Abstract
Information hiding can be seen everywhere in our daily life, and this technology improves the security of information. The requirements for information security are becoming higher and higher. The coverless information hiding with the help of mapping relationship has high capacity, but there is still a problem in which the secret message cannot find the mapping relationship and the process requires extra storage burden during the transmission. Therefore, on the basis of symmetric reversible watermarking, the paper introduces the two-level mechanism and novel arrangements to solve the problem of sufficient diversity of features and has better capacity and image quality as a whole. Besides, for the security of secret message, this paper designs a new encryption model based on Logistic mapping. This method only employs coverless information hiding of one carrier image to transmit secret message with the help of the two-level mechanism and look-up table. Reversible information hiding is applied to embed the generated location table on the original image so that ensures storage and security. The experiment certifies that the diversity of hash code is increased by using the two-level image mechanism and the quality of the image is excellent, which proves the advantages of the proposed symmetric method over the previous algorithm.
1. Introduction
The development of network technology has greatly promoted the security need in daily life [1,2]. Our daily life is inseparable from the application of network transmission, so there are many technologies used to solve the problem of network transmission security. The digital media transmitted by the network mainly includes video, audio, pictures, and text. As the main form of multimedia, the acquisition and tampering of digital images are quite easy. At present, the most commonly used methods to protect digital media are mainly grouped by encryption and information hiding. The former is that the sender applies the encryption algorithm to directly encrypt the multimedia information, and the receiver with the key can obtain the secret information in view of the encryption method. Generally speaking, the garbled state formed after encryption can easily arouse the suspicion and attention of others. The information hiding needs to conceal the existence of the secret message with the help of the carrier, that is, it is hidden in multimedia data. The secret is transmitted depending on multimedia data. The receiver exploits the corresponding extraction method to extract the secret message.
The information hiding technology is a key technology and is widely utilized in many fields such as copyright protection and digital signature [3,4]. Information hiding technology changes the carrier to hide information, which can be implemented in the spatial domain or frequency domain. Some techniques even permanently damage the original carrier image. Sahu et al. apply a two-level LSB replacement technique [5]. Muhuri et al. implement image steganography on Integer Wavelet Transformation (IWT) using Particle Swarm Optimization (PSO) algorithm in 2020 [6,7,8]. Digital watermarking focuses on protecting the secret message. The digital watermarking methods commonly used inevitably cause irreversible effects on the original carrier [9]. Therefore, the emergence of reversible information hiding technology satisfies the dual recovery of the carrier and secret message [10,11,12]. Reversible information hiding means that when the receiver receives the watermarked image not only the secret message can be extracted but also the original image can be recovered according to the embedding and extraction rules [13,14]. It not only satisfies the confidentiality of secrets but also does not permanently destroy the image, which can be widely applied to medical image transmission.
Reversible information hiding was first proposed by Honsinger et al. in 1999 [15]. There are three types of algorithms on the spatial domain most commonly used by reversible information hiding techniques: lossless compression, difference expansion [16], and histogram shifting [17,18]. Difference expansion uses the correlation characteristics between pixels to expand the pixel difference through integer transformation to embed secret [19,20]. The prediction error algorithm predicts the target pixel through the prediction model [21,22,23]. Weng et al. combine difference expansion and prediction error to improve the quality of the image embedded with data [24]. According to whether the parameters used for embedding and extraction are the same, the information hiding can be divided into symmetric and asymmetric. The symmetric mechanism is efficient and simple so most of the current information hiding technologies are symmetric [25,26,27].
Steganalysis is a technique that tries to find the secret message. Although the secret message is difficult to be found by Human Visual System (HVS) on the carrier, the existence of the secret message can still be found through the traces of these modifications [28]. Coverless information hiding is one of the means to avoid steganalysis. This method directly expresses the secret message utilizing the characteristics of the carrier [29]. Zhou et al. use faster-RCNN for training to find the labels of images to express the secret message [30]. The network architecture based on deep learning has a large transmission overhead and requires a long training time. Zou et al. come up with a novel coverless information hiding based on the average pixel value of the image, which hides the information through mapping relation and multi-level index structure [31]. Cao et al. propose an approach based on the molecular structure images of material [32]. Wang et al. construct an intelligent search algorithm for mapping relationships to implement coverless information hiding [33]. Although this method solves the problems of transmission overhead and training, it inevitably adopts the mapping relationship. Information hiding techniques based on mapping relationships still have the limitation that increases the number of mapping relationships with the extension of secret information, resulting in a large cost or even being impractical.
The coverless information hiding approach proposed by Fatimah Shamsulddin Abdulsattar well improves the efficiency of feature extraction and explores the effect of block size on image hiding [34]. However, the features generated by analysis may not satisfy the secret message embedding due to lacking diversity in the obtained hash code. To improve the success rate of secret hiding, we combine the two-level mechanism and design novel arrangements to increase the diversity of hash codes.
During the hiding process, a location table is generated, so additional storage space and transmission process are required to ensure the recovery of secret data. The hidden framework proposed in this paper combines coverless information hiding and reversible information hiding techniques [35]. This process not only satisfies the hiding capacity of the secret message but also ensures the recovery of the original image. To better solve the problem of additional information storage and the security of secret data, the newly proposed encryption model is employed to encrypt the data first, then generate eigenvalues, calculate the hash code, and establish a look-up table on the original image [36]. The generated location table is embedded taking advantage of reversible information hiding technology, and the whole process is symmetric.
