Free-Space Continuous-Variable Quantum Key Distribution with Imperfect Detector against Uniform Fast-Fading Channels
Abstract
:1. Introduction
2. Practical CV-QKD with Imperfect Detector against Uniform Fast-Fading Channels
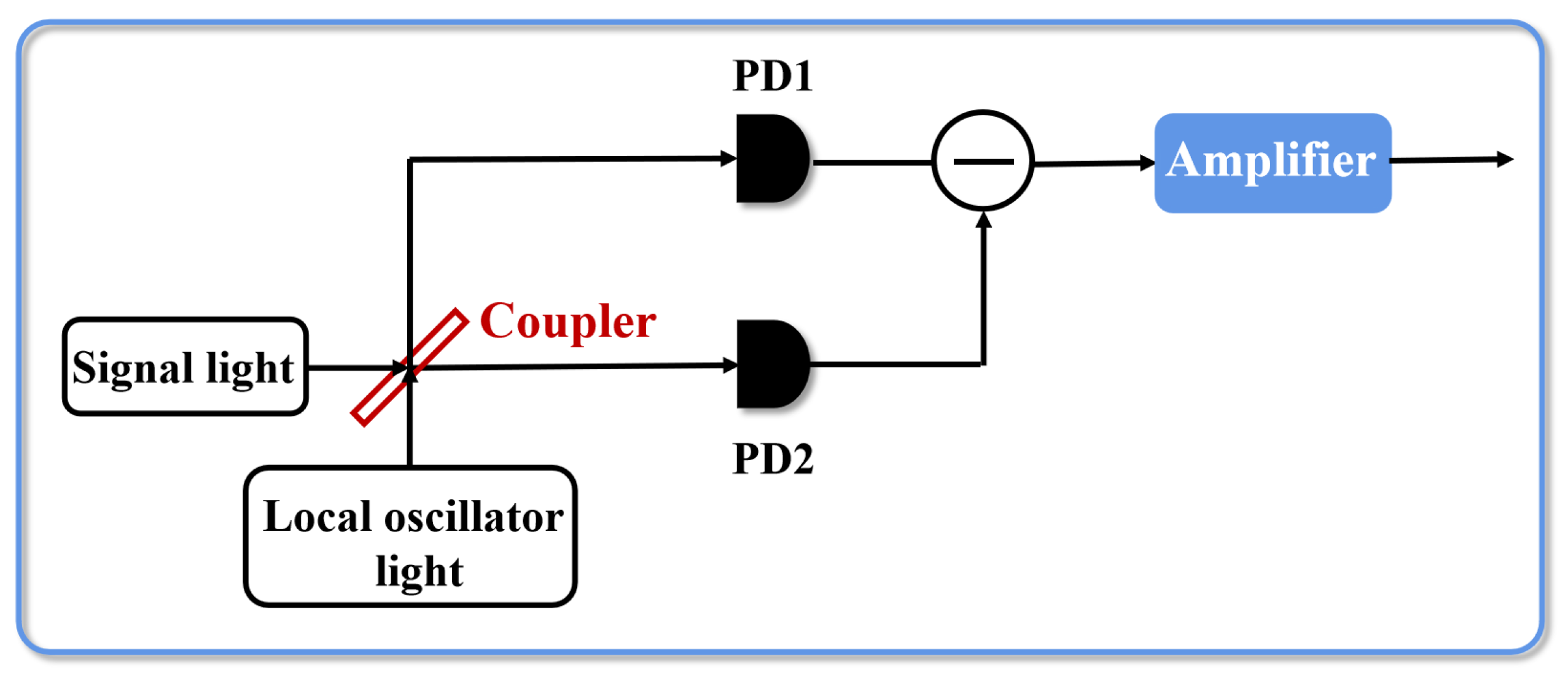
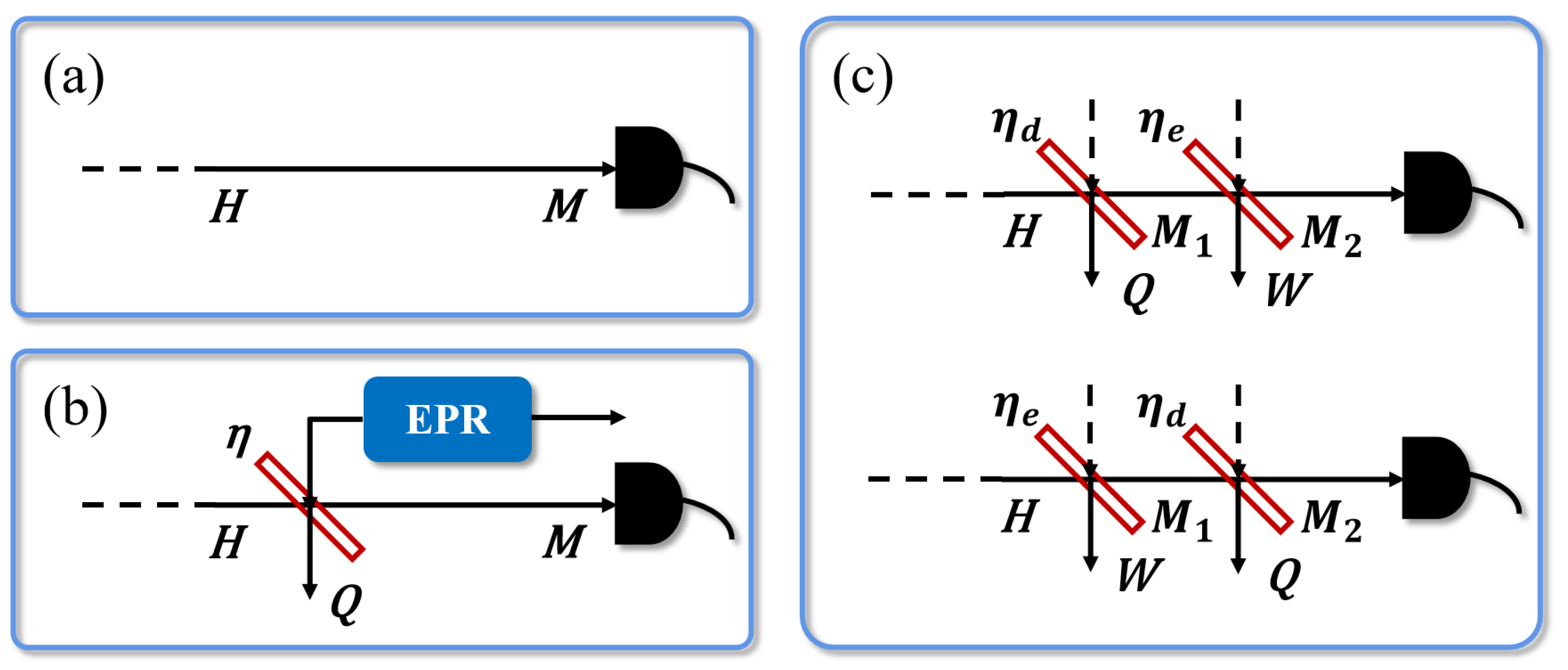
2.1. Imperfections and Trusted Model of the Practical Homodyne Detector
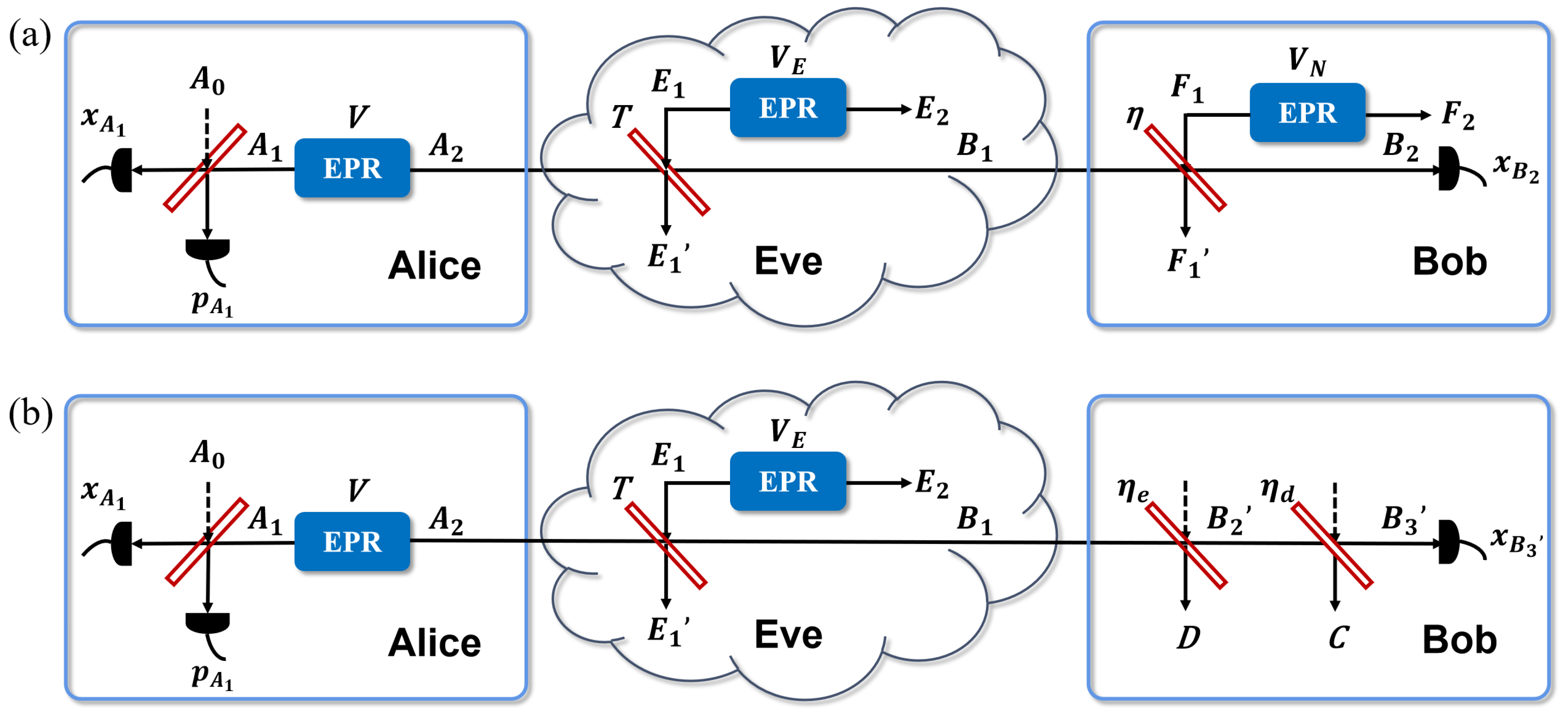
2.2. Practical CV-QKD against Fast-Fading Channels
3. Detailed Security Analysis
3.1. The Secret Key Rate of Conventional Detector Model against Fast-Fading Channels
3.2. The Secret Key Rate of Modified Detector Model against Fast-Fading Channels
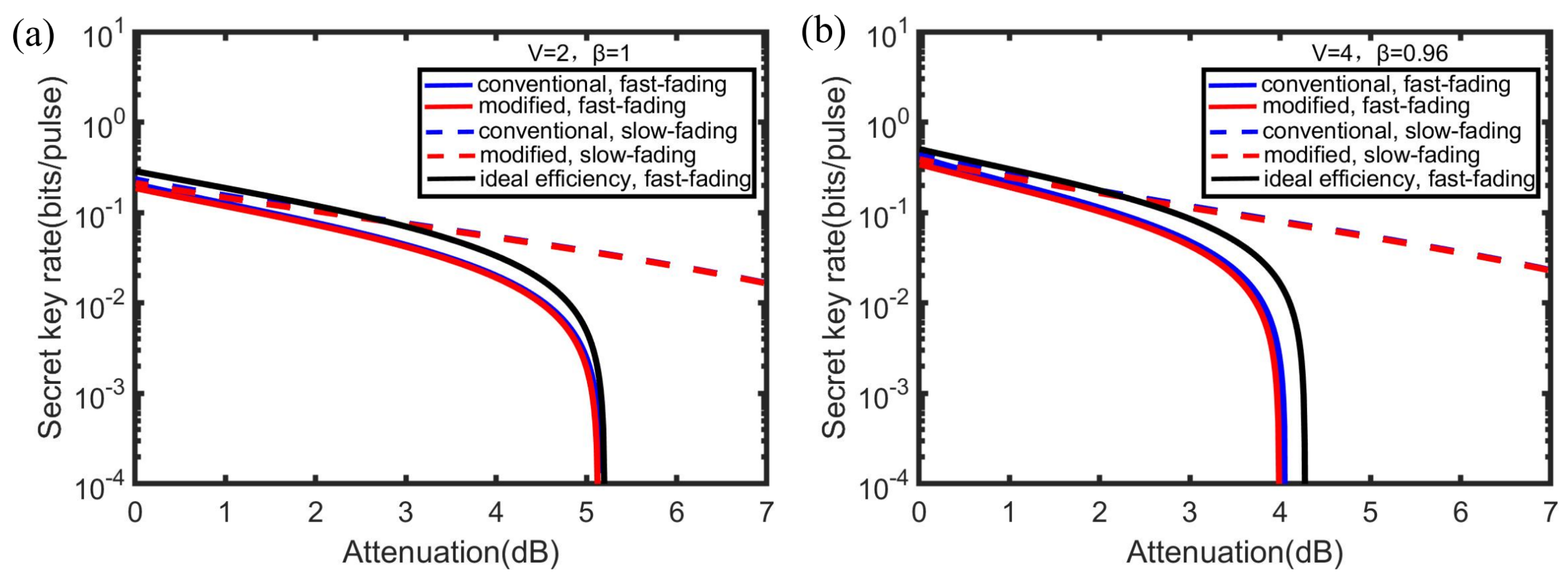
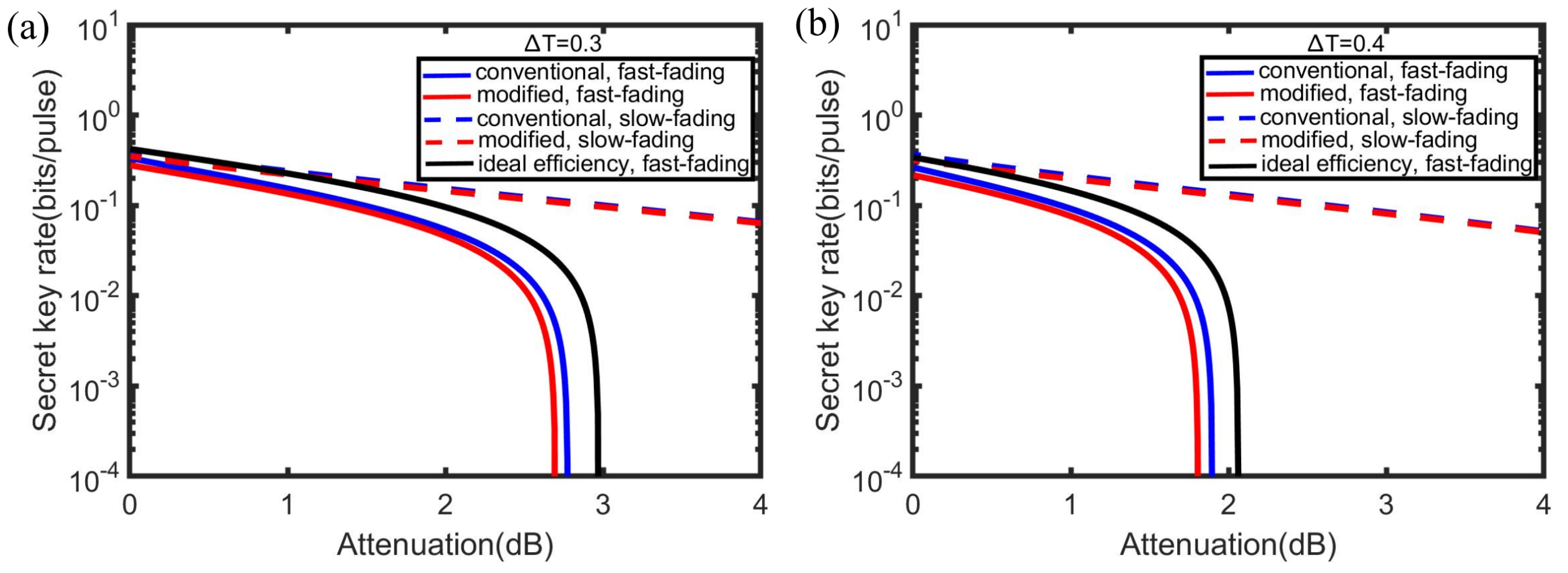
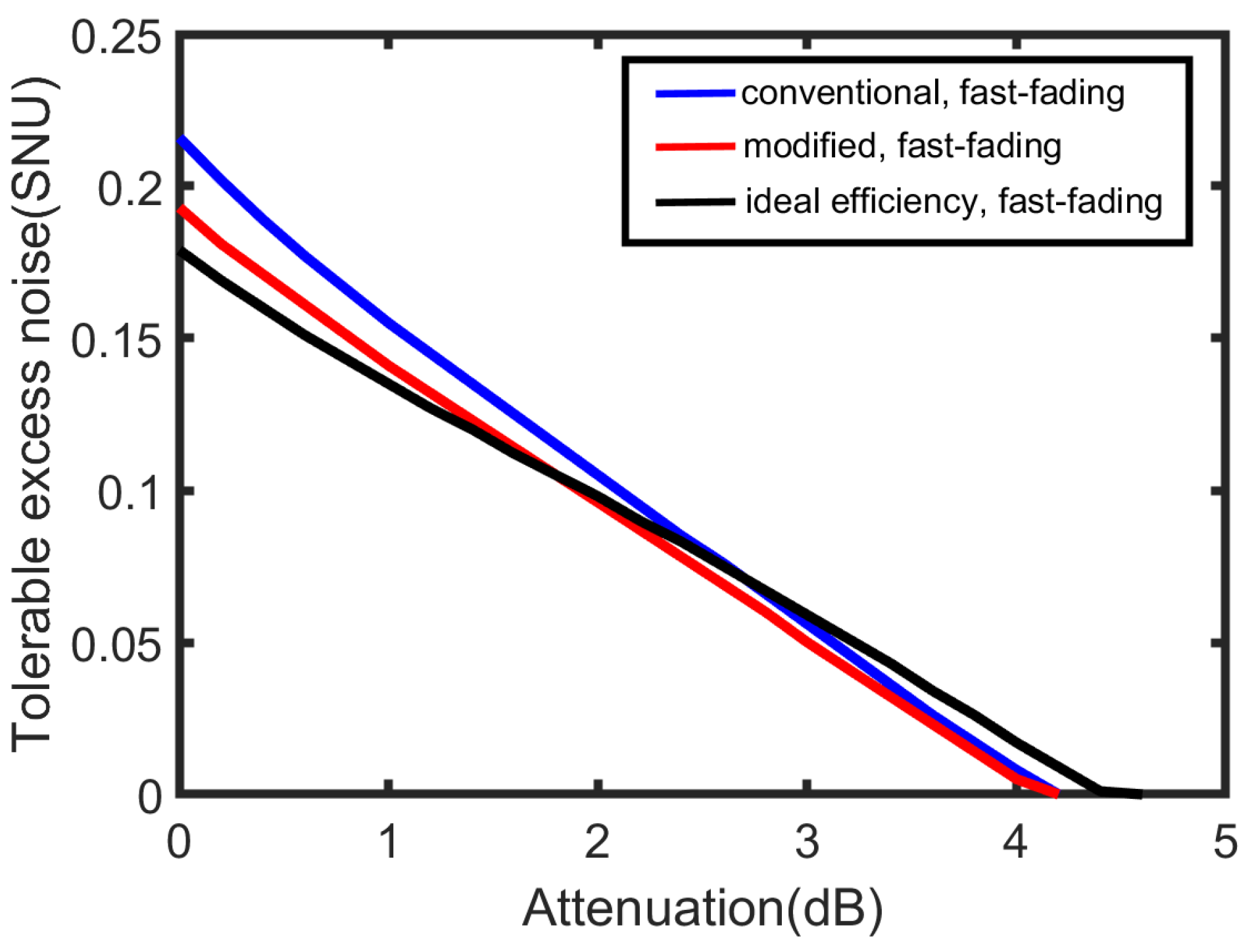
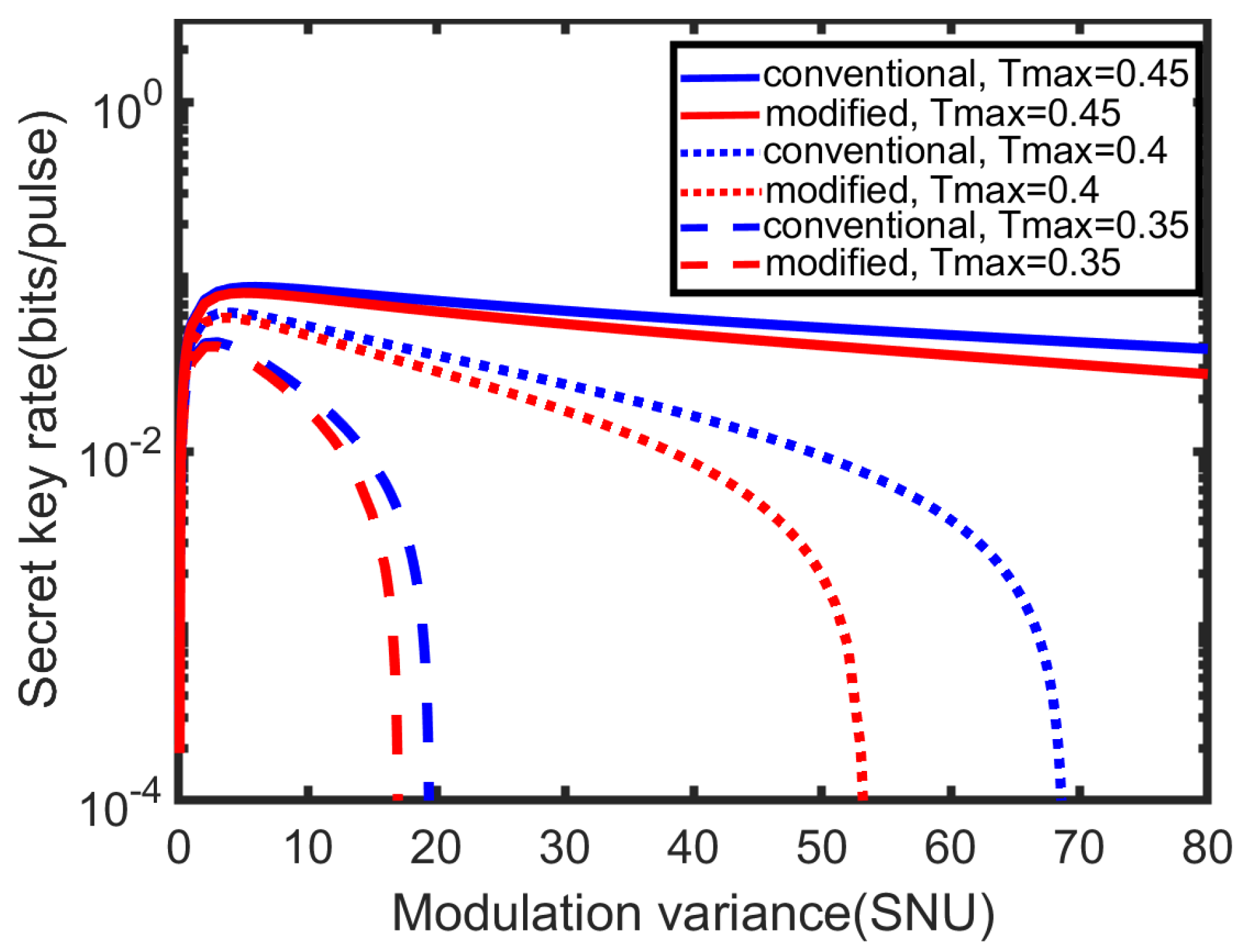
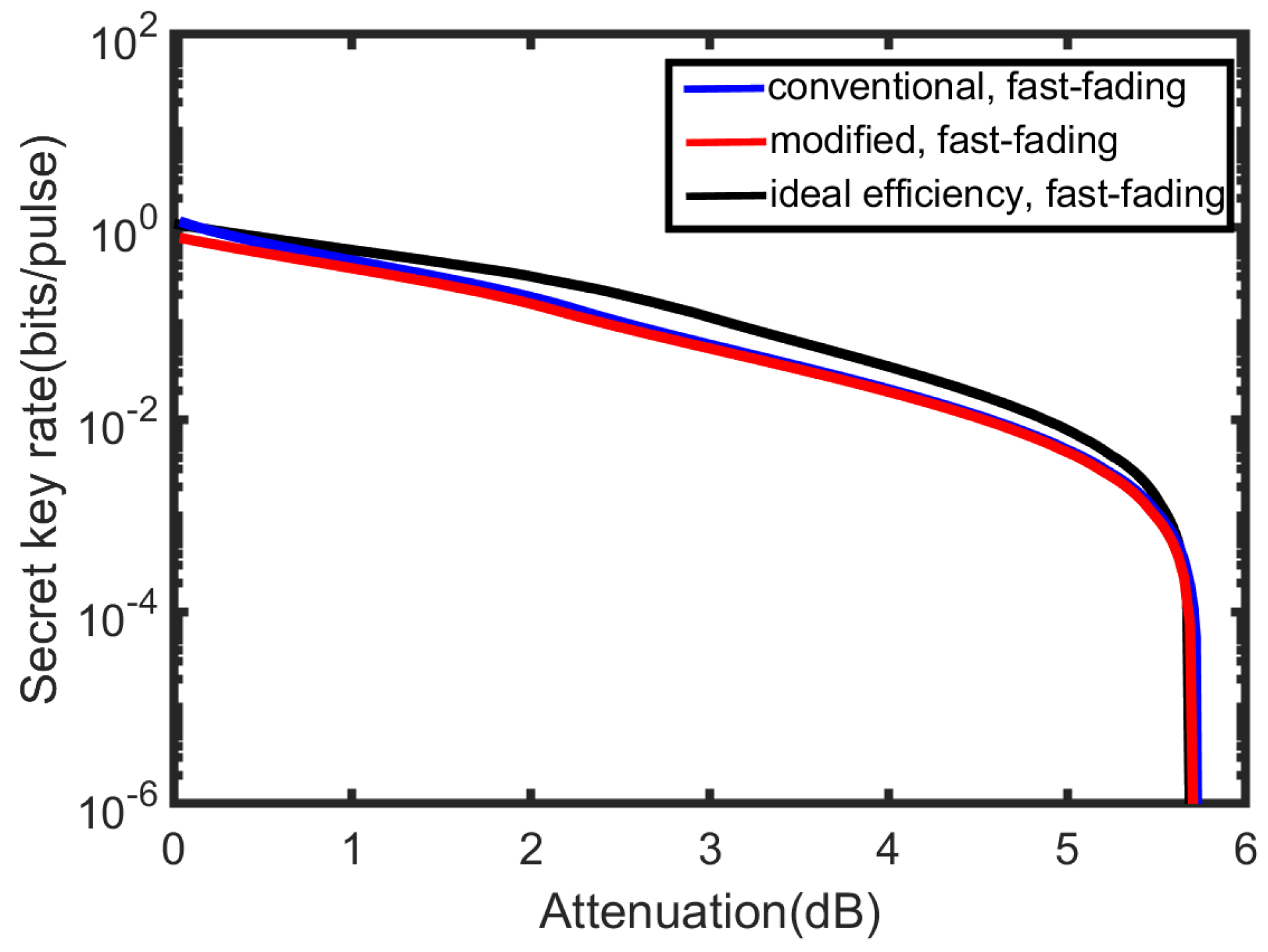
4. Simulation Results and Discussion
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. In Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, India, 9–12 December 1984; pp. 175–179. [Google Scholar]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Wallden, P. Advances in quantum cryptography. Adv. Opt. Photon. 2020, 12, 1012–1236. [Google Scholar] [CrossRef] [Green Version]
