Trusting Testcases Using Blockchain-Based Repository Approach
Abstract
:1. Introduction
2. Related Work
2.1. Overview of Blockchain Technology
- All nodes are registered in the MSP.
- A channel is created with a ledger. The ledger is initialized during channel creation.
- A policy is created with defined endorsement criteria.
- A chaincode is deployed in the ledger.
- Entity submits a transaction proposal to all required endorsers as specified in the endorsement policy. A transaction is created when an entity invokes a function in chaincode, which could be a read function or update function.
- The proposal is validated by endorsers, and the chaincode is executed and ledger data are returned as a proposal response.
- The transaction proposal, response, and ledger data are sent to the orderer as a transaction.
- A block is created by the orderer using the transaction and the block is returned to the endorsers.
- Endorsers update the state of the ledger and add the block after validation.
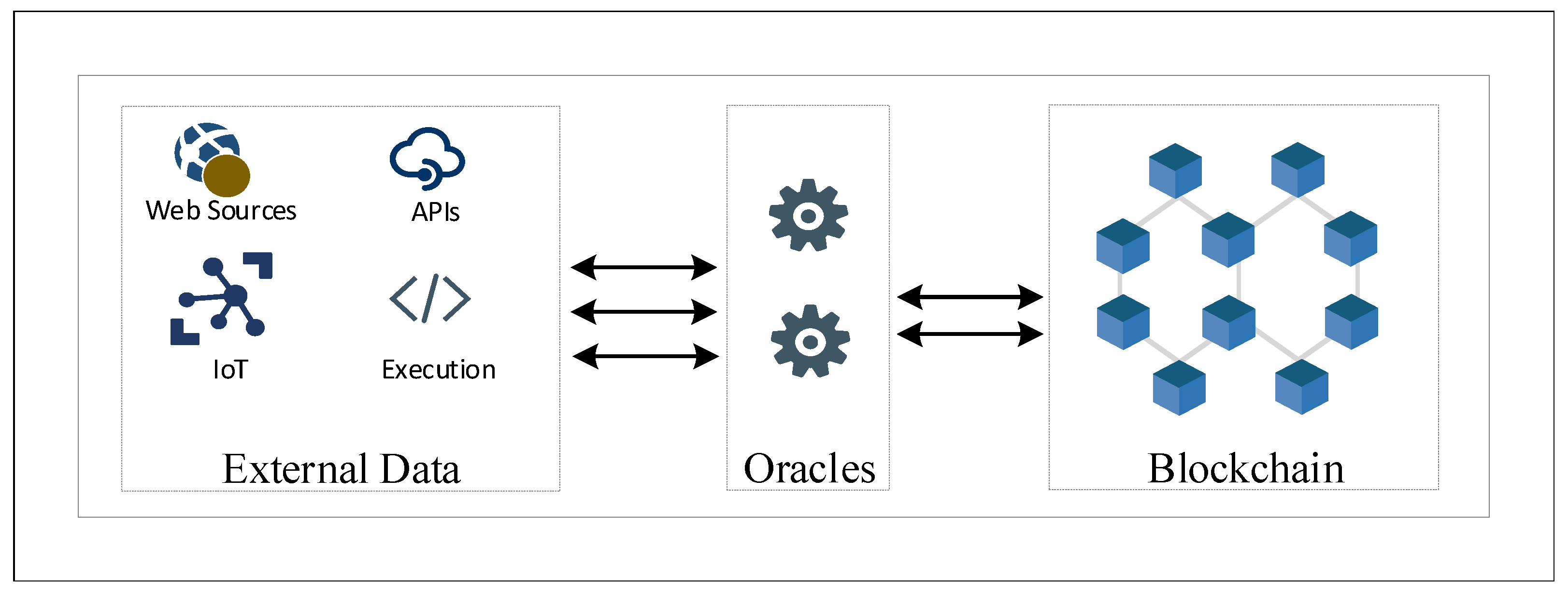
2.2. Overview of Oracles
2.3. Overview of Ipfs
2.4. Overview of Trust
- Certification Authority: an entity trusted by one or more users to create and assign certificates.
- Certification: Procedure by which a third party gives written assurance that a product, process, or service conforms to a specified requirement.
2.5. Overview of Software Testing and Certifications
- Unit Testing: tests specific components or code blocks.
- Integration Testing: tests integration of different subsystems or software components.
- Acceptance Testing: tests the entire software product to ensure conformance with end-user requirements.
- Functionality Testing: to ensure that the functions meet the intended software requirements.
- Performance Testing: to ensure the system stability and robustness under a specific workload.
- Regression Testing: to ensure that update in specific component did not introduce new issues in unchanged software components.
