Lightweight Drone-to-Ground Station and Drone-to-Drone Authentication Scheme for Internet of Drones
Abstract
1. Introduction
- A secure and lightweight D2G and D2D authentication and key agreement protocol with perfect forward secrecy for IoD is proposed.
- In order to enhance the security and privacy-preserving, we integrate PUF into GS and drones, respectively, to resist capture attacks from GS and drones. In addition, GS has no additional storage overhead for the registration and authentication process for drones. Furthermore, the mutual authentication between drones does not require the participation of GS, which is more secure and efficient.
- The proposed protocol guarantees to be secured against all known threats faced by IoD. The semantic security of the proposed protocol is formally proved under the random oracle model. Comparative analysis shows that our protocol can resist various known attacks, achieve perfect forward security and privacy protection, and maintain low computational costs.
2. Related Works
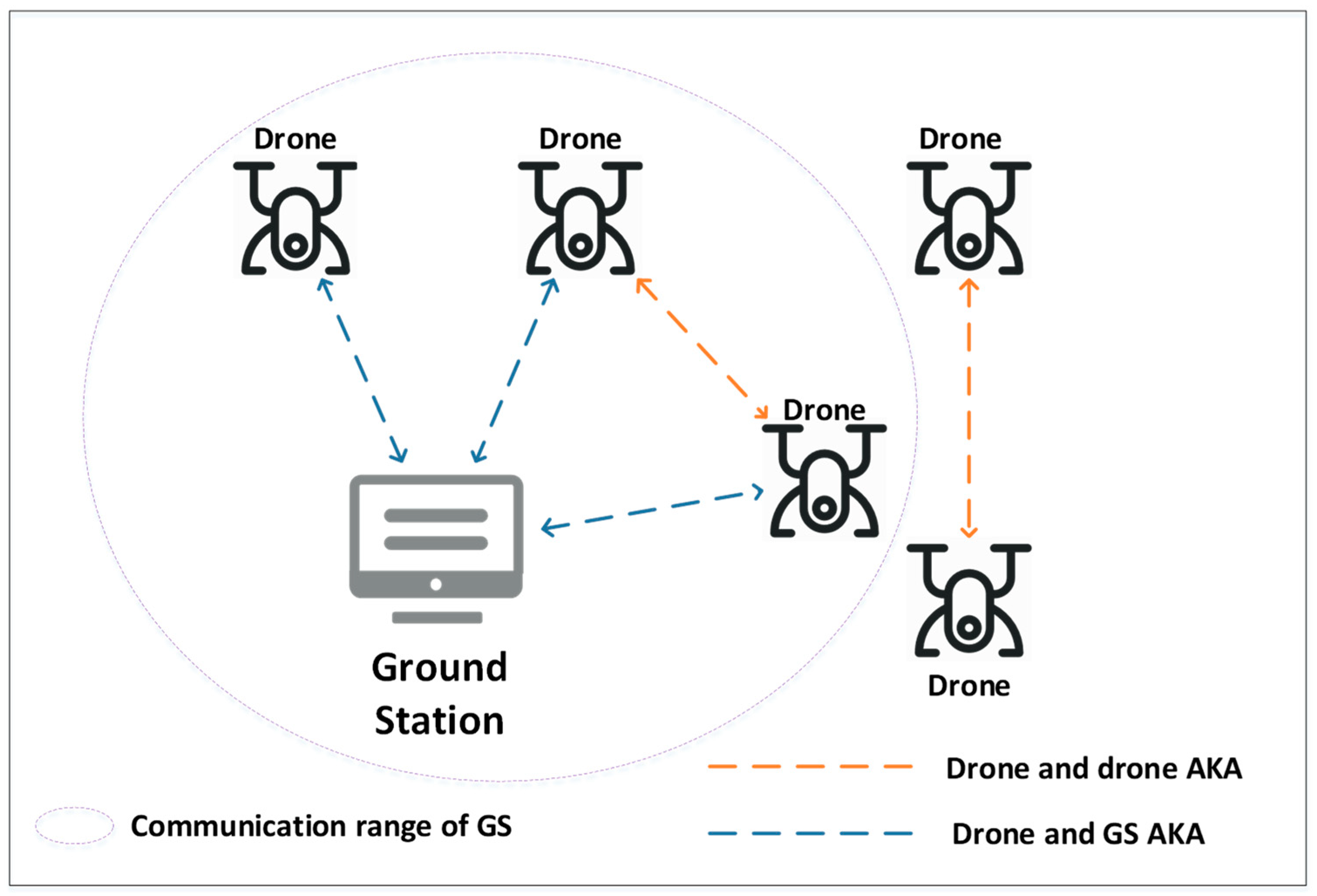
3. System Model
3.1. Network Model
3.2. Threat Model
- The adversary A may be an internal attacker or a drone with a valid registration, in which case the attacker may transmit harmful messages or initiate impersonation attacks.
