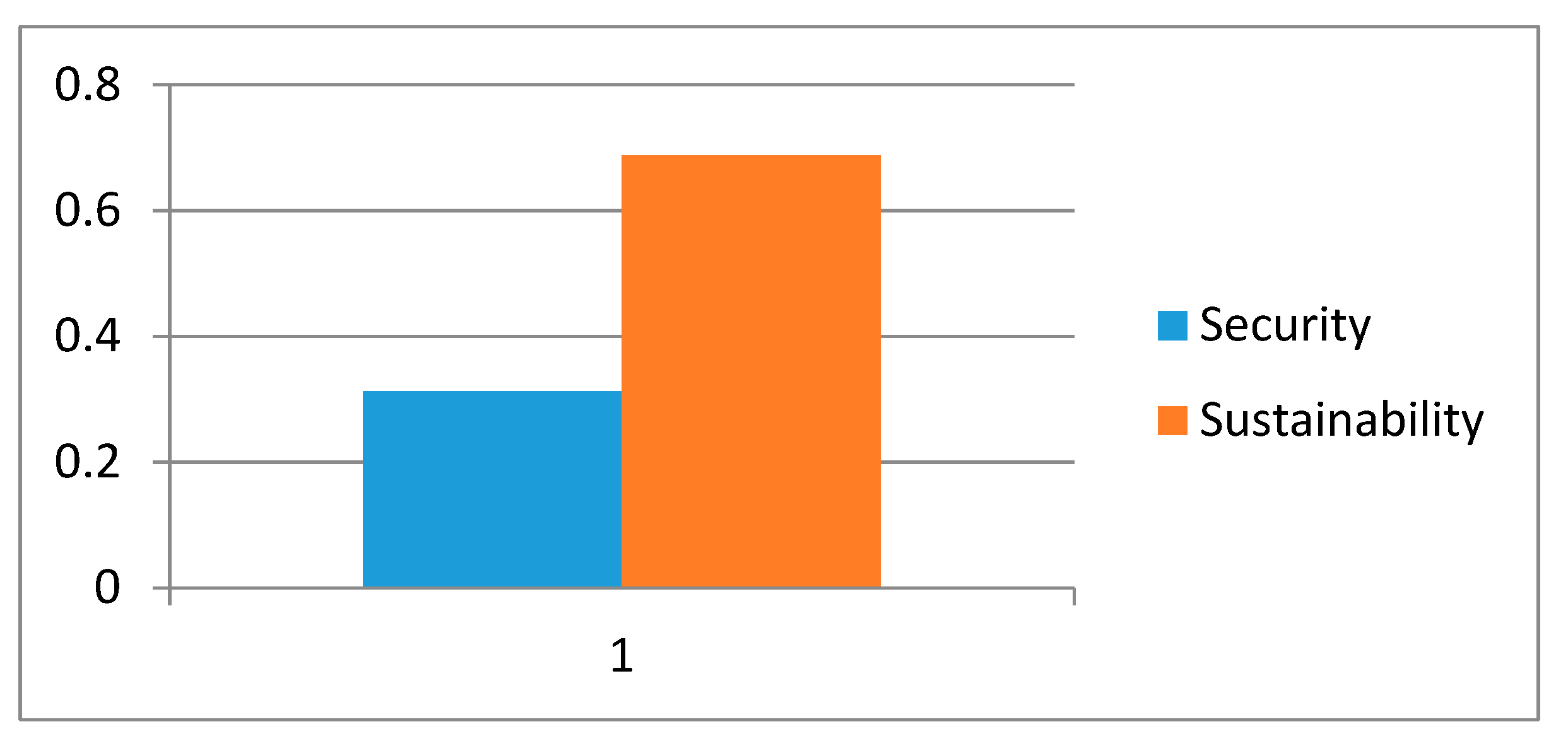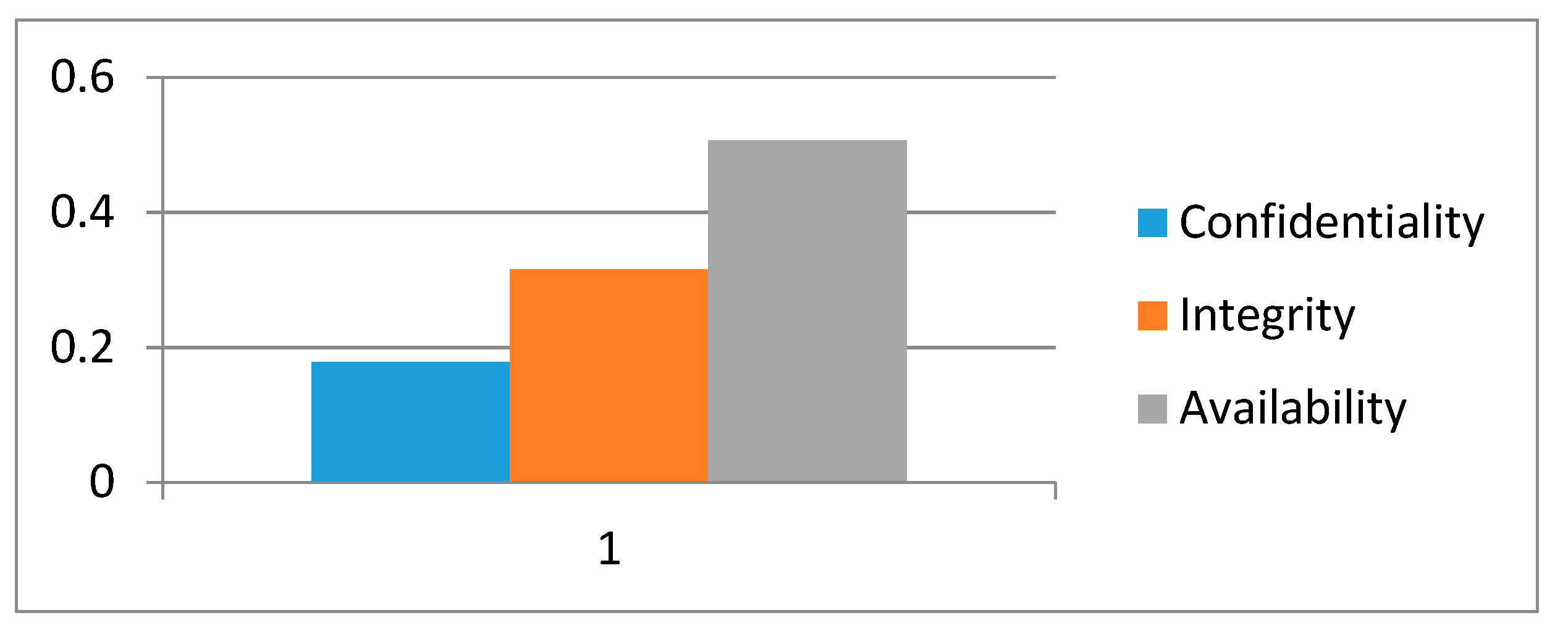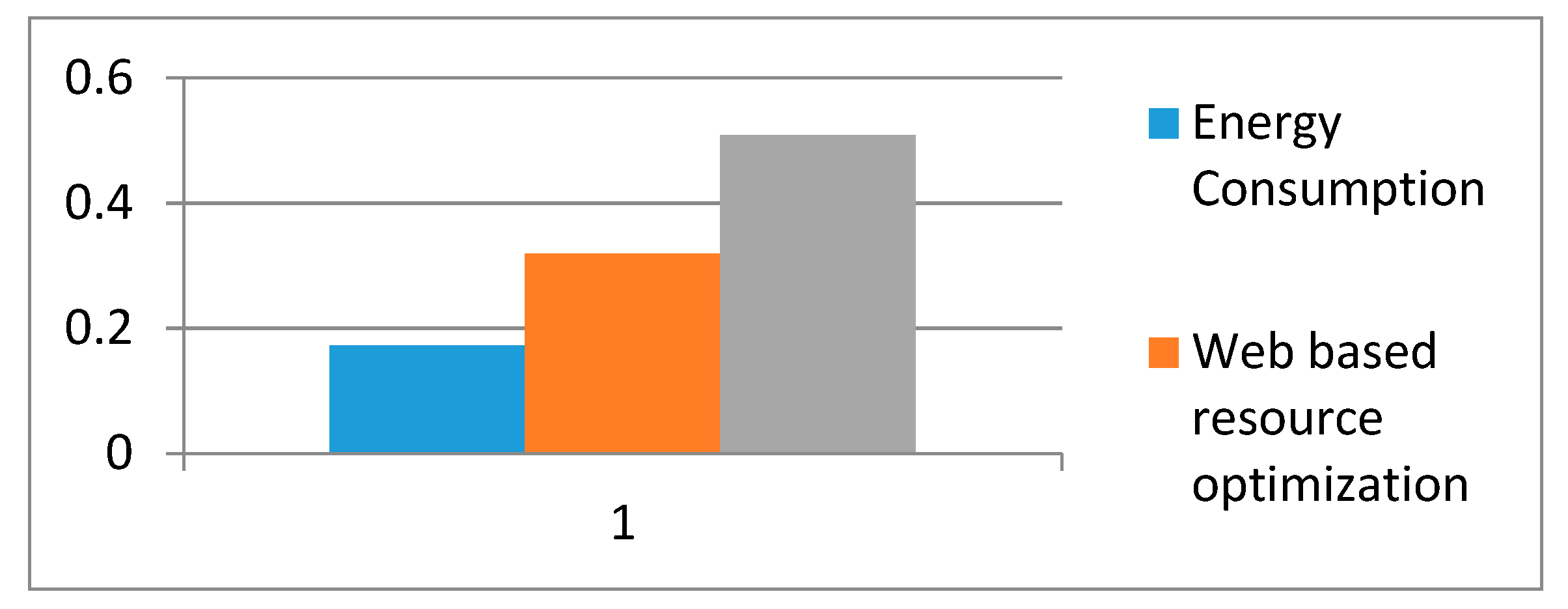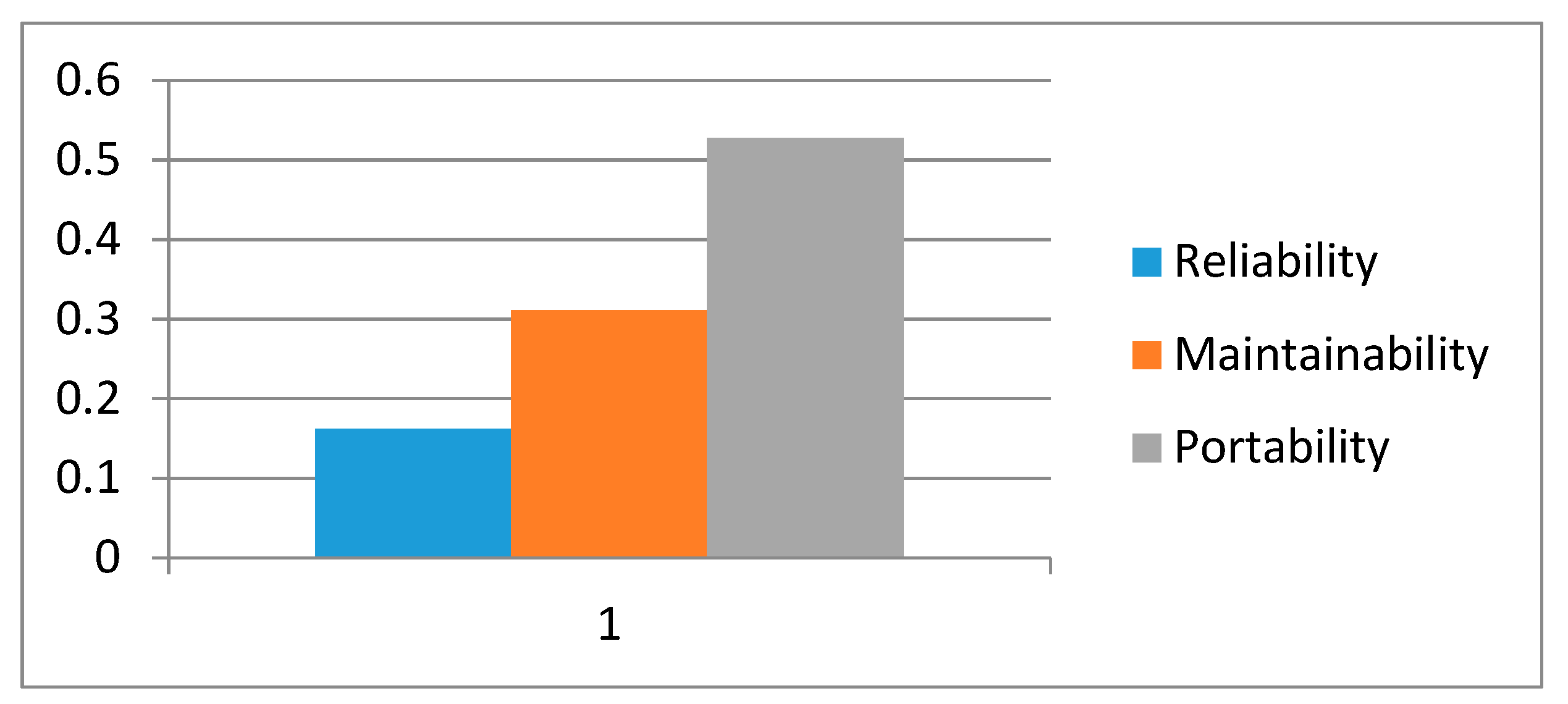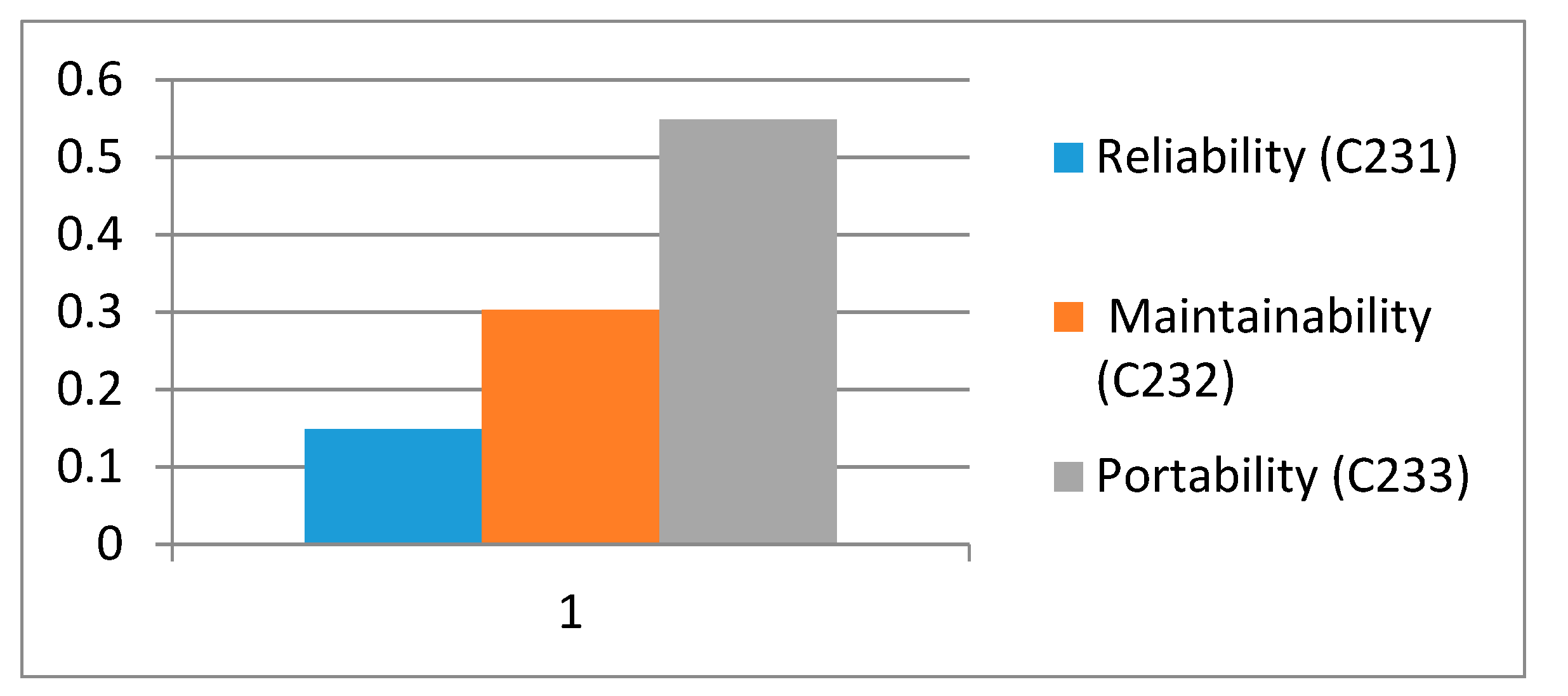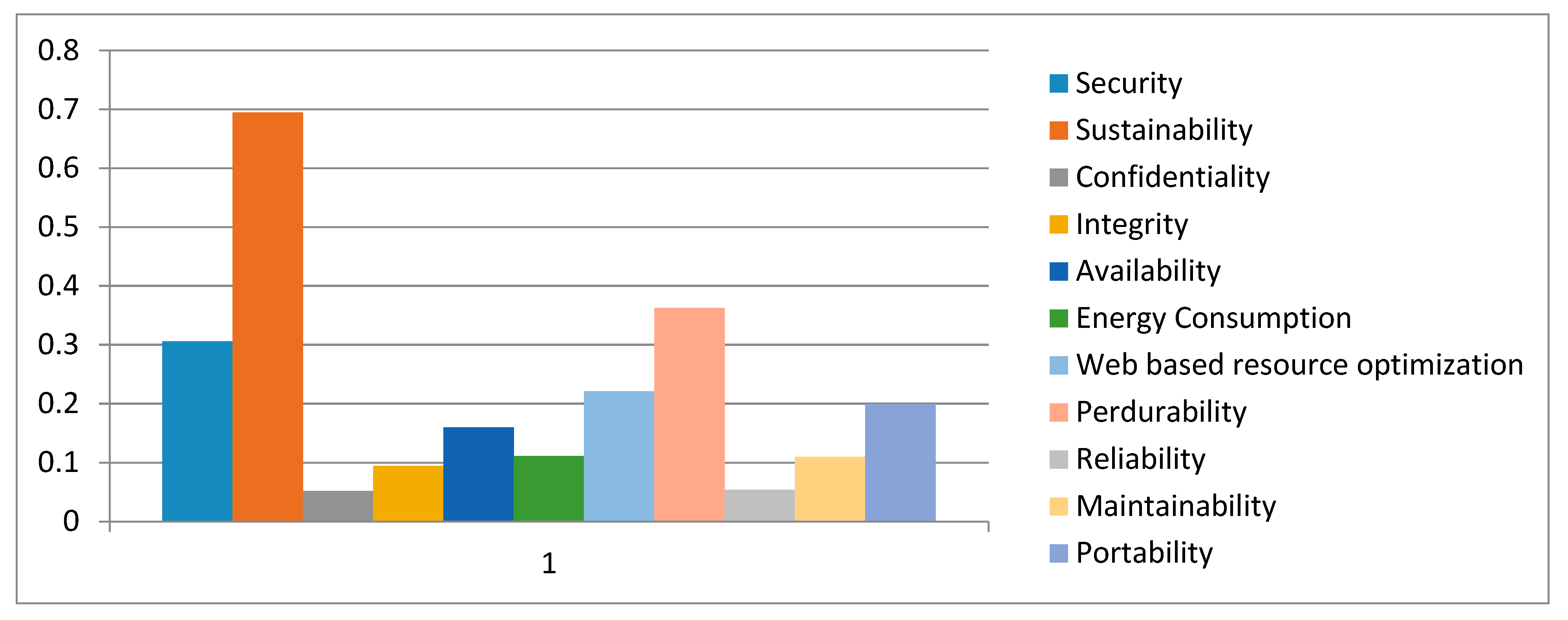3.1. Results through Fuzzy-AHP
For the most part, subjective evaluation is reasonable for assessing sustainable-security. It is hard to assess web application security in a quantitative manner. Worldwide aggregate activity prompted the detailing of formulation of sustainability policy. Lately, specialists have embraced sustainability policies to a great extent [
5,
6,
7] with successful outcomes. Likewise, development agencies are attempting to embrace high web applications security. What is more, the impact of sustainable-security factors plays an exceptional role in sustainable-security during web application development process [
41].
The paper presents a way for sustainable-security assessment with the assistance of Fuzzy-AHP. For collecting data, authors have taken the opinions of 110 experts who hail from academia as well as industry; these academicians and researchers were brought together in a simulated meeting situation. These professionals had more than 10 years of experience in web application development and had relevant expertise in using these models in symmetrical and sustainable environment. They discussed the factors with respect to different groups and gave linguistic values with the help of a scale. This contribution intends to gauge the web applications sustainable-security using the experts’ inputs.
