Fuzzy Logic and Its Application in the Assessment of Information Security Risk of Industrial Internet of Things
Abstract
:1. Introduction
- –
- ISO 27400:2022 [18]: This standard offers guidance on principles, information risk assessment, and appropriate IS and privacy controls to mitigate risks associated with the Internet of Things.
- –
- ISA/IEC 62443 [19]: A series of international standards established by the IEC (International Electrotechnical Commission) specifying cybersecurity requirements for Automated Industrial Process Control Systems (APCSs) and Building Control and Management Systems (BCMSs).
- –
2. Proposed Methodology
- Asset attractiveness;
- Asset availability;
- Asset value;
- Asset confidentiality;
- Asset integrity;
- Software and technical controls;
- Administrative controls;
- Procedural controls;
- Compliance of control measures with information security standards;
- Previous incidents.
- Damage related to equipment replacement costs;
- Downtime-related damage to the system;
- Damage associated with response costs;
- Reputational damage.
- –
- Very Low (VL);
- –
- Low (L);
- –
- Medium (M);
- –
- High (H);
- –
- Very High (VH).
- –
- Determining the weights of input linguistic variables, the essence of which is to determine the weight of each input linguistic variable in the rule base. To calculate the weight of each criterion, the method of paired comparisons is used [24]. After filling in the matrix of paired comparisons, the eigenvector is calculated, and this makes it possible to find the weights of the criteria of linguistic variables. These, in turn, are used to calculate the risks of information security.
- –
- Implementation of the information security risk assessment model based on fuzzy logic. This takes place in two research stages:
- –
- Formation of a base of fuzzy production rules to determine the assessment of the probability of occurrence of a threat and assess the level of inflicted damage caused both in interval values and in describing the nature of the risk in the following categories:
- –
- Very low risk;
- –
- Low risk;
- –
- Medium risk;
- –
- High risk;
- –
- Very high risk.
- –
- Evaluation of the correctness of the risk level determination model, which summarizes the studies by obtaining the value:
- –
- The probability of occurrence of threats and the level of possible damage, and
- –
- The risk of information security of the industrial IoT environment.
3. Results
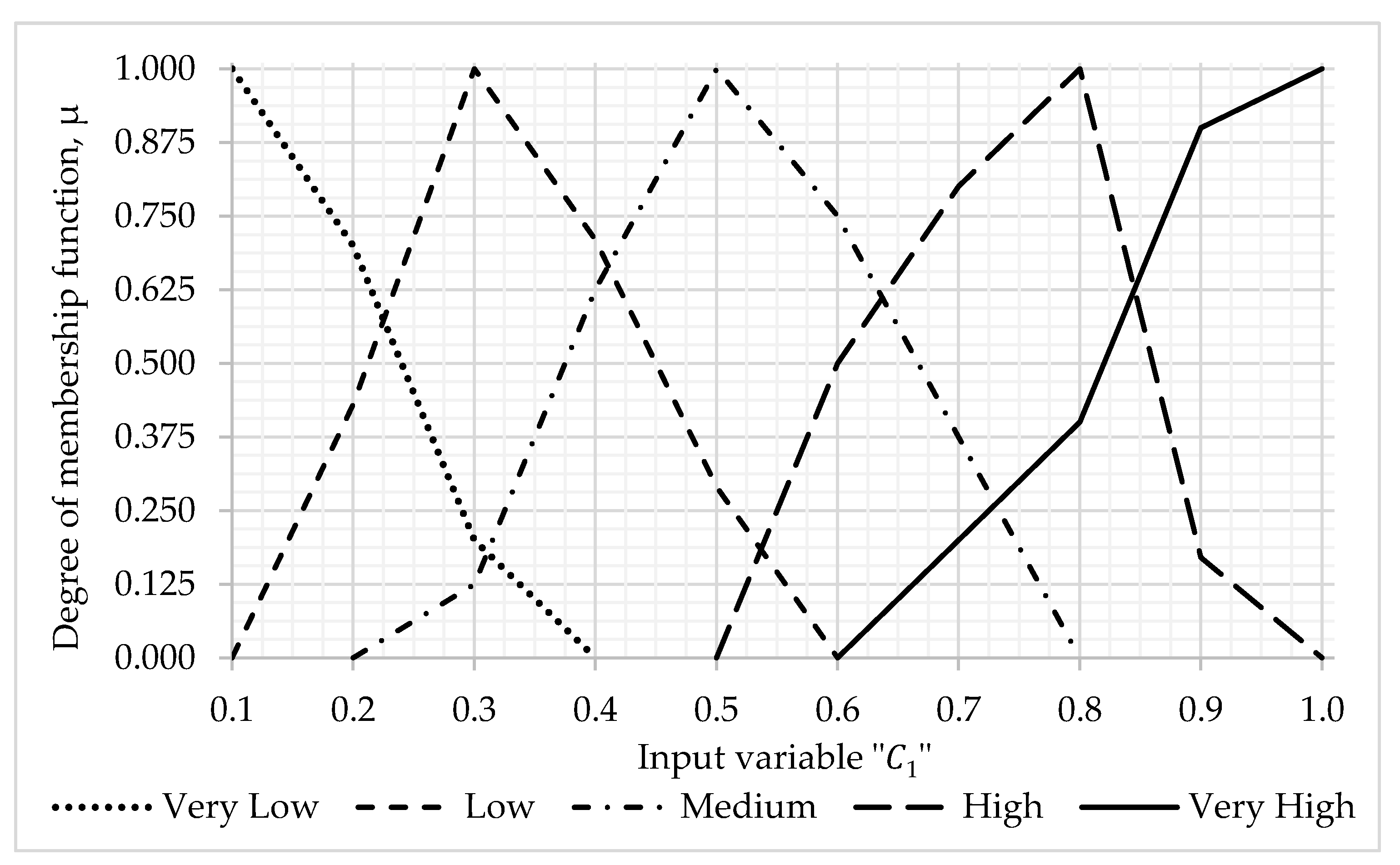
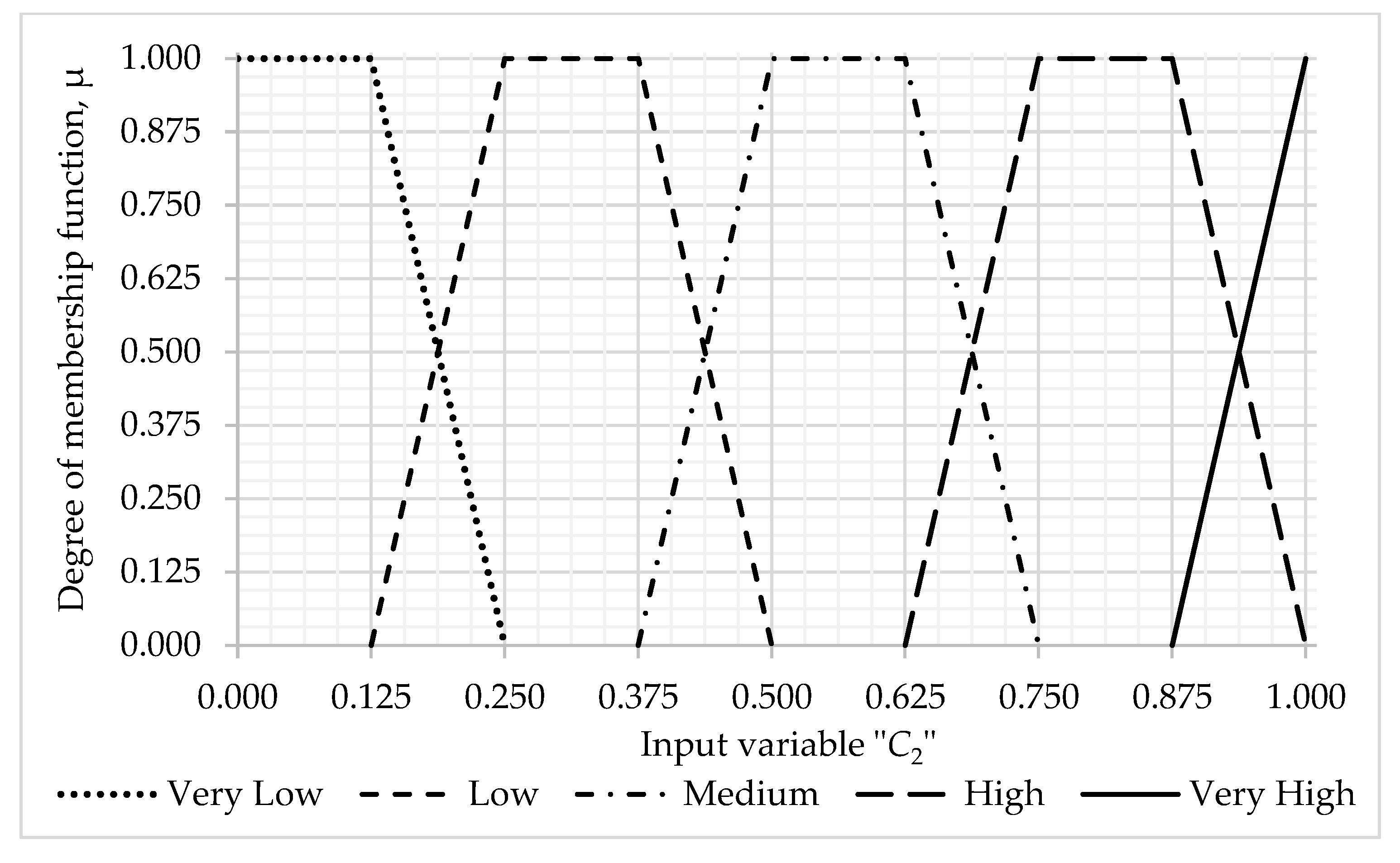
