Security Symmetry in Embedded Systems: Using Microsoft Defender for IoT to Detect Firmware Downgrade Attacks
Abstract
1. Introduction
- Fully undetectable—the Endpoint Detection and Response (EDR) failed to identify the malicious activity.
- Invisible—the system continued to display as up-to-date despite the downgrade.
- Persistent—future updates are compromised, preventing genuine patches from being applied (modification of poqexec.exe).
- Irreversible—integrity and repair utilities did not detect any issues, making the remediation challenging (modification of SFC.exe).
- Assess the potential risks and real-world impact of firmware downgrades;
- Characterize the structural and behavioral symmetries exploited by firmware downgrade attacks;
- Design a solution that mitigates these implications while considering the OT domain-specific characteristics and limitations;
- Evaluate the solution’s efficiency in both a controlled test environment and a real production network.
2. Materials and Methods
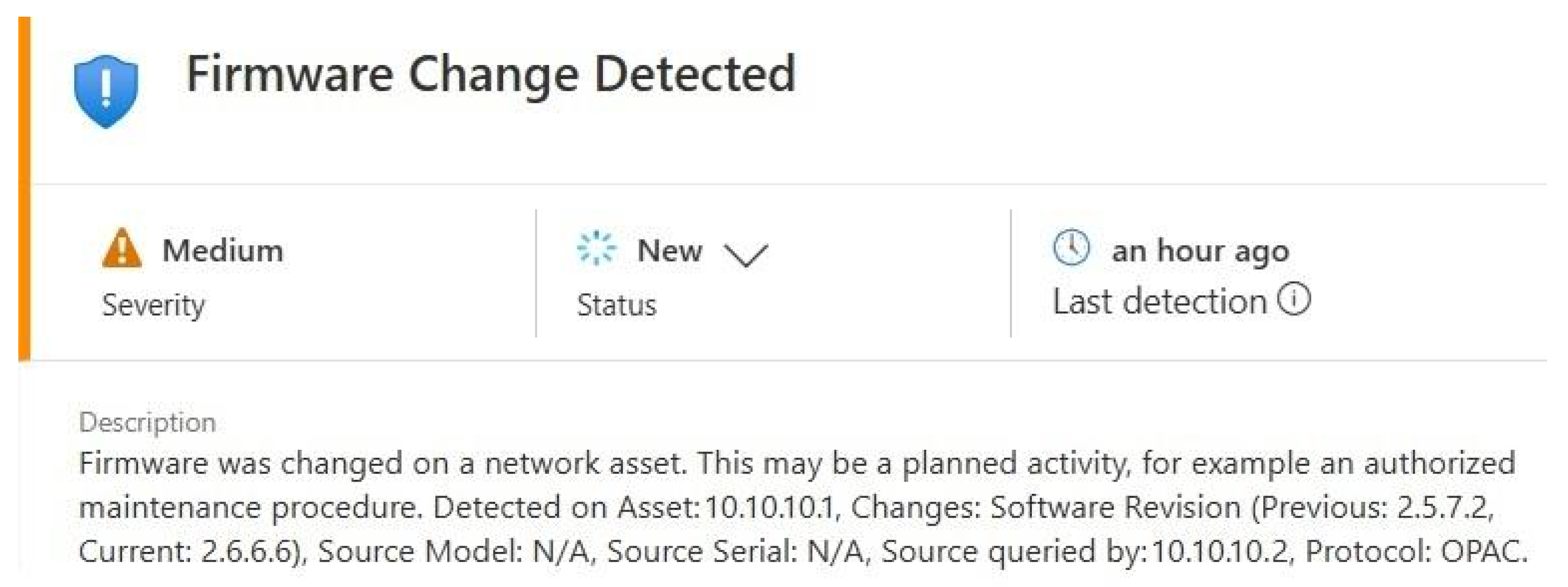
2.1. Firmware Change Detected D4IoT Alert Overview
- DS0015—Monitoring application logs for firmware changes (it should be noted that not all devices generate such logs);
- DS0001—Tracking firmware modifications and comparing them to a database of known-good versions and expected patching behavior;
- DS0029—Analyzing ICS/file transfer protocols for activities that might indicate firmware changes;
- DS0040—Monitoring operational alarms that could alert firmware changes.
- OPAC (Open Protocol Atlas Copco)—a communication protocol designed for the remote control of Atlas Copco controllers. It supports both Ethernet (TCP port 4545) and serial (Serial ASCII or Serial ASCII with 3964R handshake) connections [16].
- MODBUS—an application-layer communication protocol for establishing connections between devices from different vendors. It operates on a client–server model, utilizing various function codes for request/response messages. The protocol uses TCP port 502 [17].
- Profinet—an industrial Ethernet-based communication protocol for real-time data transfers between controllers (PLCs) and field devices (sensors, actuators, and robots). The protocol operates on TCP port 102 (configuration) and UDP 34962-34964 (communication) [18].
- Rockwell CSP2—a Layer 7 protocol designed by Rockwell Automation for communication between Allen–Bradley PLCs and Rockwell software applications. The default port is TCP 2222 [19].
- MMS (Manufacturing Message Specification)—an Ethernet-based client-server communication protocol used for data exchange between IEDs (Intelligent Electronic Devices) and higher-level systems, such as Supervisory Control and Data Acquisition (SCADA). The protocol typically operates over TCP port 102 [20].