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.K.; Pan, J.W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Grosshans, F.; Grangier, P. Continuous variable quantum cryptography using coherent states. Phys. Rev. Lett. 2002, 88, 057902. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Weedbrook, C.; Lance, A.M.; Bowen, W.P.; Symul, T.; Ralph, T.C.; Lam, P.K. Quantum cryptography without switching. Phys. Rev. Lett. 2004, 93, 170504. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Weedbrook, C.; Pirandola, S.; Garcia-Patron, R.; Cerf, N.J.; Ralph, T.C.; Shapiro, J.H.; Lloyd, S. Gaussian quantum information. Rev. Mod. Phys. 2012, 84, 621–669. [Google Scholar] [CrossRef]
- Diamanti, E.; Leverrier, A. Distributing secret keys with quantum continuous variables: Principle, Security and Implementations. Entropy 2015, 17, 6072–6092. [Google Scholar] [CrossRef]
- Guo, H.; Li, Z.; Yu, S.; Zhang, Y. Toward practical quantum key distribution using telecom components. Fundam. Res. 2021, 1, 96–98. [Google Scholar] [CrossRef]
- Karinou, F.; Brunner, H.H.; Fung, C.H.F.; Comandar, L.C.; Bettelli, S.; Hillerkuss, D.; Poppe, A. Toward the integration of CV quantum key distribution in deployed optical networks. IEEE Photonics Technol. Lett. 2018, 30, 650–653. [Google Scholar] [CrossRef]
- Zhang, Y.; Li, Z.; Chen, Z.; Weedbrook, C.; Zhao, Y.; Wang, X.; Guo, H. Continuous-variable QKD over 50 km commercial fiber. Quantum Sci. Technol. 2019, 4, 035006. [Google Scholar] [CrossRef] [Green Version]
