A Survey of Public Key Infrastructure-Based Security for Mobile Communication Systems
Abstract
:1. Introduction
Motivations
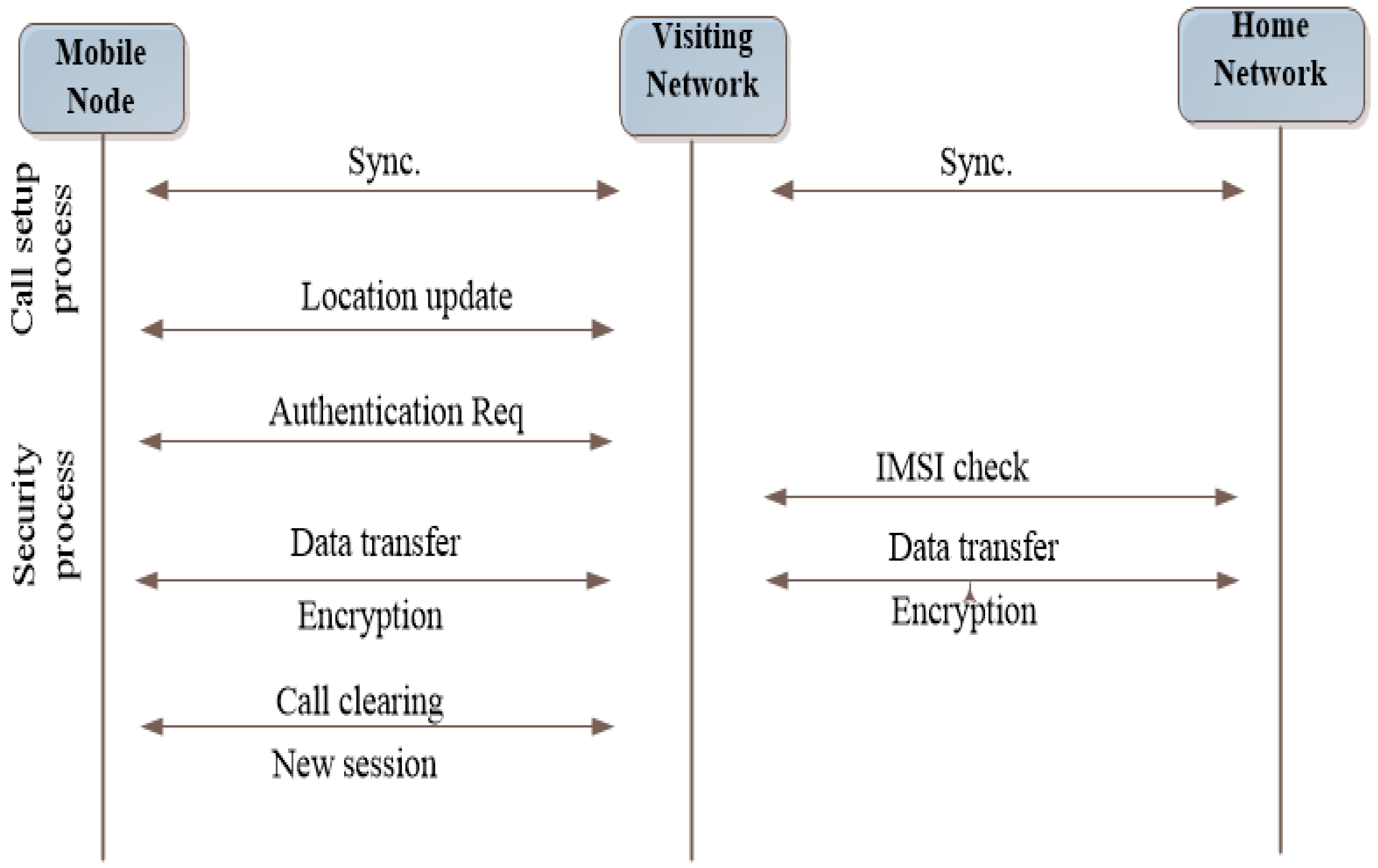
2. Mobile Communications Security Issues
2.1. 2G-GSM Security
2.2. 3G-CDMA Security
2.3. 4G-LTE Security
- Network access security: use of universal subscriber identity module (USIM) to provide secure access for a user to the evolved packet system (EPS). Includes mutual authentication and privacy features.