To appraise the sustainable-security, ten successive versions of two different developed web applications for Lucknow-India-Based Central University (Babasaheb Bhimrao Ambedkar University), including A1, A2, A3 A4, and A5 for project 1 and A6, A7, A8, A9, and A10 for project 2, have been taken. Both of these web applications are highly sensitive for their data and agree that working on their security in a sustainable manner is important. Year-wise, different versions of a web application for the entrance exam of the University are called A1, A2, A3 A4, and A5 [
40], and year-wise, different versions of a web application for national online quiz competition are called A6, A7, A8, A9, and A10 [
42]. To measure the top version,
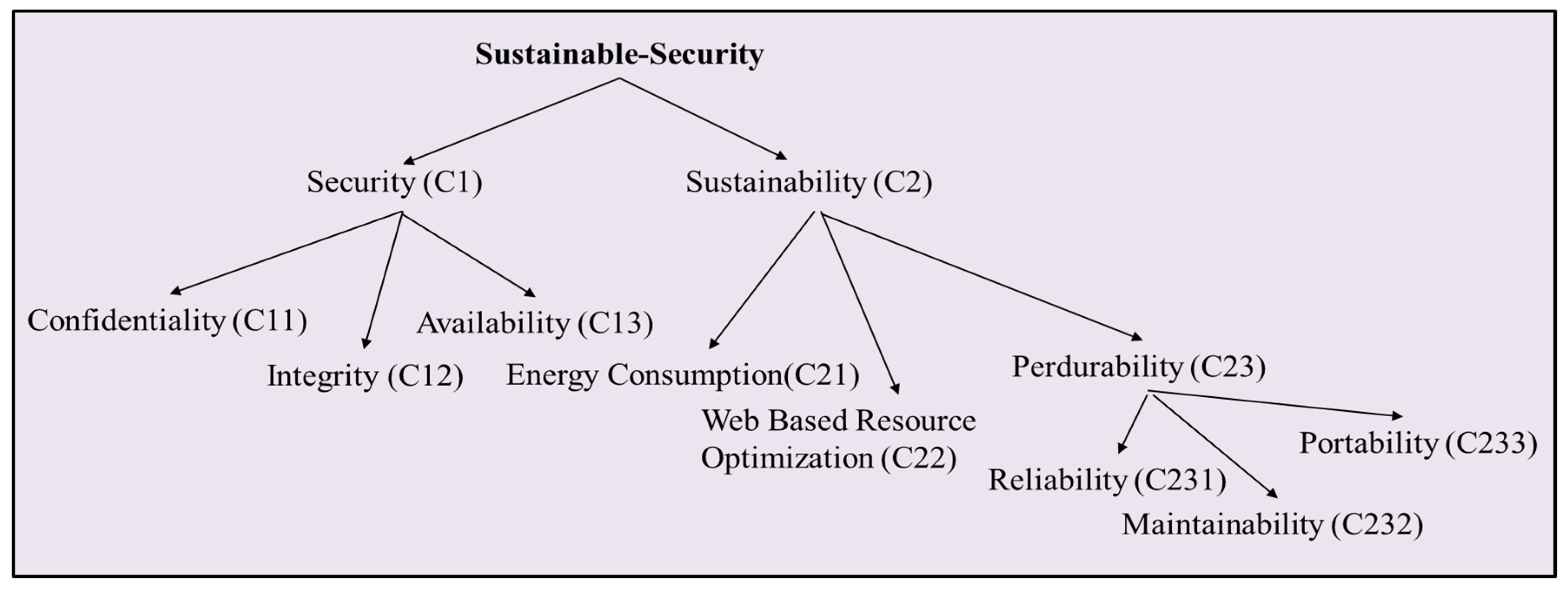
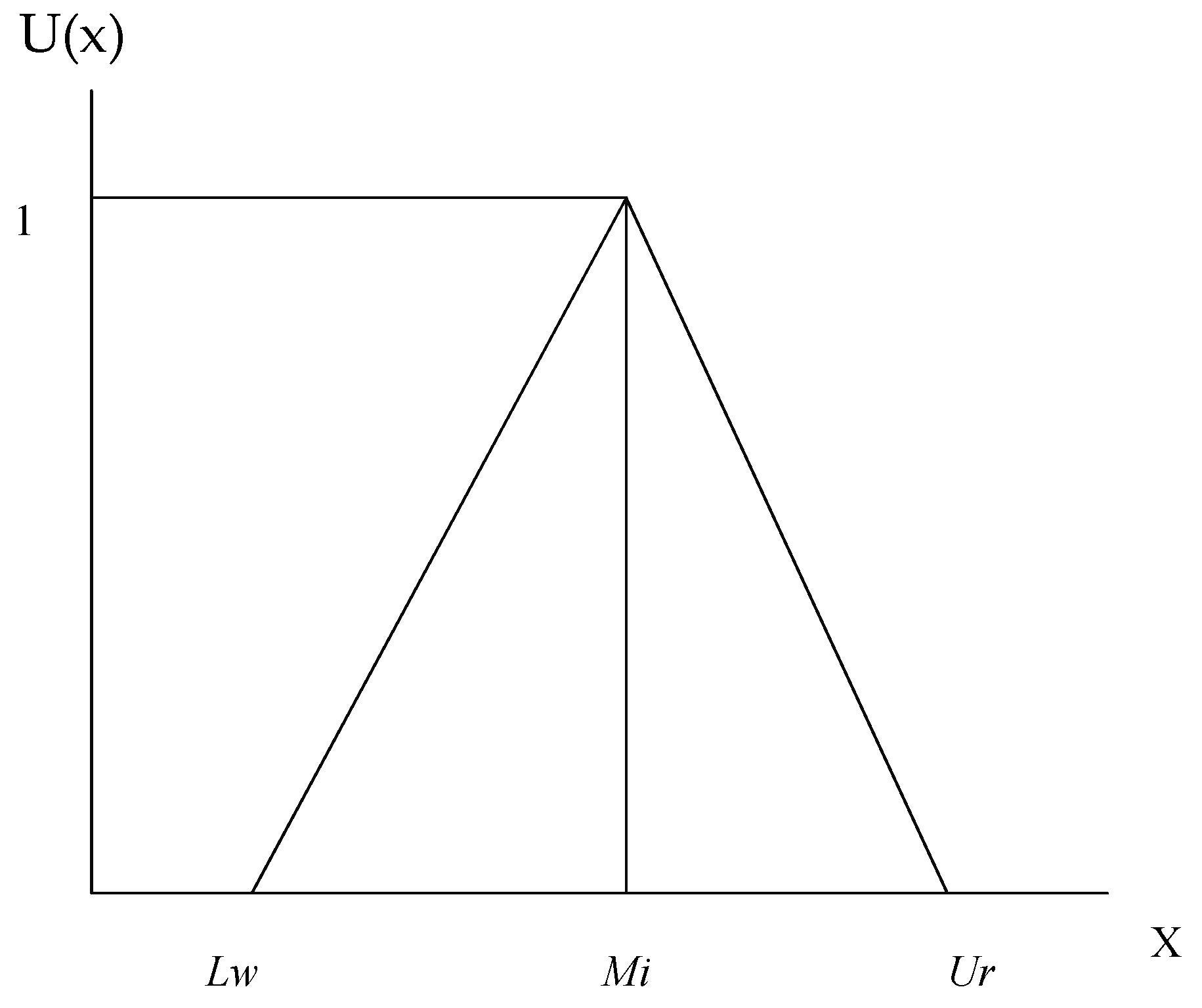
Figure 1 shows the hierarchal structure of the sustainable-security factors. With the help of Equations (1-4), triangular fuzzy numbers are evaluated. After qualitative assessment,
Table 2,
Table 3,
Table 4 and
Table 5 show a comparison that is matrix-pairwise (aggregated fuzzy) for different levels.
Table 2 shows the aggregated pairwise comparison matrix for level 1 by using fuzzy-AHP, which contains only two factors: security and sustainability.
Table 3 shows a Comparison Matrix Pairwise (Fuzzy Aggregated) for level 2, which contains three factors, including confidentiality, integrity, and availability.
Table 4 shows the aggregated comparison matrix pairwise for level 2 by using fuzzy-AHP, which contains three factors: confidentiality, integrity, and availability.
