A Hybrid Cross Layer with Harris-Hawk-Optimization-Based Efficient Routing for Wireless Sensor Networks
Abstract
:1. Introduction
Major Contribution
- Cluster formation and CH selection are mediated by k-medoids and IABC.
- A hybrid CL-HHO algorithm is presented for choosing the shortest path.
- A novel, well-known technique is used to compare the methodology’s performance.
- The effectiveness of the proposed CL-HHO improves the overall QoS performance.
2. Literature Survey
3. Materials and Methods
3.1. System Model
- Each SN is unaware of its position.
- A set of SNs distributed throughout the network has homogeneous characteristics.
- The CH and BS distance is considered non-uniform, because it directly impacts SN’s power consumption.
- Sensor nodes are not observed after deployment, because they are considered naturally organized.
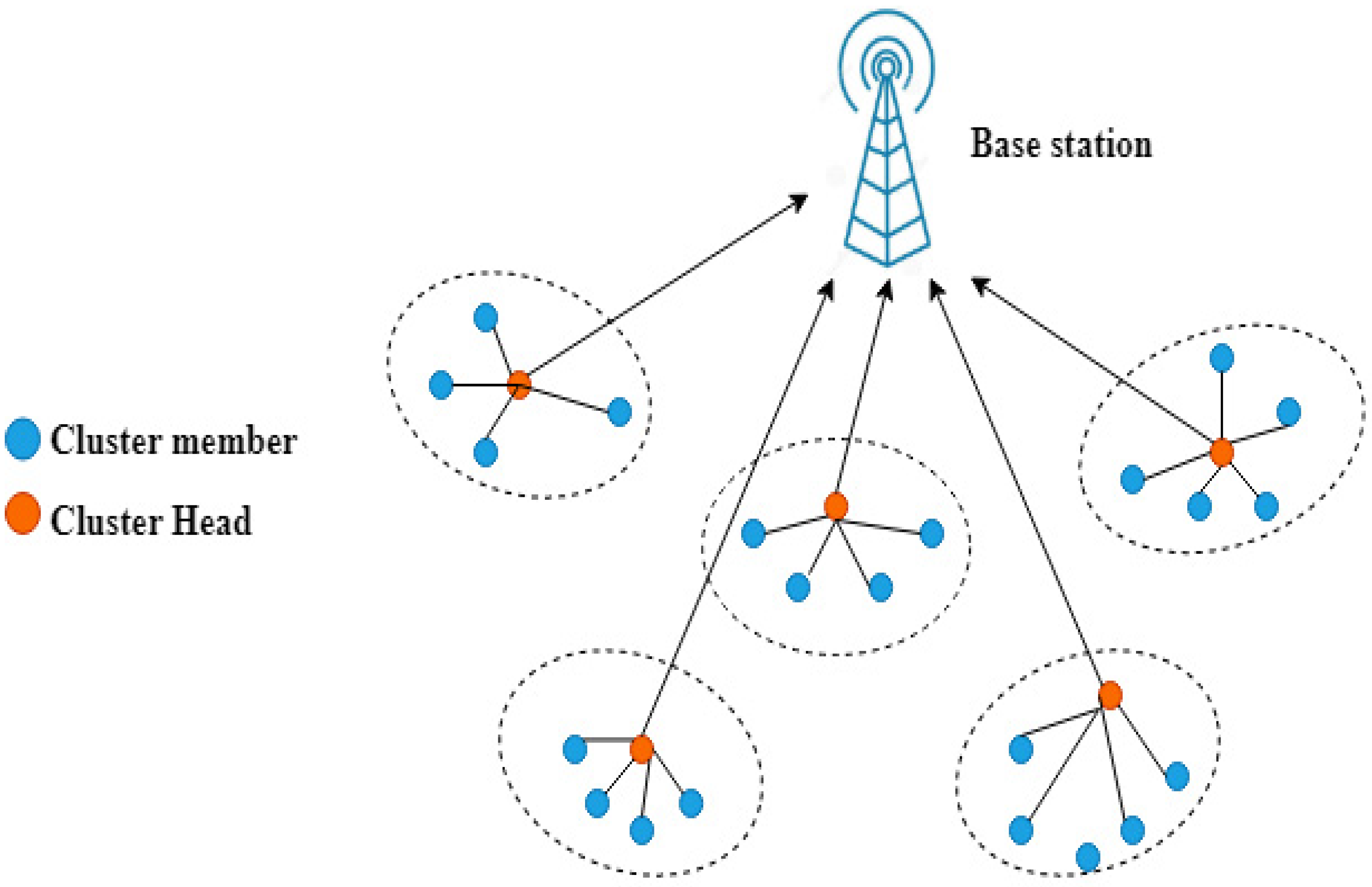
3.2. Network Model
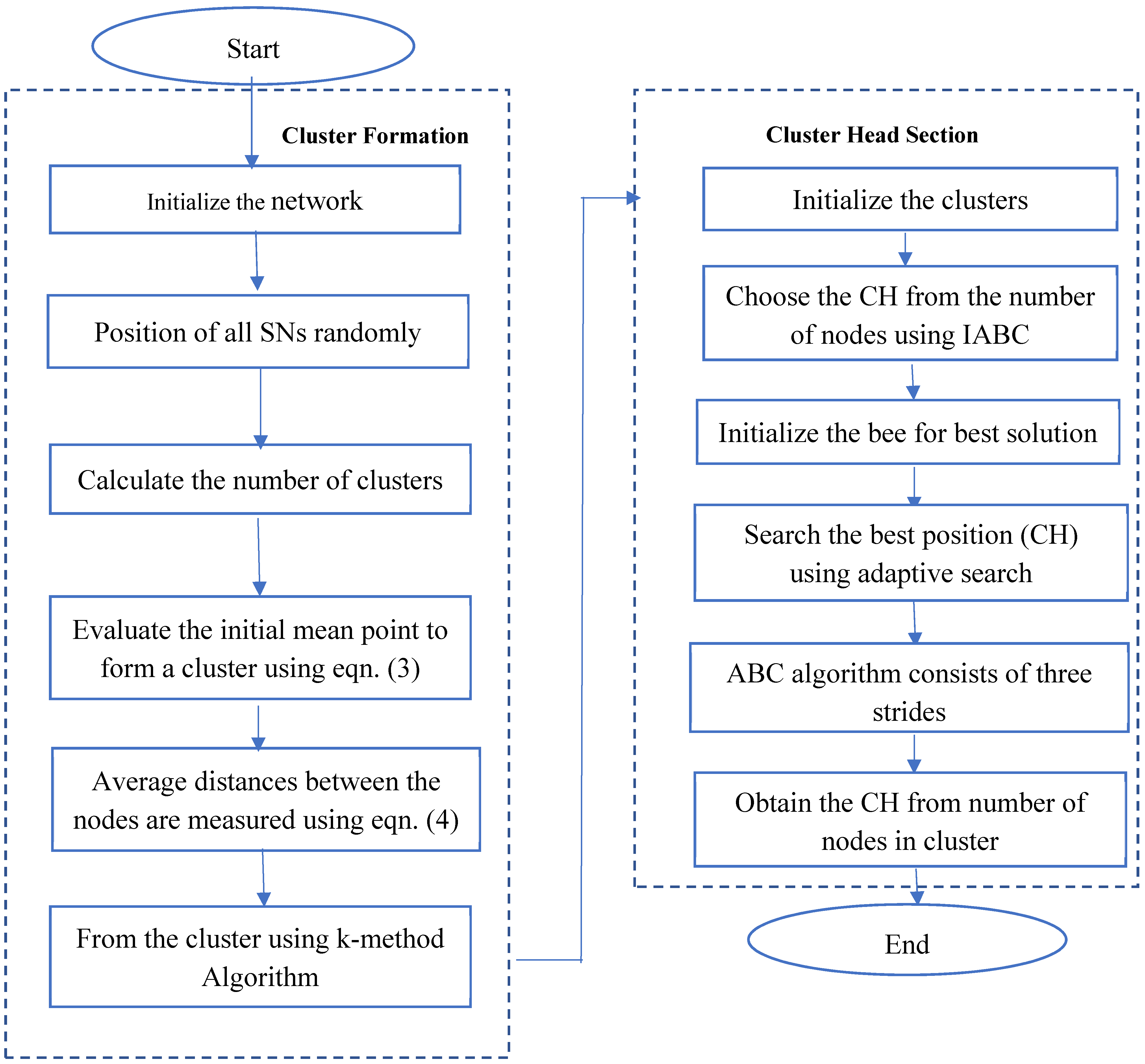
3.3. K-Medoids Clustering Algorithm
Set-Up Phase
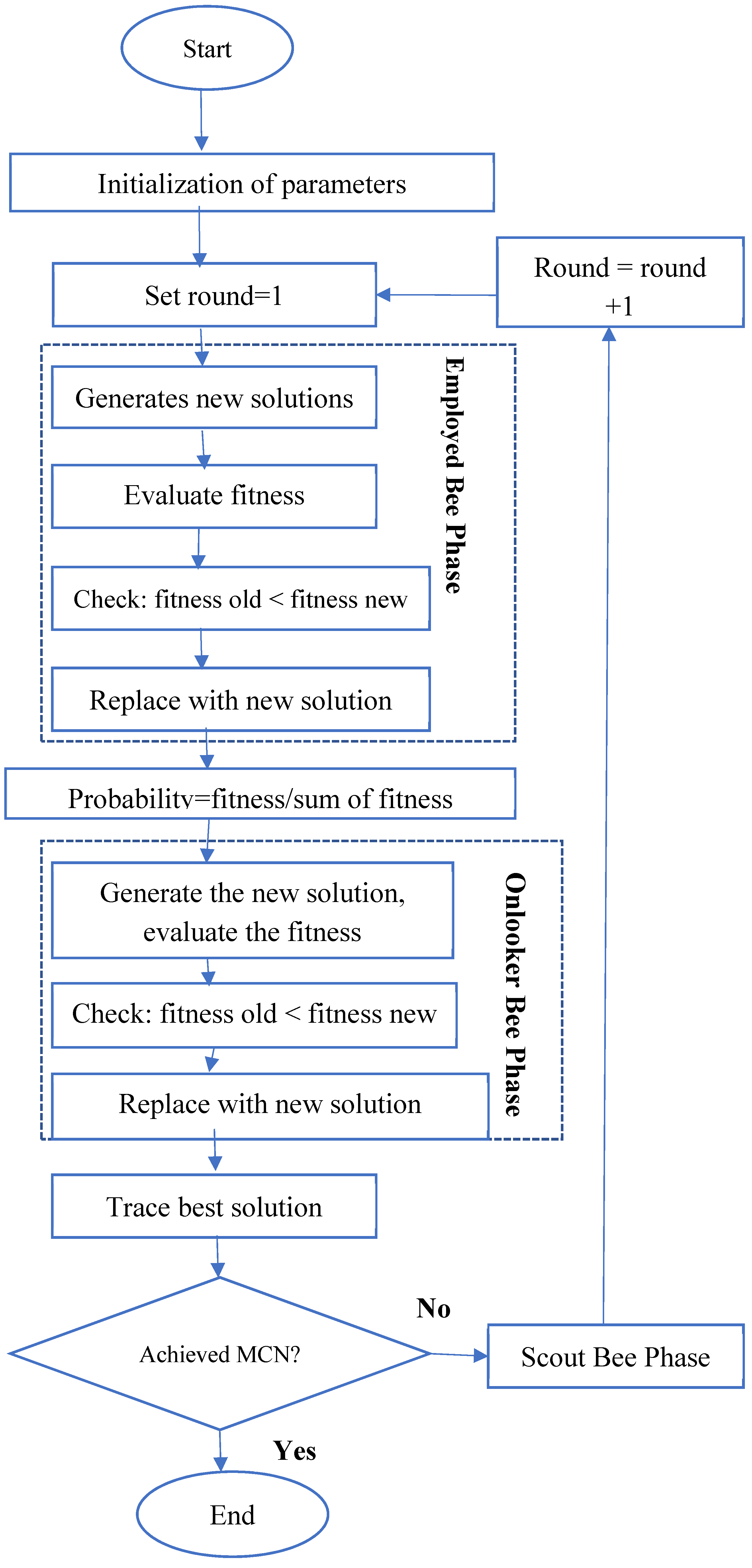
3.4. Artificial-Bee-Colony (ABC) Algorithm
3.5. Hybrid K-Medoids with IABC-Based CH-Selection Algorithm
| Algorithm 1: Algorithm for clustering using k-medoid with IABC |
| Initialization of network: Step 1: Initialize the sensor network. Step 2: Locate BS at coordinate. Step 3: Place all the SNs randomly. Cluster formation using k-medoid and selection of CH using IABC: Step 4: Number of nodes, N, is divided into number of clusters, C. Step 5: Every cluster has N number of nodes and each node is related to its nearest CH. Step 6: Randomly select the first CH by selecting a random first medoid from N in C cluster. Step 7: A three-dimensional coordinate (x, y, z) is generated by every normal node for CH. Step 8: K-means distance calculation is performed by CH. Step 9: Improved-ABC-optimization algorithm is used to select the new CH. Step 10: Repeat steps 7 to 9 until the node in the real center is found. End |
3.6. CORP
3.7. Harris Hawk’s Optimization Algorithm (HHO)
- A.
- EXPLORATION PHASE
- B.
- EXPLOITATION PHASE
4. Results and Discussion
4.1. Simulation-Parameter Setup
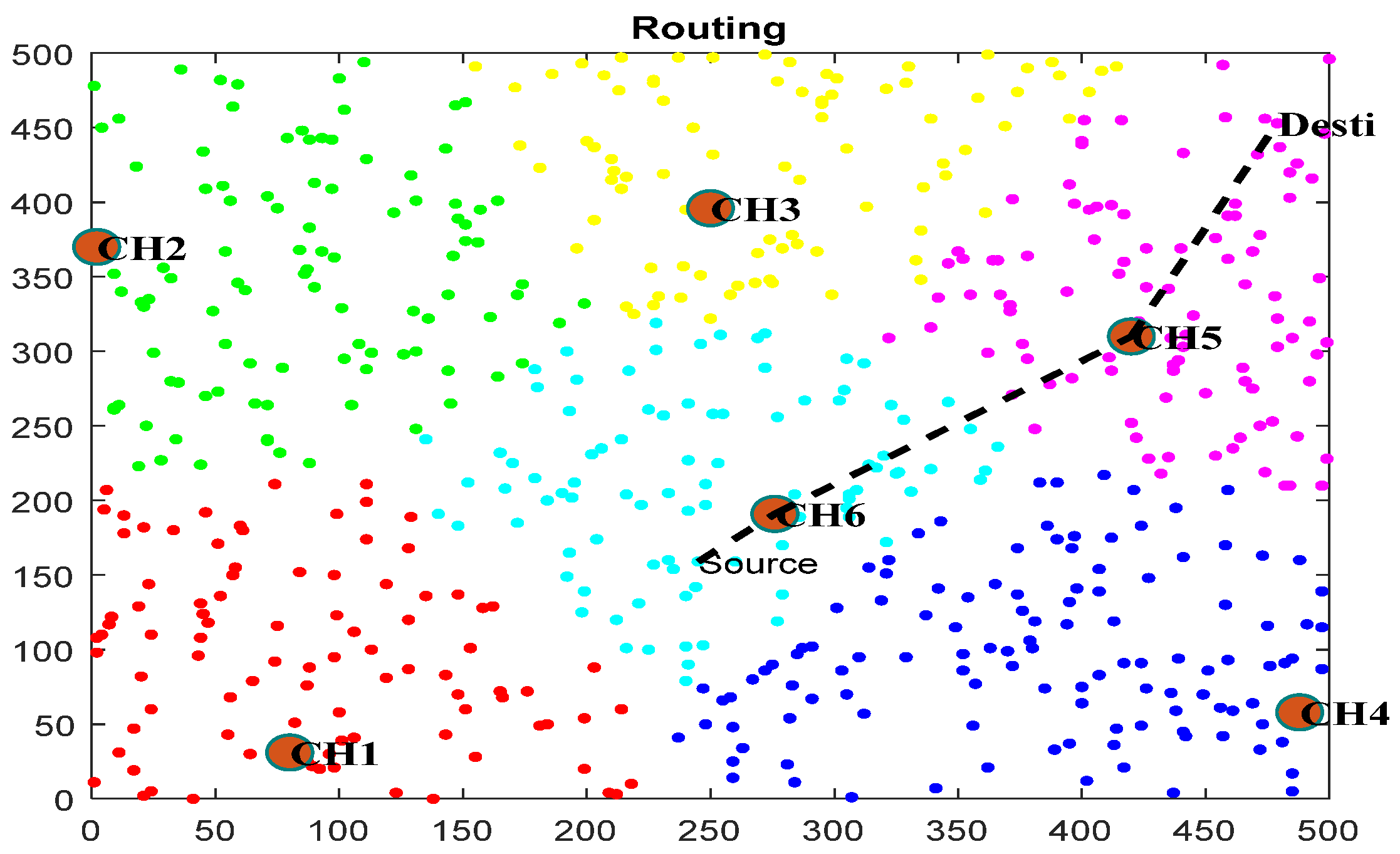
4.2. Evaluation of Clustering and Routing
4.3. Performance Analysis
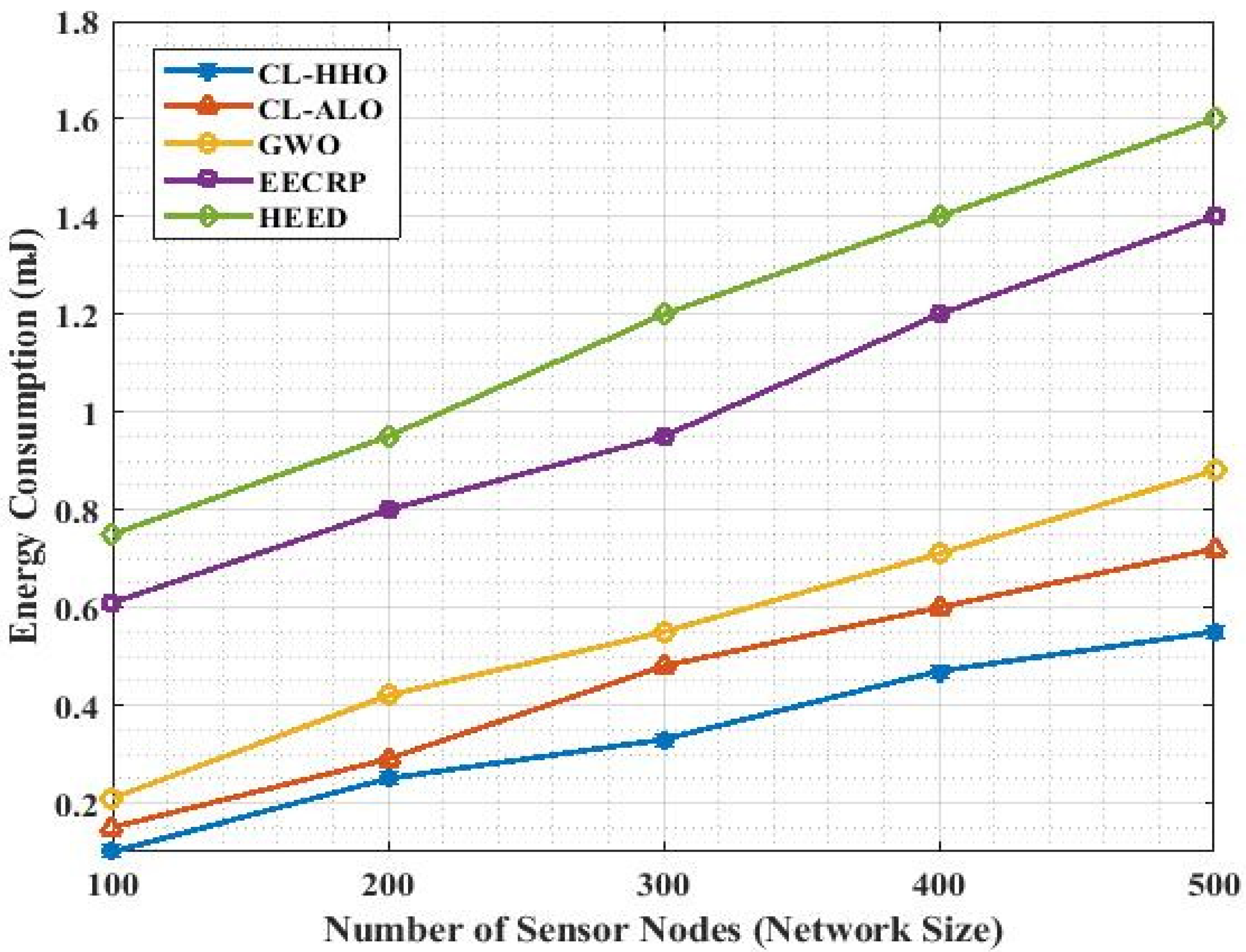
4.3.1. Energy Consumption
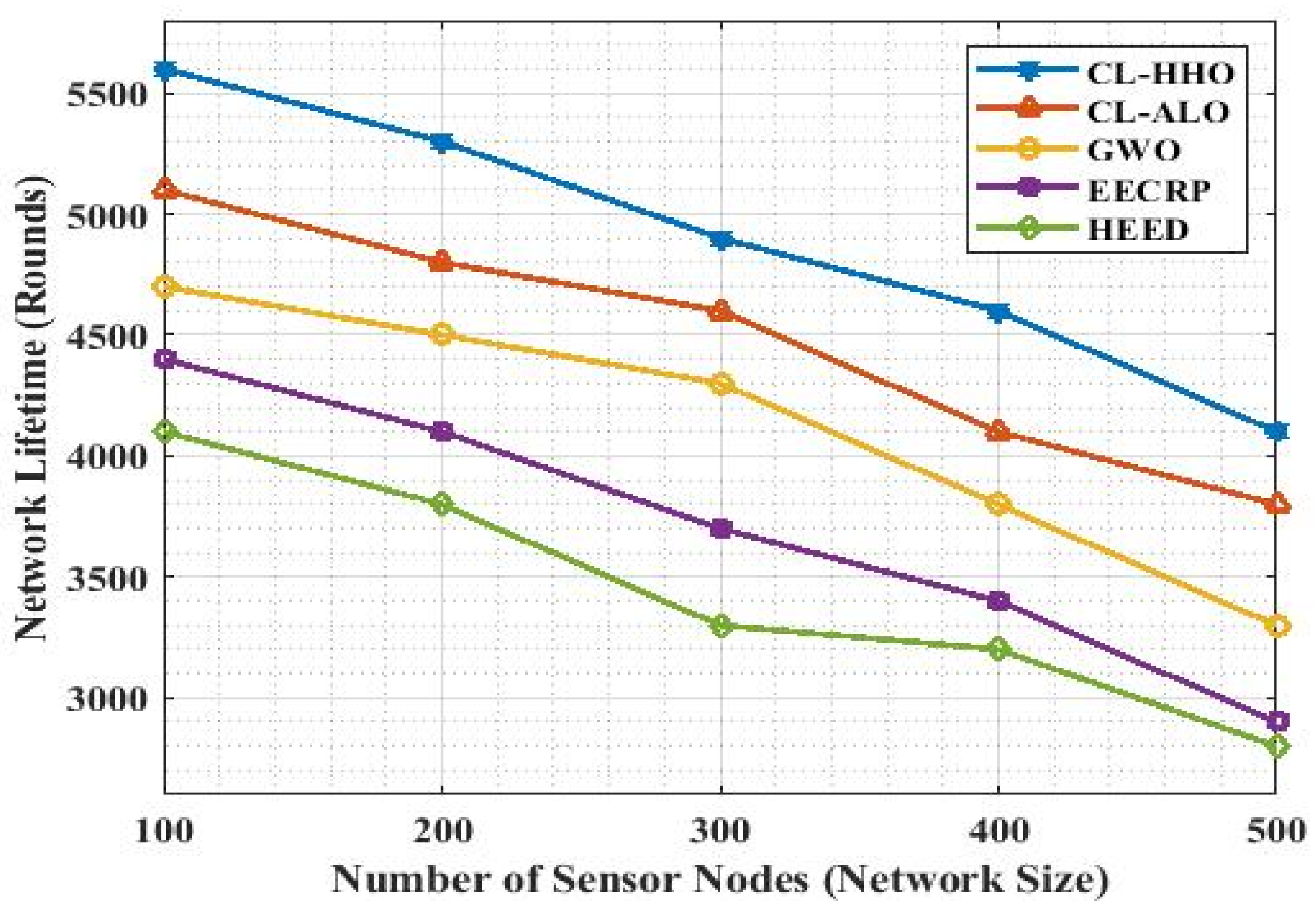
4.3.2. Network Lifetime (NLT)
4.3.3. Throughput
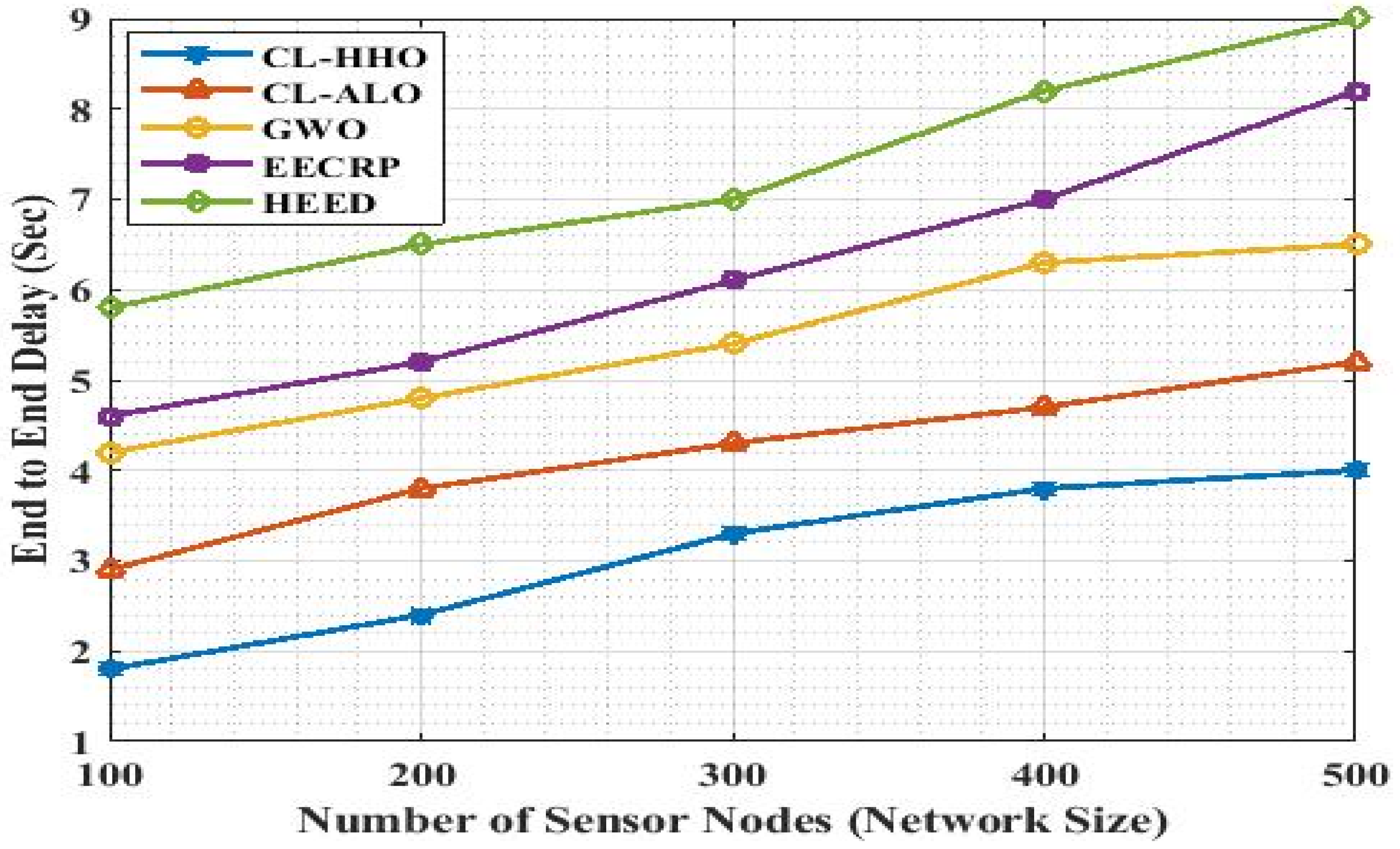
4.3.4. End-To-End Delay (E2E)
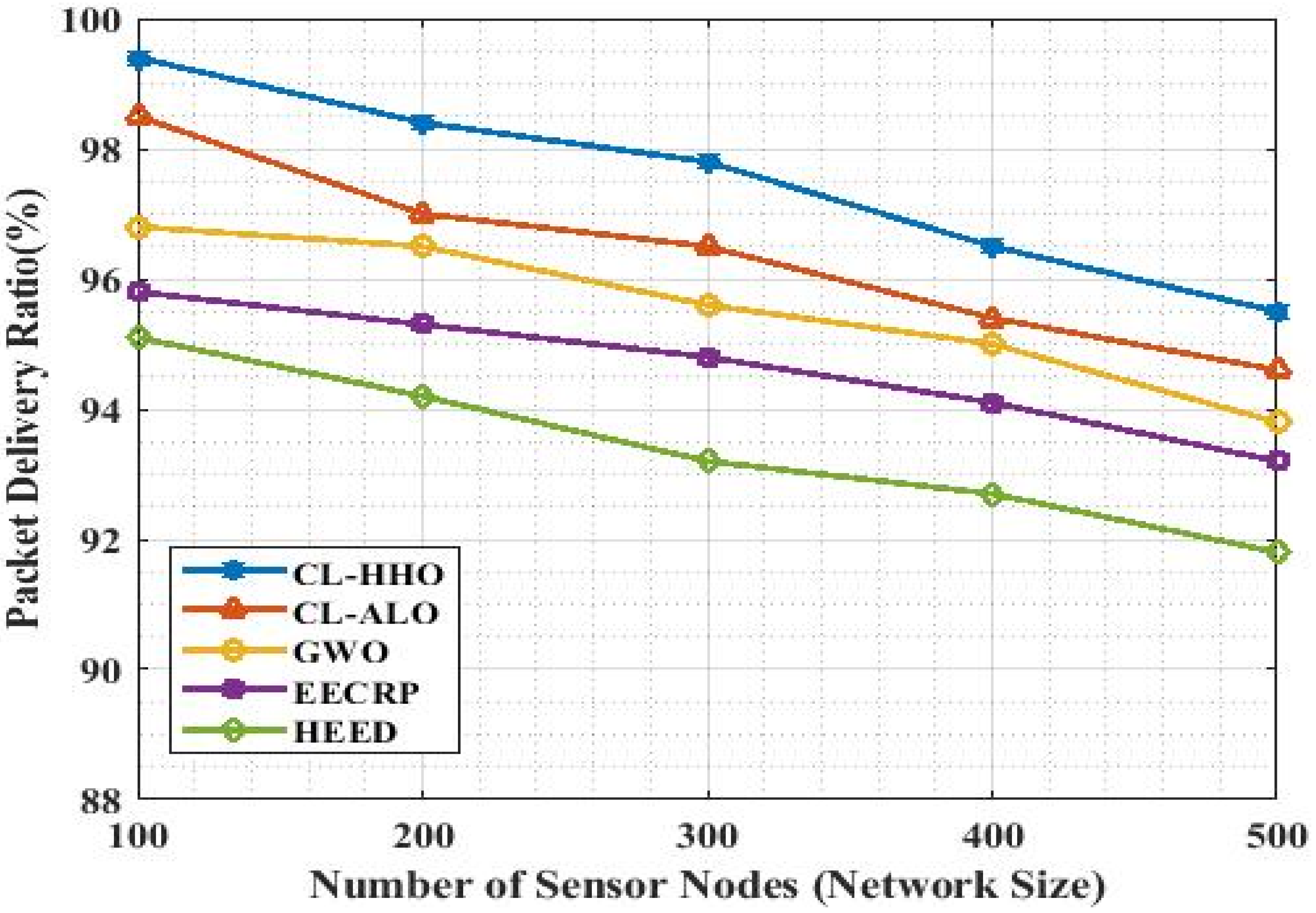
4.3.5. PDR
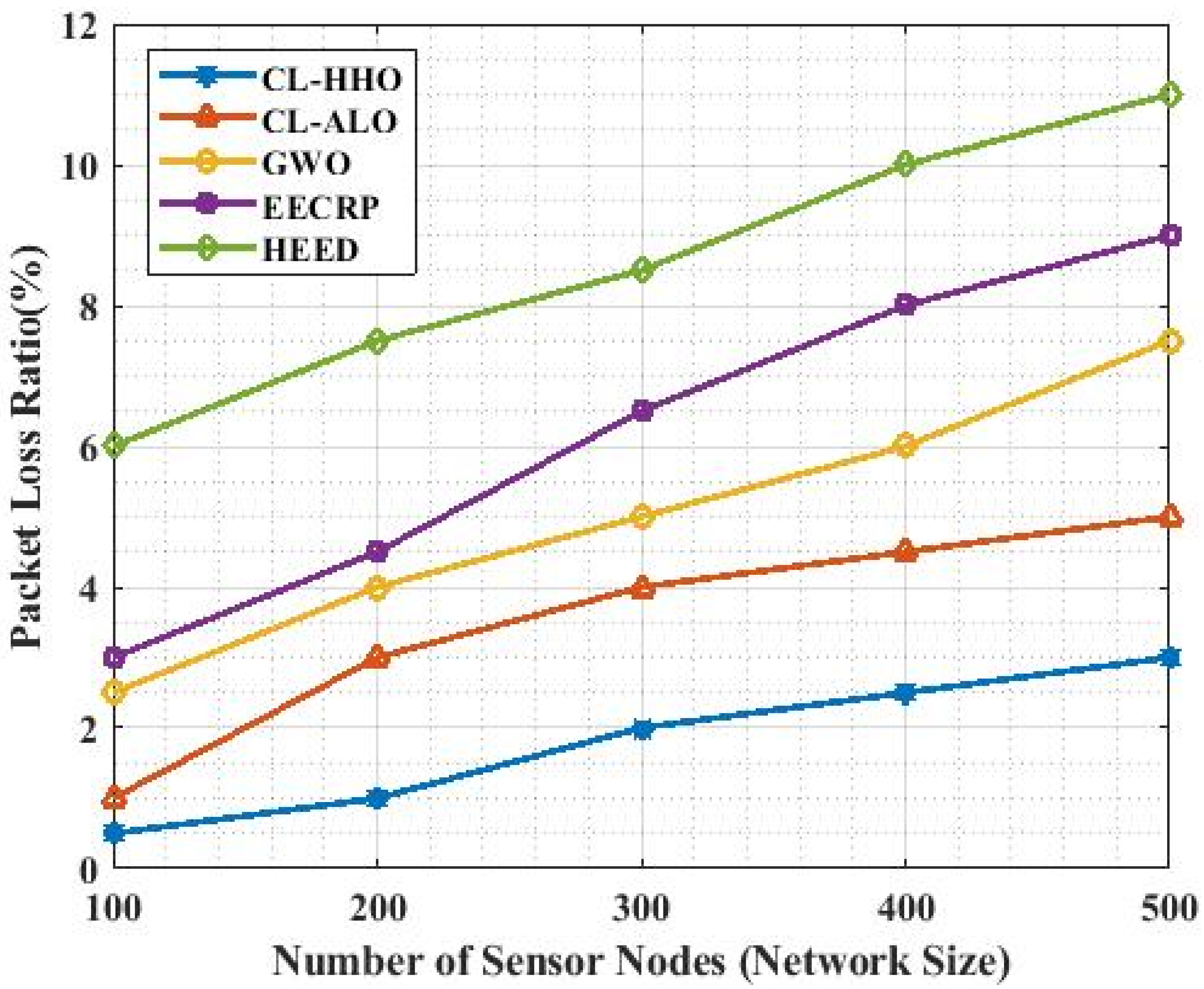
4.3.6. PLR
4.3.7. Jitter
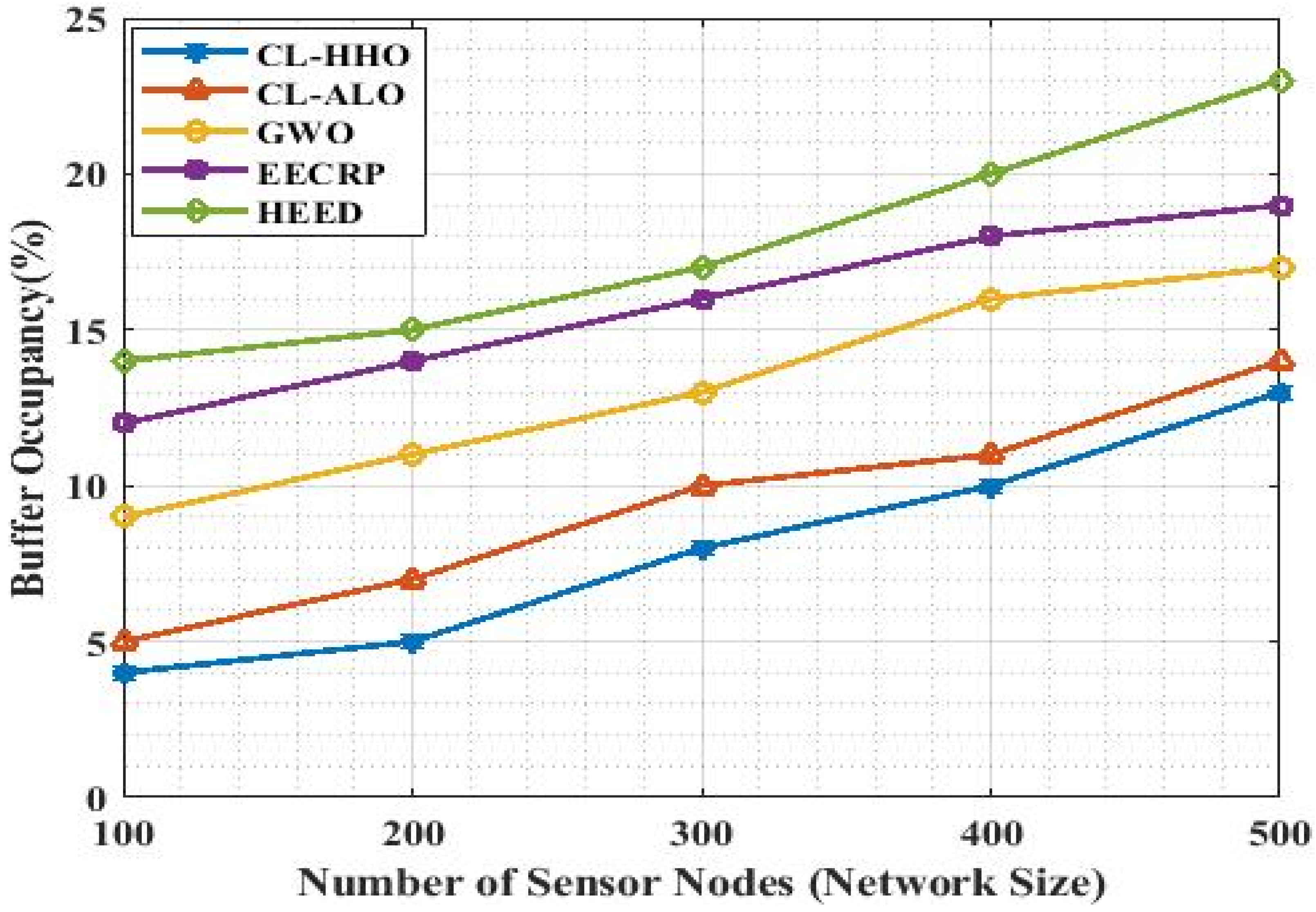
4.3.8. Buffer Occupancy
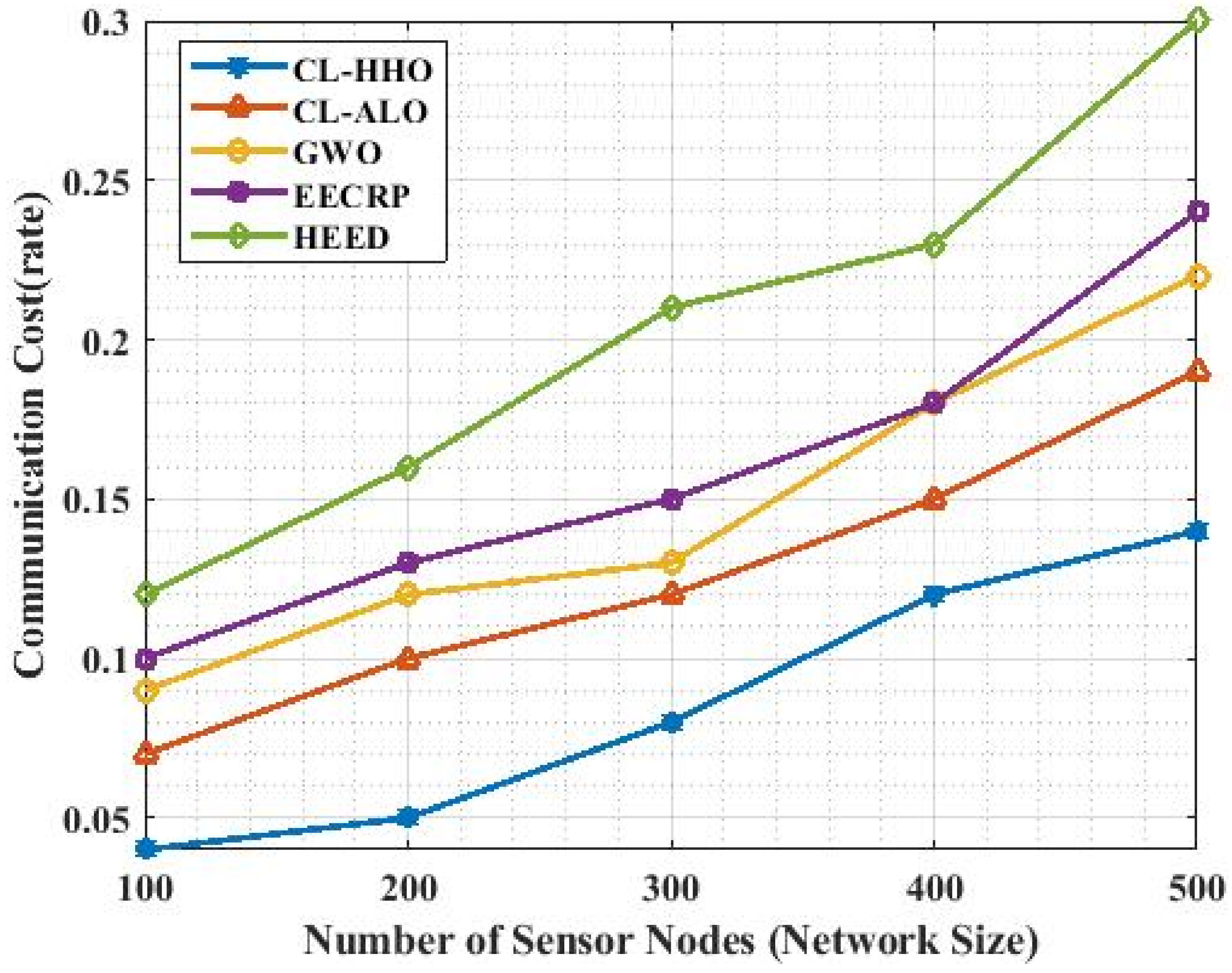
4.3.9. Communication Cost
4.3.10. CH-Selection-Time Analysis
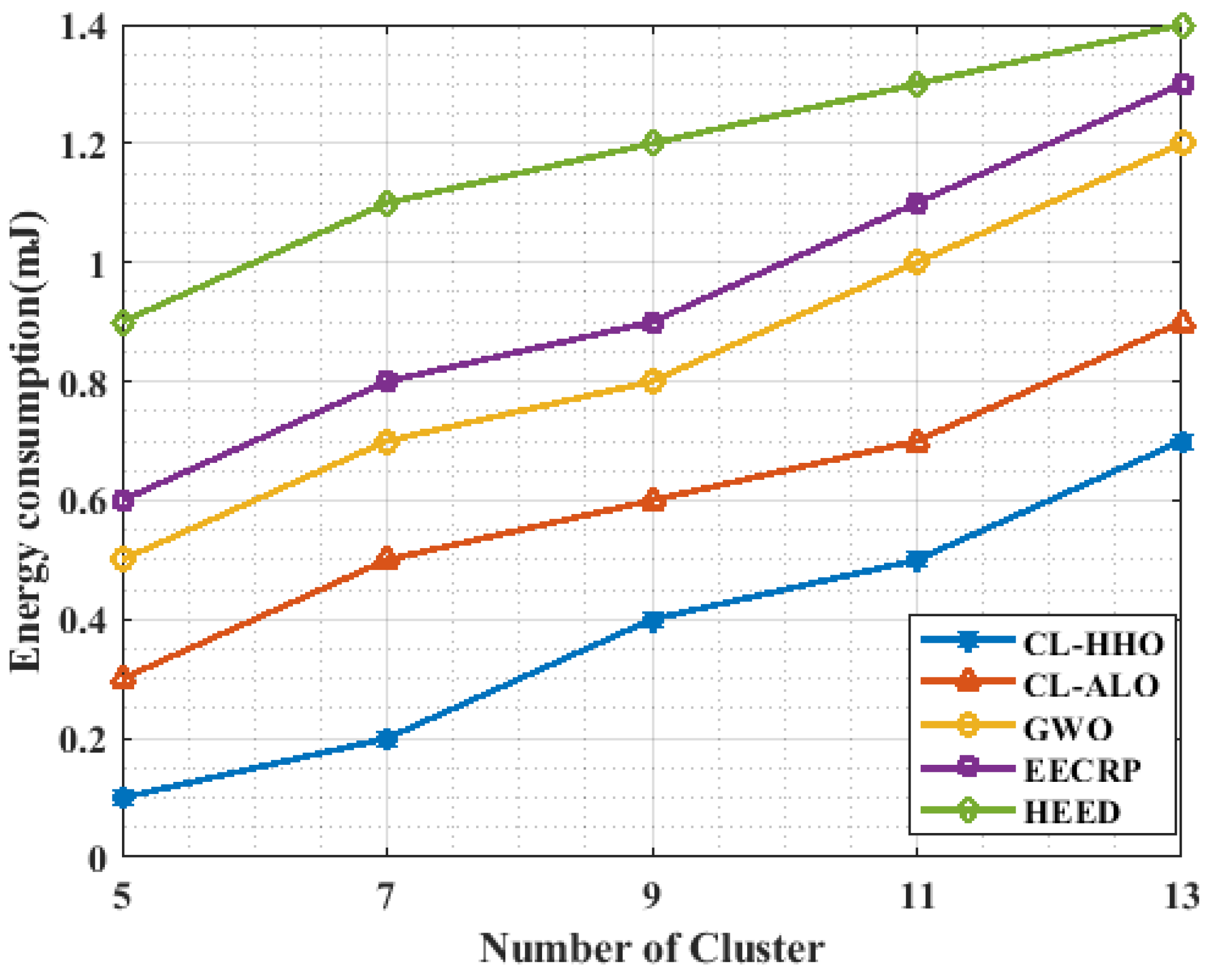
4.3.11. Energy Consumption vs. Cluster
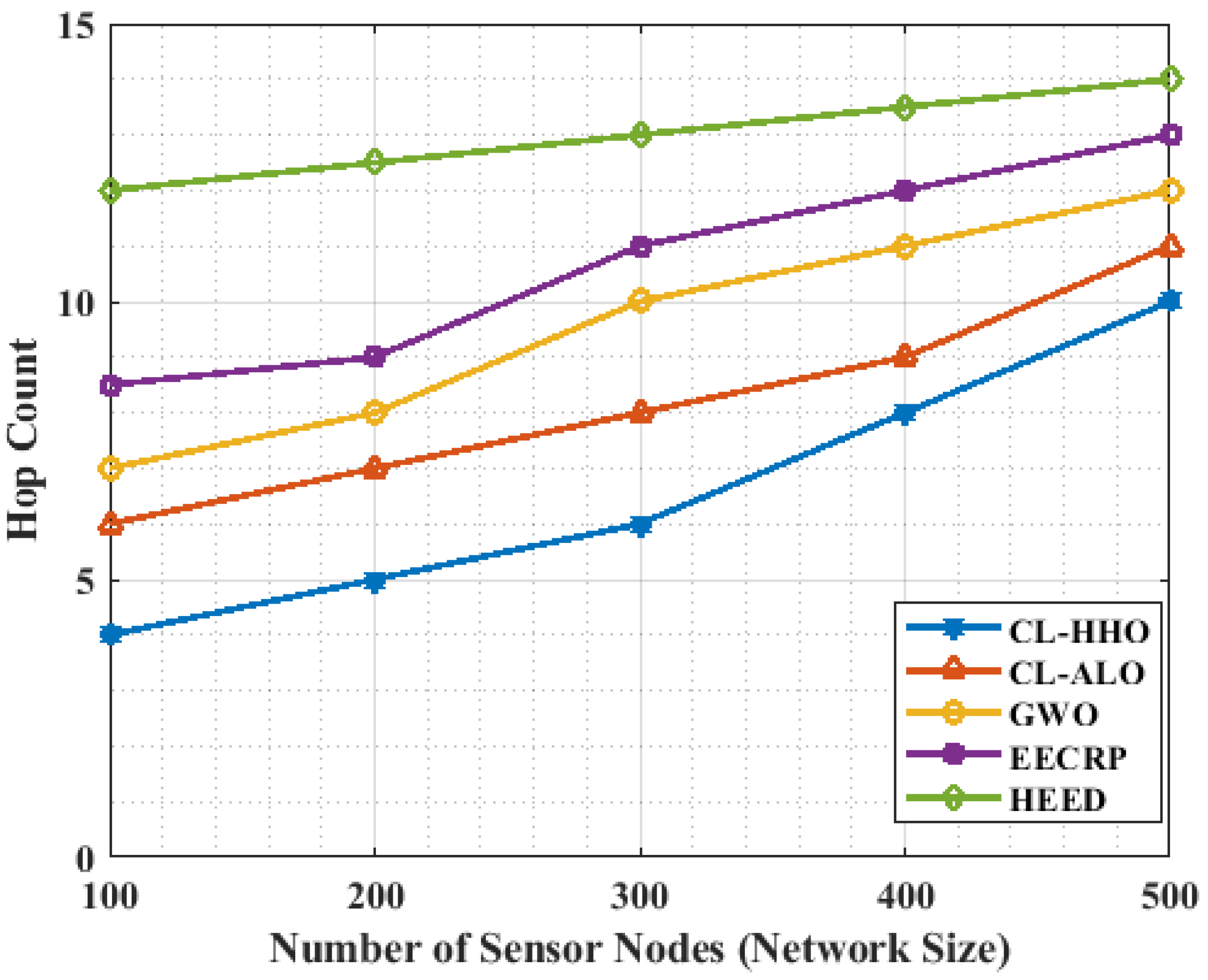
4.3.12. Hop Count