- Jouguet, P.; Kunz-Jacques, S.; Leverrier, A.; Grangier, P.; Diamanti, E. Experimental demonstration of long-distance continuous-variable quantum key distribution. Nat. Photonics 2013, 7, 378–381. [Google Scholar] [CrossRef]
- Kumar, R.; Qin, H.; Alleaume, R. Coexistence of continuous variable QKD with intense DWDM classical channels. New J. Phys. 2015, 17, 043027. [Google Scholar] [CrossRef]
- Zhang, G.; Haw, J.; Cai, H.; Xu, F.; Assad, S.M.; Fitzsimons, J.F.; Liu, A.Q. An integrated silicon photonic chip platform for continuous-variable quantum key distribution. Nat. Photonics 2019, 13, 839–842. [Google Scholar] [CrossRef]
- Eriksson, T.A.; Hirano, T.; Puttnam, B.J.; Rademacher, G.; Luís, R.S.; Fujiwara, M.; Sasaki, M. Wavelength division multiplexing of continuous variable quantum key distribution and 18.3 Tbit/s data channels. Commun. Phys. 2019, 2, 9. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Y.; Chen, Z.; Pirandola, S.; Wang, X.; Zhou, C.; Chu, B.; Guo, H. Long-distance continuous-variable quantum key distribution over 202.81 km of fiber. Phys. Rev. Lett. 2020, 125, 010502. [Google Scholar] [CrossRef]
- Liao, Q.; Xiao, G.; Zhong, H.; Guo, Y. Multi-label learning for improving discretely-modulated continuous-variable quantum key distribution. New J. Phys. 2020, 22, 083086. [Google Scholar] [CrossRef]
- Wang, H.; Pi, Y.; Huang, W.; Li, Y.; Shao, Y.; Yang, J.; Xu, B. High-speed Gaussian-modulated continuous-variable quantum key distribution with a local local oscillator based on pilot-tone-assisted phase compensation. Opt. Express 2020, 28, 32882–32893. [Google Scholar] [CrossRef]
