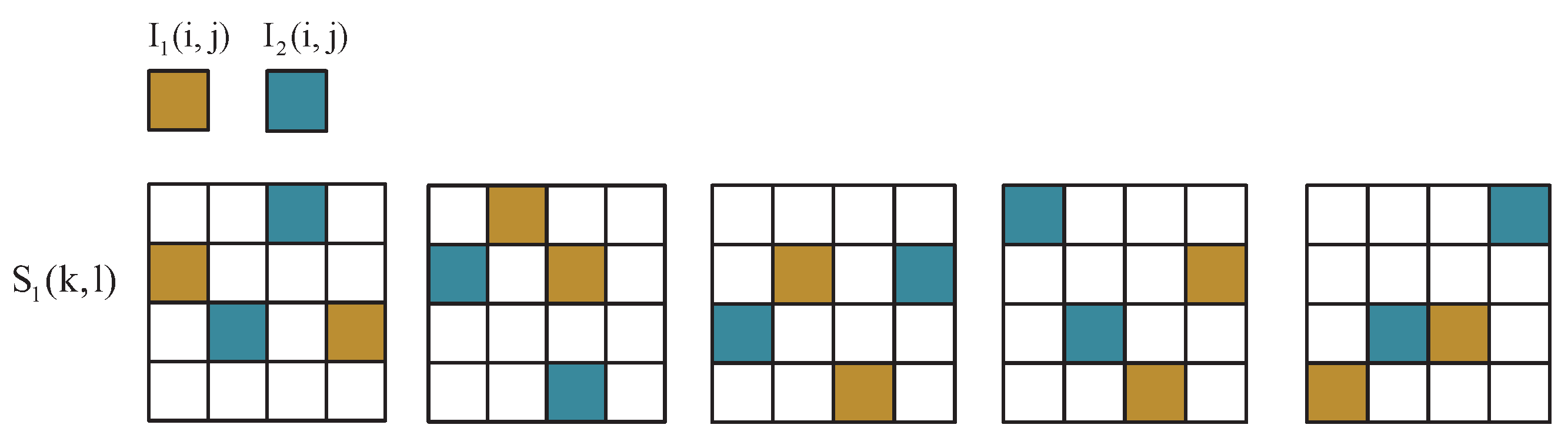1. Introduction
In today’s world, information is a popular application resource and an essential carrier of communication in our lives. The rapid development of science and technology has driven the continuous advancement of information technology, and more people have begun to pay attention to the importance of information. At the same time, more and more people have put forward more security requirements for the protection of their privacy [
1,
2,
3]. Visual cryptography (VC) is an important branch of information security and has been further developed in the field of secret sharing. It can not only ensure the security of people’s privacy but also has a simple decoding operation and numerous potential applications. Therefore, visual cryptography technology has become a hot research direction since its proposal in 1994.
Naor and Shamir designed the first visual cryptography algorithm in 1994 [
4]. The basic idea is to replace each pixel in an image with a block of pixels. The pixel information in the pixel block is filled with the superposition between pixels, and finally, an encrypted image cannot be recognized by the human eye [
4,
5,
6,
7,
8,
9,
10,
11,
12,
13]. For a
-threshold scheme, The information transmitting end encrypts the secret image into
k share images and transmits them to the receiving end. After receiving the
k share images, The receiving end superimposes and restores the secret image. The recovered secret image is displayed in black and white by the synthesized pixels. If the receiving end receives less than
k share images, The secret image cannot be recovered. Therefore, The visual cryptography scheme has sufficient security and feasibility. However, if a secret image is encrypted by this scheme, The pixels are expanded to
m pixels, in order to generate
k noise-like share images. The size of the recovered secret image is
m times of the size of the original image. Each of the black pixels and the white pixels is composed of a certain number of sub-pixels, i.e., a mixture of black and white. So, The visual quality of the recovered secret image is not ideal. Therefore, more visual cryptography algorithms tried to improve the image quality of the stacked image [
14,
15].
There is a trade-off between the quality of the recovered secret image and the size expansion. Ordinary visual cryptography divides the secret image pixels into blocks and embeds the secret pixel information with the basic matrix. Since each secret pixel can be rendered by a block of pixels in a recovered image, ordinary visual cryptography has better visual quality. However, The recovered secret image is larger than the original secret image [
5]. In 2002, Nakajima and Yamaguchi proposed extended visual cryptography for natural images [
16]. This scheme can produce a meaningful share of images. The use of halftone technology and contrast-enhancing methods improves the quality of recovering secret images. In 2011, Liu and Wu proposed a scheme that combined extended VC with digital halftoning. Embedding a cover image into a share image improves the quality of the share image [
17].
The development of meaningful visual cryptography provides more room for the development of subsequent visual cryptography technologies because, with meaningful VC, share images can be stored in large quantities, which is convenient for encrypting more secret information. Naor and Shamir also designed the first meaningful VC [
4], which has a good visual quality and is easier to store multiple share images. At the same time, share images are less likely to attract the attention of attackers. Image encryption often uses halftone images and gray-scale images, so meaningful visual cryptography requires high fidelity for share images. There are mainly two types of meaningful visual cryptography algorithms: the first is to process in the frequency domain, and then use the original encryption algorithm to embed the encrypted secret image in the frequency domain of the cover image by wavelet transform, and finally output a gray band share images with covered images [
18]. For the second method, The gray-scale image is halftoned in the spatial domain, and then the cover image is embedded in the share image using the pixel compensation method [
19].
Color visual cryptography is also one of the main researches in the field of visual cryptography [
20,
21]. Color visual cryptography has good visual quality. The earliest research on color visual cryptography was the color visual cryptography (
k,
n) solution. The secret image is encrypted into
n share images, and no less than
k share images are taken to superimpose to obtain the secret image. In 2000, Yang and Laih constructed a new color visual cryptography scheme. The basic structure of the sub-pixels can be directly used for the proposed structure in the image editing package, and it is easy to implement [
6]. In 2003, Hou proposed VC algorithms for color images. He proposed three VC methods for VC and grayscale images. These methods are based on VC for binary images, digital halftoning, and color decomposition methods. These methods have similar VC advantages to binary images [
22]. In 2011, Prakash and Govindaraju proposed a color visual cryptography scheme based on direct binary search (DBS) with adaptive searching and exchange functions [
23]. Through this solution, a better halftone image can be generated, in addition to lossless recovery.
