Formal Analysis of EAP-TLS Protocol Based on Logic of Events
Abstract
1. Introduction
- We propose a novel method for the formal analysis of the EAP-TLS protocol based on extended LoET, identifying potential man-in-the-middle attack paths and introducing an improved strategy using hash merging, encryption, and signatures, with feasibility validated through communication cost analysis.
- The present study extends the Logic of Events Theory by expanding five event classes, i.e., , , , , and , by defining corresponding event rules. At the same time, the causal axioms in the axiom system were extended, and new axioms were introduced.
- The extended Logic of Events Theory was used to construct a formal model of the EAP-TLS protocol and applied to formally verify the protocol model, ensuring that the improved protocol satisfies strong mutual authentication. The time complexity of this research method is O(n2). In terms of time complexity and ability to resist state explosion, it is better than related research methods.
2. Related Work
2.1. Deployment and Optimization Efforts
2.2. Formal Security Verification Work
2.3. Adjust the EAP-TLS Protocol for Specific Industry Scenarios
2.4. Comparison of Analysis Methods for EAP-TLS Protocol
3. Logic of Events Theory
3.1. Basic Symbols and Event Classes
3.2. Axiom System
3.2.1. Honest Axiom
3.2.2. Key Axiom
3.2.3. Causal Axioms
3.3. Verification Rules
3.3.1. Freshness Rule
3.3.2. FirstSend Rule
3.3.3. RuleF Rule
3.4. Protocol Definition
3.5. Strong Authentication
3.6. Proof Procedure
3.7. Limitations of the Logic of Events Theory
4. Extension of the Logic of Events Theory (LoET)
4.1. Extension of Event Classes and Associated Rules
4.1.1. Definition of the Event Class
4.1.2. Definition of the Event Class
4.1.3. Definition of the Event Class
4.1.4. Definition of the Event Class
4.1.5. Definition of the Event Class
4.2. Extension of Axiom System
4.2.1. Definition of the
4.2.2. Definition of the Non-Derivability Axiom
4.2.3. Extension of the Causal Axioms
5. Formal Analysis of the EAP-TLS Protocol
5.1. Introduction to the Protocol Model
5.2. Verification of Strong Authentication of the Protocol Based on the Logic of Events Theory
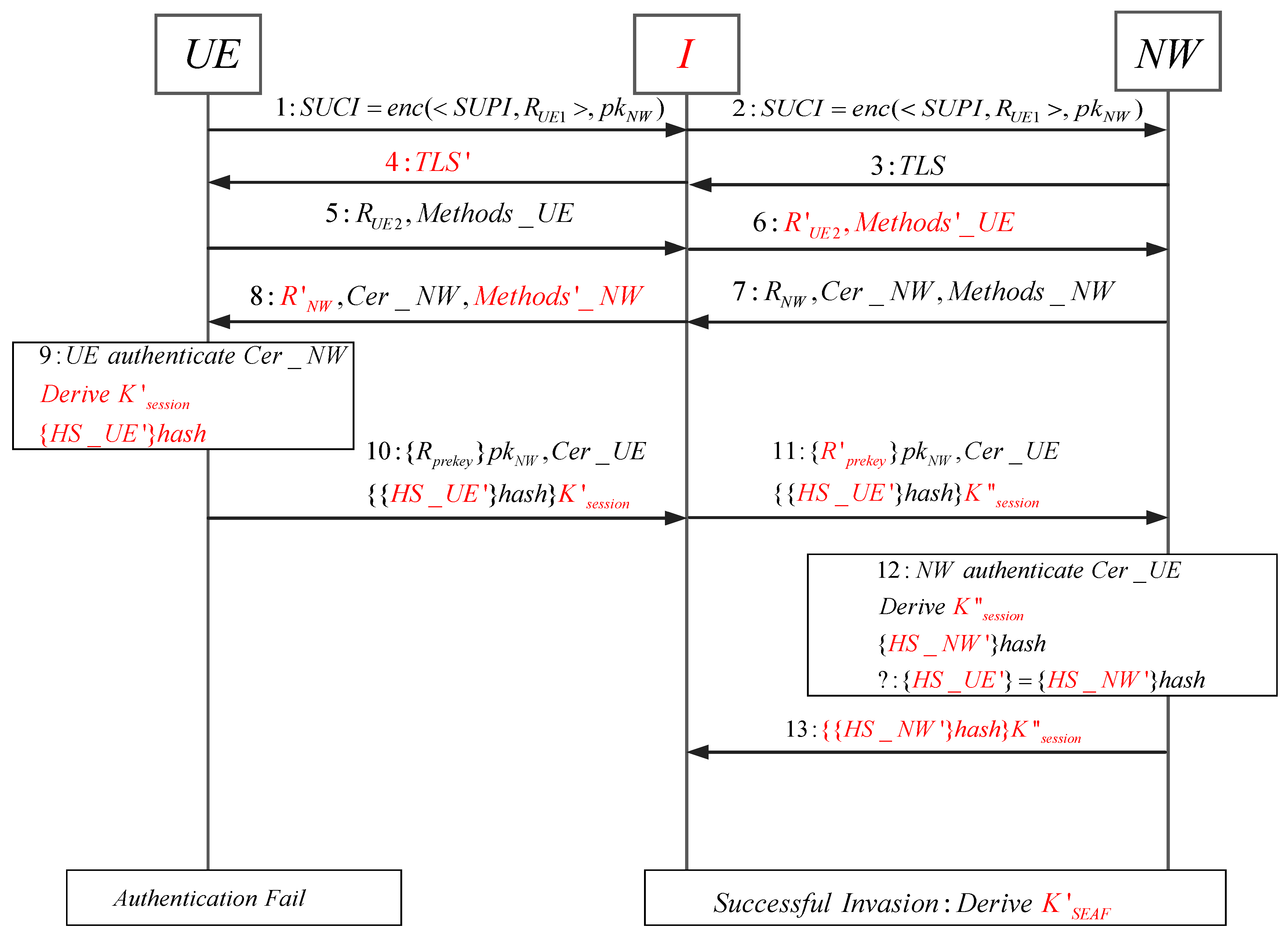
