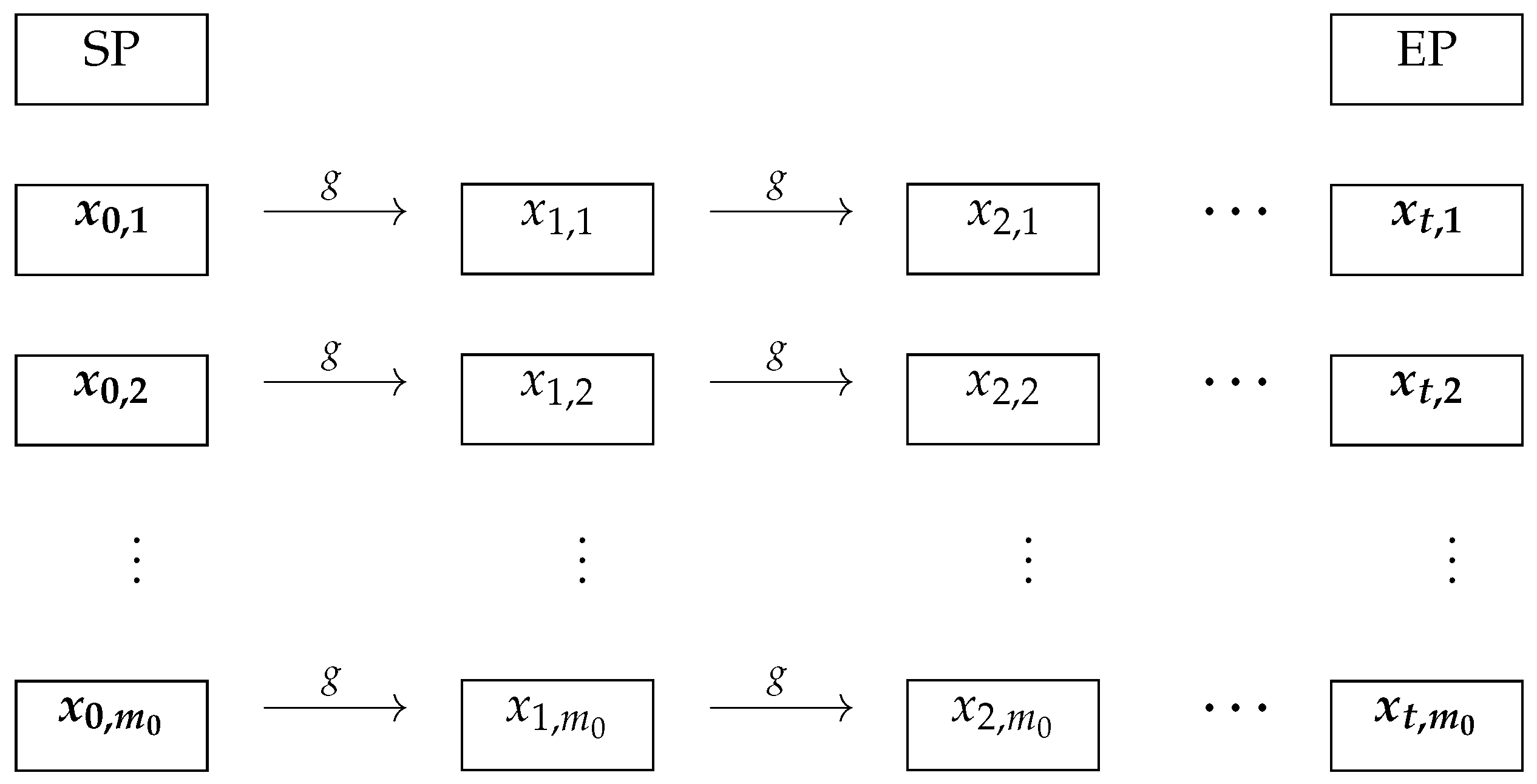2.1. Background
Green and Schroll introduced Brauer configuration algebras [
12] and Brauer graph algebras [
20] between 2017 and 2018 to investigate algebras of wild and tame representation types. Soon afterward, Espinosa [
21] introduced the notion of specialized Brauer messages to study snake graphs and their perfect matchings, as well as indecomposable Kronecker modules [
22] and the energy of
-matrices arising from some suitable graphs [
23].