We conclude the literature review by noting that, even though a color extended VC with authentication capacity is desired, currently no such design is reported. One possible reason is that to design such a VC system, one needs to meet many restrictions.
In this paper, a meaningful flipping visual cryptography algorithm is proposed based on the constraint error diffusion. The main features of our system are as follows:
The cover image can be a gray-scale image or color image. So, The share image is meaningful.
The share image and the cover image are of the same size, and there is no pixel expansion after encryption.
Two secret images are simultaneously embedded. That is, by superimposing two share images on the front side, one obtain a secret image ; by superimposing the share image and the flipped share image , one obtain the second secret image .
When the secret image are recovered by stacking, there is no interference from the cover image.
To the best of our knowledge, currently, there is no VC algorithm that meets all the above requirements.
The structure of this paper is as follows: Related background is reviewed in
Section 2. In
Section 3, we present a meaningful flipping visual cryptography algorithm.
Section 4 combines the color VC algorithm to obtain color meaningful flip VC.
Section 5 provides the experimental results.
Section 6 concludes this paper.
2. Related Works
This paper is divided into two parts: gray-scale meaningful flipping visual cryptography and color meaningful visual cryptography. Meaningful flipping visual cryptography uses the method of constrained error diffusion to embed the cover image into the share images, which improves the visual quality of the share images and can better protect the secret image from being discovered. Color flip visual cryptography can encrypt color secret images, and the share images are color images with better visual quality. In this section, we review the basic structure of VC with meaningful shares and flip VC [
24,
25]. Unless otherwise stated, all the secret images in this section and next section are binary images.
We would like to ask our readers to pay attention to the difference between the secret image and the share images.
A binary secret image is a digital image stored in a computer disk and/or memory, and it consists of white pixels and black pixels. Following the convention in VC and digital halftoning, we use a ‘1’ to represent a black pixel on the secret image, and we use a ‘0’ to represent a white pixel on the secret image.
A share image is printed on a transparency. When printing on paper, which is white by default, a printer only needs to print a black dot or print ‘no dot’. Most printers are not able to print white color except for some UV printers that are designed to print on cloth and plastic. So, when printing a share image on a transparency, a black pixel is printed as black while a white pixel is printed as ‘transparent’ since no dot is printed. So, when referring to a ‘white’ pixel on a transparency, we use the term ‘transparent’ pixel. Following the convention in VC and digital halftoning, we use a ‘1’ to represent a black pixel on a transparency, and we use a ‘0’ to represent a transparent pixel on a transparency.
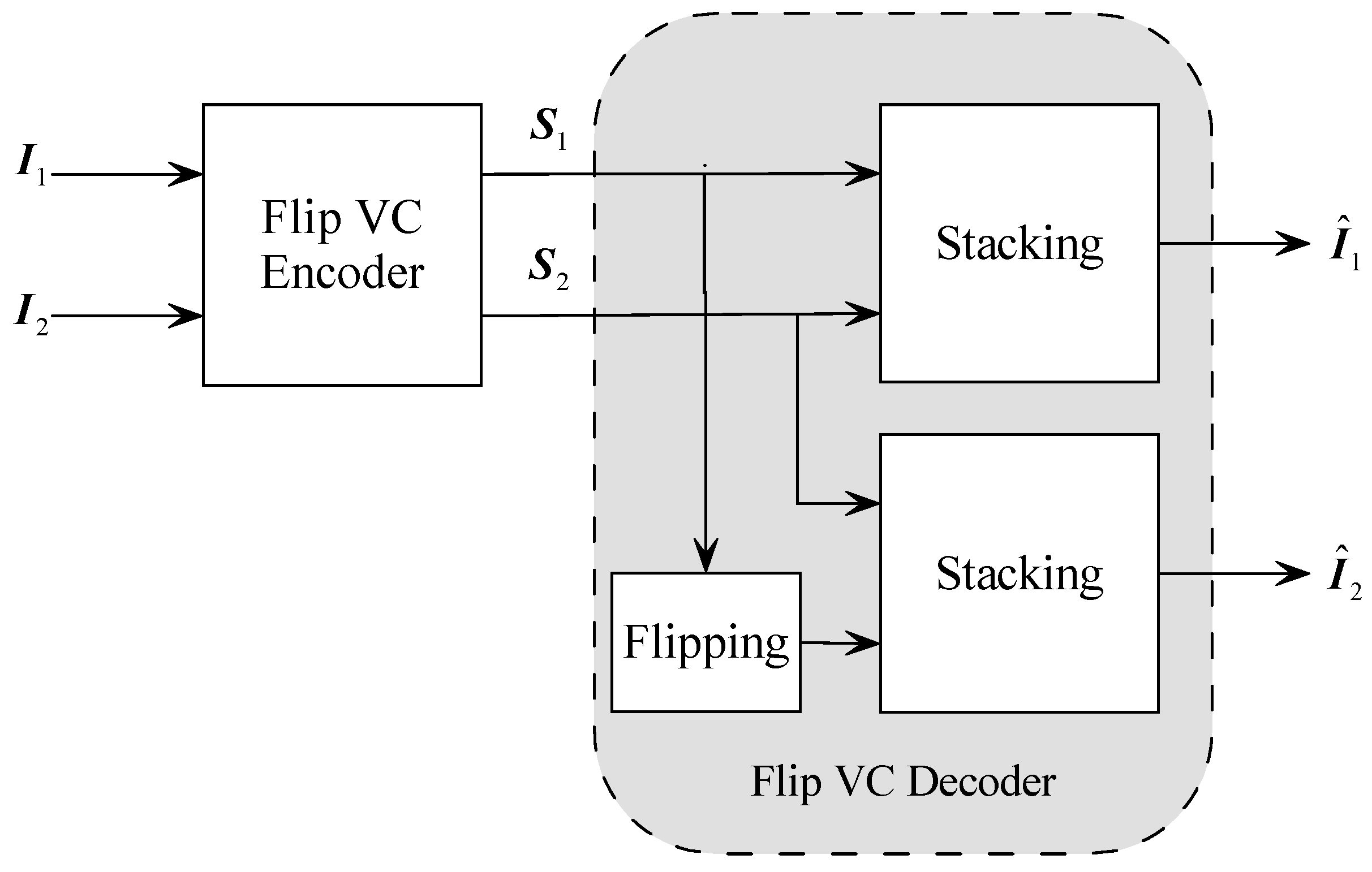
2.1. VC with Meaningful Shares
A VC system with meaningful shares is also referred to as the
extended VC in the literature. The overall structure of such a system is illustrated in
Figure 1. For illustration purposes, we consider the case with two secret images and two cover images. A secret image is an image that the holder would like to share and would like to keep confidential during the sharing process. It can be a binary image, grayscale image, or even color image. In
Figure 1,
and
are two secret images. In an ordinary VC, these secret images are encoded into share images
and
that are noise-like (i.e., meaningless). These share images are printed on transparencies, such as projector films or other transparent plastic thin sheets. Then the share images are distributed to different parties (also called participants). However, these noise-like shares may arouse the suspicion of an attacker. Extended VC is a countermeasure to this issue, where natural-looking cover images are used to generate shares. The two images
and
are two cover images. After gathering enough shares, a VC decoder can decode the secret images by simply stacking the transparencies carrying the shares. By inspecting the stacking results, a human is able to read the secret using his/her human vision system. So a VC decoder, in its strict sense, doesn’t need computation. In
Figure 1,
and
are two decoded secret images. These images are also referred to as target images in the VC literature. The target image is usually not the same as its secret image counterpart. However, as long as the content of the secret image can be recognized from the target image, one deems the decoding as valid.