- Network domain security: refers to features that allow for secure communications between Evolved Packet System/Evolved Packet Core (EPS/EPC) nodes in order to protect against attacks on the network.
- User domain security: securing access to the terminal, e.g., screen lock password, or personal identification number (PIN) to enable USIM usage.
- Application domain security: security features used by applications, e.g., hypertext transfer protocol (HTTP).
- Visibility and configurability of security: features to allow a user to know whether a security feature is in operation or not, and user-configured control over whether use of a service depends on enabled security features.
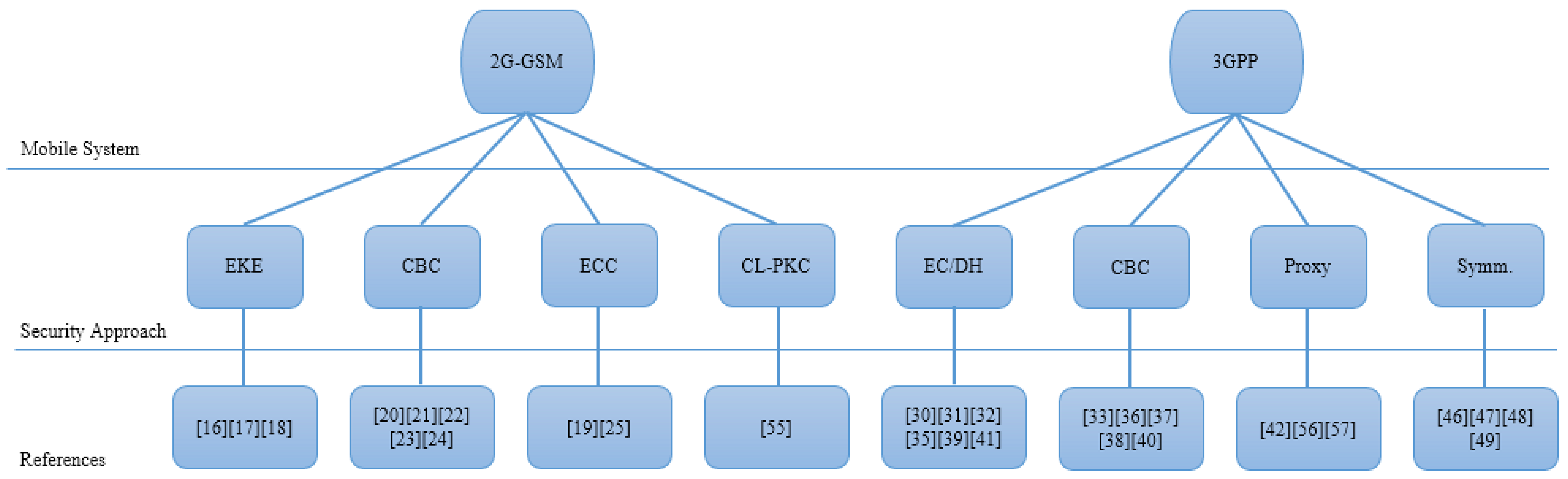
3. A Survey of the Literature
3.1. Review of PKI-Based Security for 2G-GSM Systems
3.2. Review of PKI-Based Security for 3GPP Systems
3.3. Review of Symmetric-Key Based Security for Mobile Systems
4. Security Requirements and Performance Analysis
5. New Research Directions and Challenges
5.1. Standalone Security System
5.2. Using Secure Algorithms
5.3. Using End-to-End Security and Reducing Trust on Third Party
5.4. Using Lightweight Cryptosystems
6. Conclusions
Conflicts of Interest
References
- Mitchell, C.J. Security for Mobility; Institute of Electrical Engineers: London, UK, 2004. [Google Scholar]
- 3GPP TS 33.120 (4.0.0), 3G Security: Security Principles and Objectives; Release 4; 3GPP Organizational Partners: Valbonne, France, 2001.