- Security Testing: to ensure that security mechanisms are implemented to protect sensitive data and aims to uncover vulnerabilities that may be exploited.
2.5.1. Common Criteria
- Biometric Verification Mechanisms
- Base Protection Profile for Database Management Systems
- PP for the Gateway of a Smart Metering System
- Application VPN client/Client VPN Application, Version 1.0
2.5.2. The Trusted Computer System Evaluation Criteria
2.5.3. Society of American Engineers Cyber Security Guidebook for Cyber-Physical Vehicle Systems
2.5.4. Linux Test Project
- Kernel: contains test programs related to kernel, such as filesystems, io, ipc, and system calls.
- Network: contains test programs related to network, such as ipv6, multicast, rpc, and sctp.
- Commands: contains user-level commands, such as ar, ld, ldd, and nm used in application development.
- Misc: Miscellaneous tests that do not fall under the categories mentioned above, such as crash and floating-point math set of tests.
- Self-contained: a testcase can be executed independently.
- Testcase outcome: a pass or fail outcome of testcase execution must be detected within the testcase itself.
- Return value: the return value should indicate the result of testcase execution. The value 0 is returned when testcase execution is successful.
2.6. Repository-Based Blockchain Approaches
2.7. Analysis of Security Testing
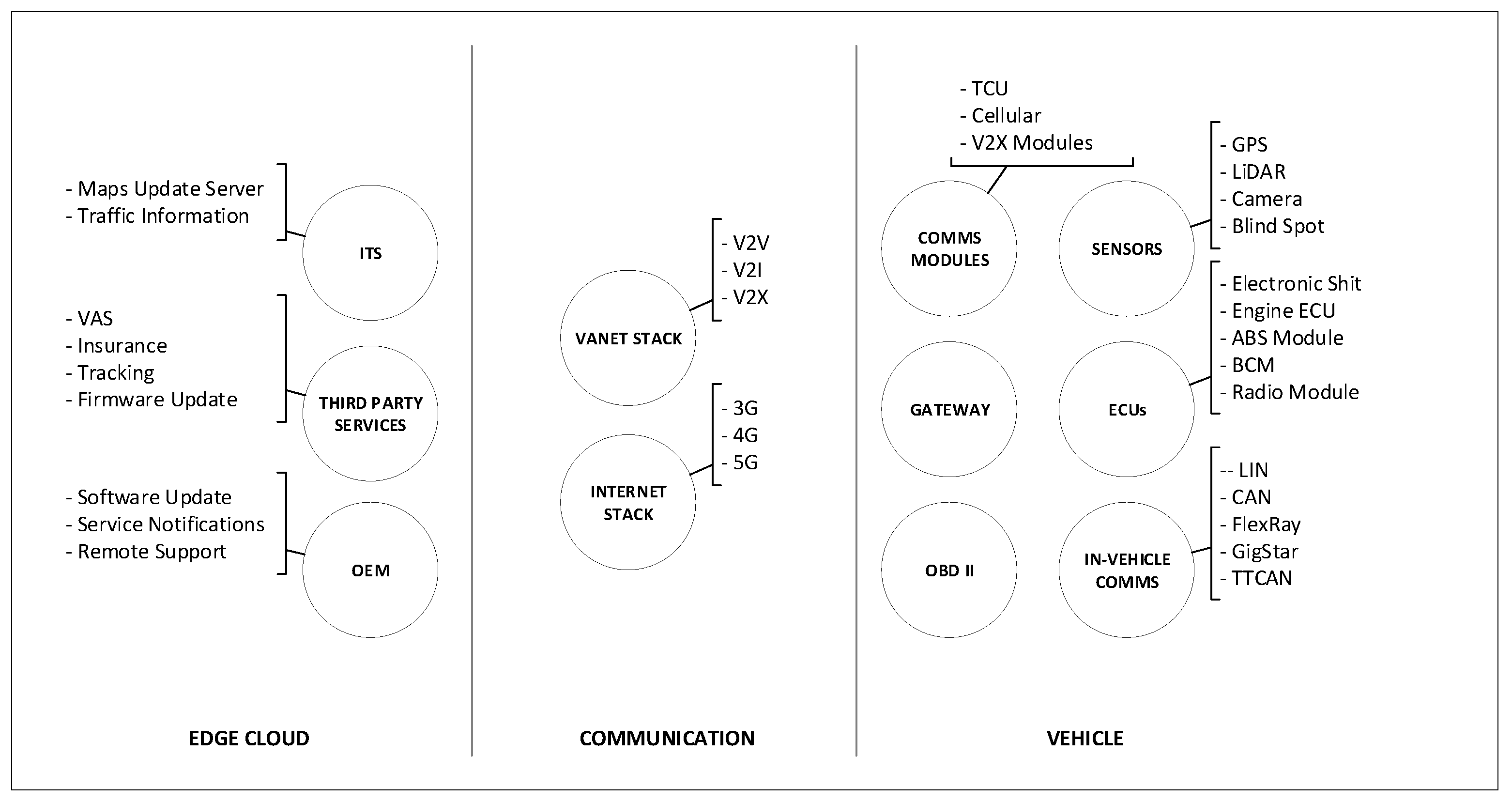
3. Enhanced Autonomous Vehicle Conceptual Model
3.1. Vehicle
3.2. Communication
3.3. Edge Cloud
- Traffic information
- Smart city integration
- Maps update service.
