Abstract
This paper deals with the N policy M/G/1 queue with working breakdowns. The supplementary variable and probability generating function techniques are implemented to develop the steady-state results. The stability condition of a stable queue, as well as several system performance measures, are also derived. A two-stage optimization method is employed to determine the optimal threshold N and the optimal joint values of two mean service rates until the stability constraint is satisfied. To demonstrate the effectiveness of two-stage optimization method, some numerical results are presented. Finally, we carry out sensitivity analysis for the expected cost function with numerical illustrations.
1. Introduction
This paper investigates optimization analysis of the N-policy M/G/1 queue with working breakdowns. The N-policy introduced by Yadin and Naor [1] is used to turn a server on when the total number of customers in the system reaches a threshold (), and to turn a server off when there are no customers in the system. There is extensive literature on the N-policy queue, which has been studied by many researchers (see a recent survey by Jayachitra and Albert [2] and the references cited therein). In many practical situations, servers break down at any time while in operation; however, they still work at a lower service rate rather than completely stopping service during the breakdown period. This is called a working breakdown, as first introduced by Kalidass and Kasturi [3]. Based on the matrix analytic method, Liou [4] found the steady-state probabilities of the number of customers in the M/M/1 queue with working breakdowns and impatient customers. Kim and Lee [5] analyzed the M/G/1 queue with disasters and working breakdowns, and derived the system size distribution and the sojourn time distribution, respectively.
The N-policy, T-policy, and the Min (N, T)-policy M/G/1 queues with unreliable servers were proposed by Wang and Ke [6]. For the T-policy, the server takes a “vacation” of a fixed length T if there are no customers in the system. When the vacation ends, the server returns from vacation and works as long as there is at least one customer in the system. Otherwise, it takes another vacation of fixed length T until at least one customer is present in the system. Moreover, the Min (N, T) policy means that the server starts working if either the condition of the N-policy or the T-policy is satisfied. For these three queues, they showed the steady-state probability that the server is busy, which is equal to the traffic intensity. Wang [7] developed the exact steady-state solutions of the N-policy M/M/1 queue with server breakdowns. The N-policy M/M/1 queue with heterogeneous arrival rates, server breakdowns, and vacations was analyzed by Ke and Pearn [8]. Wang et al. [9] utilized the principle of maximum entropy to investigate the N-policy M/G/1 queue with server breakdowns and general startup times. Using the same approach, Ke and Lin [10] approximated the steady-state probability distributions of the queue length for the N-policy M[x]/G/1 queue with an unreliable server and a single vacation. The optimal control of the N-policy M/G/1 queueing system with server breakdowns and general startup times was examined by Wang et al. [11]. They applied the direct search method to determine the optimal threshold N at the minimum cost. Jain and Bhargava [12] performed cost analysis of the N-policy for the machine repair problem with mixed standbys and an unreliable server. An N-policy MX/M/1 queueing system with server startup and breakdowns was analyzed by Vemuri et al. [13], where service was in two phases. Singh et al. [14] focused on the investigation of the N-policy queue with an unreliable server, state-dependent arrival rates, two phases of service, and m phases of repair. Moreover, Yang and Ke [15] applied the supplementary variable technique to analyze the (p, N)-policy M/G/1 queue with an unreliable server and a single vacation. Chen and Wang [16] address the sensitivity analyses of a retrial machine repair problem with warm standby units and a single server under the N-policy.
Over the years, there has been extensive literature on N-policy queues with server breakdowns, in which the server stops working completely during the breakdown period. However, there are no studies investigating the N-policy queue with working breakdowns. This queueing model accommodates many real-world systems, such as computer systems, assembly systems, and manufacturing systems. Thus, it motivates us to focus on the analysis of the N-policy M/G/1 queue with working breakdowns. The purpose of this paper is three-fold.
- (1)
- We derive several system performance measures, as well as the stability condition of this queueing model;
- (2)
- We establish a cost model to find the optimal threshold N, the optimal service rate during the normal period, and the optimal service rate during the working breakdown period under the stability condition;
- (3)
- We apply the two-stage optimization method to search for the minimum expected cost. Numerical examples are given to illustrate the effectiveness of the two-stage optimization method. Moreover, a sensitivity analysis is also performed.
