Image Encryption Based on Arnod Transform and Fractional Chaotic
Abstract
:1. Introduction
2. Preliminary
2.1. The Principle of Image Encryption Using Arnold Transform
2.2. First Image Encryption Principle of Arnold Transform
3. Analysis of Proposed Method
3.1. Improving the Principle of Image Encryption and Decryption
3.2. Arnold Transformation Using the Fractional Logistic Map
3.3. Arnold Transformation Using the Fractional Logistic Map
3.4. Fractional Order Logistic Chaos XOR
4. Implementation
- Step 0: Three fractional order chaotic sequences are generated and two are chosen randomly as a, b in the Arnold transform matrix.
- Step 1: Using fractional order Logistic chaos Arnold transform to realize encryption of spatial coordinates;
- Step 2: Three fractional order chaotic sequences are generated and one is chosen randomly as key. The parameters in this key are:
- Step 3: Using XOR involving key to realize encryption.
- Step 4: Taking the encrypted image with the key (fractional order logistic chaotic sequence to) to decrypt the image.
- Step 5: Using Arnold inverse transformation to realize second encryption of spatial coordinates.
5. Experiment and Performance Comparison
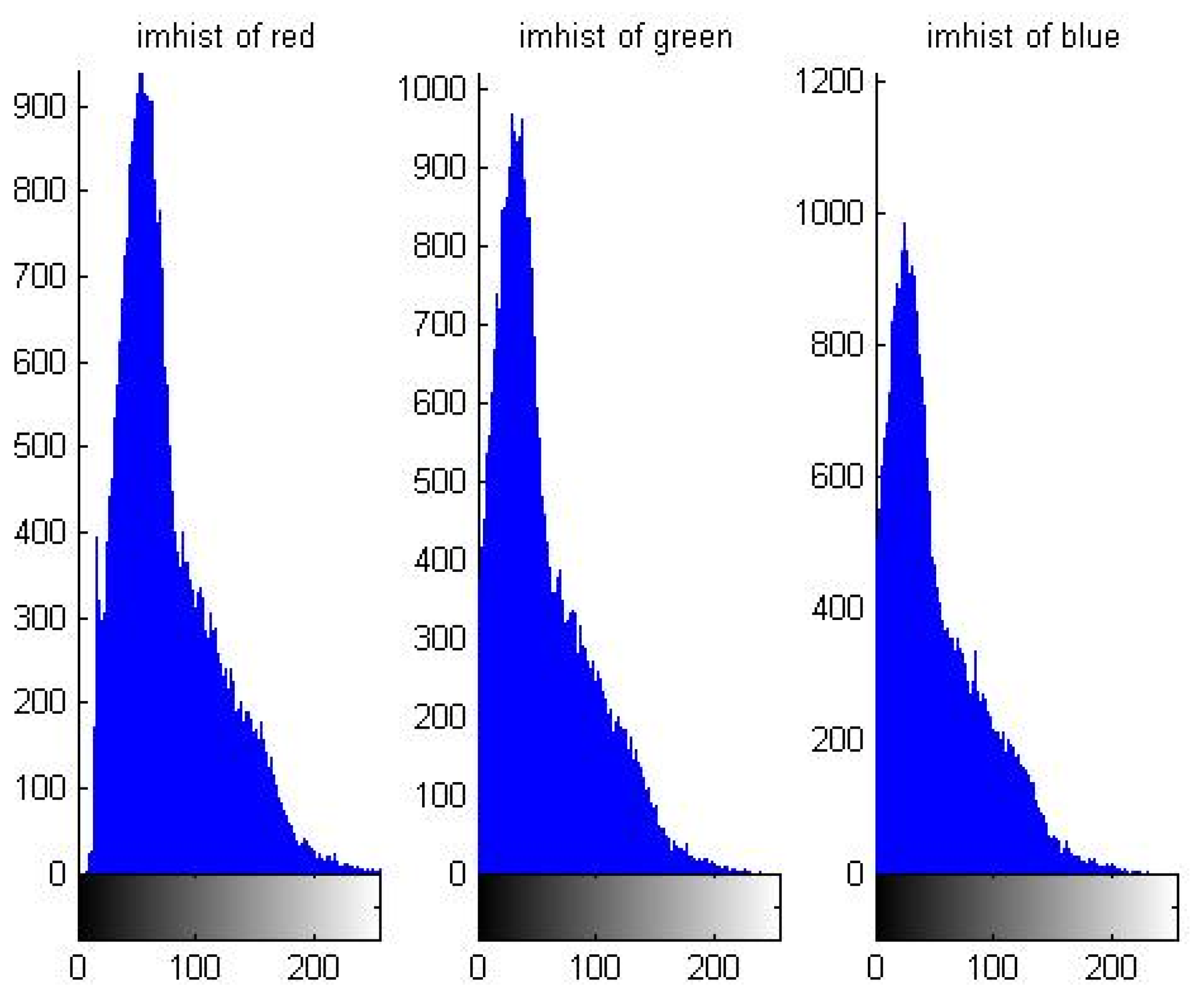
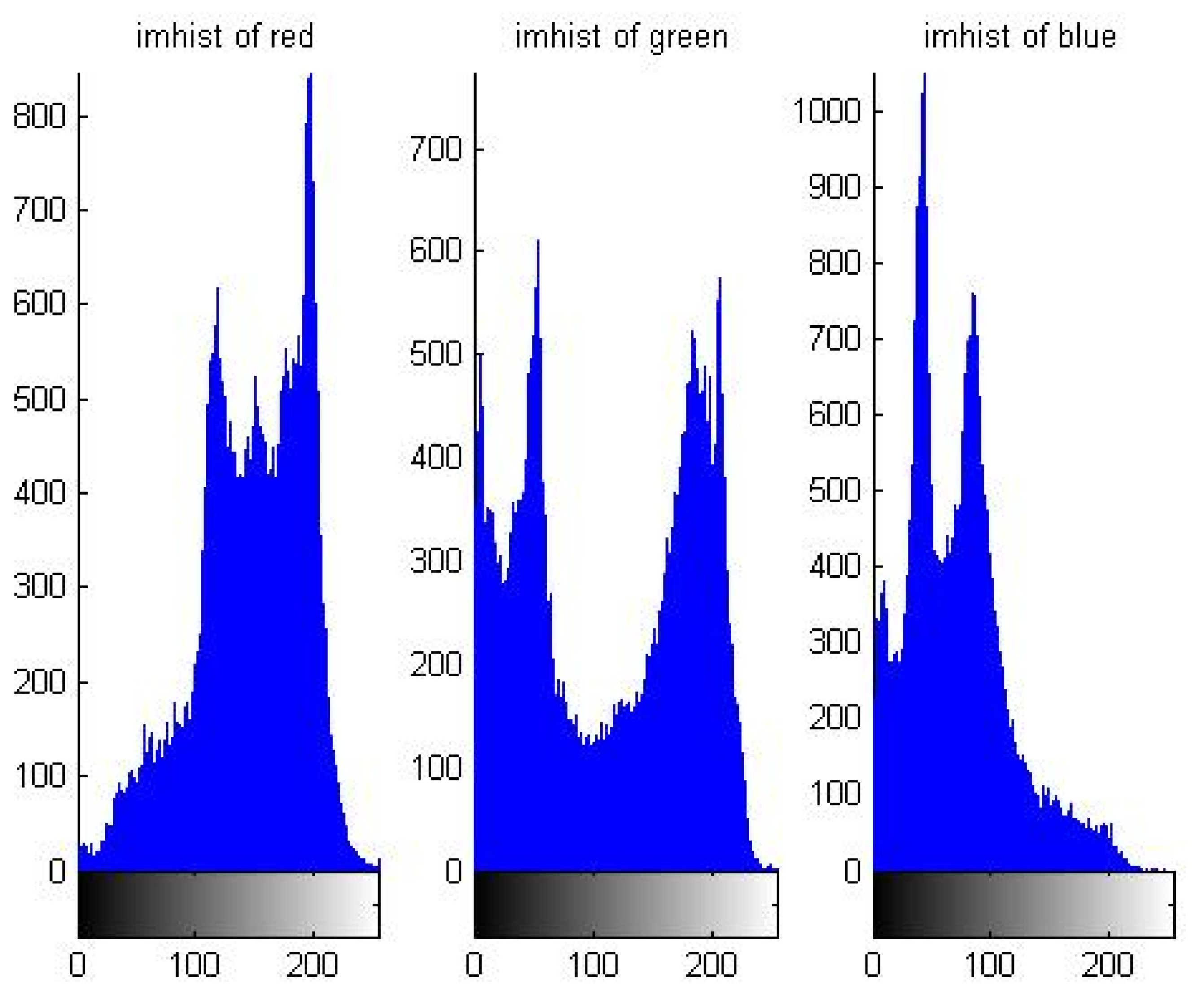
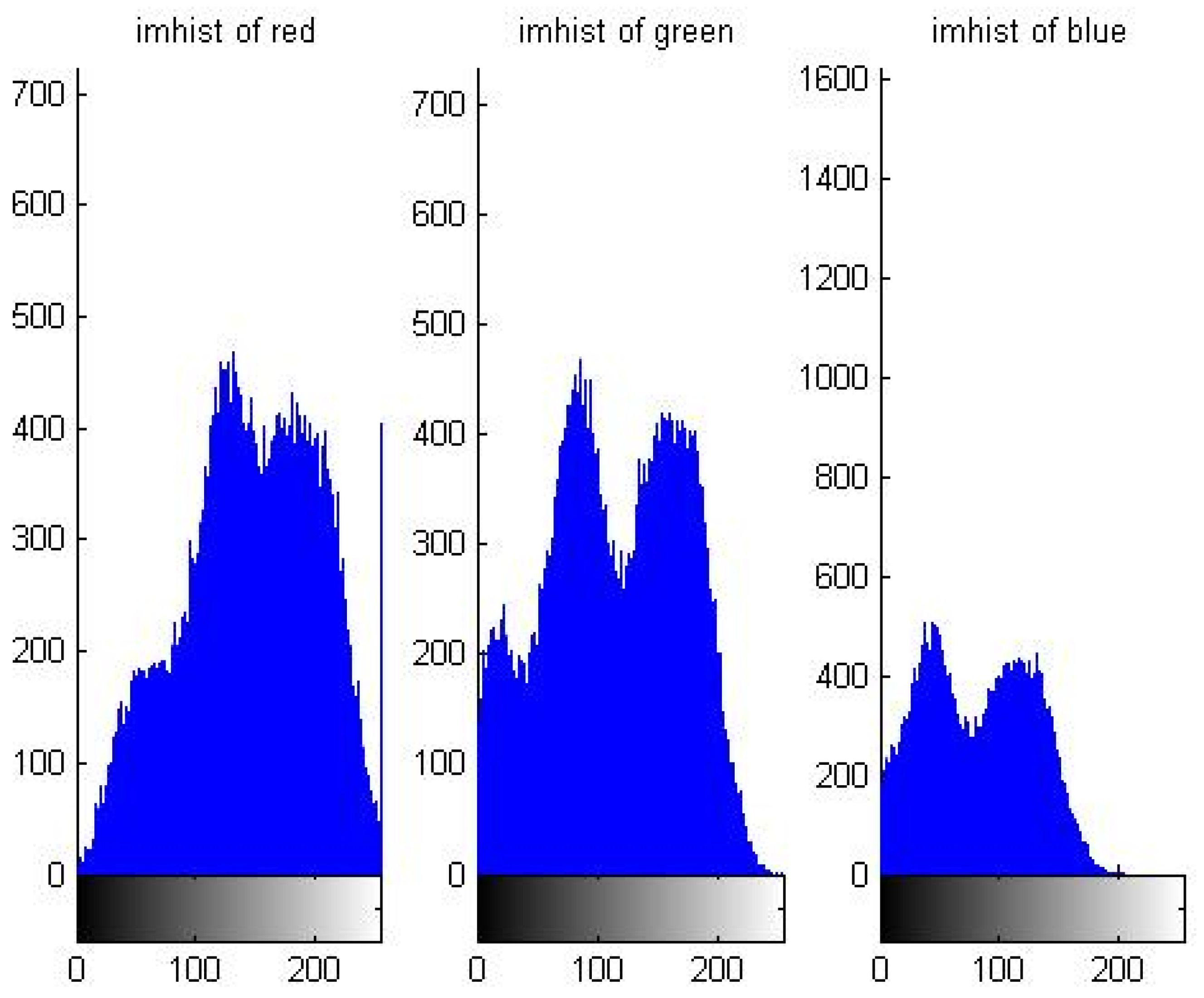
5.1. Distribution Characteristic of Pixel Value
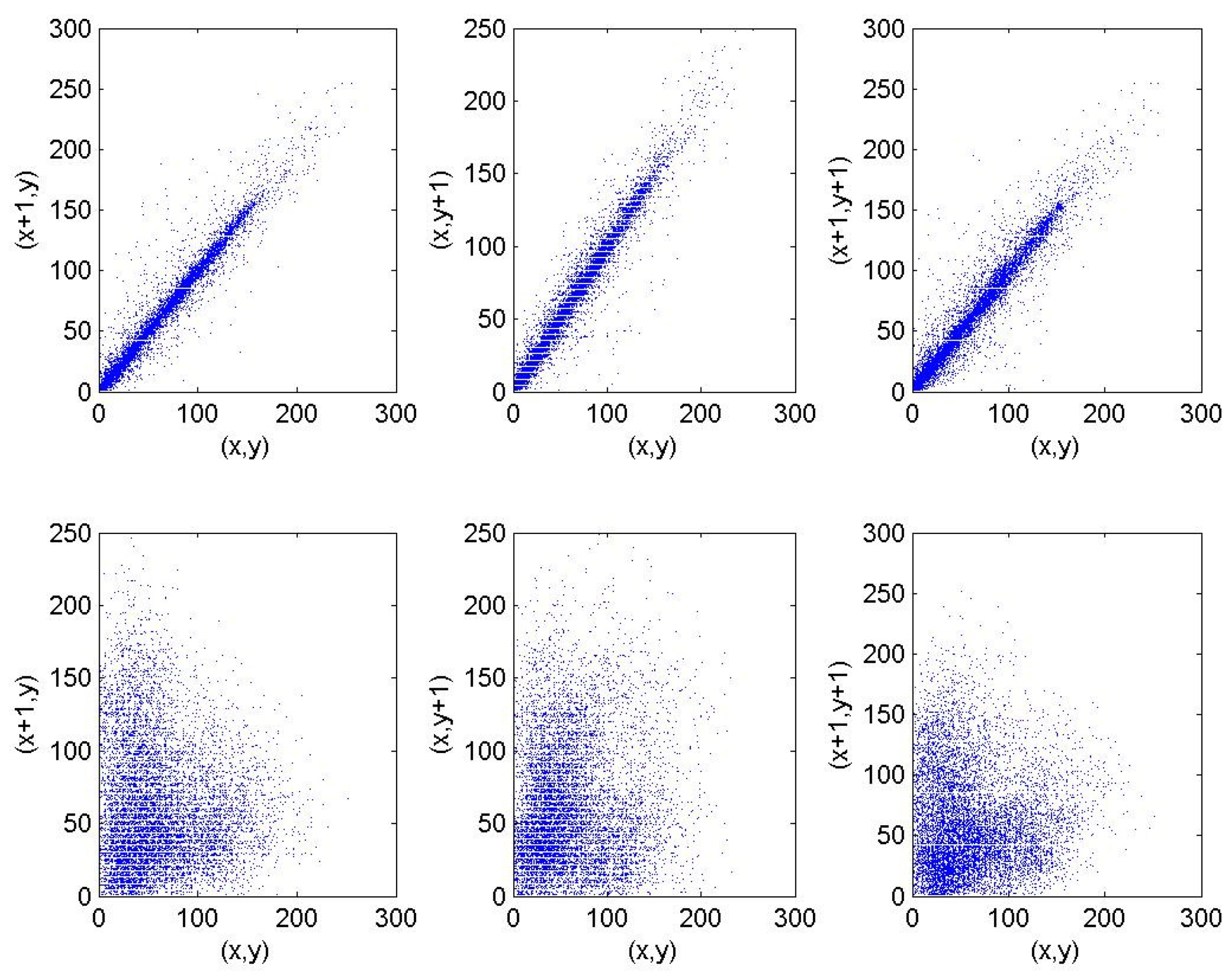
5.2. Correlation Analysis of Each Other Image
5.3. Analysis of the Ability to Resist the Difference Attack
5.4. Information Entropy Analysis
5.5. Abbreviatio of the Relative Comparative Experimental Data
5.6. Detailed Experimental Data
- (a)
- First Group Contrastive Experiment
- (b)
- Second Group Contrastive Experiment
- (c)
- Third Group Contrastive Experiment
- (d)
- Fourth Group Contrastive Experiment
6. Conclusions and Discussion
Author Contributions
Funding
Informed Consent Statement
Conflicts of Interest
References
- Li, X.; Zhou, C.; Xu, N. A secure and efficient image encryption algorithm based on DNA coding and spatiotemporal chaos. Int. J. Netw. Secur. 2018, 20, 110–120. [Google Scholar] [CrossRef]
