Abstract
The Internet of Things (IoT) suffers from a profound lack of trust between central gateways and sensors, e.g., gateways suspect sensors of flooding malicious packets, and vice versa, sensors suspect gateways of manipulating traffic data. One important reason for the mistrust is the asymmetry of a centralized network organization. A Decentralized Autonomous Organization (DAO) can establish a trustful and symmetric network with the blockchain. However, it is a vacant area for IoT networks to build trust between gateways and sensors within the DAO. In this paper, we firstly propose a trustful and secure IoT Network DAO solution (NetDAO) to mitigate the data manipulation and the malicious flooding packets. In particular, the NetDAO has a security rating algorithm to assign a reputation value for each entity in the network. Based on this, each entity can mitigate the malicious flooding packets using a proof-of-reputation packet-forwarding mechanism. In addition, the NetDAO stores traffic data using the blockchain to mitigate the data manipulation. The experimental results show that the NetDAO effectively mitigates malicious flooding packets and costs 1 s for ∼480 entities to complete the rating algorithm.
1. Introduction
A Decentralized Autonomous Organization (DAO) is a paradigm for constructing a symmetric, democratic and trustful social network without a central authority by using the blockchain technology [1,2,3,4]. In a DAO, because all management rules are written in consensus contracts and recorded in the blockchain, it is difficult for the malicious ones to cause continuous damage or run away with no traces [5]. For example, Wright et al. developed a measure of autonomy for DAOs based on the existing financial concept of liabilities [6]. Zichichi et al. proposed a blockchain-based platform for allowing any user to raise funds while becoming popular in the social network [7]. In addition, Dwivedi et al. presented a formal smart-contract language to describe the business semantics of a DAO [8]. The existing solutions mainly focus on the finance domain; how to construct a DAO for other domains (e.g., the communication network) has become a hot topic.
Does the communication network need a DAO? The answer is affirmative because central authorities in the communication network suffer from a profound lack of trust and cyber security threats [9,10,11,12,13]. For example, the lack of trust between central gateways and sensors on the Internet of Things (IoT). On one hand, central gateways mistrust sensors mainly because one of the sensors may attack the gateways with flooding packets [14]. On the other hand, sensors mistrust central gateways mainly because the gateways may manipulate or delete traffic data uploaded by the sensors [15]. Therefore, a DAO could benefit the communication network. In particular, Beniiche et al. proposed DAO-assisted multi-access edge computing to decrease the completion time of physical tasks [16]. Maksymyuk et al. presented a DAO-assisted spectrum and infrastructure sharing mechanism to increase the throughput of spectrum trading effectively [17]. However, the IoT network has no standard decentralized solution to build trust between gateways and sensors within a DAO.
This paper firstly proposes a trustful and secure IoT Network DAO solution (NetDAO) to mitigate the manipulation of data and the malicious flooding packets. In particular, the NetDAO provides a reputation-based security rating algorithm to assign a reputation value for each entity in the network. The security rating algorithm can punish malicious entities by decreasing the reputation value and reward legitimate entities by increasing the reputation value. Based on the reputation value, a proof-of-reputation packet-forwarding mechanism can mitigate the malicious flooding packets. The proof-of-reputation forwarding mechanism can also distribute traffic packets into multiple decentralized IoT sensors and organize themselves without central gateways. In addition, the NetDAO has a blockchain-based data storage mechanism to mitigate the data manipulation. The mechanism can generate a block formed with traffic data from one node and validate the block within other nodes in the IoT network. The main contributions are summarized as follows:
- First, a DAO solution for IoT networks is firstly proposed to organize the network without central authorities. The NetDAO has a novel reputation-based security rating algorithm to establish a credit system of network entities.
- Second, a novel packet-forwarding (proof-of-reputation) mechanism is included in the NetDAO not only to mitigate malicious flooding packets but also to distribute traffic packets into multiple decentralized IoT entities.
- Third, we implement the NetDAO solution using a paradigm of programmable data planes (P4). The experimental results show that the NetDAO can effectively mitigate malicious flooding packets and costs 1 s rating time when the network has ∼480 entities.
An IoT network needs the NetDAO solution because the amount of IoT nodes will increase geometrically, leading centralized security services to become unaffordable and untrustworthy [18]. In particular, an extensive number of malicious nodes could emit flood packets to a centralized security service (e.g., an identity service) and cause Distributed Denial-of-Service (DDoS) attacks [19]. Valuable traffic data (e.g., healthcare data) generated by massive IoT nodes could be manipulated, thus resulting in significant economic losses, because the data are in the control of centralized services which are vulnerable in an IoT network [20]. An IoT network overuses centralized services; it is important to improve the centralized services hosted on gateways by adding the NetDAO. It is worth noting that the NetDAO might not be applicable to resource-constrained IoT sensors, and this paper mainly focuses on Raspberry Pi devices with suitable resources to evaluate the effectiveness of the NetDAO solution.
The remainder of this paper is organized as follows. Section 2 overviews the related works. Section 3 introduces the NetDAO security rating algorithm and the packet-forwarding and data storage mechanisms. Section 4 evaluates the performance. Section 5 describes the limitations of the NetDAO solution in detail. Section 6 concludes this paper.
2. Related Works
Blockchain technology is a paradigm of enhancing data security and privacy for IoT networks. As Table 1 shows, there are four main hot topics for combining the blockchain technology and IoT networks: (1) blockchain-powered IoT network architecture, (2) blockchain-powered IoT data access management, (3) blockchain-powered IoT data sharing and (4) blockchain-powered IoT data privacy preserving.