Brauer analysis was introduced by Cañadas et al. [
13] to study quantum entanglement states based on Brauer messages and perfect matchings of the graphs associated with such states. In this work, the authors studied algebraic invariants associated with Brauer configuration algebras (
) induced by quantum entangled states of type
(Greenberger–Horne–Zeilinger) defined by the following identities:
where
n is the number of particles and
d is the dimension for every particle. In [
13], it was proven that the dimensions of
and its center (
) are given by the following identities:
Brauer analysis has also been applied to analyze several topics in cybersecurity [
24]—in particular, the Advanced Encryption Standard (AES) [
25].
Extended Brauer analysis, which embraces the study of some degree-based entropies, has been applied to analyze Dynkin and Euclidean diagrams [
14]. Such analysis was used in [
26] to define realizable branch data associated with some branched covering over some closed, connected surfaces.
Along with the works proposed by Hellman et al. [
1,
2,
3,
4,
5,
6,
7,
8,
9,
10,
11] mentioned in the Introduction of this paper, regarding the use of TMTOs to attack several cryptosystems, we also remember that van den Broek and Poll [
27] devised a TMTO attack for the A5/1 cipher used in GSM, which combines both distinguished points and rainbow tables.
Drinfeld et al. [
28] proposed the study of set-theoretical solutions of the YBE (see (
1)). In particular, non-degenerate, involutive set-theoretical solutions of the YBE were presented by Etingof et al. [
29] and Gateva-Ivanova and Van den Bergh [
30] by associating a suitable group (
) with the solution
of the Yang–Baxter equation.
This paper proposes set-theoretical solutions of the Yang–Baxter equation based on the Brauer analysis realized for the directed graphs defined by Stinson and Paterson [
11] in their TMTO attack.
Rump [
31] introduced another line of investigation to tackle the problem of classifying the non-degenerate involutive set-theoretical solutions of the YBE. It is worth noting that braces constitute one of the most important investigation lines of such an equation. For instance, Ballester et al. [
19] found set-theoretical solutions based on braces and Brauer configuration algebras [
32].
2.2. TMTO Attacks
This section describes a TMTO for a chosen plaintext attack proposed by Stinson and Paterson in [
11].
Figure 1 shows a standard diagram of a rainbow table or rainbow matrix for a TMTO. Elements in the first column (
with
) are chosen arbitrarily but must differ. They are called
start points (SPs). The elements in the last column of the matrix are called
end points (EPs). The combination of SPs and EPs is called a
table [
8].
A chain depicts the collection of elements of the same row. Functions (
g) with
from the
search spaceA to themselves are composition functions of the following form:
where
is a suitable reduction function and
h is the function that the algorithm aims to invert. Functions (
g) are called
hash-reduction functions.
Let be a cryptosystem or cryptographic system that possesses the perfect secrecy property, where denotes the set of plaintexts, ciphertexts and keys, respectively. It should be noted that cryptosystems that achieve perfect secrecy are considered unbreakable.
The following result for cryptosystems with the perfect secrecy property is proven in [
11].
Theorem 1 ([
11], Theorem 3.4)
. Suppose is a cryptosystem where . Then, the cryptosystem provides perfect secrecy if and only if every key is used with equal probability (), and for every and every , there is a unique key (K) such that . Since achieves perfect secrecy, it holds that for any and , where denotes the probability that the probability distribution associated with the set of plaintexts attains a value of x and denotes the conditional probability of attaining a plaintext value of x given a ciphertext (y). In such a case, for a given encryption function () associated with a key (), it holds that , provided that . Furthermore, .
In the sequel, we describe the TMTO introduced by Stinson and Paterson [
11] to conduct a chosen plaintext attack against a cryptosystem with the perfect secrecy property. We recall that in these types of attacks, the opponent obtains temporary access to the encryption machinery [
11]. Hence, the opponentcan choose a plaintext string (
x) and construct the corresponding ciphertext string (
y).
Let
x be a fixed plaintext and define a function (
) such that
. We define a directed graph or quiver (
) whose sets of vertices (
) and arrows (
) are defined in such a way that
According to Stinson and Paterson [
11],
and
g have the following properties:
consists of the union of disjoint directed cycles.
T is a desired time parameter.