2. Model Descriptions
We consider the N-policy M/G/1 queue with working breakdowns. It is assumed that customers arrive following a Poisson process with parameter . We assume that the service times in the normal and working breakdown states are independent and identically distributed (i.i.d.) random variables that obey arbitrary distribution functions and respectively, with respective mean service rates and . The Laplace–Stieltjes transforms of and are denoted by and , respectively. The server can serve only one customer at a time. Meanwhile, arriving customers form a single waiting line based on the first-come, first-served (FCFS) discipline. The server may suffer from failure at any time with Poisson breakdown rate when it is turned on and working. Whenever the server fails, it is immediately repaired at a repair rate , and repair times are assumed to be exponentially distributed. Arriving customers that find the server busy immediately join the queue until the server is available. During the server breakdown period, customers continue to enter the system according to a Poisson process. Once the server recovers to a normal state, it immediately serves a customer with a fast service rate . Otherwise, the failed server would be repaired and then turned off when no customers are in the system. Moreover, we assume that various stochastic processes involved in this queueing system are independent of each other.
Practical Justification of the Model
Cloud computing is the latest major computing paradigm, which shifts the deployment of computing infrastructure (such as CPU, network, and storage) from end users to the cloud data center. Computing infrastructure is virtualized in cloud computing, and therefore all cloud services are provided by virtual machines (VM), virtual networks, and virtual storage. Cloud service providers offer a VM for each cloud service request, and each VM consists of a kernel program and a root file system, with at least 5 GB disk space. As more cloud users arrive, the simultaneous disk access becomes the performance bottleneck in cloud computing. To guarantee the availability and reliability of cloud services, cloud providers usually establish distributed storage to improve storage efficiency. A practical situation related to the distributed storage system is presented for illustrative purposes. Consider a data center built and managed by the CloudStack cloud computing management system providing a platform as a service (PaaS). To increase the disk access bandwidth, a Ceph distributed storage cluster is integrated into the CloudStack cloud environment. Figure 1 depicts the system architecture of this data center. The Ceph storage cluster consists of one Ceph monitor (MON), which maintains a copy of the cluster map, and four Ceph object store daemons (OSD), which store data as objects on a storage node.
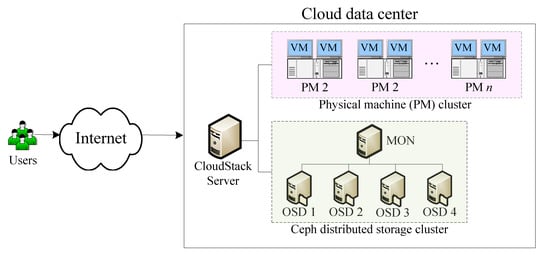
Figure 1.
A cloud data center provides a platform as a service (PaaS) via CloudStack.VM, virtual machine; OSD, object store daemon; MON, monitor.
To decrease the power consumption, the Ceph storage cluster is off at the outset. Assume that the arrival of PaaS request follows the exponential distribution with parameter . Upon the arrival of a request, the CloudStack will deploy a VM with a root file system stored in the local disk. The Ceph storage cluster will be turned on when the number of PaaS requests exceeds the predefined threshold (), and therefore CloudStack allocates root file systems in the Ceph storage cluster. Also, the Ceph storage cluster operates at an exponentially distributed full-speed disk access rate when four OSDs are working properly, while it operates at an exponentially distributed lower speed disk access rate if some of the OSDs fail, with exponentially distributed failure rate . The system manager requires an exponentially distributed repair time with mean to replace a failed OSD with a new one. The Ceph storage cluster will be shut off when none of VMs use its disk space.
3. Steady-State Results
Let be the server status at time t. Then, we get (i) 0 if the server is turned off; (ii) 1 if the server is turned on and working; and (iii) 2 if the server is turned on but subject to working breakdowns.
Here, we let the supplementary variable be the remaining service time for the customer in service. Then, the state of the system at time is given by number of customers in the system; remaining service time when the server is turned on and working; remaining service time when the server is turned on but subject to working breakdowns; and remaining service time for the customer being served.
Let
Then, is a continuous time Markov chain. Let us define
In a steady state, we define the limiting probabilities for ; ; and for , , .