- A can also eavesdrop, modify, intercept, forge, delete, and replay the messages transmitted publicly.
- A can gain access to stored data by side-channel attacks on drones and GS, but cracking PUF is tough.
4. Proposed Protocol
4.1. System Initialization Phase
4.2. Drone Registration Phase
- The drone selects its identity and sends its identity to GS via a secure channel.
- On receiving the request from the drone, GS verifies the legitimacy and uniqueness of the identity , selects a random number , calculates , , , , where is current time. Then, GS sends to drone via a secure channel and adds in the revocation list.
- The drone selects a challenge value , calculates , , , then the drone stores .
4.3. Drone-GS Authentication and Key Agreement Phase
- The drone selects a random number and a timestamp , calculates , , , , and sends {} to GS.
- On receiving the information from the drone, GS verifies the freshness of , calculates , , , , then verifies if , if not, reject it. Otherwise, GS selects a random number and a timestamp , calculates , , , ), , then sends {} to drone. The serves as a session key between the drone and GS.
- On receiving the information from GS, the drone verifies the freshness of , then calculates , , , then verifies if , if it is valid, the drone gets the session key and updates the pseudo-identity .
4.4. Drone-Drone Authentication and Key Agreement Phase
- selects two random numbers and a timestamp , calculates , , , , , , sends {} to .
- On receiving the information from , the verifies the freshness of , calculates , , , , , then verifies if , if not, reject it. Otherwise, selects a random number and a timestamp , calculates , , , then sends to . The serves as a session key between the and .
- On receiving the information from , verifies the freshness of , cal-culates , , then verifies if , if it is valid, gets the session key .
4.5. Pseudo-Identity and Public Key Update Phase
4.6. Drone Revocation/Reissue Phase
5. Security Proof
5.1. Informal Security Proof
5.1.1. Replay Attack
5.1.2. Impersonation Attack
5.1.3. Drone Physical Capture Attack
5.1.4. GS Physical Capture Attack
5.1.5. Forward and Backward Secrecy
5.1.6. MITM Attack
5.1.7. Anonymity and Untraceability
5.1.8. Desynchronization Attack
5.1.9. ESL Attack
5.1.10. Insider Attack
5.2. Formal Security Proof