Table 5 shows the aggregated comparison matrix-pairwise for level 3 by using fuzzy-AHP, which contains three sub-factors: reliability, maintainability, and portability. According to the hierarchy,
Table 2,
Table 3,
Table 4 and
Table 5 show a comparison matrix-pairwise (fuzzy aggregated) at levels 1–3. From Equations (5)–(8), this paper derived the defuzzified values and local weights. The relative importance of the security and sustainability factors in the TFN value is weighted as (0.3127, 0.4395, and 0.6252). Then, with the help of Equation (6),
ρ0.5(Lw12) = (Misecurity-sustaiability − Lwsecurity-sustaiability) * 0.5 + Lwsecurity-sustaiability
ρ0.5(Lwsecurity-sustaiability) = (0.4395 − 0.3127) * 0.5 + 0.3127 = 0.3761
From Equation (7), ρ0.5(Ursecurity-sustaiability) = Ursecurity-sustaiability − (Ursecurity-sustaiability − Misecurity-sustaiability) * 0.5
ρ0.5(Ursecurity-sustaiability) = 0.6252 − (0.6252 − 0.4395) * 0.5 = 0.5324
With the help of Equation (5),
ρ0.5, 0.5 (Ãsecurity-sustaiability) = [0.5 * 0.3761 + (1 − 0.5) * 0.5324] = 0.4542
ρ0.5, 0.5 (Ãsustainability-security) = 2.2017
From Equations (8) and (9), with respect to other criteria, the weights of particular criteria may be acquired as
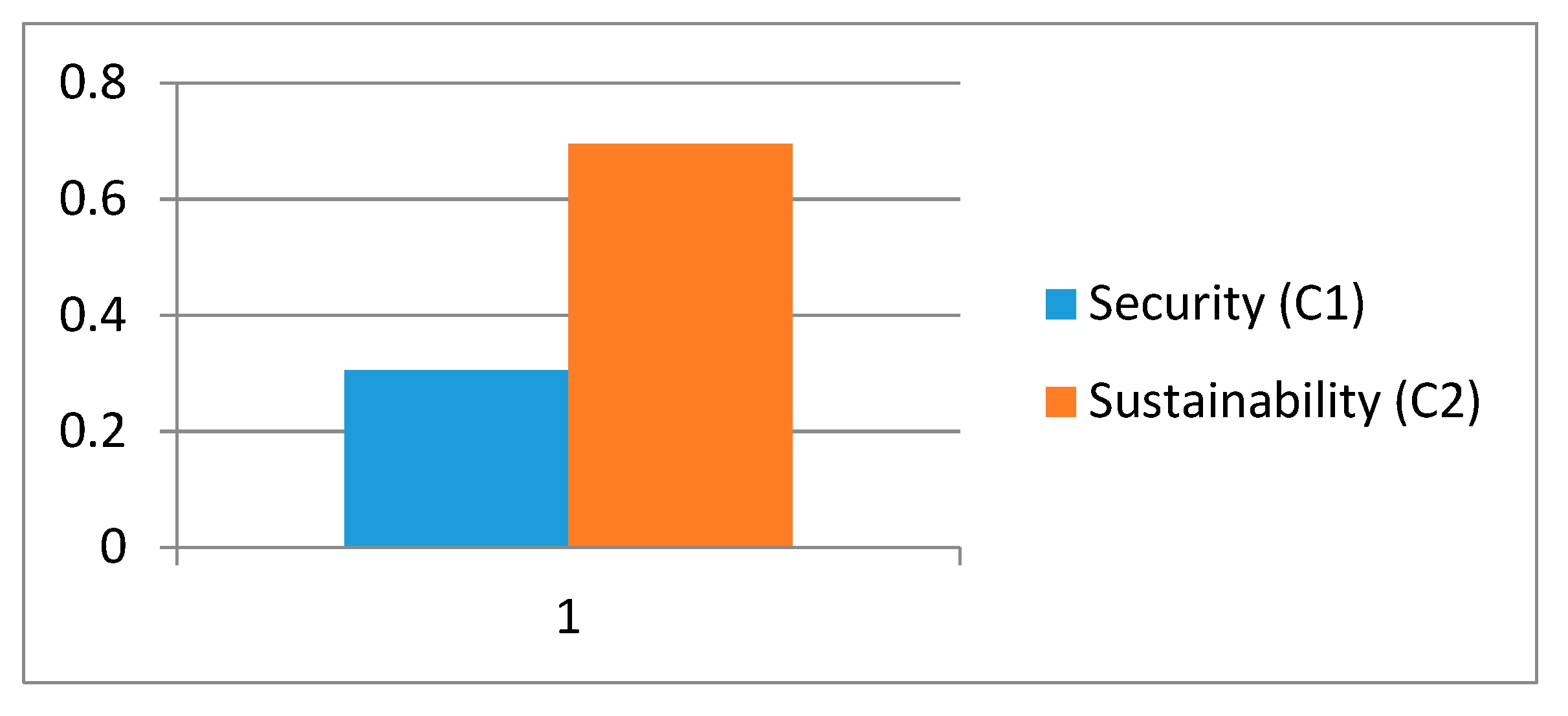
Table 6 shows the local weights of level 1 factors. From the results, it is evident that sustainability is a more important factor than security for balancing the sustainable-security.
Figure 3 shows the graphical representation of local weights of level 1 factors.
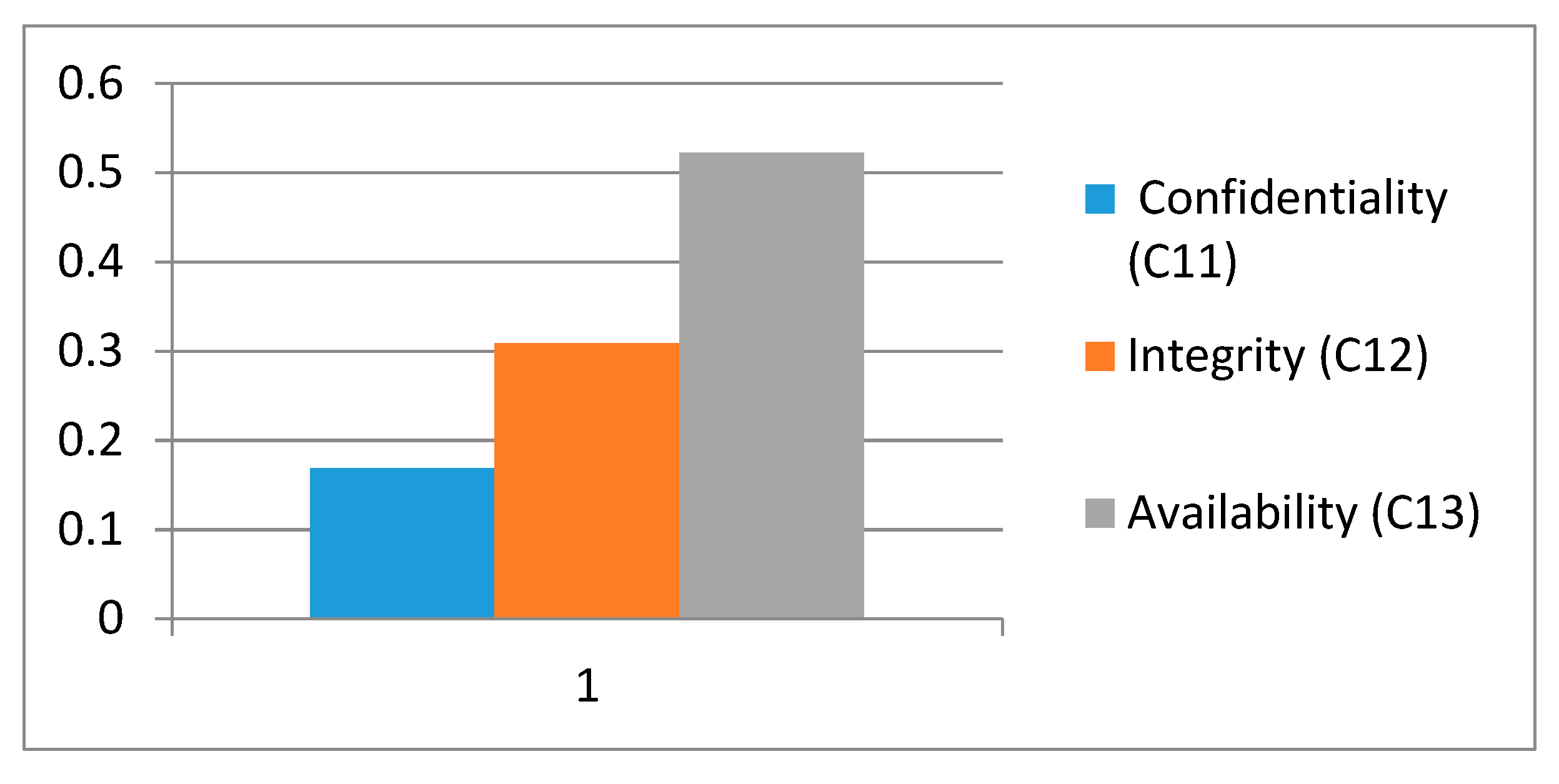
Table 7 shows the local weights of level 2 factors of security. From the results, it is evident that availability is an important factor among the three factors of this level.