- Liao, Q.; Xiao, G.; Xu, C.; Xu, Y.; Guo, Y. Discretely-modulated continuous-variable quantum key distribution with untrusted entanglement source. Phys. Rev. A 2020, 102, 032604. [Google Scholar] [CrossRef]
- Wang, T.; Huang, P.; Li, L.; Zhou, Y.; Zeng, G. Boosting higher secret key rate in quantum key distribution over mature telecom components. 2021; under review. [Google Scholar] [CrossRef]
- Kaltenbaek, R.; Acin, A.; Bacsardi, L.; Bianco, P.; Bouyer, P.; Diamanti, E.; Bassi, A. Quantum technologies in space. Exp. Astron. 2021, 51, 1677–1694. [Google Scholar] [CrossRef]
- Pirandola, S. Satellite quantum communications: Fundamental bounds and practical security. Phys. Rev. Res. 2021, 3, 023130. [Google Scholar] [CrossRef]
- Belenchia, A.; Carlesso, M.; Bayraktar, O.; Dequal, D.; Derkach, I.; Gasbarri, G.; Herr, W.; Li, Y.; Rademacher, M.; Sidhu, J.; et al. Quantum physics in space. Phys. Rep. 2022, 951, 1–70. [Google Scholar] [CrossRef]
- Hosseinidehaj, N.; Babar, Z.; Malaney, R.; Ng, S.X.; Hanzo, L. Satellite-based continuous-variable quantum communications: State-of-the-art and a predictive outlook. IEEE Commun. Surv. Tutor. 2018, 21, 881–919. [Google Scholar] [CrossRef] [Green Version]