- Liang, X.H.; Lu, R.X.; Chen, L.; Lin, X.D.; Shen, X.M. PEC: A privacy preserving emergency call scheme for mobile healthcare social networks. J. Commun. Netw. 2011, 13, 102–112. [Google Scholar] [CrossRef]
- 3GPP TS 21.133, 3GPP: Technical Specification Group Services and System Aspects; 3G Security; Security Threats and Requirements; 3GPP Organizational Partners: Valbonne, France, 2001.
- Millan, W. Cryptanalysis of the alleged CAVE algorithm. In Proceedings of the 1st International Conference on Information Security and Cryptology (ICSCI ’98), Seoul, Korea, 18–19 December 1998; pp. 107–119.
- Lauri, P. GSM Interception; Lecture Notes; Helsinki University of Technology: Helsinki, Finland, 1999. [Google Scholar]
- Wagner, D.; Schneier, B.; Kelsey, J. Cryptanalysis of the cellular message encryption algorithm. In Proceedings of the 17th international conference on cryptology (Crypto’97), Santa Barbara, CA, USA, 17–21 August 1997.
- 3GPP Technical Specification: 3GPP TS 33.102, V5.3.0, Third Generation Partnership Project; Technical Specifications Group Services and System Aspects; 3G Security; Security Architecture; 3GPP Organizational Partners: Valbonne, France, 2002.
- 3GPP Technical Report: 3GPP TR 31.900, V5.3.0. Third Generation Partnership Project; SIM/USIM Internal and External Interworking Aspects; ETSI 3rd Generation Partnership Project (3GPP); 3GPP Organizational Partners: Valbonne, France, 2006.
- 3GPP Technical Specification: 3GPP TS 33.200 version 6.1.0 Release 6, Third Generation Partnership Project; Universal Mobile Telecommunications System (UMTS); 3G Security; Network Domain Security (NDS); Mobile Application Part (MAP) application layer security; ETSI 3rd Generation Partnership Project (3GPP); 3GPP Organizational Partners: Valbonne, France, March 2005.
- Meyer, U.; Wetzel, S. A Man-in-the-Middle Attack on UMTS. In Proceedings of the 3rd ACM Workshop on Wireless Security, Philadelphia, PA, USA, 1 October 2004; pp. 90–97.
- Zhang, M.; Fang, Y. Security analysis and enhancements of 3GPP authentication and key agreement protocol. IEEE Trans. Wirel. Commun. 2005, 4, 734–742. [Google Scholar] [CrossRef]
- Tang, C.; Wu, D.O. An efficient mobile authentication scheme for wireless networks. IEEE Trans. Wirel. Commun. 2008, 7, 1408–1416. [Google Scholar] [CrossRef]
- 3rd Generation Partnership Project; Technical Specification Group Service and System Aspects; 3GPP System Architecture Evolution (SAE); Security Architecture (Rel 12) 3GPP TS 33.401 V12.5.0; 3GPP Organizational Partners: Valbonne, France, 2012.
- 3GPP EPS/EPC Security Architecture; 3GPP TS 33.401, System Architecture Evolution (SAE)-Security architecture EPS (EPC and E-UTRAN) Security Architecture; 3GPP Organizational Partners: Valbonne, France, 2008.
- Zhu, F.; Wong, D.S.; Chan, A.H.; Ye, R. Password authenticated key exchange based on RSA for imbalanced wireless networks. In Proceedings of the 5th International Conference on Information Security, London, UK, 12–13 September 2002; Springer-Verlag: Berlin/Heidelberg, Germany, 2002; pp. 150–161. [Google Scholar]
- Gong, L.; Lomas, T.M.A.; Needham, R.M.; Saltzer, J.H. Protecting poorly chosen secrets from guessing attacks. IEEE J. Sel. Areas Commun. 1993, 11, 648–656. [Google Scholar] [CrossRef]
- Aydemir, O.; Selcuk, A.A. A strong user authentication protocol for GSM. In Proceedings of the 14th IEEE International Workshop on Enabling Technologies Infrastructure for Collaborative Enterprise (WETICE’05), Linkopings, Sweden, 13–15 June 2005.