- : This game simulates the real attack first launched by A. According to the definition, we get:
- : This game simulates the eavesdropping attack. A gets all the messages transmitted publicly. Then, A guesses the random bit r. However, because of the ECDLP, the attacker cannot judge the association between the captured messages and the session keys. Therefore, we get:
- : This game simulates the collision attack on the transcripts and hash results, according to the definition of the birthday paradox, the probability of hash collision is less than , and the collision probability of other transcripts is less , Therefore, we have:
- : This game simulates A executes Corrupt() and CorruptGS() to obtain the stored information in the drone and in GS, where , . If A wants to obtain the valuable parameters, he must guess or break PUF. Suppose the probability of breaking PUF by A is . Therefore, we have:
- : A can obtain , , which are used for session keys agreements. This game simulates that A calculates the session keys according to the transcripts. We have:The session keys are generated independently and randomly. Hence, the advantage of guessing r is equal to guessing the session key. We have:
5.3. Security Comparison
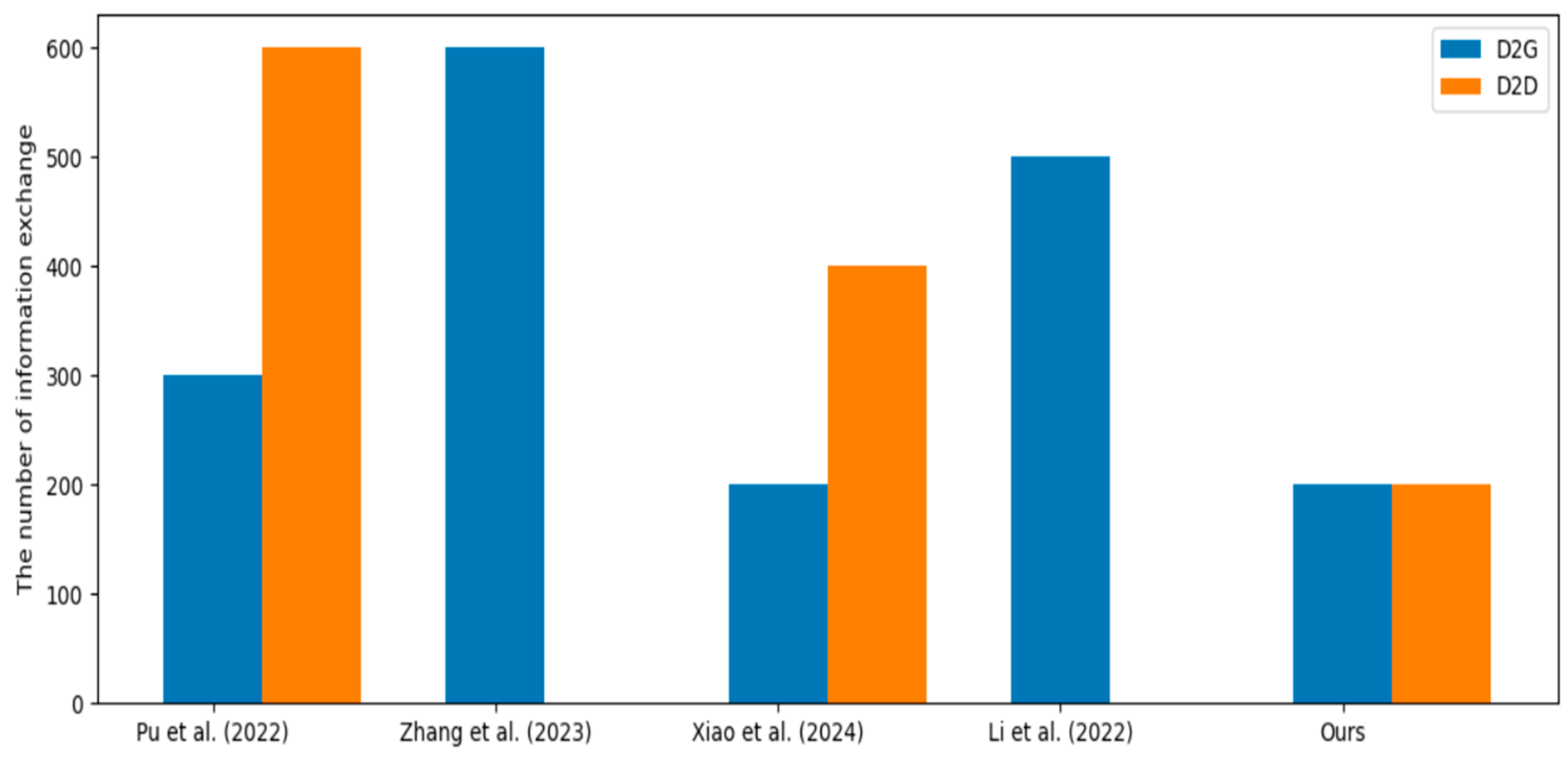
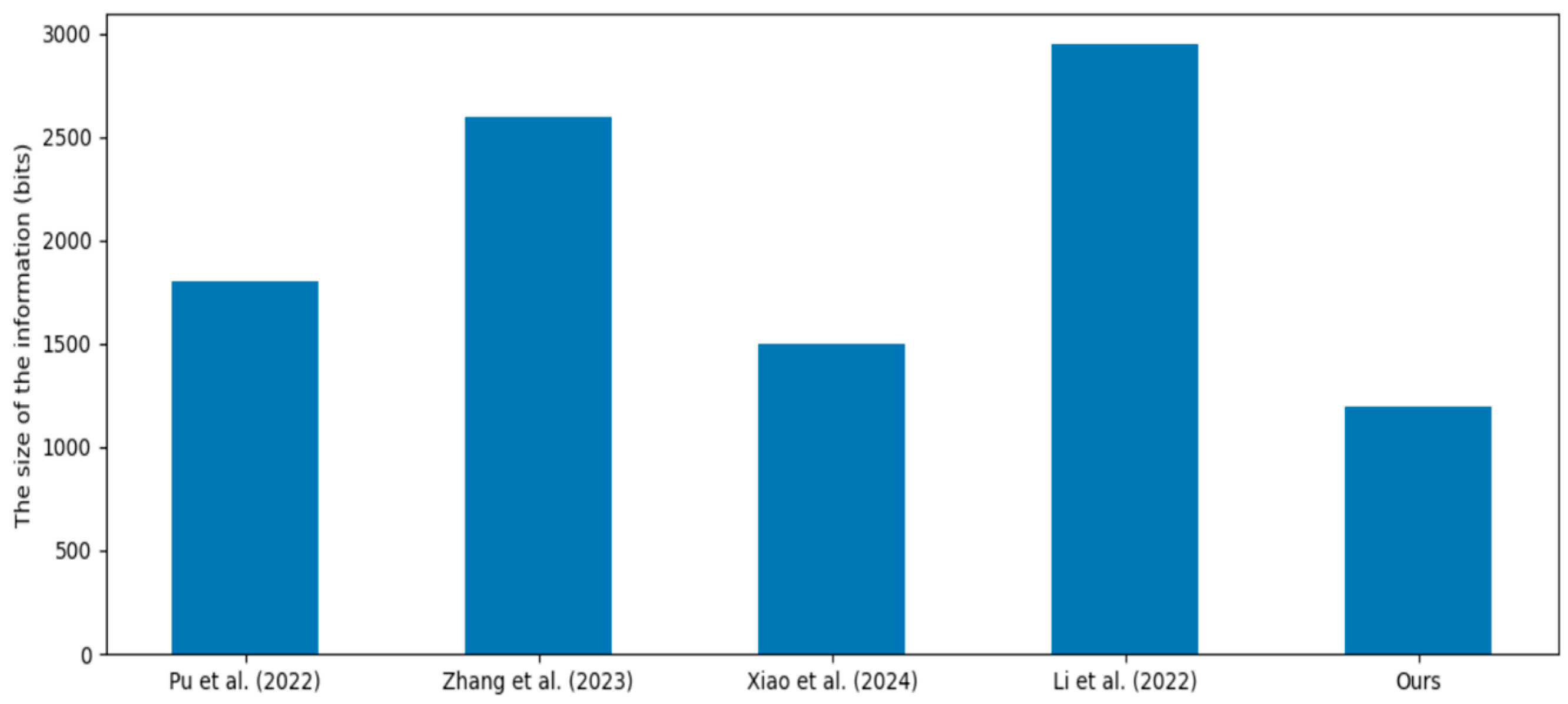
6. Performance Analysis
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Rodrigues, M.; Amaro, J.; Osório, F.S.; RLJC, B.K. Authentication methods for UAV communication. In Proceedings of the 2019 IEEE Symposium on Computers and Communications (ISCC), Barcelona, Spain, 29 June–3 July 2019; pp. 1210–1215. [Google Scholar]
- Chamola, V.; Hassija, V.; Gupta, V.; Guizani, M. A comprehensive review of the COVID-19 pandemic and the role of IoT, drones, AI, blockchain, and 5G in managing its impact. IEEE Access 2020, 8, 90225–90265. [Google Scholar] [CrossRef]
- Liu, X.; Li, Z.; Zhao, N.; Meng, W.; Gui, G.; Chen, Y.; Adachi, F. Transceiver design and multihop D2D for UAV IoT coverage in disasters. IEEE Internet Things J. 2018, 6, 1803–1815. [Google Scholar] [CrossRef]
- Gharibi, M.; Boutaba, R.; Waslander, S.L. Internet of drones. IEEE Access 2016, 4, 1148–1162. [Google Scholar] [CrossRef]
- Hall, R.J. An internet of drones. IEEE Internet Comput. 2016, 20, 68–73. [Google Scholar] [CrossRef]