- Usenko, V.C.; Heim, B.; Peuntinger, C.; Wittmann, C.; Marquardt, C.; Leuchs, G.; Filip, R. Entanglement of Gaussian states and the applicability to quantum key distribution over fading channels. New J. Phys. 2012, 14, 093048. [Google Scholar] [CrossRef]
- Wang, S.; Huang, P.; Liu, M.; Wang, T.; Wang, P.; Zeng, G. Phase compensation for free-space continuous-variable quantum key distribution. Opt. Express 2020, 28, 10737–10745. [Google Scholar] [CrossRef] [PubMed]
- Pirandola, S. Limits and security of free-space quantum communications. Phys. Rev. Res. 2021, 3, 013279. [Google Scholar] [CrossRef]
- Peuntinger, C.; Heim, B.; Muller, C.R.; Gabriel, C.; Marquardt, C.; Leuchs, G. Distribution of squeezed states through an atmospheric channel. Phys. Rev. Lett. 2014, 113, 060502. [Google Scholar] [CrossRef] [Green Version]
- Bohmann, M.; Sperling, J.; Semenov, A.A.; Vogel, W. Higher-order nonclassical effects in fluctuating-loss channels. Phys. Rev. A 2017, 95, 012324. [Google Scholar] [CrossRef] [Green Version]
- Wang, S.; Huang, P.; Wang, T.; Zeng, G. Atmospheric effects on continuous-variable quantum key distribution. New J. Phys. 2018, 20, 083037. [Google Scholar] [CrossRef] [Green Version]
- Hosseinidehaj, N.; Walk, N.; Ralph, T.C. Composable finite-size effects in free-space continuous-variable quantum-key-distribution systems. Phys. Rev. A 2021, 103, 012605. [Google Scholar] [CrossRef]
- Liao, Q.; Xiao, G.; Peng, S. Performance improvement of atmospheric continuous-variable quantum key distribution with untrusted source. Entropy 2021, 23, 760. [Google Scholar] [CrossRef]
