1. Introduction
With the developing technology, the availability and sharing of medical images on computer systems has increased. The availability of images on online systems provides serious convenience for both doctors and patients. However, the presence of medical images on the internet brings an important security problem. It is important to protect images containing private disease information. It is important to protect medical images containing disease information for patient privacy. In addition, many health institutions want to add information such as copyright and digital signature to medical images. Medical data hiding is one of the suggested solutions for this purpose.
Various information such as patient information, doctor comments and hospital logo can be added to the image using data hiding methods. The purpose of data hiding is to add secret information into various cover objects, such as images, videos, or sounds. It is critical that the carrier (stego) object containing secret information does not differ significantly from the original (cover) object.
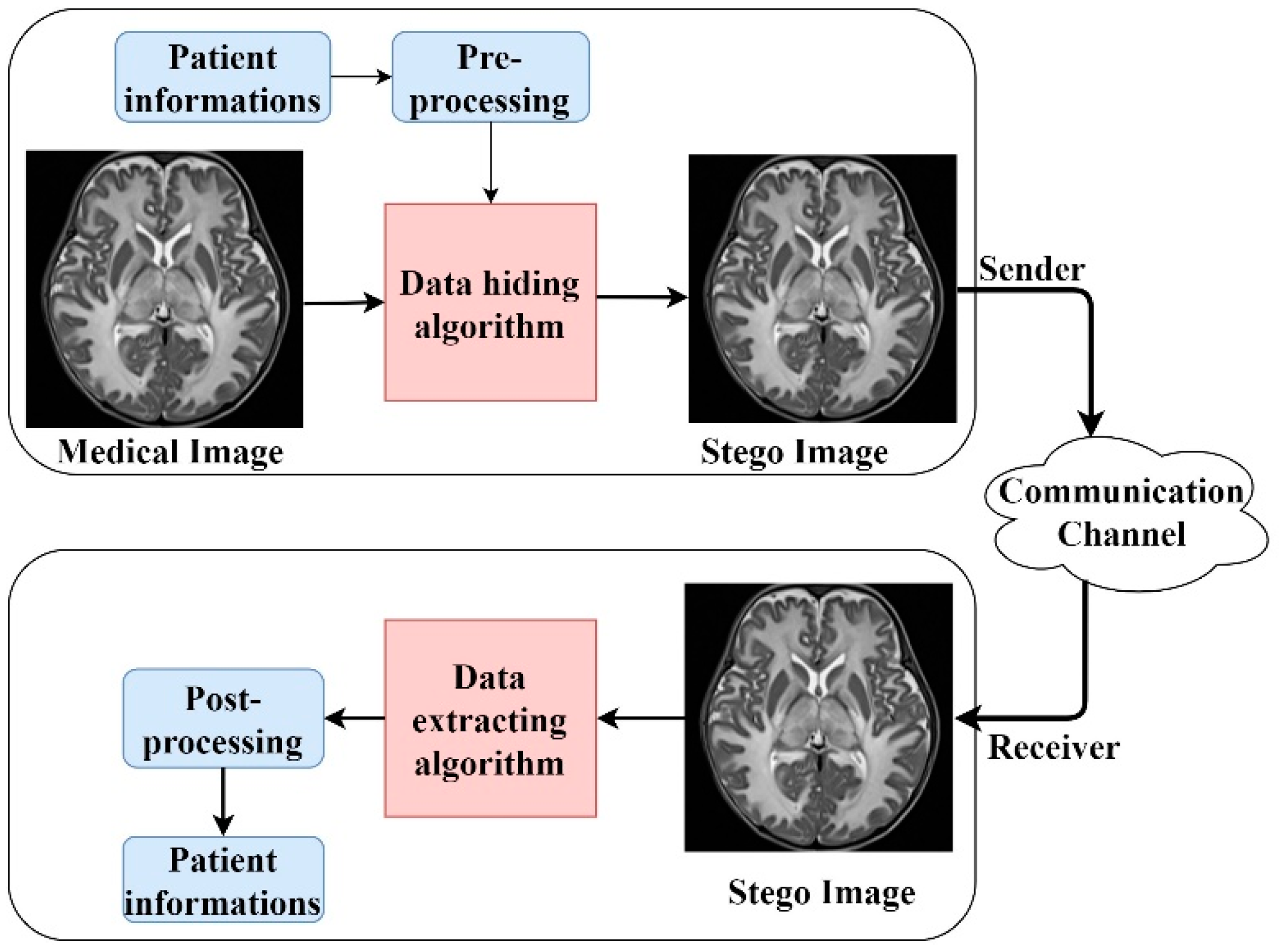
The same is true for medical images. Medical images such as ultrasound (US), X-ray, magnetic resonance imaging (MRI), and computed tomography (CT) created by the imaging device are used as the cover object. The general structure of data hiding in medical images is given in
Figure 1. Some pre-processes are applied to the patient information that will be hidden inside the medical image. Although these pre-processes vary according to the data hiding method, there may also be security operations such as encryption, coding or scrambling. The message information formed after the pre-processing is hidden in the medical image with the data hiding algorithm. The stego image containing the secret information is sent to the receiver through the communication channel. The secret message is retrieved with the data extraction algorithm on the receiver side. If there is any pre-processes like encryption or coding, it is resolved with the post-processing, and patient information is retrieved.
1.1. Literature Review
The methods proposed for hiding data in medical images vary. From histogram-based methods [
1] and [
2], hide data on peaks and zeros in the histogram of images separated into non-overlapping blocks. In [
3], a data hiding is proposed according to the improvement of medical images by histogram stretching and histogram equalization methods. In addition, there are studies which propose data hiding with the difference expansion of adjacent pixels [
4,
5,
6,
7]. In the medical image, some methods separate the region of interest (ROI) and region of non-interest (RONI). These methods hide data into encrypted RONI and the least significant bit (LSB) [
8,
9,
10], wavelet coefficient [
11,