- Abdelmaboud, A. The internet of drones: Requirements, taxonomy, recent advances, and challenges of research trends. Sensors 2021, 21, 5718. [Google Scholar] [CrossRef] [PubMed]
- Wazid, M.; Das, A.K.; Kumar, N.; Vasilakos, A.V.; Rodrigues, J.J.P.C. Design and analysis of secure lightweight remote user authentication and key agreement scheme in internet of drones deployment. IEEE Internet Things J. 2018, 6, 3572–3584. [Google Scholar] [CrossRef]
- Yang, W.; Wang, S.; Yin, X.; Wang, X.; Hu, J. A review on security issues and solutions of the internet of drones. IEEE Open J. Comput. Soc. 2022, 3, 96–110. [Google Scholar] [CrossRef]
- He, D.; Chan, S.; Guizani, M. Communication security of unmanned aerial vehicles. IEEE Wirel. Commun. 2016, 4, 134–139. [Google Scholar] [CrossRef]
- Altawy, R.; Youssef, A.M. Security, privacy, and safety aspects of civilian drones: A survey. ACM Trans. Cyber-Phys. Syst. 2016, 1, 1–25. [Google Scholar] [CrossRef]
- Pu, C. Jamming-resilient multipath routing protocol for flying ad hoc networks. IEEE Access 2018, 6, 68472–68486. [Google Scholar] [CrossRef]
- Michailidis, E.T.; Vouyioukas, D. A review on software-based and hardware-based authentication mechanisms for the internet of drones. Drones 2022, 6, 41. [Google Scholar] [CrossRef]
- Huang, Y.; Mu, J.; Wang, Y.; Zhao, R. A Review of Authentication Methods in Internet of Drones. In Proceedings of the 2023 International Conference on Networking and Network Applications (NaNA), Qingdao, China, 18–21 August 2023; pp. 7–12. [Google Scholar]
- Ashrif, F.F.; Sundararajan, E.A.; Ahmad, R.; Hasan, M.K.; Yadegaridehkordi, E. Survey on the authentication and key agreement of 6LoWPAN: Open issues and future direction. J. Netw. Comput. Appl. 2024, 221, 103759. [Google Scholar] [CrossRef]
- Mall, P.; Amin, R.; Das, A.K.; Leung, M.T.; Choo, K.K.R. PUF-based authentication and key agreement protocols for IoT, WSNs, and smart grids: A comprehensive survey. IEEE Internet Things J. 2022, 9, 8205–8228. [Google Scholar] [CrossRef]
- Hasan, M.K.; Weichen, Z.; Safie, N.; Ahmed, F.R.A.; Ghazal, T.M. A Survey on Key Agreement and Authentication Protocol for Internet of Things Application. IEEE Access 2024, 12, 61642–61666. [Google Scholar] [CrossRef]
- Soni, M.; Singh, D.K. LAKA: Lightweight authentication and key agreement protocol for internet of things based wireless body area network. Wirel. Pers. Commun. 2022, 127, 1067–1084. [Google Scholar]