5.3. Protocol Attack Path
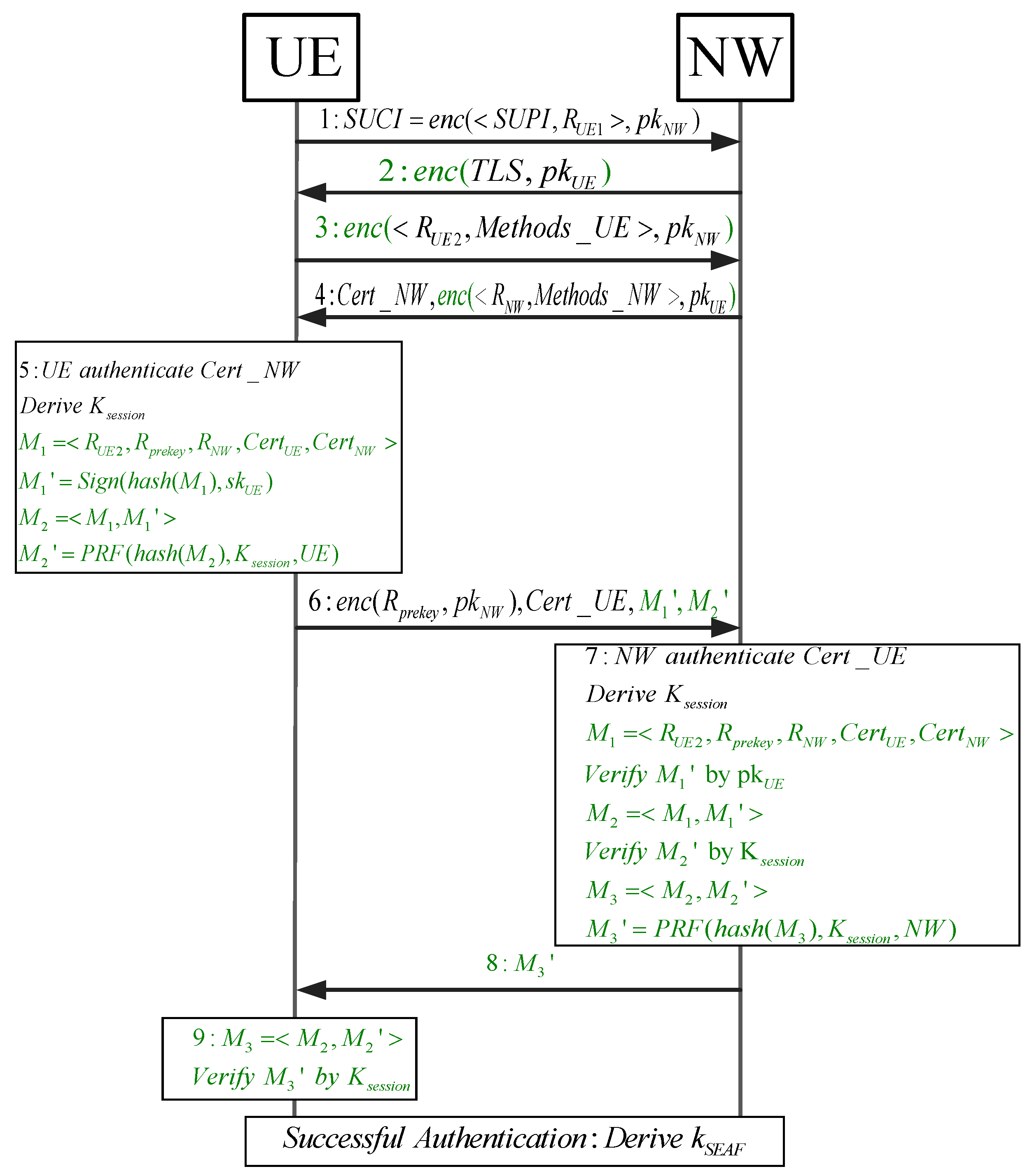
5.4. Protocol Improvement Strategy
6. Formal Analysis of the Improved EAP-TLS Protocol
6.1. Proof of Strong Authentication for EAP-TLS
6.2. Evaluation and Discussion
7. Conclusions and Future Work
- The present study proposes a new formal analysis method of the EAP-TLS protocol based on LoET. This approach formally analyzes the traditional EAP-TLS protocol, identifies the man-in-the-middle attack path in the protocol, and puts forward the enhanced strategy to mitigate the vulnerabilities through hash merging, encryption, and signature methods, alongside analyzing their communication costs to ensure feasibility.
- The five event classes , , , , and are extended, and the corresponding rules of the event classes are formulated. The causal axioms in the axiom system are extended. Through the extended Logic of Events Theory, the EAP-TLS protocol can be better formally modeled and analyzed, which improves the application scope of the Logic of Events Theory and the ability of formal analysis of security protocols.
- Due to the complexity of the handshake process of the EAP-TLS protocol, the existing LoET has difficulty in formally modeling this transport layer protocol. Through the extended LoET, the improved EAP-TLS protocol is formally modeled to determine the basic sequence and find the matching sessions and event sequences. It has been proved that the improved EAP-TLS protocol satisfies strong authentication, ensuring that the improved strategy is feasible. The time complexity of this research method is O(n2). In terms of time complexity and ability to resist state explosion, it is better than related research methods.
- This research method has significant advantages in terms of time complexity and resistance to state explosion and can perform pruning operations by eliminating events that are unlikely to have causal relationships, thereby accelerating the verification efficiency. Although this research method is more efficient in verifying complex protocols than traditional verification tools, it requires researchers to have a certain logical reasoning ability and a large knowledge reserve of LoET.