Regarding the blockchain-powered IoT network architecture, Akkaoui et al. proposed a hybrid four-layer (i.e., the end-user, edge-pool, global-chain and off-chain layers) blockchain-based IoT network architecture for the eHealth scenario [21]. Sushil et al. designed and evaluated a novel IoT architecture with blockchain and AI to support an effective big data analysis [22]. The evaluation results show that the proposed architecture outperforms the existing IoT architectures in terms of the accuracy, latency, computational complexity and energy cost in IoT applications. Singh et al. presented a secure and efficient IoT network architecture by incorporating blockchain and cloud computing technologies [23]. The proposed architecture uses Multivariate Correlation Analysis (MCA) to analyze network traffic and identify the correlation between traffic features to ensure the security of IoT networks. In addition, Pavithran et al. provided limitations that should be considered while designing blockchain architecture for IoT networks and identified that device-to-device architecture has comparatively better throughput than gateway-based architecture [24].
Regarding the blockchain-powered IoT data access management, Novo et al. designed a decentralized access management system for IoT networks by using blockchain technology [25]. The access management system is developed in a private Ethereum network under a generic genesis block to simulate real IoT scenarios. Tanwar et al. proposed an access control policy consensus algorithm for improving medical data accessibility between IoT healthcare providers and evaluated the algorithm’s performance in terms of the latency and throughput [26]. Huang et al. presented a novel data authority method for resource-constrained IoT devices to manage the access to sensor data and demonstrated that the credit-based authority method is secure and efficient by conducting extensive evaluations [27]. Liu et al. designed a blockchain-based IoT access control system which contains three kinds of smart contracts, a Device Contract (DC), Policy Contract (PC) and Access Contract (AC), and evaluated that the system can maintain a high throughput in a large-scale request environment and reach a consensus efficiently in a distributed system [28]. Zhang et al. enhanced public key encryption mechanisms using the blockchain [29,30].
Regarding blockchain-powered IoT data sharing, Kang et al. proposed a blockchain-based secure IoT data trading system which has a consortium blockchain to perform consensus processes among vehicles [31]. Patel et al. designed a cross-domain image-sharing IoT network that allows for the sharing of medical images based on a consensus blockchain [32]. The consensus system could maintain a more meticulous consensus in which less effort is needed to manage the complex security and privacy module [33]. Nguyen et al. presented a novel data sharing mechanism based on blockchain and shared interplanetary file system storage (IPFS) [34]. The mechanism has smart contracts to build a trustworthy access control method during the data sharing. Shen et al. leveraged two separate decentralized networks, a blockchain P2P network and a normal P2P network, to share medical data records [35]. In addition, Fan et al. designated a blockchain-based IoT data sharing system where hospitals collect medical summaries [36]. Hospitals acting as both orders and endorsers play the role of initiating queries, verifying and validating blocks.
Regarding blockchain-powered IoT data privacy preserving, Yang et al. proposed a novel blockchain solution to preserve the worker’s position and increase the success rate of assigned work for an IoT crowdsensing system [37]. Dwivedi et al. proposed a blockchain-based secure data management and analysis mechanism to prevent IoT data privacy preserving [38]. The mechanism modifies blockchain models suitable for IoT devices that rely on their decentralized nature and other additional privacy and security properties. In addition, Qui et al. surveyed the shortcomings of existing privacy-preserving schemes and proposed a blockchain-based location privacy protection mechanism [39]. The mechanism does not require a third-party anonymizing server, instead satisfying the principle of k-anonymity privacy protection. Gai et al. proposed a blockchain-based module for constructing a smart contract for IoT networks [40]. This module allows for the regular operation of IoT data trading transactions and provides privacy preservation in design objectives. Moreover, Chen et al. designed a novel blockchain-based secure data privacy preserving scheme for IoT networks and evaluated that the average throughput of the proposed scheme can reach 110 Transactions Per Second (TPS) [41].


Table 1.
Main related works for combining the blockchain and IoT.
Table 1.
Main related works for combining the blockchain and IoT.
| Reference | Which Type of Blockchain | Which Topic | Main Contributions |
|---|---|---|---|
| [21] | Ethereum | Blockchain and IoT network architecture | A hybrid four-layer blockchain-based IoT network architecture. |
| [22] | —— | Blockchain and IoT network architecture | A novel IoT architecture with blockchain and AI to support big data analysis. |
| [25] | Ethereum | Blockchain and IoT data access management | A decentralized access management system for IoT networks within blockchain. |
| [28] | Hyperledger Fabric | Blockchain and IoT data access management | A blockchain-based IoT access system which can maintain a high throughput. |
| [34] | Ethereum | Blockchain and IoT data sharing | A novel data sharing mechanism based on blockchain and IPFS. |
| [35] | —— | Blockchain and IoT data sharing | Two separate decentralized networks are used to share medical data record. |
| [37] | Private Blockchain | Blockchain and IoT data privacy preserving | A blockchain solution to preserve workers’ position for IoT crowdsensing system. |
| [41] | Hyperledger Fabric | Blockchain and IoT data privacy preserving | A novel preserving scheme whose throughput is 110 TPS. |
Blockchain-based rating systems are gaining popularity due to features of decentralization, transparency, immutability, auditability and anonymity [42]. The rating systems are widely used for scoring services [43], vehicles [44] and IoT nodes [45,46]. For example, Wang et al. proposed a node rating-based sharding scheme for a blockchain system [45]. In that system, nodes are scored by both the speeds and results of transactions and then are assigned into different committees by balancing the score to increase the speeds of the transactions. In the NetDAO, the nodes are rated by network-related parameters, i.e., the remaining network bandwidth rate, the packet loss rate and the link redundancy rate, to mitigate their malicious network behaviors. In addition, Yang et al. presented a new reputation system for a data credibility assessment based on the blockchain techniques [46]. In that system, nodes rate the received messages based on observations of traffic environments and pack rating scores into a blockchain data structure. The rating scores only have two values: 1 (credible) and −1 (incredible). Compared with the rating scores, the NetDAO mechanism has a more flexible reputation score whose value varies from 0.0 to 1.0.