- Pu, C.; Wall, A.; Choo, K.K.R.; Ahmed, I.; Lim, S. A lightweight and privacy-preserving mutual authentication and key agreement protocol for Internet of Drones environment. IEEE Internet Things J. 2022, 9, 9918–9933. [Google Scholar] [CrossRef]
- Hajian, R.; Haghighat, A.; Erfani, S.H. A secure anonymous D2D mutual authentication and key agreement protocol for IoT. Internet Things 2022, 18, 100493. [Google Scholar] [CrossRef]
- Jan, S.U.; Qayum, F.; Khan, H.U. Design and analysis of lightweight authentication protocol for securing IoD. IEEE Access 2021, 9, 69287–69306. [Google Scholar] [CrossRef]
- Cheon, J.H.; Han, K.; Hong, S.M.; Kim, H.J.; Kim, J.; Kim, S.; Seo, H.; Shim, H.; Song, Y. Toward a secure drone system: Flying with real-time homomorphic authenticated encryption. IEEE Access 2018, 6, 24325–24339. [Google Scholar] [CrossRef]
- Jiang, C.; Fang, Y.; Zhao, P.; Panneerselvam, J. Intelligent UAV identity authentication and safety supervision based on behavior modeling and prediction. IEEE Trans. Ind. Inform. 2020, 16, 6652–6662. [Google Scholar] [CrossRef]
- Wang, W.; Han, Z.; Gadekallu, T.R.; Raza, S.; Tanveer, J.; Su, C. Lightweight blockchain-enhanced mutual authentication protocol for UAVs. IEEE Internet Things J. 2023, 11, 9547–9557. [Google Scholar] [CrossRef]
- García, J.C.P.; Benslimane, A.; Braeken, A.; Su, Z. μTesla-Based Authentication for Reliable and Secure Broadcast Communications in IoD Using Blockchain. IEEE Internet Things J. 2023, 10, 18400–18413. [Google Scholar] [CrossRef]
- Tan, Y.; Wang, J.; Liu, J.; Kato, N. Blockchain-assisted distributed and lightweight authentication service for industrial unmanned aerial vehicles. IEEE Internet Things J. 2022, 9, 16928–16940. [Google Scholar] [CrossRef]
- Zhang, Y.; He, D.; Li, L.; Chen, B. A lightweight authentication and key agreement scheme for Internet of Drones. Comput. Commun. 2020, 154, 455–464. [Google Scholar] [CrossRef]
- Hussain, S.; Farooq, M.; Alzahrani, B.A.; Albeshri, A.; Alsubhi, K.; Chaudhry, S.A. An efficient and reliable user access protocol for Internet of Drones. IEEE Access 2023, 11, 59688–59700. [Google Scholar] [CrossRef]
