Dynamic Evolution Analysis of Incentive Strategies and Symmetry Enhancement in the Personal-Data Valorization Industry Chain
Abstract
1. Introduction
2. Literature Review
2.1. The Value Chain for Personal-Data Monetization
2.2. Applications of Evolutionary-Game Theory
3. Model Construction
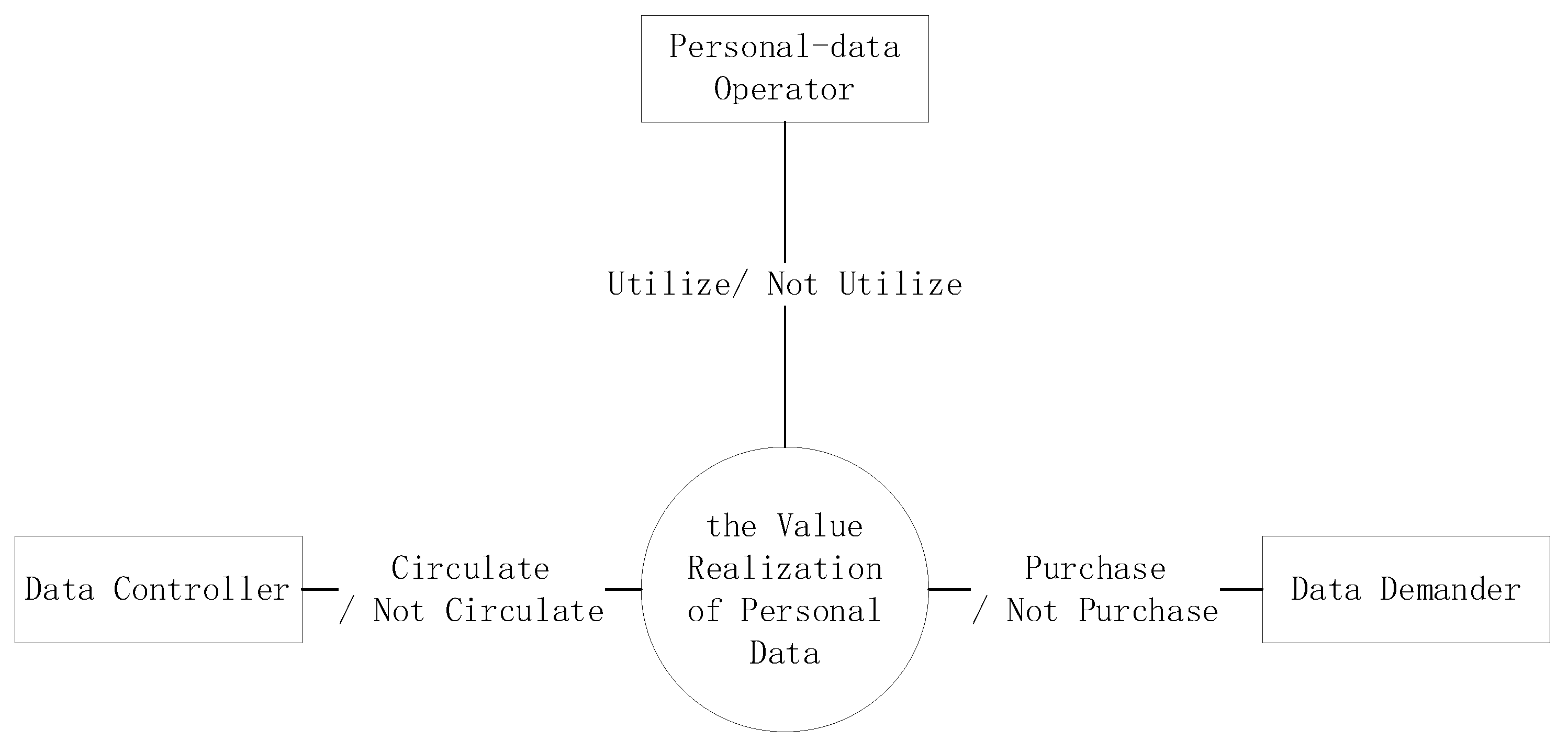
3.1. Problem Description
3.2. Model Assumptions
3.3. Payoff Matrix
4. Evolutionary-Game Model Analysis
Stability Assessment
5. Data Simulation and Results Analysis
5.1. Parameter Analysis
5.1.1. Impact of Initial Willingness
5.1.2. Impact of Breach Penalties on Personal-Data Operators and Data Demanders
5.1.3. Impact of Net Data-Product Revenue on Personal-Data Operators and Data Demanders
5.1.4. Impact of Losses from Personal-Data Privacy Breaches on the Three Parties
5.1.5. Impact of Breach Penalties and Data-Leakage Losses on the Personal-Data Operator
6. Conclusions and Policy Implications
6.1. Main Conclusions
- Initial willingness exerts a pronounced influence on strategy evolution. The initial willingness of data controllers, personal-data operators, and data demanders positively drives the evolution of data-trading behaviors. When the initial willingness of all three parties is high, the data controller’s choice to “circulate” data is only weakly affected by the willingness of operators or demanders, whereas the operator’s willingness to participate is strongly driven by the demanders’ intentions. Conversely, when initial willingness is low, all parties tend to withdraw from trading, creating a vicious cycle of “unwillingness to circulate.”