Since the secret message is hidden adopting a coverless way, this method will not produce any changes to the image, and then the pivotal information is embedded using the prediction error expansion (PEE) algorithm. Of course, other outstanding PEE algorithms could also be combined. Finally, the image can be recovered. The main contributions of this work are as follows.
- A more secure encryption model based on Logistic mapping is devised;
- The hash code based on the two-level image mechanism is more diverse and reduces the unconcealable rate of the secret message;
- A new combination of reversible information hiding and coverless information hiding is designed, which greatly improves capacity and the image quality;
- The proposed method solves the additional storage of location table without sacrificing hiding capacity and no large image database is required;
- Compared with other similar algorithms, our method has more security and better image quality and higher storage capacity.
The remainder of the paper is formed as follows. Section 2 reviews the basic Logistic mapping and previous coverless information method. The proposed model is presented in Section 3. Section 4 displays experiment results and comparative analysis. Finally, Section 5 gives a conclusion and future directions.
2. Related Works
To further improve the security of secret message, the paper designs a novel encryption model to encrypt it based on logistic mapping. This part also introduces the previous coverless information hiding algorithm proposed by [34].
2.1. Logistic Mapping
Chaos refers to the seemingly random and irregular movement that occurs in a non-deterministic system. It originates from nonlinear dynamic systems. Logistic mapping is one of the most famous chaotic mappings due to its simple expression and excellent performance [37,38,39]. Its expression form is as Equation (1).
where and y belongs to 0 and 1. The system control parameter is the constant and . When and the final sequence value belongs to , the logistic sequence is in the state of chaos. The function has the characteristics of aperiodic and sensitive dependence to the initial condition. Logistic mapping is simple without losing the complex characteristics of the chaos, so it is usually used on image encryption.
2.2. Previous Method
The main idea is to form a mapping relationship between the carrier and the secret message, and then realize the coverless hiding of the secret data. The construction of the look-up table is based on the generation of hash code. Fatimah Shamsulddin Abdulsattar generates eigenvalues based on feature decomposition, and then calculates the hash code of the image block and builds a look-up table [34]. The look-up table contains the hash code and its location information. In the image, the main feature vector represents the direction of the maximum change between image pixels, and the largest feature value is related to the foremost feature vector. The hash code is calculated by the largest eigenvalue obtained by feature decomposition which is Equation (2).
where denotes the largest value in the l-th sub-block and the block has k eigenvalues. The largest eigenvalue of adjacent image sub-blocks is arranged and combined in light of the specific arrangements to obtain an 8-bit binary hash code. The arrangements in this method are displayed in Figure 1. If the arrangement Arr.1, as shown in Figure 1a, is selected in the process, the hash code is acquired by Equation (3). When another arrangement (Arr.2 or Arr.3 or Arr.4) is selected, the function is calculated according to Equation (4).
where the is the largest value in the l-th sub-block and .
where and .
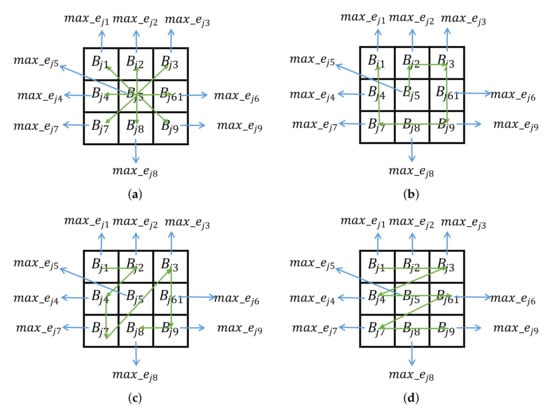
Figure 1.
The four arrangements are used in [34]. (a) Arr.1, (b) Arr.2, (c) Arr.3, and (d) Arr.4.
The hash code of each sub-block can be converted into the corresponding ASCII-code value [40]. The range of the ASCII code is . The look-up table is created by putting the positions of the hash code and the hash code into the same table. When the sender hides the secret message, they can map the table with the data and record the location of the hash code, that is, by creating a location table to achieve coverless hiding. After receiving the location table and the original image, the receiver can establish the same look-up table and then extract the hidden secret from the look-up table in the light of the mapping relationship.
According to the above description, Fatimah Shamsulddin Abdulsattar uses eigenvalue decomposition to establish the hash code as the feature of the image and then establish the look-up table. The secret message is hidden according to the mapping relationship. Although their method does not require a large database and achieves a high hidden capacity, when the image block is set to a large size, the number of hash codes generated is less. There is a problem that the secret message has no mapping relationship. When the size of the secret message increases, the corresponding location table requires more space. In other words, there is room for improvement. Our method for this problem is increasing the diversity of hash code and further improving the hiding rate.
3. Proposed Method
The information hiding technology proposed in the paper is mainly divided into two, secret message hiding and secret message extraction. The whole process is divided into two stages. The first stage takes advantage of the coverless information hiding to hide the secret message. The stage generates a vital location table. The second stage embeds the location table using the PEE algorithm. The main idea of our model is to combine coverless information hiding and PEE during hiding the secret message.