3. The NetDAO Solution
NetDAO has an architecture of integrating the DAO with IoT to mitigate the manipulation of data and malicious flooding packets. It also has a reputation-based security rating algorithm to establish a credit system of network entities. Based on this, NetDAO has a proof-of-reputation packet-forwarding mechanism not only to mitigate the malicious flooding packets but also to distribute packets into multiple decentralized IoT entities. In addition, a blockchain-based data storage mechanism is included to mitigate the data manipulation.
3.1. The Netdao Architecture
The NetDAO architecture has two layers, i.e., IoT network layer and blockchain layer, as shown in Figure 1, to mitigate the manipulation of data and malicious flooding packets. In the IoT network layer, there are gateway and sensor nodes. Each node is Raspberry Pi with 4 GB RAM and 16 GB storage resources which are suitable for running the blockchain technology. One important purpose of the IoT network layer is “impassable” of malicious flooding packets. To achieve that goal, each node is hosted with a reputation-based security rating algorithm. The algorithm can establish a credit system of network nodes and assign a reputation value for each IoT node. Based on the reputation value, a proof-of-reputation forwarding mechanism can mitigate malicious flooding packets, i.e., isolating a malicious node whose reputation value is lower than a threshold and dropping malicious packets when their source node’s reputation value is lower than a threshold. The blockchain layer has a purpose of anti-manipulation of traffic data. There are three steps to realize the goal: (1) One sensor node generates traffic data (e.g., GPS data), packs the data into a block and uploads the block to the blockchain layer; (2) the blockchain layer broadcasts the block to all nodes in the network for validation; and (3) the blockchain layer writes the block into the blockchain data structure if the block is successfully valid, otherwise the block will be abandoned. It is worth noting that the reputation value is one key rule of the block validation which is introduced in the following paragraphs.
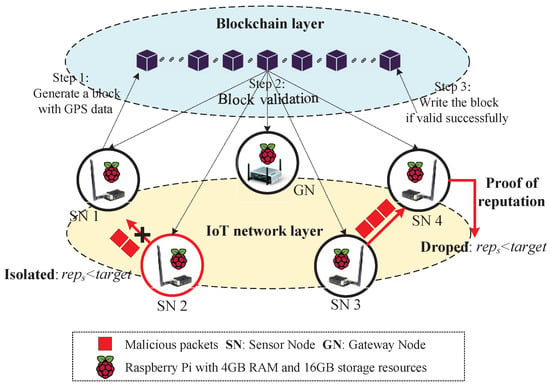
Figure 1.
The NetDAO architecture.
3.2. The Reputation-Based Security Rating Algorithm
NetDAO provides a reputation-based security rating algorithm to quantize the security or trust level for IoT nodes. In particular, one node’s (denoted as: i) reputation value is determined by two metrics: (1) a score of state of the node itself and (2) a score of the mutual-reputation given by other nodes. The node state mainly includes the remaining CPU rate, RAM rate, network bandwidth rate, packet loss rate and link redundancy rate. All the rates are in the range 0∼1. The mutual reputation is judgment reputation values given by other nodes in the IoT network within network behaviors of node i. Thus, the reputation value of network node i can be denoted as the following equations:
where represents the reputation value of node i. represents the score function of node state, e.g., the state could be the remaining CPU rate, the remaining RAM rate, the remaining network bandwidth rate, the packet loss rate and the link redundancy rate. denotes the mutual-reputation value given by node j to node i. Moreover, n denotes the number of all nodes in IoT network, i.e., all the nodes need to give a judgement reputation value to node i. In terms of engineering practice, are set as 0.2 and 0.8.
The mutual-reputation value is judged by the fluctuation of the remaining network bandwidth during a time interval . In particular, during the time interval , if the remaining bandwidth increases, a reward function will be triggered, i.e., the mutual-reputation value will increase. In other cases, if the remaining bandwidth decreases, a punishment function will be triggered, i.e., the mutual-reputation value will decrease. Thus, the mutual-reputation value can be denoted as:
whereas the punishment function can be denoted as:
where the punishment function has two parts: (1) the remaining bandwidth decrease rate and (2) the proportion of packets from node i to node j during the time interval . The punishment function can decrease the mutual-reputation value sharply. The reward function can be denoted as: ; it can increase the mutual-reputation value slowly. It is worth noting that the punishment and reward functions can make it easy for a good node to be a bad node but difficult for a bad node to be a good node. In addition, Algorithm 1 depicts the reputation-based security rating algorithm in detail.
| Algorithm 1: Compute a node’s reputation value |
 |
Figure 2 shows how to compute one node’s reputation value in the IoT network. In particular, there are three steps to compute the reputation value for node A: (1) node A obtains its state attributes, e.g., the state could be the remaining CPU rate, the remaining RAM rate, the remaining network bandwidth rate, the packet loss rate and the link redundancy rate; (2) node A requests mutual-reputation values from other nodes in the network; and (3) node A calculates its final reputation value by combining its own state attributes and the mutual-reputation values.
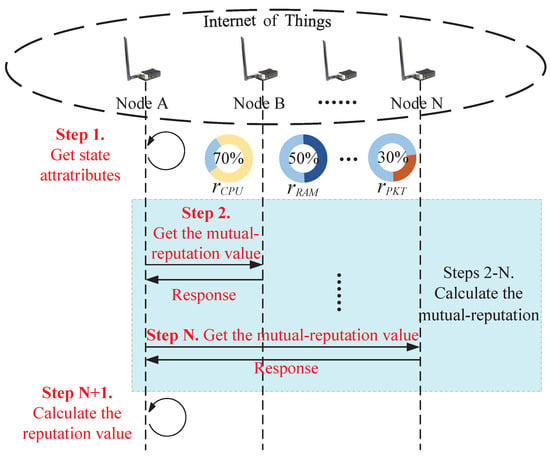
Figure 2.
