A Water Supply Pipeline Risk Analysis Methodology Based on DIY and Hierarchical Fuzzy Inference
Abstract
1. Introduction
2. Related Work
3. Proposed Methodology
4. Implementation, Results and Discussion
4.1. Implementation
4.2. Results of SHFL Model and Execution Results of DIY
5. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Kiefner, J.F.; Rosenfeld, M.J. The Role of Pipeline Age in Pipeline Safety; INGAA Foundation, INC: Worthington, DC, USA, 2012. [Google Scholar]
- Christodoulou, S.E. Water network assessment and reliability analysis by use of survival analysis. Water Resour. Manag. 2011, 25, 1229–1238. [Google Scholar] [CrossRef]
- Inanloo, B.; Tansel, B.; Shams, K.; Jin, X.; Gan, A. A decision aid gis-based risk assessment and vulnerability analysis approach for transportation and pipeline networks. Saf. Sci. 2016, 84, 57–66. [Google Scholar] [CrossRef]
- Christodoulou, S.; Aslani, P.; Deligianni, A. Integrated Gis-Based Management of Water Distribution Networks. In Proceedings of the International Conference on Computing and Decision Making in Civil and Building Engineering, Montreal, QC, Canada, 14–16 June 2006; pp. 14–16. [Google Scholar]
- Caleyo, F.; Velázquez, J.C.; Valor, A.; Hallen, J.M. Probability distribution of pitting corrosion depth and rate in underground pipelines: A monte carlo study. Corros. Sci. 2009, 51, 1925–1934. [Google Scholar] [CrossRef]
- Tang, X.; Liu, Y.; Zheng, L.; Ma, C.; Wang, H. Leak Detection of Water Pipeline Using Wavelet Transform Method. In Proceedings of the 2009 International Conference on Environmental Science and Information Application Technology, Wuhan, China, 4–5 July 2009; Volume 2, pp. 217–220. [Google Scholar]
- Kleiner, Y.; Rajani, B. Considering Time-Dependent Factors in the Statistical Prediction of Water Main Breaks. In Proceedings of the American Water Works Association Infrastructure Conference, Baltimore, MD, USA, 12–15 March 2000; pp. 12–15. [Google Scholar]
- Kleiner, Y.; Rajani, B. Forecasting variations and trends in water-main breaks. J. Infrastruct. Syst. 2002, 8, 122–131. [Google Scholar] [CrossRef]
- Zadeh, L.A. Fuzzy sets. Inf. Control 1965, 8, 338–353. [Google Scholar] [CrossRef]
- Lee, M.-L.; Chung, H.-Y.; Yu, F.-M. Modeling of hierarchical fuzzy systems. Fuzzy Sets Syst. 2003, 138, 343–361. [Google Scholar] [CrossRef]
- Fayaz, M.; Ullah, I.; Park, D.-H.; Kim, K.; Kim, D. An integrated risk index model based on hierarchical fuzzy logic for underground risk assessment. Appl. Sci. 2017, 7, 1037. [Google Scholar] [CrossRef]
- Fayaz, M.; Ahmad, S.; Ullah, I.; Kim, D. A blended risk index modeling and visualization based on hierarchical fuzzy logic for water supply pipelines assessment and management. Processes 2018, 6, 61. [Google Scholar] [CrossRef]
- Chang, C.-W.; Tao, C.-W. A simplified implementation of hierarchical fuzzy systems. Soft Comput. 2019, 23, 4471–4481. [Google Scholar] [CrossRef]
- Roelands, M.; Claeys, L.; Godon, M.; Geerts, M.; Feki, M.A.; Trappeniers, L. Enabling the masses to become creative in smart spaces. In Architecting the Internet of Things; Springer: Berlin, Germany, 2011; pp. 37–64. [Google Scholar]
- Coetzee, L.; Eksteen, J. Internet of things—Promise for the Future? An Introduction. In Proceedings of the IST Africa 2011 Conference & Exhibition, Gaborone, Botswana, 11–13 May 2011; p. 9. [Google Scholar]
- Khan, M.S.; Kim, D. DIY interface for enhanced service customization of remote IoT devices: A coap based prototype. Int. J. Distrib. Sens. Netw. 2015, 11, 542319. [Google Scholar] [CrossRef]
- Hamm, S. The Internet of Things. Available online: https://www.ibm.com/ibm/history/ibm100/us/en/ideas/sep2011china.html (accessed on 11 November 2019).
- Atzori, L.; Iera, A.; Morabito, G. The internet of things: A survey. Comput. Netw. 2010, 54, 2787–2805. [Google Scholar] [CrossRef]
- Gubbi, J.; Buyya, R.; Marusic, S.; Palaniswami, M. Internet of things (IoT): A vision, architectural elements, and future directions. Future Gener. Comput. Syst. 2013, 29, 1645–1660. [Google Scholar] [CrossRef]
- LeHong, H.; Fenn, J. Hype cycle for emerging technologies 2011. Available online: https://www.gartner.com/en/documents/1754719/hype-cycle-for-emerging-technologies-2011 (accessed on 23 October 2019).
- Miorandi, D.; Sicari, S.; De Pellegrini, F.; Chlamtac, I. Internet of things: Vision, applications and research challenges. Ad Hoc Netw. 2012, 10, 1497–1516. [Google Scholar] [CrossRef]
- Ventura, D.; Casado-Mansilla, D.; López-de-Armentia, J.; Garaizar, P.; López-de-Ipiña, D.; Catania, V. Ariima: A real IoT implementation of a machine-learning architecture for reducing energy consumption. In Ubiquitous Computing and Ambient Intelligence. Personalisation and User Adapted Services; Hervás, R., Lee, S., Nugent, C., Bravo, J., Eds.; Springer International Publishing: Cham, Switzerland, 2014; pp. 444–451. [Google Scholar]
- Kelly, S.D.T.; Suryadevara, N.K.; Mukhopadhyay, S.C. Towards the implementation of IoT for environmental condition monitoring in homes. IEEE Sens. J. 2013, 13, 3846–3853. [Google Scholar] [CrossRef]
- Gama, K.; Touseau, L.; Donsez, D. Combining heterogeneous service technologies for building an internet of things middleware. Comput. Commun. 2012, 35, 405–417. [Google Scholar] [CrossRef]
- Atzori, L.; Iera, A.; Morabito, G. From “smart objects” to “social objects”: The next evolutionary step of the internet of things. IEEE Commun. Mag. 2014, 52, 97–105. [Google Scholar] [CrossRef]
- Xiao, G.; Guo, J.; Da Xu, L.; Gong, Z. User interoperability with heterogeneous IoT devices through transformation. IEEE Trans. Ind. Inform. 2014, 10, 1486–1496. [Google Scholar] [CrossRef]
- What Is Raspberry Pi. Available online: https://www.raspberrypi.org/help/what-is-a-raspberry-pi/ (accessed on 11 November 2019).