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Kim, J.; Lee, D.; Hwang, J.; Hong, S.; Shin, D.; Shin, D. Wireless Sensor Network (WSN) Configuration Method to Increase Node Energy Efficiency through Clustering and Location Information. Symmetry 2021, 13, 390. [Google Scholar] [CrossRef]
- Lee, W.-C.; Jeon, Y.-B.; Han, S.-S.; Jeong, C.-S. Position Prediction in Space System for Vehicles Using Artificial Intelligence. Symmetry 2022, 14, 1151. [Google Scholar] [CrossRef]
- Premakumari, S.B.N.; Mohan, P.; Subramanian, K. An Enhanced Localization Approach for Energy Conservation in Wireless Sensor Network with Q Deep Learning Algorithm. Symmetry 2022, 14, 2515. [Google Scholar] [CrossRef]
- Lu, Y.; Wu, X.; Yao, L.; Zhang, T.; Zhou, X. Multi-Channel Data Aggregation Scheduling Based on the Chaotic Firework Algorithm for the Battery-Free Wireless Sensor Network. Symmetry 2022, 14, 1571. [Google Scholar] [CrossRef]
- Lin, I.-C.; Chang, C.-C.; Chang, Y.-S. Data Security and Preservation Mechanisms for Industrial Control Network Using IOTA. Symmetry 2022, 14, 237. [Google Scholar] [CrossRef]
- Zhu, L.; Xiang, H.; Zhang, K. A Light and Anonymous Three-Factor Authentication Protocol for Wireless Sensor Networks. Symmetry 2022, 14, 46. [Google Scholar] [CrossRef]
- Elhoseny, M.; Shankar, K. Reliable data transmission model for mobile ad hoc network using signcryption technique. IEEE Trans. Reliab. 2019, 69, 1077–1086. [Google Scholar] [CrossRef]
- Rani, P.L.; Kumar, G.S. Detecting Anonymous Target and Predicting Target Trajectories in Wireless Sensor Networks. Symmetry 2021, 13, 719. [Google Scholar] [CrossRef]
- Pattnaik, S.; Sahu, P.K. Adaptive Neuro-Fuzzy Inference System-Particle swarm optimization-based clustering approach and hybrid Moth-flame cuttlefish optimization algorithm for efficient routing in wireless sensor network. Int. J. Commun. Syst. 2021, 34, e4783. [Google Scholar] [CrossRef]
- Pour, S.E.; Javidan, R. A new energy aware cluster head selection for LEACH in wireless sensor networks. IET Wirel. Sens. Syst. 2021, 11, 45–53. [Google Scholar] [CrossRef]
- Pattnaik, S.; Sahu, P.K. Assimilation of fuzzy clustering approach and EHO-Greedy algorithm for efficient routing in WSN. Int. J. Commun. Syst. Int. J. Commun. Syst. 2020, 33, e4354. [Google Scholar] [CrossRef]
- Koyuncu, H.; Tomar, G.S.; Sharma, D. A New Energy Efficient Multitier Deterministic Energy-Efficient Clustering Routing Protocol for Wireless Sensor Networks. Symmetry 2020, 12, 837. [Google Scholar] [CrossRef]
- Jagadeesh, S.; Muthulakshmi, I. Dynamic clustering and routing using multi-objective particle swarm optimization with Levy distribution for wireless sensor networks. Int. J. Commun. Syst. 2021, 34, e4902. [Google Scholar] [CrossRef]
- Soleymani, S.A.; Goudarzi, S.; Kama, N.; Ismail, S.A.; Ali, M.; Zainal, Z.; Zareei, M. A Hybrid Prediction Model for Energy-Efficient Data Collection in Wireless Sensor Networks. Symmetry 2020, 12, 2024. [Google Scholar] [CrossRef]