Figure 4 shows the graphical representation of local weights of level 2 factors.
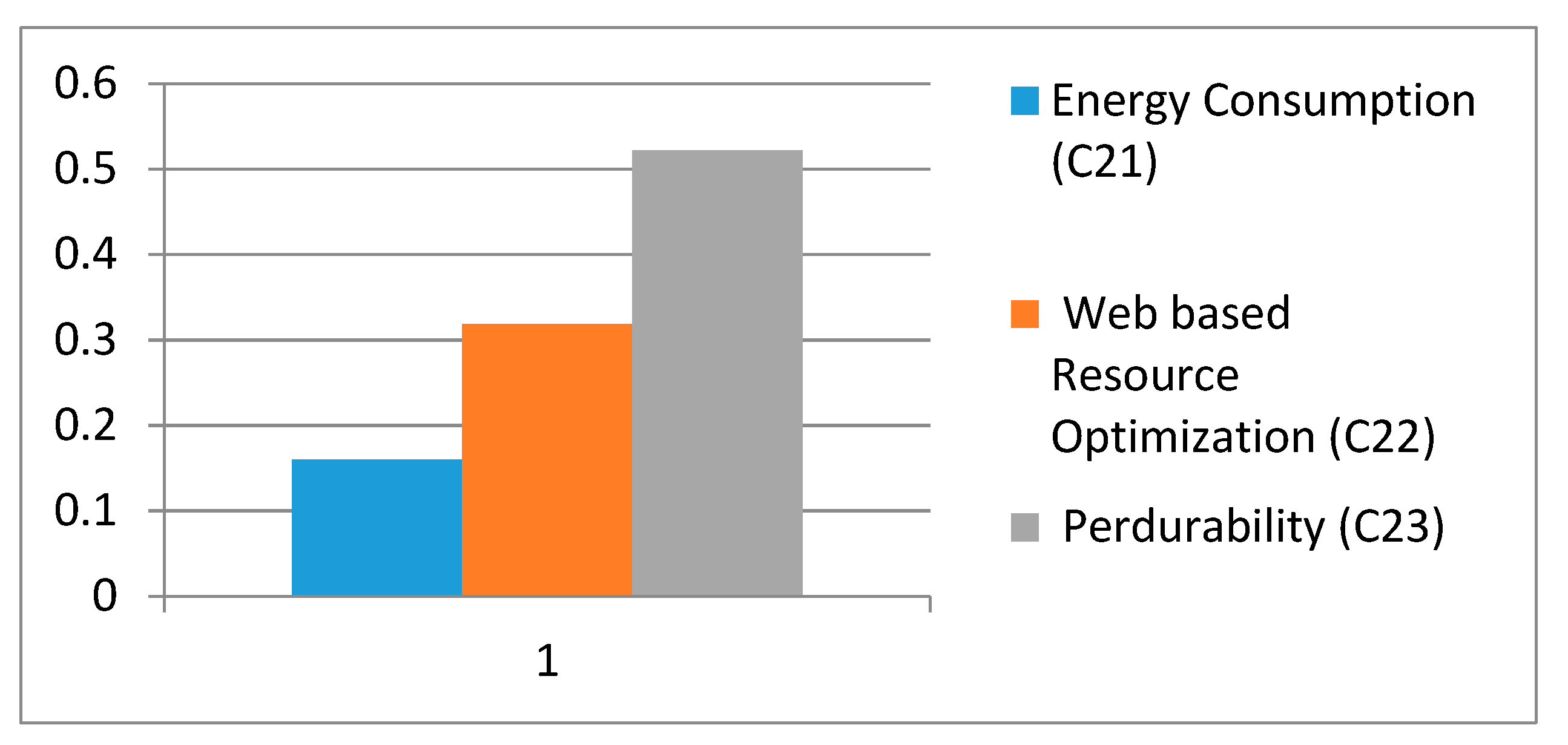
Table 8 shows the local weights of level 2 factors of sustainability. From the results, it is evident that perdurability is an important factor among the three factors of this level.
Figure 5 shows the graphical representation of local weights of level 2 factors of sustainability.
Table 9 shows the local weights of level 3 sub-factors of perdurability, and it is evident from the results that portability has the highest weight.
Figure 6 shows the graphical representation of level 3 sub-factors. From the results, it is evident that maintainability is an important factor among the three factors of this level.