Before the secret message is hidden, the new encryption model is designed to enhance the security of secret data first. To increase the diversity of hash codes, the original image is divided into two sub-images using the two-level mechanism, and the mapping relationship formed by the look-up table established by the image blocks of the sub-image and the secret message is formed to realize the coverless hiding of the secret data. Although the hiding process does not change the original image, it needs to generate a corresponding location table. Considering that the location table needs additional storage and transmission, the paper adopts PEE to realize the second embedding of the location table. After receiving the watermarked image, the receiver can extract the location table and recover the original image. After obtaining the original image, the same look-up table can be established, and the encrypted secret information can be extracted according to the mapping relationship. The secret message can be recovered through decryption model with the same key. Figure 2 shows the framework model of the proposed algorithm. Due to the parameters used in the sender and receiver are the same, the designed model is symmetric.
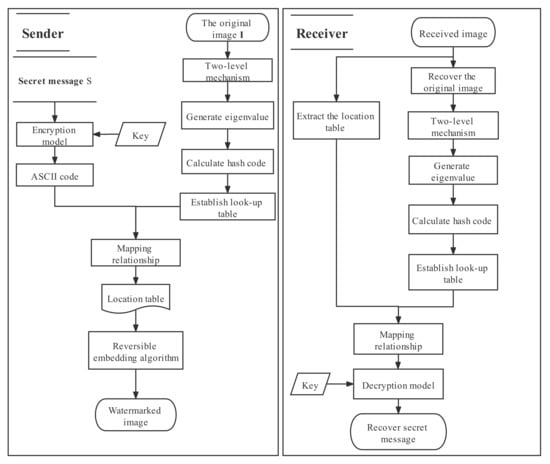
Figure 2.
The framework of the proposed model.
3.1. Encrypt the Secret Message
Logistic mapping is an encryption algorithm with a simple structure and good encryption effect. However, it is sensitive and periodic to the initial value, and its structure is relatively simple. Once the initial value is known, it is easy to be cracked. Therefore, we adopt a dual logistic mapping, and the function of the model can be described as Equation (5).
By combining the original logistic mapping and sin-logistic mapping, the final sequence is more chaotic. It is less easy to traverse to the secret message after encryption. If the initial value is not set, ten bits of secret information will be randomly selected to calculate the mean value as the initial value, see as Equation (6).
where S is the one-dimensional secret message sequence and the length is .
3.2. Hiding the Secret Message
The two-level mechanism splits the image into two sub-images, and two sub-images can be restored to the original image. Each pixel value of the image is composed of an 8-bit binary value, and the image can be divided into 8-bit planes. The image is split into two images according to the 8-bit planes of the image. The pixel value of the image is represented as Equation (7).
where p represents the pixel value in the image, represents the high-level plane, w represents the number of bits divided, and is the low-level plane. According to Equation (8), the high-level plane is divided into two parts and , where a is the constant ranging from 0 to 1.
Equation (9) is the method of dividing the low-level plane, that is, dividing the low-level plane into two sub-planes and . The parameter c is the number of bits during the division.
The two sub-planes of the high plane are combined with the two sub-planes of the low plane, respectively, according to Equation (10). Thus, two sub-images can be obtained by splitting one image according to the above-mentioned division mechanism.
The hiding stage is mainly divided into two parts; one is coverless information hiding based on the look-up table approach, and the other embeds the location table into the original image by PEE. Firstly, the image is split into two sub-images and divided into image blocks. Secondly, the 8-bits hash code of the image block is calculated according to the designed arrangements, and each group of hash code is converted into ASCII code. The ASCII code of all image blocks and their location are combined to form a look-up table. Then the secret message is hidden without changing depending on the mapping relationship. Finally, the key location table is embedded into the image by PEE. The specific embedding steps are as follows:
Step 1. Predict the pixel value by Equation (11) according to the predictor as shown in Figure 3.
where is the predicted value.
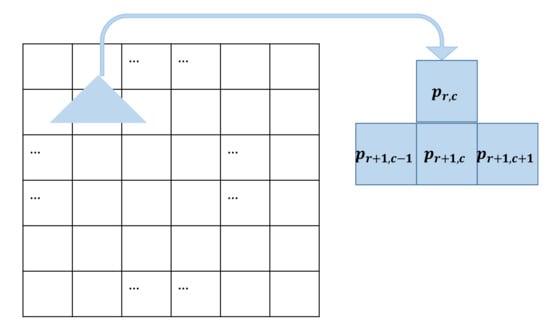
Figure 3.
The predictor used in our algorithm.
Step 2. Calculate the prediction error of the pixel according to Equation (12).
Step 3. Expand the prediction error and embed the secret message by Equation (13) where T is a threshold. The prediction error in will be used to embed the secret message.
Step 4. Modify the corresponding pixel value according to the extended prediction error referring to Equation (14).
