Private Set Intersection Based on Lightweight Oblivious Key-Value Storage Structure
Abstract
:1. Introduction
- We propose a new OKVS method, 3H-GCG, whose decoding algorithm consists of two arithmetic formulas, which is less dependent on auxiliary locations, and can be easily adapted to the PSI protocol.
- We leverage the newly proposed 3H-GCG to design a two-party PSI protocol. Our approach incorporates the OKVS and VOLE paradigm [15,16], providing resilience against malicious adversaries. We offer security proofs for our two-party PSI protocol under semi-honest security settings and malicious security settings, respectively.
- We implemented the proposed 3H-GCG and two-party PSI protocols and compared them with existing PSI protocols. When the set size is –, our PSI protocol is less computationally intensive than other existing protocols. The experiments show that for our OKVS, 3H-GCG, the ratio of raw data to constructed data is improved by about 7.5% compared to other existing OKVSs. Under the semi-honest security setting, our PSI protocol achieves the fastest runtime with a set size of . Under the malicious security setting, our PSI protocol has about 10% improvement in communication compared to existing protocols.
2. Preliminaries and Backgrand
2.1. Notation
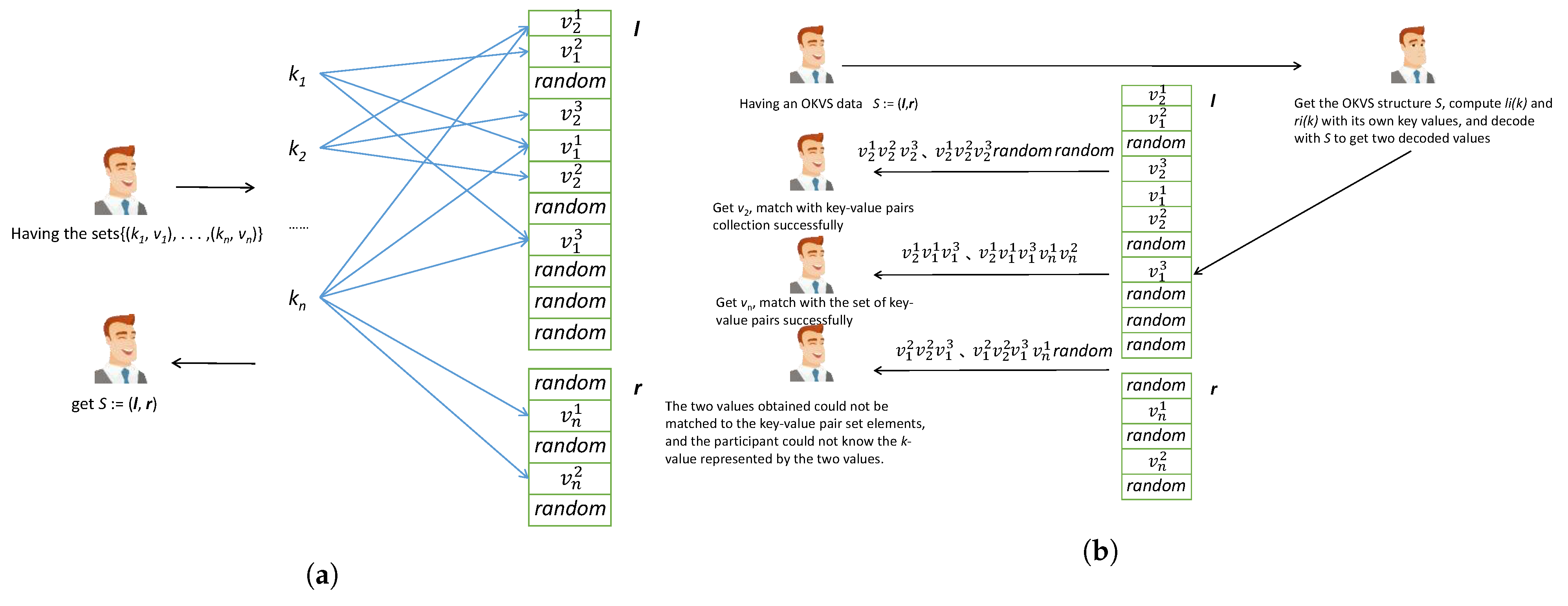
2.2. OKVS Structure Definition and Property
- : The input is a set of key-value pairs and the output is an object S. In rare cases, an error indicator ⊥ may be outputted instead.
- : The input is an object S and a key k, and the output is a value v. A KVS is considered correct if for all subsets A of with distinct keys, the following holds: if is in A and , then .
