Containment Control Problem of Linear Multiagent Systems with External Disturbance and DoS Attacks
Abstract
:1. Introduction
2. Preliminaries and Problem Statement
Notations and Preliminary Results
- (i)
- rank() = rank(B) = p,
- (ii)
- rank , where
3. Main Results
3.1. Containment Control of MASs with Directed Communication Graph without Attacks
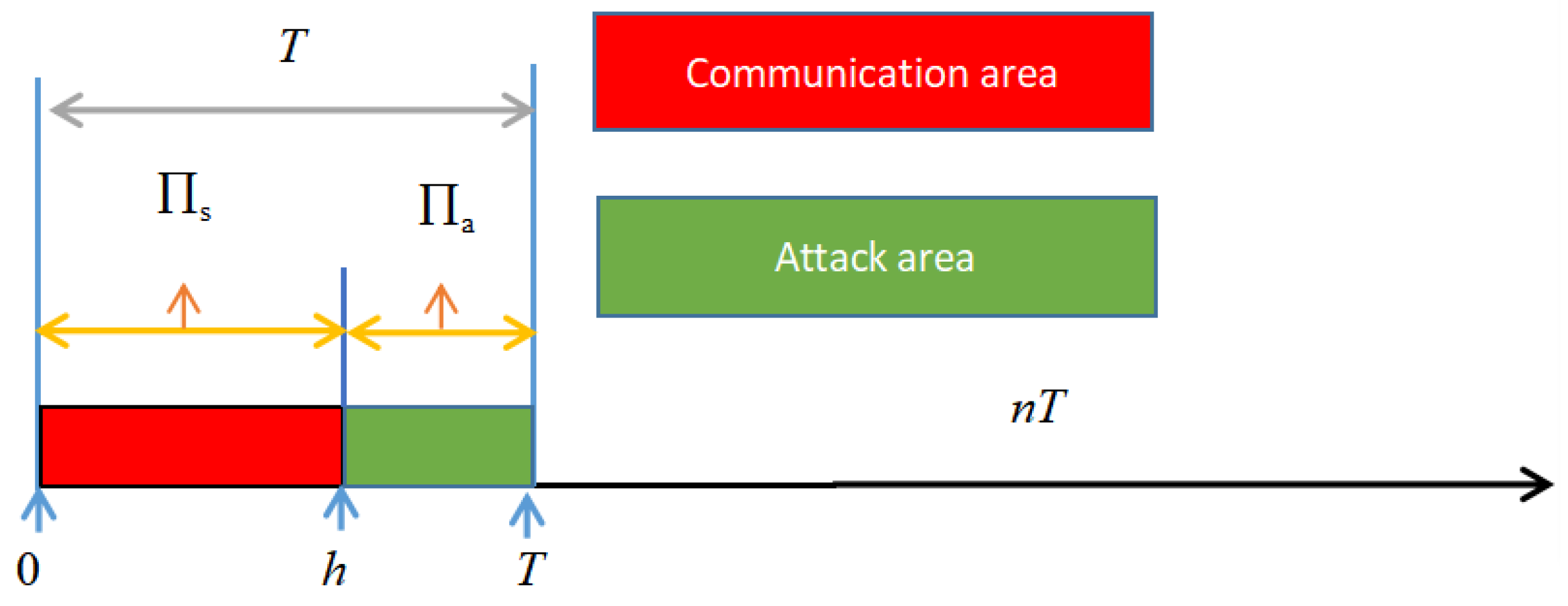
3.2. Containment Control of MASs with DoS Attacks
- (1)
- For , and .
- (2)
- For , and .
- (3)
- For , and .