Suppose we have a set of elements () such that, for every element (), either is contained in a cycle of a length of, at most, T or there exists an element () such that the distance from to in is, at most, T; then, there exists a set (Z) satisfying the following properties:
,
is .
Stinson and Paterson [
11] introduced the pseudo-code of an algorithm (Algorithm 1) to find a key (
K), given
. It finds
K in, at most,
T steps, with the time–memory trade-off represented by
, which means that in the worst case, the algorithm recovers a key in
N steps (see Example 1 in
Section 2.6 of this paper).
This paper introduces Brauer configuration algebras () induced by quivers of the form of .
| Algorithm 1: Time–memory trade-off(y) |
| |
|
|
|
|
|
2.3. Multisets and Brauer Configuration Algebras
This section recalls some definitions and notations dealing with multisets, Brauer configurations, and Brauer configuration algebras. Examples are presented in Example 1 in
Section 2.6. The authors refer the interested reader to [
12,
14,
26,
33,
34] for more information on these topics.
A
multiset is a pair
consisting of a set (
M) and a map (
) from
M to a non-negative integers set (
) such that
[
33,
34].
is said to be a
multiplicity function in the sense that
provides the number of times or occurrences of an element
m in
M. Roughly speaking, multisets allow for element repetition.
If is a multiset and , then is determined by a fixed word in the form of , where is a permutation of .
In [
14,
26], Cañadas et al. defined multisets of type
M. In such a case, if
and
is a collection of
multisets with
for
, then the collection of multisets (
) is said to be of type
M if it satisfies the following conditions.
If and is the collection of all sets () that contain m, then is endowed with a well-order or linear-order (<)with the form of , where is an expansion of set with the of form , is the multiplicity of m in , and . Henceforth, we assume the notation of instead of if no confusion arises.
If
denotes the successor of
in
, then it holds that
The
valency (
) of an element (
) is expressed by the following sum:
is endowed with a map (
) such that
, where
is the set of positive integers.
Chains in the form of are said to be successor sequences. Each successor sequence () defined by an element () gives rise to a family of equivalent circular orderings by adding a new relation in the form of (). Note that is the successor sequence of an element () with .
Remark 1. In [14,26] multiset collections of type M assume that in successor sequences (). This paper does not assume such an order for them. Collections of multisets (
) of type
M give rise to so-called Brauer quivers [
12] (
) whose set of vertices (
) is in bijective correspondence with multisets (
) (Green and Schroll [
12] called
polygons, the elements of
and vertices, the elements of
M). Arrows in
are represented by subsets in the form of
, i.e., these subsets define arrows in the form of
. In particular, circular orderings defined by successor sequences induce cycles (special cycles in the sense of Green and Schroll [
12]) in
. If
, then the special cycle defined by
is in the form of
or
if
.
Collections of multisets of type
M are
Brauer configurations as defined by Green and Schroll in [
12]. According to them, these are quadruples in the form of
, where
M is a set of vertices,
is a collection or set of polygons,
is multiplicity function (defined as
), and
is an orientation defined by the successor sequences.
According to Green and Schroll [
12] a vertex (
) is truncated (non-truncated), provided that
(
). Thus, a collection of multisets of type
M, also called Brauer configurations of type
M, has no truncated vertices. In such a case, they are said to be
reduced. Moreover, a Brauer configuration is
connected if its induced Brauer quiver is connected.
This paper restricts the general definitions of Brauer configuration algebras given by Green and Schroll in [
12] to those induced by Brauer configurations (or collections of multisets) of type
M.
Given an algebraically closed field (k), a Brauer configuration algebra of type M is a bound quiver algebra () defined by a Brauer quiver () induced by a Brauer configuration () of type M and bounded by an admissible ideal () generated by relations of the following types:
if m and belong to the same multiset; ; and and are special cycles at m and , respectively. These relations are said to be of type .
if is a special cycle at vertex and f is the first arrow of . In particular, if . These are relations of type .
Relations of type have the form of , if ; ; ; ; and and are special cycles at m and , respectively.
Cañadas et al. [
14] introduced the
covering graph (
) induced by a Brauer configuration (
) with a set of polygons (
) as the set of vertices (
) and an edge (
) connecting two polygons if, for some
, there exists a successor sequence (
) for which either
or
(in other words,
, provided that, for some
,
is a covering in the corresponding successor sequence (
)). We note that covering graphs not not have multiple edges or loops.