- OEM firmware update.
- Third-party dongles firmware update.
- Value Added Services.
4. Blockchain-Based Trusted Testcase Repository
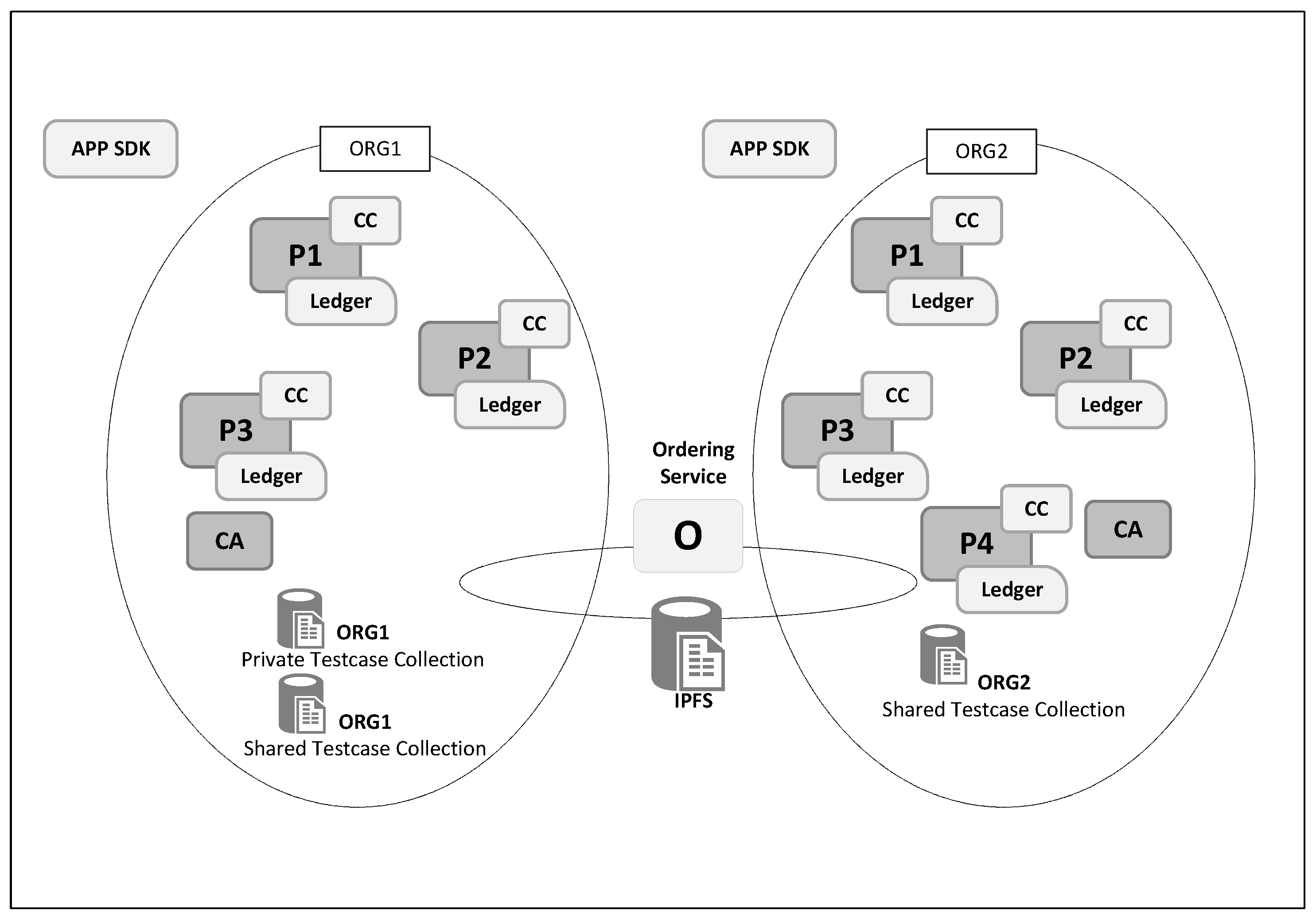
4.1. Overview of Proposed Approach
4.2. Technology and Architecture
4.2.1. Blockchain Technology
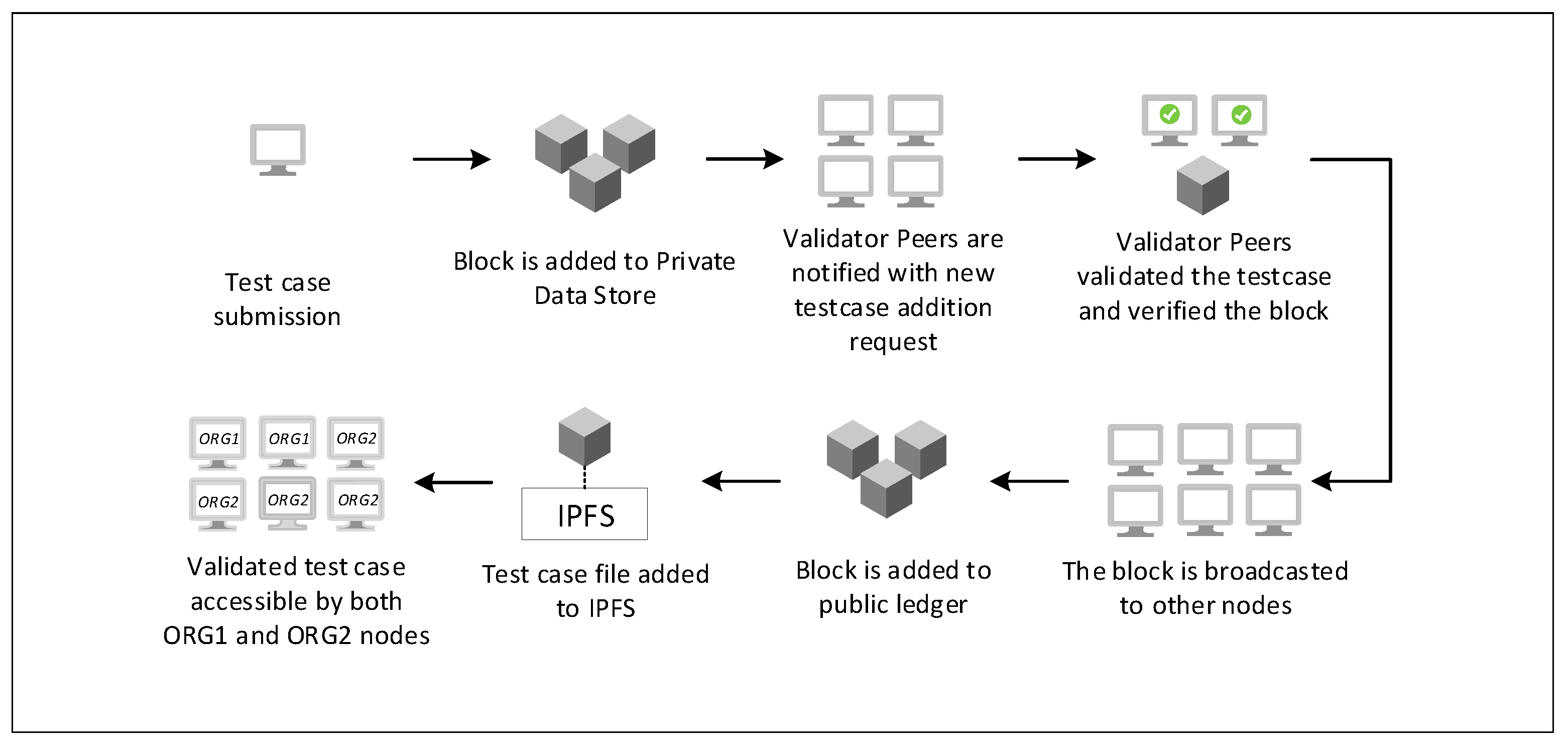
4.2.2. Validation Mechanism
4.3. Solution Design
- Testcase Registration: Using the system, developers can submit new testcases or make bug fixes in existing testcases.
- Testcase Verification: Verifies acceptance or rejection of new testcase submission or updates existing testcase.
- Testcase Query: Developers and testers can query the system for testcases, using defined parameters or categories of testing.
- Repository Manager: responsible for registration and categorization of new testcases.
- Test Manager: responsible for searching and filtering based on defined parameters to allow users to select a set of testcases applicable for the target system undergoing testing.