- Security of OKVS: An OKVS is composed of an encode and a decode algorithm. Encode takes as input a set of key-value pairs (, ) and returns a data structure S. Decode takes as input a data structure like S and a key value k, and outputs a result. Decode can be called on any key, but if it is called on one of the keys used to generate , then the result is the corresponding . The most fundamental property of an OKVS is that when is random, S hides , reducing the probability that the value of the original data k will be leaked and increasing its security.
2.3. OKVS Construction Based on Cuckoo Hash Graph
2.4. Security Model
- Semi-honest security model: For the protocol , if there exist probabilistic polynomial-time adversaries and such that for all inputs X and Y, the following equation is satisfied:
- Malicious security model: For protocol , for malicious participants and under the realistic model that can arbitrarily deviate from the protocol, there exist probabilistic polynomial-time adversaries and under the ideal model such that for all inputs X and Y, the following equation is satisfied:
2.5. Related Work
3. Proposed OKVS
3.1. OKVS Construction Based on Cuckoo Hash Graph
3.2. Parameter Analysis
- Choices of , : Since and control the collision probability of the PSI protocol, and can be set to in a semi-honest security setting, where and denote the number of elements of the sender and receiver sets, respectively. Under the malicious security setting, and can be set to , with and denoting the number of queries that the sender and receiver can make to the and random prediction machines, respectively.
- Choices of m, r: In the 3H-GCG mechanism, , where , . To ensure the success of encoding, and are taken. In this scheme, the encoding fails when the auxiliary position is less than at the time of encoding. Refer to [18] for specific calculations.
4. Private Set Intersection
4.1. OPRF-Based Vector-OLE
4.2. PSI Protocol Description
5. Theoretical Analysis
5.1. Correctness Analysis
5.2. Security Analysis
- Before the participating parties start executing the PSI protocol, the simulator M waits for the messages y sent by the malicious sender instead of the OPRF model, and all the y sent from the set .
- After the malicious sender sends and to the simulator M, M computes s.t. and then execute the PSI protocol with . Since the simulator has ruled out the collision case , the above simulation is correct and indistinguishable. However, there exists the case where the probability of having an element x in the set X of senders satisfying is , which is overall indistinguishable. We prove it using the following hybrid argument:
- The simulator M replaces the OPRF model and when the malicious recipient sends a query message to M, the simulator records the set X of messages sent by the malicious recipient and sends the response message after the query to the malicious recipient.
- The simulator executes the PSI protocol with the collected X and the Y held by itself as input to obtain the intersection set Z.