Given a subset () of the set of vertices () of a graph , a hair graph () with respect to A is obtained from by attaching to each point (, ) a linear path with vertices.
Remark 2. The following properties of Brauer configuration algebras were introduced by Green and Schroll [12], Sierra [35], and Cañadas et al. [14] (see [12] Theorem B, Proposition 2.7, Theorem 3.10, Corollary 3.12, [35] Theorem 4.9, and [14] Theorem 8). Any Brauer configuration algebra () induced by a Brauer configuration () is multiserial, and there exists a bijective correspondence between the set of indecomposable projective modules and the set of multisets or polygons ().
The number of summands in the heart () of an indecomposable projective module equals the number of non-truncated vertices in the corresponding polygon, where denotes the socle of the indecomposable projective module (P), which is generated by its corresponding simple submodules.
Green and Schroll [12] proposed the following Formula (8) for the dimension () of a Brauer configuration algebra () induced by a Brauer configuration (). Sierra [35] proposed the following Formula (9) for the dimension () of the center () of a Brauer configuration algebra () induced by a reduced and connected Brauer configuration () (Brauer configurations of type M are reduced). We note that any graph () gives rise to a Brauer configuration () of type M, where and . Cañadas et al. [14] proved that the covering graph () induced by a Brauer configuration () defined by a graph () is isomorphic to if and only if is a disjoint union of copies of connected hair graphs of type , where is an n-point cycle and .
2.4. Yang–Baxter Equation
As described before, the Yang–Baxter equation was introduced by Yang [
15] in 1967 and Baxter [
16] in 1972. Recall that if
k is an algebraically closed field of characteristic zero and
V is a
k-vector space, then a linear automorphism (
) is a solution of the Yang–Baxter equation, provided that it satisfies the following
braided relation [
22]:
R is a solution of the quantum Yang–Baxter equation if and only if
where
indicates
R acting on the
ith and
jth tensor factors and the identity on the remaining factor [
17].
Since a complete classification of the Yang–Baxter equation is an open problem, several approaches have been introduced to tackle it. For instance, Drinfeld et al. [
28] introduced the notion of a set-theoretical solution of the Yang–Baxter equation (see (
1)). In such a case, for a given set (
X) and a map (
), the identity (
1) has the following form [
19]:
where maps
are defined as
and
, respectively.
Note that if
is defined in such a way that
, then a map (
) is a set-theoretical solution of the YBE if and only if
and
satisfy the quantum Yang–Baxter equation (
11) [
18,
29].
A bijective map () such that is involutive if . r is said to be left non-degenerate (right non-degenerate) if each map () () is bijective.
Rump [
31] introduced the notion of a brace to provide set-theoretical solutions of the Yang–Baxter equation, and Cañadas et al. proposed set-theoretical solutions of the Yang–Baxter equation based on braces and Brauer configuration algebras [
32].
This paper uses Brauer quivers arising from TMTO attacks as described by Stinson and Paterson [
11] to provide set-theoretical solutions of the Yang–Baxter equation.
2.6. Main Results
This section provides the main results presented in this paper; we start by providing an illustrative example of the definitions described in previous sections.