The workflows of computing one IoT node’s reputation value.
3.3. The Proof-of-Reputation Forwarding Mechanism
Using the aforementioned reputation values, NetDAO provides a novel packet-forwarding mechanism not only to mitigate the malicious flooding packets but also to distribute traffic packets into multiple decentralized IoT entities. In particular, as Figure 3 shows, the forwarding mechanism has five pipelines: parser, ingress, queue, egress and deparser. The parser pipeline has a responsibility to shift a packet from bitstreams into network protocol fields in a logical order, e.g., parser the packet in the order of . The ingress pipeline can dynamically receive or drop a packet according to a reputation value of the packet’s source node and make a malicious flooding packet difficult to be received by its sink node. The egress pipeline can dynamically emit or drop a packet according to the current node’s reputation value, making it difficult for a malicious flooding packet to be emitted by its source node. The queue pipeline can change a packet position dynamically in the queue according to the reputation value of the packet’s source node. In addition, the deparser pipeline is responsible for shifting a packet into bitstreams and forwarding the packet via a network interface.
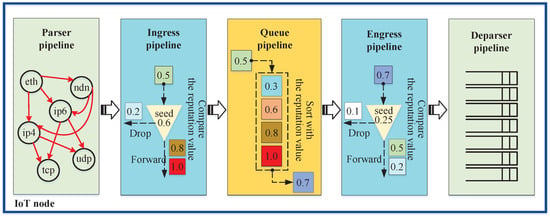
Figure 3.
Forwarding pipelines of the NetDAO.
On one hand, the NetDAO packet-forwarding mechanism can effectively mitigate the malicious flooding packets. In particular, the ingress pipeline has a responsibility to make a malicious flooding packet difficult to be received by its sink node. As Figure 4 shows, when the ingress pipeline receives a packet, it first obtains a reputation value (denoted as: ) of the packet’s source node by using the source IP field, then generates a random number (denoted as: ) and compares the number with the reputation value and finally receives the packet if , otherwise the ingress part drops the packet. In addition, the egress pipeline has a responsibility to make a malicious flooding packet difficult to be emitted by its source node. When the egress pipeline receives a packet, it first obtains a reputation value (denoted as: ) of current node, then generates a random number (denoted as: ) and compares the number with the reputation value and finally emits the packet if , otherwise the egress pipeline drops the packet. It is worth noting that random numbers are used to compare with reputation values to determine whether packets are forwarded, received or dropped. For example, if one IoT node has a large reputation value (≈1.0), then the node has a larger probability of emitting packets successfully because the random number is most likely lower than the reputation value.
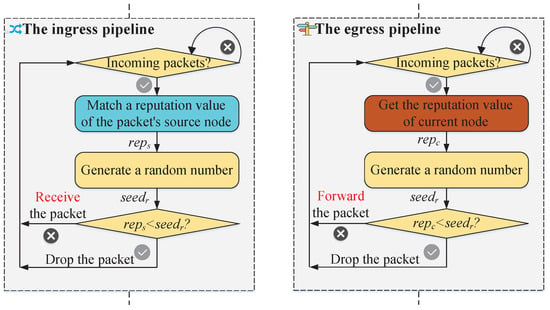
Figure 4.
The proof-of-reputation forwarding principle.
On the other hand, the NetDAO packet-forwarding mechanism can distribute management traffic packets to multiple decentralized authorities (e.g., IoT sensors) and help IoT sensors organize themselves without central gateways. In particular, as shown in Figure 5, the traditional forwarding mechanism only forwards management traffic packets between one IoT sensor and one central gateway in each session. For example, the traffic packets have payloads of temperature data uploaded from the sensor to the gateway. In that case, the central gateway may manipulate or delete traffic data uploaded by the sensor which may cause untrust between the gateway and sensor. NetDAO packet-forwarding mechanism distributes management traffic packets into every decentralized IoT sensor in each session. For example, if a packet with a payload of temperature data is emitted from IoT node1, the NetDAO mechanism forwards the packet to every other decentralized IoT node, i.e., IoT node2, node3, and node4. In that case, all decentralized nodes have backup management data and can organize themselves without central gateways. The proof-of-reputation forwarding mechanism spends additional computing and memory resources which might not be applicable to resource-constrained IoT devices.
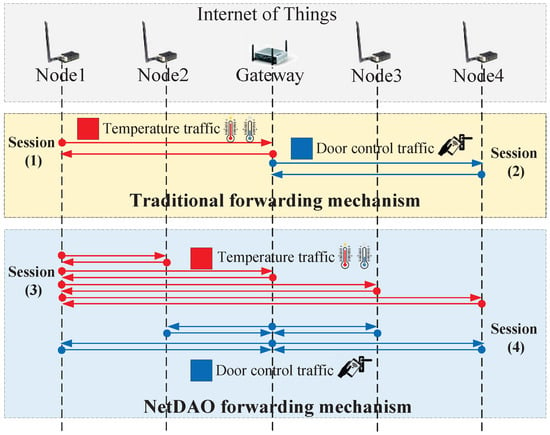
Figure 5.
The workflows of packet-forwarding mechanisms.
3.4. The Blockchain-Based Data Storage Mechanism
NetDAO stores IoT traffic data (e.g., temperature) using a blockchain-based mechanism to mitigate the risk of data manipulation or deletion. As shown in Figure 6, the mechanism can make each IoT node generate a block with five parts: Block Hash, PreBlock Hash, Merkel Hash, Timestamp and Traffic Payload (e.g., temperature data). The Block and PreBlock hashes are unique identifiers computed by a hash algorithm using the whole block content, i.e., the two hashes are dynamically changed according to the block content. The Merkel hash is a tree structure consisting of ordered data: ; each root of the tree structure has a hash value of the ordered data: . If any root hash value changes, then the Merkel hash value changes. In that case, it is easy to judge whether or not the data are manipulated according to the Merkel and PreBlock hashes.