- Ammayappan, K.; Saxena, A.; Negi, A. Mutual authentication and key agreement based on elliptic curve cryptography for GSM. In Proceedings of the 14th International Conference on Advanced Computing and Communications (ADCOM), Mangalore, India, 20–23 December 2006; pp. 183–186.
- Lee, C.C.; Hwang, M.S.; Yang, W.P. Extension of authentication protocol for GSM. IEE Proc. Commun. 2003, 150, 91–95. [Google Scholar] [CrossRef]
- Chang, C.C.; Lee, J.S.; Chang, Y.F. Efficient authentication protocols of GSM. Comput. Commun. 2005, 28, 921–928. [Google Scholar] [CrossRef]
- Al-Tawil, K.; Akram, A.; Youssef, H. A new authentication protocol for GSM networks. In Proceedings of the IEEE 23rd Annual Conference on Local Computer Networks (LCN’98), Washington, DC, USA, 11–14 October 1998; pp. 21–30.
- Lin, W.D.; Jan, J.K. A wireless-based authentication and anonymous channels for large scale area. In Proceedings of the Sixth IEEE Symposium on Computers and Communications (ISCC’01), Hammamet, Tunisia, 3–5 July 2001; pp. 36–41.
- Alberto, P. Privacy and authentication protocol providing anonymous channels in GSM. Comput. Commun. 2004, 27, 1709–1715. [Google Scholar]
- El Zouka, H.A. Providing end-to-end secure communicationsin gsm networks. Int. J. Netw. Secur. Its Appl. IJNSA 2015, 7. [Google Scholar] [CrossRef]
- Lescuyer, P.; Lucidarme, T. Evolved Packet System (EPS): The LTE and SAE Evolution of 3G; John Wiley & Sons: New York, NY, USA, 2008. [Google Scholar]
- Third Generation Partnership Project (3GPP), 3GPP TS 33.102 v8.0.0. 3G Security: Security Architecture; Release 8; 3GPP Organizational Partners: Valbonne, France, 2008.
- Third Generation Partnership Project (3GPP), 3GPP TS 33.401 v8.1.1 3G System Architecture Evolution (SAE): Security Architecture; Release 8; 3GPP Organizational Partners: Valbonne, France, 2008.
- Third Generation Partnership Project (3GPP), 3GPP TS 33.821 v1.0.0. Rationale and Track of Security Decisions in Long Term Evolved (LTE) RAN/3GPP System Architecture Evolution (SAE); Release 8; 3GPP Organizational Partners: Valbonne, France, 2007.
- Sandhya, P.; Poovizhi, S.; Varun, R. SHA-based mutual authentication in long term evolution using hyper elliptic curve cryptography. Int. J. Emerg. Sci. Eng. (IJESE) 2013, 1, 54–55. [Google Scholar]
- Gódor, G.; Imre, S. Novel authentication algorithm-public key based cryptography in mobile phone systems. IJCSNS Int. J. Comput. Sci. Netw. Secur. 2006, 6, 126–134. [Google Scholar]
- Mun, H.; Han, K.; Kim, K. 3G-WLAN Interworking: Security analysis and new authentication and key agreement based on EAP-AKA. In Proceedings of the IEEE Wireless Telecommunications Symposium WTS, Prague, Czech Republic, 22–24 April 2009; pp. 1–8.
- Kambourakis, G.; Rouskas, A.; Gritzalis, S. Performance evaluation of public key-based authentication in future mobile communication systems. EURASIP J. Wirel. Commun. Netw. 2004, 1, 184–197. [Google Scholar] [CrossRef]
- Zheng, Y.; He, D.; Tang, X.; Wang, H. AKA and authorization scheme for 4G mobile networks based on trusted mobile platform. In Proceedings of the 2005 Fifth International Conference on Information, Communications and Signal Processing, Bangkok, Thailand, 6–9 December 2005; pp. 976–980.