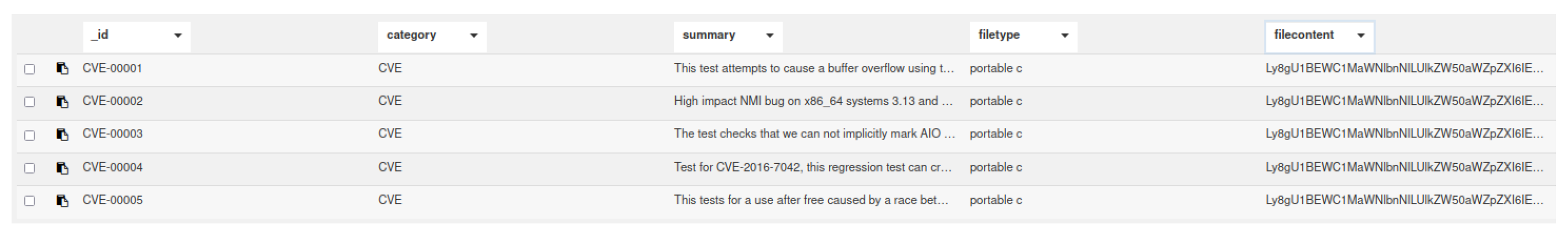
- Data Storage: testcases are stored using distributed data storage, named IPFS [9].
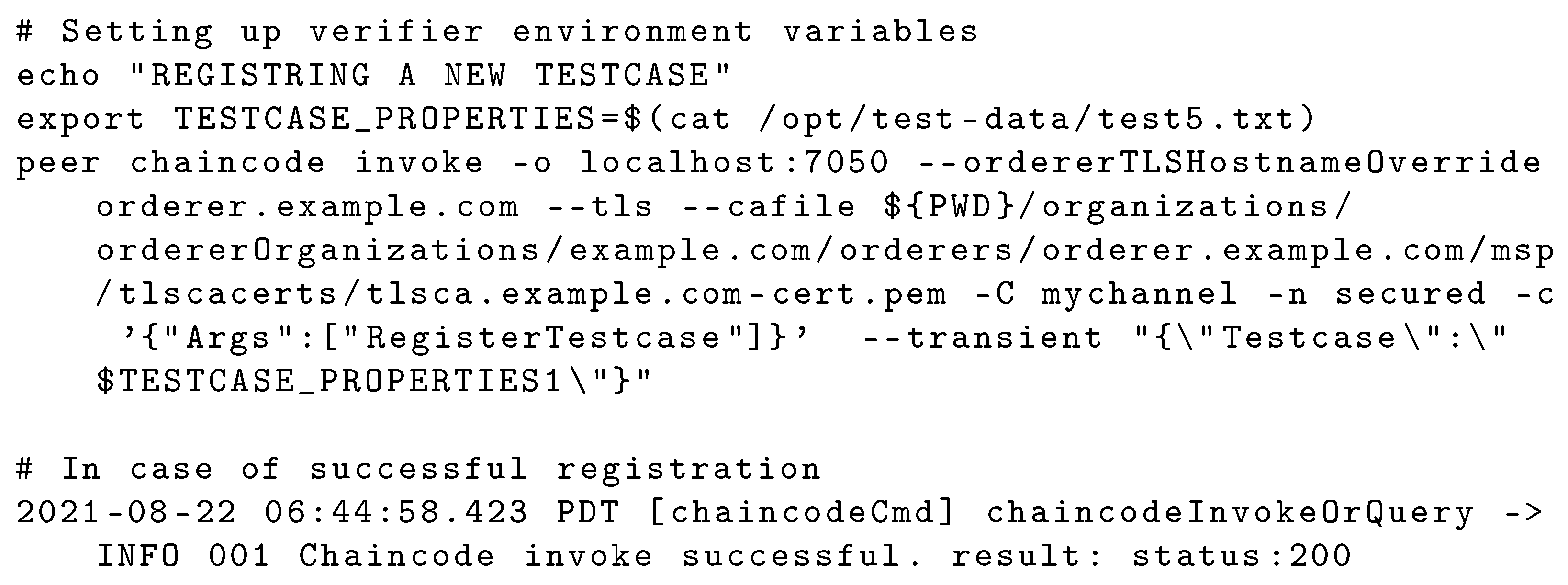
4.3.1. Testcase Registration
4.3.2. Testcase Validation
4.3.3. Query and Filter
4.3.4. Testcase Manager
4.3.5. Repository Manager
4.3.6. Distributed Data Storage
4.4. Implementation Analysis
5. Conclusions and Future Work
Author Contributions
Funding
Conflicts of Interest
Abbreviations
| CAN | Controller area network |
| CC | Common criteria |
| CVE | Common vulnerabilities and exposures |
| DSRC | Dedicated short range communication |
| ECU | Electronic control unit |
| IPFS | InterPlanetary File System |
| LIN | Local interconnect network |
| LTP | Linux Test Project |
| MSP | Membership service provider |
| OBD | On-board diagnostic port |
| OEMs | Original equipment manufacturers |
| POV | Proof-of-Validation |
| PP | Protection profile |
| SAE | Society of American Engineers |
| SLA | Service level agreement |
| TCSEC | Trusted Computer System Evaluation Criteria |
| TOE | Target of evaluation |
| VANET | Vehicular ad-hoc network |
References
- Anisetti, M.; Ardagna, C.; Damiani, E.; Polegri, G. Test-based security certification of composite services. ACM Trans. Web (TWEB) 2018, 13, 1–43. [Google Scholar]
- Chen, W.; Xu, Z.; Shi, S.; Zhao, Y.; Zhao, J. A survey of blockchain applications in different domains. In Proceedings of the 2018 International Conference on Blockchain Technology and Application, Xi’an, China, 10–12 December 2018; pp. 17–21. [Google Scholar]
- Choi, M.K.; Yeun, C.Y.; Seong, P.H. A Novel Monitoring System for the Data Integrity of Reactor Protection System Using Blockchain Technology. IEEE Access 2020, 8, 118732–118740. [Google Scholar] [CrossRef]
- Nakamoto, S.; Bitcoin, A. A Peer-to-Peer Electronic Cash System. 2008, Volume 4. Available online: https://www.debr.io/article/21260.pdf (accessed on 27 September 2021).
- Bellini, E.; Iraqi, Y.; Damiani, E. Blockchain-based distributed trust and reputation management systems: A survey. IEEE Access 2020, 8, 21127–21151. [Google Scholar] [CrossRef]
- Beniiche, A. A study of blockchain oracles. arXiv 2020, arXiv:2004.07140. [Google Scholar]
- Al-Breiki, H.; Rehman, M.H.U.; Salah, K.; Svetinovic, D. Trustworthy blockchain oracles: Review, comparison, and open research challenges. IEEE Access 2020, 8, 85675–85685. [Google Scholar] [CrossRef]