- Tandon, A.; Kumar, P.; Rishiwal, V.; Yadav, M.; Yadav, P. A Bio-inspired Hybrid Cross-Layer Routing Protocol for Energy Preservation in WSN-Assisted IoT. KSII Trans. Internet Inf. Syst. 2021, 15, 1317–1341. [Google Scholar]
- Shanmugam, R.; Kaliaperumal, B. An energy-efficient clustering and cross-layer-based opportunistic routing protocol (CORP) for wireless sensor network. Int. J. Commun. Syst. 2021, 34, e4752. [Google Scholar] [CrossRef]
- Azharuddin, M.; Kuila, P.; Jana, P.K. Energy efficient fault tolerant clustering and routing algorithms for wireless sensor networks. Comput. Electr. Eng. 2015, 41, 177–190. [Google Scholar] [CrossRef]
- Amer, A.; Fawzy, A.E.; Shokair, M.; Saad, W.; El-Halafawy, S.; Elkorany, A. Balanced Energy Efficient Grid Based Clustering Protocol for Wireless Sensor Networks. J. Comput. Digit. Syst. 2017, 6, 1–12. [Google Scholar]
- Bouyer, A.; Hatamlou, A.; Masdari, M. A new approach for decreasing energy in wireless sensor networks with hybrid LEACH protocol and fuzzy C-means algorithm. Int. J. Commun. Netw. Distrib. Syst. 2015, 14, 400–412. [Google Scholar] [CrossRef]
- Fei, Z.; Li, B.; Yang, S.; Xing, C.; Chen, H.; Hanzo, L. A survey of multi-objective optimization in wireless sensor networks: Metrics, algorithms, and open problems. IEEE Commun. Surv. Tutor. 2017, 19, 550–586. [Google Scholar] [CrossRef]
- Vimalarani, C.; Subramanian, R.; Sivanandam, S.N. An enhanced PSO-based clustering energy optimization algorithm for wireless sensor network. Sci. World J. 2016, 2016, 8658760. [Google Scholar] [CrossRef]
- Lawal Samira, A.; Suleiman, G.; Usman, A.D.; Mu’azu, M.B.; Salawudeen, A.T. Optimal Deployment of Wireless Sensor Networks (WSN) Based on Artificial Fish Swarm Optimization Algorithm. Int. J. Sci. Eng. Investig. (IJSEI) 2015, 4, 45–51. [Google Scholar]
- Banka, H.; Jana, P.K. PSO-based multiple-sink placement algorithm for protracting the lifetime of wireless sensor networks. In Second International Conference on Computer and Communication Technologies; Springer: Berlin/Heidelberg, Germany, 2016; pp. 605–616. [Google Scholar]
- Djedouboum, A.C.; Ari, A.A.A.; Mohamadou, A.M.G.A.; Aliouat, O.T.A.Z.; Gueroui, A.M.; Thiare, O. A Framework of Modeling Large-Scale Wireless Sensor Networks for Big Data Collection. Symmetry 2020, 12, 1113. [Google Scholar] [CrossRef]
- Agawam, R.; Mittal, A.; Kaur, R. Various Optimization techniques used in Wireless Sensor Networks. Int. Res. J. Eng. Technol. (IRJET) 2016, 3, 2085–2090. [Google Scholar]
- Wang, H.; Chen, Y.; Dong, S. Research on efficientefficient routing protocol for WSNs based on improved artificial bee colony algorithm. IET Wirel. Sens. Syst. 2016, 7, 15–20. [Google Scholar] [CrossRef]
- Zhu, C.; Wu, S.; Han, G.; Shu, L.; Wu, H. A Tree-Cluster-Based Data-Gathering Algorithm for Industrial WSNs With a Mobile Sink. IEEE Access 2015, 3, 381–396. [Google Scholar] [CrossRef]