- Kushner, D. The making of Arduino. IEEE Spectr. 2011, 26, 1–7. [Google Scholar]
- Li, D.; Yao, W. Risk Assessment of Long-Distance Water Transmission Pipeline Based on Fuzzy Similarity Evaluation Approach. In Proceedings of the 2016 12th International Conference on Natural Computation, Fuzzy Systems and Knowledge Discovery (ICNC-FSKD), Changsha, China, 13–15 August 2016; pp. 1096–1102. [Google Scholar]
- Tripathy, D.P.; Ala, C.K. Risk assessment in underground coalmines using fuzzy logic in the presence of uncertainty. J. Inst. Eng. (India): Ser. D 2018, 99, 157–163. [Google Scholar] [CrossRef]
- Chen, C.-T.; Lin, C.-T.; Huang, S.-F. A fuzzy approach for supplier evaluation and selection in supply chain management. Int. J. Prod. Econ. 2006, 102, 289–301. [Google Scholar] [CrossRef]
- Gul, M.; Guneri, A.F. A fuzzy multi criteria risk assessment based on decision matrix technique: A case study for aluminum industry. J. Loss Prev. Process Ind. 2016, 40, 89–100. [Google Scholar] [CrossRef]
- Zhang, J.; Gao, J.; Diao, M.; Wu, W.; Wang, T.; Qi, S. A case study on risk assessment of long distance water supply system. Procedia Eng. 2014, 70, 1762–1771. [Google Scholar] [CrossRef]
- Ullah, I.; Fayaz, M.; Kim, D. Analytical modeling for underground risk assessment in smart cities. Appl. Sci. 2018, 8, 921. [Google Scholar] [CrossRef]
- Fayaz, M.; Ullah, I.; Kim, D.-H. Underground risk index assessment and prediction using a simplified hierarchical fuzzy logic model and Kalman filter. Processes 2018, 6, 103. [Google Scholar] [CrossRef]
- Cheong, F.; Lai, R. Designing a hierarchical fuzzy logic controller using the differential evolution approach. Appl. Soft Comput. 2007, 7, 481–491. [Google Scholar] [CrossRef][Green Version]
- Leadbeater, C.; Miller, P. The Pro-Am Revolution: How Enthusiasts are Changing Our Society and Economy; Demos: London, UK, 2004. [Google Scholar]
- Roeck, D.D.; Slegers, K.; Criel, J.; Godon, M.; Claeys, L.; Kilpi, K.; Jacobs, A. I would Diyse for It!: A Manifesto for Do-It-Yourself Internet-of-Things Creation. In Proceedings of the 7th Nordic Conference on Human-Computer Interaction: Making Sense through Design, Copenhagen, Denmark, 14–17 October 2012; ACM: New York, NY, USA, 2012; pp. 170–179. [Google Scholar]
- Jin, Z.; Bose, B.K. Evaluation of Membership Functions for Fuzzy Logic Controlled Induction Motor Drive. In Proceedings of the IEEE 2002 28th Annual Conference of the Industrial Electronics Society, IECON 02, Sevilla, Spain, 5–8 November 2002; Volume 1, pp. 229–234. [Google Scholar]
- Feki, M.A.; Kawsar, F.; Boussard, M.; Trappeniers, L. The internet of things: The next technological revolution. Computer 2013, 46, 24–25. [Google Scholar] [CrossRef]
- Scott, G.; Chin, J. A DIY Approach to Pervasive Computing for the Internet of Things: A Smart Alarm Clock. In Proceedings of the 5th Computer Science and Electronic Engineering Conference (CEEC), Colchester, UK, 17–18 September 2013; pp. 57–60. [Google Scholar]
- Ahmad, S.; Hang, L.; Kim, D. Design and implementation of cloud-centric configuration repository for DIY IoT applications. Sensors 2018, 18, 474. [Google Scholar] [CrossRef]
- Heath, N. How IBM’s Node-Red is Hacking Together the Internet of Things. Available online: http://www. techrepublic.com/article/node-red (accessed on 12 November 2019).
- Kleinfeld, R.; Steglich, S.; Radziwonowicz, L.; Doukas, C. Glue.Things: A Mashup Platform for Wiring the Internet of Things with the Internet of Services. In Proceedings of the 5th International Workshop on Web of Things, Cambridge, MA, USA, 8 October 2014; pp. 16–21. [Google Scholar]
- Quoc, H.N.M.; Serrano, M.; Le-Phuoc, D.; Hauswirth, M. Super Stream Collider–Linked Stream Mashups for Everyone. In Proceedings of the Semantic Web Challenge at ISWC 2012, Boston, MA, USA, 11–15 November 2012. [Google Scholar]
- Hyemin, L.; Dongig, S.; Eunsoo, P.; Injung, H.; Gyeonghwan, H.; Dongkun, S. Open Software Platform for Companion IoT Devices. In Proceedings of the 2017 IEEE International Conference on Consumer Electronics (ICCE), Las Vegas, NV, USA, 8–10 January 2017; pp. 394–395. [Google Scholar]
- PTC. Enterprise IoT Solutions and Platform Technology. Available online: https://www.ptc.com/en/products/iiot/thingworx-platform (accessed on 23 October 2019).
- Particle. Connect Your Internet of Things (IoT) Devices. Available online: https://www.particle.io/ (accessed on 23 January 2018).