The most basic and simple algorithm model of visual cryptography is the (2, 2) scheme proposed by Naor and Shamir, which can be considered as a degenerated version of extended VC. It is also a building block of extended VC, so we review it briefly with a focus on its encoder. In the (2, 2)-threshold scheme, The secret image is encrypted into two share images. Even if an attacker obtains one of the share images, The secret image cannot be inferred from it. Two share images are needed in order to recover the secret image. The (
k,
n) threshold VC is an extension of (2,2) threshold scheme, that is, The secret image is encrypted to generate
n share images. Only when
k or more share images are superimposed, The secret image can be restored. A
-threshold scheme consists of two collections of matrices, such as:
It should be noted that all the matrices in a set
, where
, can be obtained by column permutation of a basic matrix. For example, all matrices in
can be obtained by column permutation of the matrix
Similarly, all matrices in
can be obtained by column permutation of the matrix
So
and
are usually called the basic matrices for this
-threshold VC scheme [
24].
To encode a white pixel, one randomly chooses a matrix from the set and assign the first row to share 1 and the second row to share 2. Likewise, when encoding a black pixel, one randomly chooses a matrix from the set and assign the first row to share 1 and the second row to share 2.
To illustrate this encoding process, let us consider a toy example as shown in
Figure 2. The secret image consists of two pixels on a white paper, a black pixel (top) and a white pixel (bottom). To encode the black pixel, we randomly choose a matrix from the set
. Suppose that the matrix
is chosen. Then the first row of
, which is
, is assigned to share 1 and the second row of
, which is
, is assigned to share 2. Noting that the shares are printed on transparencies, so share 1 gets a black pixel and a transparent pixel on its transparency, and share 2 get a transparent pixel and a black pixel on its transparency. When stacking share 1 and share 2, The stacking result consists of two black pixels. Likewise, to encode the second secret pixel (i.e., a white one), we randomly choose a matrix from the set
. Suppose that we get the matrix
Then the first row of is is assigned to share 1 and the second row of is is assigned to share 2. So, share 1 gets a black pixel and a transparent pixel on its transparency, and share 2 gets the same pattern as share 1. When stacking share 1 and share 2, The stacking result consists of one black pixel and one transparent pixel. So, after stacking, it is possible to distinguish between the white pixel and the black pixel in the secret image.
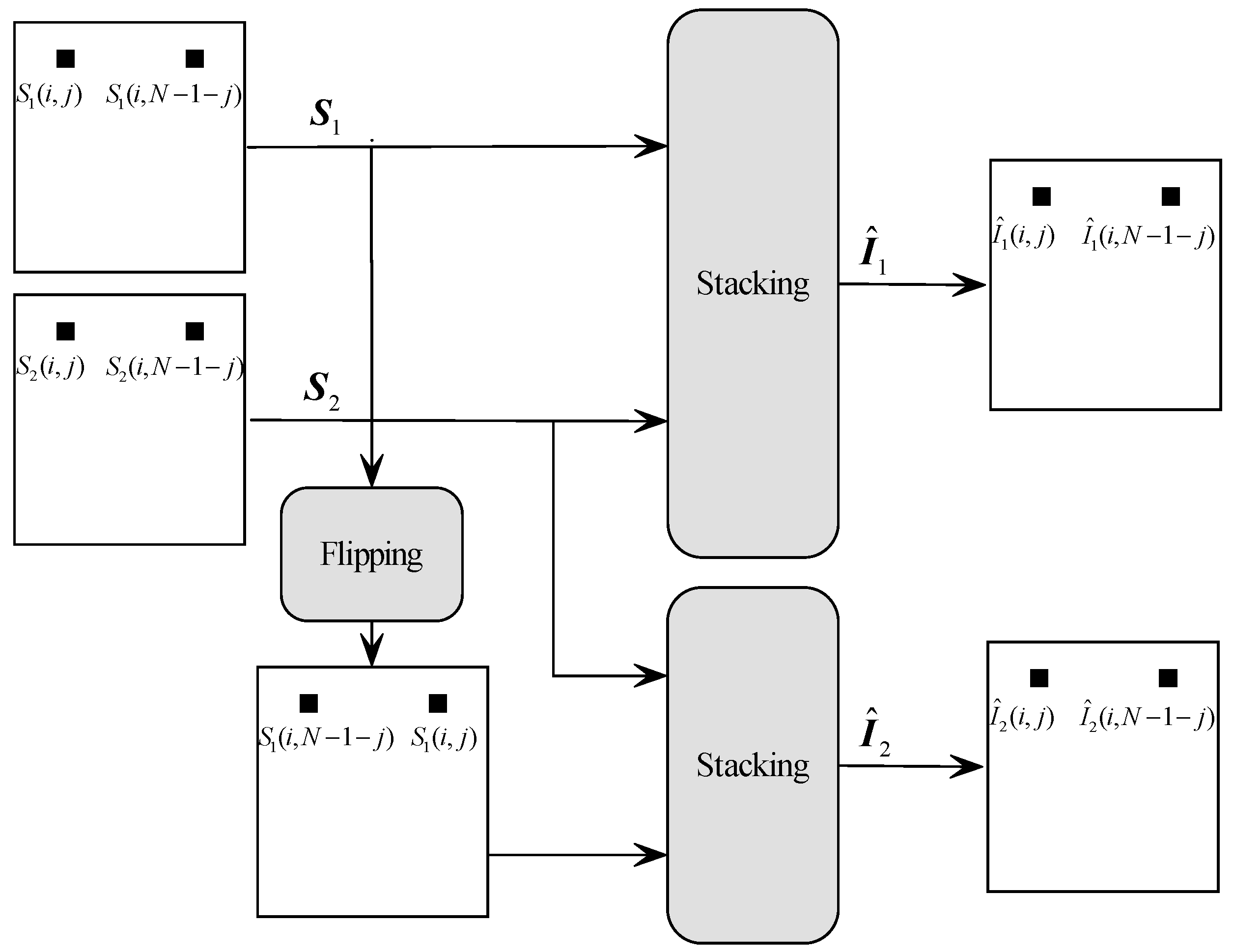
2.2. Flip VC
In 2010, Lin et al. proposed a flipping visual cryptography scheme based on non-expanded VC [
25]. The general structure of a flip VC is shown in
Figure 3. Two secret images,
and
, are encoded to generate two shares
and
. At the decoder side, if
and
are stacked, an image
is generated, which reveals the content of the secret image
. However, if we flip
horizontally before stacking with
(A flipping operation on an image is a horizontal mirroring operation so that two pixels at positions
and
are exchanged, where
N is the number of columns of that image, and
i is row index. For a more precise definition, please refer to
Section 3.1), then a different image
can be generated, which reveals the contents of
. So, a flip VC can encode two different secret images into two shares simultaneously.