- Ellis, S.; Juels, A.; Nazarov, S. Chainlink a decentralized oracle network. Retrieved March 2017, 11, 2018. [Google Scholar]
- Benet, J. Ipfs-content addressed, versioned, p2p file system. arXiv 2014, arXiv:1407.3561. [Google Scholar]
- Chen, Y.; Li, H.; Li, K.; Zhang, J. An improved P2P file system scheme based on IPFS and Blockchain. In Proceedings of the 2017 IEEE International Conference on Big Data (Big Data), Boston, MA, USA, 11–14 December 2017; pp. 2652–2657. [Google Scholar]
- Bulinska-Stangrecka, H.; Bagienska, A. Investigating the links of interpersonal trust in telecommunications companies. Sustainability 2018, 10, 2555. [Google Scholar] [CrossRef] [Green Version]
- Shehada, D.; Yeun, C.Y.; Zemerly, M.J.; Al-Qutayri, M.; Al-Hammadi, Y.; Hu, J. A new adaptive trust and reputation model for mobile agent systems. J. Netw. Comput. Appl. 2018, 124, 33–43. [Google Scholar] [CrossRef]
- Damiani, E.; Ardagna, C.A.; El Ioini, N. Open Source Systems Security Certification; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2008. [Google Scholar]
- Kruger, R.; Eloff, J.H. A common criteria framework for the evaluation of information technology systems security. In Information Security in Research and Business; Springer: Berlin/Heidelberg, Germany, 1997; pp. 197–209. [Google Scholar]
- Qiu, L.; Zhang, Y.; Wang, F.; Kyung, M.; Mahajan, H.R. Trusted Computer System Evaluation Criteria; National Computer Security Center, Citeseer: Dublin, Ireland, 1985. [Google Scholar]
- Schmittner, C.; Ma, Z.; Reyes, C.; Dillinger, O.; Puschner, P. Using SAE J3061 for automotive security requirement engineering. In Proceedings of the International Conference on Computer Safety, Reliability, and Security, Trondheim, Norway, 20–23 September 2016; Springer: Cham, Switzerland, 2016; pp. 157–170. [Google Scholar]
- Road Vehicles—Functional Safety; Standard, International Organization for Standardization: Geneva, Switzerland, 2011.
- Road Vehicles—Cybersecurity Engineering; Standard, International Organization for Standardization: Geneva, Switzerland, 2021.
- Larson, P. Testing Linux with the Linux Test Project. Ottawa Linux Symposium. 2002, p. 265. Available online: https://courses.cs.vt.edu/cs5204/fall05-gback/papers/ols2002_proceedings.pdf#page=265 (accessed on 8 March 2021).