- Singh, R.; Verma, A.K. Energy Efficient Cross Layer based Adaptive Threshold Routing Protocol for WSN. AEU-Int. J. Electron. Commun. 2017, 72, 166–173. [Google Scholar] [CrossRef]
- Kumar, P.S.; Manikandan, J. Diagnosing COVID-19 Virus in the Cardiovascular System Using ANN. In Artificial Intelligence for COVID-19. Studies in Systems, Decision and Control; Oliva, D., Hassan, S.A., Mohamed, A., Eds.; Springer: Cham, Switzerland, 2021; Volume 358. [Google Scholar] [CrossRef]
- Song, Y.; Gui, C.; Lu, X.; Chen, H.; Sun, B. A Genetic Algorithm for Energy-Efficient Based Multipath Routing in Wireless Sensor Networks. Wirel. Pers. Commun. 2015, 85, 2055–2066. [Google Scholar] [CrossRef]
- Li, H.; Liu, J. Double Cluster Based Energy Efficient Routing Protocol for Wireless Sensor Network. Int. J. Wirel. Inf. Netw. 2016, 23, 40–48. [Google Scholar] [CrossRef]
- Kumar, P.S.; Chitra, P.; Sneha, S. Design of Improved Quadruple-Mode Bandpass Filter Using Cavity Resonator for 5G Mid-Band Applications. In Future Trends in 5G and 6G: Challenges, Architecture, and Applications; CRC Press: Boca Raton, FL, USA, 2021; pp. 219–234. [Google Scholar]
- Wang, J.; Wang, K.; Niu, J.; Liu, W. A K-medoids based clustering algorithm for wireless sensor networks. In Proceedings of the 2018 International Workshop on Advanced Image Technology (IWAIT), Chiang Mai, Thailand, 7–9 January 2018; pp. 1–4. [Google Scholar] [CrossRef]
- Kalaikumar, K.; Baburaj, E. FABC-MACRD: Fuzzy and Artificial Bee Colony Based Implementation of MAC, Clustering, Routing and Data Delivery by Cross-Layer Approach in WSN. Wirel. Pers. Commun. 2018, 103, 1633–1655. [Google Scholar] [CrossRef]
- Famila, S.; Jawahar, A.; Sariga, A.; Shankar, K. Improved artificial bee colony optimization based clustering algorithm for SMART sensor environments. Peer-to-Peer Netw. Appl. 2020, 13, 1071–1079. [Google Scholar] [CrossRef]
- Kandasamy, A.; Rengarasu, S.; Burri, P.K.; Palanisamy, S.; Kumar, K.K.; Baladhandapani, A.D.; Mamo, S.A. Defected Circular-Cross Stub Copper Metal Printed Pentaband Antenna. Adv. Mater. Sci. Eng. 2022, 2022, 6009092. [Google Scholar] [CrossRef]
- Houssein, E.H.; Saad, M.R.; Hussain, K.; Zhu, W.; Shaban, H.; Hassaballah, M. Optimal Sink Node Placement in Large Scale Wireless Sensor Networks Based on Harris’ Hawk Optimization Algorithm. IEEE Access 2020, 8, 19381–19397. [Google Scholar] [CrossRef]
- Sam, P.J.C.; Surendar, U.; Ekpe, U.M.; Saravanan, M.; Kumar, P.S. A Low-Profile Compact EBG Integrated Circular Monopole Antenna for Wearable Medical Application. In Smart Antennas EAI/Springer Innovations in Communication and Computing; Malik, P.K., Lu, J., Madhav, B.T.P., Kalkhambkar, G., Amit, S., Eds.; Springer: Cham, Switzerland, 2022. [Google Scholar] [CrossRef]