After the secret message is embedded into the original and is transmitted to the receiver, the receiver could extract the message and recover the original image by the inverse process. Our method designs three novel arrangements as seen in Figure 4 to increase the diversity of hash codes. In Figure 4c, the nine values of the sub-block are scrambled randomly to generate the hash code so that each hiding process will have different results. The paper adopts the two-level mechanism and selects three arrangements from seven ways in Figure 1 and Figure 4 randomly to generate features. The random approach adopted can elevate the security of the architecture. This mode increases the diversity of hash code and can further allow the secret message to be successfully hidden. To understand the whole hiding process, the specific steps can be seen as Algorithm 1.
| Algorithm 1 Pseudo-code of the hiding model. |
Require: Original image , secret message S, the initial key , parameter , w, c, b, Ensure: Watermarked image Step 1. Generate one-dimensional sequence Y that the length is as same as the secret message using Equations (5) and (6) with the initial key . Step 2. Encrypt the secret message S by exclusive-or operation with Y and obtain the encrypted sequence . Step 3. Divide host image into two sub-images and based on the two-level mechanism by Equations (8)–(10). Step 4. Split two sub-images into image block with fixed-size b. Step 5. Further split into nine sub-blocks with the small size where l denotes the l-th sub-block in the image block . Step 6. Calculate the eigenvalue of all sub-blocks and find the largest value by Equation (2). Step 7. Acquire the hash code by arranging the eigenvalues of the sub-blocks in every image block where uses three arrangements of seven arrangements randomly. Step 8. Generate the ASCII code with every 8-bit hash code and an ASCII code corresponding to a block. Step 9. Establish look-up table including ASCII codes and their location. Step 10. Convert the encrypted message to ASCII code . Step 11. Match with the equal image block and record the location of the corresponding image block in order in the position table. Step 12. Embed the location table and additional information into the original image using above PEE. The additional information includes the encryption key, parameter w, c, b, , the arrangements selected, and the size of the secret message. |
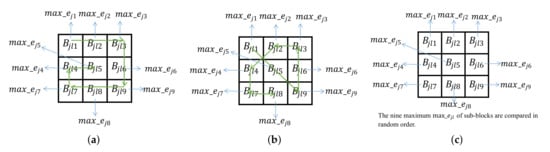
Figure 4.
The remaining three arrangements we designed. (a) Arr.5 (b) Arr.6, (c) Arr.7.
3.3. Extract the Secret Message and Recover the Original Image
The symmetric framework of requiring secret data is the inverse process of embedding. After receiving the watermarked image, the receiver first performs the inverse operation of the prediction error expansion to extract the location table and additional information. Then, the original image is recovered, and the same look-up table is established. Finally, the key and encrypted secret data are extracted according to the mapping relationship. The secret can be recovered by decrypting the encrypted message with the key. The pseudo-code is displayed in Algorithm 2 which includes the whole process of extracting the secret message and recovering the original image.
| Algorithm 2 Pseudo-code of the extraction and recover model. |
Require: Watermarked image Ensure: Recovered host image and the secret message Step 1. Extract the location table, additional information, and recover the original image . Step 2. Divide the recovered image using the same method. Step 3. Calculate the corresponding eigenvalue and hash code. Step 4. Convert the hash codes to ASCII code. Step 5. Establish the look-up table. Step 6. Acquire the encrypted secret sequence from the look-up table and the location table by the mapping relation. Step 7. Generate one-dimensional sequence that the length is as same as the secret message using Equations (5) and (6) with the initial key . Step 8. Decrypt the secret message by executing exclusive or operation between and the encrypted sequence. |
4. Experiment and Results
The computer configuration used in this article is: Intel(R) Core(TM) i5-8500 CPU @ 3.00 GHz, 16.0 GB memory, and Windows 10 (64 bits), and the experimental codes are all running on the MATLAB R2018a.
To prove the effectiveness of the encryption method, we take an example for the encryption test and compare with other encryption methods. Both methods use the same initial value to iteratively generate the sequence. Information entropy is one of the crucial indicators to measure the performance of encryption models. It is the average of the information and is expressed as Equation (15).
where satisfies .
For the digital image, the information entropy can reflect the distribution of gray values. If the gray pixel value distribution is uniform, the maximum value of information entropy will be 8, which is a proportional relationship. When the information entropy is larger, the more average the gray value distribution is, the smaller the correlation degree is.
The experimental results are shown in Table 1. It can be concluded from the data that the information entropy of the original image is 7.2081, and the information entropy after encryption can exceed 7.99; more than 7.99, in theory, means that encryption is considered successful.

Table 1.
Information entropy and correlation coefficient compared with other encryption model.
In Table 1, the information entropy of the encrypted image is 7.9954, which is closer to 8 than the other two algorithms, which proves that the method can have a more average gray value distribution after application. Our algorithm achieves the maximum information entropy, which means it performs excellently compared with other methods.
Each digital image is not independent, and the correlation between adjacent pixels is crucial. The calculation function is as Equation (16). One purpose of the image encryption is reducing the correlation between pixels, making correlation analysis invalid. The smaller the correlation value between pixels, the better the encryption effect and the safer the information. A strong correlation must be broken to avoid the statistical attack. So, we design correlation analysis experiments in three different directions and the directions include horizontal, vertical, and diagonal direction. The data are in Table 1.
So, we design correlation analysis experiments in three different directions where 2000 pairs of adjacent pixels are randomly selected for testing. The correlation coefficients in the original image and the encrypted image are calculated in the horizontal, vertical, and diagonal directions according to the above definition of the correlation coefficient. The data are in Table 1. According to Equation (16), it can be known that the coefficient may be positive or negative. When 0.3, it means that the correlation between the two variables is extremely weak and can be regarded as irrelevant. From Table 1, we can see that the correlation coefficient of the original image is close to 1, which means that there is a high correlation between pixels. On the contrary, the correlation coefficient of the encrypted image is close to 0, which means that the statistical characteristics of the encrypted image are successfully disrupted. As shown, our method achieves better dispersion than other algorithms in the horizontal, vertical, and diagonal direction and holds higher security.