12], discrete cosine transform (DCT) coefficients [
13] and dividing blocks [
14].
Studies using error control coding methods for data hiding in medical images are limited. In [
14], both noise reduction block and a simple error control coding named repetition codes are used. Repetition codes repeat the secret message several times. The author of [
14] repeated the secret message eight times and create a new thread. The new thread was embedded in MRI images. These stego MRI images were exposed to salt and pepper noise. For the extraction of the secret message, in the first stage they removed noise with the noise reduction block. In the second stage, they extracted the thread, which included the secret message eight times. In the study [
15], after the pixels in the cover object were duplicated by over-sampling, a secret message was added to the bits of the appropriate pixels. BCH coding was used as an error control method in wavelet-based hiding of [
11] and [
16] studies.
Reed Solomon (RS) coding, which is a common error control coding method, has been used limitedly in data hiding methods. Moreover, [
17] evaluated the use of error coding methods and RS codes in data hiding. Additionally, [
18] hides the message by selecting the polynomial coefficients in RS codes, with the matrix coding method which is used in various [
19] data hiding applications. In study [
20], which hides the codeword, it selects the place where the message will be hidden according to the base of the polynomial coefficient. The authors of [
21] use the RS code to fix errors in the video file from which the hidden message was extracted. The authors of [
22] hide the RS encoded message into the image, which is divided into blocks. In [
23], the cover file is made suitable for RS by sampling. The data part of the message coded with RS is added to the image and the control part is added to the region where the upper sampling is performed. The methods proposed in [
22,
23] have a complicated data hiding process due to the preferred data hiding algorithms and they take a lot of the processing load.
1.2. Contributions of the Proposed Work
For the vast majority of medical data hiding methods in the literature, no method against salt and pepper noise is recommended. Moreover, methods that apply salt and pepper noise to the Stego image generally yield results for 1% density noise. This does not show full resistance to salt and pepper noise. The study [
14], which offers results of salt and pepper noise in different densities, is only recommended for the MRI images. Moreover, in addition to noise filtering, this study can also get good results by hiding the same secret message eight times with repetition code. Although there are studies using different error control coding for non-medical images, these encodings are binary compatible and not used in decimal numbers.
