2. General Results on Secure -Domination
Given a w-dominating function , we introduce the following notation.
Given , we define .
.
Given , we define .
Given , we define .
Obviously, if f is a secure w-dominating function, then for every .
Lemma 1. Let f be a secure w-dominating function on a graph G, and let . If , then each vertex belonging to is adjacent to every vertex in and, in particular, is a clique.
Proof. Since , we only need to suppose the existence of two non-adjacent vertices and with . In such a case, , which is a contradiction. Therefore, the result follows. □
Remark 1 ([
1]).
Let G be a graph of minimum degree δ and let . If , then there exists a w-dominating function on G if and only if Throughout this section, we repeatedly apply, without explicit mention, the following necessary and sufficient condition for the existence of a secure w-dominating function on G.
Remark 2. Let G be a graph of minimum degree δ and let . If , then there exists a secure w-dominating function on G if and only if
Proof. If f is a secure w-dominating function on G, then f is a w-dominating function, and by Remark 1 we conclude that
Conversely, if , then the function f, defined by for every , is a secure w-dominating function. Therefore, the result follows. □
It was shown by Cabrera et al. [
1] that the
w-domination numbers satisfy a certain monotonicity. Given two integer vectors
and
, we say that
if
for every
. With this notation in mind, we can state the next remark which is a direct consequence of the definition of
w-dominating function.
Remark 3. [
1]
Let G be a graph of minimum degree δ and let such that and for every . If and , then every w-dominating function is a -dominating function and, as a consequence, The monotonicity also holds for the case of secure w-domination.
Remark 4. Let G be a graph of minimum degree δ and let such that and for every . If and , then every secure w-dominating function is a secure -dominating function and, as a consequence, Proof. For any -function f and any with , there exists . Since f and are w-dominating functions, by Remark 3, we conclude that, if and , then both f and are -dominating functions. Therefore, f is a secure -dominating function and, as a consequence, □
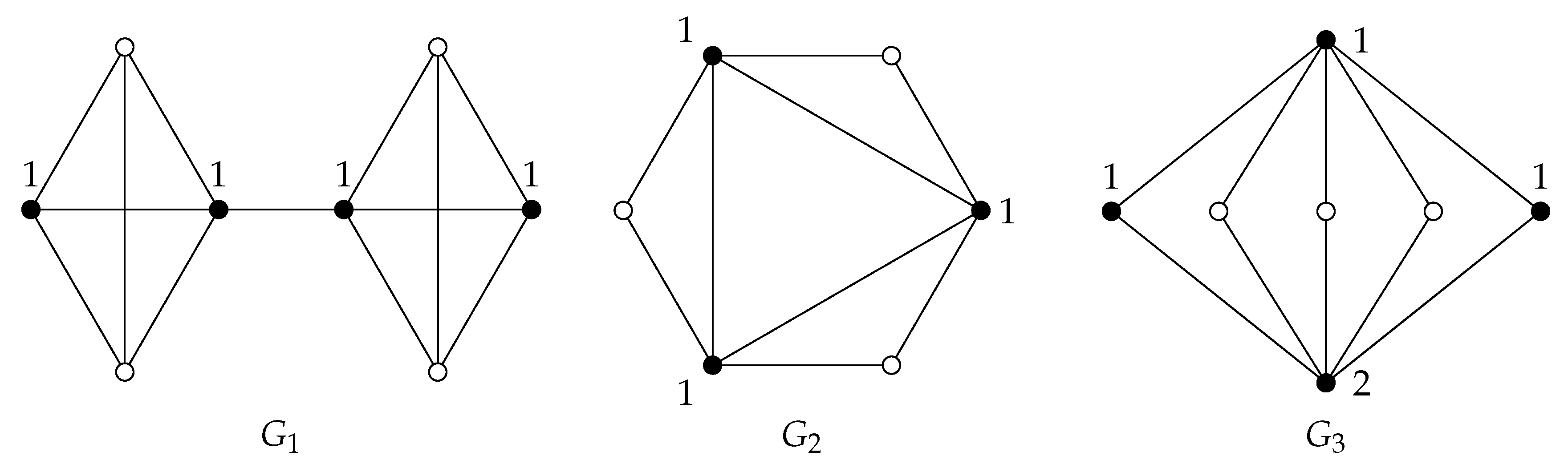
From the following equality chain, we obtain examples of equalities in Remark 4. Graph
is illustrated in
Figure 1.
Theorem 1. Let G be a graph of minimum degree δ, and let such that for every . If , then the following statements hold.
- (i)
- (ii)
If , then .