- Xu, J.; Zhu, W.; Feng, D. An efficient mutual authentication and key agreement protocol preserving user anonymity in mobile networks. Comput. Commun. 2011, 34, 319–325. [Google Scholar] [CrossRef]
- Lee, C.C.; Hwang, M.S. Security enhancement on a new authentication scheme with anonymity for wireless environments. IEEE Trans. Indus. Electron. 2006, 53, 1683–1686. [Google Scholar] [CrossRef]
- Zhu, J.; Ma, J. A new authentication scheme with anonymity for wireless environments. IEEE Trans. Consum. Electron. 2004, 50, 230–234. [Google Scholar]
- Haddad, Z.J.; Taha, S.; Ismail, I.A.S. SEPS-AKA: A secure evolved packet system authentication and key agreement scheme for LTE-A networks. Comput. Sci. Inf. Technol. 2014, 58, 57–70. [Google Scholar]
- Abdo, J.B.; Demerjian, J.; Chaouchi, H.; Pujolle, G. EC-AKA2 a revolutionary aka protocol. In Proceedings of the 2013 International Conference on Computer Applications Technology (ICCAT), Sousse, Tunisia, 20–22 January 2013; pp. 1–6.
- Abdo, J.B.; Demerjian, J.; Ahmad, K.; Chaouchi, H.; Pujolle, G. EPS mutual authentication and crypt-analyzing SP-AKA. In Proceedings of the 2013 International Conference on Computing, Management and Telecommunications (ComManTel), Ho Chi Minh City, Vietnam, 21–24 January 2013; pp. 303–308.
- Lai, C.; Li, H.; Lu, R.; Shen, X.S. SE-AKA: A secure and efficient group authentication and key agreement protocol for LTE networks. Comput. Netw. 2013, 57, 3492–3510. [Google Scholar] [CrossRef]
- Jing, Q.; Zhang, Y.; Fu, A.; Liu, X. A privacy preserving handover authentication scheme for EAP-based wireless networks. In Proceedings of the 2011 IEEE Global Telecommunications Conference (GLOBECOM 2011), Houston, TX, USA, 5–9 December 2011; pp. 1–6.
- Kim, Y.; Ren, W.; Jo, J.; Yang, M.; Jiang, Y.; Zheng, J. SFRIC: A secure Fast roaming scheme in wireless LAN using ID-based cryptography. In Proceedings of the 2007 IEEE International Conference on Communications ICC, Glasgow, Scotland, 24–28 June 2007; pp. 1570–1575.
- Choi, J.; Jung, S. A Handover authentication using credentials based on chameleon hashing. IEEE Commun. Lett. 2010, 14, 54–56. [Google Scholar] [CrossRef]
- Cao, J.; Li, H.; Ma, M.; Zhang, Y.; Lai, C. A simple and robust handover authentication between HeNB and eNB in LTE networks. Comput. Netw. 2012, 56, 2119–2131. [Google Scholar] [CrossRef]
- Chang, C.C.; Lee, C.Y.; Chiu, Y.C. Enhance authentication scheme with anonymity for roaming service in global mobility networks. Comput. Commun. 2009, 32, 611–618. [Google Scholar] [CrossRef]
- He, D.; Ma, M.; Zhang, Y.; Chen, C. A strong user authentication scheme with smart cards for wireless communications. Comput. Commun. 2011, 34, 367–374. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. Lightweight and energy efficient mutual authentication and key agreement scheme with user anonymity for secure communication in global mobility networks. IEEE Syst. J. 2015. [Google Scholar] [CrossRef]
- Gope, P.; Hwang, T. An efficient mutual authentication and key agreement scheme preserving strong anonymity of the mobile user in global mobility networks. J. Netw. Comput. Appl. 2016, 62, 1–8. [Google Scholar] [CrossRef]
- Zhang, Y.; Chen, X.; Li, J.; Li, H. Generic construction for secure and efficient handoff authentication schemes in EAP-based wireless networks. Comput. Netw. 2014, 75, 192–211. [Google Scholar] [CrossRef]
- Huang, Y.; Shen, C.; Shieh, S.W. S-AKA: A provable and secure authentication key agreement protocol for UMTS networks. IEEE Trans. Veh. Technol. 2011, 60, 4509–4519. [Google Scholar] [CrossRef]
- Park, C. Authentication protocol providing user anonymity and untraceability in wireless mobile communication systems. Comput. Netw. 2004, 44, 319–333. [Google Scholar] [CrossRef]
- Palekar, A.; Simon, D.; Josefsson, S.; Zhou, H.; Zorn, G. Protected EAP Protocol (PEAP) Version 2, IETF, October 2004. Available online: https://www.ietf.org/archive/id/draft-josefsson-pppext-eap-tls-eap-10.txt (accessed on 24 August 2016).