- Currently, the development of automatic verification tools is rapid. An important task in the future is to combine the LoET method proposed in this paper with the automatic verification tool Tamarin. Tamarin is an automatic protocol verification tool that uses multi-set rewrite rules and symbolic reasoning. LoET can map its event classes and axiom systems into facts and multi-set rewrite rules in Tamarin and can deduce causal relationships through the sequential relationship and dependency rules between facts. This enables Tamarin to avoid searching for event states that cannot have matching relationships during the verification search process. Compared with using the Tamarin tool alone, it can improve verification efficiency and enhance the ability to resist state explosion. This combination approach enables Tamarin to serve as the automatic reasoning backend for LoET, integrating the precise expression and rigorous reasoning capabilities of LoET with Tamarin’s automatic verification capabilities, significantly enhancing the efficiency and rigor of protocol analysis.
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
Appendix A.1. Definition of Thread
Appendix A.2. Basic Sequences
Appendix A.3. Matching Session
Appendix A.4. Protocol Actions
Appendix B
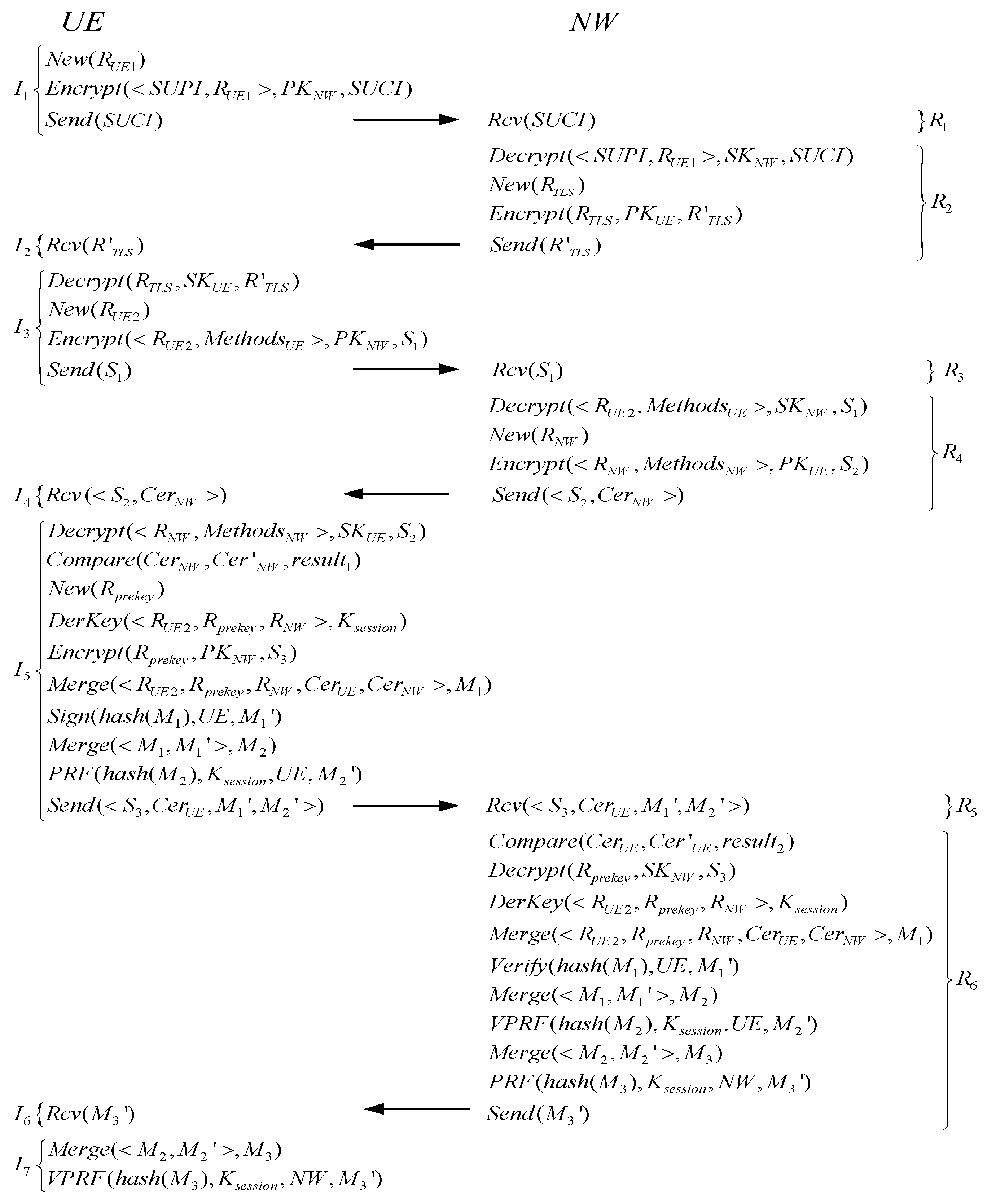
Appendix B.1. The Specific Process for Verifying the Strong Authentication Property of the EAP-TLS Protocol
Appendix B.2. Communication Overhead Analysis of the Improved Strategy
| Operation Type | Count | Estimated Time Cost (Milliseconds) | Total Added Communication (Bytes) | Description |
|---|---|---|---|---|
| RSA-2048 Encryption | 3 | ~2.4 | 768 | Each RSA-2048 encryption produces 256 bytes (standard output length defined in TLS 1.2 protocol specifications). |
| SHA-256 Merged Hash Construction | 6 | ~0.3 | 192 | Each SHA-256 hash generates 32 bytes; hash merging operations concatenate and merge these values. |
| Verification Field Construction | 2 | ~0.1 | 64 | Each verification field (e.g., HMAC or hash-based digest) contributes 32 bytes. |
| RSA-2048 Signature | 1 | ~2.0 | 256 | The RSA-2048 digital signature produces a 256-byte output. |
| Total | 12 | ~4.8–5.0 | 1280 | Aggregate added payload from all introduced operations. |
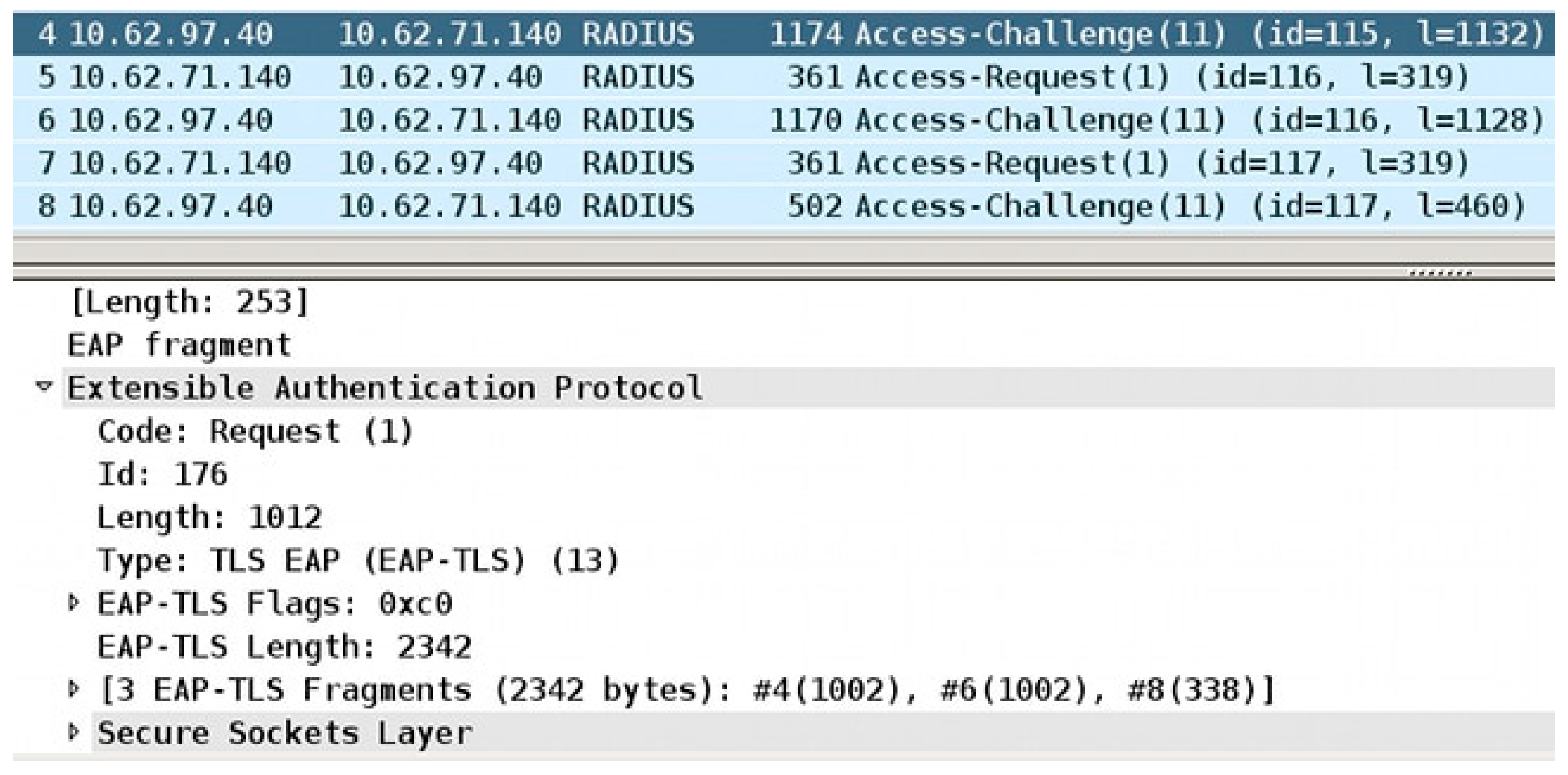
References