Proof. Since every secure w-dominating function on G is a w-dominating function on G, (i) follows.
Let be a -function. Since f is a -dominating function, for every with and . If , then f is a -dominating function, which implies that . Assume . Let and . If , then , which is a contradiction. Thus, , which implies that f is a -dominating function. Therefore, , and (ii) follows. □
The inequalities above are tight. For instance, for any integers , we have that and .
Corollary 1. Let G be a graph of minimum degree δ and order n. Let such that for every and . The following statements hold.
- (i)
If , then .
- (ii)
If , then .
Proof. Assume . By Theorem 1, we have that . Now, if , then for any -function f there exists at least one vertex such that and , which is a contradiction. Thus, .
Analogously, if , then Theorem 1 leads to . In this case, if , then for any -function f there exists at least one vertex such that and , which is a contradiction. Therefore, . □
As the following result shows, the bounds above are tight.
Proposition 1. For any integer n and any such that , Proof. Assume . Let such that if and otherwise. In both cases, the function , defined by , and whenever , is a secure w-dominating function. Hence, . Therefore, by Corollary 1 the result follows. □
Theorem 2. Let G be a graph of minimum degree δ, and let such that , and for every . If for every , and for every , then Proof. Assume that for every and for every . Let be a -function. We claim that f is a secure -dominating function. Since for every with , we deduce that f is a -dominating function. Now, let and with . We differentiate the following cases for .
Case 1. . In this case, and .
Case 2. . In this case, and .
Case 3. Assume . Notice that . Now, if or , then , while if , then .
According to the three cases above, is a -dominating function. Therefore, f is a secure -dominating function, and so □
The inequality above is tight. For instance, for .
From Theorems 1 and 2, we derive the next known inequality chain, where
G has minimum degree
, except in the last inequality in which
.
The following result is a particular case of Theorem 2.
Corollary 2. Let G be a graph of minimum degree δ, and let and 1 . If for every , where and , then For Graph
illustrated in
Figure 1, we have that
. Notice that
for
.
Next, we show a class of graphs where . To this end, we need to introduce some additional notation and terminology. Given the two Graphs and , the corona product graph is the graph obtained from and , by taking one copy of and copies of and joining by an edge every vertex from the ith copy of with the ith vertex of . For every , the copy of in associated to x is denoted by .
Theorem 3 ([
1])
. Let be a corona graph where does not have isolated vertices, and let . If and , then From the result above, we deduce that under certain additional restrictions on and w we can obtain .
Theorem 4. Let be a corona graph, where does not have isolated vertices and is a triangle-free graph. Let such that . If , then Proof. Since does not have isolated vertices, the upper bound is straightforward, as the function f, defined by for every and for the remaining vertices of , is a secure w-dominating function.
On the other hand, let be a -function and suppose that there exists such that . Since , there exist at least two different vertices . Hence, , which implies that u and v are adjacent and, since is a triangle-free graph, and for every . Thus, by Lemma 1, we conclude that is a clique, which is a contradiction as and is a triangle-free graph. This implies that for every , and so .
Therefore, , and by Theorem 3 we conclude that which completes the proof. □
Theorem 5. Let G be a graph of minimum degree δ and an integer. For any with and , Proof. Let be a -function and S a -set. We define a function as follows. Let , , and for every .
We claim that g is a secure -dominating function. First, we observe that, if with , then and . Moreover, if with , then and . Hence, g is a -dominating function.
Now, let . Notice that there exists a vertex with . Hence, . We differentiate the following cases for .
Case 1. . In this case, and, as , we obtain that .
Case 2. . In this case, and .
Case 3. Assume . Notice that . If or , then .
Moreover, if , then and so . Finally, if , then and therefore .
According to the three cases above, is a -dominating function. Therefore, f is a secure -dominating function, and so □
From Theorem 5, we derive the next known inequalities, which are tight.
Corollary 3. For a graph G, the following statements hold.
Ref. [
15]
. Ref. [
12]
, where G has minimum degree at least one. Ref. [
19]
.
To establish the following result, we need to define the following parameter.
In particular, for
and a graph
G of order
n, we have that
.
Theorem 6. Let G be a graph of minimum degree δ and order n. The following statements hold for any with .
- (i)
If there exists such that , then
- (ii)
If , then
- (iii)
Let such that , and let . If and for every , then
- (iv)
Let and . If and , then .
- (v)
If , then
Proof. If there exists such that , then for any -function we define a secure -dominating function by for every and for every . Hence, . Therefore, (i) follows.