Information hiding should realize the complete hiding of the secret message under the premise of ensuring the quality of the original image. In [34], the experimental results prove that there will be cases where secret message cannot be found to match it in the look-up table. Hash codes are important features used in coverless information hiding. When the range of generated features is large and different enough, hash codes are more diverse. The paper designs new arrangements, and there are seven arrangements now. In addition, we employ the two-level mechanism. Comparative experiments are performed on three different images, as shown in Figure 5. In the same figure, the experiment compares the generated types of hash codes by seven arrangements.

Figure 5.
The three test images. (a) Lena, (b) Pepper, (c) Plane.
The results are put in Table 2 which has only one arrangement. From the data in Table 2, we see that the types of hash codes generated under the two-level mechanism become larger, that is, the designed model can find more different hash codes. The diversity of the hash code is enhanced. However, the types of hash codes generated under a single arrangement still cannot reach 256. Therefore, the paper increases the formation range of hash codes and increases the diversity of hash code through the two-level mechanism and three new arrangements to achieve 256 different hash codes. The method can generate enough unique features in a non-overlapping way. To prove the effectiveness, a comparative experiment is carried out on Figure 5 when hiding the same secret message.

Table 2.
Types of different hash codes generated under different arrangements.
From the data, we can see that the hash code value generated under the two-level mechanism is larger, that is, the designed model can find more different hash codes. The diversity of the hash code is enhanced. However, the types of hash codes generated when a single arrangement is adopted still cannot reach 256. Therefore, the paper increases the formation range of hash codes and increases the diversity of hash code through the two-level mechanism and three new arrangements to achieve 256 different hash codes. The method can generate enough unique features in a non-overlapping way. To prove the effectiveness, a comparative experiment is carried out on Figure 5 when hiding the same secret message. The size of the secret message is set as 6272 bits. The test and comparison experiment results are shown in Table 3.

Table 3.
Comparison of the types of hash code and the number of the secret message cannot find.
In the experiment, the size of the secret message is set as 6272 bits. The test and comparison experiment results are shown in Table 3. Arr.4 is used in [34] and our method selected three arrangements including Arr.2, Arr.4, and Arr.5. In Table 3, “Hash code(types)” denotes the types of hash code generated, and “No-find(bits)” is that the secret message cannot find the corresponding hash code. Since every 8 bits of secret information are converted into ASCII code for embedding, the ASCII-code range is between 0 and 255. Therefore, the hash code generated should be converted into ASCII code in 256 cases. It can be seen from the test data that the previous method cannot produce enough types of hash code. There is some message that cannot find the mapping relationship in the look-up table. Our algorithm obtains more different hash codes, that is, the diversity of hash code is increased by adding arrangements and the two-level mechanism. Due to the diversity of hash code increasing, the number of no-find cases will decrease accordingly. We increase the concealment rate of secret message through adding the two-level mechanism and designing new arrangements. As the results in Table 3, when the same number of bits is hidden in the same image, we can hide all secret message compared with the previous method.
Our coverless information hiding method can store an infinite amount of secret information, but for ensuring the security and transmission space of the location table, we also use reversible information hiding technology to embed the location table into the original image. Therefore, the embedding capacity depends on the method of reversible information hiding technology used. This paper adopts a simple PPE algorithm. After hiding the secret data, the image carrying the secret message is put in Figure 6. The secret message cannot be detected from Figure 6c by our eyes.
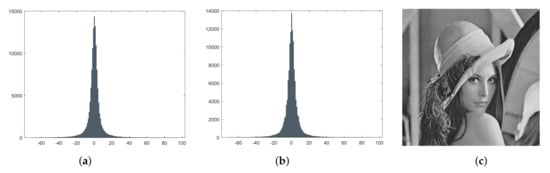
Figure 6.
The image with the secret message applying our method. (a) The histogram of the predict error; (b) the histogram of predict error after embedding message; (c) the image carrying the secret message.
Reference [34] realizes the high capacity. The high hiding capacity is one of our goals in the paper. The experiment of the capacity in the paper is compared with other methods in Figure 5a, “Lena”. The test results are stored in Table 4, where the different image has the different capacity with different embedding algorithms. The capacity represents the largest length of secret message that can be hidden under the algorithm model. From the data in Table 4, our method has the highest capacity to hide the secret message. Regarding reversible information hiding technology, it can also be combined with technologies with higher hiding ability. In the future, different reversible information hiding technologies can be selected according to the size of secret data.

Table 4.
Comparison of the hiding capacity with other papers.
In view of analyzing the image quality, this experiment is compared with several methods. This paper still uses the standard Peak Signal-to-Noise Ratio (PSNR) and Structural Similarity (SSIM) to measure the quality of several methods. PSNR is one of the criteria for measuring the invisibility of images embedded with watermarks in information hiding, calculated by Equation (17).
where and , respectively, are the pixel value in the original host and the stego image. and denote the total number of image rows and columns.
SSIM is an index to judge the similarity between two images, and the calculation function can be seen in Equation (18). Here, SSIM is used to measure the extraction quality of secret information.
where and represent the average of I and . and is the variance of and . is the covariance. and are two constants to avoid dividing by zero.
Table 5 shows PSNR and SSIM for different methods without suffering any attacks. From the calculation results, we can see that our method is the best performance of these methods. This algorithm achieves excellent image quality when it has the same capacity and can obtain the original secret message.

Table 5.
PSNR and SSIM about our proposed method and other papers.