3.1. Steady-State Probability Equations
Using the arguments of Cox [17], the Kolmogorov forward equations for this queueing model under the stability condition are given by
The above equations are solved under the following boundary conditions at
where
3.2. Probability Generating Function
The probability generating function (p.g.f.) technique is used to derive analytic solutions and in neat closed-form expressions. The respective probability generating functions of , , and are defined as follows:
We express in terms of as
where
Equation (4) is multiplied by , and then the equations are added term by term. We finally get
Similarly, Equation (5) is multiplied by , and then the equations are added term by term. We finally obtain
Equations (6) and (7) are multiplied by , and then the equations are added term by term. We finally get
and
Solving Equations (9) and (10) yields
and
Substituting Equations (13) and (14) into Equations (11) and (12) yields
And
We define the following notations:
Using Cramer’s rule to solve Equations (15) and (16), we obtain the expressions for
and
Substituting Equations (17) and (18) into Equations (13) and (14), we obtain
and
The denominator of has one of its roots (say) between 0 and 1. Since , for , the numerator of must vanish at . Therefore
where
It should be noted that when and , the expression in Equation (21) for is identical to the existing result in the literature (see Kalidass and Kasturi [3]).
Let be the p.g.f. of the number of customers in the system; thus
Substituting Equations (8), (19), and (20) into Equation (22), the expression for is given by
where
Thus, can be obtained by using the normalizing condition . That is,
However, since the denominator and numerator are both 0, we apply L’Hospital’s rule and find that
where
Hence, can be written as
where
We first mention that when , then and , the expression in Equation (28) for , which corresponds to the existing result in the literature (see Kalidass and Kasturi [3]). In particular, if we set , then we get and . Therefore, we have
Next, it is important to mention that if we put , then we obtain
which coincides with the existing result in the literature (see Wang [7]).
3.3. Stability Condition
The condition for a stable queueing system is given by Equation (28), since
After some routine manipulations, we can get
which is called the stability condition.
Substituting , , and into Equation (29), and by performing the algebraic manipulations, we have ; that is, the system is stable if , which is identical to the existing stability condition in the literature (see Kalidass and Kasturi [3]).
4. System Performance Measures
4.1. Computations for , , and
In steady state, let the probability that the server is turned off; the probability that the server is turned on and working; and the probability that the server is turned on but subject to working breakdowns.
Thus, we get
It is apparent from Equation (2) that
From Equations (19) and (20), we have
Since
Then from Equation (31) we get
4.2. Computations for , , , and
The idle period, the busy period, the partial breakdown period, and the busy cycle are defined in the following:
- (1)
- Idle period I: the length of time during which the server is turned off or is removed from the system;
- (2)
- Busy period B: the length of time during which the server is turned on and in operation and customers are being served;
- (3)
- Partial breakdown period D: the length of time during which the server is broken down and customers are being served;
- (4)
- Busy cycle C: the length of time from the beginning of an idle period to the beginning of the next idle period.
The expected lengths of the idle period, busy period, partial breakdowns period, and the busy cycle are denoted by and , respectively. Since the busy cycle is equal to the sum of the idle period, the busy period, and the breakdown period, we obtain
Due to the memoryless property of the Poisson process, the length of idle period is equivalent to the sum of N exponential random variables, each with mean 1/. Thus, the expected length of the idle period is given by
The long-run fraction of time the server is idle, busy, and in working breakdown states is given by
Thus, we obtain
4.3. Computations for and
Let us define that the expected number of customers in the system when the server is turned off; the expected number of customers in the system when the server is turned on and working; the expected number of customers in the system when the server is turned on but subject to working breakdown; the expected number of customers in the system.
The expressions for , , , and are obtained as follows:
To determine the expression for , we compute in Equation (8). Then, we obtain
To find , we compute in Equation (23) by using L’Hôspital’s rule twice to obtain
where the values of , , , and can be obtained from Equations (25) and (26).
Again, to find , we compute in Equation (24) by using L’Hôspital’s rule twice to get
where the values of , , , and can be obtained from Equations (25) and (27).