- CDP (Cisco Discovery Protocol)—a proprietary Layer 2 protocol designed for directly connected network devices (such as routers, switches, and bridges). It enables network management applications to discover Cisco devices, providing at least their IP address and device type [21].
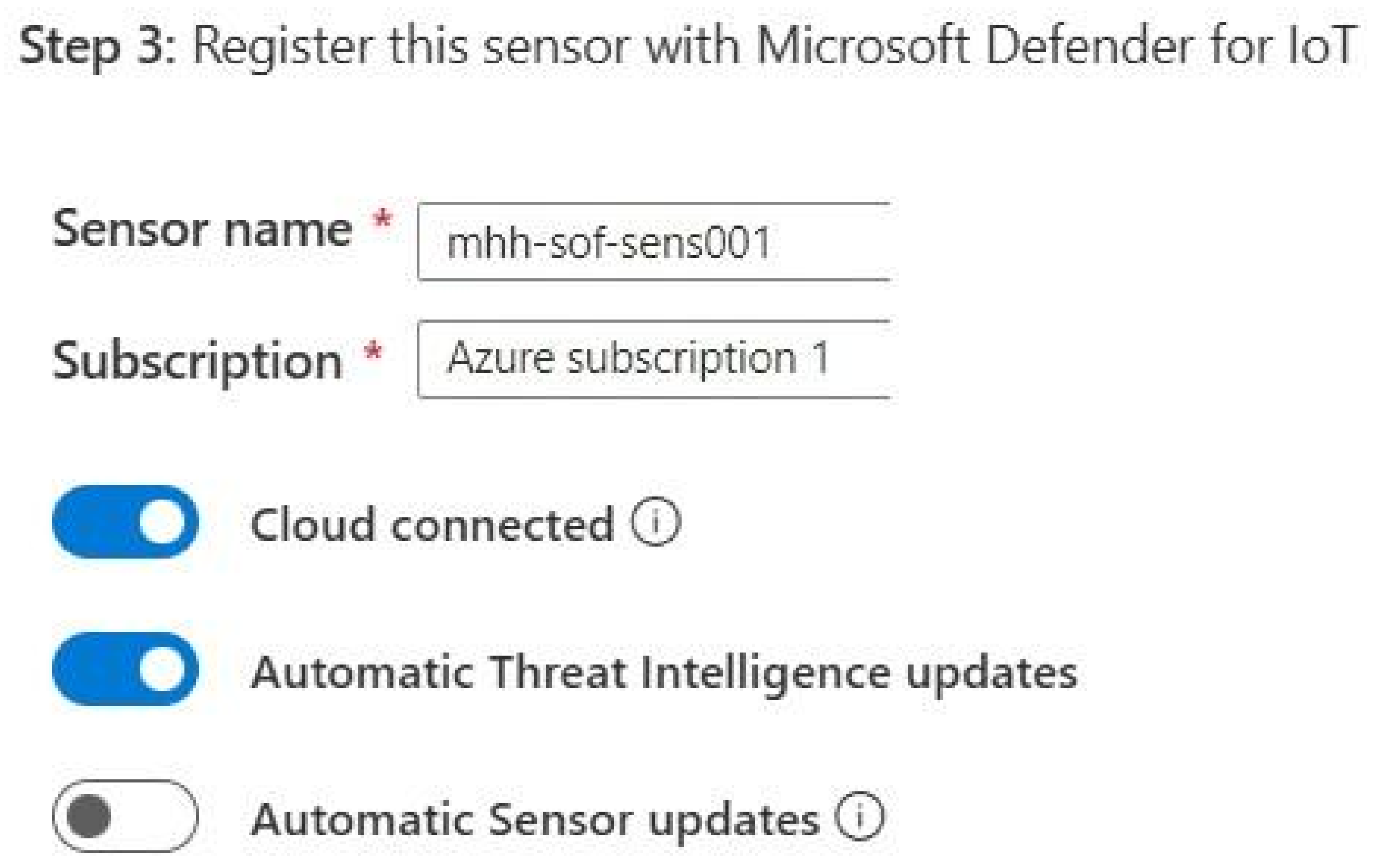
2.2. D4IoT Setup Prerequisites
2.3. Implementation of a Detection Mechanism for Firmware Downgrade