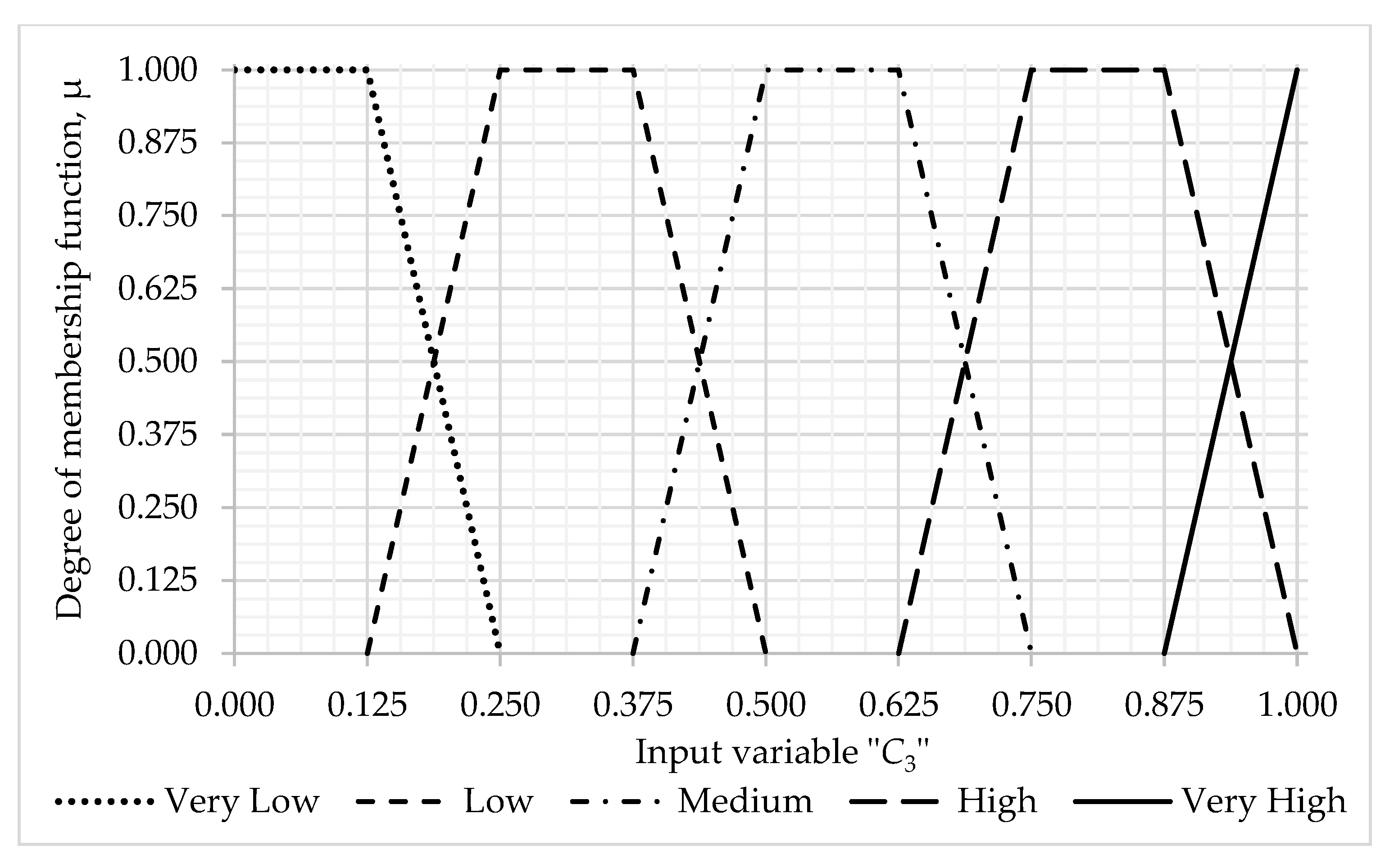
3.1. Algorithm for Assessing the Probability of Occurrence of a Threat
- –
- —asset attractiveness;
- –
- —existing control;
- –
- C3 —previous incidents.
- Is the asset significant to the organization’s business processes?
- Is the asset important to the achievement of the organization’s objectives?
- Is the asset unique to the organization?
- Are there alternatives that can replace the asset?
- Does the asset contain sensitive data?
- Are there safeguards that protect the confidentiality of the information asset?
- Is the asset intact and not subject to change?
- Are there safeguards that protect the integrity of the asset?
- Is the asset easily accessible to the right users?
- Are there safeguards that protect the asset from unauthorized access?
- –
- Protection of network nodes;
- –
- Monitoring of network activity;
- –
- Authentication and authorization;
- –
- Protection from physical attacks;
- –
- Protection against malicious programs;
- –
- Data security;
- –
- Data backup;
- –
- Training.
3.2. Algorithm for Assessing the Level of Inflicted Damage
- –
- —Financial damage;
- –
- —Reputational damage.
3.3. Determining the Weights of Input Linguistic Variables
- –
- Expert estimates of respondents (i)–(v) on the values of pairwise comparison coefficients, —eigenvector and —values of weights according to criteria , и (see Table A1, Table A2 and Table A3, Appendix A);
- –
- Calculated values of weights estimating the level —threat occurrence probability (see Table A3, Appendix A);
- –
- Calculated and values according to criteria C4 and assessing the level of —the damage caused (see Table A4, Appendix A).
3.4. Implementation of the Information Security Risk Assessment Model Based on Fuzzy Logic
3.4.1. Formation of a Base of Fuzzy Production Rules
- –
- Information base of fuzzy production rules for evaluating —probability of occurrence of threats (total 125 rules)—with the values of the terms of the input linguistic variable —attractiveness of assets—with a weight coefficient = 0.4126; —existing control—with a weight coefficient = 0.3952; —previous incidents—with weight coefficient = 0.1929; Very low—0.2, Low—0.4, Medium—0.6, High—0.8; Very high—1.0 and the calculated values of the term boundaries of the output linguistic variable —probability of occurrence of a threat: Very low—[0.0; 0.3], Low—(0.3; 0.5], Medium—(0.5; 0.7], High—(0.7; 0.9], Very High—(0.9; 1.0]) (see Table A5, Appendix A).
- –