- Liao, S.; Cai, W.; Liu, W.; Zhang, L.; Li, Y.; Ren, J.G.; Pan, J.W. Satellite-to-ground quantum key distribution. Nature 2017, 549, 43. [Google Scholar] [CrossRef] [Green Version]
- Bedington, R.; Arrazola, J.M.; Ling, A. Progress in satellite quantum key distribution. NPJ Quantum Inf. 2017, 3, 30. [Google Scholar] [CrossRef]
- Günthner, K.; Khan, I.; Elser, D.; Stiller, B.; Bayraktar, Ö.; Müller, C.R.; Leuchs, G. Quantum-limited measurements of optical signals from a geostationary satellite. Optica 2017, 4, 611–616. [Google Scholar] [CrossRef] [Green Version]
- Dequal, D.; Vidarte, L.T.; Rodriguez, V.R.; Vallone, G.; Villoresi, P.; Leverrier, A.; Diamanti, E. Feasibility of satellite-to-ground continuous-variable quantum key distribution. NPJ Quantum Inf. 2021, 7, 3. [Google Scholar] [CrossRef]
- Papanastasiou, P.; Weedbrook, C.; Pirandola, S. Continuous-variable quantum key distribution in uniform fast-fading channels. Phys. Rev. A 2018, 97, 032311. [Google Scholar] [CrossRef] [Green Version]
- Zhang, Y.; Huang, Y.; Chen, Z.; Li, Z.; Yu, S.; Guo, H. One-time shot-noise unit calibration method for continuous-variable quantum key distribution. Phys. Rev. Appl. 2020, 13, 024058. [Google Scholar] [CrossRef] [Green Version]
- Hosseinidehaj, N.; Malaney, R. CV-MDI quantum key distribution via satellite. Quantum Inf. Comput. 2017, 17, 361–379. [Google Scholar] [CrossRef]