- Sun, P.J.; Shen, S.G.; Wan, Y.; Wu, Z.D. A Survey of IoT Privacy Security: Architecture, Technology, Challenges, and Trends. IEEE Internet Things J. 2024, 11, 34567–34591. [Google Scholar] [CrossRef]
- Rakotonirina, I.; Barthe, G.; Schneidewind, C. Decision and Complexity of Dolev-Yao Hyperproperties. Proc. ACM Program. Lang. 2024, 8, 1913–1944. [Google Scholar] [CrossRef]
- Cook, S.A. The Complexity of Theorem-Proving Procedures. In Logic, Automata, and Computational Complexity: The Works of Stephen A. Cook, 1st ed.; Kapron, B.M., Ed.; Association for Computing Machinery: New York, NY, USA, 2023; pp. 143–152. [Google Scholar]
- Zhang, J.; Yang, L.; Cao, W.; Wang, Q. Formal Analysis of 5G EAP-TLS Authentication Protocol Using ProVerif. IEEE Access 2020, 8, 23674–23688. [Google Scholar] [CrossRef]
- Li, Z.; Xiao, M.; Xu, R. Formal Analysis of Signal Protocol Based on Logic of Events Theory. Sci. Rep. 2024, 14, 20606. [Google Scholar] [CrossRef] [PubMed]
- Xiao, M.; Bickford, M. Logic of Events for Proving Security Properties of Protocols. In Proceedings of the International Conference on Web Information Systems and Mining, Shanghai, China, 7–8 November 2009. [Google Scholar]
- Yang, K.; Xiao, M.; Zhong, X.; Zhong, Y. A Novel Formal Logic for Formal Analysis of Timeliness in Non-Repudiation Protocols. J. King Saud Univ. Comput. Inf. Sci. 2023, 35, 101664. [Google Scholar] [CrossRef]
- Xiao, M.; Zhong, Y.; Li, Z.; Chen, F. Formal Analysis of DTLS-SRTP Combined Protocol Based on Logic of Events. Appl. Sci. 2024, 14, 1804. [Google Scholar] [CrossRef]
- Ma, Y.; Cao, X. How to Use EAP-TLS Authentication in PWLAN Environment. In Proceedings of the International Conference on Neural Networks and Signal Processing (ICNNSP), Nanjing, China, 14–17 December 2003; pp. 1677–1680. [Google Scholar]
- Shojaie, B.; Saberi, I.; Salleh, M.; Niknafskermani, M.; Alavi, S.M. Improving EAP-TLS Performance Using Cryptographic Methods. In Proceedings of the 2012 International Conference on Computer & Information Science (ICCIS), Kuala Lumpur, Malaysia, 12–14 June 2012; pp. 760–764. [Google Scholar]
- Shojaie, B.; Saberi, I.; Salleh, M. Enhancing EAP-TLS Authentication Protocol for IEEE 802.11i. Wirel. Netw. 2017, 23, 1491–1508. [Google Scholar] [CrossRef]
- Ghilen, A.; Azizi, M.; Bouallegue, R. Integration of a Quantum Authenticated Key Distribution Scheme in the EAP-TLS Protocol. In Proceedings of the IEEE/ACS 12th International Conference of Computer Systems and Applications (AICCSA), Marrakech, Morocco, 17–20 November 2015; pp. 1–5. [Google Scholar]