- Breach-penalty mechanisms regulate the equilibrium state. Penalties for breach constrain the behaviors of all parties and incentivize the ideal equilibrium of “circulate–utilize–purchase.” Stronger penalties impose tighter constraints on potential violators and better protect compliant parties, thereby enhancing the stability and sustainability of data trading. Excessively high penalties, however, may induce risk-averse parties to exit the market; hence, a balance must be struck between punitive severity and trading incentives.
- Net benefits exert a dual effect on participation willingness. An increase in the net benefit of data products markedly raises the willingness of operators and demanders to participate, boosting their confidence in data-value development. Yet overly high net benefits may trigger opportunistic behavior on the demand side, causing demanders to bypass operators and obtain data directly. Such circumvention undermines the operators’ willingness to participate and negatively affects the stability of the entire value chain.
- Privacy-leakage risk inhibits trading behaviors. The sensitivity of personal data and the high risk of privacy leakage significantly dampen the willingness of all parties to trade. When supporting infrastructure is weak and the trading environment insecure, the potential loss from a privacy incident is magnified, intensifying participants’ concerns. Breach-of-contract damages can still discipline stakeholders under low-to-moderate risk and encourage them to join the personal-data value chain; however, once external risk becomes sufficiently high, the contract ceases to have any deterrent effect.
6.2. Policy Recommendations
6.3. Research Limitations and Future Directions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
| Parameter | Meaning |
|---|---|
| Probability that the data controller elects to circulate personal data, | |
| Personal-data circulation payoff to the data controller when the data controller chooses to circulate and the personal-data operator chooses to exploit, | |
| Personal-data product payoff to the data controller when the data controller chooses to circulate, the personal-data operator chooses to exploit, and the data requester chooses to purchase, | |
| Aggregate cost incurred by the data controller when it chooses to circulate personal data, | |
| Breach-of-contract damages payable by the data controller for an unjustified withdrawal, | |
| Loss suffered by the data controller owing to privacy leakage arising from the circulation and use of personal data, | |
| Probability that the personal-data operator’s trading platform elects to exploit the data resource, | |
| Personal-data product payoff to the personal-data operator when the data controller chooses to circulate, the personal-data operator chooses to exploit, and the data requester chooses to purchase, | |
| Aggregate cost borne by the personal-data operator when the data controller chooses to circulate personal data and the personal-data operator chooses to exploit, | |
| Aggregate cost borne by the personal-data operator when the data controller chooses not to circulate personal data and the personal-data operator chooses to exploit, | |
| Breach-of-contract damages payable by the personal-data operator for an unjustified withdrawal, | |
| Loss suffered by the personal-data operator owing to privacy leakage arising from the circulation and use of personal data, | |
| Probability that the data requester elects to purchase the data resource or product, | |
| Payoff to the data requester from processing and analyzing personal data when the data controller chooses to circulate, | |
| Aggregate cost incurred by the data requester to collect, process, and use personal data when the data controller chooses to circulate and the personal-data operator chooses to exploit, | |
| Aggregate cost incurred by the data requester to collect, process, and use personal data when the data controller chooses to circulate and the personal-data operator chooses not to exploit, | |
| Breach-of-contract damages payable by the data requester for an unjustified withdrawal, | |
| Loss suffered by the data requester owing to privacy leakage arising from the circulation and use of personal data, |
References
- China Center for Information Industry Development. China Data Factor Market Development Report (2020–2021). Available online: http://www.100ec.cn/detail--6591616.html (accessed on 15 March 2025).