Now, assume . Let S be a -set. Let f be the function defined by for every and for the remaining vertices. Since , we can conclude that f is a secure -dominating function. Therefore, , which implies that (ii) follows.
To prove (iii), assume that , and for every . Let be a -function. We construct a function as for every . Hence, for every , while for the remaining cases. Thus, for every with we have that , which implies that f is a -dominating function. Now, for every , there exists . Hence, for every with , we have that , which implies that is a -dominating function. Therefore, f is a secure -dominating function, and so . Therefore, (iii) follows.
Now, assume that and . Let be a -function. We construct a function as for every and for every . Hence, for every , and for the remaining cases. Thus, if and , then , and if , then . This implies that f is a -dominating function. Now, for every , there exists . Hence, if and , then , and if , then . This implies that is a -dominating function, and so f is a secure -dominating function. Therefore, , concluding that (iv) follows.
Furthermore, if
, then, by applying (iv) for
, we deduce that
Therefore, (v) follows. □
In the next subsections, we consider several applications of Theorem 6 where we show that the bounds are tight. For instance, the following particular cases is of interest.
Corollary 4. Let G be a graph of minimum degree δ, and let with .
- (i’)
If , then .
- (ii’)
If , then .
- (iii’)
If , then .
- (iv’)
Let . If and , then .
Proof. If , then by Theorem 6 (i) we conclude that (i’) and (ii’) follow. If , then by Theorem 6 (v) we deduce (iii’). Finally, if and , then by Theorem 6 (iii) we deduce that (iv’) follows. □
To show that the inequalities above are tight, we consider the following examples. For (i’), we have . For (ii’) we have for every graph G with universal vertices. Finally, for (iii’) and (iv’), we take and for every .
We already know that , for every . In contrast, the picture is quite different for the case of secure -domination, as there are graphs where the gap is arbitrarily large. For instance, , while, if , then .
Proposition 2. Let G be a graph of order n. Let such that . If is a spanning subgraph of G with minimum degree , then Proof. Let be the set of all edges of G not belonging to the edge set of . Let and, for every , let and , the edge-deletion subgraph of G induced by .
For any -function f and any with , there exists . Since f and are w-dominating functions on , both are w-dominating functions on , and so we can conclude that f is a secure w-dominating function on , which implies that . Hence, . □
As a simple example of equality in Proposition 2 we can take any graph
G of order
n, having
universal vertices. In such a case, for
we have that
From Proposition 2, we obtain the following result.
Corollary 5. Let G be a graph of order n and such that .
If G is a Hamiltonian graph and , then .
If G has a Hamiltonian path and , then .
To derive some lower bounds on , we need to establish the following lemma.
Lemma 2 ([
1])
. Let G be a graph with no isolated vertex, maximum degree Δ and order n. For any w-dominating function on G such that , Theorem 7. Let G be a graph with no isolated vertex, maximum degree Δ and order n. Let such that and . The following statements hold.
If and for every , then
If , then
If and for every , then
Proof. Let
and
for every
. Let
be a
-function. By Lemma 2, we deduce the following.
Therefore, Theorem 1 (ii) leads to
The proof of the remaining items is completely analogous. In the last two cases, we consider that is a -function, and we apply Theorem 1 (i) instead of (ii). □
The bounds above are sharp. For instance,
is achieved by Graph
shown in
Figure 1, the bound
is achieved by
for every
, the bound
is achieved by the corona graph
with
, while
is achieved by
,
and
with
and
.
To conclude the paper, we consider the problem of characterizing the graphs G and the vectors w for which takes small values. It is readily seen that if and only if , and . Next, we consider the case
Theorem 8. Let such that . For a graph G of order at least three, if and only if one of the following conditions holds.
- (i)
, and one of the following conditions holds.
.
, , and .
, and .
- (ii)
, , and .
- (iii)
and .
- (iv)
, , and .
Proof. Assume first that and let be a -function. Notice that and .
Firstly, we consider that , i.e., for some universal vertex . In this case, , , and for every . By Lemma 1, if , then is a clique, which implies that . Obviously, in such a case, . Finally, the case, and leads to , as . Therefore, (i) follows.
From now on, assume that . Hence, for every . If and , then and is a secure dominating set. Therefore, (ii) follows. If , then is a secure total dominating set of cardinality two, and so . Therefore, (iii) follows. Finally, assume . In this case, is a double dominating set of cardinality two, and by Lemma 1 we know that is a clique for any . Hence, and, in such a case, . Therefore, (iv) follows.
Conversely, if one of the four conditions holds, then it is easy to check that , which completes the proof. □