- Han, L. A Threat Analysis of the Extensible Authentication Protocol; Honors Project Report; Carleton University: Ottawa, ON, Canada, 2006. [Google Scholar]
- Ramadan, M.; Li, F.; Xu, C.X.; Abdalla, A.; Abdalla, H. An efficient end-to-end mutual authentication scheme for 2G-GSM system. In Proceedings of the 2016 IEEE International Conference on Big Data Analysis (ICBDA 2016), Hangzhou, China, 12–14 March 2016; pp. 1–6.
- Ramadan, M.; Li, F.; Xu, C.X.; Oteng, K.; Ibrahim, H. Authentication and key agreement scheme for CDMA cellular system. In Proceedings of the 2015 IEEE International Conference on Communication Software and Networks (ICCSN), Chengdu, China, 6–7 June 2015; pp. 118–124.
- Ramadan, M.; Li, F.; Xu, C.X.; Mohamed, A.; Abdalla, H.; Abdalla, A. User-to-user mutual authentication and key agreement scheme for LTE cellular system. Int. J. Netw. Secur. 2016, 18, 769–781. [Google Scholar]
- D’Orazio, C.J.; Choo, K.R.; Yang, L.T. Data exfiltration from internet of things devices: iOS devices as case studies. IEEE Internet Things J. 2016. [Google Scholar] [CrossRef]
- Hwang, T.; Gope, P. Provably secure mutual authentication and key exchange scheme for expeditious mobile communication through synchronously one-time secrets. Wirel. Pers. Commun. 2014, 77, 197–224. [Google Scholar] [CrossRef]
- D’Orazio, C.; Ariffin, A.; Choo, K.R. iOS anti-forensics: How can we securely conceal, delete and insert data? In Proceedings of the 2014 47th Hawaii International Conference on System Science, Waikoloa, HI, USA, 6–9 January 2014.
- Do, Q.; Martini, B.; Choo, K.R. Is the data on your wearable device secure? An android wear smartwatch case study. In Software: Practice and Experience (Softw. Pract. Exper.); Wiley Online Library: New York, NY, USA, 2016. [Google Scholar]
- Do, Q.; Martini, B.; Choo, K.R. A forensically sound adversary model for mobile devices. PLoS ONE 2015, 10, e0138449. [Google Scholar] [CrossRef] [PubMed]
- Azfar, A.; Choo, K.R.; Liu, L. Android mobile VoIP apps: A survey and examination of their security and privacy. Electron. Commer. Res. 2016, 16, 73–111. [Google Scholar] [CrossRef]