- The simulator uses the elements in Z and the consistent values of the non-intersecting elements in Y to input into OPRF for calculation, the calculated values are assembled into , and is sent to the malicious recipient.
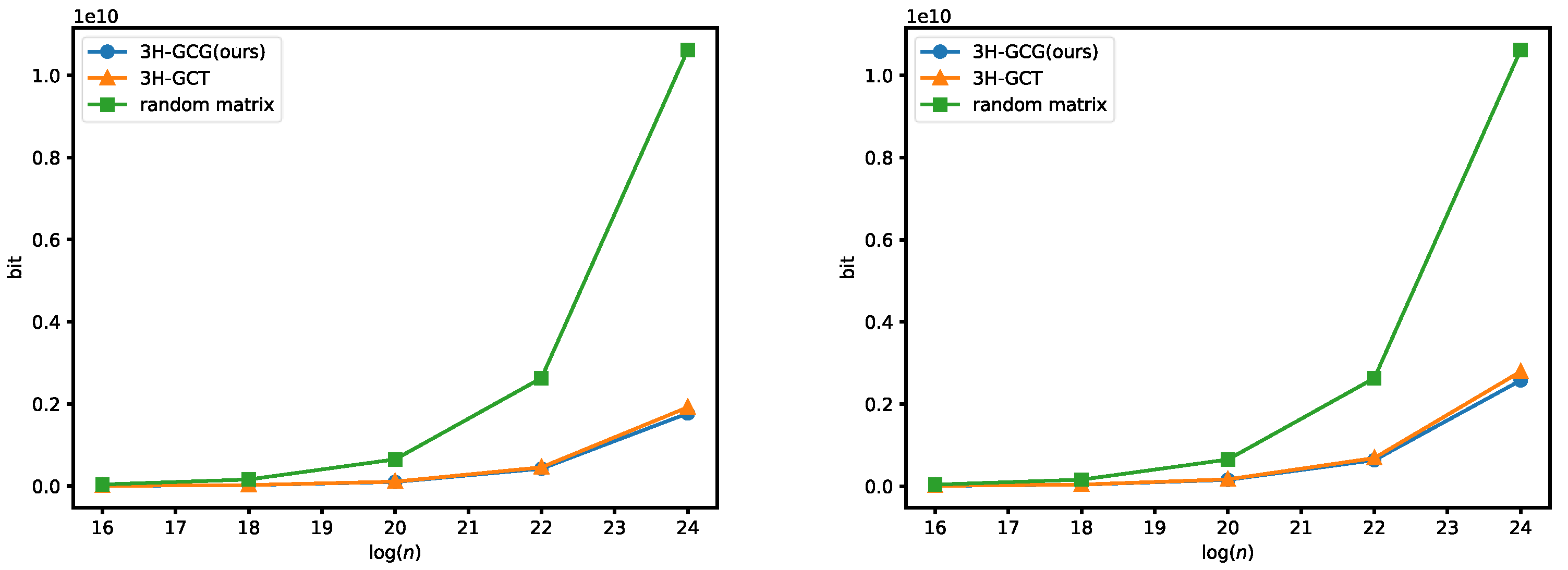
6. Theoretical Efficacy Analysis and Experimental Comparison
6.1. OKVS Part
6.2. PSI Part
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Areekijseree, K.; Tang, Y.; Chen, J. Secure and Efficient Multi-Party Directory Publication for Privacy-Preserving Data Sharing. In Proceedings of the SecureComm, Singapore, 8–10 August 2018; Volume 254, pp. 71–94. [Google Scholar]
- Karl, R.; Takeshita, J.; Mohammed, A.; Striegel, A.; Jung, T. Cryptonomial: A Framework for Private Time-Series Polynomial Calculations. In Proceedings of the SecureComm, Virtual, 6–9 September 2021; Volume 398, pp. 332–351. [Google Scholar]
- Rindal, P.; Rosulek, M. Improved Private Set Intersection Against Malicious Adversaries. In Proceedings of the EUROCRYPT, Paris, France, 4 May 2017; Volume 10210, pp. 235–259. [Google Scholar]
- Rindal, P.; Rosulek, M. Malicious-secure private set intersection via dual execution. In Proceedings of the CCS, Dallas, TX, USA, 3 November 2017; pp. 1229–1242. [Google Scholar]
- Garimella, G.; Rosulek, M.; Singh, J. Structure-Aware Private Set Intersection, with Applications to Fuzzy Matching. In Proceedings of the CRYPTO, Santa Barbara, CA, USA, 15–18 August 2022; pp. 323–352. [Google Scholar]
- Freedman, M.J.; Hazay, C.; Nissim, K.; Pinkas, B. Efficient Set Intersection with Simulation-Based Security. In Proceedings of the CRYPTO, Santa Barbara, CA, USA, 14–18 August 2016; pp. 115–155. [Google Scholar]
- Blanton, M.; Aguiar, E. Private and oblivious set and multiset operations. Int. J. Inf. Sec. 2016, 15, 493–518. [Google Scholar]
- Hazay, C. Oblivious Polynomial Evaluation and Secure Set-Intersection from Algebraic PRFs. J. Cryptol. 2018, 31, 537–586. [Google Scholar]
- Nevo, O.; Trieu, N.; Yanai, A. Simple, fast malicious multiparty private set intersection. In Proceedings of the CCS, Virtual, 15–19 November 2021; pp. 1151–1165. [Google Scholar]
- Zhu, K.; Chen, W.; Jiao, L.; Wang, J.; Peng, Y.; Zhang, L. Online training data acquisition for federated learning in cloud-edge networks. J. Comput. Netw. 2023, 223, 109556. [Google Scholar] [CrossRef]
- Freedman, M.J.; Nissim, K.; Pinkas, B. Efficient Private Matching and Set Intersection. In Proceedings of the EUROCRYPT, Interlaken, Switzerland, 2–6 May 2004; pp. 1–19. [Google Scholar]
- Pinkas, B.; Schneider, T.; Weinert, C.; Wieder, U. Efficient Circuit-Based PSI via Cuckoo Hashing. In Proceedings of the EUROCRYPT, Tel Aviv, Israel, 29 April–3 May 2018; pp. 125–157. [Google Scholar]
- Pinkas, B.; Rosulek, M.; Trieu, N.; Yanai, A. SpOT-Light: Lightweight Private Set Intersection from Sparse OT Extension. In Proceedings of the CRYPTO, Santa Barbara, CA, USA, 18–22 August 2019; pp. 401–431. [Google Scholar]
- Orrù, M.; Orsini, E.; Scholl, P. Actively Secure 1-out-of-N OT Extension with Application to Private Set Intersection. In Proceedings of the CT-RSA, San Francisco, CA, USA, 14–17 February 2017; pp. 381–396. [Google Scholar]