- Lodewyck, J.; Bloch, M.; Garcia-Patron, R.; Fossier, S.; Karpov, E.; Diamanti, E.; Grangier, P. Quantum key distribution over 25 km with an all-fiber continuous-variable system. Phys. Rev. A 2007, 76, 042305. [Google Scholar] [CrossRef] [Green Version]
- Huang, Y.; Zhang, Y.; Xu, B.; Huang, L.; Yu, S. A modified practical homodyne detector model for continuous-variable quantum key distribution: Detailed security analysis and improvement by the phase-sensitive amplifier. J. Phys. B At. Mol. Opt. Phys. 2020, 54, 015503. [Google Scholar] [CrossRef]
- Chu, B.; Zhang, Y.; Huang, Y.; Yu, S.; Chen, Z.; Guo, H. Practical source monitoring for continuous-variable quantum key distribution. Quantum Sci. Technol. 2021, 6, 025012. [Google Scholar] [CrossRef]
- Huang, L.; Zhang, Y.; Yu, S. Continuous-variable measurement-device-independent quantum key distribution with one-time shot-noise unit calibration. Chin. Phys. Lett. 2021, 38, 040301. [Google Scholar] [CrossRef]
- Ruppert, L.; Peuntinger, C.; Heim, B.; Günthner, K.; Usenko, V.C.; Elser, D.; Marquardt, C. Fading channel estimation for free-space continuous-variable secure quantum communication. New J. Phys. 2019, 21, 123036. [Google Scholar] [CrossRef]
- Van Assche, G.; Cardinal, J.; Cerf, N.J. Reconciliation of a quantum-distributed Gaussian key. IEEE Trans. Inf. Theory 2004, 50, 394–400. [Google Scholar] [CrossRef] [Green Version]