- Nchinda, N.; Cameron, A.; Retzepi, K.; Lippman, A. MedRec: A network for personal information distribution. In Proceedings of the 2019 International Conference on Computing, Networking and Communications (ICNC), Honolulu, HI, USA, 18–21 February 2019; pp. 637–641. [Google Scholar]
- Keller, M. Design and Implementation of a Blockchain-Based Trusted VNF Package Repository. Ph.D. Thesis, University of Zürich, Zürich, Switzerland, 2019. [Google Scholar]
- Scheid, E.J.; Keller, M.; Franco, M.F.; Stiller, B. BUNKER: A Blockchain-based trUsted VNF pacKagE Repository. In Proceedings of the International Conference on the Economics of Grids, Clouds, Systems, and Services, Leeds, UK, 17–19 September 2019; Springer: Cham, Switzerland, 2019; pp. 188–196. [Google Scholar]
- Caldarelli, G.; Ellul, J. Trusted academic transcripts on the blockchain: A systematic literature review. Appl. Sci. 2021, 11, 1842. [Google Scholar] [CrossRef]
- Rasool, S.; Saleem, A.; Iqbal, M.; Dagiuklas, T.; Mumtaz, S.; Qayyum, Z.U. Docschain: Blockchain-Based IoT Solution for Verification of Degree Documents. IEEE Trans. Comput. Soc. Syst. 2020, 7, 827–837. [Google Scholar] [CrossRef]
- Zaabi, A.O.A.; Yeun, C.Y.; Ernesto Damiani, G. An Enhanced Conceptual Security Model for Autonomous Vehicles. Adv. Sci. Technol. Eng. Syst. J. 2020, 5, 853–864. [Google Scholar] [CrossRef]
- Wyglinski, A.M.; Huang, X.; Padir, T.; Lai, L.; Eisenbarth, T.R.; Venkatasubramanian, K. Security of autonomous systems employing embedded computing and sensors. IEEE Micro 2013, 33, 80–86. [Google Scholar] [CrossRef]
- Szydlowski, C.P. Can Specification 2.0: Protocol and Implementations; Technical Report, SAE Technical Paper; SAE: Warrendale, PA, USA, 1992. [Google Scholar]
- Talbot, S.C.; Ren, S. Comparision of fieldbus systems can, ttcan, flexray and lin in passenger vehicles. In Proceedings of the 2009 29th IEEE International Conference on Distributed Computing Systems Workshops, Montreal, QC, Canada, 22–26 June 2009; pp. 26–31. [Google Scholar]
- Wolf, M.; Weimerskirch, A.; Paar, C. Secure in-vehicle communication. In Embedded Security in Cars; Springer: Berlin/Heidelberg, Germany, 2006; pp. 95–109. [Google Scholar]
- Buttyán, L.; Holczer, T.; Vajda, I. On the effectiveness of changing pseudonyms to provide location privacy in VANETs. In European Workshop on Security in Ad-Hoc and Sensor Networks; Springer: Berlin/Heidelberg, Germany, 2007; pp. 129–141. [Google Scholar]
- Raya, M.; Hubaux, J.P. The security of vehicular ad hoc networks. In Proceedings of the 3rd ACM Workshop on Security of Ad Hoc and Sensor Networks, Alexandria, VA, USA, 7 November 2005; pp. 11–21. [Google Scholar]
- Papadimitratos, P.; Buttyan, L.; Holczer, T.; Schoch, E.; Freudiger, J.; Raya, M.; Ma, Z.; Kargl, F.; Kung, A.; Hubaux, J.P. Secure vehicular communication systems: Design and architecture. IEEE Commun. Mag. 2008, 46, 100–109. [Google Scholar] [CrossRef] [Green Version]
- Bariah, L.; Shehada, D.; Salahat, E.; Yeun, C.Y. Recent advances in VANET security: A survey. In Proceedings of the 2015 IEEE 82nd Vehicular Technology Conference (VTC2015-Fall), Boston, MA, USA, 6–9 September 2015; pp. 1–7. [Google Scholar]
- Seo, H.; Lee, K.D.; Yasukawa, S.; Peng, Y.; Sartori, P. LTE evolution for vehicle-to-everything services. IEEE Commun. Mag. 2016, 54, 22–28. [Google Scholar] [CrossRef]
- Sharma, S.; Kaushik, B. A survey on internet of vehicles: Applications, security issues & solutions. Veh. Commun. 2019, 20, 100182. [Google Scholar]
- Vijayarangam, S.; Chandra Babu, G.; Ananda Murugan, S.; Kalpana, N.; Malarvizhi Kumar, P. Enhancing the security and performance of nodes in Internet of Vehicles. Concurr. Comput. Pract. Exp. 2021, 33, 1. [Google Scholar] [CrossRef]
- Almehrezi, F.R.; Yeun, C.Y.; Yoo, P.D.; Damiani, E.; Al Hammadi, Y.; Yeun, H. An Emerging Security Framework for Connected Autonomous Vehicles. In Proceedings of the 2020 7th International Conference on Behavioural and Social Computing (BESC), Bournemouth, UK, 5–7 November 2020; pp. 1–4. [Google Scholar]