- Yu, S.; Das, A.K.; Park, Y. SLAP-IoD: Secure and lightweight authentication protocol using physical unclonable functions for internet of drones in smart city environments. IEEE Trans. Veh. Technol. 2022, 71, 10374–10388. [Google Scholar] [CrossRef]
- Alladi, T.; Venkatesh, V.; Chamola, V.; Chaturvedi, N. Drone-MAP: A novel authentication scheme for drone-assisted 5G networks. In Proceedings of the IEEE INFOCOM 2021-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Vancouver, BC, Canada, 10–13 May 2021; pp. 1–6. [Google Scholar]
- Wu, T.; Guo, X.; Chen, Y.; Kumari, S.; Chen, C. Amassing the security: An enhanced authentication protocol for drone communications over 5G networks. Drones 2021, 6, 10. [Google Scholar] [CrossRef]
- Bansal, G.; Chamola, V.; Sikdar, B. SHOTS: Scalable secure authentication-attestation protocol using optimal trajectory in UAV swarms. IEEE Trans. Veh. Technol. 2022, 71, 5827–5836. [Google Scholar] [CrossRef]
- Javed, S.; Khan, M.A.; Abdullah, A.M.; Alsirhani, A.; Alomari, A.; Noor, F.; Ullah, I. An efficient authentication scheme using blockchain as a certificate authority for the internet of drones. Drones 2022, 6, 264. [Google Scholar] [CrossRef]
- Mishra, A.K.; Wazid, M.; Singh, D.P.; Das, A.K.; Singh, J.; Vasilakos, A.V. Vasilakos. Secure Blockchain-Enabled Authentication Key Management Framework with Big Data Analytics for Drones in Networks Beyond 5G Applications. Drones 2023, 7, 508. [Google Scholar] [CrossRef]
- Zhang, S.; Liu, Y.; Han, Z.; Yang, Z. A lightweight authentication protocol for UAVs based on ECC scheme. Drones 2023, 7, 315. [Google Scholar] [CrossRef]
- Xiao, Y.; Tao, Y. SLAKA-IoD: A Secure and Lightweight Authentication and Key Agreement Protocol for Internet of Drones. Drones 2024, 8, 374. [Google Scholar] [CrossRef]
- Li, L.; Lian, X.; Wang, Y.; Tan, L. CSECMAS: An efficient and secure certificate signing based elliptic curve multiple authentication scheme for drone communication networks. Appl. Sci. 2022, 12, 9203. [Google Scholar] [CrossRef]
- Bansal, G.; Sikdar, B. Location aware clustering: Scalable authentication protocol for UAV swarms. IEEE Netw. Lett. 2021, 3, 177–180. [Google Scholar] [CrossRef]
- Cho, G.; Cho, J.; Hyun, S.; Kim, H. SENTINEL: A Secure and Efficient Authentication Framework for Unmanned Aerial Vehicles. Appl. Sci. 2020, 10, 3149. [Google Scholar] [CrossRef]