- Opinions of the General Office of the Communist Party of China Central Committee and the General Office of the State Council on Accelerating the Development and Utilization of Public Data Resources. Available online: https://www.gov.cn/zhengce/202410/content_6978911.htm (accessed on 25 February 2025).
- Ji, W.; Weng, Z. The Justification and Interpretation of Property Rights in Personal Data. Law Soc. Dev. 2024, 30, 168–189. [Google Scholar]
- Rao, C. The Legal Dilemma and Institutional Reshaping of Trust Mechanisms in Data Transactions. Acad. J. Zhongzhou 2025, 2, 73–80. [Google Scholar]
- Wan, F. Right Confirmation and Authorization Mechanism for Public Data: An Investigation Based on “Data Mitosis”. J. Dalian Univ. Technol. Soc. Sci. 2024, 45, 70–80. [Google Scholar]
- Zhang, S. On the Realization of the Structural Division of Data Property Rights in Law. Orient. Law 2023, 2, 73–85. [Google Scholar]
- Gu, W.; Fan, Z.; Fan, X. Research on the Personal Data Collection, Compliant Use and Management Enlightenment: Based on Text Analysis of Privacy Policies of Digital Resource Vendors. Inf. Stud. Theory Appl. 2025, 48, 56–64. [Google Scholar]
- Song, H. Types and Protection of Personal Data Property Rights. South China Financ. 2024, 12, 85–97. [Google Scholar]
- Wang, X. The Legal Application Dilemma and Outlet of the “Three New” Elements of the New Quality Productive Forces Enabled by Data Elements. Sci. Technol. Prog. Policy 2025, 42, 21–32. [Google Scholar]
- Cui, C. The Normative Expression of Residual Control over Data—Reflections on and Reconstruction of Personal Information Rights and Interests. Soc. Sci. J. 2024, 3, 120–129. [Google Scholar]
- Xiang, L.; Gao, Q. Analysis of the Characteristics, Basic Attributes and Contents of Personal Data Right in the Era of Big Data. Inf. Stud. Theory Appl. 2018, 41, 45–50+36. [Google Scholar]
- Xu, K. Three Approaches to Data Protection: Comment on the Case of Weibo Accusing Maimai of Unfair Competition. J. Shanghai Univ. Soc. Sci. 2017, 34, 15–27. [Google Scholar]
- Fei, A.; Chen, C. The Right of Withdraw of Consent in Personal Data Transactions—Conflict with the Contractual Bindingness as an Entry Point. J. Guangxi Univ. Philos. Soc. Sci. 2024, 46, 171–182. [Google Scholar]
- Xia, Q. A Study on the Construction of Private Law Institutions for Personal Data Transactions. China Leg. Sci. 2024, 5, 144–164. [Google Scholar]
- Cheng, X. On Legal Framework of the Personal Data Authorization Mechanism. Trib. Political Sci. Law 2023, 41, 77–89. [Google Scholar]
- Fu, X. On the Data Trust Model in the Distribution of Personal Data Interests. Orient. Law 2025, 1, 60–74. [Google Scholar]
- Wei, Y.; Chen, X.; Zou, X. Evolutionary Game Analysis of Personal Information Protection based on Data Sharing. Inq. Into Econ. Issue 2019, 12, 79–88. [Google Scholar]
- Wang, Z.; Deng, Y.; Liang, L. User Authorization Mechanism Design for Personal Data Circulation: An Evolutionary Game Among Individuals, Enterprises, and Government. J. Zhengzhou Univ. Philos. Soc. Sci. 2023, 56, 61–69. [Google Scholar]