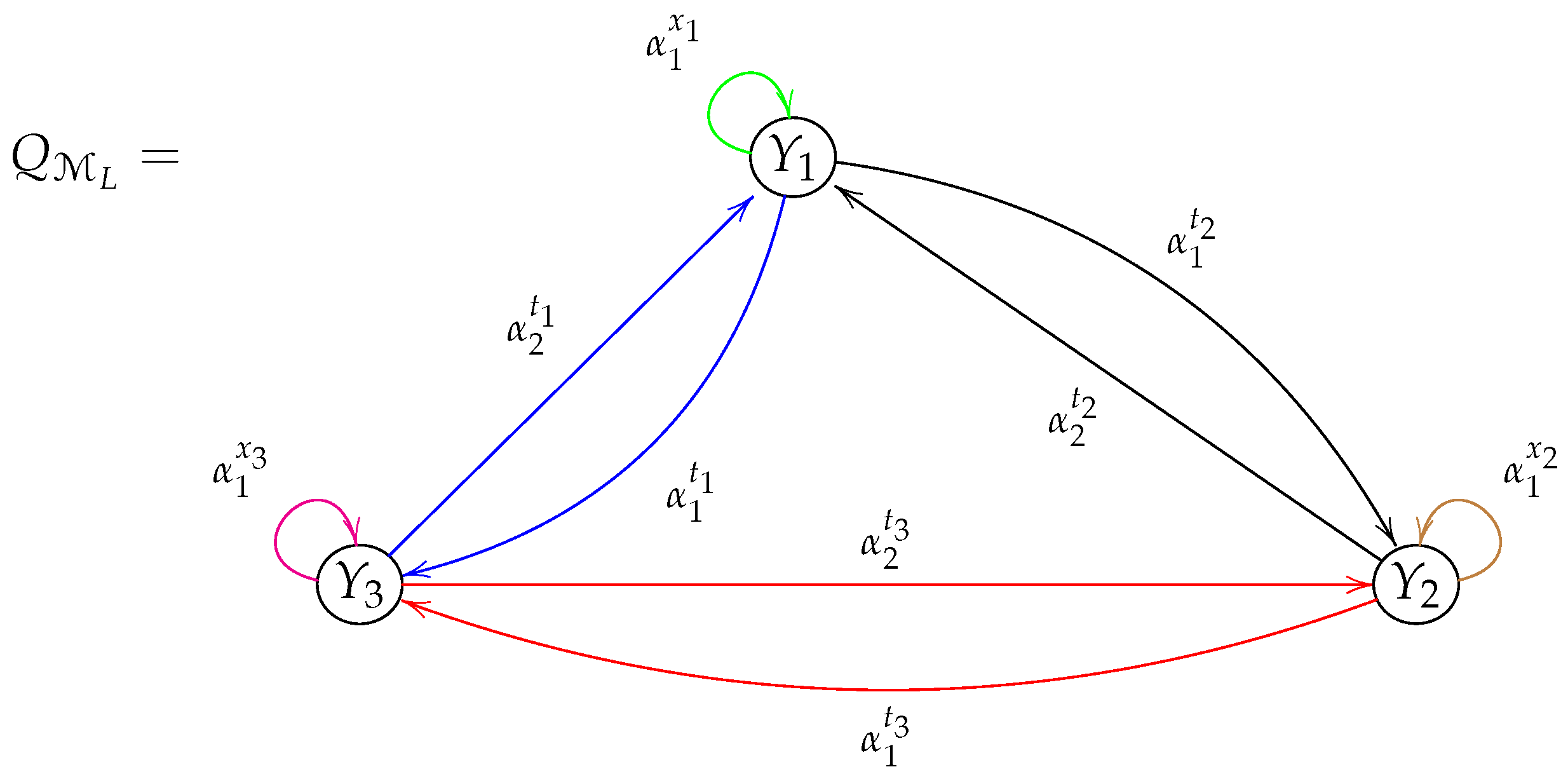
Example 1. Let us consider a Latin square cryptosystem () such that , whose rules of encryption and decryption are represented by rows of the Latin square (L) shown in Table 1, that is, . It is well known that achieves perfect secrecy, provided that every key is used with equal properties [11]. We define a Brauer configuration ()| of type M such that Then, , , . The successor sequences are defined as follows: Figure 2 shows the Brauer quiver induced by Brauer configuration . The Brauer configuration algebra () induced by Brauer configuration is a bound quiver algebra in the form of , where the admissible ideal () is generated by relations of three types. The following are examples of relations in .
; ; .
, ; , .
, ; , . , .
, if and .
, if and .
The Brauer configuration algebra () has the following properties:
is indecomposable as an algebra, provided that the Brauer quiver () is connected.
.
.
The covering graph () induced by the Brauer configuration () is isomorphic to the three-point cycle.
The following are entropies associated with the Brauer configuration () and the corresponding covering graph (G).
.
, provided that G is 2-regular.
. Note that is an approximation of the dimension of the Brauer configuration algebra (), where is a reduction of obtained by deleting vertices in M () with .
The quiver () induced by the time–memory trade-off for a chosen plaintext attack against the Latin square cryptosystem is isomorphic to the Brauer quiver (). The isomorphism can be realized by the following map between the corresponding sets of arrows ( and ). In this paper, it is assumed that . Thus, a Brauer analysis of the Brauer configuration () is also a Brauer analysis for the TMTO of a known plaintext attack against the Latin square cryptosystem.