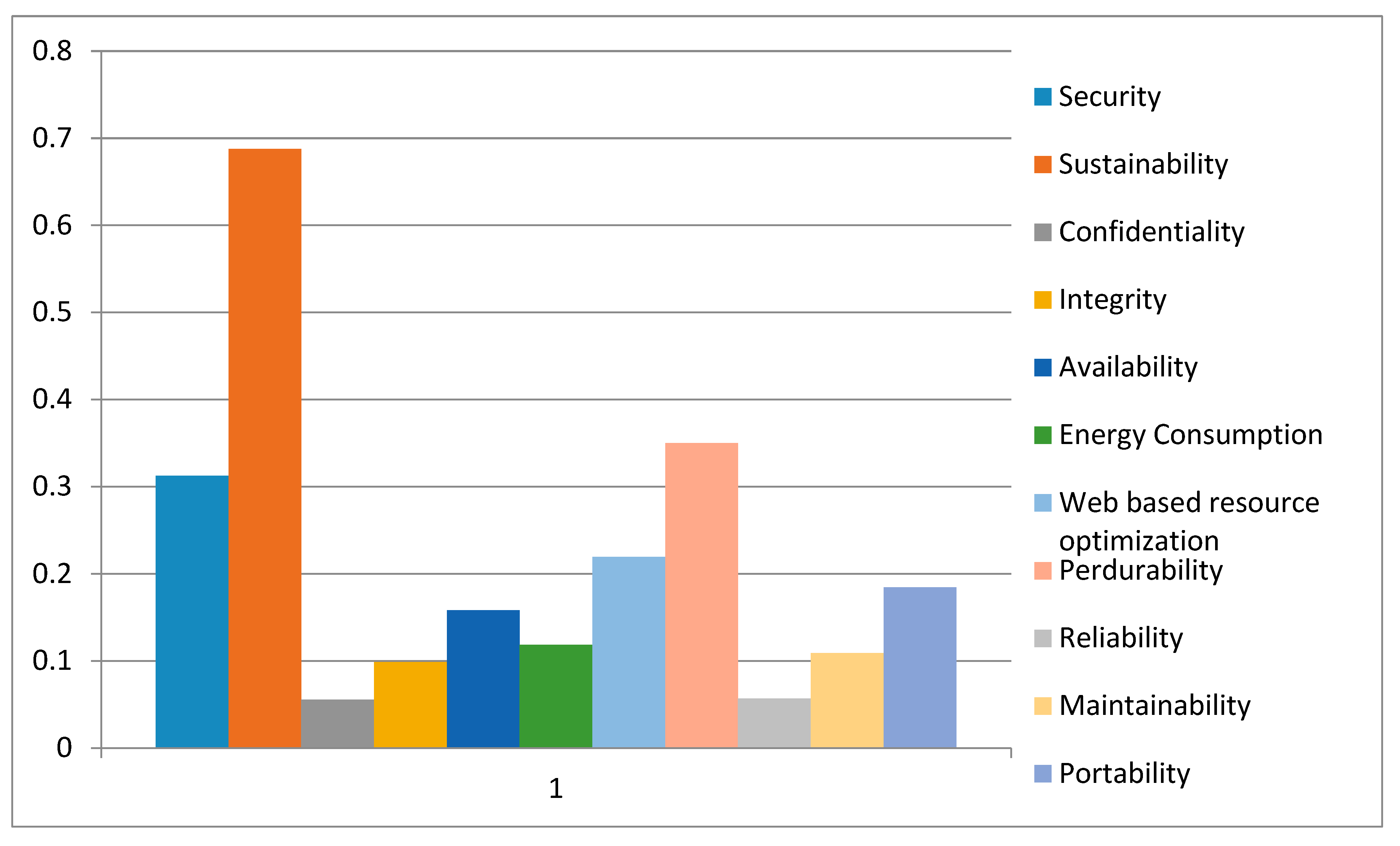
Table 10 shows the final or global weights and the overall priorities of the tree structure. Where A1, A2, A3……An, symbols are described as the alternatives and objective weights of the criteria that are stated in
Table 10.
The combined significances of levels 2 and 3 are then persevered by aggregating the weights throughout the hierarchy. In sustainable-security, security has 0.3123 weight and sustainability has 0.6877 weight. This implies that security is more significant than sustainability to achieve sustainable-security at its best. For security, confidentiality has 0.0557 weight, integrity has 0.0985 weight, and availability has 0.1581 weight, and therefore availability is most important for sustainable-security. For sustainability, the final weight of energy consumption is 0.1185, the weight of web based resource optimization is 0.2193, and the weight of perdurability is 0.3499.
Among these three, the weighting of perdurability is highest. This indicates that improvement in sustainable-security can be achieved by focusing on perdurability.
Figure 7 shows the final weights of factors from the hierarchy shown in
Figure 1 and the results show that sustainability has the highest weight among all. The three sub-factors of perdurability have the following final weights, reliability is 0.0566, maintainability is 0.1088, and portability is 0.1845. The value of sustainable-security for different alternatives has been evaluated as below.
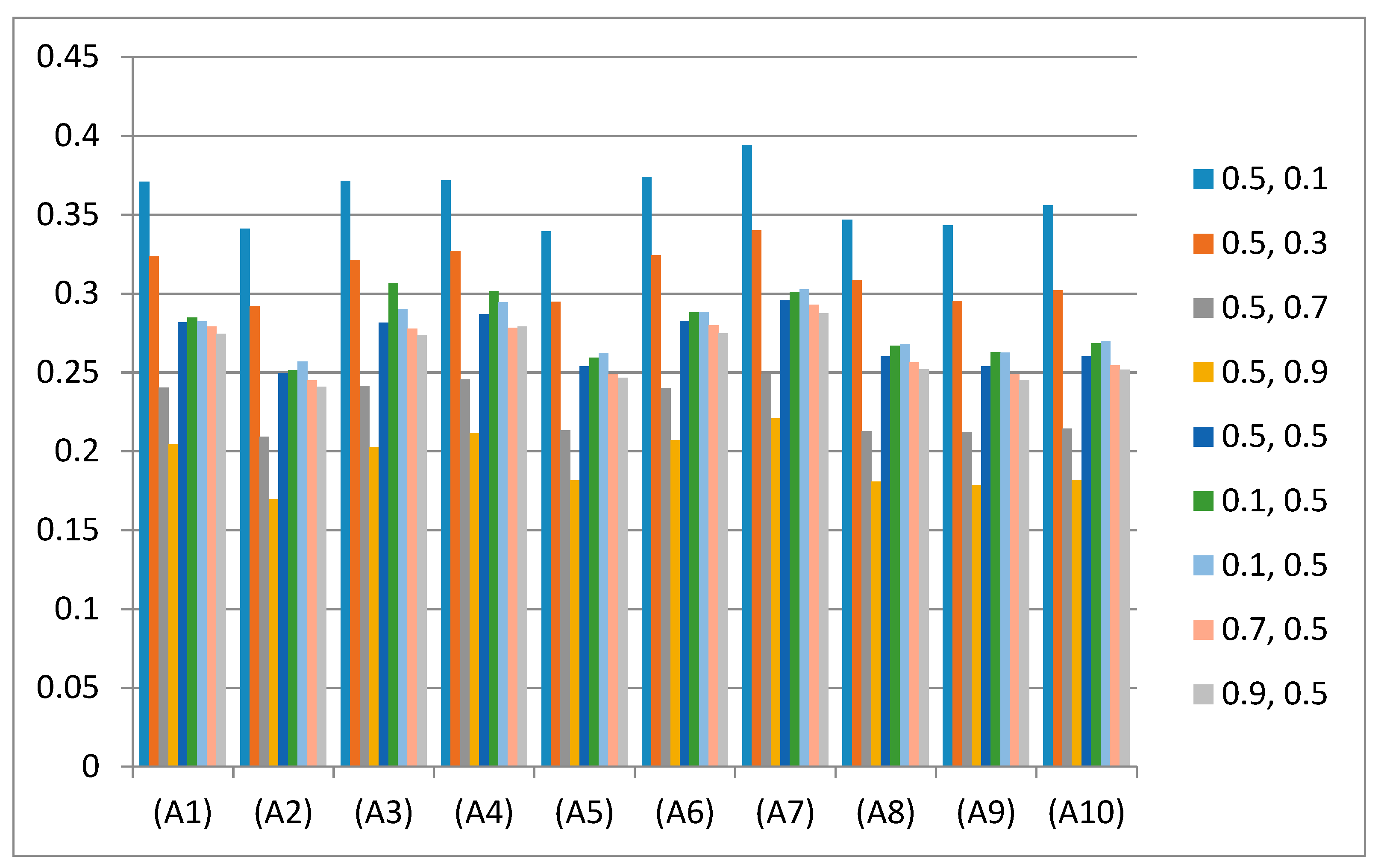
Impacts of sustainable-security for altered options are assessed as 0.2817, 0.2495, 0.2814, 0.2870, 2540, 2826, 0.2956, 0.2601, 0.2538, and 0.2602 for A1, A2, A3, A4, A5, A6, A7, A8, A9, and A10, respectively. The results show the A7 have highly sustainable-security in all alternatives web application of BBA University.