- (4)
- For , and
- (5)
- For , i.e.,
- (6)
- For , i.e.,
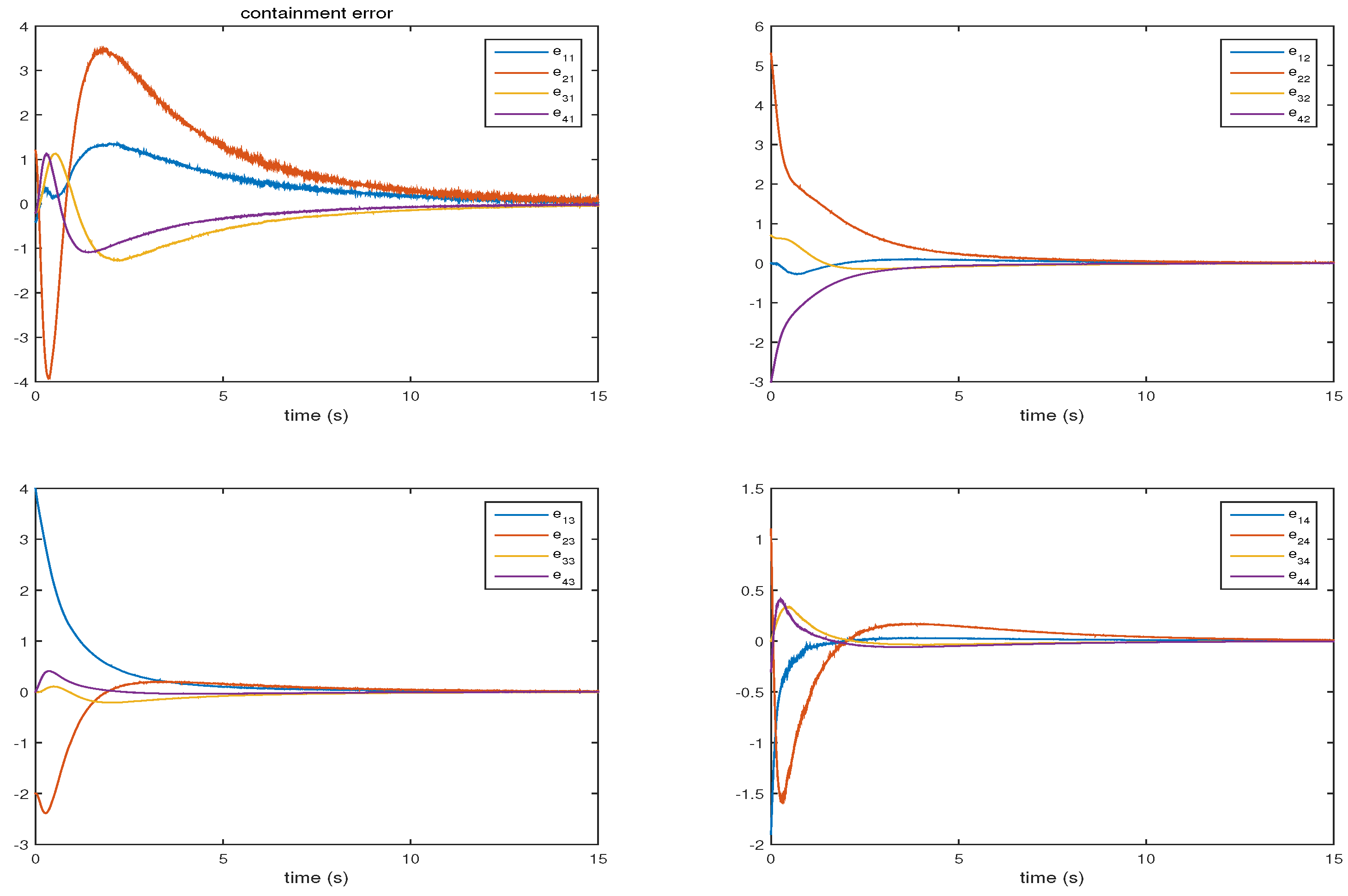
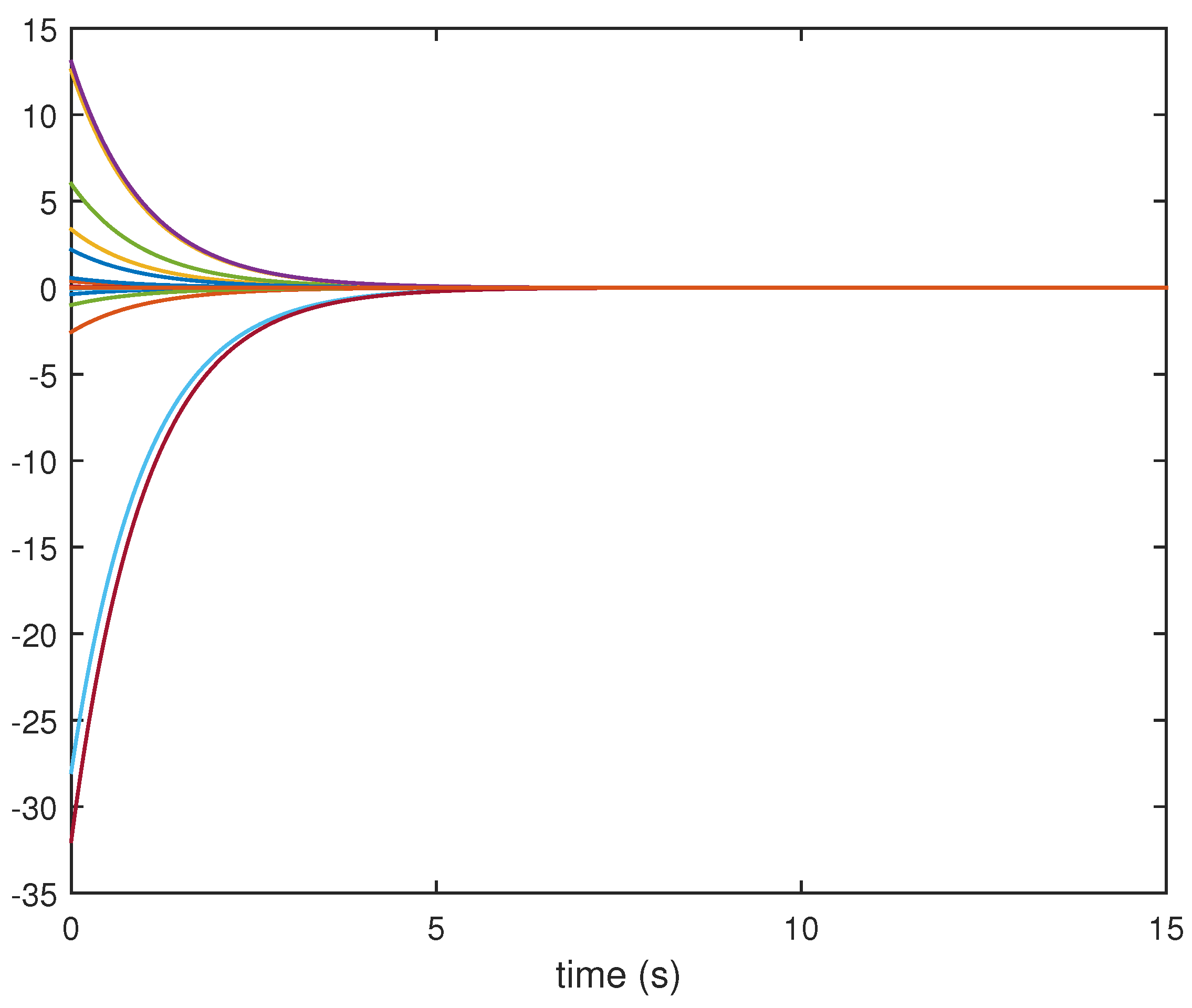
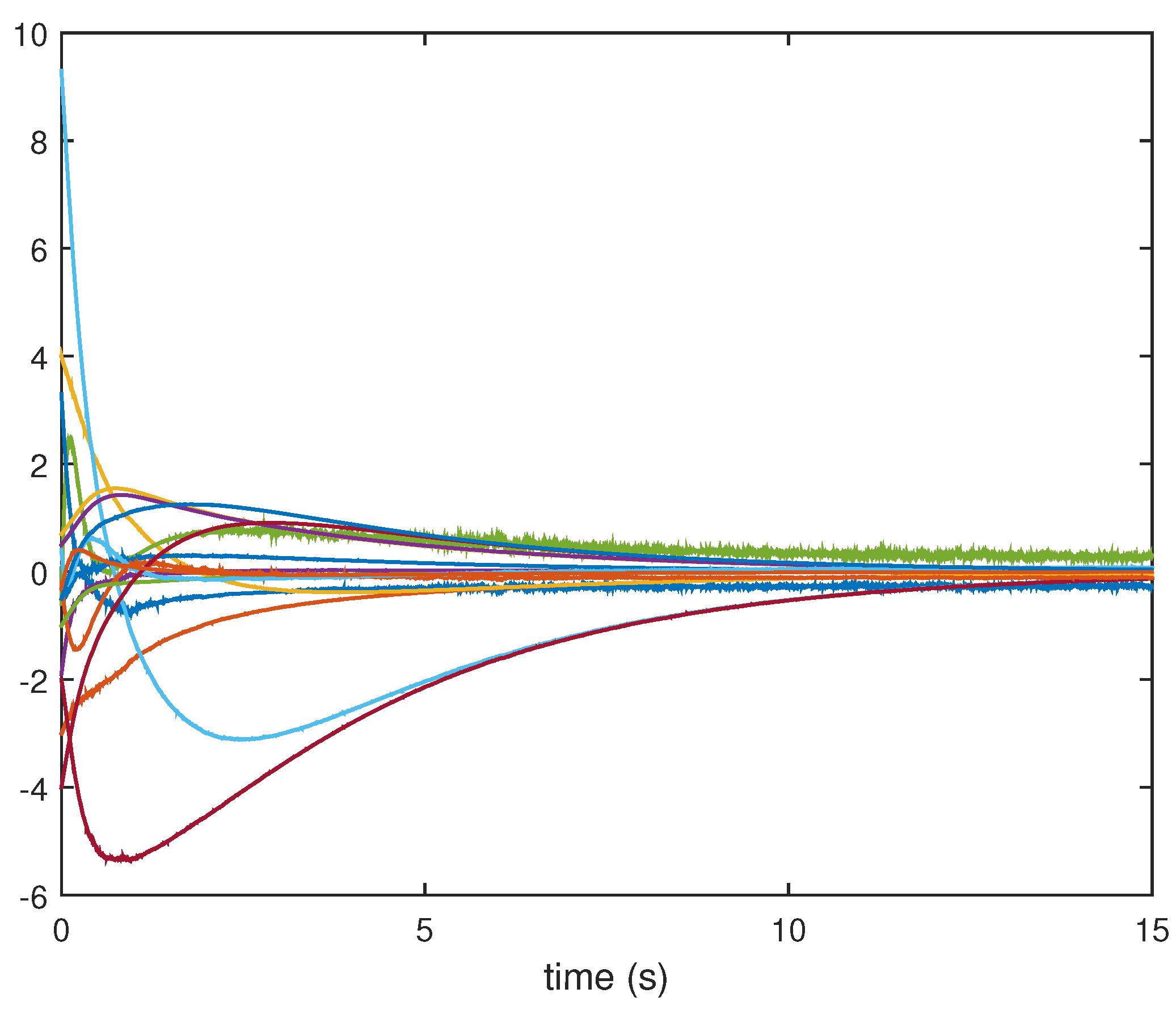
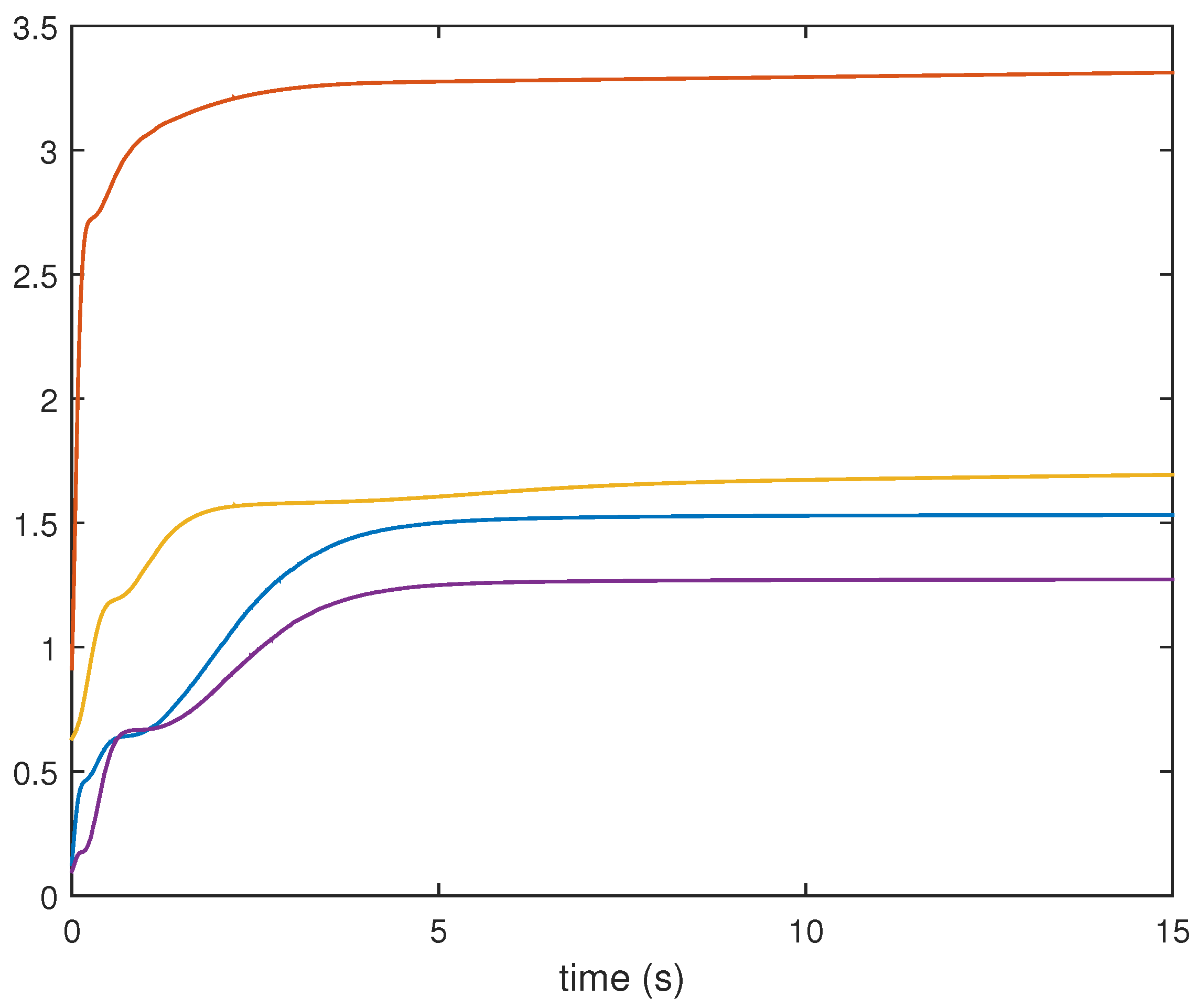
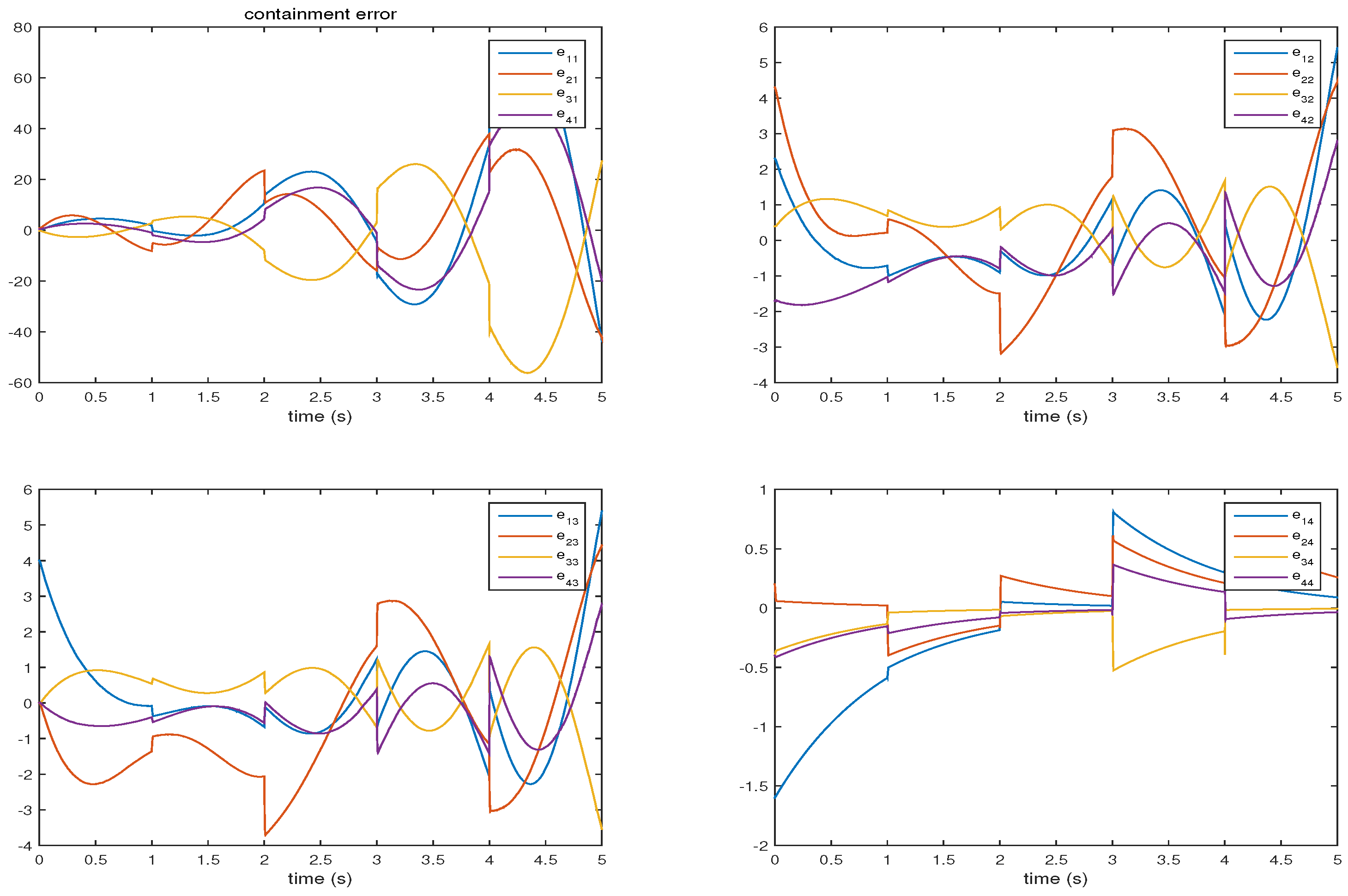
4. Numerical Example
5. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Oh, K.; Park, M.C.; Ahn, H.S. A survey of multi-agent formation control. Automatica 2015, 53, 424–440. [Google Scholar] [CrossRef]
- Saber, R.O. Flocking for multi-agent dynamic systems: Algorithms and theory. IEEE Trans. Autom. Control 2006, 51, 401–420. [Google Scholar] [CrossRef]
- Fu, J.J.; Wang, J.Z. Observer-based finite-time coordinated tracking for general linear multi-agent systems. Automatica 2016, 66, 231–237. [Google Scholar] [CrossRef]
