A Modified Wei-Hua-He Digital Signature Scheme Based on Factoring and Discrete Logarithm
Abstract
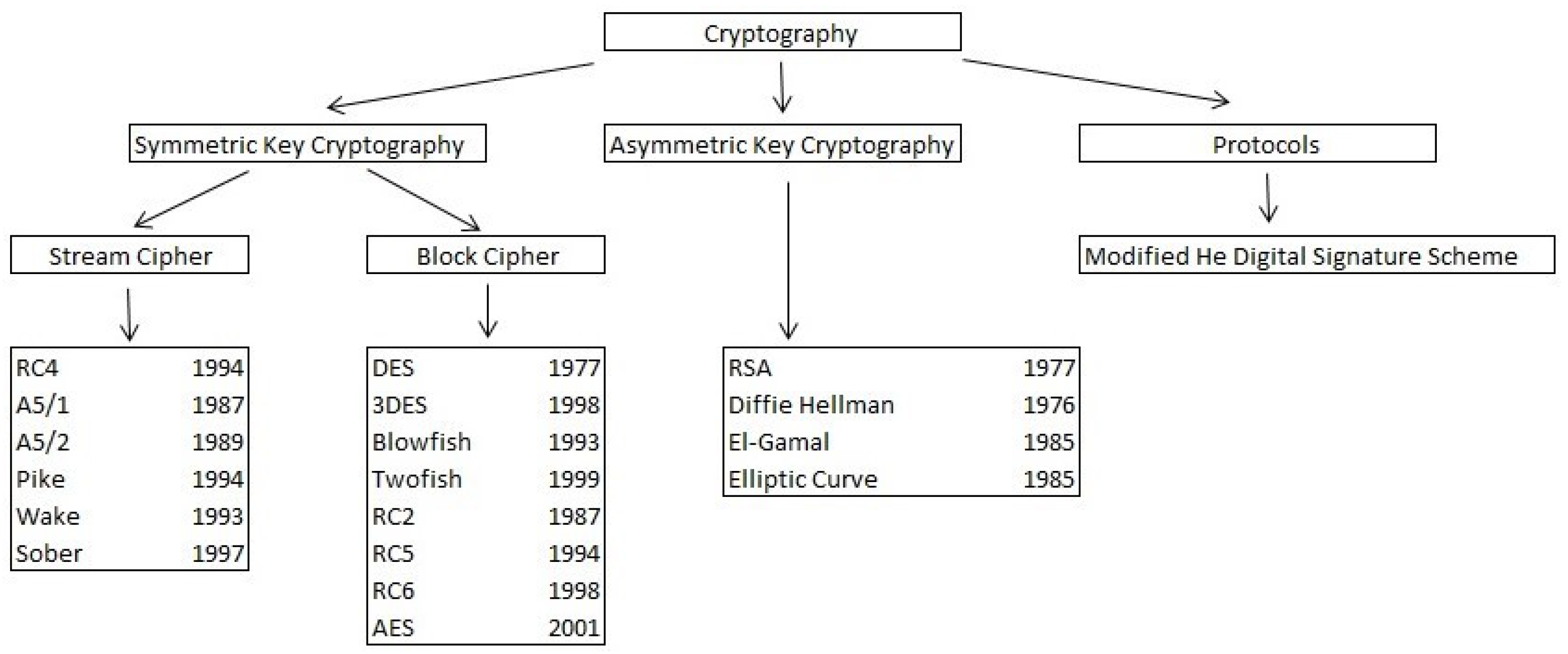
:1. Introduction
2. Motivation and Outline of the Paper
3. Security Model
3.1. Factoring Large Integer
3.2. Discrete Logarithm Problem
3.3. Expanded Root Problem
4. Proposed a Modified-He Digital Signature Scheme
4.1. Modified-He Digital Signature Scheme
4.1.1. Public Parameter
4.1.2. Key Generation
| Algorithm 1 Key Generation Algorithm |
|
- -
- p, g: Global parameters.
- -
- x: Alice’s Private key.
- -
- y: Alice’s Public key.
4.1.3. Signature Generation
| Algorithm 2 Signature Generation Algorithm |
|
- -
- m: The message must be signed.
- -
- : Alice’s signature on m.