2.4. Selected Methods’ Rationale
3. Results
3.1. Setting Up the Test Bed
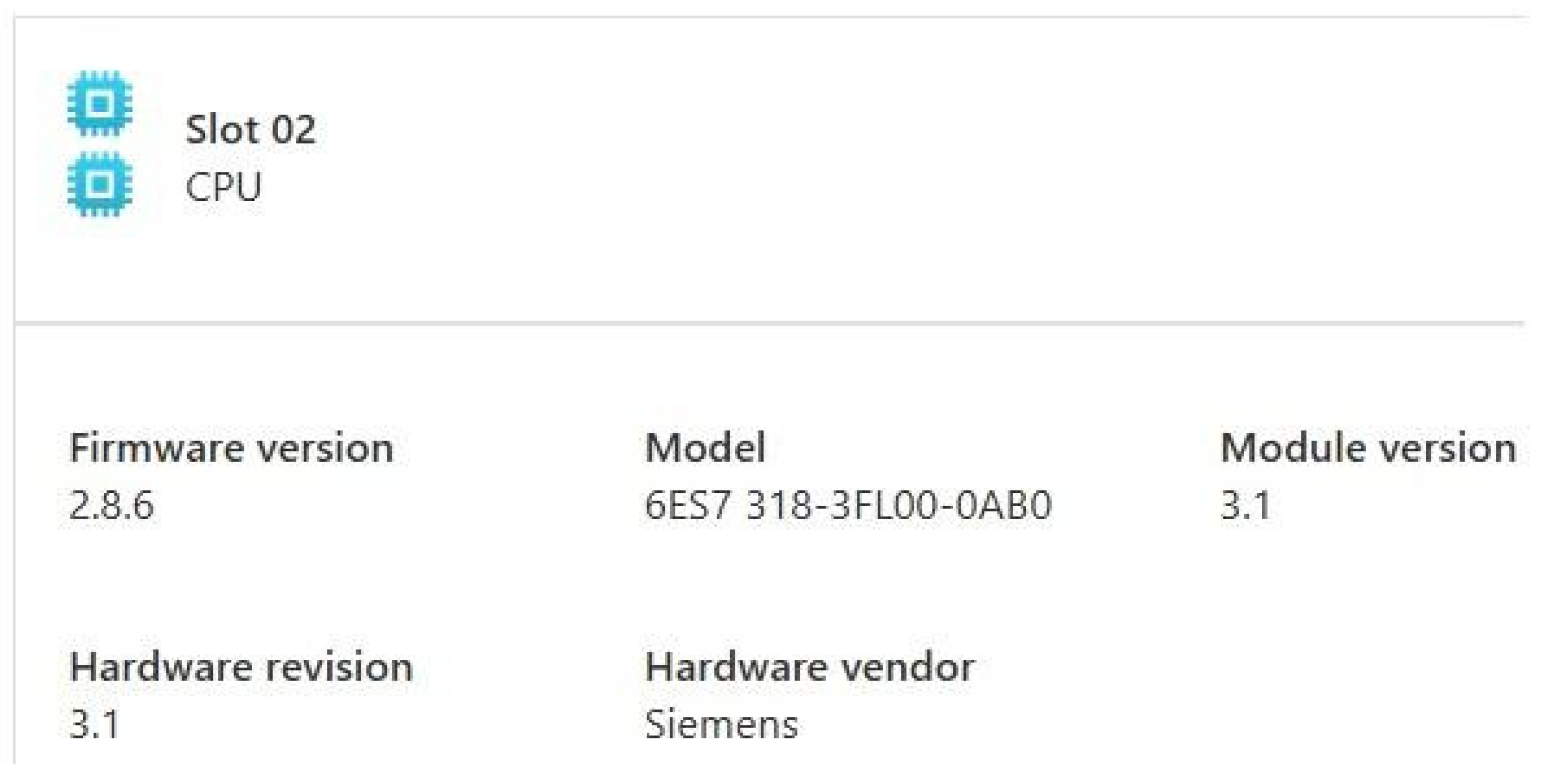
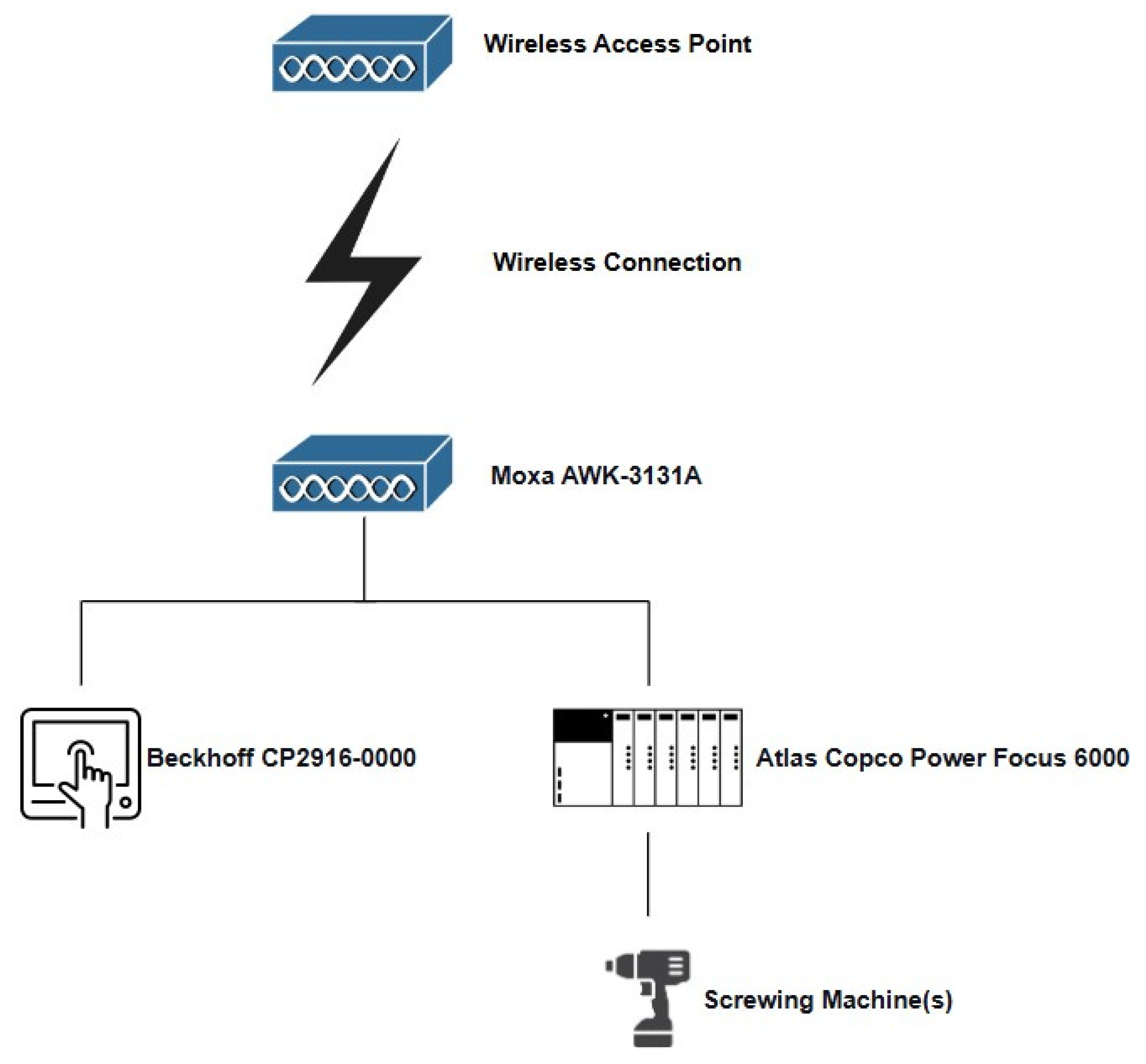
- Atlas Copco Power Focus 6000—a single, centralized tightening controller, typically connected to one or more screwing machines, and presented in Figure 11;