However, more restrictions are enforced on encoder in flip VC than ordinary VC.
Figure 4 shows the stacking operation by the decoder. While in conventional VC one only needs to consider one pixel a time, now we need to consider operations on four pixels
simultaneously, where
is the pixel at the
location of share image
, and
N is the number of columns. These four pixels can be grouped into a quadruple
To recover the secret image, The decoder must meet the following requirements:
Stacking with , the secret image should be revealed, i.e., , where ⊗ denotes the stacking operation.
Stacking with , the secret image should be revealed, i.e., .
Stacking with , the secret image should be revealed, i.e., .
Stacking with , the secret image should be revealed, i.e., .
The first two conditions ensure that when and are stacked, we can decode the secret image . The last two conditions ensure that when flipped is stacked with , we can decode the secret image .
Lin et al. constructed 16 basic matrices for each of the quadruples
where
B denotes ‘black’ and
W denotes ‘white’. As an example, The basic matrix for quadruple ‘BWBB’ is [
25]:
So, if the encoder needs to encode the quadruple
then it randomly selects one column from the basic matrix
and assign it to the four pixels
on the two shares
and
, respectively. It is not difficult to verify that, when the first row and the third row of
are stacked, The ratio of black is 1. This ensures that when stacking
and
, The probability of black pixel is 1. When the second row and the fourth row are stacked, The ratio of black is 5/6. This ensures that when stacking
and
, The probability of black pixel is 5/6 and the probability of white pixel is 1/6. So a relative contrast of
can be ensured on stacking results. For a complete list of the 16 basic matrices, please refer to Table 1 in [
25]. Lin also proved that using these basic matrices, a relative contrast of
can be ensured on stacking results. Furthermore, his construction is also proved to be secure.
3. Proposed Scheme
Before elaborating on the proposed algorithm, let us fix the notations for matrix operation and share stacking.
3.1. Definition of Operation
Definition 1 (matrix concatenation)
. Let be one of the matrices in the share matrix, where are the position indices of the block matrix in the share matrices. Defineas the concatenation of matrices. For example, if then we have Definition 2 (stacking)
. Operation for image stacking ⊗ is the logical OR operate, where. For two matrices and , results in pixel-wise OR between two pixels at the same position on and .
Definition 3 (matrix flipping)
. Matrix flipping operation flips the matrix with respect to its central column. Let , where is the set of real numbers, and m and n are even integers. Then we havewhere For example, givenand then we haveThe flipping operation is part of the VC decoder presented in the next subsection. Definition 4 (Left and right region of a matrix)
. Given a matrix , we define the operation as returning the left half region of the matrix :Similarly, we define the operation as returning the right half region of the matrix :Obviously, when concatenating the two halves, we should have . 3.2. Overview
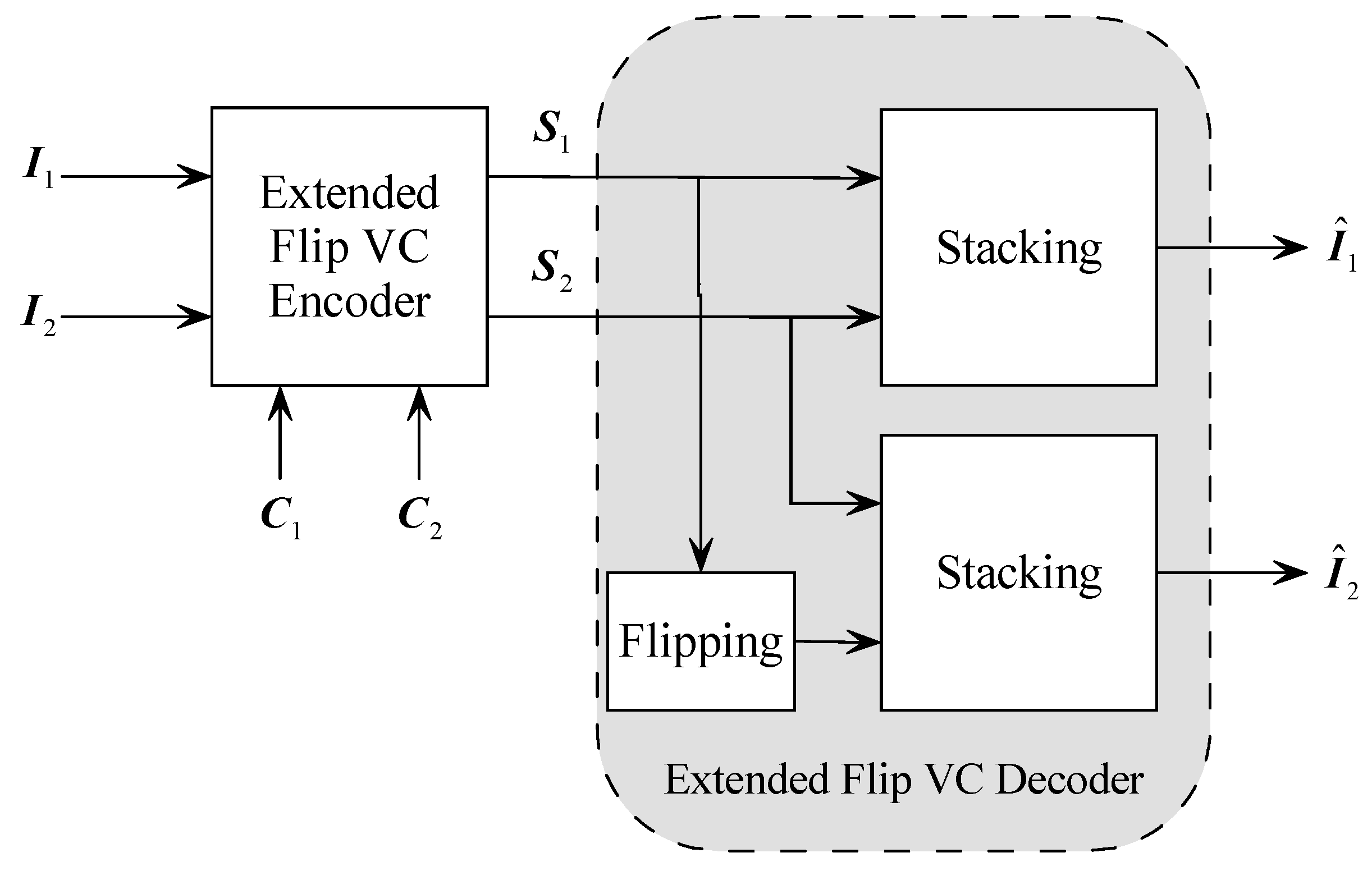
In this section, we describe the overall structure of the proposed algorithm. The block diagram of this system is shown in the
Figure 5. During encoding stage, two secret images
and
are encrypted into two shares
and
that are perceptually similar to the two cover images
and
.
These shares are distributed to two different participants. During decoding stage, after gathering two shares, The decoder is able to recover the content of the secret images by stacking operation. More specific, The content of secret image
can be recovered by stacking
and
:
and the content of the secret image
can be recovered by stakcing
with the flipped
where