5. Cost Optimization Analysis
We establish the steady-state expected cost function per unit time for the policy M/G/1 queue server with working breakdowns, in which , , and are decision variables. We note that is a discrete variable with a natural number, and and are continuous variables with positive numbers. Our objective is to determine the optimum value of (e.g., ), so as to minimize this function.
5.1. Cost Function
We select the following cost elements, where holding cost per unit time for each customer present in the system; cost per unit time to keep the server off; cost per unit time to keep the server on; breakdown cost per unit time for a broken server; startup cost for turning the server on plus shut-down cost for turning the server off; fixed cost for a fast service rate; and fixed cost for a slow service rate.
Using these cost elements listed above, the total expected cost function per unit time is defined as
The cost minimization problem can be presented mathematically as
subject to
Suppose that the cost parameters in Equation (44) are linear in the expected number of the indicated quantity. Due to the fact is a discrete quantity, and are continuous quantities, and the highly non-linear and complex nature of the optimization problem, it would have been extremely difficult to develop the optimum solution symbolically. Furthermore, we should explicitly indicate that the solution really gives the minimum value. The results of extensive numerical experiments show that the cost function is truly convex and that the solution actually gives a minimum. The two-stage optimization method combines the direct search method and the quasi-Newton method, which first find the major discrete adjustment quantity , and then determine the minor continuous adjustment quantities and ; that is, we use the two-stage optimization method with as its initial values to determine the optimal value of , which we denote as
5.2. Direct Search Method
Since is a discrete variable, successive values of are directly substituted for the cost function until the minimum value of for example is achieved. We choose the service time distribution to be (two-stage Erlang distribution). The following numerical results are provided by using the following cost parameters
The cost minimization problem can be expressed mathematically as
subject to:
At first, we provide a numerical example to determine the optimal value by using the direct search method. We fix , , (2.5, 2.0), vary from 1 to 10, and select different values of = 0.4, 1.0, 2.0.
Table 1 and Figure 2 depict the various values of on (i) the expected cost and (ii) the optimal threshold We should note that a minimum expected cost (a) of $ 316.37 is achieved at for = 0.4, (b) of $ 468.16 is achieved at for = 1.0, and (c) of $ 921.24 is achieved at for = 2.0. If the function is unimodal, a single relative minimum exists. To find , we have to show the existence of convexity or unimodality of . Figure 2 demonstrates the curve representing the expected cost function, and it shows that the expected cost function is convex.

Table 1.
The expected cost for various values of , , and .
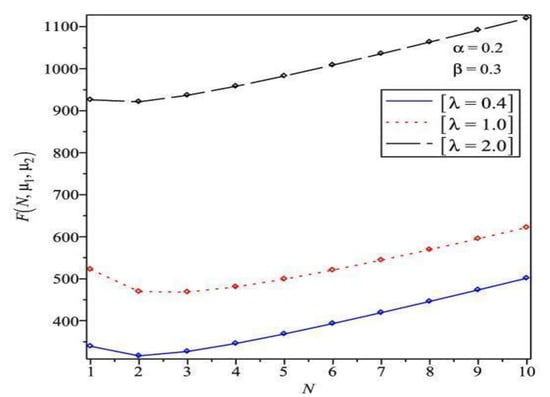
Figure 2.
Plot of for different values of
5.3. Two-Stage Optimization Method
We initialize and use the two-stage optimization method to search until the minimum value of (i.e., ) is achieved and the stability constraint is satisfied.
The cost minimization problem can be illustrated mathematically as
subject to:
The steps of the two-stage optimization method are depicted as follows.
- Step 1.
- Set , and .
- Step 2.
- Set the initial trial solution for , convergence tolerance , inverse Hessian approximation , , and initialize by the direct search method.
- Step 3.
- Compute .
- Step 4.
- , , , ; repeat until (the Wolfe conditions).
- Step 5.
- Find the new trial solution , and according to , where is calculated from a line search method to satisfy the Wolfe conditions (see Nocedal and Wright [18]); that is,
- Step 6.
- Set and repeat Steps 3-5 if , , or , where , , and are the tolerances; otherwise, go to Step 7.
- Step 7.
- Find the minimum value , where .
We select 2, , , , vary the values of from 1.0 to 10.0, and vary the values of from 1.0 to 20.0. The numerical results of are depicted in Figure 3. Figure 3 reveals that: (1) the expected cost function is convex in and (2) at .