Table 2 provides examples of the use of Algorithm 1 to recover a key from a plaintext in a Latin square cryptosystem of order ; columns x and y provide a plaintext and corresponding ciphertext. Column Z shows the set (Z) defined for a TMTO, and column provides all possible encryption values associated with the ciphertext (y). Column provides such a value after applying the first step of the algorithm, and column K shows the recovered key. The Latin squares used to apply the algorithm are presented in Appendix A (the corresponding Latin square is shown in Table 1). The following result allows us to define Brauer configuration algebras from quivers of type
(see (
5)).
Theorem 2. A quiver () (see (5)) defined by a TMTO for a chosen plaintext attack against a cryptosystem () that achieves perfect secrecy induces an integer partition ( of ), where , , is the number of all cycles in of size j, and . Proof. Firstly, note that contains, at most, cycles of size N and, at most, cycles of size 2. In particular, if x is a fixed plaintext (), then the set of arrows defines a permutation (), where denotes the symmetric group consisting of all N-element permutations, is a product of, at most, and cycles of size j; then, if all the encryption rules are chosen in such a way that the corresponding quiver () consists only of two cycles, it holds that (note that in this case, there exits such that for all j). Thus, for any other choice of the encryption rule, it holds that , provided that any permutation is a product of two cycles. This completes the proof. □
Next, Theorem 3 provides the properties of a Brauer configuration algebra induced by a quiver of type .
Theorem 3. Let be a quiver defined by a TMTO for a chosen plaintext attack against a cryptosystem () that achieves perfect secrecy; then, if has an associated integer partition () with and , it holds that induces a Brauer configuration algebra () with the following properties:
is indecomposable as an algebra.
Each indecomposable projective module () has summands, where is the out-degree of the vertex (x) in .
In particular, , where denotes the ith triangular number. .
The covering graph () induced by the Brauer quiver () is isomorphic to the N-vertex complete graph ().
Proof. Note that defines a Brauer configuration () of type M such that , , , if , . If , then , , and . The orientation () is represented by arrows and cycles of defined by pairs in the form of , with fixed. Under these circumstances, is the Brauer quiver induced by whose disjoint cycles are special cycles. It induces the Brauer configuration algebra (, where k is an algebraically closed field and is an admissible ideal generated by relations of type , and ).
In the sequel, we prove the different items proposed in the theorem.
Note that for fixed, the pairs define a permutation (), since the TMTO is applied to the complete set () and the Brauer configuration () is connected; therefore, the Brauer quiver () is connected.
Any element () is non-truncated and defines a unique cycle in up to equivalence. Thus, the out-degree of a vertex () in equals the number of its elements (x) for which . The result holds, provided that each polygon () contains a unique element () such that .
By definition, there are vertices with valency of for . Thus, . Moreover, the function expressed as from the set of algebras of type (induced by a TMTO for a chosen plaintext attack against the fixed cryptosystem ()) to the set of positive integers attains the minimum value () if for any . The maximum value () of is attained if elements in M have a valency of N. The result holds, taking into account that and .
We note that has vertices and N loops; then, .
Note that for a fixed key () and , . Thus, any pair () with can be obtained from an arrow in the form of for some . Such an arrow defines the edge ().
□
Corollary 1 provides the entropy values associated with the Brauer configuration () defined in Theorem 3.
Corollary 1. Let be the covering graph induced by the Brauer configuration of type M (); then, the following results hold:
.
.
, where .
Proof. Since G is regular, it holds that the number of edges in G is . Thus, and .
Since has N vertices with a valency of 1 and, for each j, there are vertices with a valency of , then has the proposed values by definition. This completes the proof. □
Theorem 4 provides set-theoretical solutions to the Yang–Baxter equation (see identity (
12)).
Theorem 4. Let and be a pair of Latin square cryptosystems such that and with and encryption rules and represented by Latin squares and , respectively, where is obtained from by applying a permutation () to the columns of and for any ; then, the map () such that , where and with and , is a set-theoretical solution of the Yang–Baxter equation.
Proof. Note that for
, it holds that
. Thus, if
, then the following identities hold:
Thus, and satisfy the set-theoretical Yang–Baxter equation. This completes the proof. □