3.3. Results through Classical-AHP
After estimating the sustainable-security of web applications with the Fuzzy-AHP technique, the classical-AHP method was also used in this section to prove the accuracy of the whole assessments and outcomes. AHP is a useful resource for resolving unstructured issues in economics, and social and information sciences [
38,
40]. In classical-AHP, the manner of records collection and assessment identical to the Fuzzy-AHP, but the sole distinction is that no fuzzification and defuzzification are required. Therefore, the information is taken in its original shape for classical-AHP. Further, according to the set of sustainable-security factors through the hierarchy, the relative independent weights and priorities of each set of factors have been depicted in
Table 12,
Table 13,
Table 14 and
Table 15.
Table 12 shows the local weights of security and sustainability through classical-AHP.
Figure 9 shows a graphical representation of the local weights of level 1 factors.
Table 13 shows the local weights of level 2 factors, which are Confidentiality, integrity, and availability. Among these, availability has the highest weight.
Figure 10 shows the graphical representation of second-level factors.
Table 14 shows the local weights of level 2 factors. Among these, perdurability has the highest weight for improving the whole sustainable-security.
Figure 11 shows the graphical representation of second level factors.
Table 15 shows the local weights of level 3 factors. Among these, portability has the highest weight for improving the whole sustainable-security.
Figure 12 shows the graphical representation of third level factors. According to the hierarchy,
Table 16 and
Figure 13 show the dependent weights and an overall ranking of the hierarchy. Also, the results of all weights after applying it to project 1 and 2 are depicted in the
Table 16.
The eleven evaluative criteria are weighted as follows, security (0.3053), sustainability (0.6947) confidentiality (0.0515), integrity (0.0942), availability (0.1595), energy consumption (0.1110), web based resource optimization (0.2211), perdurability (0.3626), reliability (0.0538), maintainability (0.1099), and portability (0.1990), of which availability is most significant for sustainable-security of web application. The impact of sustainable-security in different alternatives is determined as follows.
Sustainable-security of different alternatives is estimated as 0.2885, 0.2491, 0.2809, 0.2878, 0.2536, 0.2834, 0.2966, 0.2607, 0.2531, and 0.2594 for A1, A2, A3, A4, A5, A6, A7, A8, A9, and A10 respectively. The results show the A7 has highly sustainable-security, i.e., version 2 of online quiz competition web application.
3.4. Comparison between Results
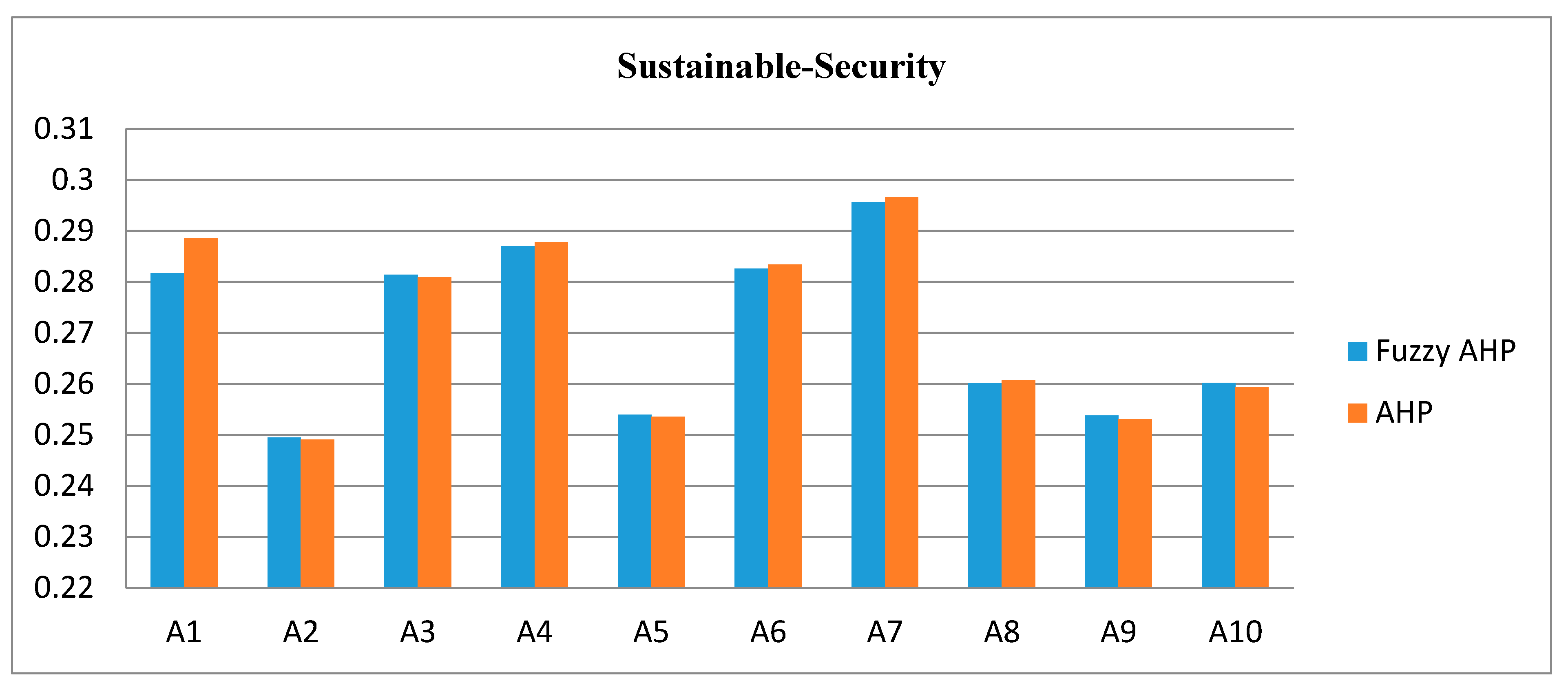
The difference between the impacts of sustainable-security of web applications through fuzzy-AHP and classical-AHP techniques is negligible as shown in
Table 17;
Figure 14 shows the graphical representation of the difference between the results.
As evident from the results, fuzzy-AHP and classical-AHP strategies have extraordinary procedures. Also, the outcomes are unique, yet fundamentally the same. This empirical work has taken the Pearson’s Correlation Method [
40] for assessing the correlation between outcomes. The correlation coefficient shows the impact of the relationship between two values. The scale lies between −1 and +1 [
43]. The value near to −1 shows the lower bonding between values, and the value near to +1 shows the tighter bonding between values. The Pearson correlation between the results of Fuzzy-AHP and AHP is 0.9935, which shows the strong correlation between the results achieved.
As given in
Table 17, the results with different approaches with same dataset have been obtained, and these results show that the correlation between the results of Fuzzy-AHP and AHP is highly correlated. Further, the results also show that the covered factors of sustainable-security and their contribution to efficient sustainable-security are remarkable. Alka Agrawal et al. recently published an article in which they assessed sustainable-security [
44]. This article contained first-level factors of security pillars in which three were CIA and one was perdurability. These factors were not very balanced because only one factor of sustainability was taken in that work.
In addition, according to the experts of Cigniti Solutions, sustainable-security depends fully on its contributing factors [
45]. Therefore, in the current paper, the authors have taken sustainability as a contributor in the first level of hierarchy, which improvises the results in the end. Additionally, for testing the results, Alka Agrawal et al. took six alternatives only, whereas this paper takes ten alternatives of a web application, which verifies the results. According to Alka Agrawal et al.,
perdurability was important, whereas, according to this work,
Sustainability at first level and
Web based Resource Optimization at second level are the most important attributes among all for maintaining sustainable-security of web applications.