- Aggregate fuzzy rules for assessing the probability of occurrence of a threat. Note that aggregation is the process of combining the output parameters of each rule into one fuzzy set. The rules for aggregating fuzzy products are carried out using the classical fuzzy logical operation “AND” of two elementary statements [24,28]. For example, the output variable – the probability of occurrence of a threat occurring–takes on the value “Very Low” in rules No. 1, 2, 3, 6, and 26, which can be combined using a conjunction. As a result of the aggregation of the resulting rules, fuzzy causal relationships between antecedents and consequents were obtained (see Table A6, Appendix A).
- –
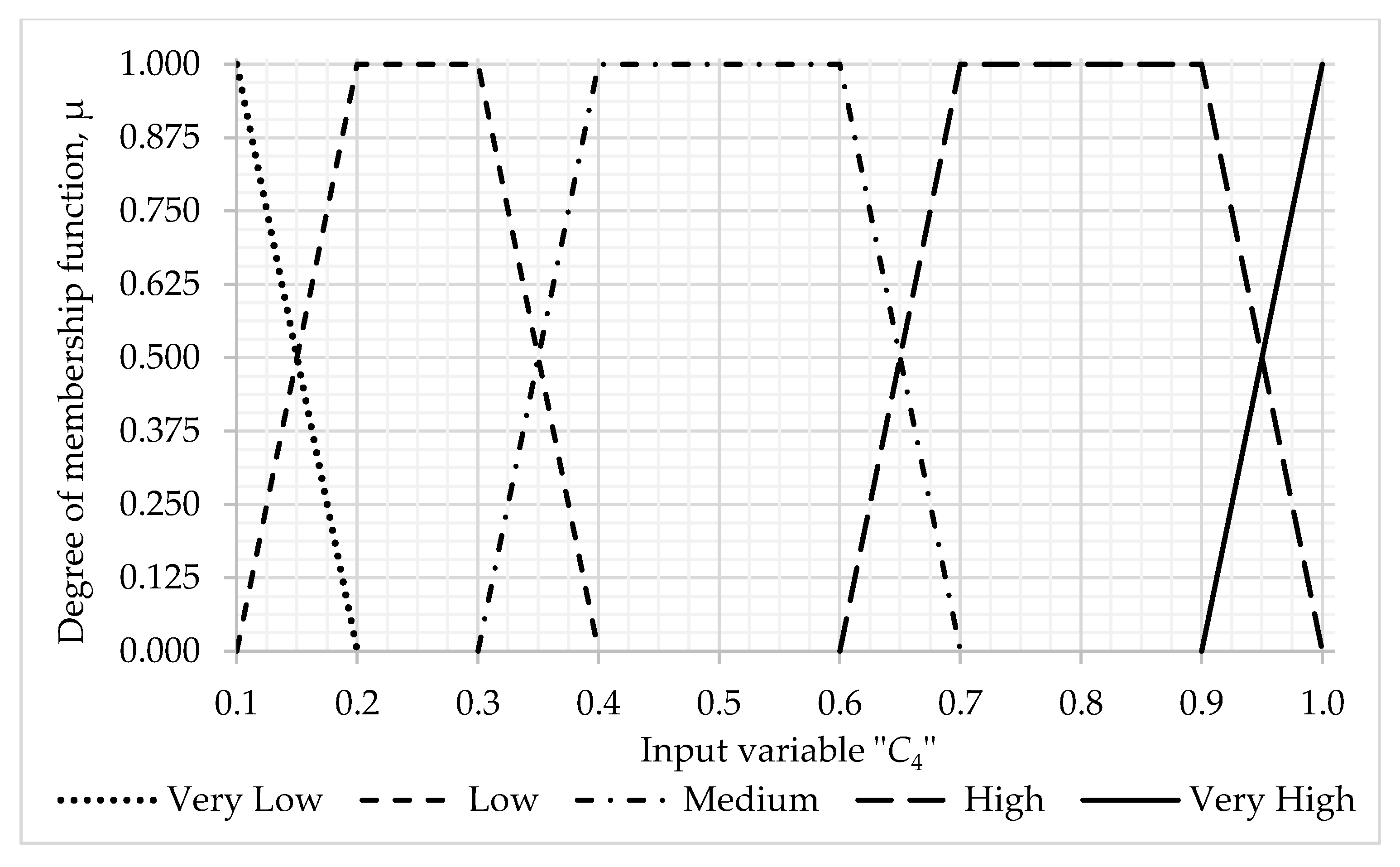
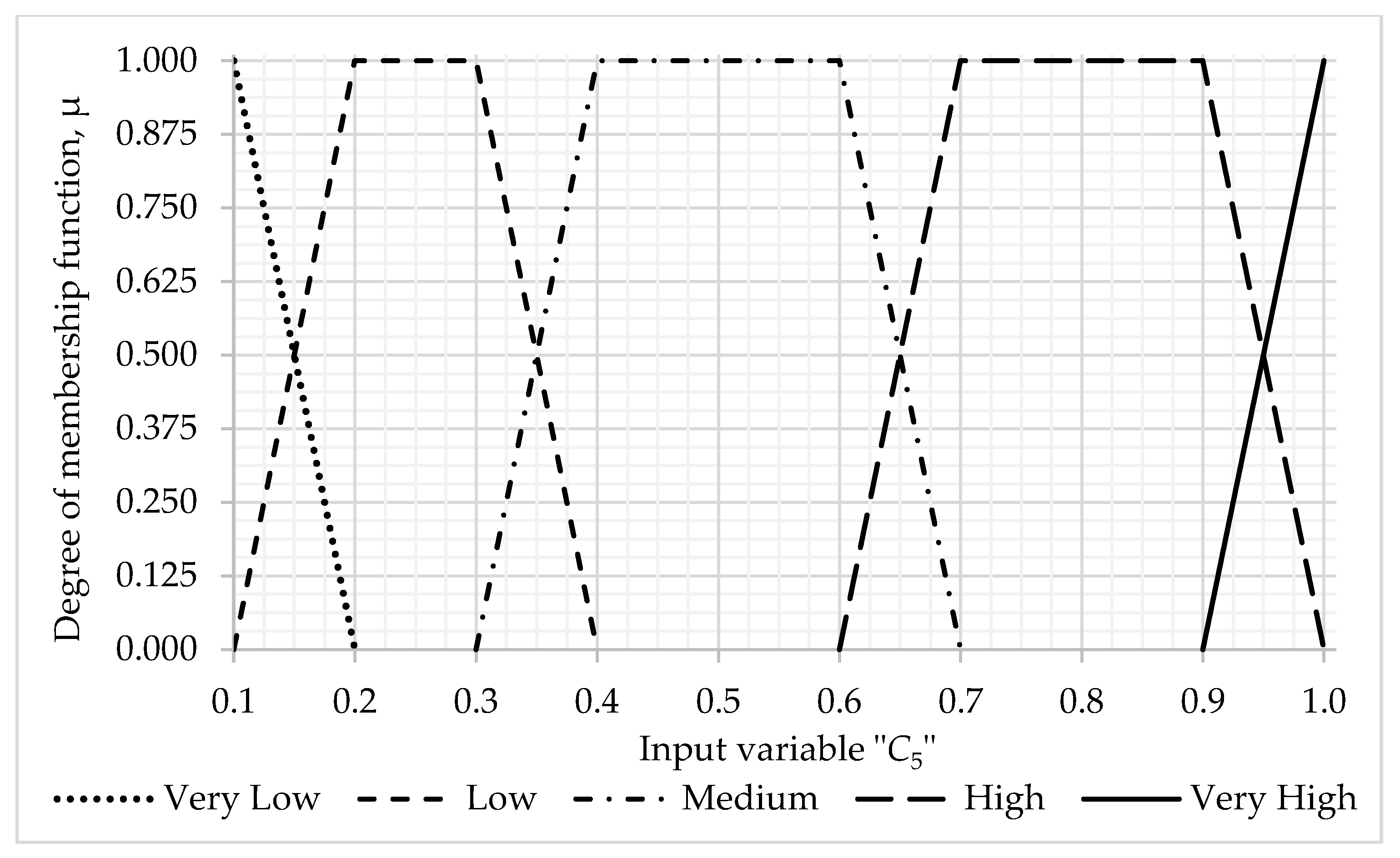
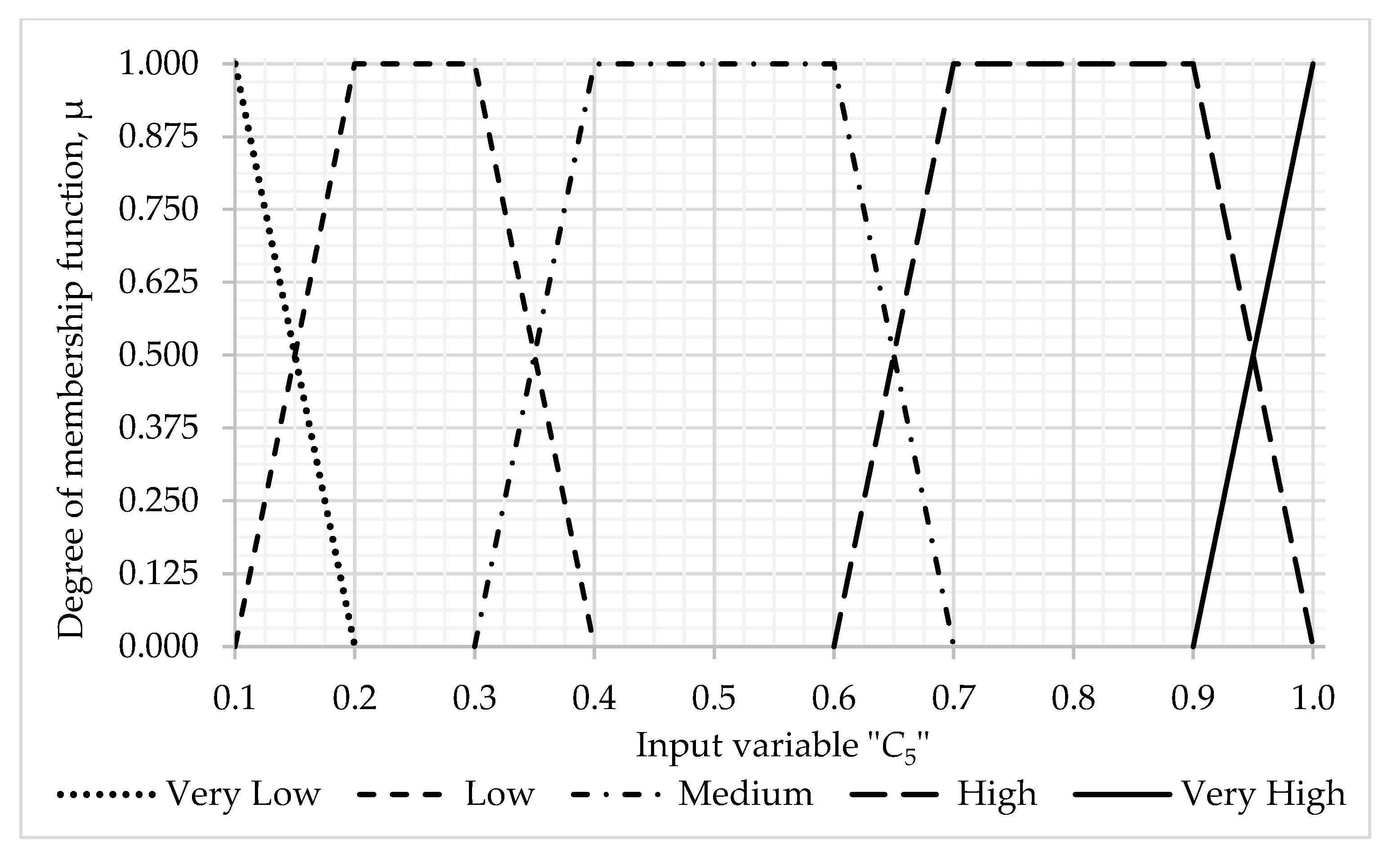
- Information base of fuzzy production rules for evaluation —the level of inflicted damage caused by threats to the protected assets of IIoT systems (total 25 rules)–with the values of the terms of the input linguistic variable C4—financial costs with a weight coefficient = 0.5833 and —damage to reputation with a weight coefficient ω5 = 0.4167: Very low—0.2, Low—0.4, Medium—0.6, High—0.8; Very high—1.0, and the calculated value of the term boundaries of the output linguistic variable —manifestation of the damage: Very Low—[0.0; 0.3], Low—(0.3; 0.5), Medium—(0.5; 0.7), High—(0.7; 0.9), Very High—(0.9; 1.0] (see Table A7, Appendix A).
- –
- Aggregated fuzzy rules for assessing the level of inflicted damage caused. As a result of the aggregation of the resulting rules, fuzzy causal relationships between antecedents and consequents were obtained (see Table A8, Appendix A).
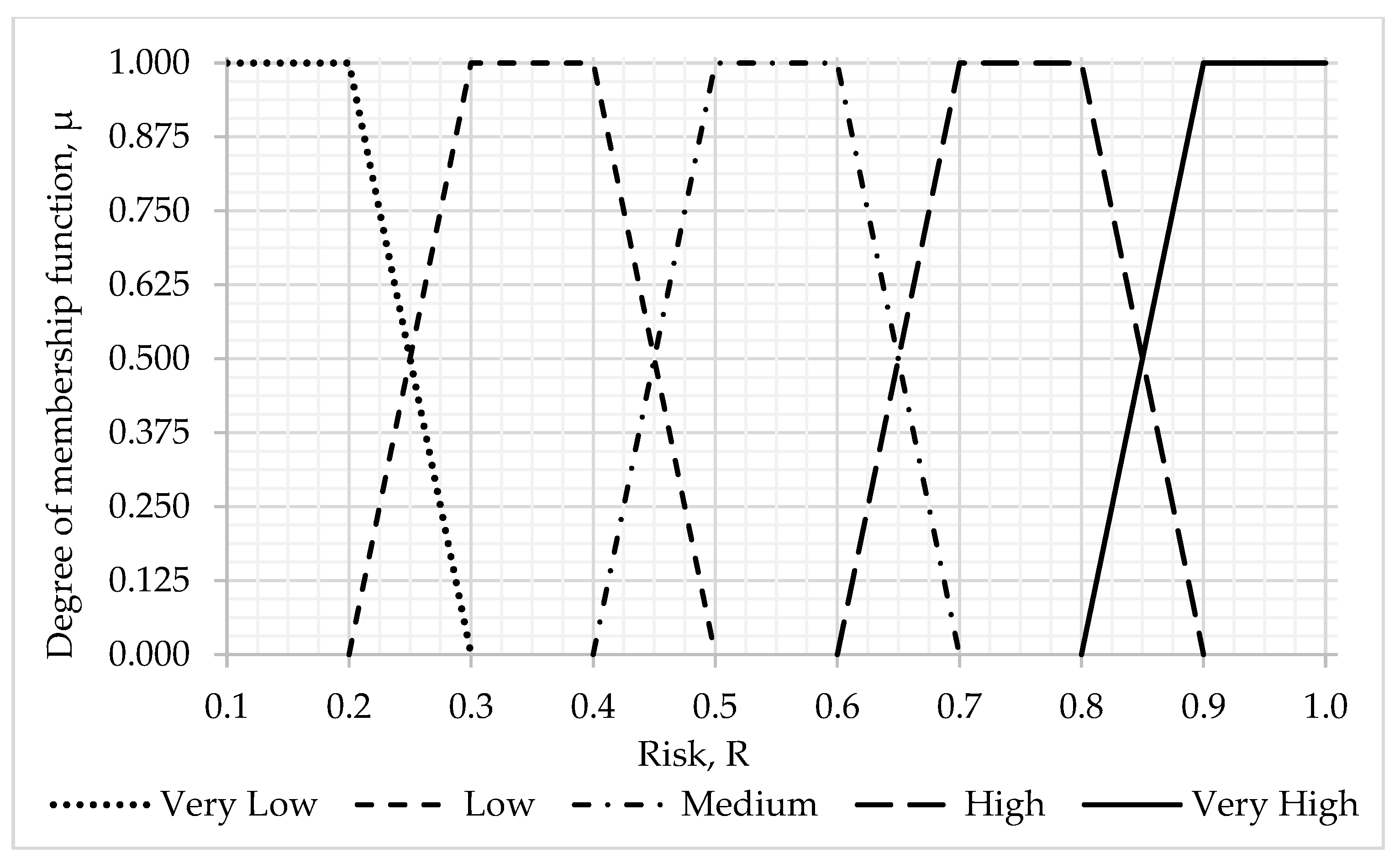
- –
- Very low risk: [0.0000; 0.0625), meaning a slight adverse impact on the activities of the organization and the assets of the organization;
- –
- Low risk: [0.0625; 0.2025), meaning a limited adverse impact on the activities of the organization and the assets of the organization;
- –
- Medium risk: [0.2025; 0.5625), meaning that threats can have a serious adverse effect on the activities of the organization, the assets of the organization, individuals, and other organizations;
- –
- High risk: [0.5625; 0.7225), meaning that threats can have a serious or catastrophic adverse effect on the activities of the organization and the assets of the organization;
- –
- Very high risk: [0.7225; 1.0000], meaning that threats can lead to multiple serious or catastrophic consequences for the organization’s activities and the organization’s assets.