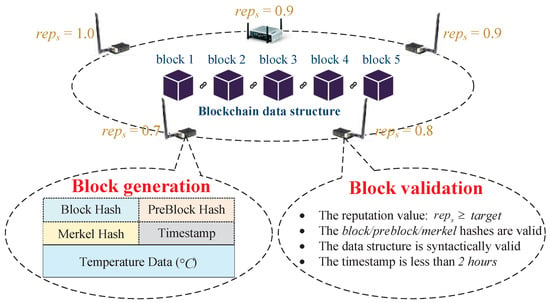
Figure 6.
The block generation and validation processes.
After a block is generated, the NetDAO forwarding mechanism broadcasts the block to each decentralized IoT node for the validation process. In particular, the block validation process generally has four steps: (1) a IoT node judges whether the block generation node’s reputation value satisfies: ; (2) the node judges whether the Block, PreBlock and Merkel hashes are valid by using classical hash algorithms; (3) the node judges whether the block data structure is syntactically valid; and 4) the node judges whether the block timestamp is less than two hours in the future. It is worth noting that all the IoT nodes receive the block and validate it by performing the aforementioned four steps. If the block is confirmed successfully by of the IoT network nodes, then the block will be recorded in the blockchain; otherwise, the block cannot be recorded and written in the blockchain.
After a block is validated successfully, the block will be recorded and stored in the IoT network. In particular, as Figure 7 shows, there are four steps to store the block in each node: (1) encrypt IoT traffic data (e.g., temperature and humidity) and pass the block validation; (2) obtain copy pieces (denoted as: ) for each traffic data; (3) store each piece into different nodes in the network; and (4) identify each stored piece (denoted as: ) by mapping the traffic data with the storage node . The reason for copying IoT traffic data is to avoid a single node of failure. In other words, if one node is attacked and the traffic data are deleted, then the service or network cannot be interrupted because other nodes also store the same data.
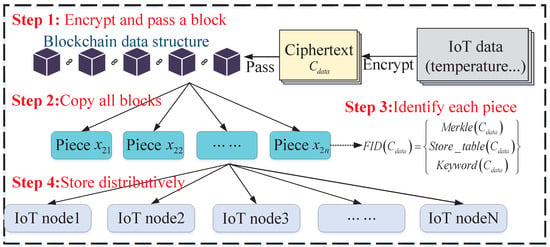
Figure 7.
The block storage process.
4. Performance Evaluation
Using a paradigm of programmable data planes (P4), we implement the NetDAO solution and evaluate its security rating algorithm performance in terms of the rating time and the reputation variability. In addition, we also evaluate how the NetDAO forwarding mechanism can mitigate malicious packet flooding by two metrics: the number of TX-packets and RX-packets. It is worth noting that the blockchain is hosted on an experimental network with five nodes in total. Each node is a Raspberry Pi with 4GB RAM and 16GB storage resources which are suitable for running a lightweight blockchain [47].
4.1. The Rating Time
To evaluate the NetDAO security rating algorithm, we implement the algorithm and compare its performance with state-of-the-art algorithms in terms of the algorithm time. In particular, the practical Byzantine fault tolerance (PBFT) algorithm is compared as a baseline because that algorithm is widely used due to its good performance in terms of latency, resource requirements and node scalability, as well as node complexity [48]. Due to the limited number of nodes in our experiments, the time spent by security rating algorithm is simulated using a Python script installed on each IoT node. The script obtains the parameters with the psutil component, obtains the mutual-reputation value with a UDP socket component and computes the algorithm time with a timer component. The script runs multiple UDP sockets simultaneously to simulate the communication exchanges of the reputation values among a large number of nodes. The experimental results are shown in Figure 8. It is clear that increasing the number of network nodes causes an increase in the algorithm time of the NetDAO and baseline algorithms. In addition, the algorithm time of the NetDAO algorithm is approximately 1 s when the IoT network has 480 nodes. The algorithm time of the baseline algorithm is approximately 1 s when the IoT network has 150 nodes. That is, the NetDAO security rating algorithm is more efficient than the state-of-the-art baseline algorithm.
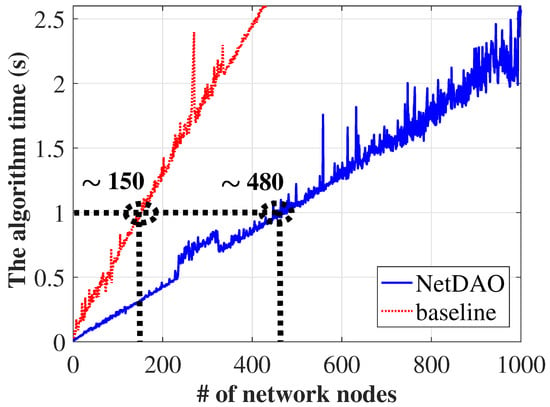
Figure 8.
The algorithm time.
4.2. The Reputation Variability
We also evaluate the effectiveness of the NetDAO security rating algorithm in terms of the reputation variability. In our experiments, we randomly choose one IoT node as a legitimate node to emit packets with a low rate, randomly select one IoT node as a malicious node to flood malicious packets with a rate of 1000/s and monitor how the reputation values of the two nodes change. The experimental results are shown in Figure 9. At the 20th second, the reputation value of IoT node2 decreases sharply to close to 0.0. This is because the node starts to flood the packets, which harvests the network bandwidth and triggers the NetDAO security rating algorithm to punish the node with a decrease in reputation. At the 40th second, the reputation value of node2 increases slowly to 0.2. This is because the node stops to flood the packets, which triggers the security rating algorithm to reward the node with an increase in reputation. It is clear that the NetDAO algorithm can effectively manage a node reputation according to the node’s network behaviors.