- Rindal, P.; Schoppmann, P. VOLE-PSI: Fast OPRF and Circuit-PSI from Vector-OLE. In Proceedings of the EUROCRYPT, Zagreb, Croatia, 17–21 October 2021; pp. 901–930. [Google Scholar]
- Rindal, P.; Raghuraman, S. Blazing Fast PSI from Improved OKVS and Subfield VOLE. In Proceedings of the CCS, Los Angeles, CA, USA, 7–11 November 2022; pp. 2505–2517. [Google Scholar]
- Pinkas, B.; Rosulek, M.; Trieu, N.; Yanai, A. PSI from PaXoS: Fast, malicious private set intersection. In Proceedings of the EUROCRYPT, Virtual, 11–15 May 2020; pp. 739–767. [Google Scholar]
- Garimella, G.; Pinkas, B.; Rosulek, M.; Yanai, A. Oblivious Key-Value Stores and Amplification for Private Set Intersection. In Proceedings of the CRYPTO, Virtual, 16–20 August 2021; pp. 395–425. [Google Scholar]
- Manulis, M.; Pinkas, B.; Poettering, B. Privacy-Preserving Group Discovery with Linear Complexity. In Proceedings of the ACNS, Beijing, China, 22–25 June 2010; pp. 420–437. [Google Scholar]
- Kolesnikov, V.; Matania, N.; Pinkas, B. Practical multi-party private set intersection from symmetric-key techniques. In Proceedings of the CCS, Dallas, TX, USA, 30 October–3 November 2017; pp. 1257–1272. [Google Scholar]
- Pinkas, B.; Schneider, T.; Tkachenko, O.; Yanai, A. Efficient Circuit-Based PSI with Linear Communication. In Proceedings of the EUROCRYPT, Darmstadt, Germany, 19–23 May 2019; pp. 122–153. [Google Scholar]
- Kolesnikov, V.; Rosulek, M.; Trieu, N.; Wang, B. Scalable Private Set Union from Symmetric-Key Techniques. In Proceedings of the ASIACRYPT, Kobe, Japan, 8–12 December 2019; pp. 636–666. [Google Scholar]
- Schoppmann, P.; Gascon, A.; Reichert, L.; Raykova, M. Distributed Vector-OLE: Improved Constructions and Implementation. In Proceedings of the CCS, New York, NY, USA, 11–15 November 2019; pp. 1055–1072. [Google Scholar]
- Meadows, C. A more efficient cryptographic matchmaking protocol for use in the absence of a continuously available third party. In Proceedings of the S&P, Oakland, CA, USA, 7–9 April 1986; pp. 134–137. [Google Scholar]
- Kolesnikov, V.; Kumaresan, R.; Rosulek, M.; Trieu, N. Efficient batched oblivious PRF with applications to private set intersection. In Proceedings of the CCS, Vienna, Austria, 24–28 October 2016; pp. 818–829. [Google Scholar]
- Changyu, D.; Liqun, C.; Zikai, W. When private set intersection meets big data: An efficient and scalable protocol. In Proceedings of the CCS, Berlin, Germany, 4–8 November 2013; pp. 789–800. [Google Scholar]
- Chase, M.; Miao, P. Private Set Intersection in the Internet Setting from Lightweight Oblivious PRF. In Proceedings of the CRYPTO, Santa Barbara, CA, USA, 17–21 August 2020; pp. 34–63. [Google Scholar]
- Wang, P.; Wu, X.; He, X. Vibration-Theoretic Approach to Vulnerability Analysis of Nonlinear Vehicle Platoons. J. IEEE Trans. Intell. Transp. Syst. 2023, 24, 11334–11344. [Google Scholar] [CrossRef]




| n | m | r | (Semi-Honest) | (Malicious) |
|---|---|---|---|---|
| 1.2n | 134 | 72 | 120 | |