- Wan, Z.; Vorobeychik, Y.; Xia, W.; Liu, Y.; Wooders, M.; Guo, J.; Yin, Z.; Clayton, E.W.; Kantarcioglu, M.; Malin, B.A. Using Game Theory to Thwart Multistage Privacy Intrusions When Sharing Data. Sci. Adv. 2021, 7, eabe9986. [Google Scholar] [CrossRef]
- Zhang, L.; Zhang, Z. Study on Data Entry Transaction and Trusted Circulation System Construction Based on Multi-agent Evolutionary Game Equilibrium Model. Comput. Sci. 2025, 52, 127–136. [Google Scholar]
- Liu, X. Personal Data Pricing for Large Language Models Based on Privacy compensation. Data Anal. Knowl. Discov. 2025, 9, 106–116. [Google Scholar]
- Shang, X.; Han, H.; Zhu, Z. Mechanism Design of Right to Earnings of Data Utilization Based on Evolutionary Game Model. Comput. Sci. 2021, 48, 144–150. [Google Scholar]
- Huang, W. Research on the Pricing of Personal Big Data Using Labor Game and Privacy Utility. Master’s Thesis, Zhongnan University of Economics and Law, Wuhan, China, 16 March 2025. [Google Scholar]
- Guo, X.; Wang, H.; Kong, N. Two-sided pricing strategy for personal health data trading under information asymmetry. J. Ind. Eng. Eng. Manag. 2022, 36, 129–139. [Google Scholar]
- Su, Q.; Ji, L. The Coordination Mechanism of Medical Data Sharing Based on Stochastic Evolutionary Game. Inf. Sci. 2023, 41, 37–47. [Google Scholar]
- Huang, Z.; Xiong, H. Evolution of Users’ Knowledge Sharing and Hiding Behaviors in Online Health Community. Data Anal. Knowl. Discov. 2023, 7, 125–139. [Google Scholar]
- Alexander, J.M. Evolutionary Game Theory. In The Stanford Encyclopedia of Philosophy; Zalta, E.N., Ed.; Metaphysics Research Lab, Stanford University: Stanford, CA, USA, 2021. [Google Scholar]





| Data Controllers | Personal-Data Operators | Data Demanders | |
|---|---|---|---|
| Purchase | Not Purchase | ||
| Circulate | Utilize | , , | , , |
| Not Utilize | , , | , , | |
| Not Circulate | Utilize | , , | , , |
| Not Utilize | , , | , , | |
| Equilibrium Point | Stability Analysis | |||
|---|---|---|---|---|
| ESS | ||||
| Unstable | ||||
| Unstable | ||||
| Unstable | ||||
| Saddle OR ESS | ||||
| Saddle OR ESS | ||||
| Unstable | ||||
| Saddle OR ESS |
| Parameter | ||||||||
| Initial Value | 10 | 15 | 5 | 4 | 5 | 25 | 12 | 18 |
| Parameter | ||||||||
| Initial Value | 7 | 5 | 15 | 10 | 12 | 2 | 5 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ma, J.; Yu, J.; Cheng, Y. Dynamic Evolution Analysis of Incentive Strategies and Symmetry Enhancement in the Personal-Data Valorization Industry Chain. Symmetry 2025, 17, 1639. https://doi.org/10.3390/sym17101639
Ma J, Yu J, Cheng Y. Dynamic Evolution Analysis of Incentive Strategies and Symmetry Enhancement in the Personal-Data Valorization Industry Chain. Symmetry. 2025; 17(10):1639. https://doi.org/10.3390/sym17101639
Chicago/Turabian StyleMa, Jun, Junhao Yu, and Yingying Cheng. 2025. "Dynamic Evolution Analysis of Incentive Strategies and Symmetry Enhancement in the Personal-Data Valorization Industry Chain" Symmetry 17, no. 10: 1639. https://doi.org/10.3390/sym17101639
APA StyleMa, J., Yu, J., & Cheng, Y. (2025). Dynamic Evolution Analysis of Incentive Strategies and Symmetry Enhancement in the Personal-Data Valorization Industry Chain. Symmetry, 17(10), 1639. https://doi.org/10.3390/sym17101639