3.4.2. Evaluation of the Correctness of the Model for Determining the Level of Risk
- –
- Attractiveness of assets, = 0.25;
- –
- Existing control, = 0.20;
- –
- Previous incidents, = 0.55.
- –
- Attractiveness of assets, C1: = 0.4, = 0.6, = 0.0, = 0.0, = 0.0;
- –
- Existing control, : = 0.3, = 0.7, = 0.0, = 0.0, = 0.0;
- –
- Previous incidents, : = 0.0, = 0.8, = 0.2, = 0.0, = 0.0.
- –
- If the condition of a fuzzy production rule is a simple fuzzy statement, then the degree of its truth corresponds to the value of the membership function of the corresponding term of the linguistic variable.
- –
- If the condition represents a compound statement, then the degree of truth of the compound statement is determined using the logical operation of conjunction.
- –
- Rule 3. = M: = min(0.4; 0.3; 1.0) = 0.3;
- –
- Rule 8. = M: = min(0.4; 0.7; 1.0) = 0.4;
- –
- Rule 28. = M: = min(0.6; 0.3; 1.0) = 0.3;
- –
- Rule 33. = M: = min(0.6; 0.7; 1.0) = 0.6.
- –
- Financial costs, = 0.67;
- –
- Damage to reputation, = 0.33.
- –
- Financial costs, : = 0.0, = 0.0, = 0.3, = 0.7, = 0.0;
- –
- Damage to reputation, : = 0.0, = 0.2, = 0.8, = 0.0, = 0.0.
- –
- Rule 12. = M: = min(0.3; 0.2) = 0.2;
- –
- Rule 13. = M: = min(0.3; 0.8) = 0.3;
- –
- Rule 17. = M: = min(0.7; 0.2) = 0.2;
- –
- Rule 18. = H: = min(0.7; 0.8) = 0.7.
- –
- Attractiveness of assets, = 0.85;
- –
- Existing control, = 0.70;
- –
- Previous incidents, C3 = 0.90.
- –
- Attractiveness of assets, : = 0.0, = 0.0, = 0.0, = 0.5, = 0.5;
- –
- Existing control, : = 0.0, = 0.0, = 0.08, = 0.12, = 0.0;
- –
- Previous incidents, : = 0.0, = 0.0, = 0.0, = 0.2, = 0.6.
- –
- Rule 89. = H: = min(0.5; 0.08; 0.2) = 0.08;
- –
- Rule 90. = H: = min(0.5; 0.08; 0.6) = 0.08;
- –
- Rule 94. = H: = min(0.5; 0.12; 0.2) = 0.12;
- –
- Rule 95. = H: = min(0.5; 0.12; 0.6) = 0.12;
- –
- Rule 114. = H: = min(0.5; 0.08; 0.2) = 0.08;
- –
- Rule 115. = H: = min(0.5; 0.08; 0.6) = 0.08;
- –
- Rule 119. = H: = min(0.5; 0.12; 0.2) = 0.12;
- –
- Rule 120. = VH: = min(0.5; 0.12; 0.6) = 0.12.
- –
- Financial costs, = 0.50;
- –
- Damage to reputation, = 0.75.
- –
- Financial costs, : = 0.0, = 0.0, = 0.0, = 0.14, = 0.0;
- –
- Damage to reputation, : = 0.0, = 0.0, = 1.0, = 0.0, = 0.0.
- –
- Rule 18. = H: = min(0.14; 1.0) = 0.14.
- –
- Attractiveness of assets, = 0.40;
- –
- Existing control, = 0.28;
- –
- Previous incidents, = 0.32.
- –
- Attractiveness of assets, : = 0.0, = 0.5, = 0.5, = 0.0, = 0.0;
- –
- Existing control, C2: = 0.19, = 1.0, = 0.0, = 0.0, = 0.0;
- –
- Previous incidents, : = 0.21, = 1.0, = 0.0, = 0.0, = 0.0.
- –
- Rule 26. = VL: = min(0.5; 0.19; 0.21) = 0.19;
- –
- Rule 27. = L: = min(0.5; 0.19; 1.0) = 0.19;
- –
- Rule 31. = L: = min(0.5; 1.0; 0.21) = 0.21;
- –
- Rule 32. = L: = min(0.5; 1.0; 1.0) = 0.5;
- –
- Rule 51. = L: = min(0.5; 0.19; 0.21) = 0.19;
- –
- Rule 52. = L: = min(0.5; 0.19; 1.0) = 0.19;
- –
- Rule 56. = L: = min(0.5; 1.0; 0.21) = 0.21;
- –
- Rule 57. = L: = min(0.5; 1.0; 1.0) = 0.5.
- –
- Financial costs, = 0.16;
- –
- Damage to reputation, = 0.84.
- –
- Financial costs, : = 0.4, = 0.6, = 0.0, = 0.0, = 0.0;
- –
- Damage to reputation, : = 0.0, = 0.0, = 0.0, = 0.6, = 0.0.
- –
- Rule 4. = L: = min(0.4; 0.6) = 0.4;
- –
- Rule 9. = M: = min(0.6; 0.6) = 0.6.
4. Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A
| Input Variables | Expert (i) | Expert (ii) | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 1.0 | 0.5 | 3.0 | 1.14 | 0.3487 | 1.0 | 1.0 | 2.0 | 1.26 | 0.3474 | |
| 2.0 | 1.0 | 2.0 | 1.59 | 0.4836 | 1.0 | 1.0 | 3.0 | 1.44 | 0.4434 | |
| 0.3 | 0.5 | 1.0 | 0.55 | 0.1677 | 0.3 | 0.5 | 1.0 | 0.55 | 0.1692 | |
| Input Variables | Expert (iii) | Expert (iv) | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 1.0 | 2.0 | 1.0 | 1.26 | 0.4126 | 1.0 | 0.5 | 2.0 | 1.00 | 0.3711 | |
| 0.5 | 1.0 | 2.0 | 1.00 | 0.3275 | 0.5 | 1.0 | 3.0 | 1.14 | 0.4247 | |
| 1.0 | 0.5 | 1.0 | 0.79 | 0.2599 | 0.5 | 0.3 | 1.0 | 0.55 | 0.2042 | |
| Input Variables | Expert (v) | Criteria Weights | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 1.0 | 2.0 | 1.0 | 1.26 | 0.5396 | 0.3487 | 0.3474 | 0.4126 | 0.3711 | 0.4119 | |
| 0.5 | 1.0 | 2.0 | 1.00 | 0.2970 | 0.4836 | 0.4434 | 0.3275 | 0.4247 | 0.3952 | |
| 1.0 | 0.5 | 1.0 | 0.79 | 0.1634 | 0.1677 | 0.1692 | 0.2599 | 0.2042 | 0.1929 | |
| Input Variables | Criteria Weights | |||||
|---|---|---|---|---|---|---|
| 0.6667 | 0.3333 | 0.6667 | 0.7500 | 0.5000 | 0.5833 | |
| 0.3333 | 0.6667 | 0.3333 | 0.2500 | 0.5000 | 0.4167 | |
| (i) | (ii) | (iii) | (iv) | (v) | (vi) | (vii) | (viii) | (ix) | (i) | (ii) | (iii) | (iv) | (v) | (vi) | (vii) | (viii) | (ix) |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | VL | 0.2 | VL | 1.0 | VL | 0.2 | 0.52 | VL | 64 | M | 0.6 | M | 0.6 | H | 0.8 | 0.64 | M |
| 2 | VL | 0.2 | VL | 1.0 | L | 0.4 | 0.55 | VL | 65 | M | 0.6 | M | 0.6 | VH | 1.0 | 0.68 | M |
| 3 | VL | 0.2 | VL | 1.0 | M | 0.6 | 0.59 | VL | 66 | M | 0.6 | H | 0.4 | VL | 0.2 | 0.44 | M |
| 4 | VL | 0.2 | VL | 1.0 | H | 0.8 | 0.63 | L | 67 | M | 0.6 | H | 0.4 | L | 0.4 | 0.48 | M |
| 5 | VL | 0.2 | VL | 1.0 | VH | 1.0 | 0.67 | L | 68 | M | 0.6 | H | 0.4 | M | 0.6 | 0.52 | M |
| 6 | VL | 0.2 | L | 0.8 | VL | 0.2 | 0.44 | VL | 69 | M | 0.6 | H | 0.4 | H | 0.8 | 0.56 | H |
| 7 | VL | 0.2 | L | 0.8 | L | 0.4 | 0.48 | L | 70 | M | 0.6 | H | 0.4 | VH | 1.0 | 0.60 | H |
| 8 | VL | 0.2 | L | 0.8 | M | 0.6 | 0.51 | L | 71 | M | 0.6 | VH | 0.2 | VL | 0.2 | 0.36 | M |
| 9 | VL | 0.2 | L | 0.8 | H | 0.8 | 0.55 | L | 72 | M | 0.6 | VH | 0.2 | L | 0.4 | 0.40 | H |
| 10 | VL | 0.2 | L | 0.8 | VH | 1.0 | 0.59 | L | 73 | M | 0.6 | VH | 0.2 | M | 0.6 | 0.44 | H |
| 11 | VL | 0.2 | M | 0.6 | VL | 0.2 | 0.36 | L | 74 | M | 0.6 | VH | 0.2 | H | 0.8 | 0.48 | H |