Considering the existing works, the advantages of the proposed study and its contributions to the literature are:
Results tested for CT, MRI, US, and X-ray images, against salt and pepper noise at several densities.
It is proposed to use more effective RS coding instead of complex data hiding algorithms to remove salt and pepper noise.
To the best of our knowledge, this is one of the first data hiding studies of medical images-based on Reed Solomon coding.
Since the proposed data hiding method directly hides decimal numbers, the hiding capacity per pixel is high.
Noise-resistant spatial plane data hiding becomes more resistant to noise with the proposed method.
The rest of this paper is as follows; in
Section 2, Reed Solomon encoding and decoding processes are described. The proposed method is presented in
Section 3. Experimental test results are evaluated in
Section 4.
Section 5 contains the conclusion.
2. Reed Solomon Coding
The Reed Solomon (RS) coding [
24] used in this study is the decimal class of BCH codes used for non-binary coefficients. In RS coding, the amplitude of the error varies according to the Galois field used and may be a decimal value.
RS codes are defined in the Galois field
, where m denotes the number of bits in a symbol. The symbols for
are
. When an information message with the symbol number k is encoded with the RS code, together with the parity symbols added, a codeword with the symbol
is obtained, and denoted by RS(n, k) [
25,
26]. When the parity symbol length is accepted as
2t, up to
t incorrect symbols can be corrected in the RS(n, k) code. For information with symbol length
k, the information polynomial is as follows:
is the element of Galois field and all
coefficients are created with the help of minimal polynomial systematic RS(n, k) code, that can be given as in Equation (2).
denotes the parity polynomial, and refers to the
degrees remainder after division of
times shifted information polynomial to the generator polynomial
.
The
degree
polynomial has coefficients within
and is fully divided by
. The RS(n, k) codeword, which is formed as in Equation (5); the symbols are elements of
The
c codeword is sent to the receiver from the communication channel. Subject to noise or distortion in the channel such as
, the new codeword is taken by the receiver as
in Equation (6).
RS decoding consists of the error detection and correction process from the data transmitted through the noisy channel. The decoding process, which is more complex than the encoding process, will be briefly summarized here. See [
25] and [
26] for more information. With RS decoding, the corrected codeword of
is recovered, by trying to correct the incorrect symbols in the
message. To find the error in the message, the syndrome (error indicator) of the received signal is calculated first.
The syndrome has 2t terms, such as
. The
variable in the syndrome represents the amplitude of the error at the
position, and
indicates the location of the error. The number of error,
u and variable
i are defined as
and
, respectively. If the
2t pieces of
terms in the syndrome are all equal to zero, then there is no error. So, there is no need for a correction. However, if one or more
terms are nonzero, error location polynomials must be found. Error location polynomial for
is shown as,
The Berlekamp–Massey algorithm is the best known method to create error location polynomial in RS coding. After creating the polynomial with this algorithm, the easiest way to find the roots of the polynomial defined in is to use the Chien search method. After the roots of the polynomial are found, the opposite roots of these roots in give the location of the error.
In the first stage, the error location polynomial, the roots of the polynomial and the error locations were found, but this information is not enough to correct the error, since RS encoding is recommended for non-binary numbers. Therefore, the amplitude of the error should also be determined. To determine the amplitude of the error, the error amplitude polynomial
is created as in Equation (9).
Forney equations are used to construct the error amplitude polynomial, and calculate the amplitude of the error. The amplitude of the error for the value of
in
is
where
denotes derivate of
. Thus, the location and amplitude of the errors in the u positions are found in the noisy
codeword in the receiver. After all error values (
) are found, the error of the information message in the RS(n, k) codeword is corrected as in Equation (11), where
denotes bit-wise ex-or operation.