- Liu, H.; Jin, C. A color image encryption scheme based on arnold scrambling and quantum chaotic. Int. J. Netw. Secur. 2017, 19, 347–357. [Google Scholar]
- Farwa, S.; Shah, T.; Muhammad, N.; Bibi, N.; Jahangir, A.; Arshad, S. An Image Encryption Technique based on Chaotic S-Box and Arnold Transform. Int. J. Adv. Comput. Sci. Appl. 2017, 8, 360–364. [Google Scholar] [CrossRef] [Green Version]
- Jin, X.; Yin, S.; Li, X.; Zhao, G.; Tian, Z.; Sun, N.; Zhu, S. Color image encryption in YCbCr space. In Proceedings of the International Conference on Wireless Communications & Signal, Yangzhou, China, 13–15 October 2016. [Google Scholar] [CrossRef]
- Ni, Z.; Kang, X.; Wang, L. A novel image encryption algorithm based on bit-level improved Arnold transform and hyper chaotic map. In Proceedings of the IEEE International Conference on Signal and Image, Kuching, Malaysia, 17–20 September 2017; pp. 156–160. [Google Scholar] [CrossRef]
- Hu, Y.; Xie, X.; Liu, X.; Zhou, N. Quantum Multi-Image Encryption Based on Iteration Arnold Transform with Parameters and Image Correlation Decomposition. Int. J. Theor. Phys. 2017, 56, 2192–2205. [Google Scholar] [CrossRef]