- Sun, J.; Geng, Z.; Lv, Y.; Li, Z.; Ding, Z. Distributed Adaptive Consensus Disturbance Rejection for Multi-Agent Systems on Directed Graphs. IEEE Trans. Control Netw. Syst. 2018, 5, 629–639. [Google Scholar] [CrossRef]
- Wang, P.; Wen, G.; Yu, X.; Yu, W.; Lv, Y. Consensus Disturbance Rejection for Linear Multiagent Systems With Directed Switching Communication Topologies. IEEE Trans. Control Netw. Syst. 2020, 7, 254–265. [Google Scholar] [CrossRef]
- Ma, Q.; Miao, G.Y. Distributed containment control of linear multi-agent systems. Neurocomputing 2014, 133, 399–403. [Google Scholar] [CrossRef]
- Li, Z.K.; Ren, W.; Liu, X.D.; Fu, M.Y. Distributed containment control of multi-agent systems with general linear dynamics in the presence of multiple leaders. Int. J. Robust Nonlinear Control 2013, 23, 534–547. [Google Scholar] [CrossRef]
- Zuo, S.; Song, Y.D.; Lewis, F.L.; Davoudi, A. Adaptive output containment control of heterogeneous multi-agent systems with unknown leaders. Automatica 2018, 92, 235–239. [Google Scholar] [CrossRef]