3. Proposed RS-Based Data Hiding Method
In this study, we aim to increase the resistance of the message hidden in medical images against salt and pepper noise. In the proposed method, the secret message is encoded with Reed Solomon codes and hidden in medical images. It is assumed that the stego image created by the proposed method is exposed to salt and pepper noise in the communication channel. Although the main purpose of the study is to test the resistance to noise, the method used for data hiding is also compatible with high capacity hiding. With the proposed method, we aimed to determine how accurately the secret message was extracted from the noisy medical image.
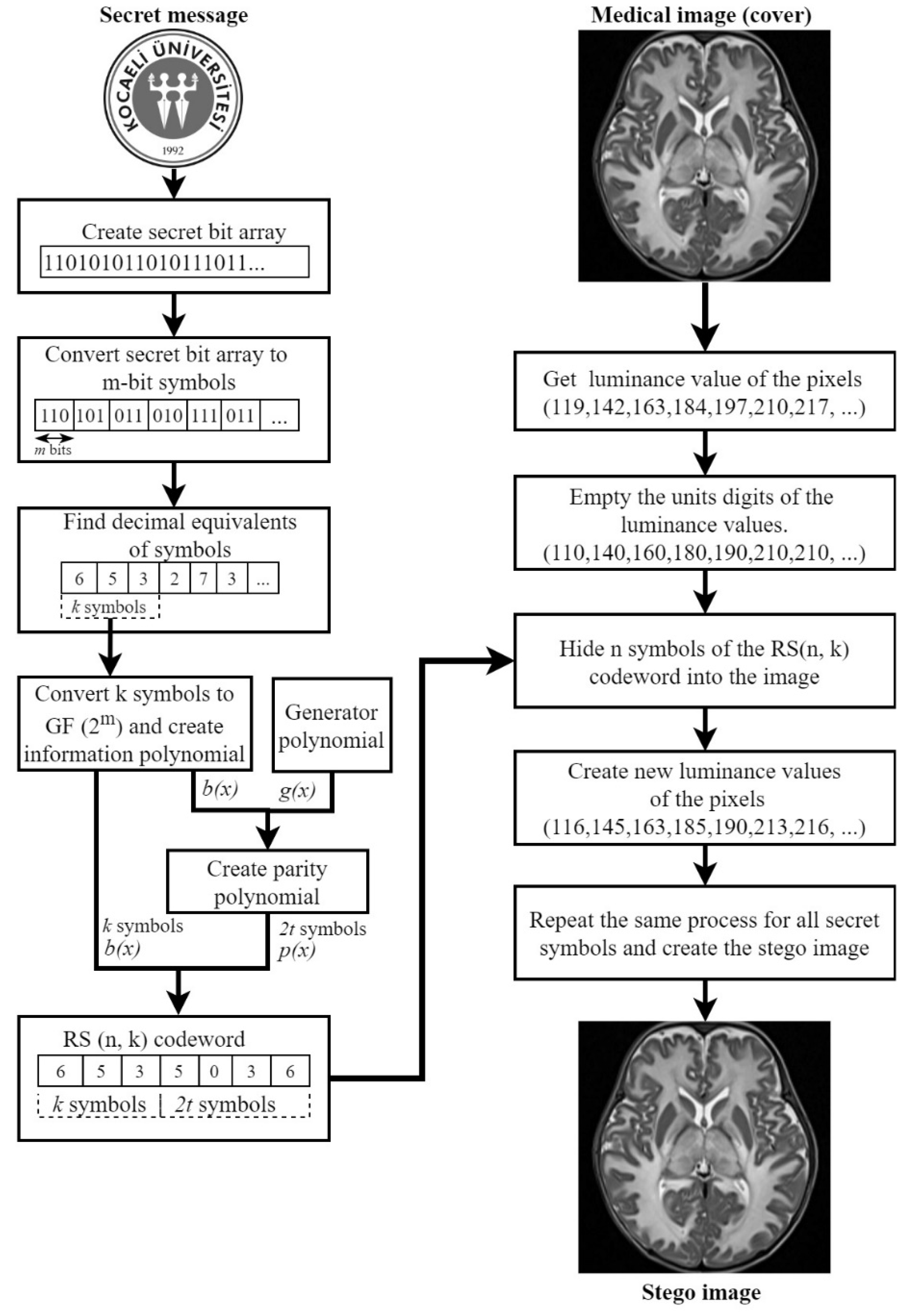
In the proposed method, first of all, operations are made with the logo that will be hidden in the medical image as a secret message. The brightness values of the secret logo are transferred to a message array as a result of the row-column operations. Each element in the message array is converted to eight-bit numbers. A new array is created with all converted brightness value elements. In RS(n, k) coding, each symbol consists of decimal numbers encoded with m bits. Therefore, the bit sequence of the secret message is divided into m-bit symbols. Each m-bit symbol is converted to decimal values. Decimal message symbols are converted to numbers in Galois field, with the help of minimal polynomial. By taking k of these message symbols, polynomial is created. With the help of the information polynomial , and the generator polynomial , the parity polynomial, that will add to the RS(n, k) codeword, is calculated as in Equation (3). Finally, the RS(n, k) codeword that consists of k message symbols and 2t parity symbols, is obtained as a n-element Reed Solomon message array. The secret message is now ready to be hidden in the medical image.