In the network transmission, images may be intercepted or tampered with, so the information hiding algorithm needs to have the ability to resist attacks, which we call robustness. The robustness refers to the nature of an image with the secret message that can still extract information after suffering the attack. To reflect the robustness of the model designed, we compare it with the previous model. The experimental results are shown in Table 6.

Table 6.
The extraction rate using different methods under different attacks.
It can be seen from the extraction rate that under the same hidden capacity, our algorithm has higher value, which means that our model has better robustness.
Pixel Difference Histogram (PDH) is an important indicator to measure security [44,45]. The PDH graph reveals the relationship between the pixel difference and the number of occurrences of the difference. The X-axis represents the pixel difference between two consecutive pixels, and the Y-axis is the frequency of the difference. The zig-zag phenomenon that appears in the PDH curve is called the undesired step effect. If this effect appears in the curve, it is considered that the image hides the secret message. The greater the distortion of the image containing the secret message, the corresponding PDH curve shows undesired steps; conversely, when the distortion is very small, the PDH curve would look as smooth as the original image.
The same secret message is hidden in three test images located in Figure 5. Figure 7a,d,g are the curves using [34]. In this experiment, the first stage (coverless information hiding) and the final image that carries the location table of our algorithm are represented in the analysis, respectively. Figure 7b,e,f are the first stage and Figure 7c,f,i denote the results in the final image.
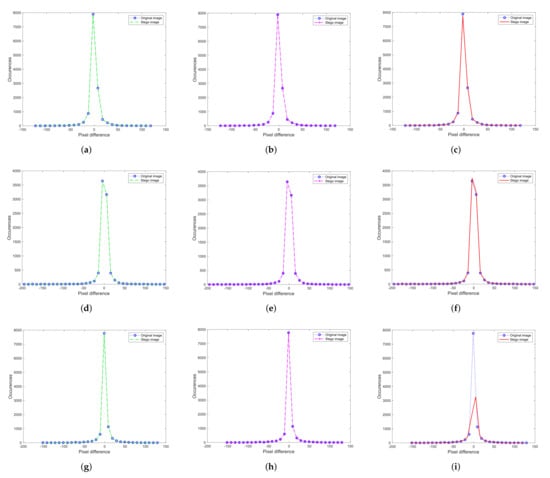
Figure 7.
The PDH analysis with different images: (a–c) are the results in “Lena”, (d–f) are the results in “Pepper”, and (g–i) are the results in “Plane”.
It can be seen that these PDH curves are still as smooth as the original image after hiding the secret message and they do not show the effects of any steps. Therefore, this algorithm is undetectable by PDH analysis and is considered to have a certain degree of security.
5. Conclusions
Network transmission is a vital part of our modern life. With the convenience it brings, information security issues follow. Information hiding has made great progress. Considering the problems of the previous work requires a large number of training databases, has the low hiding rate, and occupies a big space. This work adopts a two-level mechanism, look-up table, and reversible information hiding technology based on high-quality information hiding. Through reversible information hiding, the additional storage and transmission burden is solved. In addition, to further improve the security of the secret message, a new encryption model is designed. Compared with different methods in the experiment, our proposed model achieves high capacity and perfect hiding rate under the premise of ensuring image quality. The robustness is achieved in the attack tests. To verify the security, the PDH analysis is also performed. The test results prove that the method is undetectable by PDH. Therefore, our algorithm can achieve better results in terms of image quality, capacity, and security compared with other methods. The proposed symmetry model is outstanding and efficient.
Furthermore, we can combine different methods with higher capacity and better robustness in future work. In addition, more diverse hash codes or other feature values can be designed to hide the secret message. The method is efficient in the paper, but once an attacker masters our model, hidden information can be extracted or even tampered with. So, to further improve the security of secret messages, asymmetric mechanisms are also the focus of our future research.
Author Contributions
Conceptualization, X.-X.S. and J.-S.P.; formal analysis, J.-S.P., X.-X.S., V.S. and S.-C.C.; methodology, J.-S.P., X.-X.S., S.-C.C. and H.Y.; validation, J.-S.P., H.Y. and V.S.; writing—original draft preparation, X.-X.S.; writing—review and editing, J.-S.P., X.-X.S., S.-C.C., V.S. and H.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research received no external funding.
Data Availability Statement
Not applicable.
Conflicts of Interest
The authors declare no conflict of interest.