- Klir, G.J.; Yuan, B. Fuzzy Sets and Fuzzy Logic: Theory and Applications; Prentice Hall: Upper Saddle River, NJ, USA, 1995; p. 563. [Google Scholar]
- Fayaz, M.; Ullah, I.; Kim, D. An optimized fuzzy logic control model based on a strategy for the learning of membership functions in an indoor environment. Electronics 2019, 8, 132. [Google Scholar] [CrossRef]
- Fayaz, M.; Kim, D. A prediction methodology of energy consumption based on deep extreme learning machine and comparative analysis in residential buildings. Electronics 2018, 7, 222. [Google Scholar] [CrossRef]
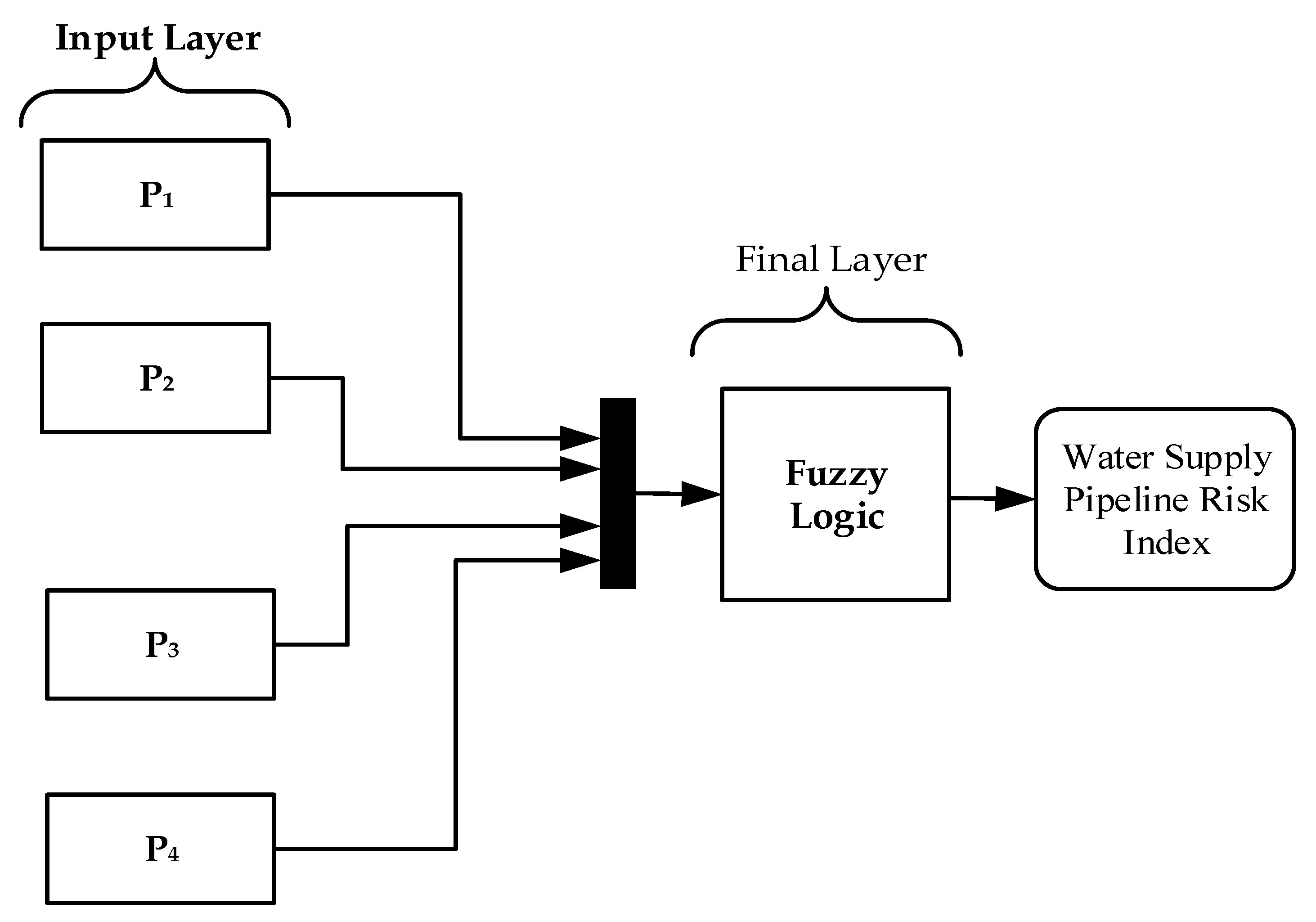
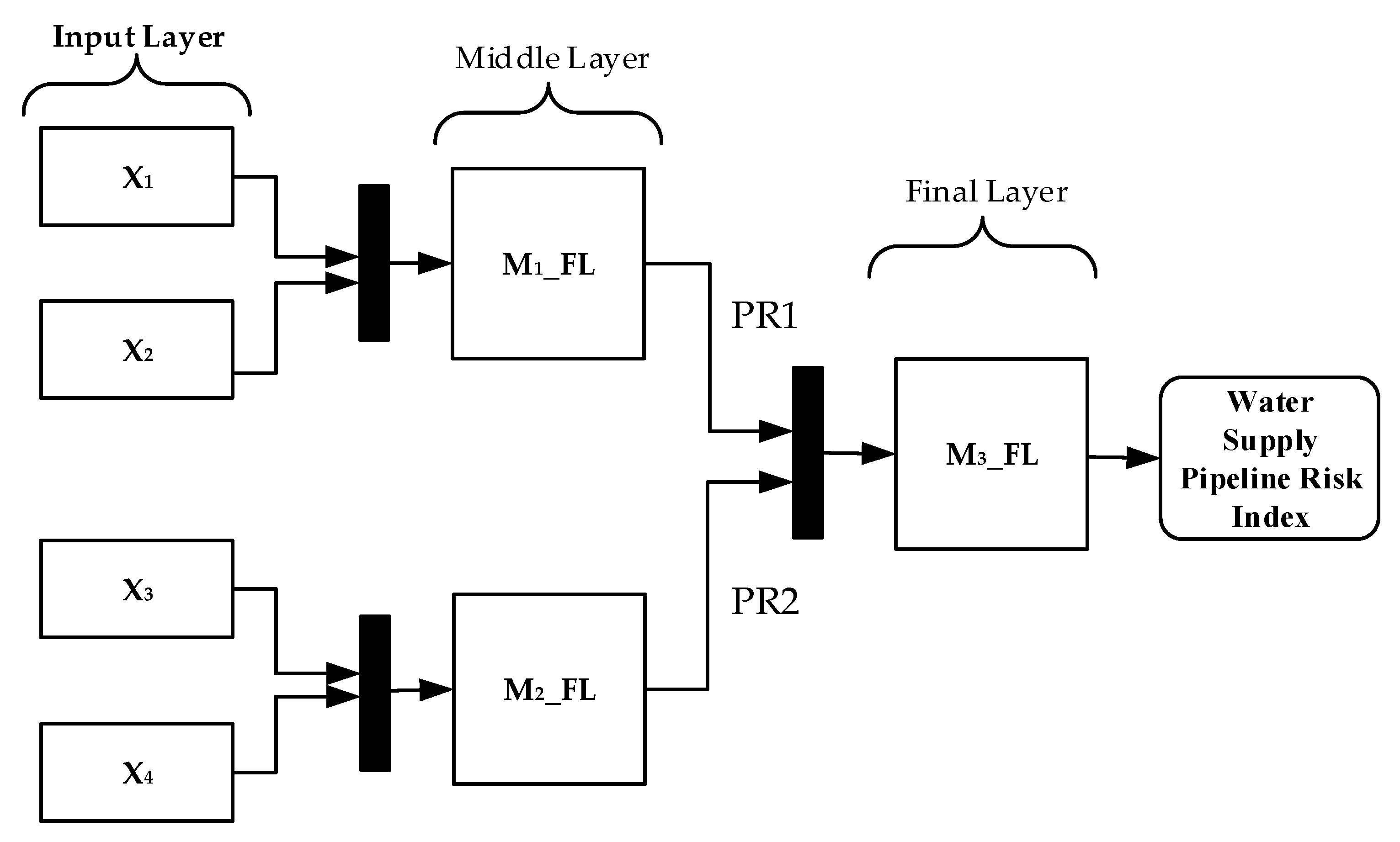