- Xu, L.; Gou, X.; Li, Z.; Li, J. A novel chaotic image encryption algorithm using block scrambling and dynamic index based diffusion. Opt. Lasers Eng. 2017, 91, 41–52. [Google Scholar] [CrossRef]
- Vaish, A.; Kumar, M. Color image encryption using MSVD, DWT and Arnold transform in fractional Fourier domain. Opt. -Int. J. Light Electron Opt. 2017, 145. [Google Scholar] [CrossRef]
- Chai, X.; Gan, Z.; Chen, Y.; Zhang, Y. A visually secure image encryption scheme based on compressive sensing. Signal Process. 2017, 134, 35–51. [Google Scholar] [CrossRef] [Green Version]
- Song, L.; Yang, F.; Pan, G. Arnold transform and Gray code transformation of the dual scrambling algorithm to study. Comput. Appl. Softw. 2016, 33, 304–307. [Google Scholar]
- Zhang, Z.; Li, Y. Tetrolet transform and SVD combination of blind detection robust digital watermarking embedding strategy. Comput. Eng. Sci. 2017, 39, 492–499. [Google Scholar]
- Xie, G.; Su, B.H. Digital image encryption algorithm based on Arnold hierarchical cyclic transformation. Comput. Eng. Des. 2017, 38, 1200–1204. [Google Scholar]