- Milicevic, M.; Feng, C.; Zhang, L.M.; Gulak, P.G. Quasi-cyclic multi-edge LDPC codes for long-distance quantum cryptography. NPJ Quantum Inf. 2018, 4, 21. [Google Scholar] [CrossRef] [Green Version]
- Zhou, C.; Wang, X.; Zhang, Y.; Zhang, Z.; Yu, S.; Guo, H. Continuous-variable quantum key distribution with rateless reconciliation protocol. Phys. Rev. Appl. 2019, 12, 054013. [Google Scholar] [CrossRef] [Green Version]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fan, L.; Bian, Y.; Zhang, Y.; Yu, S. Free-Space Continuous-Variable Quantum Key Distribution with Imperfect Detector against Uniform Fast-Fading Channels. Symmetry 2022, 14, 1271. https://doi.org/10.3390/sym14061271
Fan L, Bian Y, Zhang Y, Yu S. Free-Space Continuous-Variable Quantum Key Distribution with Imperfect Detector against Uniform Fast-Fading Channels. Symmetry. 2022; 14(6):1271. https://doi.org/10.3390/sym14061271
Chicago/Turabian StyleFan, Lu, Yiming Bian, Yichen Zhang, and Song Yu. 2022. "Free-Space Continuous-Variable Quantum Key Distribution with Imperfect Detector against Uniform Fast-Fading Channels" Symmetry 14, no. 6: 1271. https://doi.org/10.3390/sym14061271
APA StyleFan, L., Bian, Y., Zhang, Y., & Yu, S. (2022). Free-Space Continuous-Variable Quantum Key Distribution with Imperfect Detector against Uniform Fast-Fading Channels. Symmetry, 14(6), 1271. https://doi.org/10.3390/sym14061271