| 12 | VL | 0.2 | M | 0.6 | L | 0.4 | 0.40 | L | 75 | M | 0.6 | VH | 0.2 | VH | 1.0 | 0.52 | H |
| 13 | VL | 0.2 | M | 0.6 | M | 0.6 | 0.44 | L | 76 | H | 0.8 | VL | 1.0 | VL | 0.2 | 0.76 | L |
| 14 | VL | 0.2 | M | 0.6 | H | 0.8 | 0.47 | L | 77 | H | 0.8 | VL | 1.0 | L | 0.4 | 0.80 | L |
| 15 | VL | 0.2 | M | 0.6 | VH | 1.0 | 0.51 | M | 78 | H | 0.8 | VL | 1.0 | M | 0.6 | 0.84 | M |
| 16 | VL | 0.2 | H | 0.4 | VL | 0.2 | 0.28 | L | 79 | H | 0.8 | VL | 1.0 | H | 0.8 | 0.88 | M |
| 17 | VL | 0.2 | H | 0.4 | L | 0.4 | 0.32 | L | 80 | H | 0.8 | VL | 1.0 | VH | 1.0 | 0.92 | M |
| 18 | VL | 0.2 | H | 0.4 | M | 0.6 | 0.36 | M | 81 | H | 0.8 | L | 0.8 | VL | 0.2 | 0.68 | M |
| 19 | VL | 0.2 | H | 0.4 | H | 0.8 | 0.39 | M | 82 | H | 0.8 | L | 0.8 | L | 0.4 | 0.72 | M |
| 20 | VL | 0.2 | H | 0.4 | VH | 1.0 | 0.43 | M | 83 | H | 0.8 | L | 0.8 | M | 0.6 | 0.76 | M |
| 21 | VL | 0.2 | VH | 0.2 | VL | 0.2 | 0.20 | M | 84 | H | 0.8 | L | 0.8 | H | 0.8 | 0.80 | M |
| 22 | VL | 0.2 | VH | 0.2 | L | 0.4 | 0.24 | M | 85 | H | 0.8 | L | 0.8 | VH | 1.0 | 0.84 | M |
| 23 | VL | 0.2 | VH | 0.2 | M | 0.6 | 0.28 | M | 86 | H | 0.8 | M | 0.6 | VL | 0.2 | 0.61 | M |
| 24 | VL | 0.2 | VH | 0.2 | H | 0.8 | 0.32 | M | 87 | H | 0.8 | M | 0.6 | L | 0.4 | 0.64 | M |
| 25 | VL | 0.2 | VH | 0.2 | VH | 1.0 | 0.35 | M | 88 | H | 0.8 | M | 0.6 | M | 0.6 | 0.68 | M |
| 26 | L | 0.4 | VL | 1.0 | VL | 0.2 | 0.60 | VL | 89 | H | 0.8 | M | 0.6 | H | 0.8 | 0.72 | H |
| 27 | L | 0.4 | VL | 1.0 | L | 0.4 | 0.64 | L | 90 | H | 0.8 | M | 0.6 | VH | 1.0 | 0.76 | H |
| 28 | L | 0.4 | VL | 1.0 | M | 0.6 | 0.68 | L | 91 | H | 0.8 | H | 0.4 | VL | 0.2 | 0.53 | M |
| 29 | L | 0.4 | VL | 1.0 | H | 0.8 | 0.71 | L | 92 | H | 0.8 | H | 0.4 | L | 0.4 | 0.56 | H |
| 30 | L | 0.4 | VL | 1.0 | VH | 1.0 | 0.75 | L | 93 | H | 0.8 | H | 0.4 | M | 0.6 | 0.60 | H |
| 31 | L | 0.4 | L | 0.8 | VL | 0.2 | 0.52 | L | 94 | H | 0.8 | H | 0.4 | H | 0.8 | 0.64 | H |
| 32 | L | 0.4 | L | 0.8 | L | 0.4 | 0.56 | L | 95 | H | 0.8 | H | 0.4 | VH | 1.0 | 0.68 | H |
| 33 | L | 0.4 | L | 0.8 | M | 0.6 | 0.60 | L | 96 | H | 0.8 | VH | 0.2 | VL | 0.2 | 0.45 | H |
| 34 | L | 0.4 | L | 0.8 | H | 0.8 | 0.64 | L | 97 | H | 0.8 | VH | 0.2 | L | 0.4 | 0.49 | H |
| 35 | L | 0.4 | L | 0.8 | VH | 1.0 | 0.67 | M | 98 | H | 0.8 | VH | 0.2 | M | 0.6 | 0.52 | H |
| 36 | L | 0.4 | M | 0.6 | VL | 0.2 | 0.44 | L | 99 | H | 0.8 | VH | 0.2 | H | 0.8 | 0.56 | H |
| 37 | L | 0.4 | M | 0.6 | L | 0.4 | 0.48 | L | 100 | H | 0.8 | VH | 0.2 | VH | 1.0 | 0.60 | VH |
| 38 | L | 0.4 | M | 0.6 | M | 0.6 | 0.52 | M | 101 | VH | 1.0 | VL | 1.0 | VL | 0.2 | 0.85 | M |
| 39 | L | 0.4 | M | 0.6 | H | 0.8 | 0.56 | M | 102 | VH | 1.0 | VL | 1.0 | L | 0.4 | 0.88 | M |
| 40 | L | 0.4 | M | 0.6 | VH | 1.0 | 0.59 | M | 103 | VH | 1.0 | VL | 1.0 | M | 0.6 | 0.92 | M |
| 41 | L | 0.4 | H | 0.4 | VL | 0.2 | 0.36 | M | 104 | VH | 1.0 | VL | 1.0 | H | 0.8 | 0.96 | M |
| 42 | L | 0.4 | H | 0.4 | L | 0.4 | 0.40 | M | 105 | VH | 1.0 | VL | 1.0 | VH | 1.0 | 1.00 | M |
| 43 | L | 0.4 | H | 0.4 | M | 0.6 | 0.44 | M | 106 | VH | 1.0 | L | 0.8 | VL | 0.2 | 0.77 | M |
| 44 | L | 0.4 | H | 0.4 | H | 0.8 | 0.48 | M | 107 | VH | 1.0 | L | 0.8 | L | 0.4 | 0.81 | M |
| 45 | L | 0.4 | H | 0.4 | VH | 1.0 | 0.52 | M | 108 | VH | 1.0 | L | 0.8 | M | 0.6 | 0.84 | M |
| 46 | L | 0.4 | VH | 0.2 | VL | 0.2 | 0.28 | M | 109 | VH | 1.0 | L | 0.8 | H | 0.8 | 0.88 | H |
| 47 | L | 0.4 | VH | 0.2 | L | 0.4 | 0.32 | M | 110 | VH | 1.0 | L | 0.8 | VH | 1.0 | 0.92 | H |
| 48 | L | 0.4 | VH | 0.2 | M | 0.6 | 0.36 | M | 111 | VH | 1.0 | M | 0.6 | VL | 0.2 | 0.69 | M |
| 49 | L | 0.4 | VH | 0.2 | H | 0.8 | 0.40 | H | 112 | VH | 1.0 | M | 0.6 | L | 0.4 | 0.73 | H |
| 50 | L | 0.4 | VH | 0.2 | VH | 1.0 | 0.44 | H | 113 | VH | 1.0 | M | 0.6 | M | 0.6 | 0.76 | H |
| 51 | M | 0.6 | VL | 1.0 | VL | 0.2 | 0.68 | L | 114 | VH | 1.0 | M | 0.6 | H | 0.8 | 0.80 | H |
| 52 | M | 0.6 | VL | 1.0 | L | 0.4 | 0.72 | L | 115 | VH | 1.0 | M | 0.6 | VH | 1.0 | 0.84 | H |
| 53 | M | 0.6 | VL | 1.0 | M | 0.6 | 0.76 | L | 116 | VH | 1.0 | H | 0.4 | VL | 0.2 | 0.61 | H |
| 54 | M | 0.6 | VL | 1.0 | H | 0.8 | 0.80 | L | 117 | VH | 1.0 | H | 0.4 | L | 0.4 | 0.65 | H |
| 55 | M | 0.6 | VL | 1.0 | VH | 1.0 | 0.84 | M | 118 | VH | 1.0 | H | 0.4 | M | 0.6 | 0.69 | H |
| 56 | M | 0.6 | L | 0.8 | VL | 0.2 | 0.60 | L | 119 | VH | 1.0 | H | 0.4 | H | 0.8 | 0.72 | H |
| 57 | M | 0.6 | L | 0.8 | L | 0.4 | 0.64 | L | 120 | VH | 1.0 | H | 0.4 | VH | 1.0 | 0.76 | VH |
| 58 | M | 0.6 | L | 0.8 | M | 0.6 | 0.68 | M | 121 | VH | 1.0 | VH | 0.2 | VL | 0.2 | 0.53 | H |
| 59 | M | 0.6 | L | 0.8 | H | 0.8 | 0.72 | M | 122 | VH | 1.0 | VH | 0.2 | L | 0.4 | 0.57 | H |
| 60 | M | 0.6 | L | 0.8 | VH | 1.0 | 0.76 | M | 123 | VH | 1.0 | VH | 0.2 | M | 0.6 | 0.61 | VH |
| 61 | M | 0.6 | M | 0.6 | VL | 0.2 | 0.52 | M | 124 | VH | 1.0 | VH | 0.2 | H | 0.8 | 0.65 | VH |
| 62 | M | 0.6 | M | 0.6 | L | 0.4 | 0.56 | M | 125 | VH | 1.0 | VH | 0.2 | VH | 1.0 | 0.68 | VH |
| 63 | M | 0.6 | M | 0.6 | M | 0.6 | 0.60 | M |
| (i) | (ii) | (iii) | ||
|---|---|---|---|---|
| R1 | (C1 = VL) ∧ (C2 = VL) ∧ (C3 = VL) ∨ (C1 = VL) ∧ (C2 = VL) ∧ (C3 = L) ∨ | (C1 = VL) ∧ (C2 = VL) ∧ (C3 = M) ∨ (C1 = VL) ∧ (C2 = L) ∧ (C3 = VL) ∨ | (C1 = L) ∧ (C2 = VL) ∧ (C3 = VL) | Y1 = VL |