- Brzuska, C.; Jacobsen, H.; Stebila, D. Safely Exporting Keys from Secure Channels. In Advances in Cryptology—EUROCRYPT 2016; Fischlin, M., Coron, J.S., Eds.; Springer: Berlin, Germany, 2016; Volume 9665, pp. 670–698. [Google Scholar]
- Wang, C.; Ma, M.; Zhang, L. An Efficient EAP-Based Pre-Authentication for Inter-WRAN Handover in TV White Space. IEEE Access 2017, 5, 9785–9796. [Google Scholar] [CrossRef]
- Zhang, J.; Wang, Q.; Yang, L.; Feng, T. Formal Verification of 5G-EAP-TLS Authentication Protocol. In Proceedings of the 2019 IEEE Fourth International Conference on Data Science in Cyberspace (DSC), Hangzhou, China; 2019; pp. 503–509. [Google Scholar]
- Chen, L.; Xu, P.; Wang, D. Formal Verification Research on EAP-TLS Protocol. Comput. Sci. 2022, 49, 685–689. (In Chinese) [Google Scholar]
- Wang, Y.; Xiong, Y.; Huang, W.; Wu, J. A Formal Analysis Scheme for 5G Private Network Authentication Protocol. Inf. Netw. Secur. 2021, 21, 1–7. (In Chinese) [Google Scholar]
- Wang, Q. Applying SPIN Checker on 5G EAP-TLS Authentication Protocol Analysis. Comput. Sci. Inf. Syst. 2024, 21, 21–36. [Google Scholar] [CrossRef]
- Zhu, N.; Xu, J.; Cui, B. Formal Analysis of 5G EAP-TLS 1.3. In Advances in Internet, Data & Web Technologies; Barolli, L., Ed.; Springer: Cham, Switzerland, 2024; Lecture Notes on Data Engineering and Communications Technologies; Volume 193, pp. 140–151. [Google Scholar]
- Ma, Z.; Du, R.; Chen, J.; He, K. Formal Analysis of 5G EAP-TLS Protocol Based on Tamarin Prover. J. Wuhan Univ. Nat. Sci. Ed. 2023, 69, 653–664. [Google Scholar]
- Shi, M.; Chen, J.; Ma, Z.; He, K.; Jia, M.; Du, R. A Formal Analysis of 5G EAP-TLS Protocol. IEEE Trans. Netw. 2025, 12, 112–125. [Google Scholar] [CrossRef]
- Hao, Q.; Sun, L.; Guo, S.; Liu, H.; Qian, D.; Zhu, X. Improvement of EAP-TLS Protocol Based on Pseudonym Mechanism. In Proceedings of the 2021 International Conference on Wireless Communications and Smart Grid, Hangzhou, China, 13–15 August 2021; pp. 23–28. [Google Scholar]
- Yadav, A.K.; Misra, M.; Liyanage, M.; Varshney, G. Secure and User Efficient EAP-Based Authentication Protocol for IEEE 802.11 Wireless LANs. In Proceedings of the 2020 IEEE 17th International Conference on Mobile Ad Hoc and Sensor Systems, Delhi, India, 10–13 December 2020; pp. 576–584. [Google Scholar]