- Zhang, Y.; Zhang, B. Image encryption algorithm based on Logistic chaotic system. Comput. Appl. Res. 2015, 32, 1770–1773. [Google Scholar]
- Wang, Y.; Zhou, S. Image encryption algorithm based on fractional Chen’s chaotic system. Comput. Appl. 2013, 33, 1043–1046. [Google Scholar] [CrossRef]
- Gong, L.; Ceng, S.; Zhou, N. Color image encryption algorithm based on spectral cutting and two-dimensional Arnold transform. Comput. Appl. 2012, 32, 2599–2602. [Google Scholar] [CrossRef]
- Li, C.; Luo, G.; Li, C. Image encryption scheme based on skew tent chaos map and Arnold transform. Comput. Appl. Res. 2017, 87, 127–133. [Google Scholar] [CrossRef]
- Li, S.; Fang, D.L. A color image watermarking algorithm based on Amold transform. Microelectron. Comput. 2017, 53–57. [Google Scholar]
- Xiao, Z.; Zhang, H.; Chen, H. Zero watermarking for enhanced singular value decomposition and cellular neural network. Chin. J. Image Graph. 2017, 22, 288–296. [Google Scholar] [CrossRef]
- Wu, G.C.; Baleanu, D.; Xie, H.P.; Chen, F.L. Chaos synchronization of fractional chaotic maps based on the stability condition. Phys. A Stat. Mech. Appl. 2016, 460, 374–383. [Google Scholar] [CrossRef]