is the flipping operation as defined in previous subsection.
We can recover the secret image that have the same information content as when stacking the front side of share with the front side of share . However, when we stack the front side of share and the reverse side of share , we can recover the secret image .
3.3. Determining Pixel Position
Let us assume in this section that the cover images are gray-scale images and the secret images are binary images. The grayscale cover image is of M rows and N columns. We divide the share images into blocks of size , and encode the 1-bit of (i.e., 1 pixel) secret image into block in the share images. So the size of the secret images has rows and columns, where returns the nearest integer towards the .
When stacking two shares in order to recover the secret image, two types of interference may appear:
In order to recover secret images without interference, we must superimpose pixels that do not contain secret information in black. Let the matrix contain all the secret image pixels and the matrix contain all the auxiliary black pixels, where p is the index of the matrix of the secret image informations and q is the index of the share matrix. When recovering a secret image, in order to avoid interference of another secret image pixel, another secret pixel must be black after stacking. We define these pixels as auxiliary secret pixels .
In our algorithm, The positions for encoding the secret pixels are generated randomly. This random approach is advantageous than deterministic approaches in terms of security and ensuring the exact number of secret image pixels (SIP). The position determination algorithm is summarized in Algorithm 1.
We assume that each share image is segmented into blocks. Within each block, there are black pixels, which means that pixels are used for encoding the secret pixel from and pixels are used for encoding the secret pixel from .
When stacking two shares, we must use auxiliary black pixels (ABP) to remove the interference from the non-SIPs on stacking result. To ensure that we have enough ABPs, then number of ABPs should be at least half of the number of non-SIPS, i.e.,
| Algorithm 1 Determine pixel position |
| Input: |
| Q: Size of block. |
| : Size of the share image. |
| : The number of pixels in each secret image in a block. |
| : The number of black auxiliary pixels in a block. |
| Output: |
| and : Position matrix of pixel locations of secret image and secret image |
| pixels in the share image. |
| and : Position matrix of black auxiliary pixel position in share image and . |
| 1: for 1 to do |
| 2: for 1 to do |
| 3: Generate non-repeating random numbers from 1 to to form a sequence , |
| and map the sequence to a pixel block. |
| 4: Select the first random numbers and return their corresponding positions in the pixel block x(k), y(k), Where x(k) and y(k) represent the row and column positions of the kth random number in the pixel block, respectively. |
| 5: for m←1 to do |
| 6: |
| 7: end for |
| 8: for m← to do |
| 9: |
| 10: end for |
| 11: Select the random number after the th and return its corresponding position |
| x(k), y(k) in the pixel block. |
| 12: for m← to do |
| 13: |
| 14: end for |
| 15: for m← to end do |
| 16: |
| 17: end for |
| 18: end for |
| 19: end for |
| 20: Return the position matrices |
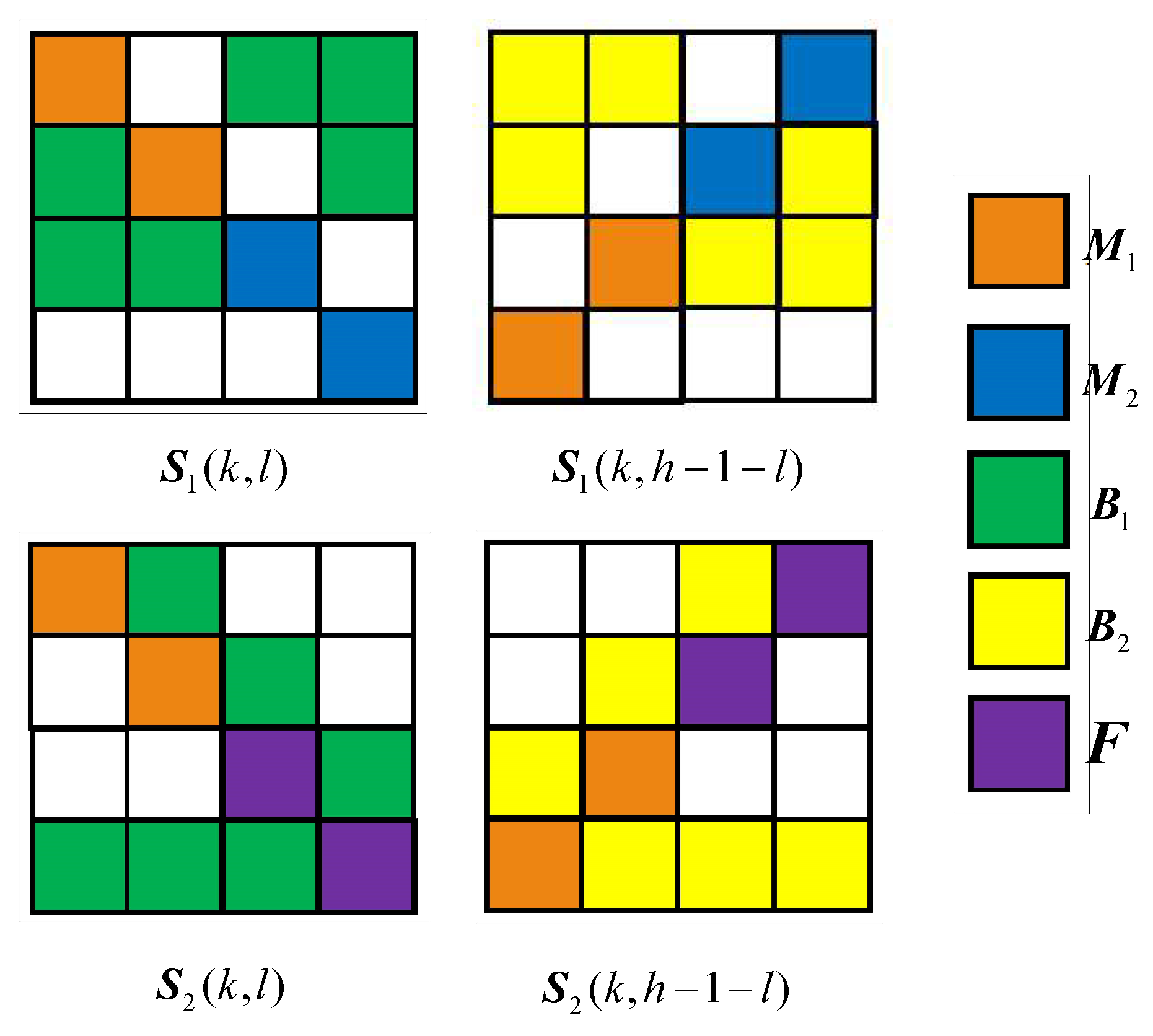
First, to determine the location for SIPs and non-SIPs, we generate a vector which contains a permutation of all integers between 1 and . Then we use the first numbers as positions of the SIPs for , and use the numbers as positions of the SIPs for . The positions are for ABPs in share , and the positions are for ABPs on share . Next, we map these positions into positions in a block, and fill the corresponding positions of with 1 and other positions with 0.
For example, let us take
, then we have