- Yadav, A.K.; Misra, M.; Pandey, P.K.; Liyanage, M. An EAP-Based Mutual Authentication Protocol for WLAN-Connected IoT Devices. IEEE Trans. Ind. Inform. 2023, 19, 1343–1355. [Google Scholar] [CrossRef]
- Yadav, A.K.; Misra, M.; Pandey, P.K.; Ranaweera, P.; Liyanage, M.; Kumar, N. A Secure Authentication Protocol for IoT-WLAN Using EAP Framework. IEEE Trans. Depend. Secur. Comput. 2025, 22, 49–65. [Google Scholar] [CrossRef]
- Zhou, Z.; Abawajy, J. Reinforcement Learning-Based Edge Server Placement in the Intelligent Internet of Vehicles Environment. IEEE Trans. Intell. Transp. Syst. 2025, in press. 1–11. [Google Scholar] [CrossRef]
- Kumar, P.; Kumar, D. DoMT: An Evaluation Framework for WLAN Mutual Authentication Methods. In Mobile Radio Communications and 5G Networks; Marriwala, N., Tripathi, C., Jain, S., Kumar, D., Eds.; Springer: Singapore, 2022; Lecture Notes in Networks and Systems; Volume 339, pp. 307–322. [Google Scholar]
- Hu, X.; Jiang, Y.; Hu, A. Secondary Authentication Method Suitable for 5G-Based Power Terminals and Formal Analysis. In Proceedings of the 2022 2nd International Joint Conference on Energy, Electrical and Power Engineering (CoEEPE 2022), Beihai, China, 19–21 November; Hu, C., Cao, W., Eds.; Springer: Singapore, 2023; Lecture Notes in Electrical Engineering; Volume 1060, pp. 450–465. [Google Scholar]
- Ajit, M.; Sankaran, S.; Jain, K. Formal Verification of 5G EAP-AKA Protocol. In Proceedings of the 2021 31st International Telecommunication Networks and Applications Conference, Sydney, Australia, 24–26 November 2021; pp. 140–146. [Google Scholar]
- Schwenk, J. Point-to-Point Security. In Guide to Internet Cryptography; Schwenk, J., Ed.; Springer: Cham, Switzerland, 2022; Information Security and Cryptography; pp. 153–177. [Google Scholar]
- Walz, A.; Niemann, K.H.; Göppert, J.; Fischer, K.; Merklin, S.; Ziegler, D.; Sikora, A. Profinet Security: A Look on Selected Concepts for Secure Communication in the Automation Domain. In Proceedings of the 2023 IEEE 21st International Conference on Industrial Informatics, Lemgo, Germany, 18–20 July 2023; pp. 1–6. [Google Scholar]
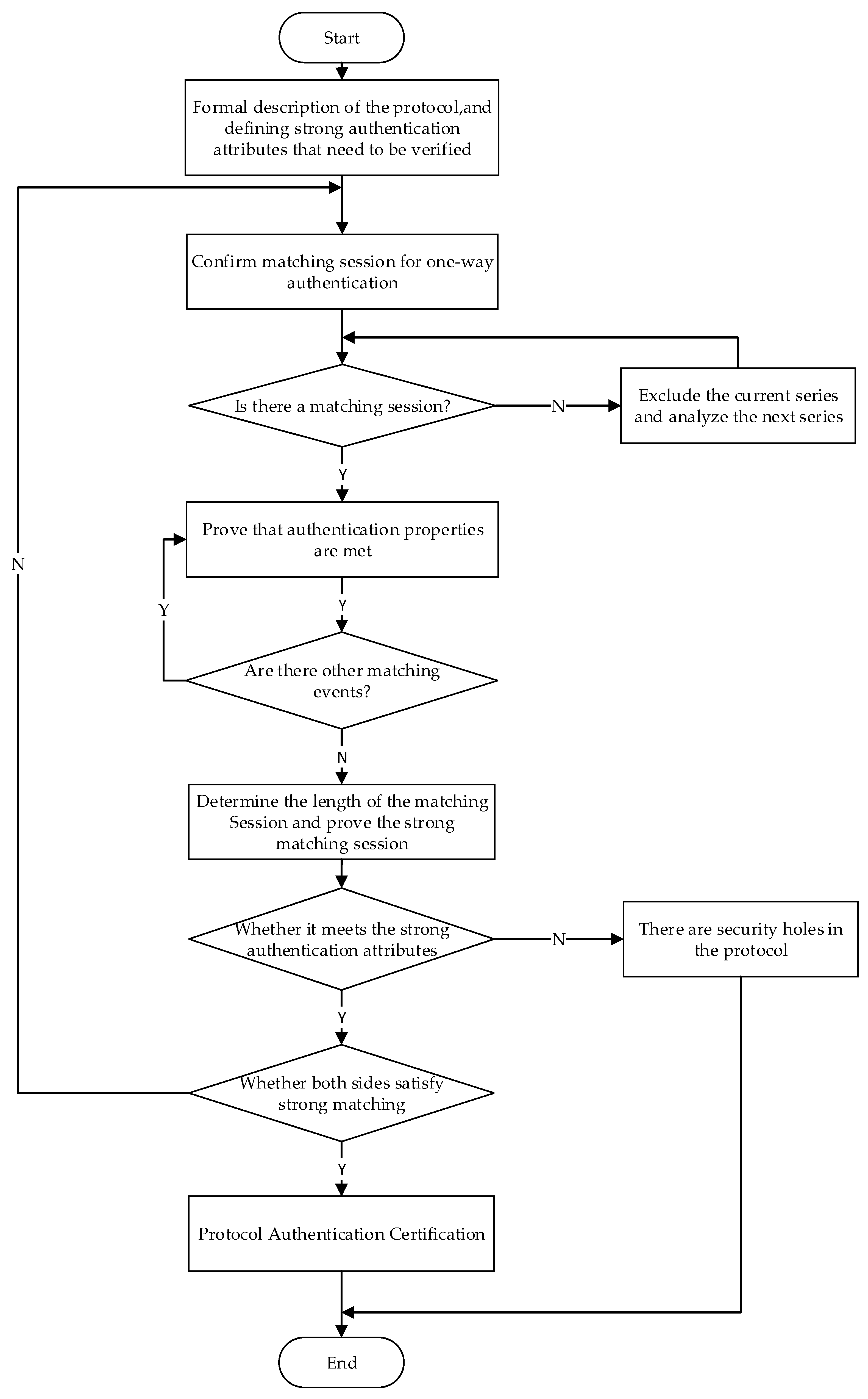
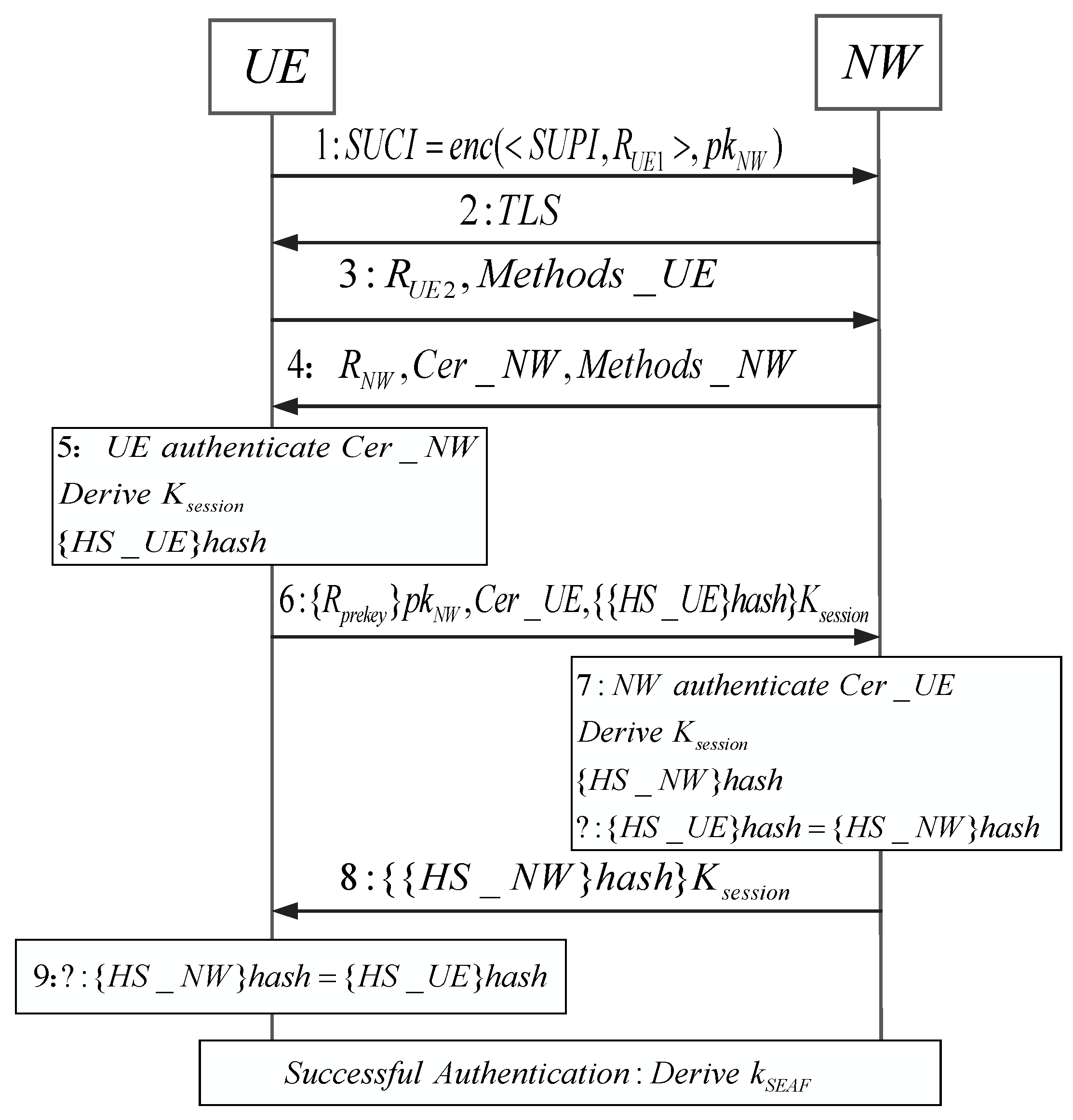
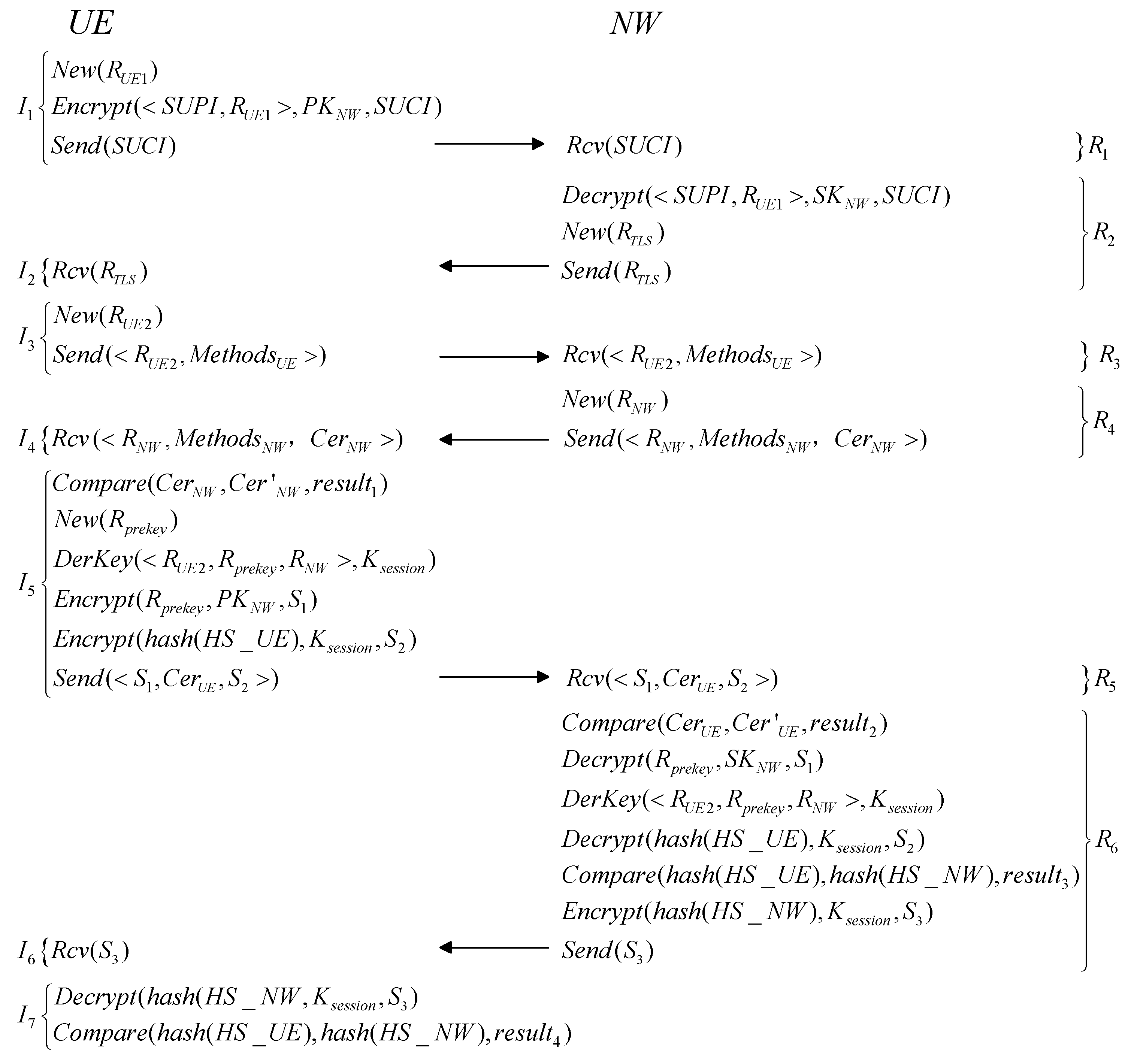
| Reference | Research Method | Modeling Accuracy | Communication Overhead Consideration |