Abbreviations
The following abbreviations are used in this manuscript:
| Original image | |
| Watermarked image | |
| Secret message | |
| Initial key on the encryption algorithm | |
| Y | One-dimensional sequence used for encryption |
| n-th value in Y | |
| System control parameter | |
| The k-th eigenvalue in the l-th sub-block | |
| The largest value in all eigenvalues of the l-th sub-block | |
| The l-th sub-block of j-th block | |
| Hash code | |
| The length of secret message | |
| p | The pixel value in the image |
| The high-level plane | |
| The low-level plane | |
| w | The number of bits divided in the plane |
| The predicted pixel value | |
| The pixel value of the original image at row r and column i | |
| The error value between the pixel value and the predicted value | |
| T | Threshold |
| The modified error value | |
| The modified pixel value | |
| One bit in secret message S | |
| The average of the information | |
| Correlation coefficient between p and | |
| The pixel value in the original image | |
| The pixel value in the stego image | |
| The total rows of image | |
| the total columns of image | |
| PSO | Particle Swarm Optimization |
| IWT | Integer Wavelet Transformation |
| PEE | Prediction Error Expansion |
| PDH | Pixel Difference Histogram |
References
- Pfleeger, C.P. The fundamentals of information security. IEEE Softw. 1997, 14, 15–16. [Google Scholar] [CrossRef]
- Shelupanov, A.; Evsyutin, O.; Konev, A.; Kostyuchenko, E.; Kruchinin, D.; Nikiforov, D. Information Security Methods—Modern Research Directions. Symmetry 2019, 11, 150. [Google Scholar] [CrossRef] [Green Version]
- Mei, X.S.; Chen, H.T.; Fan, H.Y.; Lu, Z.M.; Yeh, J.h. A Robust Digital Image Watermarking Scheme for Content Protection. J. Netw. Intell. 2020, 5, 54–61. [Google Scholar]
- Zhang, Z.; Chen, S.; Sun, X.; Liang, Y. Trajectory privacy protection based on spatial-time constraints in mobile social networks. J. Netw. Intell. 2021, 6, 485–499. [Google Scholar]
- Sahu, A.K.; Swain, G. A novel n-rightmost bit replacement image steganography technique. 3D Res. 2019, 10, 2. [Google Scholar] [CrossRef]
- Muhuri, P.K.; Ashraf, Z.; Goel, S. A novel image steganographic method based on integer wavelet transformation and particle swarm optimization. Appl. Soft Comput. 2020, 92, 106257. [Google Scholar] [CrossRef]
- Song, P.C.; Chu, S.C.; Pan, J.S.; Yang, H. Simplified Phasmatodea population evolution algorithm for optimization. Complex Intell. Syst. 2021, 1–19. [Google Scholar] [CrossRef]
- Pan, J.S.; Song, P.C.; Pan, C.A.; Abraham, A. The Phasmatodea Population Evolution Algorithm and Its Application in 5G Heterogeneous Network Downlink Power Allocation Problem. J. Internet Technol. 2021, 22, 1199–1213. [Google Scholar]
- Pan, J.S.; Sun, X.X.; Chu, S.C.; Abraham, A.; Yan, B. Digital watermarking with improved SMS applied for QR code. Eng. Appl. Artif. Intell. 2021, 97, 104049. [Google Scholar] [CrossRef]
- Ni, Z.; Shi, Y.Q.; Ansari, N.; Su, W. Reversible data hiding. IEEE Trans. Circuits Syst. Video Technol. 2006, 16, 354–362. [Google Scholar]
- Luo, H.; Chu, S.C.; Lu, Z.M. Self embedding watermarking using halftoning technique. Circuits Syst. Signal Process. 2008, 27, 155–170. [Google Scholar] [CrossRef]
- Shi, Y.Q.; Li, X.; Zhang, X.; Wu, H.T.; Ma, B. Reversible data hiding: Advances in the past two decades. IEEE Access 2016, 4, 3210–3237. [Google Scholar] [CrossRef]
- Nguyen, T.D.; Le, H.D. A reversible data hiding scheme based on (5, 3) Hamming code using extra information on overlapped pixel blocks of grayscale images. Multimed. Tools Appl. 2021, 80, 13099–13120. [Google Scholar] [CrossRef]
- Linb, C.Y.Y.C.H.; Hua, W.C. Reversible data hiding for high-quality images based on integer wavelet transform. J. Inf. Hiding Multimed. Signal Process. 2012, 3, 142–150. [Google Scholar]
- Honsinger, C.W.; Jones, P.W.; Rabbani, M.; Stoffel, J.C. Lossless Recovery of an Original Image Containing Embedded Data. U.S. Patent 6,278,791, 21 August 2001. [Google Scholar]
- Hu, Y.; Lee, H.K.; Li, J. DE-based reversible data hiding with improved overflow location map. IEEE Trans. Circuits Syst. Video Technol. 2008, 19, 250–260. [Google Scholar]
- Faragallah, O.S.; Elaskily, M.A.; Alenezi, A.F.; El-sayed, H.S.; Kelash, H.M. Quadruple histogram shifting-based reversible information hiding approach for digital images. Multimed. Tools Appl. 2021, 80, 26297–26317. [Google Scholar] [CrossRef]
- Weng, S.; Zhao, Y.; Pan, J.S.; Ni, R. A novel reversible watermarking based on an integer transform. In Proceedings of the 2007 IEEE International Conference on Image Processing, San Antonio, TX, USA, 16 September–19 October 2007; Volume 3, pp. III-241–III-244. [Google Scholar]
- Tian, J. Reversible data embedding using a difference expansion. IEEE Trans. Circuits Syst. Video Technol. 2003, 13, 890–896. [Google Scholar] [CrossRef] [Green Version]