- Moxa AWK-3131A—industrial wireless AP/bridge/client that supports IEEE 802.11 a/b/g/n and is utilized to connect the “Atlas Copco Power Focus 6000” and “Beckhoff CP2916-0000” to the wireless network, presented in Figure 12;
- Beckhoff CP2916-0000—industrial panel PC (processor + HMI) that runs Windows 10 IoT. Utilized for direct monitoring and process control, presented in Figure 13.
3.2. Testing the Implemented Solution
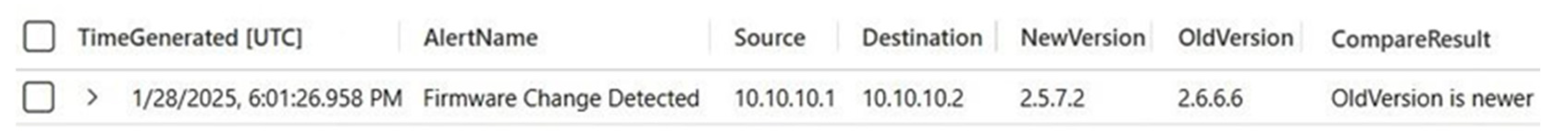


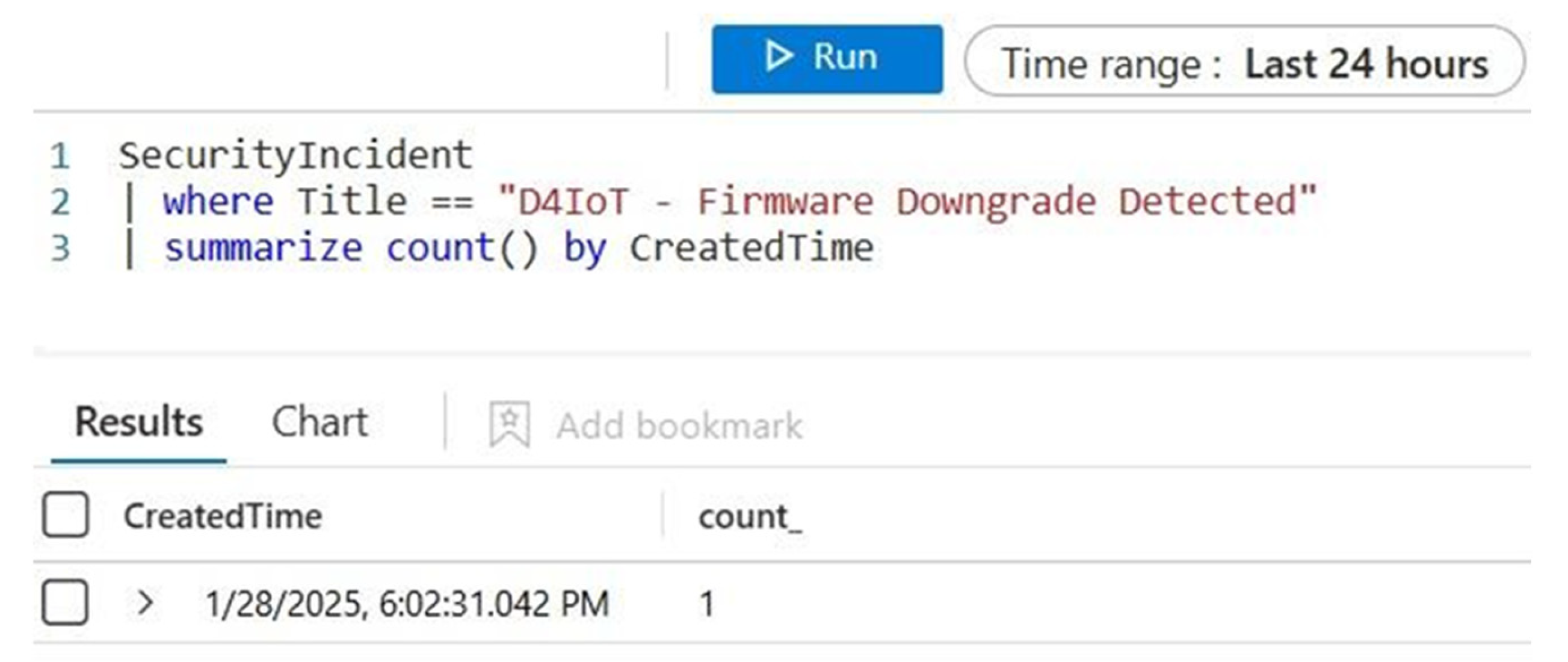
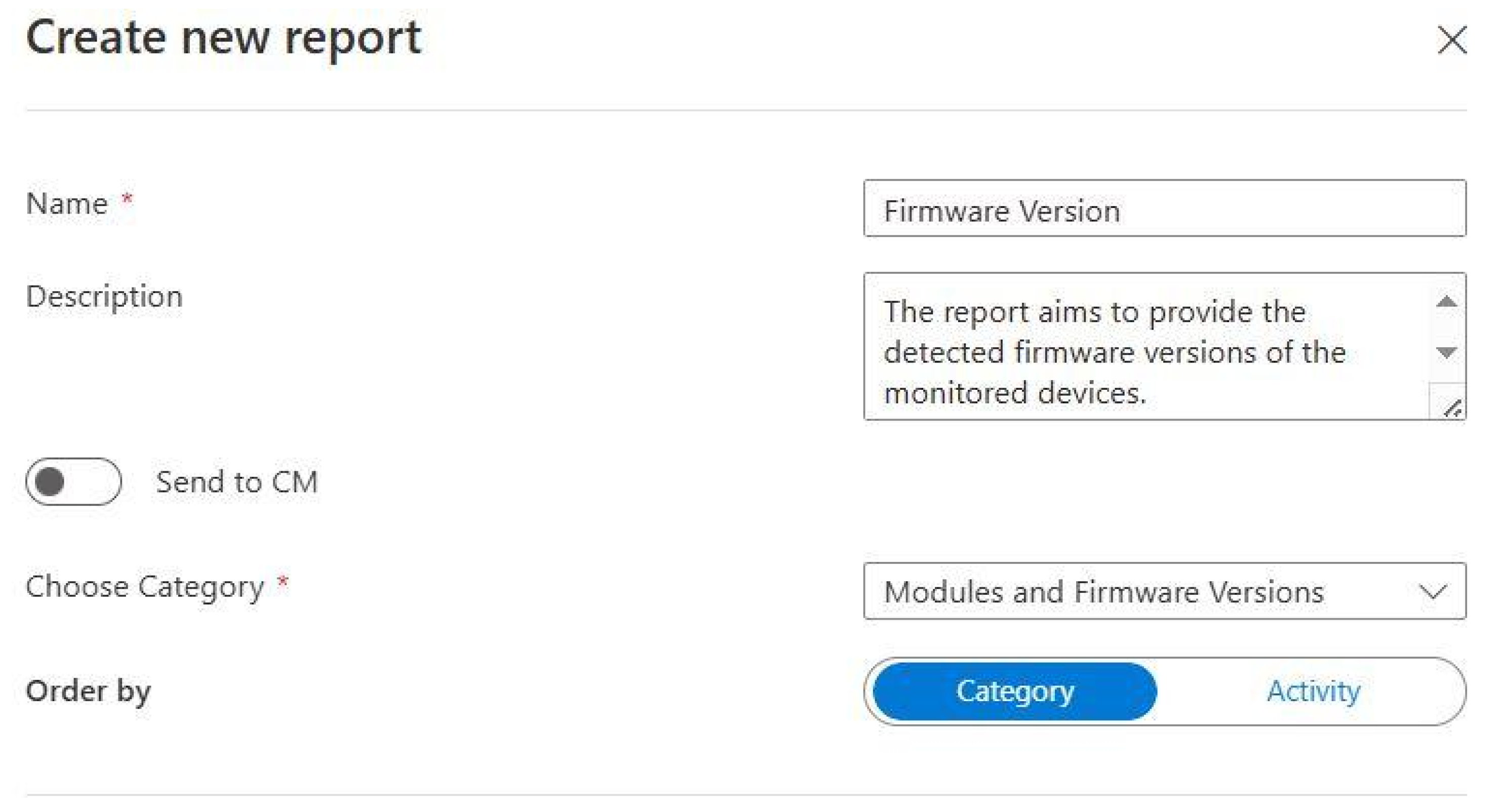
3.3. Implementation of Automation for Weekly Reports of Firmware Change Detected D4IoT Alerts
- Recurrence—defines the execution interval (e.g., once a week) and the starting point (e.g., specific date). This operation triggers the Logic Apps and initiates the following steps.