|---|---|---|---|
| The present study | LoET (Extended) | High—handshake fully modeled | ✔Analyzes communication cost of improvements |
| Ref. [15] | Scyther | Limited | ✖ Not considered |
| Ref. [16] | ProVerif | Limited | ✖ Not considered |
| Ref. [17] | SmartVerif | Moderate | ✖ Not considered |
| Ref. [18] | SPIN | Limited | ✖ Not considered |
| Ref. [20] | Tamarin | High | ✖ Not considered |
| Basic Symbols, Predicates, and Event Classes | Semantics |
|---|---|
| Id | The subjects participating in the agreement |
| Atom | A class representing confidential information |
| Data | All plaintext and messages |
| e/event Nonce | Represent an event |
| E | Event set |
| Nonce | Random number |
| n | Represents a challenge number in a Nonce event |
| has | Logical relation contains |
| || | Logical relation independence |
| Represents a locally finite partial order | |
| loc(e) | Represent the subject where event e occurs |
| key(e) | The subject key of event e |
| Thread | An ordered list of actions |
| bss | the parameter list of basic protocol actions |
| Subject A participates in the protocol Pr | |
| Messages m1 and m2 have a weak matching relationship | |
| Messages m1 and m2 have a strong matching relationship | |
| The basic sequence bss authenticates n messages | |
| Event e generates a number of challenges | |
| The Data class message sent by event e | |
| The Data class message received in event e | |
| The subject encrypts the plaintext x with the key k to obtain the ciphertext c | |
| The subject decrypts the ciphertext c with the key k to obtain the plaintext x | |
| The subject signs the plaintext x to obtain the signature message s | |
| The subject verifies the signed message s to obtain the plaintext x | |
| Presentation Event language | |
| Field | Semantics | Field | Semantics |
|---|---|---|---|
| UE | User Equipment | NW | Core network |
| SUPI | The permanent unique identifier of the subscriber | Handshake messages from UE | |
| The random number generated by the UE | Pre-master key random number generated by the UE | ||
| Public key of the core network (NW) | Certificate of the UE | ||
| TLS | The handshake process initiation flag, which is subsequently abstracted as a random number | Handshake messages from the NW | |
| The random number generated by the UE | Certificate of the NW | ||