. Let us assume that the random permutation is
Then, the positions
are used for embedding pixel from
, and the positions
are used to embed pixel from
. The positions for ABPs on share
and
are
and
, respectively. Suppose that the current image block index is
, then we get the following position matrices:
These positions are also illustrated in
Figure 6.
3.4. Embedding the Secret Image into Shares
From the last subsection, we get a collection of secret pixel locations and non-secret pixel locations. In this section, we describe the process of embedding the secret information at the secret pixel locations. Since every block in the share contains two pieces of secret information and corresponds to another share in different ways, the secret pixel position needs special design when embedding the secret pixel.
In order to eliminate interference during stacking, we have to adjust the position matrices obtained from previous section before embedding secret pixels. The ABP matrix must meet the following two requirements
When stacking and , the ABP matrix should cover the SIPs for the secret image ;
When stacking and , the ABP matrix should cover the SIPs for the secret image .
So, we should adjust the position matrices as follows.
These positions on shares
and
are illustrated in
Figure 7.
The basic matrices for bit 1 and bit 0 are denoted as
and
, respectively. For example, for a (2, 2) scheme, when
, we let
That is, when the secret pixel is bit 0, then is selected and it is transformed into , where denotes column permutation. The first line of is filled into the corresponding secret pixel position in share 1, and the second row is filled in the corresponding secret pixel in share .
Now that we know how to embed a secret bit, then we can embed the whole secret image into the shares. First, we embed the bits from . The other block index is (k,l), which is also the pixel index of the secret pixel. If the pixel in is 0, we need to fill the lines of into the corresponding positions in the two shares, otherwise we fill in . Next, the bits from is embedded based on the information of . If the bit of is 0, we fill in the complement of the position information in into the position in . Instead, the location information is copied. Finally, fill the auxiliary secret pixel and the auxiliary black pixel position with the bit 1.
3.5. Embed Cover Image In Share
The above section describes the process of embedding two secret images into two shares. The share obtained through this process is meaningless. In this section, we use constraint error diffusion to embed the cover image into the shares [
26], making the shares meaningful. The pixels in the share image are sequentially scanned using the raster scanning order. The cover image is quantized and embedded into the share image. The quantization process can be expressed as
where
,
, and
are the position matrices obtained from previous sections. The first term in the summation says that for those positions carrying the SIPs and ABPs, we leave them unchanged during cover image embedding process. The second terms says that for those positions allocated for carrying cover image, we use a simple binary quantizer:
To achieve better visual quality for the share images, the error between the share images and the cover images is spread to the non-secret information positions and the non-auxiliary positions by the error diffusion. Error diffusion diffuses the error produced by quantization at current location to its neighbors, so that when quantizing these neighboring pixels, these errors can be compensated. A diffusion kernel is like a filter kernel that determines how the errors are allocated to its neighbors [
24].
Let be the diffusion kernel located in the pixel (k, l), then in the constrained diffusion, the modified diffusion coefficient is . That is, the diffusion coefficient is set to 0 at the and and positions.