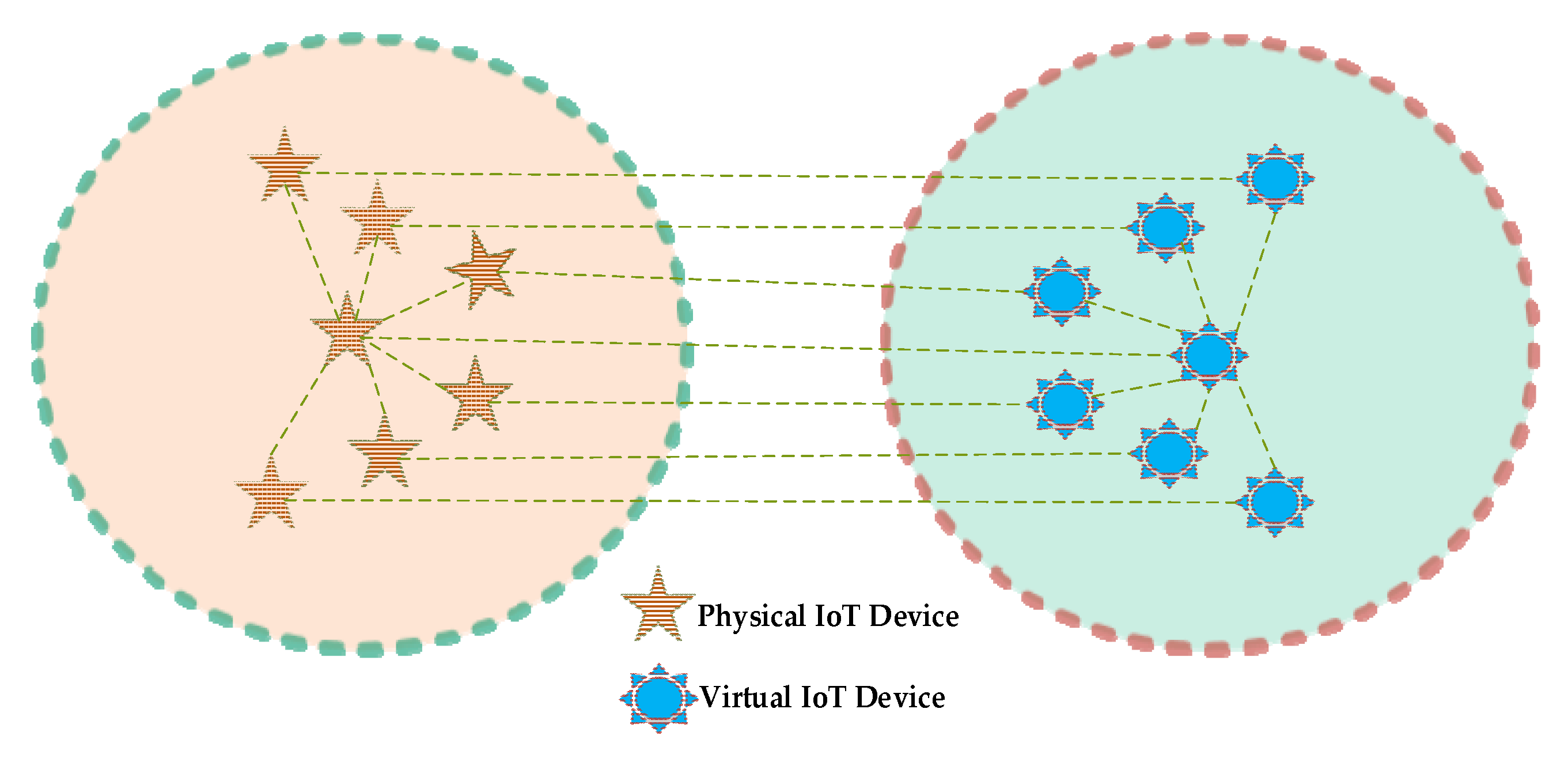
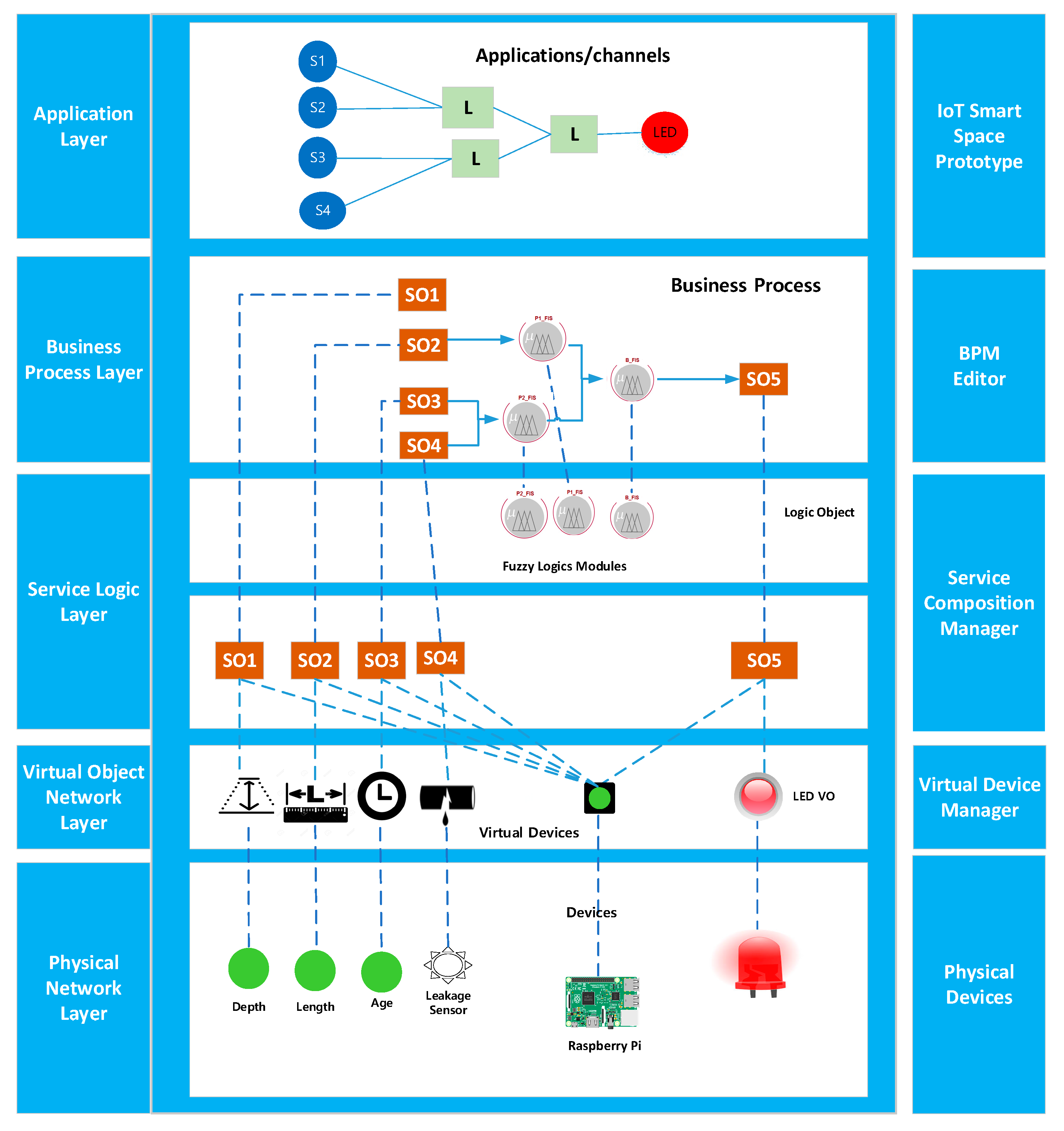

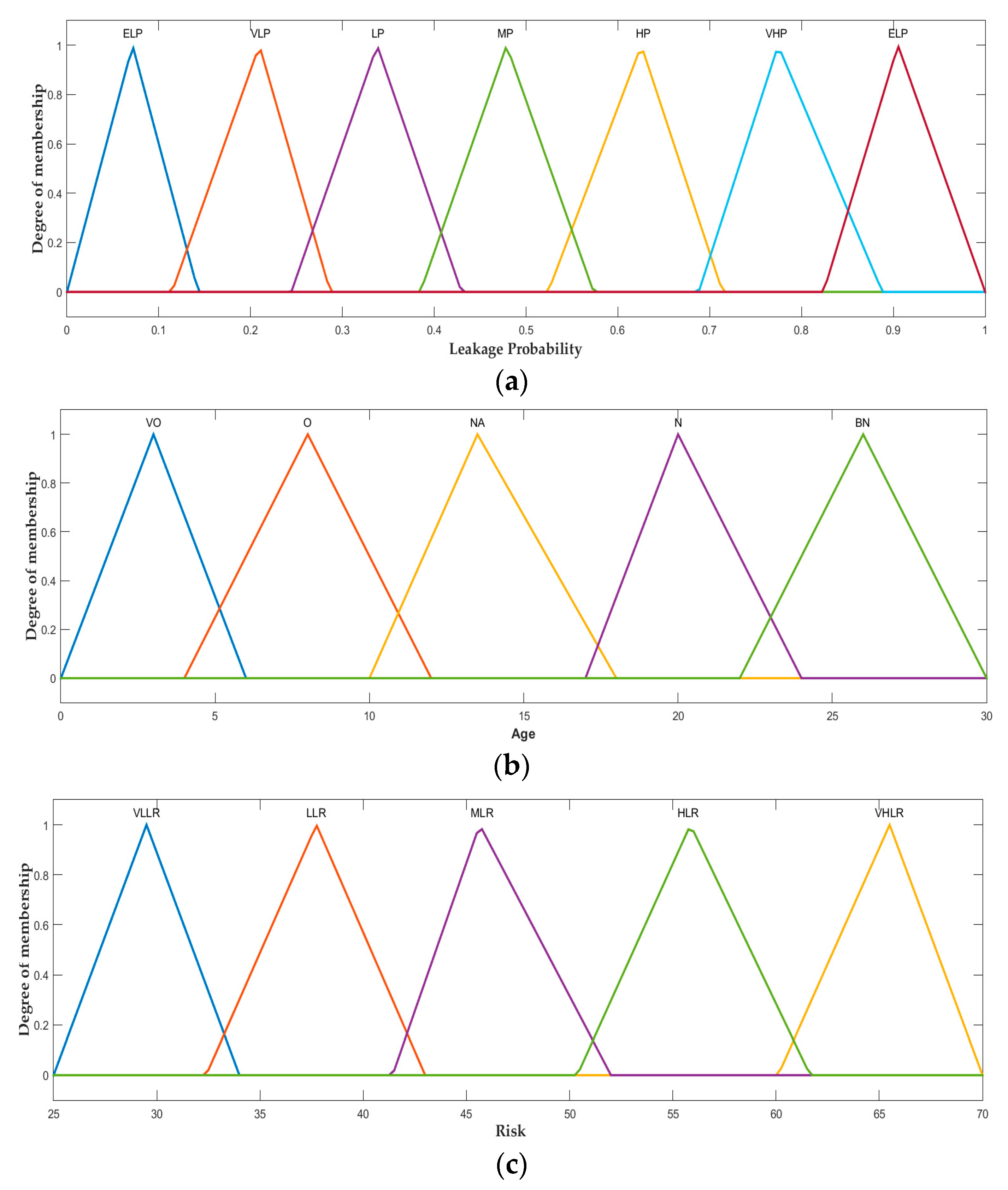
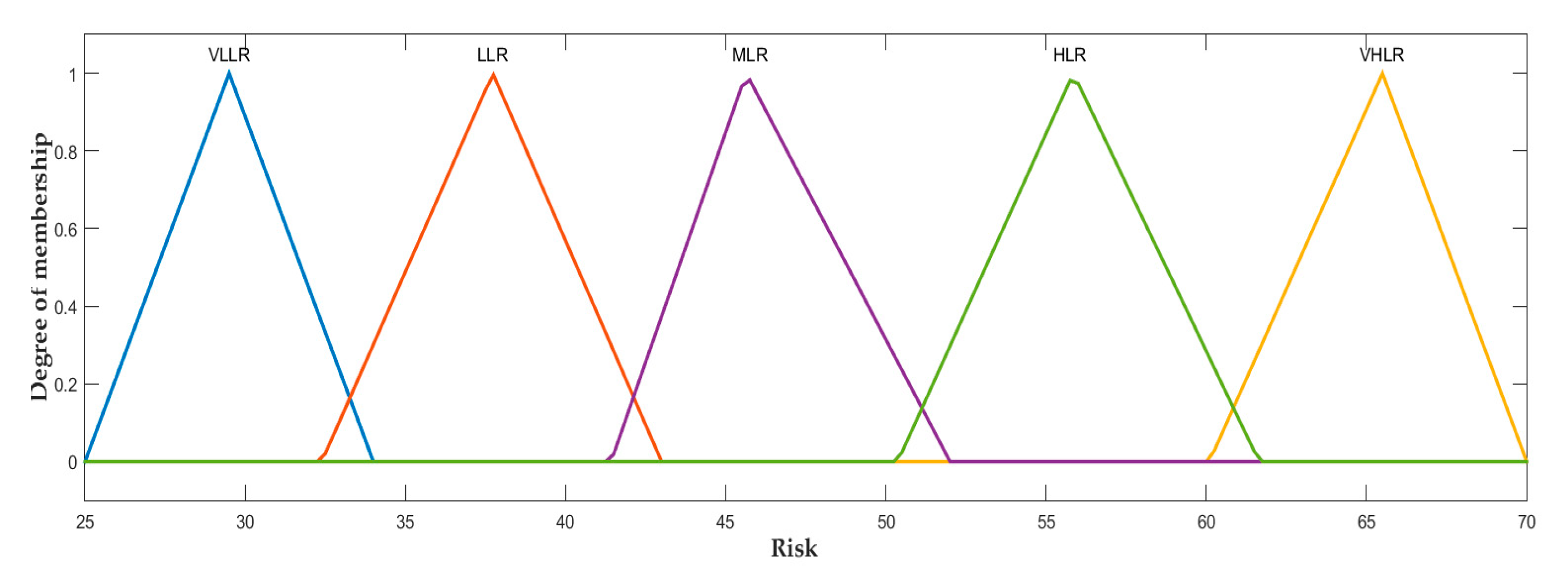