| R2 | (C1 = VL) ∧ (C2 = VL) ∧ (C3 = H) ∨ (C1 = VL) ∧ (C2 = VL) ∧ (C3 = VH) ∨ (C1 = VL) ∧ (C2 = L) ∧ (C3 = L) ∨ (C1 = VL) ∧ (C2 = L) ∧ (C3 = M) ∨ (C1 = VL) ∧ (C2 = L) ∧ (C3 = H) ∨ (C1 = VL) ∧ (C2 = L) ∧ (C3 = VH) ∨ (C1 = VL) ∧ (C2 = M) ∧ (C3 = VL) ∨ (C1 = VL) ∧ (C2 = M) ∧ (C3 = L) ∨ (C1 = VL) ∧ (C2 = M) ∧ (C3 = M) ∨ (C1 = VL) ∧ (C2 = M) ∧ (C3 = H) ∨ | (C1 = VL) ∧ (C2 = H) ∧ (C3 = VL) ∨ (C1 = VL) ∧ (C2 = H) ∧ (C3 = L) ∨ (C1 = L) ∧ (C2 = VL) ∧ (C3 = L) ∨ (C1 = L) ∧ (C2 = VL) ∧ (C3 = M) ∨ (C1 = L) ∧ (C2 = VL) ∧ (C3 = H) ∨ (C1 = L) ∧ (C2 = VL) ∧ (C3 = VH) ∨ (C1 = L) ∧ (C2 = L) ∧ (C3 = VL) ∨ (C1 = L) ∧ (C2 = L) ∧ (C3 = L) ∨ (C1 = L) ∧ (C2 = L) ∧ (C3 = M) ∨ (C1 = L) ∧ (C2 = L) ∧ (C3 = H) ∨ | (C1 = L) ∧ (C2 = M) ∧ (C3 = VL) ∨ (C1 = L) ∧ (C2 = M) ∧ (C3 = L) ∨ (C1 = M) ∧ (C2 = VL) ∧ (C3 = VL) ∨ (C1 = M) ∧ (C2 = VL) ∧ (C3 = L) ∨ (C1 = M) ∧ (C2 = VL) ∧ (C3 = M) ∨ (C1 = M) ∧ (C2 = VL) ∧ (C3 = H) ∨ (C1 = M) ∧ (C2 = L) ∧ (C3 = VL) ∨ (C1 = M) ∧ (C2 = L) ∧ (C3 = L) ∨ (C1 = H) ∧ (C2 = VL) ∧ (C3 = VL) ∨ (C1 = H) ∧ (C2 = VL) ∧ (C3 = L) | Y1 = L |
| R3 | (C1 = VL) ∧ (C2 = M) ∧ (C3 = VH) ∨ (C1 = VL) ∧ (C2 = H) ∧ (C3 = M) ∨ (C1 = VL) ∧ (C2 = H) ∧ (C3 = H) ∨ (C1 = VL) ∧ (C2 = H) ∧ (C3 = VH) ∨ (C1 = VL) ∧ (C2 = VH) ∧ (C3 = VL) ∨ (C1 = VL) ∧ (C2 = VH) ∧ (C3 = L) ∨ (C1 = VL) ∧ (C2 = VH) ∧ (C3 = M) ∨ (C1 = VL) ∧ (C2 = VH) ∧ (C3 = H) ∨ (C1 = VL) ∧ (C2 = VH) ∧ (C3 = VH) ∨ (C1 = L) ∧ (C2 = L) ∧ (C3 = VH) ∨ (C1 = L) ∧ (C2 = M) ∧ (C3 = M) ∨ (C1 = L) ∧ (C2 = M) ∧ (C3 = H) ∨ (C1 = L) ∧ (C2 = M) ∧ (C3 = VH) ∨ (C1 = L) ∧ (C2 = H) ∧ (C3 = VL) ∨ (C1 = L) ∧ (C2 = H) ∧ (C3 = L) ∨ (C1 = L) ∧ (C2 = H) ∧ (C3 = M) ∨ (C1 = L) ∧ (C2 = H) ∧ (C3 = H) ∨ (C1 = L) ∧ (C2 = H) ∧ (C3 = VH) ∨ (C1 = L) ∧ (C2 = VH) ∧ (C3 = VL) ∨ | (C1 = L) ∧ (C2 = VH) ∧ (C3 = L) ∨ (C1 = L) ∧ (C2 = VH) ∧ (C3 = M) ∨ (C1 = M) ∧ (C2 = VL) ∧ (C3 = VH) ∨ (C1 = M) ∧ (C2 = L) ∧ (C3 = M) ∨ (C1 = M) ∧ (C2 = L) ∧ (C3 = H) ∨ (C1 = M) ∧ (C2 = L) ∧ (C3 = VH) ∨ (C1 = M) ∧ (C2 = M) ∧ (C3 = VL) ∨ (C1 = M) ∧ (C2 = M) ∧ (C3 = L) ∨ (C1 = M) ∧ (C2 = M) ∧ (C3 = M) ∨ (C1 = M) ∧ (C2 = M) ∧ (C3 = H) ∨ (C1 = M) ∧ (C2 = M) ∧ (C3 = VH) ∨ (C1 = M) ∧ (C2 = H) ∧ (C3 = VL) ∨ (C1 = M) ∧ (C2 = H) ∧ (C3 = L) ∨ (C1 = M) ∧ (C2 = H) ∧ (C3 = M) ∨ (C1 = M) ∧ (C2 = VH) ∧ (C3 = VL) ∨ (C1 = H) ∧ (C2 = VL) ∧ (C3 = M) ∨ (C1 = H) ∧ (C2 = VL) ∧ (C3 = H) ∨ (C1 = H) ∧ (C2 = VL) ∧ (C3 = VH) ∨ (C1 = H) ∧ (C2 = L) ∧ (C3 = VL) ∨ | (C1 = H) ∧ (C2 = L) ∧ (C3 = L) ∨ (C1 = H) ∧ (C2 = L) ∧ (C3 = M) ∨ (C1 = H) ∧ (C2 = L) ∧ (C3 = H) ∨ (C1 = H) ∧ (C2 = L) ∧ (C3 = VH) ∨ (C1 = H) ∧ (C2 = M) ∧ (C3 = VL) ∨ (C1 = H) ∧ (C2 = M) ∧ (C3 = L) ∨ (C1 = H) ∧ (C2 = M) ∧ (C3 = M) ∨ (C1 = H) ∧ (C2 = H) ∧ (C3 = VL) ∨ (C1 = VH) ∧ (C2 = VL) ∧ (C3 = VL) ∨ (C1 = VH) ∧ (C2 = VL) ∧ (C3 = L) ∨ (C1 = VH) ∧ (C2 = VL) ∧ (C3 = M) ∨ (C1 = VH) ∧ (C2 = VL) ∧ (C3 = H) ∨ (C1 = VH) ∧ (C2 = VL) ∧ (C3 = VH) ∨ (C1 = VH) ∧ (C2 = L) ∧ (C3 = VL) ∨ (C1 = VH) ∧ (C2 = L) ∧ (C3 = L) ∨ (C1 = VH) ∧ (C2 = L) ∧ (C3 = M) ∨ (C1 = VH) ∧ (C2 = M) ∧ (C3 = VL) | Y1 = M |
| R4 | (C1 = L) ∧ (C2 = VH) ∧ (C3 = H) ∨ (C1 = L) ∧ (C2 = VH) ∧ (C3 = VH) ∨ (C1 = M) ∧ (C2 = H) ∧ (C3 = H) ∨ (C1 = M) ∧ (C2 = H) ∧ (C3 = VH) ∨ (C1 = M) ∧ (C2 = VH) ∧ (C3 = L) ∨ (C1 = M) ∧ (C2 = VH) ∧ (C3 = M) ∨ (C1 = M) ∧ (C2 = VH) ∧ (C3 = H) ∨ (C1 = M) ∧ (C2 = VH) ∧ (C3 = VH) ∨ (C1 = H) ∧ (C2 = M) ∧ (C3 = H) ∨ (C1 = H) ∧ (C2 = M) ∧ (C3 = VH) ∨ | (C1 = H) ∧ (C2 = H) ∧ (C3 = L) ∨ (C1 = H) ∧ (C2 = H) ∧ (C3 = M) ∨ (C1 = H) ∧ (C2 = H) ∧ (C3 = H) ∨ (C1 = H) ∧ (C2 = H) ∧ (C3 = VH) ∨ (C1 = H) ∧ (C2 = VH) ∧ (C3 = VL) ∨ (C1 = H) ∧ (C2 = VH) ∧ (C3 = L) ∨ (C1 = H) ∧ (C2 = VH) ∧ (C3 = M) ∨ (C1 = H) ∧ (C2 = VH) ∧ (C3 = H) ∨ (C1 = VH) ∧ (C2 = L) ∧ (C3 = H) ∨ (C1 = VH) ∧ (C2 = L) ∧ (C3 = VH) ∨ | (C1 = VH) ∧ (C2 = M) ∧ (C3 = L) ∨ (C1 = VH) ∧ (C2 = M) ∧ (C3 = M) ∨ (C1 = VH) ∧ (C2 = M) ∧ (C3 = H) ∨ (C1 = VH) ∧ (C2 = M) ∧ (C3 = VH) ∨ (C1 = VH) ∧ (C2 = H) ∧ (C3 = VL) ∨ (C1 = VH) ∧ (C2 = H) ∧ (C3 = L) ∨ (C1 = VH) ∧ (C2 = H) ∧ (C3 = M) ∨ (C1 = VH) ∧ (C2 = H) ∧ (C3 = H) ∨ (C1 = VH) ∧ (C2 = VH) ∧ (C3 = VL) ∨ (C1 = VH) ∧ (C2 = VH) ∧ (C3 = L) | Y1 = H |
| R5 | (C1 = H) ∧ (C2 = VH) ∧ (C3 = VH) ∨ (C1 = VH) ∧ (C2 = H) ∧ (C3 = VH) ∨ | (C1 = VH) ∧ (C2 = VH) ∧ (C3 = M) ∨ (C1 = VH) ∧ (C2 = VH) ∧ (C3 = H) ∨ | (C1 = VH) ∧ (C2 = VH) ∧ (C3 = VH) ∨ | Y1 = VH |
| (i) | (ii) | (iii) | (iv) | (v) | (vi) | (vii) | (i) | (ii) | (iii) | (iv) | (v) | (vi) | (vii) | (i) | (ii) | (iii) | (iv) | (v) | (vi) | (vii) |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1 | VL | 1 | VL | 1 | 1.000 | VL | 10 | L | 2 | VH | 5 | 3.251 | M | 19 | H | 4 | H | 4 | 4.000 | H |
| 2 | VL | 1 | L | 2 | 1.417 | VL | 11 | M | 3 | VL | 1 | 2.166 | L | 20 | H | 4 | VH | 5 | 4.417 | H |
| 3 | VL | 1 | M | 3 | 1.834 | L | 12 | M | 3 | L | 2 | 2.583 | M | 21 | VH | 5 | VL | 1 | 3.332 | M |
| 4 | VL | 1 | H | 4 | 2.251 | L | 13 | M | 3 | M | 3 | 3.000 | M | 22 | VH | 5 | L | 2 | 3.749 | H |
| 5 | VL | 1 | VH | 5 | 2.668 | M | 14 | M | 3 | H | 4 | 3.417 | M | 23 | VH | 5 | M | 3 | 4.166 | H |
| 6 | L | 2 | VL | 1 | 1.583 | L | 15 | M | 3 | VH | 5 | 3.834 | H | 24 | VH | 5 | H | 4 | 4.583 | VH |
| 7 | L | 2 | L | 2 | 2.000 | L | 16 | H | 4 | VL | 1 | 2.749 | M | 25 | VH | 5 | VH | 5 | 5 | VH |
| 8 | L | 2 | M | 3 | 2.417 | L | 17 | H | 4 | L | 2 | 3.166 | M | |||||||
| 9 | L | 2 | H | 4 | 2.834 | M | 18 | H | 4 | M | 3 | 3.583 | H |
| (i) | (ii) | (iii) | ||
|---|---|---|---|---|
| R6 | (C4 = VL) ∧ (C5 = VL) ∨ | (C4 = VL) ∧ (C5 = L) | Y2 = VL | |
| R7 | (C4 = VL) ∧ (C5 = M) ∨ (C4 = VL) ∧ (C5 = H) ∨ | (C4 = L) ∧ (C5 = VL) ∨ (C4 = L) ∧ (C5 = L) ∨ | (C4 = L) ∧ (C5 = M) ∨ (C4 = M) ∧ (C5 = VL) | Y2 = L |
| R8 | (C4 = VL) ∧ (C5 = VH) ∨ (C4 = L) ∧ (C5 = H) ∨ (C4 = L) ∧ (C5 = VH) ∨ | (C4 = M) ∧ (C5 = L) ∨ (C4 = M) ∧ (C5 = M) ∨ (C4 = M) ∧ (C5 = H) ∨ | (C4 = H) ∧ (C5 = VL) ∨ (C4 = H) ∧ (C5 = L) ∨ (C4 = VH) ∧ (C5 = VL) | Y2 = M |
| R9 | (C4 = M) ∧ (C5 = VH) ∨ (C4 = H) ∧ (C5 = M) ∨ | (C4 = H) ∧ (C5 = H) ∨ (C4 = H) ∧ (C5 = VH) ∨ | (C4 = VH) ∧ (C5 = L) ∨ (C4 = VH) ∧ (C5 = M) | Y2 = H |
| R10 | (C4 = VH) ∧ (C5 = H) ∨ | (C4 = VH) ∧ (C5 = VH) | Y2 = VH | |
References