| Authentication method chosen by the User Equipment (UE) | Authentication method of the NW | ||
| Random number generated by the core network (NW) | Derived temporary session key |
| Steps | Matching Events and Event Ordering | Proof Basis | Results |
|---|---|---|---|
| 1 | , | By applying the axioms, six matching events are identified, resulting in a weak matching session of length six. | |
| 2 | , | ||
| 3 | , | ||
| 4 | |||
| 5 | |||
| 6 | |||
| 7 | , , , | By applying the axioms and rules, the chronological order of six events is proven, resulting in a strong matching session of length six. | |
| 8 | |||
| 9 | |||
| 10 | |||
| 11 | |||
| 12 |
| Reference | Research Method | Resistance to State Explosion | Time Complexity | Verification Efficiency |
|---|---|---|---|---|
| The present study | LoET (Extended) | High | ✔ Precisely models handshake chains; avoids state explosion caused by attacker interactions; and successfully verifies strong mutual authentication. | |
| Refs. [16,19] | ProVerif | Low | ✖ Difficult to handle handshake complex structures; incomplete modeling of the certificate mechanism. | |
| Refs. [20,21] | Tamarin | Medium | ✖ Modeling overhead is high; requires manual lemma assistance; time-consuming for full handshake analysis; and struggles with complex identity chain verification. | |
| Ref. [17] | SmartVerif | Medium | ✖ Efficiency drops sharply when pruning fails; completeness cannot be guaranteed. | |
| Ref. [18] | SPIN | Low | ✖ Frequent state explosion; difficult to model handshake loops. |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xiao, M.; Cheng, W.; Fan, H.; Shao, H.; Li, Z.; Zhong, Y. Formal Analysis of EAP-TLS Protocol Based on Logic of Events. Symmetry 2025, 17, 1456. https://doi.org/10.3390/sym17091456
Xiao M, Cheng W, Fan H, Shao H, Li Z, Zhong Y. Formal Analysis of EAP-TLS Protocol Based on Logic of Events. Symmetry. 2025; 17(9):1456. https://doi.org/10.3390/sym17091456
Chicago/Turabian StyleXiao, Meihua, Weili Cheng, Hongming Fan, Huaibin Shao, Zehuan Li, and Yingqiang Zhong. 2025. "Formal Analysis of EAP-TLS Protocol Based on Logic of Events" Symmetry 17, no. 9: 1456. https://doi.org/10.3390/sym17091456
APA StyleXiao, M., Cheng, W., Fan, H., Shao, H., Li, Z., & Zhong, Y. (2025). Formal Analysis of EAP-TLS Protocol Based on Logic of Events. Symmetry, 17(9), 1456. https://doi.org/10.3390/sym17091456