In this study, we aimed to make corrections unless all k symbols in the codeword are distorted. RS(7, 3) coding has been used in terms of compliance with both these conditions and the proposed hiding method. Therefore,
and
, and the maximum number of errors that can be corrected in a codeword, is
symbols.
These symbols embed to the luminance value of medical images with the proposed embedding method. For the data hiding method, it is proposed to hide a symbol directly into the brightness value of the pixel instead of the classic bit substitution methods. Thus, each symbol will be added to a pixel luminance (p) according to Equations (12) and (13). In this process, the proposed method changes pixel values a little, but when compared with its other advantages, these changes can be neglected. Because, the proposed method change pixel values, but these changes are unnoticeable in the human visual system. By hiding an RS symbol to a pixel, we change and lose some information. However, we reduce the amount of RS symbols that are affected by noise. This is because if the bits of a symbol are divided into more than one pixel the amount of noise exposure will increase. Moreover, when a secret symbol is embedded with the proposed method, there is not much significant loss. A lot of data hiding algorithms, such as [
19,
27], aim to reduce the lost or changes after embedding secret messages, while providing high capacity and high fidelity.
In the proposed data hiding method, n-tuple of the pixel of the medical image is taken first. Then, the units digit of the each luminance value is emptied and the new pixel value (
) is obtained, as in Equation (12). Because of preventing pixel luminance from exceeding the range 0-255 in the stego image, if a pixel value is 250 or greater, its value is set to 249. Each secret symbol of the Reed Solomon codeword is embedded to corresponding
as in Equation (13), and the modified pixel (
) is obtained.
This process continues until all secret message symbols are hidden in the medical image. The stego image is transferred to the communication channel to be sent to the receiver. A practical representation of the proposed data hiding method in
Figure 2 is given over RS(7, 3). When the example in
Figure 2 is examined, it is seen that the proposed data hiding method does not make many changes in the pixel values. Although it is focused on the extracting performance of the hidden message from the noisy signal, the embedding capacity of the proposed method can be increased by up to 3 bits per pixel (bpp).
The data extraction process on the receiver side is performed similarly to the hiding process. The stego image which exposed to salt and pepper noise in the channel is going to the receiver. Reed Solomon decoder uses the number defined in . Therefore, if the noise corrupted pixels’ unit digits exceeds , a pre-process must be done. With help of the pre-process, the unit digit of erroneous pixel which bigger than set as . This process does not affect any secret data while help the working RS decode. Because, if the symbol value is not correct, it does not matter what it is. RS will correct the symbol with the decoding process anyway.