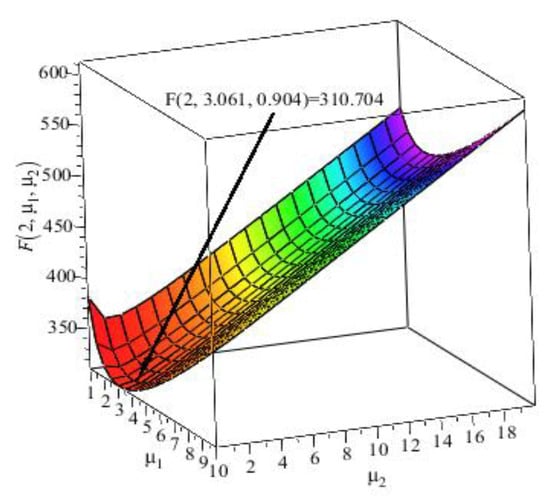
Figure 3.
Plot of for 2, .
We also perform a sensitivity analysis for the cost function, along with changes in the designated values of the system parameters. Table 2 reveals that: (i) increases as or increases; (ii) increases as decreases; (iii) both and increase as or increases; (iv) both and increase as decreases. From Table 2, it is important to note that (i) increases as increases; (ii) does not change, even though varies from 0.2 to 0.3; and (iii) does not change, even though varies from 0.3 to 0.5. Intuitively, this seems too insensitive to changes in and .

Table 2.
The two-stage optimization method in searching the optimal solution for various values of .
5.4. Sensitivity Analysis for the Expected Cost Function
In this section, we fulfill a sensitivity analysis for the cost function with respect to changes in designated values of the system parameters. To analyze the influences of various system parameters on the cost function, we use a graphical analysis of the following five cases. We fix the following cost parameters:
to study the listed below five cases:
- Case 1: , , , ; select different values of 1, 3, 9, and vary from 0.6 to 0.8.
- Case 2: , , , ; choose different values of 1, 3, 9, and vary from 1.0 to 2.0.
- Case 3: , , , ; select different values of 1, 3, 9, and vary from 0.8 to 2.0.
- Case 4: , , , ; select different values of 1, 3, 9, and vary from 0.2 to 0.5.
- Case 5: , , , ; choose different values of 1, 3, 9, and vary from 3.0 to 5.0.
Figure 4, Figure 5, Figure 6, Figure 7 and Figure 8 show the sensitivity performance of the expected cost with respect to , , , , and for various values of 1, 3, 9. We should note that the sign of sensitivity reveals the monotonicity of the expected cost by changing the values of system parameters. Figure 4 reveals that (i) is positive, which means that incremental change of increases the expected cost; (ii) increases as increases for all ; and (iii) as is fixed, becomes larger as increases. It appears from Figure 5 that (i) is negative, which means that incremental change of decreases the expected cost; and (ii) increases as increases for all . Figure 6 shows that (i) is negative, which means that incremental change of decreases the expected cost; (ii) increases as increases; and (iii) as is fixed, becomes larger as decreases. Moreover, has a smaller increasing shape than . We observe from Figure 7 that (i) is positive; (ii) increases as increases for all ; (iii) as is fixed, increases as increases. It can be seen in Figure 8 that (i) is negative; (ii) increases as increases; and (iii) as is fixed, decreases as increases.
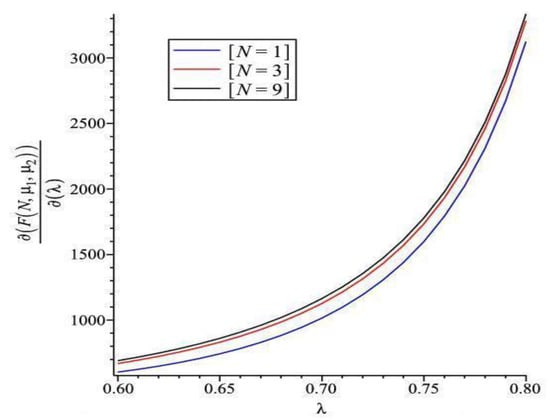
Figure 4.
Sensitivity analysis of F with respect to for different ().