- Yu, S.; Lee, J.; Sutrala, A.K.; Das, A.K.; Park, Y. LAKA-UAV: Lightweight authentication and key agreement scheme for cloud-assisted Unmanned Aerial Vehicle using blockchain in flying ad-hoc networks. Comput. Netw. 2023, 224, 109612. [Google Scholar] [CrossRef]
- Bhattarai, I.; Pu, C.; Choo, K.-K.R.; Korać, D. A Lightweight and Anonymous Application-Aware Authentication and Key Agreement Protocol for the Internet of Drones. IEEE Internet Things J. 2024, 11, 19790–19803. [Google Scholar] [CrossRef]
- Alkatheiri, M.S.; Saleem, S.; Alqarni, M.A.; Aseeri, A.O.; Chauhdary, S.H.; Zhuang, Y. A Lightweight Authentication Scheme for a Network of Unmanned Aerial Vehicles (UAVs) by Using Physical Unclonable Functions. Electronics 2022, 11, 2921. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A. On the security of public key protocols. IEEE Trans. Inf. Theory 1983, 29, 198–208. [Google Scholar] [CrossRef]
- Canetti, R.; Krawczyk, H. Universally composable notions of key exchange and secure channels. In Proceedings of the Advances in Cryptology—EUROCRYPT 2002: International Conference on the Theory and Applications of Cryptographic Techniques, Amsterdam, The Netherlands, 28 April–2 May 2002; pp. 337–351. [Google Scholar]



| Scheme | Year | Cryptographic Techniques | Advantages | Limits |
|---|---|---|---|---|
| [19] | 2021 | Utilize hash message authentication code | Protects the communication between drone and drone | Authentication requires GS |
| [20] | 2018 | Utilize homomorphic encryption | Guarantees the security against eavesdropping and forgery attacks | Vulnerable to session key leaks and insider attacks |
| [21] | 2020 | Utilize Kalman Trajectory Predicting Algorithm | Provides the government with intelligent control | Does not resist physical capture attack |
| [28] | 2019 | Utilize ECC | Provides mutual authentication between base station devices and UAVs | Does not resist physical capture attack |
| [6] | 2019 | Utilize fuzzy extractor | Provides three-factor security | Does not guarantee perfect backward secrecy |
| [27] | 2023 | Utilize one-way hash function | Provides mutual authentication for user and drone | Does not resist physical capture attack |
| [23] | 2023 | Utilize one-way hash function | Provides a lightweight blockchain-enhanced mutual authentication | Does not resist physical capture attack |