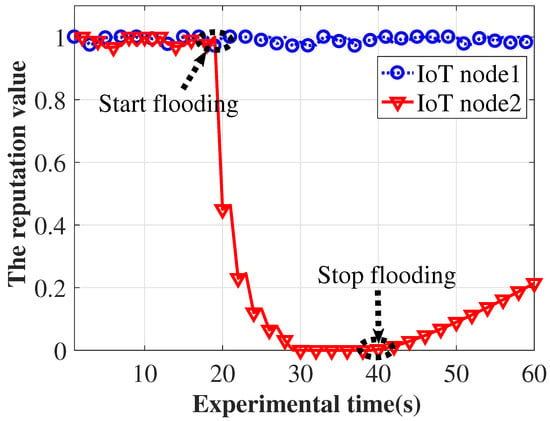
Figure 9.
The reputation value.
4.3. The Number of Packets
To evaluate how the NetDAO forwarding mechanism can mitigate malicious packet flooding, our experiments measure the mechanism by two metrics: the number of TX-packets and RX-packets. In particular, the enhanced distributed low-rate attack-mitigating mechanism is compared as a baseline because that mechanism is highly cited in the IoT domain [49]. The baseline mechanism maintains a lightweight malicious request table, which is very small, to offload the burden of a practical forwarding-state table. When a packet request is matched in a malicious request table, it will be marked as malicious and dropped directly without any impact on the forwarding-state table. In our experiments, the number of TX-packets is collected every second at the source node, and the number of RX-packets is also collected every second at the sink node. In addition, malicious packets start to flood at the 20th second with a rate of 1000/s. The experimental results are shown in Figure 10. It is clear that both the source and sink nodes have a small number of packets at the beginning of the experiments. When the flooding happens, the NetDAO forwarding mechanism can decrease the number of TX-packets from ∼1000 to ∼50 at the source node. The baseline mechanism cannot mitigate the flooding packets at the source node because the mechanism lacks a flooding-trance method. In addition, the number of RX-packets at the sink node is approximately decreased from ∼1000 to ∼70, i.e., both the NetDAO and baseline mechanisms can mitigate the flooding packets at the sink node.
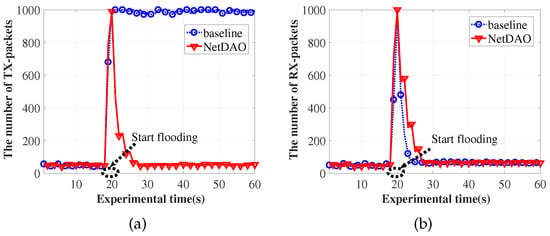
Figure 10.
The number of packets. (a) The source node; (b) the sink node.
5. Limitations
This section discusses the limitations of the NetDAO mechanism in terms of the required resources and network scales. (1) The limitation of the required resources: The NetDAO has a blockchain-based data storage mechanism to mitigate the data manipulation; it might not be applicable to resource-constrained IoT sensors (e.g., 16 KB of memory) because classical blockchain technology requires too much memory and network resources. To expand the scope of the NetDAO application, the mechanism needs to be further optimized with a lightweight blockchain technology. The lightweight blockchain should have the responsibility to enable resource-constrained devices to take part in the block generation and validation processes. (2) The limitation of the network scales: The NetDAO distributes new blocks to multiple decentralized nodes (e.g., IoT sensors) for validation and validated blocks to multiple decentralized nodes for distributed storage. That is, each node contains block data generated from other nodes. The amount of data will be super large when the IoT network has an extensive number of nodes. To make the NetDAO be more practical, a novel block validation mechanism without the storage of block data needs to be considered carefully.
6. Conclusions
This paper has designed a novel NetDAO security rating algorithm to establish a credit system for IoT network entities. Based on this, a proof-of-reputation packet-forwarding mechanism has been included not only to mitigate malicious flooding packets but also to distribute traffic packets into multiple decentralized IoT entities. Moreover, a blockchain-based data storage mechanism has been designed to mitigate the data manipulation. The experimental results have demonstrated that the NetDAO can effectively mitigate malicious flooding packets and costs 1 s rating time when the network has ∼480 nodes. In future work, we will decrease the time of the NetDAO security rating algorithm and evaluate the computing and memory overheads. In addition, more applications for the reputation values of network entities will be implemented.
Author Contributions
Methodology, G.L. and G.-B.H.; software, G.L. and J.-Y.H.; validation, J.-Y.H. and Y.Z.; writing—G.L.; writing—review and editing, C.-Y.C.; project administration, Y.Z.; All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Innovation Network Research Program of China Telecom with grant number I-2022-07.