- Forecast, C.C. Global connected car market to grow threefold within five years. In GSMA Connected Living Programme: MAutomotive; GSMA: London, UK, 2013. [Google Scholar]
- Lu, N.; Cheng, N.; Zhang, N.; Shen, X.; Mark, J.W. Connected vehicles: Solutions and challenges. IEEE Internet Things J. 2014, 1, 289–299. [Google Scholar] [CrossRef]
- Liu, N. Internet of Vehicles: Your next connection. Huawei WinWin 2011, 11, 23–28. [Google Scholar]
- Kim, K.; Kim, J.S.; Jeong, S.; Park, J.H.; Kim, H.K. Cybersecurity for autonomous vehicles: Review of attacks and defense. Comput. Secur. 2021, 103, 102150. [Google Scholar] [CrossRef]


| Term | Name | Description |
|---|---|---|
| CC | Common Criteria | Common Criteria Methodology for Information Technology Security Evaluation. |
| CEM | Common Evaluation Methodology | Common Evaluation Methodology for Information Technology Security Evaluation. |
| PP | Protection Profile | An implementation-independent set of security requirements for a category of products. |
| ST | Security Target | A set of implementation-dependent security requirements for a specific product. |
| TOE | Target of Evaluation | The product under evaluation. |
| TFS | TOE Security Functionality | The security functionality of the product under evaluation. |
| TSS | TOE Summary Specification | A description of how a TOE satisfies security functional requirements in the product under evaluation. |
| SFR | Security Functional Requirement | A requirement for security enforcement by the TOE. |
| SAR | Security Assurance Requirement | A requirement to assure the security of the TOE |
| D Minimal Protection | C Discretionary Protection |
| Software systems that have been evaluated and failed to meet the requirements of other categories | C1 Discretionary Security Protection C2 Controlled Access Protection |
| B Mandatory Protection | A Verified Protection |
| B1 Labeled Security Protection B2 Structured Protection B3 Security Domains | A1 Verified Design-Beyond A1 |
| Guide | Description |
|---|---|
| SAE J3061-1 | Automotive Cybersecurity Integrity Level |
| SAE J3061-2 | Security Testing Methods |
| SAE J3061-3 | Security Testing Tools |
| SAE J3101 | Requirements for Hardware-Protected Security for Ground Vehicle Applications |
| SAE J3138 | Guidance for Securing the Data Link Connector (DLC) |
| TTYPE | Description |
| TPASS | Test has passed |
| TFAIL | Test has failed |
| TINFO | General information message |
| TWARN | Warning message, which does not stop test execution |
| TBROK | Test broken message, which indicates failure in test preparation phase. |
| TCONF | Incompatible current configuration, such as syscall not implemented or unsupported architecture type |
| Attribute | Description | Example |
|---|---|---|
| Testcase ID | Identified of testcase | 35md..9sdj |
| Testcase Version | Testcase version | 1.0.3 |
| Summary | Testcase summary | […] |
| Testcase Category | Testcase category | Kernel |
| Verification Status | Testcase verification status | Unverified, Verified |
| Verifiers | Verifiers public keys | key1, key2, key3 |
| File Hash | Testcase file hash | Fgsg,,,,,asdert3 |
| File type | Testcase file type | Portable Shell or C |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al Zaabi, A.; Yeun, C.Y.; Damiani, E. Trusting Testcases Using Blockchain-Based Repository Approach. Symmetry 2021, 13, 2024. https://doi.org/10.3390/sym13112024
Al Zaabi A, Yeun CY, Damiani E. Trusting Testcases Using Blockchain-Based Repository Approach. Symmetry. 2021; 13(11):2024. https://doi.org/10.3390/sym13112024
Chicago/Turabian StyleAl Zaabi, Abdulla, Chan Yeob Yeun, and Ernesto Damiani. 2021. "Trusting Testcases Using Blockchain-Based Repository Approach" Symmetry 13, no. 11: 2024. https://doi.org/10.3390/sym13112024
APA StyleAl Zaabi, A., Yeun, C. Y., & Damiani, E. (2021). Trusting Testcases Using Blockchain-Based Repository Approach. Symmetry, 13(11), 2024. https://doi.org/10.3390/sym13112024