| [24] | 2023 | Utilize one-way hash function | Utilizes blockchain to manage drone authentication | Authentication requires GS |
| [33] | 2023 | Utilize one-way hash function | Provides an authentication key management framework with big data analytics | Does not resist physical capture attack |
| [34] | 2023 | Utilize ECC | Provides drone-GS authentication | Does not resist physical capture attack |
| [35] | 2024 | Utilize one-way hash function | Provides low computation overload | Does not resist GS capture attack |
| [36] | 2022 | Utilize ECC | Establishes a secure session between the GS and a UAV | Substantial computational overhead |
| [37] | 2021 | Utilize PUF | Uses K-Means clustering to construct UAV clusters | Does not resist replay attack, anonymity, and perfect forward secrecy |
| Notation | Description |
|---|---|
| GS | Ground station |
| The generator of the elliptic curve | |
| Private and public key of GS | |
| Private and public key of drone | |
| Physical unclonable function | |
| The challenge and response pair | |
| Hash function | |
| XOR operation | |
| Concatenation | |
| Timestamp of current time | |
| Symmetric encryption/decryption function | |
| The session key between drone and GS | |
| The session key between drones |
| Feature | [17] | [34] | [35] | [37] | Ours |
|---|---|---|---|---|---|
| A1 | ✗ | ✗ | ✔ | ✔ | ✔ |
| A2 | ✗ | ✔ | ✔ | ✗ | ✔ |
| A3 | ✗ | ✔ | ✔ | ✔ | ✔ |
| A4 | ✔ | ✔ | ✔ | ✔ | ✔ |
| A5 | ✗ | ✗ | ✗ | ✗ | ✔ |
| A6 | ✔ | ✔ | ✔ | ✔ | ✔ |
| A7 | ✔ | ✔ | ✔ | ✗ | ✔ |
| A8 | ✗ | ✔ | ✗ | ✗ | ✔ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xie, Q.; Zhang, J. Lightweight Drone-to-Ground Station and Drone-to-Drone Authentication Scheme for Internet of Drones. Symmetry 2025, 17, 556. https://doi.org/10.3390/sym17040556
Xie Q, Zhang J. Lightweight Drone-to-Ground Station and Drone-to-Drone Authentication Scheme for Internet of Drones. Symmetry. 2025; 17(4):556. https://doi.org/10.3390/sym17040556
Chicago/Turabian StyleXie, Qi, and Jilin Zhang. 2025. "Lightweight Drone-to-Ground Station and Drone-to-Drone Authentication Scheme for Internet of Drones" Symmetry 17, no. 4: 556. https://doi.org/10.3390/sym17040556
APA StyleXie, Q., & Zhang, J. (2025). Lightweight Drone-to-Ground Station and Drone-to-Drone Authentication Scheme for Internet of Drones. Symmetry, 17(4), 556. https://doi.org/10.3390/sym17040556