4.1.4. Signature Verification
| Algorithm 3 Signature Verification Algorithm |
|
5. Concrete Example
5.1. Case No.1
- -
- Key Generation:
- value:
- 24204868133185954948052711126594325904950644150970719475783883549526026684120585565950513865485930072746045479777366698672918299160381477023509089521582173311372610467900279664561595681832113078528139
- value:
- 46173725832913847121436400620212043936761099218517385905639143767656777138039469879991523917154111781240677870551683249265592165846507448502443411532538863488166829223210826165970651547223649717795467
- p value:
- 97609316808472870454405302102049090631926400165007064779331430655320976676509628237857272091298564595016008517939469595141604772331116744670145968787226236724839270110107504464205570942192609743912751
- x value:
- 96927043459506992604160311113571440553541919877615452252875327060463577853683601233201782815133749826662760029498030584804703017548549339102193245959130740336143062341792496995862986391669440371955440
- g value:
- 60013100423475503376399617651347989516045909050522869961906226199920595075171660893963793787893012012968840554284018252356769557437724220116706787567813657613554342599141372868197388513025892460290169
- y value:
- 85357427054426942199227586846504813044343555691588811131491758591820003607591087796535054464276499368983800094634708787100885187797117994310277076638012713825790478365924942604617693838464217803924069
- -
- Signature Generation:
- n value:
- 6606054386291357364822658203234928691403561908506902958678631526085068054203034649360833665962190203
- t value:
- 8053063664829756788647635899905504492016188419011410808052242481159600935020471507742315216319919049
- value:
- 70067210427643294166222138993027798549657752697978469744048422500317294658740486555926205285400445471012016076449158573561242986921045773455811824689759844689682710067019646496820350622771577003668315
- value:
- 63286413639814488044951356532672917048602261731658337043906390063897091166780570790757474238526364226010764551385536115912885996253027630186549611517935457368517603605898077282586571429762806196993171
- value:
- 4362334494999478712775223492146009226763303825372585916187531903065240668375193030266442109201908173
- s value:
- 10109401522387889362354893052037631219529810827236397051544803016293074663620418259531567409456774642
- k value:
- 89881079201538338220393406015238195358929126275967524834232024829552517663753517265223614378459978284022849122332354878981301520340512477020707075692653202807205629702940580761107577790339645950841917584875586333453715730999863979292629122054004168288828032880046018817432607968266238388909227544658
- -
- Signature Verification:
- value:
- 70067210427643294166222138993027798549657752697978469744048422500317294658740486555926205285400445471012016076449158573561242986921045773455811824689759844689682710067019646496820350622771577003668315
- value:
- 63286413639814488044951356532672917048602261731658337043906390063897091166780570790757474238526364226010764551385536115912885996253027630186549611517935457368517603605898077282586571429762806196993171
- value:
- 4362334494999478712775223492146009226763303825372585916187531903065240668375193030266442109201908173
- s value:
- 10109401522387889362354893052037631219529810827236397051544803016293074663620418259531567409456774642
- k value:
- 89881079201538338220393406015238195358929126275967524834232024829552517663753517265223614378459978284022849122332354878981301520340512477020707075692653202807205629702940580761107577790339645950841917584875586333453715730999863979292629122054004168288828032880046018817432607968266238388909227544658
- y value:
- 85357427054426942199227586846504813044343555691588811131491758591820003607591087796535054464276499368983800094634708787100885187797117994310277076638012713825790478365924942604617693838464217803924069
- value:
- 85357427054426942199227586846504813044343555691588811131491758591820003607591087796535054464276499368983800094634708787100885187797117994310277076638012713825790478365924942604617693838464217803924069
5.2. Case No.2—The Digital Signature s Is a Forgery
- -
- Key Generation:
- value:
- 24204868133185954948052711126594325904950644150970719475783883549526026684120585565950513865485930072746045479777366698672918299160381477023509089521582173311372610467900279664561595681832113078528139
- value:
- 46173725832913847121436400620212043936761099218517385905639143767656777138039469879991523917154111781240677870551683249265592165846507448502443411532538863488166829223210826165970651547223649717795467
- p value:
- 97609316808472870454405302102049090631926400165007064779331430655320976676509628237857272091298564595016008517939469595141604772331116744670145968787226236724839270110107504464205570942192609743912751