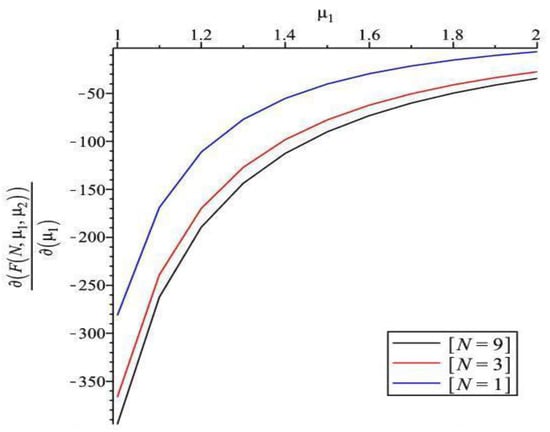
Figure 5.
Sensitivity analysis of F with respect to for different ().
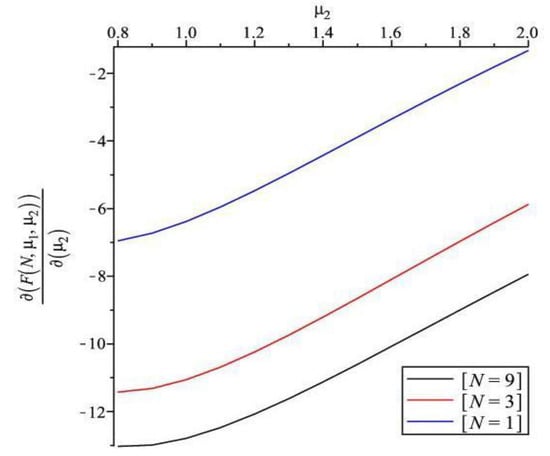
Figure 6.
Sensitivity analysis of F with respect to for different ().
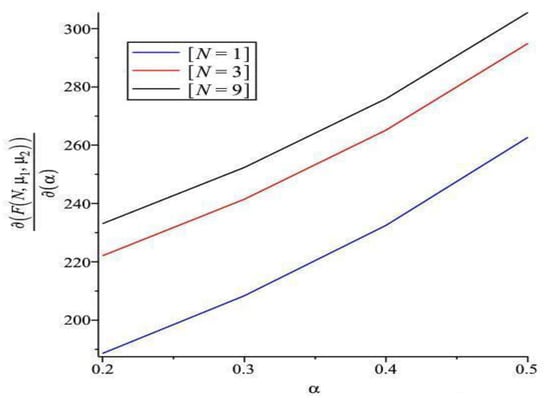
Figure 7.
Sensitivity analysis of F with respect to for different ().
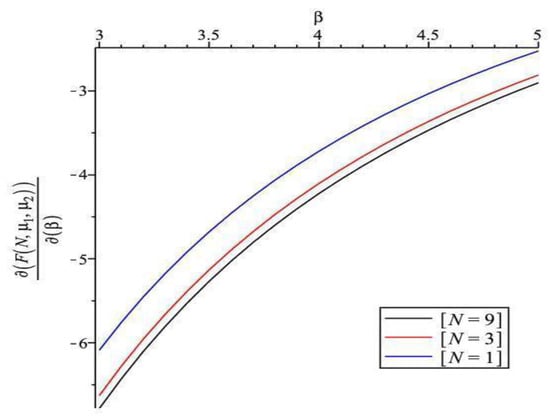
Figure 8.
Sensitivity analysis of F with respect to for different N ().
6. Conclusions
This paper studied the N policy M/G/1 queue with working breakdowns. Steady-state probabilities were obtained by means of the supplementary variable and probability generating function techniques. The expected cost function per unit time was established to determine the joint optimal values of until the stability constraint is satisfied. More especially, an efficient and useful method (two-stage optimization method) was utilized to search the optimal joint values of that minimize the cost function. Sensitivity analysis of the cost function has been performed for specific values of the system parameters , , , , and , as well as various values of .
Author Contributions
All authors contributed equally and significantly in this paper submission. All authors have read and agreed to the published version of the manuscript.
Funding
This paper was partially supported by Ministry of Science and Technology, Taiwan, ROC, under contract number: MOST-103-2221-E-126-004-MY3.