- Run query and list results—executes a KQL query that searches the “Firmware Change Detected” D4IoT alerts for the pre-defined period (e.g., last 7 days). The query is presented in Figure 19.
- Condition—validates whether the KQL query has produced any results (i.e., found “Firmware Change Detected” D4IoT alerts in the specified period).
- Create CSV table—collects the query results and stores them in a CSV file.
- Send an email (V2)—sends the created CSV file containing the “Firmware Change Detected” D4IoT alerts to a pre-defined list of recipients.

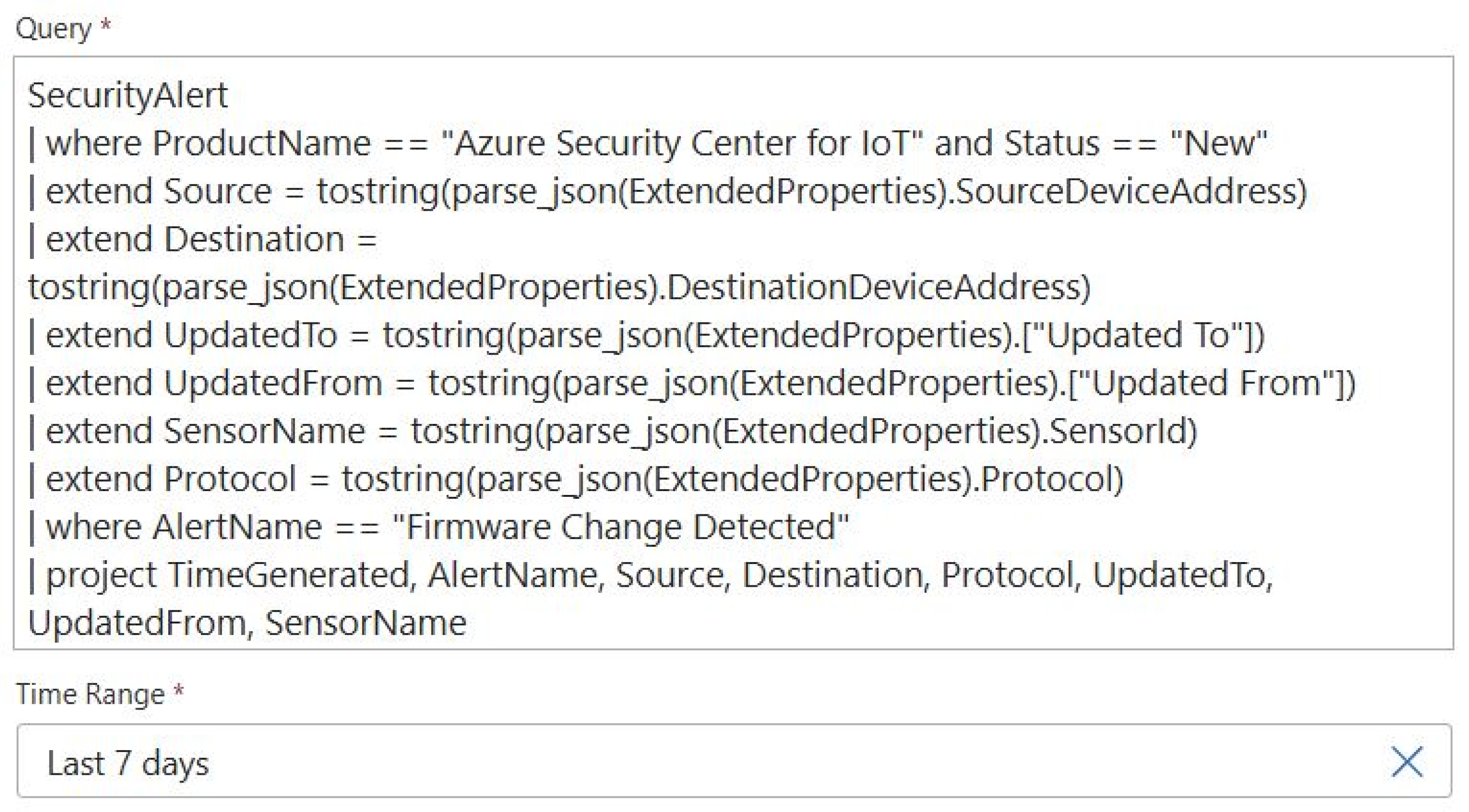
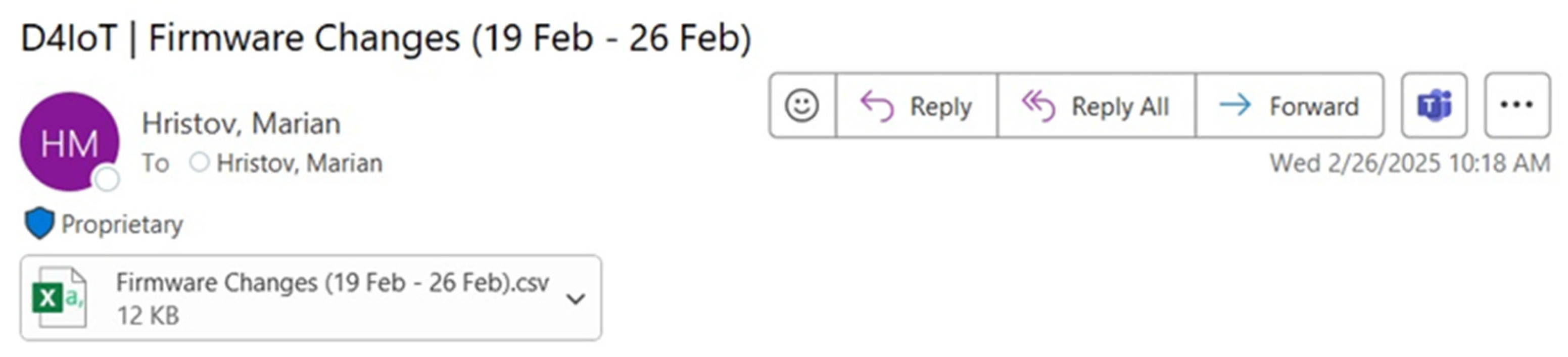
4. Discussion
4.1. Discussion of Results
4.2. Evaluation and Discussion of Impacts
4.3. Limitations and Future Implications
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Abbreviations
| AI | Artificial Intelligence |
| CSV | Comma-Separated Values |
| D4IoT | Microsoft Defender for IoT |
| EDR | Endpoint Detection and Response |
| HMI | Human–Machine Interface |
| ICS | Industrial Control Systems |
| IED | Intelligent Electronic Device |
| IoT | Internet of Things |
| IT | Information Technology |
| KQL | Kusto Query Language |
| MAC | Media Access Control |
| MMS | Manufacturing Message Specification |
| MTTD | Mean Time to Detect |
| OPAC | Open Protocol Atlas Copco |
| OS | Operating System |
| OT | Operational Technology |
| PLC | Programmable Logic Controller |
| RTU | Remote Terminal Unit |
| SCADA | Supervisory Control and Data Acquisition |
| SIEM | Security Information and Event Management |
| SIS | Safety Instrumented System |
| SOC | Security Operations Center |
| TCP | Transmission Control Protocol |
| TTPs | Tactics, Techniques, and Procedures |
| UDP | User Datagram Protocol |
References
- Blackhat Official Conference Page © 2025 Informa PLC, August 2024. Available online: https://www.blackhat.com (accessed on 2 June 2025).
- DEF CON Official Conference Page © 2025 DEF CON Communications, Inc., August 2024. Available online: https://defcon.org (accessed on 2 June 2025).
- Leviev, A. Official Research Projects Page. Available online: https://www.alonleviev.com/research-projects (accessed on 2 June 2025).