- Dhanasekaran, S.; Ramesh, J. Channel estimation using spatial partitioning with coalitional game theory (SPCGT) in wireless communication. Wireless Netw. 2021, 27, 1887–1899. [Google Scholar] [CrossRef]
- Suganyadevi, K.; Nandhalal, V.; Palanisamy, S.; Dhanasekaran, S. Data Security and Safety Services using Modified Timed Efficient Stream Loss-Tolerant Authentication in Diverse Models of VANET. In Proceedings of the 2022 International Conference on Edge Computing and Applications (ICECAA), Coimbatore, India, 21–23 September 2022; pp. 417–422. [Google Scholar] [CrossRef]
- S, D.; Palanisamy, S.; Hajjej, F.; Khalaf, O.I.; Abdulsahib, G.M.; S, R. Discrete Fourier Transform with Denoise Model Based Least Square Wiener Channel Estimator for Channel Estimation in MIMO-OFDM. Entropy 2022, 24, 1601. [Google Scholar] [CrossRef] [PubMed]
- Murugesan, S.; Ramalingam, S.; Kanimozhi, P. Theoretical modelling and fabrication of smart waste man-agement system for clean environment using WSN and IOT. Mater. Today Proc. 2021, 45, 1908–1913. [Google Scholar] [CrossRef]
- Ramalingam, S.; Baskaran, K.; Kalaiarasan, D. IoT Enabled Smart Industrial Pollution Monitoring and Control System Using Raspberry Pi with BLYNK Server. In Proceedings of the 2019 International Conference on Communication and Electronics Systems (ICCES), Coimbatore, India, 17–19 July 2019; pp. 2030–2034. [Google Scholar] [CrossRef]
- Venkataramanan, C.; Ramalingam, S.; Manikandan, A. LWBA: Lévy-walk Bat Algorithm Based Data Prediction for Precision Agriculture in Wireless Sensor Networks. J. Intell. Fuzzy Syst. 2021, 41, 2891–2904. [Google Scholar] [CrossRef]
- Ramalingam, S.; Baskaran, K. An Efficient Data Prediction Model Using Hybrid Harris Hawk Optimization with Random Forest Algorithm in Wireless Sensor Network. J. Intell. Fuzzy Syst. 2021, 40, 5171–5195. [Google Scholar] [CrossRef]
- Subahi, A.F.; Khalaf, O.I.; Alotaibi, Y.; Natarajan, R.; Mahadev, N.; Ramesh, T. Modified Self-Adaptive Bayesian Algorithm for Smart Heart Disease Prediction in IoT System. Sustainability 2022, 14, 14208. [Google Scholar] [CrossRef]
- Lilhore, U.K.; Khalaf, O.I.; Simaiya, S.; Romero, C.A.T.; Abdulsahib, G.M.; Kumar, D. A depth-controlled and energy-efficient routing protocol for underwater wireless sensor networks. Int. J. Distrib. Sens. Netw. 2022, 18, 15501329221117118. [Google Scholar] [CrossRef]
- Singhal, S.; Jatana, N.; Subahi, A.F.; Gupta, C.; Khalaf, O.I.; Alotaibi, Y. Fault coverage-based test case prioritization and selection using african buffalo optimization. Comput. Mater. Contin. 2023, 74, 6755–6774. [Google Scholar] [CrossRef]
- Rahman, H.; Tariq, J.; Masood, M.A.; Subahi, A.F.; Khalaf, O.I.; Alotaibi, Y. Multi-tier sentiment analysis of social media text using supervised machine learning. Comput. Mater. Contin. 2023, 74, 5527–5543. [Google Scholar] [CrossRef]
- Agrawal, R.; Faujdar, N.; Romero, C.A.T.; Sharma, O.; Abdulsahib, G.M.; Khalaf, O.I.; Mansoor, R.F.; Ghoneim, O.A. Classification and comparison of ad hoc networks: A review. Egypt. Inform. J. 2022. [Google Scholar] [CrossRef]