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Liu, Y.; Shang, C. Application of Blockchain Technology in Agricultural Water Rights Trade Management. Sustainability 2022, 14, 7017. [Google Scholar] [CrossRef]
- Bischof, E.; Botezatu, A.; Jakimov, S.; Suharenko, I.; Ostrovski, A.; Verbitsky, A.; Yanovich, Y.; Zhavoronkov, A.; Zmudze, G. Longevity Foundation: Perspective on Decentralized Autonomous Organization for Special-Purpose Financing. IEEE Access 2022, 10, 33048–33058. [Google Scholar] [CrossRef]
- Hassan, S.; De Filippi, P. Decentralized autonomous organization. Int. Pol. Rev. 2021, 10, 1–10. [Google Scholar] [CrossRef]
- Wang, F.Y.; Ding, W.; Wang, X.; Garibaldi, J.; Teng, S.; Imre, R.; Olaverri-Monreal, C. The DAO to DeSci: AI for Free, Fair, and Responsibility Sensitive Sciences. IEEE Intell. Syst. 2022, 37, 16–22. [Google Scholar] [CrossRef]
- Wang, S.; Ding, W.; Li, J.; Yuan, Y.; Ouyang, L.; Wang, F.Y. Decentralized autonomous organizations: Concept, model, and applications. IEEE Trans. Comput. Social Syst. 2019, 6, 870–878. [Google Scholar] [CrossRef]
- Wright, S.A. Measuring DAO Autonomy: Lessons From Other Autonomous Systems. IEEE Trans. Technol. Soc. 2021, 2, 43–53. [Google Scholar] [CrossRef]
- Zichichi, M.; Contu, M.; Ferretti, S.; D’Angelo, G. LikeStarter: A Smart-contract based Social DAO for Crowdfunding. In Proceedings of the IEEE INFOCOM 2019-IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Paris, France, 29 April 2019–2 May 2019; pp. 313–318. [Google Scholar]
- Dwivedi, V.; Norta, A.; Wulf, A.; Leiding, B.; Saxena, S.; Udokwu, C. A formal specification smart-contract language for legally binding decentralized autonomous organizations. IEEE Access 2021, 9, 76069–76082. [Google Scholar] [CrossRef]
- Refaey, A.; Hammad, K.; Magierowski, S.; Hossain, E. A blockchain policy and charging control framework for roaming in cellular networks. IEEE Netw. 2019, 34, 170–177. [Google Scholar] [CrossRef]
- Liang, J.; Zhang, M.; Leung, V.C. A reliable trust computing mechanism based on multisource feedback and fog computing in social sensor cloud. IEEE Int. Things J. 2020, 7, 5481–5490. [Google Scholar] [CrossRef]
- Liu, G.; Quan, W.; Cheng, N.; Gao, D.; Lu, N.; Zhang, H.; Shen, X. Softwarized IoT Network Immunity Against Eavesdropping With Programmable Data Planes. IEEE Int. Things J. 2021, 8, 6578–6590. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Cheng, N.; Shen, X. Secure password-protected encryption key for deduplicated cloud storage systems. IEEE Trans. Dependable Secure Comput. 2021, 19, 2789–2806. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Li, H.; Yang, K.; Cheng, N.; Shen, X. PROTECT: Efficient password-based threshold single-sign-on authentication for mobile users against perpetual leakage. IEEE Trans. Mob. Comput. 2020, 20, 2297–2312. [Google Scholar] [CrossRef]
- Butun, I.; Österberg, P.; Song, H. Security of the Internet of Things: Vulnerabilities, attacks, and countermeasures. IEEE Commun. Surv. Tutor. 2019, 22, 616–644. [Google Scholar] [CrossRef]
- Chinaei, M.H.; Gharakheili, H.H.; Sivaraman, V. Optimal witnessing of healthcare IoT data using blockchain logging contract. IEEE Int. Things J. 2021, 8, 10117–10130. [Google Scholar] [CrossRef]
- Beniiche, A.; Ebrahimzadeh, A.; Maier, M. The way of the DAO: Toward decentralizing the tactile internet. IEEE Netw. 2021, 35, 190–197. [Google Scholar] [CrossRef]
- Maksymyuk, T.; Gazda, J.; Volosin, M.; Bugar, G.; Horvath, D.; Klymash, M.; Dohler, M. Blockchain-empowered framework for decentralized network management in 6G. IEEE Commun. Mag. 2020, 58, 86–92. [Google Scholar] [CrossRef]
- Liu, Y.; Wang, K.; Lin, Y.; Xu, W. LightChain: A lightweight blockchain system for industrial internet of things. IEEE Trans. Ind. Inform. 2019, 15, 3571–3581. [Google Scholar] [CrossRef]
- Kolias, C.; Kambourakis, G.; Stavrou, A.; Voas, J. DDoS in the IoT: Mirai and other botnets. Computer 2017, 50, 80–84. [Google Scholar] [CrossRef]
- Ferrag, M.A.; Derdour, M.; Mukherjee, M.; Derhab, A.; Maglaras, L.; Janicke, H. Blockchain Technologies for the Internet of Things: Research Issues and Challenges. IEEE Int. Things J. 2019, 6, 2188–2204. [Google Scholar] [CrossRef]
- Akkaoui, R.; Hei, X.; Cheng, W. EdgeMediChain: A Hybrid Edge Blockchain-Based Framework for Health Data Exchange. IEEE Access 2020, 8, 113467–113486. [Google Scholar] [CrossRef]
- Singh, S.K.; Rathore, S.; Park, J.H. BlockIoTIntelligence: A Blockchain-enabled Intelligent IoT Architecture with Artificial Intelligence. Future Gener. Comput. Syst. 2020, 110, 721–743. [Google Scholar] [CrossRef]
- Singh, S.; Ra, I.H.; Meng, W.; Kaur, M.; Cho, G.H. SH-BlockCC: A secure and efficient Internet of things smart home architecture based on cloud computing and blockchain technology. Int. J. Distr. Sens. Netw. 2019, 15, 1550147719844159. [Google Scholar] [CrossRef]
- Pavithran, D.; Shaalan, K.; Al-Karaki, J.N.; Gawanmeh, A. Towards building a blockchain framework for IoT. Clust. Comput. 2020, 23, 2089–2103. [Google Scholar] [CrossRef]