Acknowledgments
The authors would like to thank two anonymous referees for their helpful comments on this paper that significantly improved the quality of the paper.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Yadin, M.; Naor, P. Queueing systems with a removable service station. Oper. Res. Quar. 1963, 14, 393–405. [Google Scholar] [CrossRef]
- Jayachitra, P.; Albert, A.J. Recent developments in queueing models under N-policy: A short survey. Int. J. Math. Arch. 2014, 5, 227–233. [Google Scholar]
- Kalidass, K.; Kasturi, R. A queue with working breakdowns. Comput. Ind. Eng. 2012, 63, 779–783. [Google Scholar] [CrossRef]
- Liou, C.-D. Markovian queue optimisation analysis with an unreliable server subject to working breakdowns and impatient customers. Int. J. Syst. Sci. 2015, 46, 2165–2182. [Google Scholar] [CrossRef]
- Kim, B.K.; Lee, D.H. The M/G/1 queue with disasters and working breakdowns. Appl. Math. Modell. 2014, 38, 1788–1798. [Google Scholar] [CrossRef]
- Wang, K.-H.; Ke, J.-C. Control policies of an M/G/1 queueing system with a removable and non-reliable server. Inter. Trans. Oper. Res. 2002, 9, 195–212. [Google Scholar] [CrossRef]
- Wang, K.-H. Optimal operation of a Markovian queueing system with a removable and non-reliable server. Microelectron. Reliab. 1995, 35, 1131–1136. [Google Scholar] [CrossRef]
- Ke, J.-C.; Pearn, W.L. Optimal management policy for heterogeneous arrival queueing systems with server breakdowns and vacations. Qual. Tech. Quant. Manag. 2004, 1, 149–162. [Google Scholar] [CrossRef]
- Wang, K.-H.; Wang, T.-Y.; Pearn, W.L. Maximum entropy analysis to the N policy M/G/1 queueing system with server breakdowns and general startup times. Appl. Math. Comput. 2005, 165, 45–61. [Google Scholar] [CrossRef]
- Ke, J.-C.; Lin, C.-H. Maximum entropy approach for batch-arrival queue under N policy with an un-reliable server and single vacation. J. Comput. Appl. Math. 2008, 221, 1–15. [Google Scholar] [CrossRef]
- Wang, K.-H.; Wang, T.-Y.; Pearn, W.L. Optimal control of the N policy M/G/1 queueing system with server breakdowns and general startup times. Appl. Math. Modell. 2007, 31, 2199–2212. [Google Scholar] [CrossRef]
- Jain, M.; Bhargava, C. N-policy machine repair system with mixed standbys and unreliable server. Qual. Tech. Quant. Manag. 2009, 6, 171–184. [Google Scholar] [CrossRef]
- Vemuri, V.K.; Boppana, V.S.N.H.P.; Kotagiri, C.; Bethapudi, R.T. Optimal strategy analysis of an N-policy two-phase MX/M/1 queueing system with server startup and breakdowns. OPSEARCH 2011, 48, 109–122. [Google Scholar] [CrossRef]
- Singh, C.J.; Jain, M.; Kumar, B. Analysis of queue with two phases of service and m phases of repair for server breakdown under N-policy. Int. J. Serv. Oper. Manag. 2013, 16, 373–406. [Google Scholar] [CrossRef]
- Yang, D.-Y.; Ke, J.-C. Cost optimization of a repairable M/G/1 queue with a randomized policy and single vacation. Appl. Math. Modell. 2014, 38, 5113–5125. [Google Scholar] [CrossRef]
- Chen, W.L.; Wang, K.-H. Reliability analysis of a retrial machine repair problem with warm standbys and a single server with N-policy. Reliab. Eng. Syst. Saf. 2018, 180, 476–486. [Google Scholar] [CrossRef]
- Cox, D.R. The analysis of non-Markovian stochastic processes by the inclusion of supplementary variables. Proc. Camb. Philos. Soc. 1955, 51, 433–441. [Google Scholar] [CrossRef]
- Nocedal, J.; Wright, S.J. Numerical Optimization; Springer Series in Operations Research; Springer: New York, NY, USA, 1999. [Google Scholar]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).