The values in the units digit of the pixel brightness in the stego image are taken until the message ends and the distorted message sequence is created. In the false message array, syndrome is generated for each codeword in length n. To detect the locations of errors in the syndrome, error location polynomial is created by the Berlekamp–Massey algorithm. The roots of the error location polynomial are calculated by the Chien search method. By calculating the opposite roots of the found roots, the locations of the error/errors in the message syndrome are determined. Error amplitude polynomial is created for the amplitude information of the detected errors. With the help of Forney equations, the amplitude of the error is calculated by using and . As a result of these operations, the error/noise model is extracted. There are k hidden messages that are extracted from noisy images, as in Equation (11). Thus, k hidden messages in an RS(n, k) codeword are retrieved. This process continues until all the secret messages in all syndromes are cleared and separated. Each decimal element in the extracted secret message array is converted to m-bit numbers and a secret message bit sequence are created. By usage of this bit sequence, the pixel values of the logo are created and the secret message is retrieved by the receiver.
4. Experimental Results
The images were taken from the open source European Society of Radiology database [
28]. The images are shown in
Figure 3 and all are in 480×480 resolution. For ease of comparison, the gray logo of Kocaeli University is used as a secret message instead of a text message. The gray logo was set in different resolutions, hidden in medical images, and the test results were examined. In the proposed method, Reed Solomon codewords are produced by RS(7, 3).
The primary purpose of this study is to retrieve the secret logo right from the noisy environment. However, it was also tested whether the visual quality of the proposed data hiding method gives good results. First of all, stego images of the proposed method were evaluated in terms of quality parameters. For this purpose, the quality criteria such as mean square error (MSE), peak signal to noise ratio (PSNR) and structural similarity (SSIM) were examined in stego images. Equation (14) shows MSE calculated with
size original (
) and stego (
) images, and Equation (15) shows PSNR.
Equation (16) shows the structural similarity index (SSIM). If the mean values for original and stego images
and
, variances are
and
, and covariance is
, then SSIM is calculated as,
where the C
1 and C
2 coefficients are small constants. If two images are the same, then SSIM is equal to 1.
Table 1 shows the results of the proposed method for different embedding capacity in terms of bit-per-pixel (bpp). In the
Table 1, it is seen that performance results of same type stego images are almost the same. The fact is that, it is deduced that results do not change too much when the number of images increases. Therefore, for simplicity, the rest of the paper shows the result for the images in the first column of
Figure 3.
Table 2 shows the average performance values of all images for different capacity sizes. The PSNR value is above 35 dB and the SSIM value is close to 1 in the images without any compression process; this shows that the visual quality does not change too much after hiding. When
Table 2 is examined, it can be seen that the data hiding into the unit digit of the pixel of the cover image gives acceptable results.
In
Table 3 and
Table 4, the quality values of stego images of the proposed method were compared with existing medical data hiding methods. In most of the medical data hiding methods extracted, message quality is more important than high embedding capacity. So, experimental results were given for the same embedding capacity for a fair comparison. On the other hand, the hidden message is extracted with similar accuracy from noisy stego images for all capacity values. In
Table 3, PSNR and SSIM values are given for the stego MRI image, with 0.79 bpp or less embedding capacity. The proposed method provides superiority to the other two methods in terms of PSNR. Although [
3] study is in good condition in terms of SSIM, the amount of hidden data is low. It is obvious that the [
3] method will yield much lower results than the proposed method for 0.79 bpp capacity.
In
Table 4, quality comparison results are given for the different stego image with 0.33 bpp or less embedding capacity. If the embedding capacity of the other methods is equal to the proposed method, all values of these methods will decrease. Considering this situation, stego images offer better visual qualities than existing methods in terms of both PSNR and SSIM.
After data hiding, the stego image is transmitted to the receiver side through the communication channel that noiseless or contains different densities of salt and pepper noise. Secret data was extracted from the stego image in the receiver and the results were evaluated. Another data hiding (called no-RS) method was used to compare the performance of the proposed RS-based method. In this method, the secret logo is hidden directly on medical images without the RS method. Namely, the message sequence of the secret logo, which is converted into bits as a result of pre-processing, is divided into triple symbol groups and converted into decimal numbers. These elements are hidden directly to the units digit of the medical image by a similar method.
The abbreviations in the tables are as follows:
Proposed RS-based: the proposed method of this paper that used RS-based data hiding.