- Palanisamy, S.; Thangaraju, B. Design and analysis of clover leaf-shaped fractal antenna integrated with stepped impedance resonator for wireless applications. Int. J. Commun. Syst. 2022, 35, e5184. [Google Scholar] [CrossRef]
- Nivethitha, T.; Palanisamy, S.K.; Prakash, K.M.; Jeevitha, K. Comparative study of ANN and fuzzy classifier for forecasting electrical activity of heart to diagnose COVID-19. Mater. Today Proc. 2021, 45, 2293–2305. [Google Scholar] [CrossRef] [PubMed]
- Palanisamy, S.; Thangaraju, B.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S.; Alassery, F. A Novel Approach of Design and Analysis of a Hexagonal Fractal Antenna Array (HFAA) for Next-Generation Wireless Communication. Energies 2021, 14, 6204. [Google Scholar] [CrossRef]
- Palanisamy, S.; Thangaraju, B.; Khalaf, O.I.; Alotaibi, Y.; Alghamdi, S. Design and Synthesis of Multi-Mode Bandpass Filter for Wireless Applications. Electronics 2021, 10, 2853. [Google Scholar] [CrossRef]
- Kumar, S.; Balakumaran, T. Modeling and simulation of dual layered U-slot multiband microstrip patch antenna for wireless applications. Nanoscale Rep. 2021, 4, 15–18. [Google Scholar] [CrossRef]
- Radhakrishnan, K.; Ramakrishnan, D.; Khalaf, O.I.; Uddin, M.; Chen, C.-L.; Wu, C.-M. A Novel Deep Learning-Based Cooperative Communication Channel Model for Wireless Underground Sensor Networks. Sensors 2022, 22, 4475. [Google Scholar] [CrossRef]
- Palanisamy, S. Predictive Analytics with Data Visualization. J. Ubiquitous Comput. Commun. Technol. 2022, 4, 75–96. [Google Scholar] [CrossRef]
- Malik, P.K.; Naim, A.; Singh, R. (Eds.) Printed Antennas: Design and Challenges, 1st ed.; CRC Press: Boca Raton, FL, USA, 2022. [Google Scholar] [CrossRef]
- Haus, B.; Yap, J.S.; Schaefer, L.; Mercorelli, P. Soft Optimal Computing Methods to Identify Surface Roughness in Manufacturing Using a Monotonic Regressor. In Soft Computing: Theories and Applications; Kumar, R., Ahn, C.W., Sharma, T.K., Verma, O.P., Agarwal, A., Eds.; Lecture Notes in Networks and Systems; Springer: Singapore, 2022; p. 425. [Google Scholar] [CrossRef]
- Kumar, P.S.; Valarmathy, S. Development of a novel algorithm for SVMBDT fingerprint classifier based on clustering approach. In Proceedings of the IEEE-International Conference On Advances In Engineering, Science And Management (ICAESM-2012), Nagapattinam, India, 30–31 March 2012; pp. 256–261. [Google Scholar]
- Haus, B.; Mercorelli, P.; Yap, J.S.; Schäfer, L. Soft Optimal Computing to Identify Surface Roughness in Manufacturing Using a Gaussian and a Trigonometric Regressor. In Soft Computing and Its Engineering Applications icSoftComp 2021. Communications in Computer and Information Science; Patel, K.K., Doctor, G., Patel, A., Lingras, P., Eds.; Springer: Cham, Switzerland, 2022; Volume 1572. [Google Scholar] [CrossRef]