4. Flip Visual Cryptography for Color Images
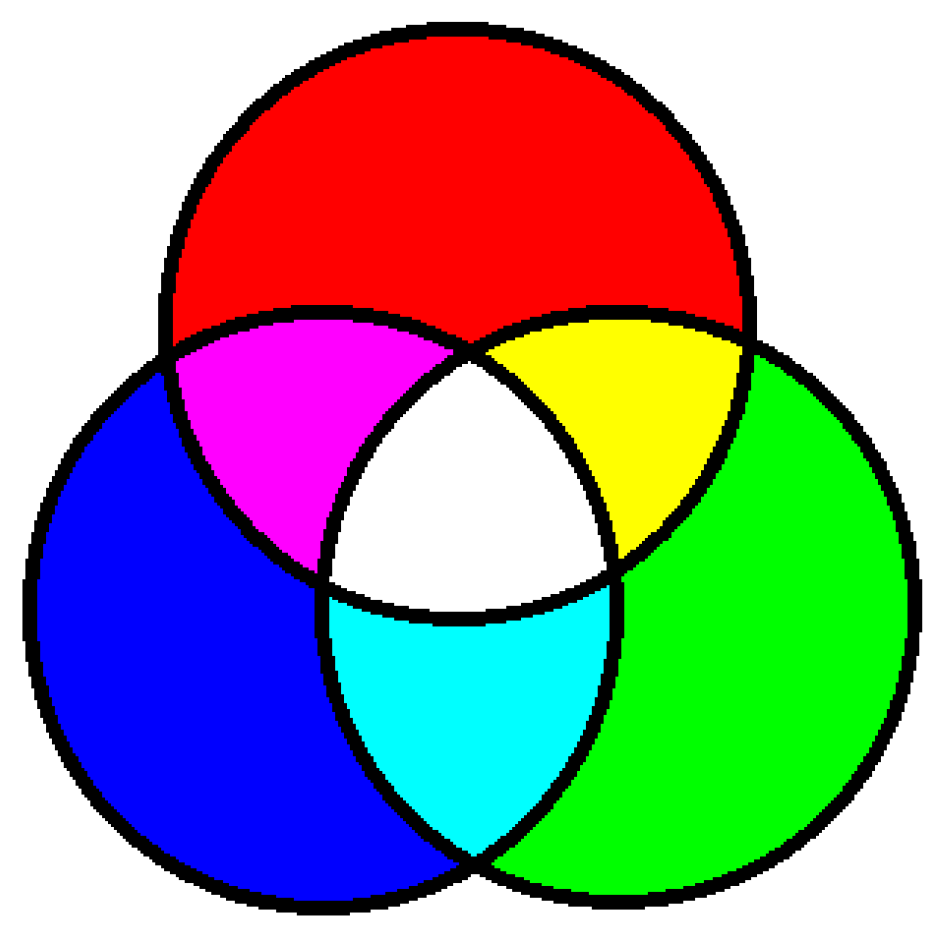
Color visual cryptography has better visual quality than its gray-scale counterpart since it can render more details with colors. In this section, we design a color VC in RGB color space. The secret image is divided into three channels of R, G, and B, and the secret image is embedded into the share image according to the principle of color stacking. The color overlay model is shown in
Figure 8.
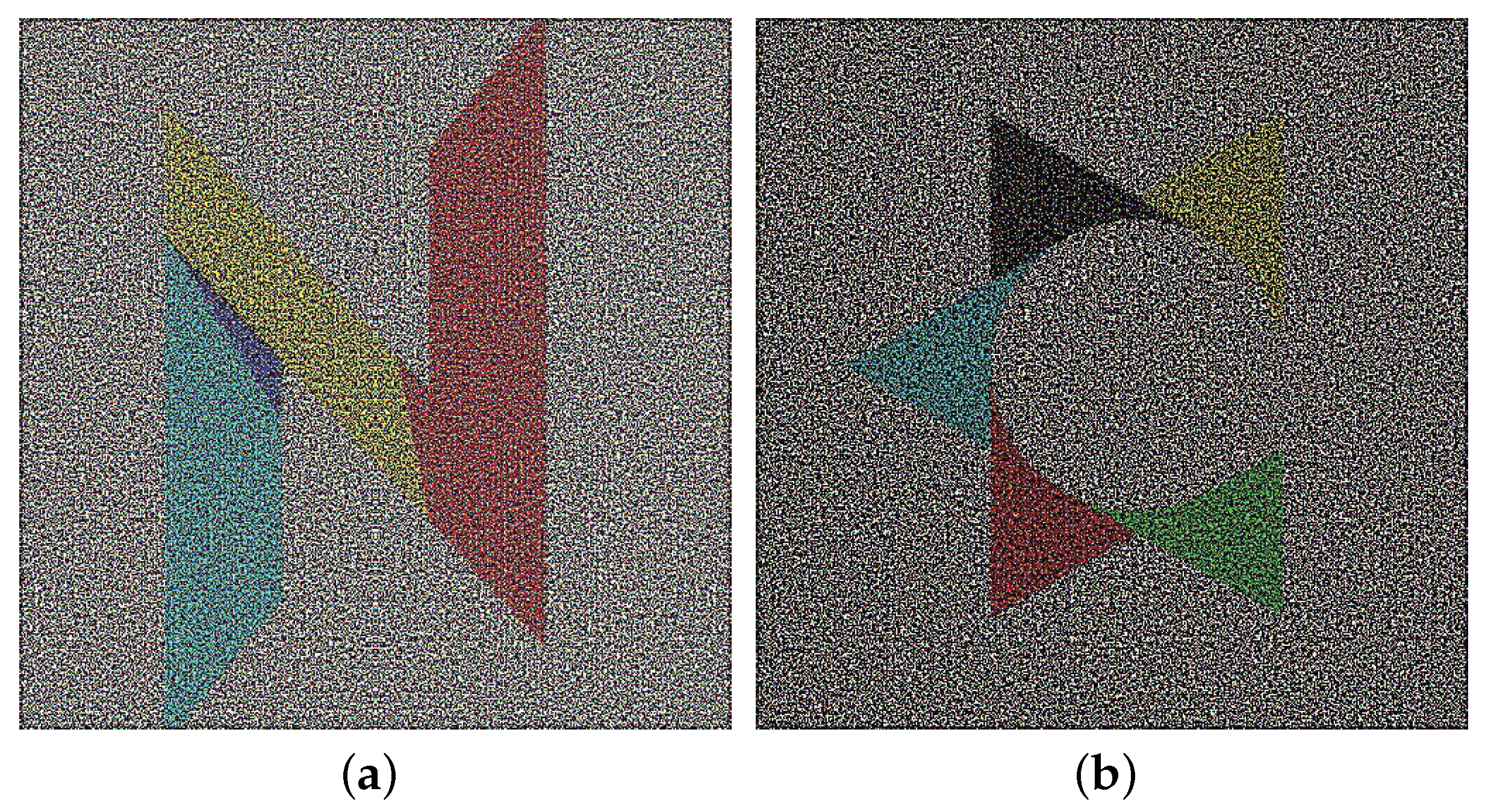
Our color VC is based on the human perception of color. When different pixels having different colors are clustered then our HVS (Human Visual System) perceives and average color. For example, if four pixels having color R, G, B, and W (R: red, G: green, B: blue, and W: white) are arranged as a
block, then we perceive white. Similarly, the effect of other colors can be achieved according to the proportion of colors in a small block. For example, if we have two B, one R and one G, then the ratio of the R, G, and B colors that are shared by the two shares is
, and the perceived color is blue. We can get different proportions of different colors after superimposing the sharing of different colors, as shown in
Figure 9.