- Novo, O. Blockchain Meets IoT: An Architecture for Scalable Access Management in IoT. IEEE Int. Things J. 2018, 5, 1184–1195. [Google Scholar] [CrossRef]
- Tanwar, S.; Parekh, K.; Evans, R. Blockchain-based electronic healthcare record system for healthcare 4.0 applications. J. Inform. Secur. Appl. 2020, 50, 102407. [Google Scholar] [CrossRef]
- Huang, J.; Kong, L.; Chen, G.; Wu, M.Y.; Liu, X.; Zeng, P. Towards Secure Industrial IoT: Blockchain System With Credit-Based Consensus Mechanism. IEEE Trans. Ind. Inform. 2019, 15, 3680–3689. [Google Scholar] [CrossRef]
- Liu, H.; Han, D.; Li, D. Fabric-iot: A Blockchain-Based Access Control System in IoT. IEEE Access 2020, 8, 18207–18218. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Ni, J.; Li, H.; Shen, X. Blockchain-assisted public-key encryption with keyword search against keyword guessing attacks for cloud storage. IEEE Trans. Cloud Comput. 2019, 9, 1335–1348. [Google Scholar] [CrossRef]
- Zhang, Y.; Xu, C.; Lin, X.; Shen, X. Blockchain-based public integrity verification for cloud storage against procrastinating auditors. IEEE Trans. Cloud Comput. 2019, 9, 923–937. [Google Scholar] [CrossRef]
- Kang, J.; Yu, R.; Huang, X.; Maharjan, S.; Zhang, Y.; Hossain, E. Enabling localized peer-to-peer electricity trading among plug-in hybrid electric vehicles using consortium blockchains. IEEE Trans. Ind. Inform. 2017, 13, 3154–3164. [Google Scholar] [CrossRef]
- Patel, V. A framework for secure and decentralized sharing of medical imaging data via blockchain consensus. Health Inform. J. 2019, 25, 1398–1411. [Google Scholar] [CrossRef] [PubMed]
- Liu, X.; Wang, Z.; Jin, C.; Li, F.; Li, G. A blockchain-based medical data sharing and protection scheme. IEEE Access 2019, 7, 118943–118953. [Google Scholar] [CrossRef]
- Nguyen, D.C.; Pathirana, P.N.; Ding, M.; Seneviratne, A. Blockchain for secure ehrs sharing of mobile cloud based e-health systems. IEEE Access 2019, 7, 66792–66806. [Google Scholar] [CrossRef]
- Shen, B.; Guo, J.; Yang, Y. MedChain: Efficient healthcare data sharing via blockchain. Appl. Sci. 2019, 9, 1207. [Google Scholar] [CrossRef]
- Fan, K.; Wang, S.; Ren, Y.; Li, H.; Yang, Y. Medblock: Efficient and secure medical data sharing via blockchain. J. Med. Syst. 2018, 42, 1–11. [Google Scholar] [CrossRef]
- Yang, M.; Zhu, T.; Liang, K.; Zhou, W.; Deng, R.H. A blockchain-based location privacy-preserving crowdsensing system. Future Gener. Comput. Syst. 2019, 94, 408–418. [Google Scholar] [CrossRef]
- Dwivedi, A.D.; Srivastava, G.; Dhar, S.; Singh, R. A decentralized privacy-preserving healthcare blockchain for IoT. Sensors 2019, 19, 326. [Google Scholar] [CrossRef]
- Qiu, Y.; Liu, Y.; Li, X.; Chen, J. A novel location privacy-preserving approach based on blockchain. Sensors 2020, 20, 3519. [Google Scholar] [CrossRef]
- Gai, K.; Wu, Y.; Zhu, L.; Qiu, M.; Shen, M. Privacy-preserving energy trading using consortium blockchain in smart grid. IEEE Trans. Ind. Inform. 2019, 15, 3548–3558. [Google Scholar] [CrossRef]
- Chen, C.L.; Yang, J.; Tsaur, W.J.; Weng, W.; Wu, C.M.; Wei, X. Enterprise data sharing with privacy-preserved based on hyperledger fabric blockchain in IIOT’s application. Sensors 2022, 22, 1146. [Google Scholar] [CrossRef]
- Yadav, J.S.; Yadav, N.S.; Sharma, A.K. Security analysis of smart contract based rating and review systems: The perilous state of blockchain-based recommendation practices. Connect. Sci. 2022, 34, 1273–1298. [Google Scholar] [CrossRef]
- Rehman, M.; Javaid, N.; Awais, M.; Imran, M.; Naseer, N. Cloud Based Secure Service Providing for IoTs Using Blockchain. In Proceedings of the 2019 IEEE Global Communications Conference (GLOBECOM), Waikoloa, HI, USA, 9–13 December 2019; pp. 1–7. [Google Scholar]
- Liu, Y.; Xiong, Z.; Hu, Q.; Niyato, D.; Zhang, J.; Miao, C.; Leung, C.; Tian, Z. VRepChain: A Decentralized and Privacy-preserving Reputation System for Social Internet of Vehicles Based on Blockchain. IEEE Trans. Veh. Technol. 2022, 1–12. [Google Scholar] [CrossRef]
- Wang, J.; Zhou, Y.; Li, X.; Xu, T.; Qiu, T. A node rating based sharding scheme for blockchain. In Proceedings of the 2019 IEEE 25th International Conference on Parallel and Distributed Systems (ICPADS), Tianjin, China, 4–6 December 2019; pp. 302–309. [Google Scholar]
- Yang, Z.; Zheng, K.; Yang, K.; Leung, V.C. A blockchain-based reputation system for data credibility assessment in vehicular networks. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017; pp. 1–5. [Google Scholar]
- Bandara, E.; Tosh, D.; Foytik, P.; Shetty, S.; Ranasinghe, N.; De Zoysa, K. Tikiri: Towards a lightweight blockchain for IoT. Future Gener. Comput. Syst. 2021, 119, 154–165. [Google Scholar] [CrossRef]
- Wang, Y.; Zhong, M.; Cheng, T. Research on PBFT consensus algorithm for grouping based on feature trust. Sci. Rep. 2022, 12, 1–12. [Google Scholar] [CrossRef] [PubMed]
- Liu, G.; Quan, W.; Cheng, N.; Zhang, H.; Yu, S. Efficient DDoS attacks mitigation for stateful forwarding in Internet of Things. J. Netw. Comput. Appl. 2019, 130, 1–13. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).