- x value:
- 96927043459506992604160311113571440553541919877615452252875327060463577853683601233201782815133749826662760029498030584804703017548549339102193245959130740336143062341792496995862986391669440371955440
- g value:
- 60013100423475503376399617651347989516045909050522869961906226199920595075171660893963793787893012012968840554284018252356769557437724220116706787567813657613554342599141372868197388513025892460290169
- y value:
- 85357427054426942199227586846504813044343555691588811131491758591820003607591087796535054464276499368983800094634708787100885187797117994310277076638012713825790478365924942604617693838464217803924069
- -
- Signature Generation:
- n value:
- 6606054386291357364822658203234928691403561908506902958678631526085068054203034649360833665962190203
- t value:
- 8053063664829756788647635899905504492016188419011410808052242481159600935020471507742315216319919049
- value:
- 70067210427643294166222138993027798549657752697978469744048422500317294658740486555926205285400445471012016076449158573561242986921045773455811824689759844689682710067019646496820350622771577003668315
- value:
- 63286413639814488044951356532672917048602261731658337043906390063897091166780570790757474238526364226010764551385536115912885996253027630186549611517935457368517603605898077282586571429762806196993171
- value:
- 4362334494999478712775223492146009226763303825372585916187531903065240668375193030266442109201908173
- s value:
- 10109401522387889362354893052037631219529810827236397051544803016293074663620418259531567409456774642
- k value:
- 89881079201538338220393406015238195358929126275967524834232024829552517663753517265223614378459978284022849122332354878981301520340512477020707075692653202807205629702940580761107577790339645950841917584875586333453715730999863979292629122054004168288828032880046018817432607968266238388909227544658
- -
- Signature Verification:
- value:
- 70067210427643294166222138993027798549657752697978469744048422500317294658740486555926205285400445471012016076449158573561242986921045773455811824689759844689682710067019646496820350622771577003668315
- value:
- 63286413639814488044951356532672917048602261731658337043906390063897091166780570790757474238526364226010764551385536115912885996253027630186549611517935457368517603605898077282586571429762806196993171
- value:
- 4362334494999478712775223492146009226763303825372585916187531903065240668375193030266442109201908173
- s value:
- 4521308241444014122898680809477187136593433501725012770600777497339439501606330425756001185558080619
- k value:
- 89881079201538338220393406015238195358929126275967524834232024829552517663753517265223614378459978284022849122332354878981301520340512477020707075692653202807205629702940580761107577790339645950841917584875586333453715730999863979292629122054004168288828032880046018817432607968266238388909227544658
- y value:
- 85357427054426942199227586846504813044343555691588811131491758591820003607591087796535054464276499368983800094634708787100885187797117994310277076638012713825790478365924942604617693838464217803924069
- value:
- 94805404770283119169184237934036849389009329852856940437329202514352678675112384998024393372605900982597679807777937374725414832514624329996562642611822655963113671746537255685709398262399855215280623.
6. Security Attacks
6.1. Public Key Attack
6.2. Valid Signature Attack
6.3. Forging a Valid Signature Attack
6.4. Known Message Attack
6.5. Total Break
6.6. Existential Unforgeability under Chosen Message Attack
7. Conclusions
Author Contributions
Funding
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| Symbol/Acronym | Description |
| p | Prime number |
| Finite Field | |
| g | Generator of |
| Greatest Common Divisor of the integers p and g | |
| g mod p | Remainder upon dividing g by p |
| x | Secret key |
| y | Public key |
| m | Message |
| Hashing of the message | |
| Signature | |
| IFP | Integer Factoring Problem |
| DLP | Discrete Logarithm Problem |
| RC | Rivest Cipher |
| RSA | Rivest Shamir Adleman |
| DH | Diffie Hellman |
| DSA | Digital Signature Algorithm |
| ECDLP | Elliptic Curve Discrete Logarithm Problem |
| ECDH | Elliptic Curve Diffie Hellman |
| ECDSA | Elliptic Curve Digital Signature Algorithm |
| 3DES | Trible Data Encryption Standard |
| AES | Advanced Encryption Standard |
References
- Paar, C.; Pelzl, J. Understanding Cryptography: A Textbook for Students and Practitioners; Springer Science & Business Media: New York, NY, USA, 2009. [Google Scholar]
- Harn, L. Enhancing the security of El Gamal’s signature scheme. IEE Proc.-Comput. Digit. Tech. 1995, 142, 376. [Google Scholar] [CrossRef]