- Kulbhushan, S.; Sameer, M. Challenges in Wireless Sensor Network. SSRN Electron. J. 2014, 2, 1165–1168. [Google Scholar]
- Alaa, E.; Hazem, E.-B.; Samir, E.; Sajjad, H.; Asaad, H.; Samir, Z. Challenges in Wireless Sensor Networks. Int. J. Adv. Res. Comput. Sci. Technol. 2016, 4, 22–27. [Google Scholar]
- Kumar, P.; Boopathy, S.; Dhanasekaran, S.; Anand, K.R.G. Optimization of Multi-Band Antenna for Wireless Communication Systems using Genetic Algorithm. In Proceedings of the 2021 International Conference on Advancements in Electrical, Electronics, Communication, Computing and Automation (ICAECA), Virtual. 8–9 October 2021; pp. 1–6. [Google Scholar] [CrossRef]
- Ahmad, R.; Wazirali, R.; Abu-Ain, T. Machine Learning for Wireless Sensor Networks Security: An Overview of Challenges and Issues. Sensors 2022, 22, 4730. [Google Scholar] [CrossRef] [PubMed]




| References | Proposed Algorithm | Limitation |
|---|---|---|
| [9] | MFO-CFO | Jitter and buffer occupancy are considered for QoS perfromance |
| [11] | (EHO)-Greedy algorithm | CH-selection time is high |
| [13] | MOPSO-L | Poor energy consumption |
| [15] | BiHCLR algorithm | High computational complexity |
| [18] | Balanced-energy-efficient-grid-based clustering protocol | Poor QoS performance |
| [21] | EPSO-CEO | Communication cost is high |
| [25] | Hybrid GA-PSO approach | Energy consumption cannot be minimized sufficiently |
| [27] | TCBDGA | High computational complexity |
| [29] | BPSNs and EHSNs | The overhead issues are not addressed |
| PARAMETER | VALUE |
|---|---|
| Total Clusters | 6 |
| Number of nodes | 500 |
| Initial energy | 0.1 J |
| Communication-Tx Energy | 20.5 mW |
| Communication-Rx Energy | 14 mW |
| Deployment area | 500 500 |
| Packet size | 512 bytes |
| Packet-sending rate | 1 packet/s |
| Node distribution | Random |
| Methods | Energy Consumption | ||||
|---|---|---|---|---|---|
| No. of nodes | 100 | 200 | 300 | 400 | 500 |
| CL-HHO | 0.1 | 0.25 | 0.33 | 0.47 | 0.55 |
| CL-ALO | 0.15 | 0.29 | 0.48 | 0.6 | 0.72 |
| GWO | 0.21 | 0.42 | 0.55 | 0.71 | 0.88 |
| EECRP | 0.61 | 0.8 | 0.95 | 1.2 | 1.4 |
| HEED | 0.75 | 0.95 | 1.2 | 1.4 | 1.6 |
| Methods | NLT | ||||
|---|---|---|---|---|---|
| No. of nodes | 100 | 200 | 300 | 400 | 500 |
| CL-HHO | 5600 | 5300 | 4900 | 4600 | 4100 |
| CL-ALO | 5100 | 4800 | 4600 | 4100 | 3800 |
| GWO | 4700 | 4500 | 4300 | 3800 | 3300 |
| EECRP | 4400 | 4100 | 3700 | 3400 | 2900 |
| HEED | 4100 | 3800 | 3300 | 3200 | 2800 |
| Methods | Throughput | ||||
|---|---|---|---|---|---|
| No. of nodes | 100 | 200 | 300 | 400 | 500 |
| CL-HHO | 0.98 | 0.92 | 0.89 | 0.85 | 0.79 |
| CL-ALO | 0.93 | 0.85 | 0.77 | 0.72 | 0.69 |
| GWO | 0.85 | 0.78 | 0.71 | 0.65 | 0.60 |
| EECRP | 0.75 | 0.70 | 0.68 | 0.60 | 0.55 |
| HEED | 0.71 | 0.65 | 0.61 | 0.54 | 0.49 |
| Methods | E2E Delay | ||||
|---|---|---|---|---|---|