- Wu, G.C.; Baleanu, D. Discrete chaos in fractional delayed logistic maps. Nonlinear Dyn. 2015, 80, 1697–1703. [Google Scholar] [CrossRef]
- Abdeljawad, T.; Banerjee, S.; Wu, G.C. Discrete tempered fractional calculus for new chaotic systems with short memory and image encryption. Optik 2020, 203, 163698. [Google Scholar] [CrossRef]
- Wu, G.C.; Deng, Z.G.; Baleanu, D.; Zeng, D.Q. New variable-order fractional chaotic systems for fast image encryption. Chaos 2019, 29, 083103. [Google Scholar] [CrossRef]
- Saeed, S.T.; Riaz, M.B.; Awrejcewicz, J.; Ahmad, H. Exact Symmetric Solutions of MHD Casson Fluid Using Chemically Reactive Flow with Generalized Boundary Conditions. Energies 2021, 14, 6243. [Google Scholar] [CrossRef]
- Aneja, M.; Sharma, S. Numerical study of bioconvection flow of nanofluids using non-Fourier’s heat flux and non-Fick’s mass flux theory. Int. J. Mod. Phys. B 2019, 33, 1950376. [Google Scholar] [CrossRef]
- Saeed, S.T.; Riaz, M.B. A fractional study of generalized Oldroyd-B fluid with ramped conditions via local & non-local kernels. Nonlinear Eng. 2021, 10, 177–186. [Google Scholar] [CrossRef]
- Ur Rehman, A.; Riaz, M.B.; Akgül, A.; Saeed, S.T. Dumitru Baleanu Heat and Mass Transport Impact on MHD Second-Grade Fluid: A Comparative Analysis of Fractional Operators; Wiley: Hoboken, NJ, USA, 2021; Volume 50, p. 6. [Google Scholar] [CrossRef]
- Abdeljawad, T.; Riaz, M.B.; Saeed, S.T.; Iftikhar, N.I. MHD Maxwell Fluid with Heat Transfer Analysis under Ramp Velocity and Ramp Temperature Subject to Non-Integer Differentiable Operators. Comput. Model. Eng. Sci. 2021, 126, 821–841. [Google Scholar] [CrossRef]

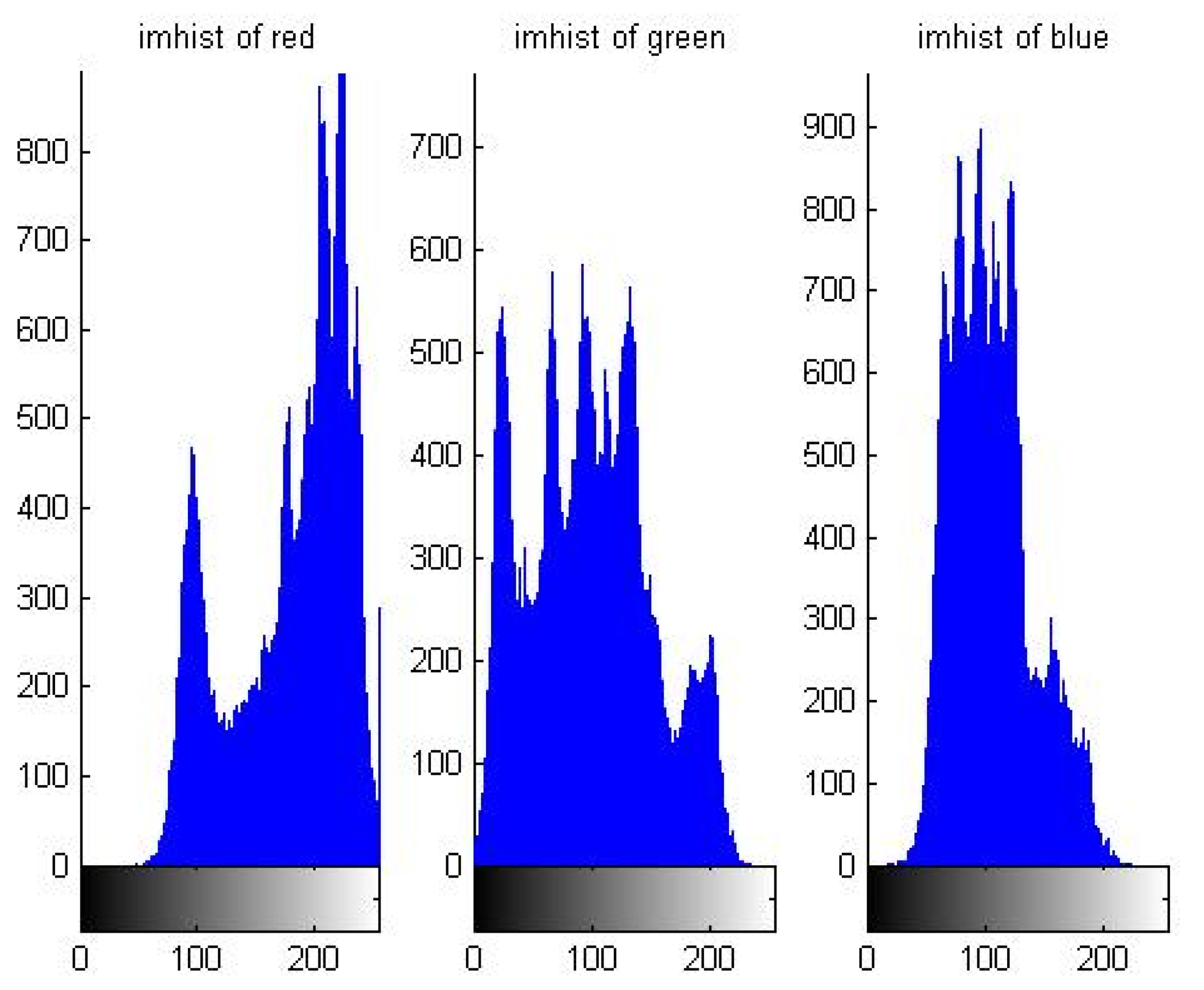
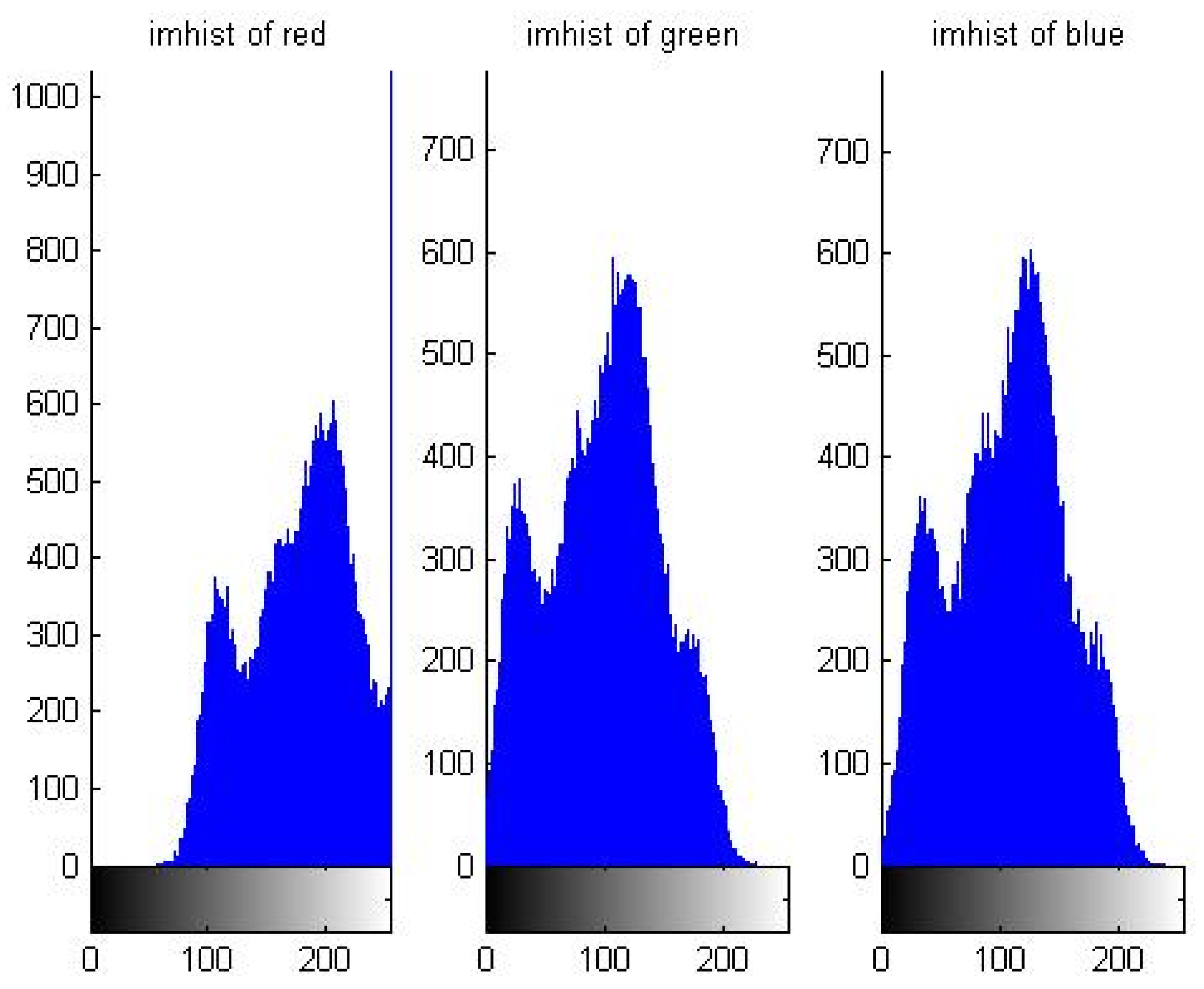
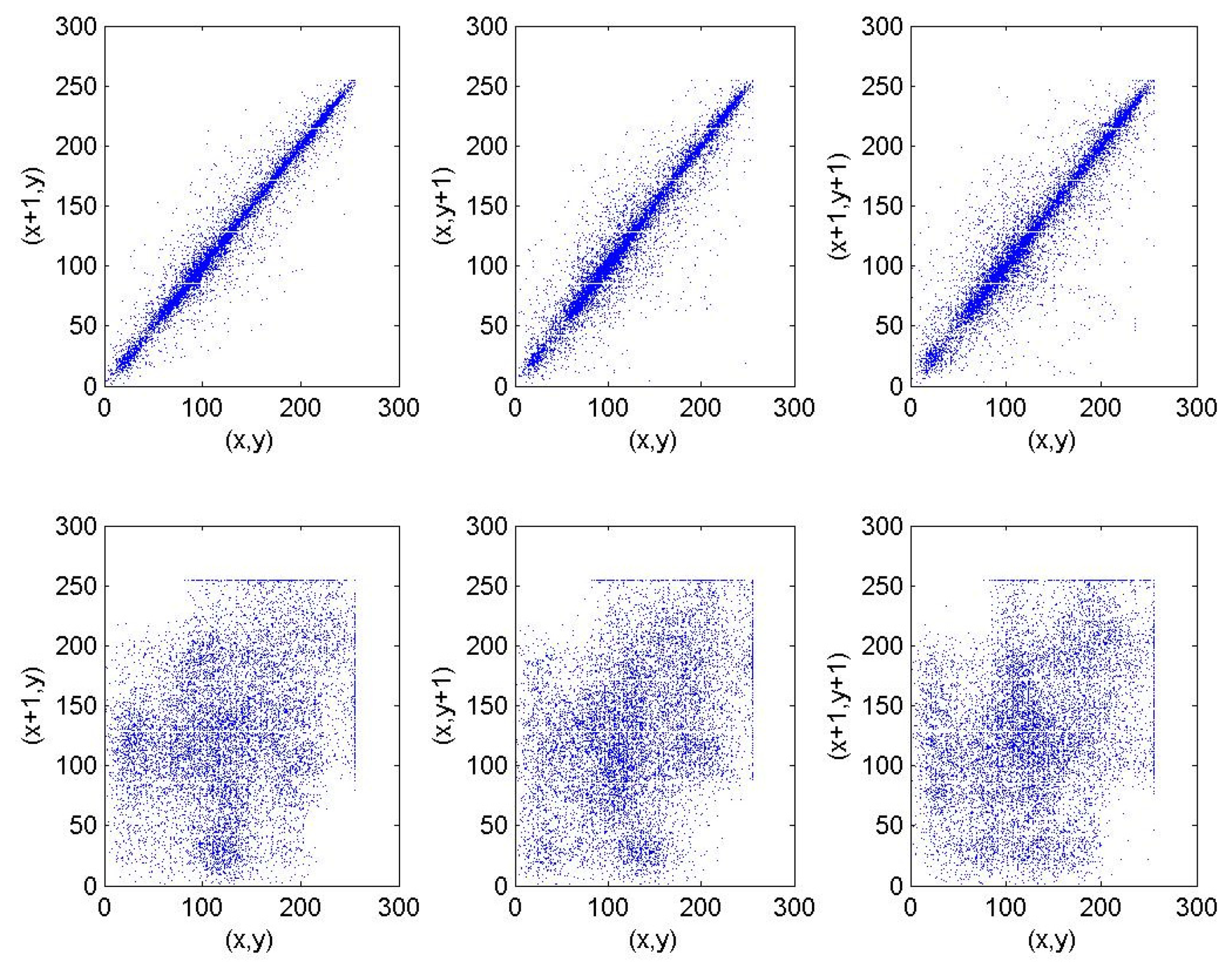

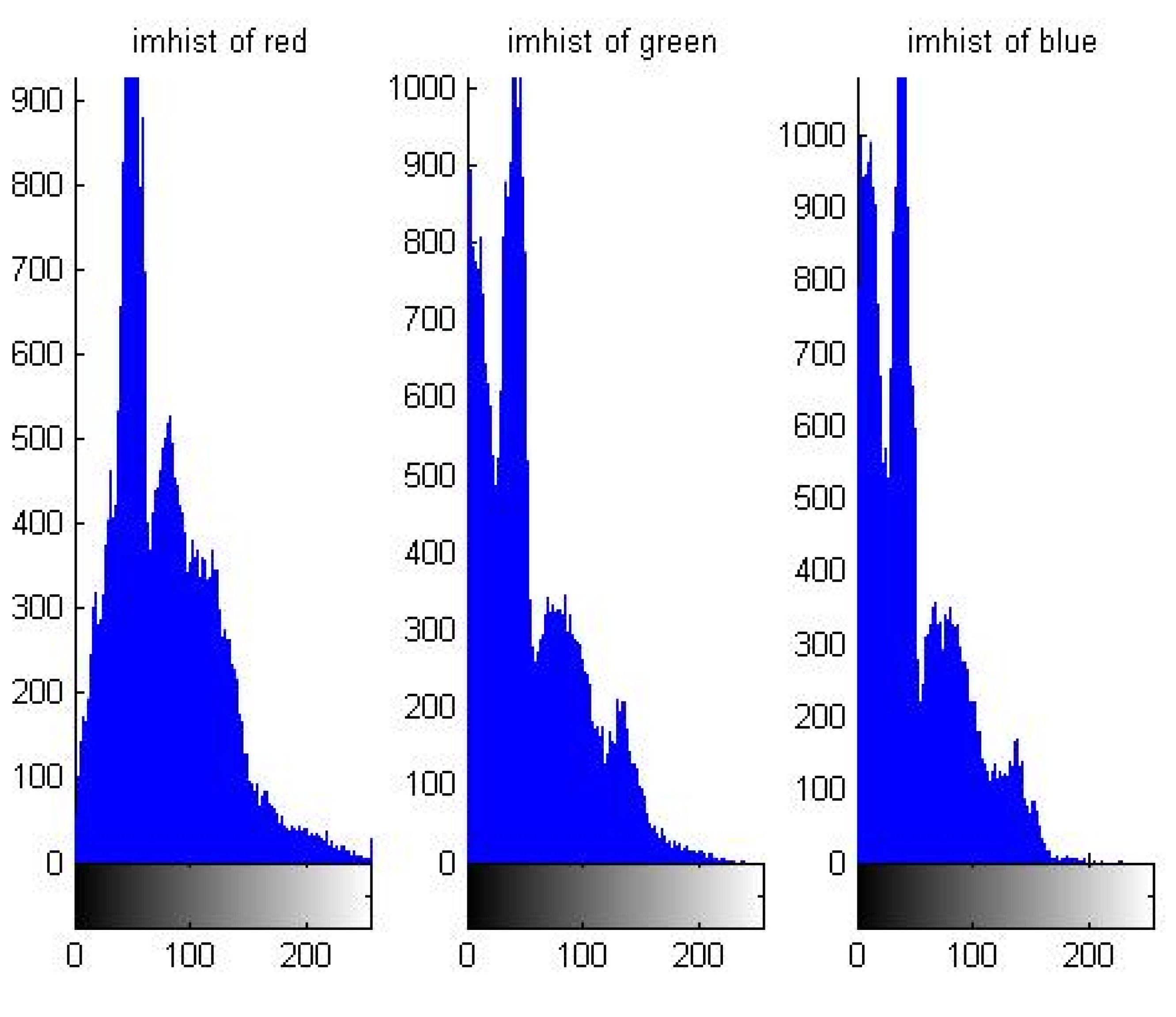

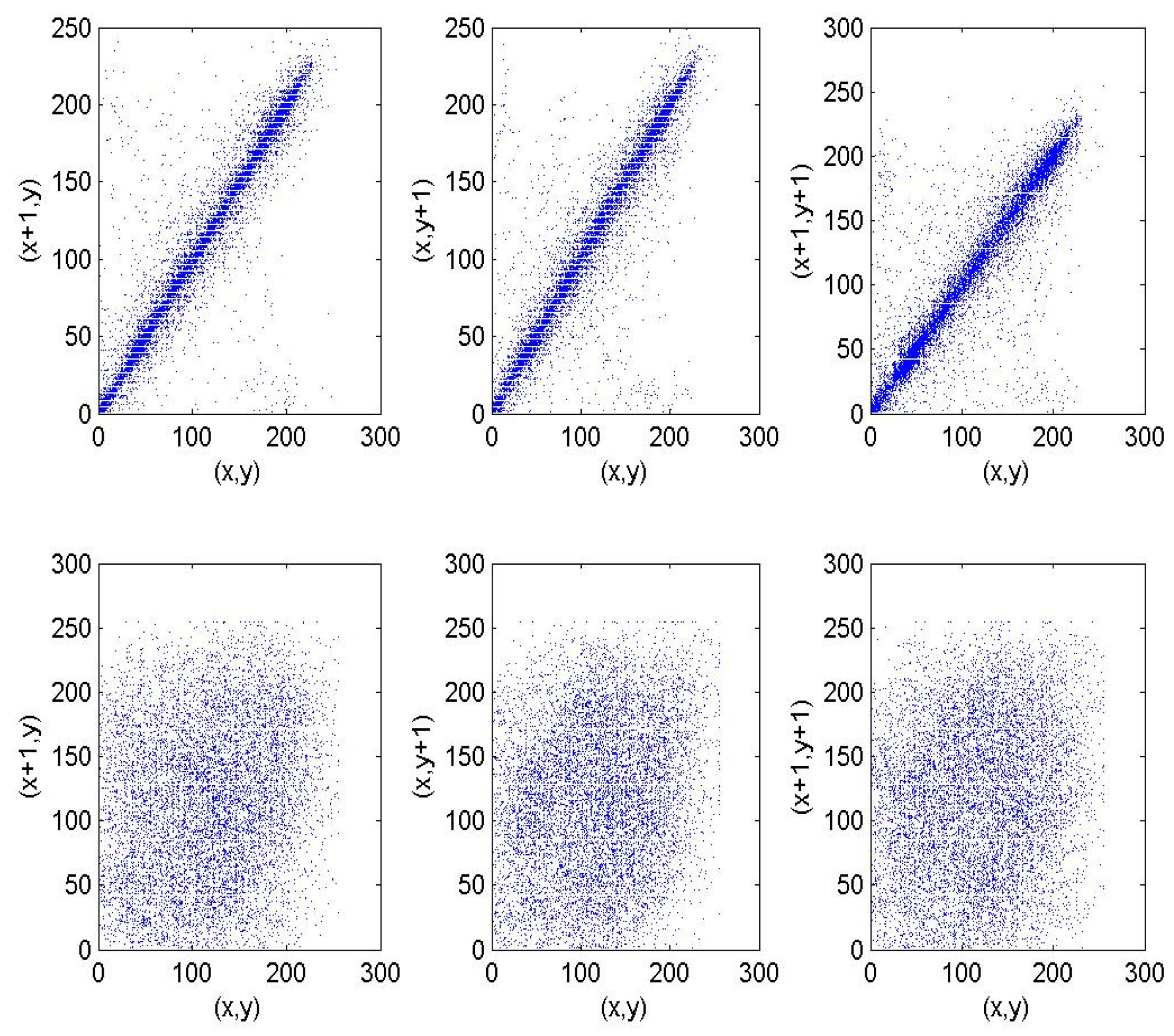

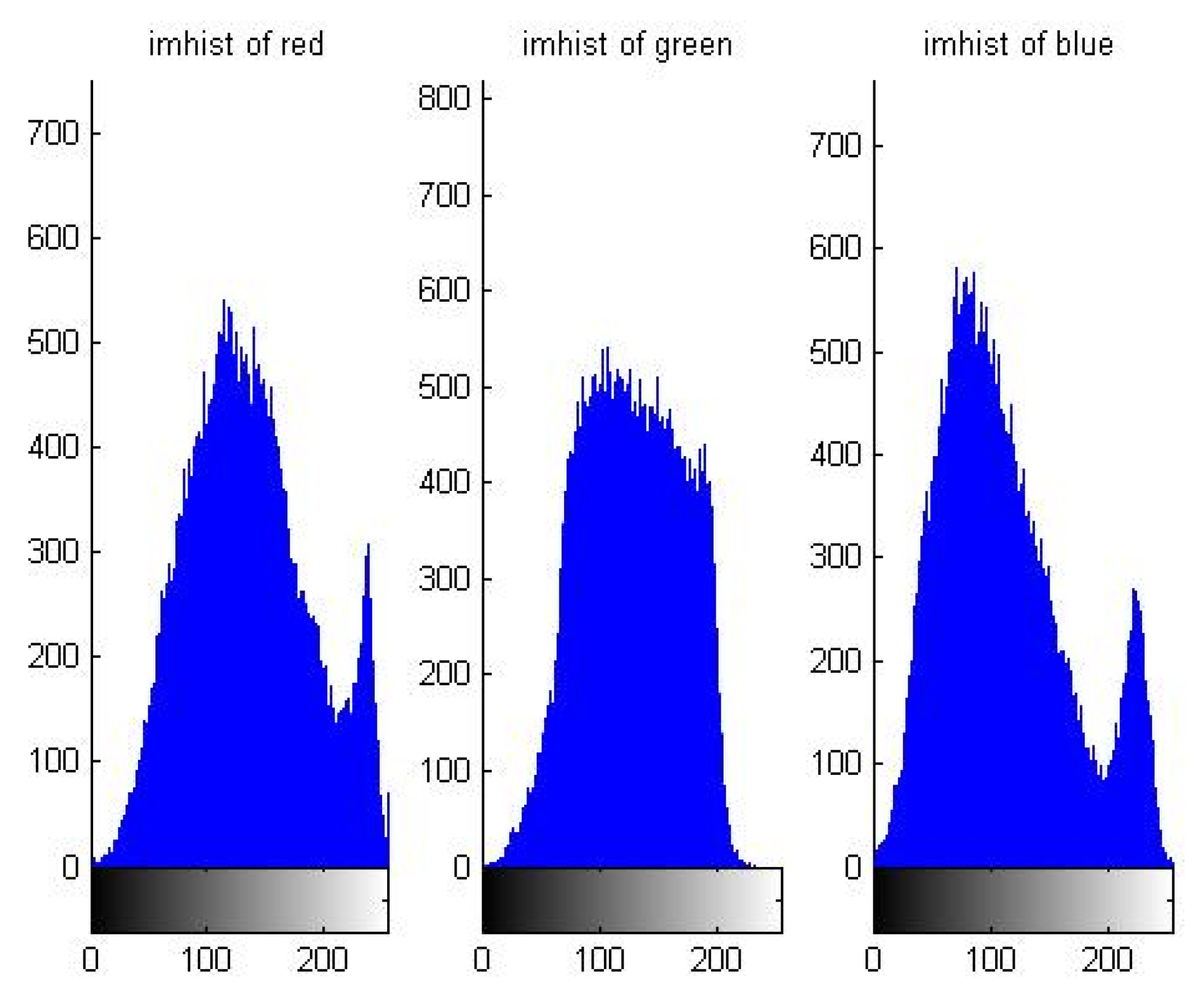

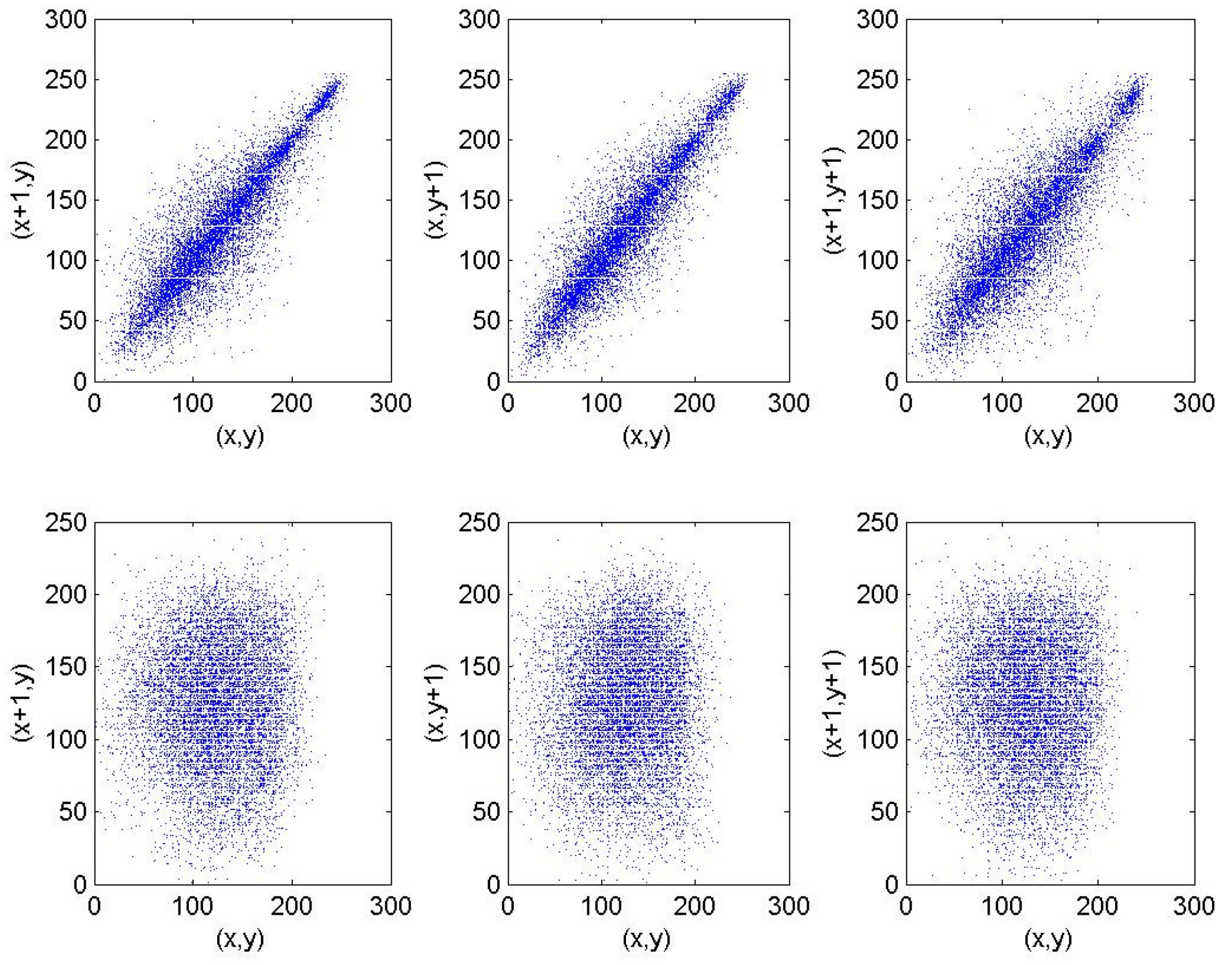
| Order | Period | Order | Period |
|---|---|---|---|
| 4 | 3 | 64 | 48 |
| 8 | 6 | 128 | 96 |
| 16 | 12 | 256 | 62 |
| 32 | 24 | 512 | 384 |
| Hm1 | Hm2 | NPCR | UACI | |