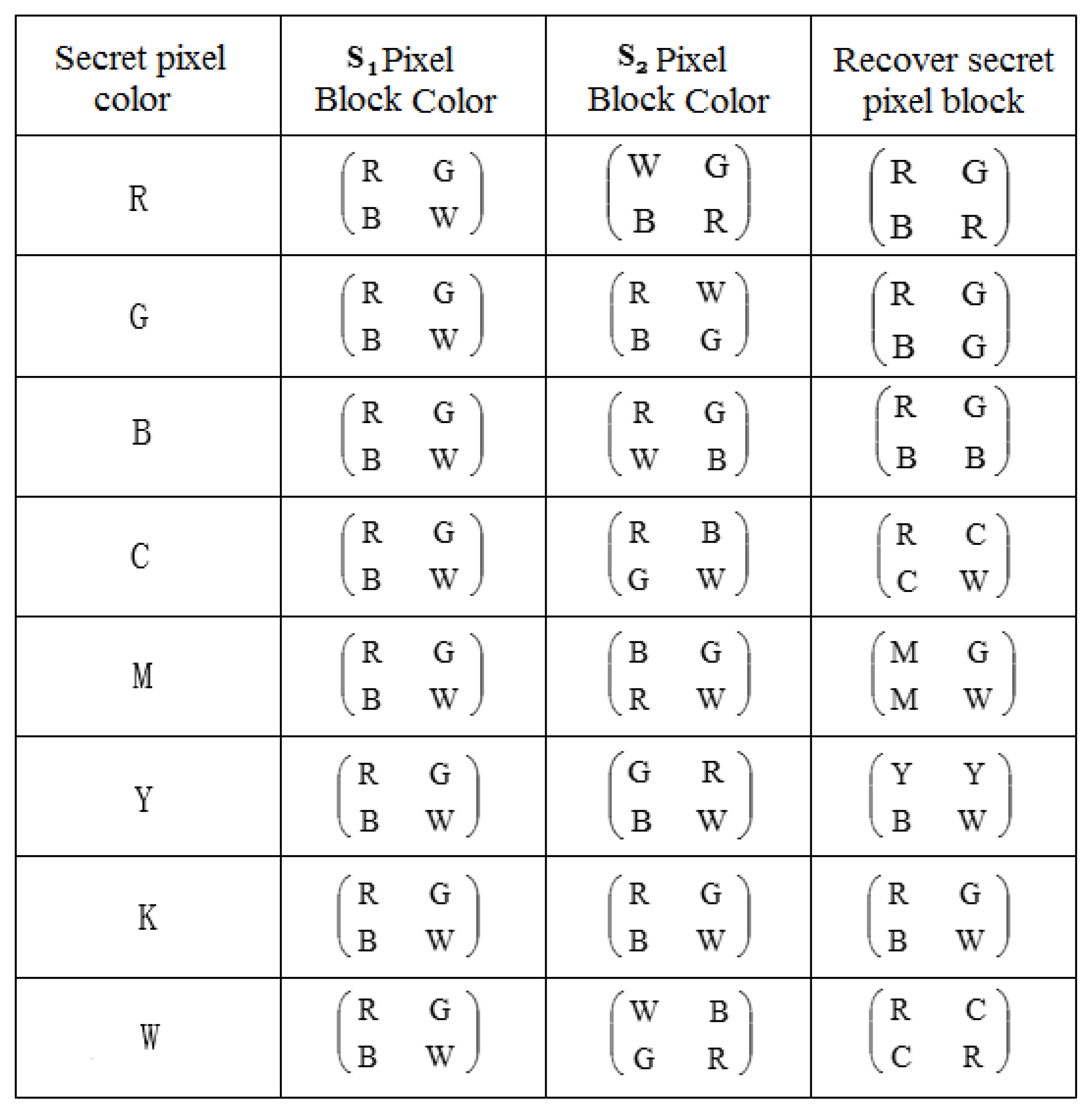
The steps to embed a secret image in a share during the color visual cryptography process are as described as follows:
Step 1: Color decomposition and halftoning. The RGB color image channels of and are separately halftoned.
Step 2: Embed R, G, B, W at the secret information 1 position in the (k, l), where (k, l) denotes the position of the pixel block, where .
Step 3: Embed the corresponding color in the secret information position of the (i, j) pixel block according to the color of (i, j) and the color of (i, j) position corresponding to secret information .
Step 4: Embed in the secret information position of the pixel block at (i, N + 1 −j) position according to the color of (i, N + 1 −j) and the color of the secret information 1 of (i, j) pixel block.
Step 5: Embed R, G, B, and W at the secret information position in (i, N + 1 − j) position pixel block.
Step 6: Fill in secret information position of (i, N + 1 −j) pixel block according to the color of (i, N + 1 −j) and the color of secret information 1 in (i, N + 1 − j) pixel block.
Step 7: According to the color of (i, j) and the color of secret information in (i, N + 1 −j) pixel block, fill in the corresponding color of the secret information position in (i, j) pixel block.