- He, D.; Chen, J. An efficient certificate-less designated verifier signature scheme. Int. Arab J. Inf. Technol. 2013, 10, 389–396. [Google Scholar]
- Hea, D.; Chen, J.; Zhang, R. An efficient identity-based blind signature scheme without bilinear pairings. Comput. Electr. Eng. 2011, 37, 444–450. [Google Scholar] [CrossRef]
- Scott, M. MIRACLE-Multiprecision Integer and Rational Arithmetic C/C++ Library; Shamus Software Ltd.: Dublin, Ireland, 2003. [Google Scholar]
- Ramadan, M.; Du, G.; Li, F.; Xu, C.X. EEE-GSM: End-to-End Encryption Scheme over GSM System. Int. J. Secur. Appl. 2016, 10, 229–240, ISSN:1738-9976 IJSIA. [Google Scholar] [CrossRef]
- Al-Riyami, S.; Paterson, G. Certificateless public key cryptography. In Advances in Cryptology-ASIACRYPT; Springer: Berlin/Heidelberg, Germany, 2003; pp. 452–473. [Google Scholar]
- Lee, S.; Kim, Y.; Han, J.; Lee, D. Protection method for data communication between ADS-B sensor and next-generation air traffic control systems. Information 2014, 5, 622–633. [Google Scholar] [CrossRef]
- Yang, C.; Sun, Y.; Wu, Q. Batch attribute-based encryption for secure clouds. Information 2015, 6, 704–718. [Google Scholar] [CrossRef]
| Reference | Security Technique | Mutual Authentication | Replay Attack | MITM Attack | TTP | End-to-End Security |
|---|---|---|---|---|---|---|
| [16] | RSA-EKE | No | No | No | No | No |
| [17] | PKI-EKE | No | Yes | No | Yes | No |
| [18] | PKI-EKE | No | Yes | Yes | Yes | No |
| [19] | ECC | No | Yes | No | Yes | No |
| [20] | CBC | Yes | Yes | No | Yes | No |
| [21] | CBC | Yes | Yes | Yes | Yes | No |
| [24] | CBC | Yes | Yes | No | No | No |
| [25] | ECC | No | No | Yes | No | Yes |
| [55] | CL-PKC | Yes | Yes | Yes | No | Yes |
| Reference | Security Technique | Mutual Authentication | Replay Attack | MITM Attack | TTP | End-to-End Security |
|---|---|---|---|---|---|---|
| [30] | Hyper ECC | Yes | No | Yes | No | Yes |
| [32] | ECC-DH | Yes | Yes | Yes | No | No |