|---|---|---|---|---|
| Lena | 7.7580 | 7.7816 | 0.1723 | 0.0725 |
| Hm1 | Hm2 | NPCR | UACI | |
|---|---|---|---|---|
| girl | 7.0467 | 6.9732 | 0.1638 | 0.0586 |
| Hm1 | Hm2 | NPCR | UACI | |
|---|---|---|---|---|
| peppers | 7.5743 | 7.4929 | 0.1661 | 0.0757 |
| Hm1 | Hm2 | NPCR | UACI | |
|---|---|---|---|---|
| baboon | 7.6701 | 7.39777 | 0.1602 | 0.0682 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chen, C.; Zhang, H.; Wu, B. Image Encryption Based on Arnod Transform and Fractional Chaotic. Symmetry 2022, 14, 174. https://doi.org/10.3390/sym14010174
Chen C, Zhang H, Wu B. Image Encryption Based on Arnod Transform and Fractional Chaotic. Symmetry. 2022; 14(1):174. https://doi.org/10.3390/sym14010174
Chicago/Turabian StyleChen, Chao, Hongying Zhang, and Bin Wu. 2022. "Image Encryption Based on Arnod Transform and Fractional Chaotic" Symmetry 14, no. 1: 174. https://doi.org/10.3390/sym14010174
APA StyleChen, C., Zhang, H., & Wu, B. (2022). Image Encryption Based on Arnod Transform and Fractional Chaotic. Symmetry, 14(1), 174. https://doi.org/10.3390/sym14010174