- Lee, N.Y.; Hwang, T. The security of He and Kiesler’s signature schemes. IEE Proc.-Comput. Digit. Tech. 1995, 142, 370–372. [Google Scholar] [CrossRef]
- Tiersma, H. Enhancing the security of El Gamal’s signature scheme. IEE Proc.-Comput. Digit. Tech. 1997, 144, 47–48. [Google Scholar] [CrossRef]
- Shao, Z. Signature schemes based on factoring and discrete logarithms. IEE Proc.-Comput. Digit. Tech. 1998, 145, 33–36. [Google Scholar] [CrossRef]
- Li, J.; Xiao, G. Remarks on new signature scheme based on two hard problems. Electron. Lett. 1998, 34, 2401. [Google Scholar] [CrossRef]
- Lee, N. Security of Shao’s signature schemes based on factoring and discrete logarithms. IEE Proc.-Comput. Digit. Tech. 1999, 146, 119–121. [Google Scholar] [CrossRef]
- He, W.H. Digital signature scheme based on factoring and discrete logarithms. Electron. Lett. 2001, 37, 220–222. [Google Scholar] [CrossRef]
- Pon, S.; Lu, E.; Jeng, A. Meta-He digital signature schemes based on factoring and discrete logarithms. Appl. Math. Comput. 2005, 165, 171–176. [Google Scholar]
- Chung, Y.F.; Huang, K.H.; Lai, F.; Chen, T.S. ID-based digital signature scheme on the elliptic curve cryptosystem. Comput. Stand. Interfaces 2007, 29, 601–604. [Google Scholar] [CrossRef]
- Su, P.C. Enhanced short signature scheme with hybrid problems. Comput. Electr. Eng. 2011, 37, 174–179. [Google Scholar] [CrossRef]
- Verma, S.; Sharma, B.K. A new digital signature scheme based on two hard problems. Int. J. Pure Appl. Sci. Technol. 2011, 5, 55–59. [Google Scholar]
- Vishnoi, S.; Shrivastava, V. A new digital signature algorithm based on factorization and discrete logarithm problem. Int. J. Comput. Trends Technol. 2012, 3, 653–657. [Google Scholar]
- Berezin, A.; Moldovyan, N.; Shcherbacov, V. Cryptoschemes Based on Dificulty of Simultaneous Solving Two Diferent Dificult Problems. Comput. Sci. J. Mold. 2013, 62, 280–290. [Google Scholar]
- Van Hiep, P.; Mong, N.H.; Dung, L.H. Constructing a digital signature algorithm based on the difficult of co-resolve two hard problems: Integer factorization and discrete logarithm. J. Sci. Technol. Danang Univ. 2018, 7, 28. [Google Scholar]
- Thai, N.V.; Dung, L.H. A public key cryptosystem based on the difficult of co-resolved two hard problems: Discrete logarithm and root finding. J. Inf. Commun. Minist. Inf. Commun. 2018, 12, 2018. [Google Scholar]
- Dung, L.H.; Duc, T.M.; Van, L.X. A new method for constructing digital signature schemes base on difficulty of the integer factorization and discrete logarithm root problems the Zn. In Proceedings of the Fundamental and Applied IT Research Conference, Hanoi, Vietnam, 8–9 October 2018; pp. 1–9. [Google Scholar]
- Hong, D.L. A new digital signature scheme based on the hardness of some expanded root problems. Procedia Comput. Sci. 2020, 171, 541–550. [Google Scholar]
- Lizama-Pérez, L.A. Digital signatures over HMAC entangled chains. Eng. Sci. Technol. Int. J. 2022, 32, 101076. [Google Scholar] [CrossRef]
- Moldovyan, D. A practical digital signature scheme based on the hidden logarithm problem. Comput. Sci. J. Mold. 2021, 86, 206–226. [Google Scholar]
- Huang, X.; Dong, Y.; Ye, G.; Yap, W.S.; Goi, B.M. Visually meaningful image encryption algorithm based on digital signature. Digit. Commun. Netw. 2022, in press. [Google Scholar] [CrossRef]
- Gallian, J.A. Contemporary Abstract Algebra; Chapman and Hall: New York, NY, USA, 2021. [Google Scholar]
- Koblitz, N. A Course in Number Theory and Cryptography; Springer Science & Business Media: New York, NY, USA, 1994; Volume 114. [Google Scholar]

| Cryptosystems | Cipher | Security Level (bit) |
|---|---|---|
| 256 | ||
| Asymmetric key cryptosystem | RSA | 15,360 bit |
| DH, DSA, Elgamal | 15,360 bit | |
| ECDH, ECDSA | 512 bit | |
| Symmetric key cryptosystem | AES, 3DES | 256 bit |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
R, E.; Anjaneyulu, G.S.G.N. A Modified Wei-Hua-He Digital Signature Scheme Based on Factoring and Discrete Logarithm. Symmetry 2022, 14, 2443. https://doi.org/10.3390/sym14112443
R E, Anjaneyulu GSGN. A Modified Wei-Hua-He Digital Signature Scheme Based on Factoring and Discrete Logarithm. Symmetry. 2022; 14(11):2443. https://doi.org/10.3390/sym14112443
Chicago/Turabian StyleR, Elumalai, and G. S. G. N. Anjaneyulu. 2022. "A Modified Wei-Hua-He Digital Signature Scheme Based on Factoring and Discrete Logarithm" Symmetry 14, no. 11: 2443. https://doi.org/10.3390/sym14112443
APA StyleR, E., & Anjaneyulu, G. S. G. N. (2022). A Modified Wei-Hua-He Digital Signature Scheme Based on Factoring and Discrete Logarithm. Symmetry, 14(11), 2443. https://doi.org/10.3390/sym14112443