- Hofer, F. Architecture, technologies and challenges for cyber-physical systems in industry 4.0: A systematic mapping study. In Proceedings of the 12th ACM/IEEE International Symposium on Empirical Software Engineering and Measurement (ESEM), Oulu, Finland, 11–12 October 2018; pp. 1–10. [Google Scholar] [CrossRef]
- Sisinni, E.; Saifullah, A.; Han, S.; Jennehag, U.; Gidlund, M. Industrial Internet of Things: Challenges, opportunities, and directions. IEEE Trans. Ind. Inform. 2018, 14, 4724–4734. [Google Scholar] [CrossRef]
- Tange, K.; De Donno, M.; Fafoutis, X.; Dragoni, N. A Systematic Survey of Industrial Internet of Things Security: Requirements and Fog Computing Opportunities. IEEE Commun. Surv. Tutor. 2020, 22, 2489–2520. [Google Scholar] [CrossRef]
- Yu, X.; Guo, H. A Survey on IIoT Security. In Proceedings of the Conference: IEEE VTS Asia Pacific Wireless Communications Symposium (APWCS), Singapore, 28–30 August 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Panchal, A.; Khadse, V.; Mahalle, P. Security Issues in IIoT: A Comprehensive Survey of Attacks on IIoT and Its Countermeasures. In Proceedings of the Conference: 2018 IEEE Global Conference on Wireless Computing and Networking (GCWCN), Lonavala, India, 23–24 November 2018; pp. 124–130. [Google Scholar] [CrossRef]
- Shah, Y.; Sengupta, S. A survey on Classification of Cyber-attacks on IoT and IIoT devices. In Proceedings of the Conference: 2020 11th IEEE Annual Ubiquitous Computing, Electronics & Mobile Communication Conference (UEMCON), New York, NY, USA, 28–31 October 2020; pp. 0406–0413. [Google Scholar] [CrossRef]
- Tamy, S.; Belhadaoui, H.; Rabbah, M.; Rabbah, N.; Rifi, M. An evaluation of machine learning algorithms to detect attacks in SCADA network. In Proceedings of the Conference: 2019 7th Mediterranean Congress of Telecommunications (CMT), Fez, Morocco, 24–25 October 2019; pp. 1–5. [Google Scholar] [CrossRef]
- Al-Hawawreh, M.; Sitnikova, E. Industrial Internet of Things based ransomware detection using stacked variational neural network. In Proceedings of the 2019 Conference on Big Data and Internet of Things (BDIOT), Melbourn, VIC, Australia, 22–24 August 2019; pp. 126–130. [Google Scholar] [CrossRef]
- Wang, H.; Chen, Z.; Zhao, J.; Di, X.; Liu, D. A Vulnerability Assessment Method in Industrial Internet of Things Based on Attack Graph and Maximum Flow. IEEE Access 2018, 6, 8599–8609. [Google Scholar] [CrossRef]
- Li, Z.; Kang, J.; Yu, R.; Ye, D.; Deng, Q.; Zhang, Y. Consortium Blockchain for Secure Energy Trading in Industrial Internet of Things. IEEE Trans. Ind. Inform. 2017, 14, 3690–3700. [Google Scholar] [CrossRef]
- Huang, Y.-L.; Sun, W.-L. An AHP-Based Risk Assessment for an Industrial IoT Cloud. In Proceedings of the IEEE International Conference on Software Quality, Reliability and Security Companion (QRS-C), Lisbon, Portugal, 16–20 July 2018; pp. 637–638. [Google Scholar] [CrossRef]
- Hassani, H.L.; Bahnasse, A.; Martin, E.; Roland, C.; Bouattane, O.; Diouri, M.E. Vulnerability and security risk assessment in a IIoT environment in compliance with standard IEC 62443. Procedia Comput. Sci. 2021, 191, 33–40. [Google Scholar] [CrossRef]
- Tsiknas, K.; Taketzis, D.; Demertzis, K.; Skianis, C. Cyber Threats to Industrial IoT: A Survey on Attacks and Countermeasures. IoT 2021, 2, 163–186. [Google Scholar] [CrossRef]
- Wentian, C.; Huijun, Y. Research on Information Security Risk Assessment Method Based on Fuzzy Rule Set. Wirel. Commun. Mob. Comput. 2021, 9663520. [Google Scholar] [CrossRef]
- Tubis, A.; Werbińska-Wojciechowska, S.; Góralczyk, M.; Wróblewski, A.; Ziętek, B. Cyber-Attacks Risk Analysis Method for Different Levels of Automation of Mining Processes in Mines Based on Fuzzy Theory Use. Sensors 2020, 20, 7210. [Google Scholar] [CrossRef]
- Kuzminykh, I.; Ghita, B.; Sokolov, V.; Bakhshi, T. Information Security Risk Assessment. Encyclopedia 2021, 1, 602–617. [Google Scholar] [CrossRef]
- Zadeh, L.A. Is there a need for fuzzy logic? Inf. Sci. 2008, 178, 2751–2779. [Google Scholar] [CrossRef]
- ISO/IEC 27400:2022; Cybersecurity–IoT Security and Privacy. ISO: Geneva, Switzerland, 2023. Available online: www.iso27001security.com (accessed on 21 July 2023).
- ISA/IEC 62443; Series of Standards—Security for Industrial Automation and Control Systems. ISA: Eindhoven, The Netherlands, 2023. Available online: https://www.isa.org/standards-and-publications/isa-standards/isa-iec-62443-series-of-standards (accessed on 21 July 2023).
- Force, J.T. Guide for Conducting Risk Assessments; NIST SP 800-30 Rev. 1; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2012. [Google Scholar] [CrossRef]
- Force, J.T. Risk Management Framework for Information Systems and Organizations: A System Life Cycle Approach for Security and Privacy; NIST SP 800-37 Rev. 2; National Institute of Standards and Technology: Gaithersburg, MD, USA, 2018. [Google Scholar] [CrossRef]
- ISO/IEC 27005:2022; Information Security, Cybersecurity and Privacy Protection—Guidance on Managing Information Security Risks. ISO: Geneva, Switzerland, 2022. Available online: https://www.iso.org/standard/80585.html (accessed on 21 July 2023).
- Freund, J.; Jones, J. Measuring and Managing Information Risk: A FAIR Approach; Butterworth-Heinemann: Oxford, UK, 2014; p. 408. [Google Scholar]
- Saaty, T.L. There is no mathematical validity for using fuzzy number crunching in the analytic hierarchy process. J. Syst. Sci. Syst. Eng. 2006, 15, 457–464. [Google Scholar] [CrossRef]
- Reports of the Kaspersky Lab Industrial Infrastructure Information Security Incident Response Center (Kaspersky ICS CERT). Available online: https://ics-cert.kaspersky.ru/publications/reports/2023/09/13/threat-landscape-for-industrial-automation-systems-statistics-for-h1-2023/ (accessed on 21 July 2023).