- Li, Z.; Liu, X.; Fu, M.; Xie, L. Global H∞ consensus of multi-agent systems with Lipschitz non-linear dynamics. IET Control Theory Appl. 2012, 6, 2041–2048. [Google Scholar] [CrossRef]
- Wang, C.; Sun, J.; Zuo, Z.; Ding, Z. Consensus disturbance rejection of network-connected dynamic systems with input delay and unknown network connectivity. IFAC Pap. Line 2017, 50, 10357–10362. [Google Scholar] [CrossRef]
- Zegzhda, D.; Lavrova, D.; Pavlenko, E.; Shtyrkina, A. Cyber attack prevention based on evoluttional cybernetics approach. Symmetry 2020, 12, 1931. [Google Scholar] [CrossRef]
- Zegzhda, D.; Lavrova, D.; Shtyrkina, A. multifractal analysis of internet backbone traffic for denial of service attacks. Autom. Control Comput. Sci. 2018, 52, 936–994. [Google Scholar] [CrossRef]
- Zhang, H.; Cheng, P.; Shi, L.; Chen, J. Optimal dental-of-service attack scheduling with energy constrain. IEEE Trans. Control Netw. Syst. 2015, 6, 3023–3028. [Google Scholar]
- Zha, L.; Liu, J.; Cao, J. Resilient event-triggered consensus control for nonlinear muti-agent systems with DoS attacks. J. Frankl. Inst. 2019, 356, 7071–7090. [Google Scholar] [CrossRef]
- Xu, Y.; Fang, M.; Shi, P.; Wu, Z. Event-based secure consensus of mutiagent systems against DoS attacks. IEEE Trans. Cybern. 2020, 50, 3468–3476. [Google Scholar] [CrossRef]
- Tang, Y.; Zhang, D.; Shi, P.; Zhang, W.; Qian, F. Event-based formation control for nonlinear multi-agent systems under DoS attacks. IEEE Trans. Autom. Control 2021, 66, 452–459. [Google Scholar] [CrossRef]
- Han, T.; Li, J.; Guan, Z.H.; Cai, C.X.; Zhang, D.X.; He, D.X. Containment control of multi-agent systems via a disturbance observer-based approach. J. Frankl. Inst. 2019, 356, 2919–2933. [Google Scholar] [CrossRef]
