and | Goal 3 |
| S19: | . | Goal 4 |
By S16, A6, A10, RBL3, RBL4, and RBL7, we have
| S20: | and | Goal 9 |
| S21: | . | Goal 10 |
The above BAN logic analysis formally proves the authentication process has any two of MU, FA, and HA authenticate each other and the shared secrets are established as claimed.