No-RS: similar to the proposed method, but without RS coding secret data embedded directly.
Figure 4 shows the logos extracted from stego images exposed to salt and pepper noise at a density of 1%. Thanks to the proposed RS-based method, the logo is exactly retrieved in the same quality in all medical image types.
Figure 5 shows the logos extracted from MRI stego images that were exposed to salt and pepper noise of different densities. When
Figure 5 is examined carefully, it is seen that the logos hidden by the proposed RS-based method are highly resistant to salt and pepper noises of various densities. As the logo size increases, the hidden message symbols begin to spread to the whole image, and the logo is slightly distorted.
Besides the visual evaluations of the extracted logo, objective evaluations were made. The SSIM value is calculated for the similarity of the stego image, as well as for the similarity of the logo.
Table 5 shows the SSIM results of the logo extracted from CT, MRI, X-ray and US stego images for different noise densities. The values that the proposed RS-based method reaches at 10% noise density are not reached even in 1% noise density without RS. Therefore, the message hidden by the proposed RS-based method has a high resistance to noise.
The bit error rate (BER) value is used to determine the rate of distortion in the hidden message, which indicates the ratio of the number of bits broken to the total number of bits. In Equation (17), a calculation is made for the embedded (
) and extracted (
) bit values of the M × N size logo. The higher the amount of distortion of the secret message, the higher the BER value; the lower BER value means better results.
Table 6 shows the BER value in the logo, retrieved from the stego images. According to
Table 6, the message hidden by the no-RS method was extracted with a higher error rate than the message hidden by the proposed RS method. Despite the noise, the message hidden by the proposed RS method can be obtained with very few errors.
The results of the proposed RS-based method and no-RS methods for all images are given in
Table 5 and
Table 6. There are two more striking aspects in the results in
Table 6. First, the hidden message in data hiding by the proposed RS-based method is almost error-free, even at 10% density noise. However, in hiding without RS, the message is erroneously extracted, even at the lowest noise. Second, the proposed method gives very superior results at all noise values. However, when the noise density approaches 50%, the values of the proposed method begin to decrease very much. The main reason for this is that loud noise completely changes the RS codewords. This is because it is not possible to extract the correct information in the completely distorted codewords.
In
Figure 6, the BER and SSIM results of the hidden message extracted from the stego image for different salt and pepper noise intensities are presented with comparative graphics.
Finally, the proposed method was compared with the existing methods in this study. In
Table 7, the BER values of the secret message are compared with similar methods in the literature. All of the methods in
Table 7 evaluated the extracted secret message from the stego image that contains salt and pepper noise, with a density of 1%. The proposed method recovers the message without loss at 1% noise density, while other methods give up to a quarter of the message losses.
While the noise density is 1%, there are two methods with the BER value closest to the proposed method. In
Table 8, a second comparison was made for these two methods for different noise densities.
Table 8 shows the BER and SSIM comparison results of the secret message. When
Table 8 is evaluated, it is seen that the proposed method has better BER values compared to [
30]. At noise densities of 5% and 10%, the proposed RS-based method is superior to the [
14] methods, which proposed that one uses a noise filtering block. Although the BER value of the proposed RS-based method at 20% noise density is superior, the SSIM value is lower. At 50% noise density, both methods give bad results.
Finally, the performance of the proposed method is tested against different noises. Three types of noises added to the stego images and test results were evaluated in terms of BER. The normal distributed Gaussian noise and uniform distributed additive uniform and multiplicative speckle noises are applied to the stego images with different variance sizes. The test results are given in
Table 9. As stated above, the proposed method is resistant to an amount of noise densiy. So, Gaussian and uniform noises are set to one fifth of the stego images. The mean values for all noise types are zero. From
Table 9 it is seen that the hidden message is extracted, with lower error for Gaussian and uniform noise.
On the other hand, speckle noise affects stego images more than other noises. So, hidden messages in the CT and MRI are extracted correctly, while an important part of secret messages in the US and X-ray is lost. Therefore, the proposed RS-based method has also resisted against Gaussian and uniform noises for all images.