- Arrow, K.J.; Kruz, M. Public Investment, the Rate of Return, and Optimal Fiscal Policy; RFF Press: New York, NY, USA, 2013; p. 218. [Google Scholar] [CrossRef]
- Gaultier-Gaillard, S.; Louisot, J.P.; Rayner, J. Managing reputational risk—From theory to practice. In Reputation Capital: Building and Maintaining Trust in the 21st Century; Springer: Berlin/Heidelberg, Germany, 2009. [Google Scholar] [CrossRef]
- Kureichik, V.M.; Kazharov, A. Using fuzzy logic controller in ant colony optimization. Adv. Intell. Syst. Comput. 2015, 347, 151–158. [Google Scholar] [CrossRef]
- Shang, W.; Gong, T.; Chen, C.; Hou, J.; Zeng, P. Information Security Risk Assessment Method for Ship Control System Based on Fuzzy Sets and Attack Trees. Secur. Commun. Netw. 2019, 3574675. [Google Scholar] [CrossRef]
- Huijuan, G.; Lei, D.; Wenchao, X. Cybersecurity Risk Assessment of Industrial Control Systems Based on Order-α Divergence Measures Under an Interval-Valued Intuitionistic Fuzzy Environment. IEEE Access 2022, 10, 43751–43765. [Google Scholar] [CrossRef]
- Stojanović, M.; Markovic-Petrovic, J. A Model for Dynamic Cyber Security Risk Assessment in the Industrial IoT Environment. In Proceedings of the Sinteza 2022—International Scientific Conference on Information Technology and Data Related Research, Online, 16 April 2022; pp. 230–237. [Google Scholar] [CrossRef]
- Atlam, H.; Walters, R.; Wills, G.; Daniel, J. Fuzzy Logic with Expert Judgment to Implement an Adaptive Risk-Based Access Control Model for IoT. Mob. Netw. Appl. 2021, 26, 2545–2557. [Google Scholar] [CrossRef]
- Adaros-Boye, C.; Kearney, P.; Josephs, M.; Ulmer, H. An Indicators-of-Risk Library for Industrial Network Security. In Proceedings of the Conference: ARES 2021: The 16th International Conference on Availability, Reliability and Security, Vienna, Austria, 17–20 August 2021. [Google Scholar] [CrossRef]
- Figueroa-Lorenzo, S.; Añorga, J.; Arrizabalaga, S. A Survey of IIoT Protocols: A Measure of Vulnerability Risk Analysis Based on CVSS. ACM Comput. Surv. 2020, 53, 1–53. [Google Scholar] [CrossRef]
- Abdymanapov, S.; Muratbekov, M.; Sharipbay, A.; Barlybayev, A. Fuzzy Expert System of Information Security Risk Assessment on the Example of Analysis Learning Management Systems. IEEE Access 2021, 9, 156556–156565. [Google Scholar] [CrossRef]
- Sikman, L.; Latinovic, T.; Sarajlic, N. Modelling of Fuzzy Expert System for an Assessment of Security Information Management System UIS. Tech. Gaz. 2022, 29, 60–65. [Google Scholar] [CrossRef]
- Amirova, A.; Tokhmetov, A. A model for risk analysis in the Industrial Internet of Things. J. Theor. Appl. Inf. Technol. 2021, 99, 3449–3459. [Google Scholar]
- McLaughlin, S.; Konstantinou, C.; Wang, X.; Davi, L.; Sadeghi, A.; Maniatakos, M.; Karri, R. The Cybersecurity Landscape in Industrial Control Systems. Proc. IEEE 2016, 104, 1039–1057. [Google Scholar] [CrossRef]
- Makhazhanova, U.; Kerimkhulle, S.; Mukhanova, A.; Bayegizova, A.; Aitkozha, Z.; Mukhiyadin, A.; Tassuov, B.; Saliyeva, A.; Taberkhan, R.; Azieva, G. The Evaluation of Creditworthiness of Trade and Enterprises of Service Using the Method Based on Fuzzy Logic. Appl. Sci. 2022, 12, 11515. [Google Scholar] [CrossRef]
| Values of Base Terms | Number of Score | |||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | |
| Very Low (VL) | 10 | 7 | 2 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| Low (L) | 0 | 3 | 7 | 5 | 2 | 0 | 0 | 0 | 0 | 0 |
| Medium (M) | 0 | 0 | 1 | 5 | 8 | 6 | 3 | 0 | 0 | 0 |
| High (H) | 0 | 0 | 0 | 0 | 0 | 4 | 5 | 6 | 1 | 0 |
| Very High (VH) | 0 | 0 | 0 | 0 | 0 | 0 | 2 | 4 | 9 | 10 |
| Values of Base Terms | ||||||||||
|---|---|---|---|---|---|---|---|---|---|---|
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | |
| Very Low (VL) | 1 | 0.7 | 0.2 | 0 | 0 | 0 | 0 | 0 | 0 | 0 |
| Low (L) | 0 | 0.43 | 1 | 0.71 | 0.29 | 0 | 0 | 0 | 0 | 0 |
| Medium (M) | 0 | 0 | 0.125 | 0.625 | 1 | 0.75 | 0.375 | 0 | 0 | 0 |
| High (H) | 0 | 0 | 0 | 0 | 0 | 0.5 | 0.8 | 1 | 0.17 | 0 |
| Very High (VH) | 0 | 0 | 0 | 0 | 0 | 0 | 0.2 | 0.4 | 0.9 | 1 |
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | |
|---|---|---|---|---|---|---|---|---|
| C2 | 0.125 | 0.250 | 0.375 | 0.500 | 0.625 | 0.750 | 0.875 | 1.000 |
| 5% | 10% | 15% | 20% | 25% | 30% | 35% | 40% and Higher | |
|---|---|---|---|---|---|---|---|---|
| C3 | 0.125 | 0.250 | 0.375 | 0.500 | 0.625 | 0.750 | 0.875 | 1.000 |
| Term | Meaning | Description |
|---|---|---|
| Very low | 0–0.3 | There are no objective prerequisites for the emergence of a threat |
| Low | 0.2–0.5 | Some prerequisites for the emergence of a threat exist, but the security measures taken significantly complicate its implementation |
| Average | 0.4–0.7 | Objective prerequisites for the emergence of a threat exist, and the number of security measures is sufficient to neutralize it |
| High | 0.6–0.9 | Objective prerequisites for the emergence of a threat exist, and the number of security measures is insufficient |
| Very high | 0.8–1 | Objective prerequisites for a threat exist, and security measures have not been taken |
| 1% | 2% | 3% | 4% | 5% | 6% | 7% | 8% | 9% | 10% | |
|---|---|---|---|---|---|---|---|---|---|---|
| C4 | 0.1 | 0.2 | 0.3 | 0.4 | 0.5 | 0.6 | 0.7 | 0.8 | 0.9 | 1.0 |
| Term | Description |
|---|---|
| Very low | Minor damage, less than 1% of annual income |
| Low | Low damage, 2–4% of annual income |
| Average | Noticeable damage, 4–7% of annual income |
| High | Large damage, 7–10% of annual income |
| Very high | Very large damage, more than 10% of annual income |
| 1% | 2% | 3% | 4% | 5% | 6% | 7% | 8% | 9% | 10% | |
|---|---|---|---|---|---|---|---|---|---|---|
| C5 | 0.1 | 0.2 | 0.3 | 0.4 | 0.5 | 0.6 | 0.7 | 0.8 | 0.9 | 1.0 |
| Term | Description |
|---|---|
| Very low | Minor damage, less than 1% of annual income |
| Low | Low damage, 2–4% of annual income |
| Average | Noticeable damage, 4–7% of annual income |
| High | Large damage, 7–10% of annual income |
| Very high | Very large damage, more than 10% of annual income |
| Term | Meaning | Description |
|---|---|---|
| Very low | 0–0.3 | The level of damage caused has virtually no effect on the operation of the facility |
| Low | 0.2–0.5 | The level of damage caused slightly affects the operation of the facility |
| Average | 0.4–0.7 | The level of damage caused makes it difficult for the facility to operate |
| High | 0.6–0.9 | The level of damage caused has a significant impact on the operation of the facility |
| Very high | 0.8–1 | The level of damage caused greatly affects the operation of the facility |
| Comparing Two Elements | Value |
|---|---|
| 1 | |
| 3 | |
| 5 | |
| 7 | |
| 9 | |
| Values intermediate in degree between those listed | 2, 4, 6, 8 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Kerimkhulle, S.; Dildebayeva, Z.; Tokhmetov, A.; Amirova, A.; Tussupov, J.; Makhazhanova, U.; Adalbek, A.; Taberkhan, R.; Zakirova, A.; Salykbayeva, A. Fuzzy Logic and Its Application in the Assessment of Information Security Risk of Industrial Internet of Things. Symmetry 2023, 15, 1958. https://doi.org/10.3390/sym15101958
Kerimkhulle S, Dildebayeva Z, Tokhmetov A, Amirova A, Tussupov J, Makhazhanova U, Adalbek A, Taberkhan R, Zakirova A, Salykbayeva A. Fuzzy Logic and Its Application in the Assessment of Information Security Risk of Industrial Internet of Things. Symmetry. 2023; 15(10):1958. https://doi.org/10.3390/sym15101958
Chicago/Turabian StyleKerimkhulle, Seyit, Zhulduz Dildebayeva, Akylbek Tokhmetov, Akzhibek Amirova, Jamalbek Tussupov, Ulzhan Makhazhanova, Alibek Adalbek, Roman Taberkhan, Alma Zakirova, and Alua Salykbayeva. 2023. "Fuzzy Logic and Its Application in the Assessment of Information Security Risk of Industrial Internet of Things" Symmetry 15, no. 10: 1958. https://doi.org/10.3390/sym15101958
APA StyleKerimkhulle, S., Dildebayeva, Z., Tokhmetov, A., Amirova, A., Tussupov, J., Makhazhanova, U., Adalbek, A., Taberkhan, R., Zakirova, A., & Salykbayeva, A. (2023). Fuzzy Logic and Its Application in the Assessment of Information Security Risk of Industrial Internet of Things. Symmetry, 15(10), 1958. https://doi.org/10.3390/sym15101958