| No. of nodes | 100 | 200 | 300 | 400 | 500 |
| CL-HHO | 1.8 | 2.4 | 3.3 | 3.8 | 4.0 |
| CL-ALO | 2.9 | 3.8 | 4.3 | 4.7 | 5.2 |
| GWO | 4.2 | 4.8 | 5.4 | 6.3 | 5.5 |
| EECRP | 4.6 | 5.2 | 6.1 | 7.0 | 8.2 |
| HEED | 5.8 | 6.5 | 7.0 | 8.2 | 9.0 |
| Methods | PDR | ||||
|---|---|---|---|---|---|
| No. of Nodes | 100 | 200 | 300 | 400 | 500 |
| CL-HHO | 99.4 | 98.4 | 97.8 | 96.5 | 95.5 |
| CL-ALO | 98.5 | 97.0 | 96.5 | 95.4 | 94.6 |
| GWO | 96.8 | 96.5 | 95.6 | 95.0 | 93.8 |
| EECRP | 95.8 | 95.3 | 94.8 | 94.1 | 93.2 |
| HEED | 95.1 | 94.2 | 93.2 | 92.7 | 91.8 |
| Methods | PLR | ||||
|---|---|---|---|---|---|
| No. of Nodes | 100 | 200 | 300 | 400 | 500 |
| CL-HHO | 0.5 | 1 | 2 | 2.5 | 3.0 |
| CL-ALO | 1 | 3 | 4 | 4.5 | 5.0 |
| GWO | 2.5 | 4 | 5 | 6 | 7.5 |
| EECRP | 3 | 4.5 | 6.5 | 8.0 | 9 |
| HEED | 6 | 7.5 | 8.5 | 10 | 11 |
| Methods | Jitter | ||||
|---|---|---|---|---|---|
| No. of Nodes | 100 | 200 | 300 | 400 | 500 |
| CL-HHO | 0.45 | 0.41 | 0.39 | 0.36 | 0.35 |
| CL-ALO | 0.53 | 0.48 | 0.45 | 0.41 | 0.39 |
| GWO | 0.60 | 0.58 | 0.56 | 0.53 | 0.50 |
| EECRP | 0.68 | 0.64 | 0.61 | 0.56 | 0.52 |
| HEED | 0.73 | 0.69 | 0.66 | 0.61 | 0.57 |
| Methods | Buffer Occupancy | ||||
|---|---|---|---|---|---|
| No. of Nodes | 100 | 200 | 300 | 400 | 500 |
| CL-HHO | 4 | 5 | 8 | 10 | 13 |
| CL-ALO | 5 | 7 | 10 | 11 | 14 |
| GWO | 9 | 11 | 13 | 16 | 17 |
| EECRP | 12 | 14 | 16 | 18 | 19 |
| HEED | 14 | 15 | 17 | 20 | 23 |
| Methods | Communication Cost | ||||
|---|---|---|---|---|---|
| No. of nodes | 100 | 200 | 300 | 400 | 500 |
| CL-HHO | 0.04 | 0.05 | 0.08 | 0.12 | 0.14 |
| CL-ALO | 0.07 | 0.10 | 0.12 | 0.15 | 0.19 |
| GWO | 0.09 | 0.12 | 0.15 | 0.18 | 0.22 |
| EECRP | 0.10 | 0.13 | 0.16 | 0.18 | 0.24 |
| HEED | 0.12 | 0.16 | 0.21 | 0.23 | 0.30 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xue, X.; Shanmugam, R.; Palanisamy, S.; Khalaf, O.I.; Selvaraj, D.; Abdulsahib, G.M. A Hybrid Cross Layer with Harris-Hawk-Optimization-Based Efficient Routing for Wireless Sensor Networks. Symmetry 2023, 15, 438. https://doi.org/10.3390/sym15020438
Xue X, Shanmugam R, Palanisamy S, Khalaf OI, Selvaraj D, Abdulsahib GM. A Hybrid Cross Layer with Harris-Hawk-Optimization-Based Efficient Routing for Wireless Sensor Networks. Symmetry. 2023; 15(2):438. https://doi.org/10.3390/sym15020438
Chicago/Turabian StyleXue, Xingsi, Ramalingam Shanmugam, SatheeshKumar Palanisamy, Osamah Ibrahim Khalaf, Dhanasekaran Selvaraj, and Ghaida Muttashar Abdulsahib. 2023. "A Hybrid Cross Layer with Harris-Hawk-Optimization-Based Efficient Routing for Wireless Sensor Networks" Symmetry 15, no. 2: 438. https://doi.org/10.3390/sym15020438
APA StyleXue, X., Shanmugam, R., Palanisamy, S., Khalaf, O. I., Selvaraj, D., & Abdulsahib, G. M. (2023). A Hybrid Cross Layer with Harris-Hawk-Optimization-Based Efficient Routing for Wireless Sensor Networks. Symmetry, 15(2), 438. https://doi.org/10.3390/sym15020438