- Du, X.N.; Yu, H. Consensus of multi-agent systems with delayed sampled-data and directed topologies. Neurocomputing 2019, 363, 78–87. [Google Scholar] [CrossRef]
- Horn, R.; Johnson, C. Matrix Analysis; Cambridge University Press: New York, NY, USA, 1985. [Google Scholar]
- Bernstein, D. Matrix Mathematics: Theory, Facts, and Formulas; Princeton University Press: Princeton, NJ, USA, 2009. [Google Scholar]
- Jiang, B.; Wang, J.; Soh, Y. An adaptive technique for robust diagnosis of faults with independent effects on system outputs. Int. J. Control 2002, 75, 792–802. [Google Scholar] [CrossRef]
- Feng, Z.; Hu, G.; Wen, G. Distributed consensus tracking for multi-agent systems under two types of attacks. Int. J. Robust Nonlinear Control 2016, 26, 896–918. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, X.; Luo, H.; Chen, W.; Gao, L. Containment Control Problem of Linear Multiagent Systems with External Disturbance and DoS Attacks. Symmetry 2023, 15, 384. https://doi.org/10.3390/sym15020384
Xu X, Luo H, Chen W, Gao L. Containment Control Problem of Linear Multiagent Systems with External Disturbance and DoS Attacks. Symmetry. 2023; 15(2):384. https://doi.org/10.3390/sym15020384
Chicago/Turabian StyleXu, Xiaole, Huan Luo, Wenhai Chen, and Lixin Gao. 2023. "Containment Control Problem of Linear Multiagent Systems with External Disturbance and DoS Attacks" Symmetry 15, no. 2: 384. https://doi.org/10.3390/sym15020384
APA StyleXu, X., Luo, H., Chen, W., & Gao, L. (2023). Containment Control Problem of Linear Multiagent Systems with External Disturbance and DoS Attacks. Symmetry, 15(2), 384. https://doi.org/10.3390/sym15020384