- SafeBreach © Copyrights SafeBreach Inc. 2025. Windows Downdate: Downgrade Attacks Using Windows Updates, August 2024. Available online: https://www.safebreach.com/blog/downgrade-attacks-using-windows-updates (accessed on 2 June 2025).
- Hau, B.; Lee, T.; Homan, J. SYNful Knock—A Cisco Router Implant—Part I, Mandiant Blog, 15 September 2015. Available online: https://cloud.google.com/blog/topics/threat-intelligence/synful-knock-acis (accessed on 2 June 2025).
- Holmes, G. Evolution of Attacks on Cisco IOS Devices. Cisco Blog, 8 October 2015. Available online: https://blogs.cisco.com/security/evolution-of-attacks-on-cisco-ios-devices (accessed on 2 June 2025).
- Srivastava, A.; Thakur, S.; Kuruvila, A.P.; Balsara, P.T.; Basu, K. Hardware-Based Detection of Malicious Firmware Modification in Microgrids. In Proceedings of the 2024 37th International Conference on VLSI Design and 2024 23rd International Conference on Embedded Systems (VLSID), Kolkata, India, 6–10 January 2024; pp. 186–191. [Google Scholar] [CrossRef]
- Konstantinou, C.; Maniatakos, M. Impact of Firmware Modification Attacks on Power Systems Field Devices. In Proceedings of the 2015 IEEE International Conference on Smart Grid Communications (SmartGridComm), Miami, FL, USA, 2–5 November 2015; pp. 283–288. [Google Scholar] [CrossRef]
- Jain, S.; Lakshmi, V.; Srivathsa, R. IoT and OT Security Handbook: Assess Risks, Manage Vulnerabilities, and Monitor Threats with Microsoft Defender for IoT; Packt Publishing: Birmingham, UK, 2023. [Google Scholar]
- Diver, R.; Bushey, G.; Perkins, J. Microsoft Sentinel in Action: Architect, Design, Implement, and Operate Microsoft Sentinel as the Core of Your Security Solutions; Packt Publishing: Birmingham, UK, 2022. [Google Scholar]
- Microsoft. Microsoft Defender for IoT Alert Reference, 28 March 2024. Available online: https://learn.microsoft.com/en-us/azure/defender-for-iot/organizations/alert-engine-messages (accessed on 2 June 2025).
- Ekisa, C.; Ó Briain, D.; Kavanagh, Y. Leveraging the MITRE ATT&CK Framework for Threat Identification and Evaluation in Industrial Control System Simulations. In Proceedings of the 2024 35th Irish Signals and Systems Conference (ISSC), Belfast, UK, 13–14 June 2024; pp. 1–6. [Google Scholar] [CrossRef]
- MITRE ATT&CK. T0857: System Firmware. Available online: https://attack.mitre.org/techniques/T0857 (accessed on 2 June 2025).