| 1.2n | 135 | 76 | 122 | |
| 1.2n | 135 | 80 | 124 | |
| 1.2n | 136 | 84 | 126 | |
| 1.2n | 137 | 88 | 128 |
| OKVS | Encoding Cost | (Batch) Decoding Cost | Rate |
|---|---|---|---|
| polynomial | 1 | ||
| random matrix (binary) | 1 | ||
| random matrix (linear) | |||
| garbled bloom filter | |||
| PaXoS [17] | 0.4- | ||
| 3H-GCT [18] (binary) | 0.8- | ||
| 3H-GCT [18] (linear) | 0.8- | ||
| 3H-GCG(ours) (binary) | 0.86- | ||
| 3H-GCG(ours) (linear) | 0.86- |
| Protocals | Communication | |||
|---|---|---|---|---|
| Semi-Honest PSI | ||||
| DH-PSI [24] | 584n | 592n | 600n | |
| KKRT16 [25] | 984n | 1008n | 1032n | |
| PRTY19 low-Comm [13] | 509n | 513n | 517n | |
| PRTY19 fast [13] | 603n | 619n | 635n | |
| PRTY20 [17] | 1208n | 1268n | 1302n | |
| CM20 [27] | 678n | 694n | 702n | |
| RS21 w = 2 [15] | 914n | 426n | 398n | |
| GPR+21 star [18] | 780n | 788n | 804n | |
| OURS | 507n | 515n | 523n | |
| Malicious PSI | ||||
| PRTY20 [17] | 1766n | |||
| GPR+21 star [18] | 1357n | |||
| OURS | 1165n | |||
| Protocol | Setting | Running Time (Set Size n) (ms) | Communication (MB) | ||||||
|---|---|---|---|---|---|---|---|---|---|
| DH-PSI [24] | se | 31,378 | 127,893 | 518,620 | 2,063,949 | 4.69 | 19 | 76 | 308 |
| KKRT16 [25] | se | 99 | 406 | 1170 | 7916 | 7.73 | 31.88 | 128.5 | 530.1 |
| PRTY20 (w = 2) [17] | se | 534 | 910 | 2673 | 18,806 | 13.21 | 54.56 | 224.5 | 861.9 |
| CM20 [27] | se | 409 | 1217 | 6515 | 29,148 | 5.343 | 21.75 | 87.66 | 357.6 |
| SpOT-low [21] | se | 878 | 3476 | 14,558 | 90,144 | 3.91 | 15.6 | 63.2 | 253 |
| SpOT-fast [21] | se | 561 | 2354 | 6190 | 36,150 | 4.61 | 18.9 | 76.4 | 314 |
| GPR+21 [18] | se | 129 | 492 | 1365 | 8574 | 5.63 | 22.8 | 96.71 | 385.63 |
| OURS | se | 117 | 392 | 1176 | 8120 | 5.14 | 20.97 | 85.45 | 344.27 |
| RR17a [3] | ma | 1366 | 5619 | - | - | 154.17 | 616.55 | - | - |
| RR17b [4] | ma | 716 | 2727 | 12,010 | - | 95.78 | 383.03 | 1616.03 | - |
| PRTY20 [17] | ma | 476 | 1803 | 3128 | 18,679 | 14.71 | 60.33 | 247.6 | 950 |
| GPR+21 [18] | ma | 146 | 577 | 1674 | 10,134 | 8.68 | 35.59 | 136.66 | 532.97 |
| OURS | ma | 153 | 563 | 1652 | 12,304 | 8.26 | 30.15 | 116.38 | 459.7 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Jiang, Z.; Guo, X.; Yu, T.; Zhou, H.; Wen, J.; Wu, Z. Private Set Intersection Based on Lightweight Oblivious Key-Value Storage Structure. Symmetry 2023, 15, 2083. https://doi.org/10.3390/sym15112083
Jiang Z, Guo X, Yu T, Zhou H, Wen J, Wu Z. Private Set Intersection Based on Lightweight Oblivious Key-Value Storage Structure. Symmetry. 2023; 15(11):2083. https://doi.org/10.3390/sym15112083
Chicago/Turabian StyleJiang, Zhengtao, Xiaoxuan Guo, Ting Yu, Hanyu Zhou, Jiaqi Wen, and Zhengyang Wu. 2023. "Private Set Intersection Based on Lightweight Oblivious Key-Value Storage Structure" Symmetry 15, no. 11: 2083. https://doi.org/10.3390/sym15112083
APA StyleJiang, Z., Guo, X., Yu, T., Zhou, H., Wen, J., & Wu, Z. (2023). Private Set Intersection Based on Lightweight Oblivious Key-Value Storage Structure. Symmetry, 15(11), 2083. https://doi.org/10.3390/sym15112083