| [33] | SSL | No | No | Yes | Yes | No |
| [34] | CBC-TMP | Yes | Yes | Yes | Yes | No |
| [35] | DH | Yes | No | Yes | No | No |
| [36] | CBC | Yes | Yes | No | Yes | No |
| [37] | CBC | No | Yes | Yes | Yes | No |
| [38] | RSA | Yes | No | No | Yes | No |
| [41] | ECC-DH | Yes | Yes | Yes | Yes | No |
| [42] | Proxy | Yes | No | Yes | No | Yes |
| [56] | Pairing | Yes | Yes | Yes | Yes | No |
| [57] | Proxy | Yes | Yes | Yes | No | Yes |
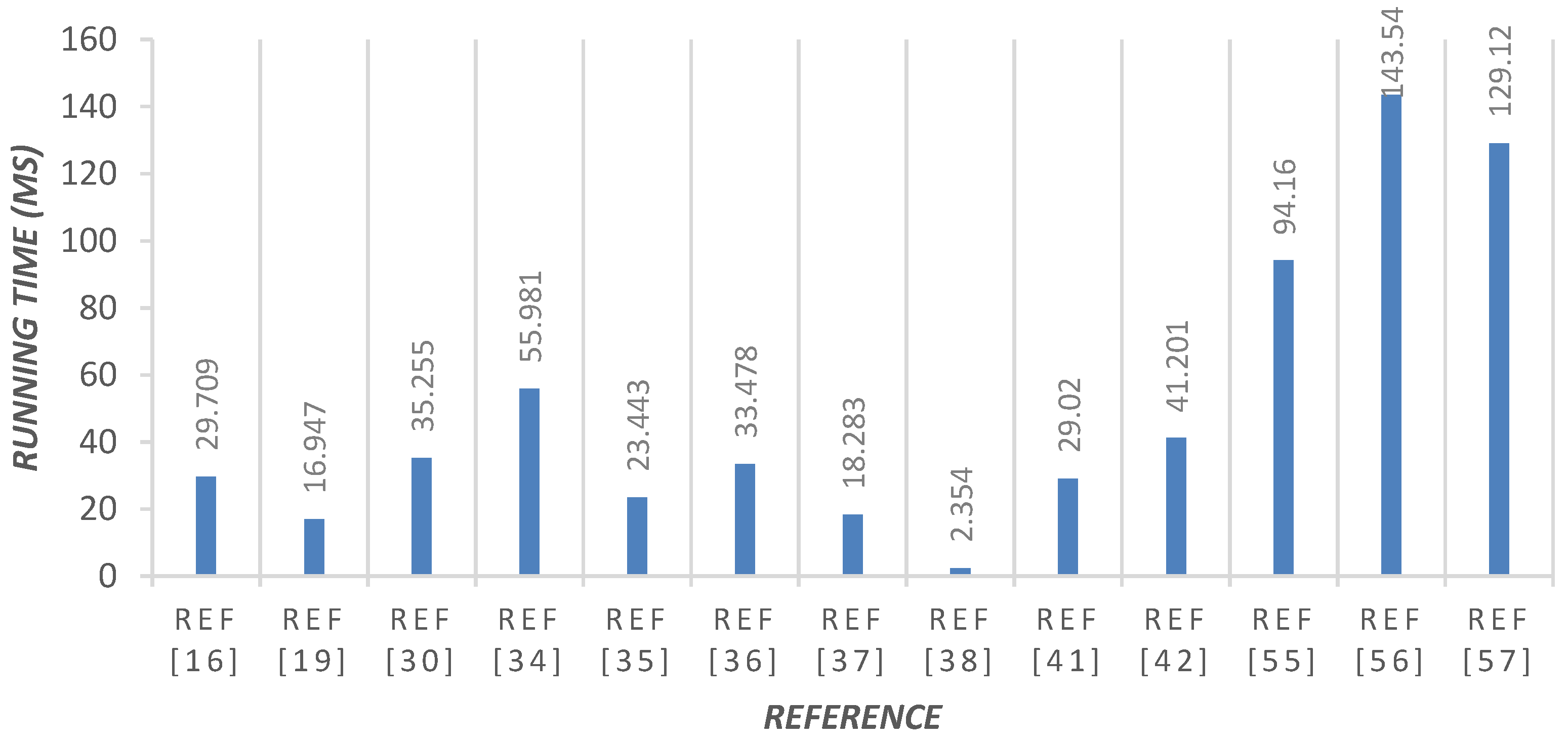
| Reference | No. of Phases | Computational Cost | Total Running Time (ms) | Comment |
|---|---|---|---|---|
| [16] | 4 | 2Td + 9Th + 2Ts | 29.709 | Middle |
| [19] | 3 | 4Te + 4Th + 5Ts | 16.947 | Low |
| [30] | 4 | 4Te + 2Th + 5Td + Tp | 35.255 | Middle |
| [34] | 5 | Td + 18Th + 17Ts | 55.981 | High |
| [35] | 3 | 7Td + 5Th + 11Ts | 23.443 | Middle |
| [36] | 3 | 11Th + 7Ts | 33.478 | Middle |
| [37] | 3 | 6Th + 8Ts | 18.283 | Low |
| [38] | 4 | 2Td + 3Ts | 2.354 | Low |
| [41] | 8 | 2Te + 9Th | 29.020 | Middle |
| [42] | 2 | 13Te + 10Th + 2Ts | 41.201 | Middle |
| [55] | 4 | 2Te + 2Th + Tm + 4Tp | 94.16 | High |
| [56] | 6 | 9Tm + 2Th + 4Tp | 143.540 | High |
| [57] | 3 | 5Te + 4Th + 2Tm + 5Tp | 129.120 | High |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ramadan, M.; Du, G.; Li, F.; Xu, C. A Survey of Public Key Infrastructure-Based Security for Mobile Communication Systems. Symmetry 2016, 8, 85. https://doi.org/10.3390/sym8090085
Ramadan M, Du G, Li F, Xu C. A Survey of Public Key Infrastructure-Based Security for Mobile Communication Systems. Symmetry. 2016; 8(9):85. https://doi.org/10.3390/sym8090085
Chicago/Turabian StyleRamadan, Mohammed, Guohong Du, Fagen Li, and Chunxiang Xu. 2016. "A Survey of Public Key Infrastructure-Based Security for Mobile Communication Systems" Symmetry 8, no. 9: 85. https://doi.org/10.3390/sym8090085
APA StyleRamadan, M., Du, G., Li, F., & Xu, C. (2016). A Survey of Public Key Infrastructure-Based Security for Mobile Communication Systems. Symmetry, 8(9), 85. https://doi.org/10.3390/sym8090085