- Liang, G.; Weller, S.R.; Zhao, J.; Luo, F.; Dong, Z.Y. The 2015 Ukraine Blackout: Implications for False Data Injection Attacks. IEEE Trans. Power Syst. 2017, 32, 3317–3318. [Google Scholar] [CrossRef]
- Al-Rabiaah, S. The “Stuxnet” Virus of 2010 as an Example of an “APT” and Its “Recent” Variants. In Proceedings of the 2018 21st Saudi Computer Society National Computer Conference (NCC), Riyadh, Saudi Arabia, 25–26 April 2018; pp. 1–5. [Google Scholar] [CrossRef]
- Atlas Copco. Open Protocol Specification Release 2.8.0. Available online: https://s3.amazonaws.com/co.tulip.cdn/OpenProtocolSpecification_R280.pdf (accessed on 2 June 2025).
- Modbus Organization. Modbus Protocol Overview. Available online: https://www.modbus.org (accessed on 2 June 2025).
- PROFINET. PROFINET Protocol Overview. Available online: https://www.profinet.com (accessed on 2 June 2025).
- Rockwell Automation. TCP and UDP Port Configuration—Quick Reference Guide, COMM-QR001A-EN-E; Rockwell Automation: Milwaukee, WI, USA, 2014. [Google Scholar]
- Typhoon HIL. IEC 61850 MMS Protocol Documentation. Available online: https://www.typhoon-hil.com/documentation/typhoon-hil-software-manual/References/iec_61850_mms_protocol.html (accessed on 2 June 2025).
- Cisco. Understanding and Configuring CDP. Software Configuration Guide—Release 12.2(25)EW. Available online: https://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst4500/12-2/25ew/configuration/guide/conf/cdp.pdf (accessed on 2 June 2025).
- Splunk. Enterprise Security Product Overview. Available online: https://www.splunk.com/en_us/products/enterprise-security.html (accessed on 2 June 2025).
- Microsoft. Provision Sensors for Cloud Management, 30 March 2023. Available online: https://learn.microsoft.com/en-us/azure/defender-for-iot/organizations/ot-deploy/provision-cloud-management (accessed on 2 June 2025).
- Microsoft. Tutorial: Connect Microsoft Defender for IoT with Microsoft Sentinel, 8 March 2023. Available online: https://learn.microsoft.com/en-us/azure/defender-for-iot/organizations/iot-solution (accessed on 2 June 2025).
- Microsoft. Scalar Function Case(), 12 August 2024. Available online: https://learn.microsoft.com/en-us/kusto/query/case-function?view=microsoft-fabric (accessed on 2 June 2025).
- Microsoft. What Is Azure Logic Apps? 29 January 2025. Available online: https://learn.microsoft.com/en-us/azure/logic-apps/logic-apps-overview (accessed on 2 June 2025).









| Device | IP Address | Subnet Mask |
|---|---|---|
| Moxa AWK-3131A | 10.10.10.10 | 255.255.255.240 |
| Beckhoff CP2916-0000 | 10.10.10.1 | 255.255.255.240 |
| Atlas Copco Power Focus 6000 | 10.10.10.2 | 255.255.255.240 |
| # | Operation | Description | Expected Results | Actual Results |
|---|---|---|---|---|
| 1 | Asset Discovery | D4IoT detects the Atlas Copco device | D4IoT identifies the device’s firmware version | Firmware Version Identified: 2.6.6.6 |
| 2 | Firmware Downgrade | The Atlas Copco device is downgraded | “Firmware Change Detected” alert | Alert Generated Indicating Firmware Version: 2.5.7.2 |
| 3 | Incident Generation | Trigger a Sentinel incident for a firmware downgrade | “D4IoT—Firmware Downgrade Detected” incident | Incident Generated |
| 4 | Firmware Upgrade | The Atlas Copco device is upgraded | Second “Firmware Change Detected” alert | Alert Generated Indicating Firmware Version: 2.6.6.6 |
| 5 | Incident Suppression | The designed detection mechanism supresses the activity | The second “Firmware Change Detected” alert does not trigger an incident | No Incident Generated |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Hristov, M.; Nenova, M.; Dimitrova, V. Security Symmetry in Embedded Systems: Using Microsoft Defender for IoT to Detect Firmware Downgrade Attacks. Symmetry 2025, 17, 1061. https://doi.org/10.3390/sym17071061
Hristov M, Nenova M, Dimitrova V. Security Symmetry in Embedded Systems: Using Microsoft Defender for IoT to Detect Firmware Downgrade Attacks. Symmetry. 2025; 17(7):1061. https://doi.org/10.3390/sym17071061
Chicago/Turabian StyleHristov, Marian, Maria Nenova, and Viktoria Dimitrova. 2025. "Security Symmetry in Embedded Systems: Using Microsoft Defender for IoT to Detect Firmware Downgrade Attacks" Symmetry 17, no. 7: 1061. https://doi.org/10.3390/sym17071061
APA StyleHristov, M., Nenova, M., & Dimitrova, V. (2025). Security Symmetry in Embedded Systems: Using Microsoft Defender for IoT to Detect Firmware Downgrade Attacks. Symmetry, 17(7), 1061. https://doi.org/10.3390/sym17071061