- Alattar, A.M. Reversible watermark using the difference expansion of a generalized integer transform. IEEE Trans. Image Process. 2004, 13, 1147–1156. [Google Scholar] [CrossRef] [PubMed]
- Thodi, D.M.; Rodriguez, J.J. Prediction-error based reversible watermarking. In Proceedings of the 2004 International Conference on Image Processing, ICIP’04, Singapore, 24–27 October 2004; Volume 3, pp. 1549–1552. [Google Scholar]
- Tseng, H.W.; Hsieh, C.P. Prediction-based reversible data hiding. Inf. Sci. 2009, 179, 2460–2469. [Google Scholar] [CrossRef]
- Weng, S.; Chu, S.C.; Cai, N.; Zhan, R. Invariability of Mean Value Based Reversible Watermarking. J. Inf. Hiding Multim. Signal Process. 2013, 4, 90–98. [Google Scholar]
- Weng, S.; Zhao, Y.; Ni, R.; Pan, J.S. Lossless data hiding based on prediction-error adjustment. Sci. China Ser. F Inf. Sci. 2009, 52, 269–275. [Google Scholar] [CrossRef]
- Yu, Y.; Lei, M.; Liu, X.; Qu, Z.; Wang, C. Novel zero-watermarking scheme based on DWT-DCT. China Commun. 2016, 13, 122–126. [Google Scholar] [CrossRef]
- Weng, S.; Chen, Y.; Hong, W.; Pan, J.S.; Chang, C.C.; Liu, Y. An improved integer transform combining with an irregular block partition. Symmetry 2019, 11, 49. [Google Scholar] [CrossRef] [Green Version]
- Yan, Y.S.; Cai, H.L.; Yan, B. Data Hiding in Symmetric Circular String Art. Symmetry 2020, 12, 1227. [Google Scholar] [CrossRef]
- Pan, J.S.; Luo, H.; Lu, Z.M. Look-up table based reversible data hiding for error diffused halftone images. Informatica 2007, 18, 615–628. [Google Scholar] [CrossRef]
- Zhou, Z.; Su, Y.; Zhang, Y.; Xia, Z.; Du, S.; Gupta, B.B.; Qi, L. Coverless Information Hiding Based on Probability Graph Learning for Secure Communication in IoT Environment. IEEE Internet Things J. 2021. [Google Scholar] [CrossRef]
- Zhou, Z.; Cao, Y.; Wang, M.; Fan, E.; Wu, Q.J. Faster-RCNN Based Robust Coverless Information Hiding System in Cloud Environment. IEEE Access 2019, 7, 179891. [Google Scholar] [CrossRef]
- Zou, L.; Sun, J.; Gao, M.; Wan, W.; Gupta, B.B. A novel coverless information hiding method based on the average pixel value of the sub-images. Multimed. Tools Appl. 2019, 78, 7965–7980. [Google Scholar] [CrossRef]
- Cao, Y.; Zhou, Z.; Sun, X.; Gao, C. Coverless information hiding based on the molecular structure images of material. Comput. Mater. Contin. 2018, 54, 197–207. [Google Scholar]
- Wang, Y.; Wu, B. An intelligent search method of mapping relation for coverless information hiding. J. Cyber Secur. 2020, 5, 48–61. [Google Scholar]
- Abdulsattar, F.S. Towards a high capacity coverless information hiding approach. Multimed. Tools Appl. 2021, 80, 18821–18837. [Google Scholar] [CrossRef]
- Weng, S.; Pan, J.s.; Li, L. Reversible data hiding based on an adaptive pixel-embedding strategy and two-layer embedding. Inf. Sci. 2016, 369, 144–159. [Google Scholar] [CrossRef]
- Wu, T.Y.; Chen, C.M.; Wang, K.H.; Pan, J.S.; Zheng, W.; Chu, S.C.; Roddick, J.F. Security Analysis of Rhee et al.’s Public Encryption with Keyword Search Schemes: A Review. J. Netw. Intell. 2018, 3, 16–25. [Google Scholar]
- Andrecut, M. Logistic map as a random number generator. Int. J. Mod. Phys. B 1998, 12, 921–930. [Google Scholar] [CrossRef]
- Pareek, N.K.; Patidar, V.; Sud, K.K. Image encryption using chaotic logistic map. Image Vis. Comput. 2006, 24, 926–934. [Google Scholar] [CrossRef]
- Li, C.; Xie, T.; Liu, Q.; Cheng, G. Cryptanalyzing image encryption using chaotic logistic map. Nonlinear Dyn. 2014, 78, 1545–1551. [Google Scholar]
- Elshoush, H.T.; Ali, I.A.; Mahmoud, M.M.; Altigani, A. A novel approach to information hiding technique using ASCII mapping based image steganography. J. Inf. Hiding Multimed. Signal Process. 2021, 12, 65–82. [Google Scholar]
- Zhou, Z.; Wu, Q.J.; Yang, C.N.; Sun, X.; Pan, Z. Coverless image steganography using histograms of oriented gradients-based hashing algorithm. J. Internet Technol. 2017, 18, 1177–1184. [Google Scholar]
- Zhang, X.; Peng, F.; Long, M. Robust coverless image steganography based on DCT and LDA topic classification. IEEE Trans. Multimed. 2018, 20, 3223–3238. [Google Scholar] [CrossRef]
- Sahu, A.K.; Swain, G. Reversible image steganography using dual-layer LSB matching. Sens. Imaging 2020, 21, 1–21. [Google Scholar] [CrossRef]
- Pradhan, A.; Sahu, A.K.; Swain, G.; Sekhar, K.R. Performance evaluation parameters of image steganography techniques. In Proceedings of the 2016 International Conference on Research Advances in Integrated Navigation Systems (RAINS), Bangalore, India, 6–7 May 2016; pp. 1–8. [Google Scholar]
- Swain, G. Very high capacity image steganography technique using quotient value differencing and LSB substitution. Arab. J. Sci. Eng. 2019, 44, 2995–3004. [Google Scholar] [CrossRef]
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