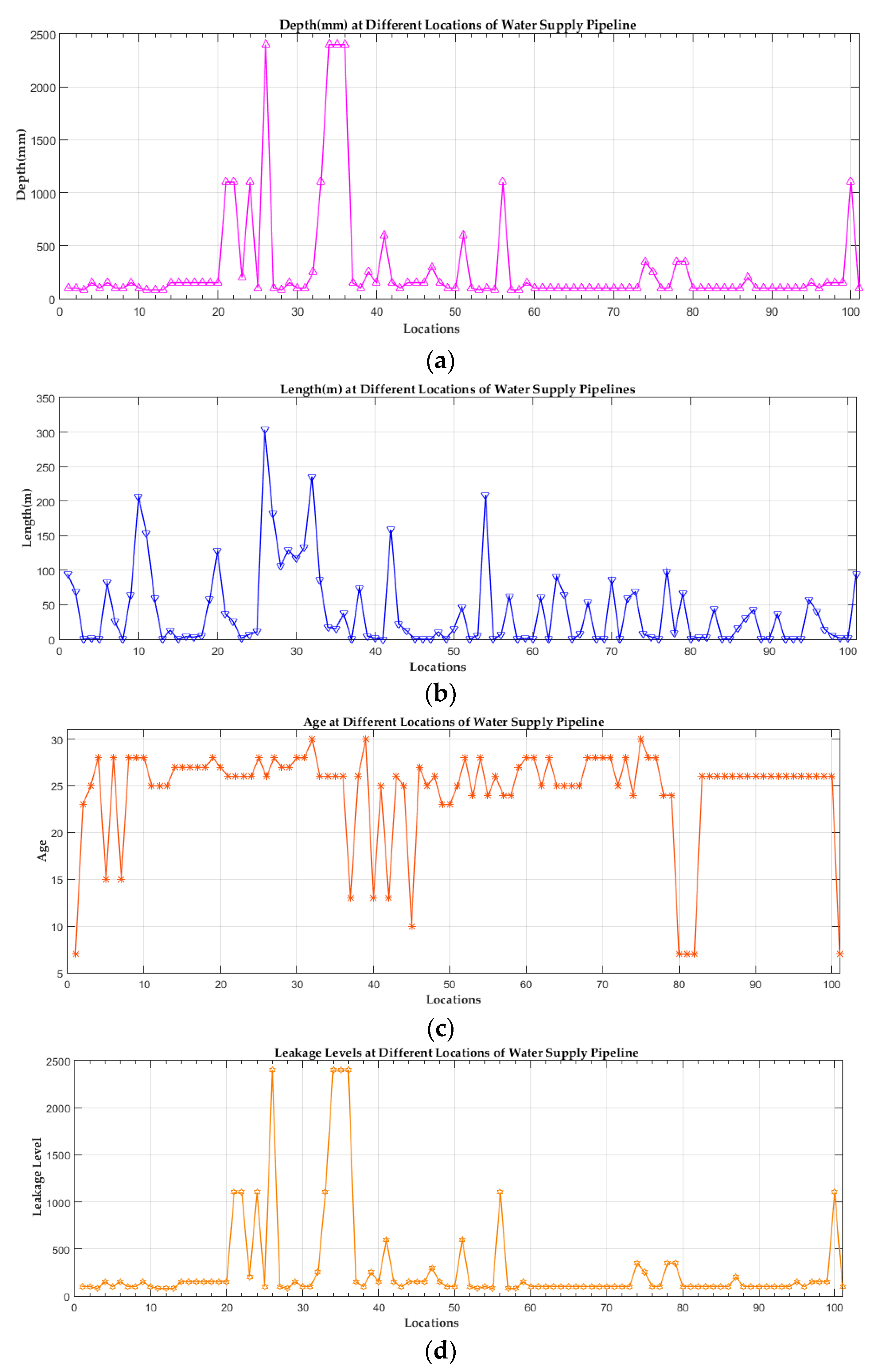

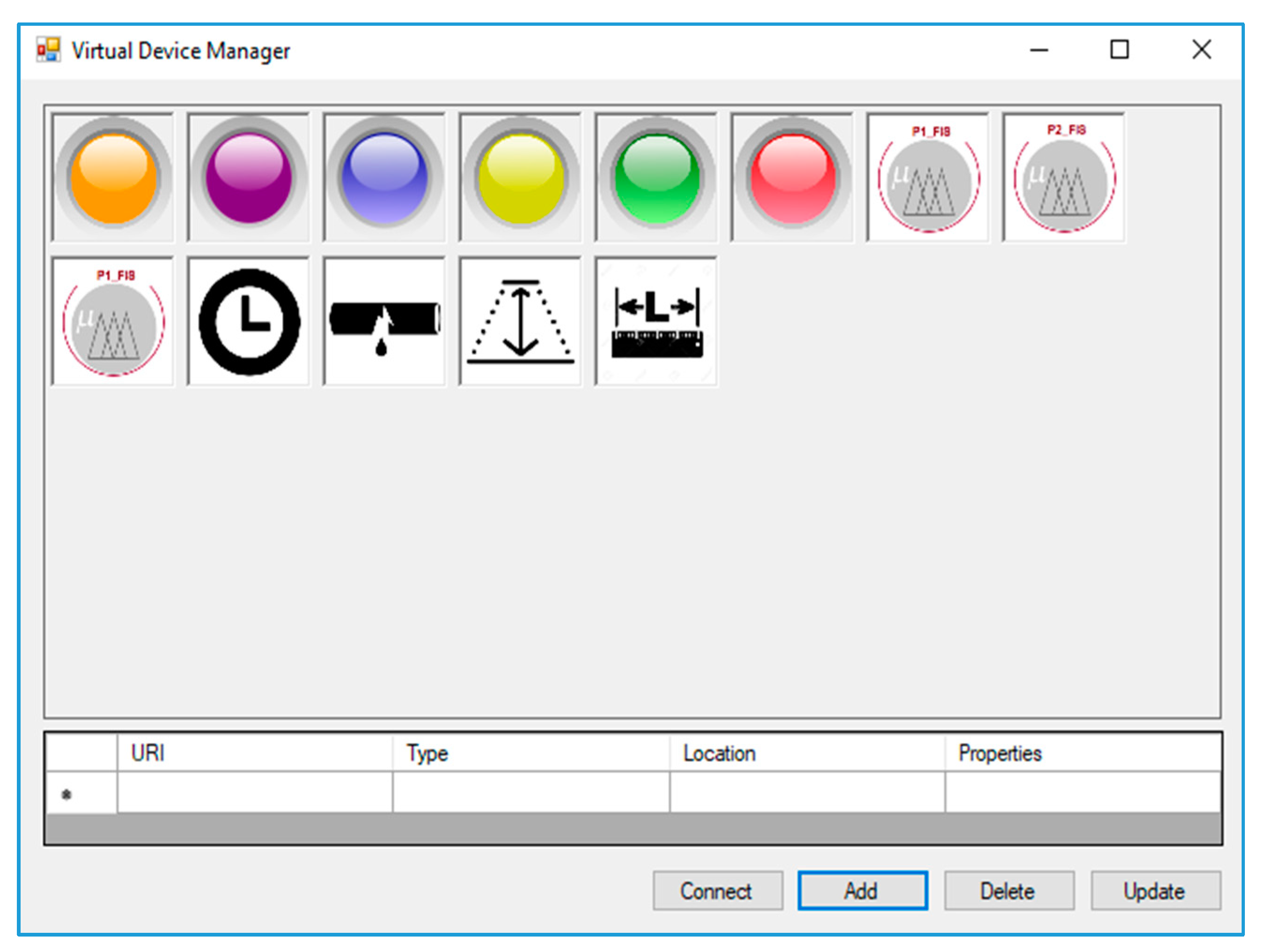
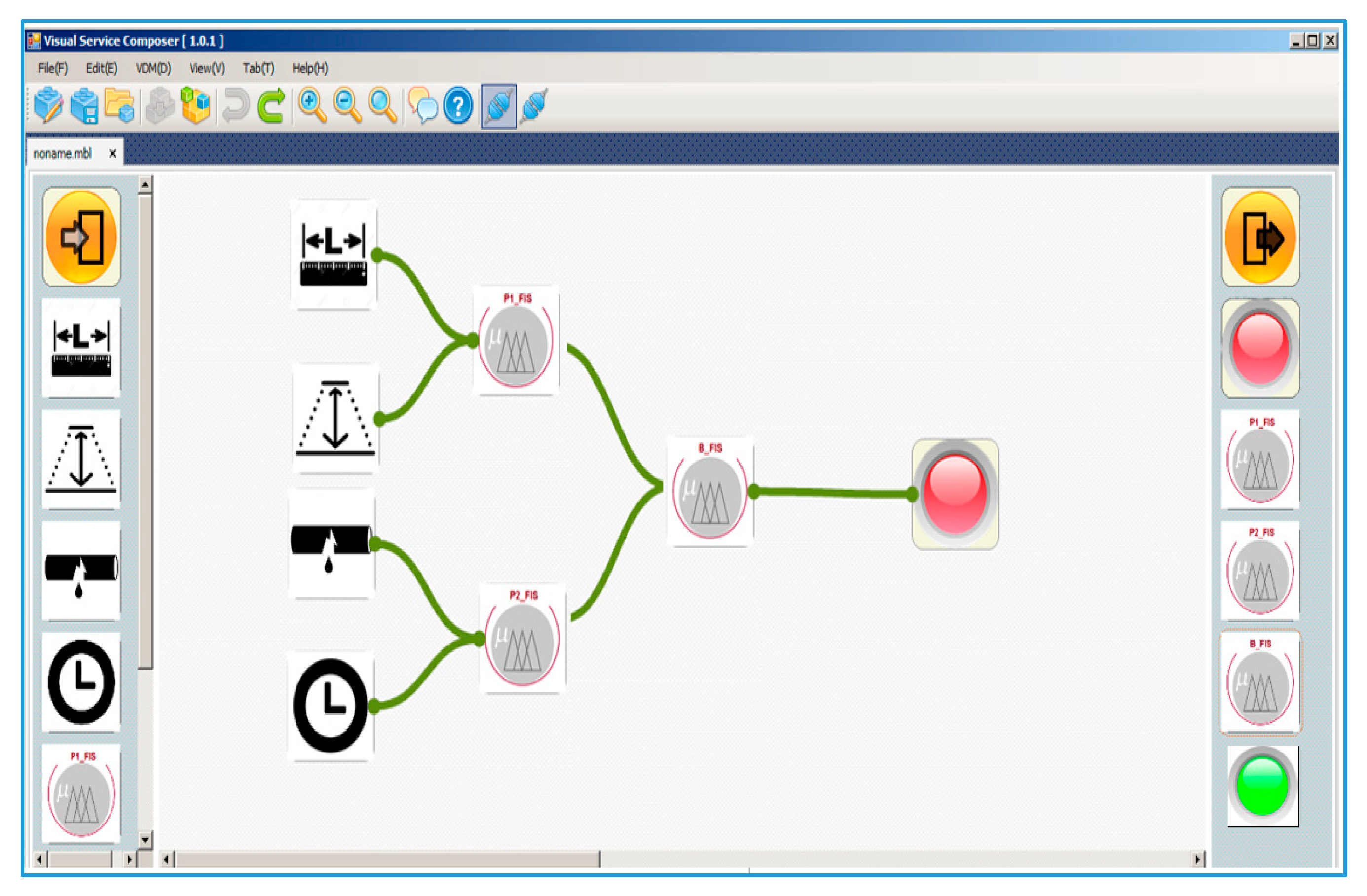
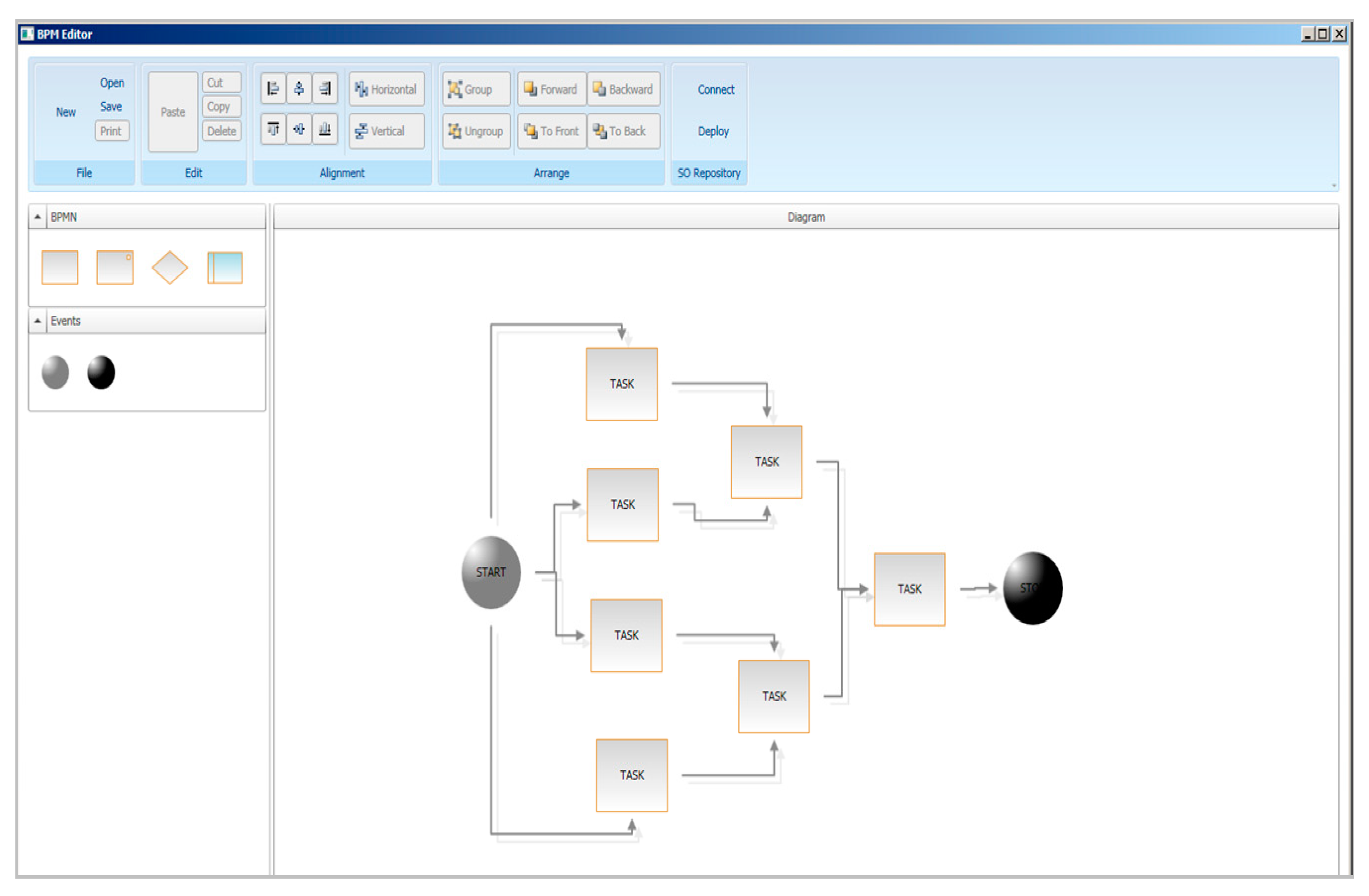
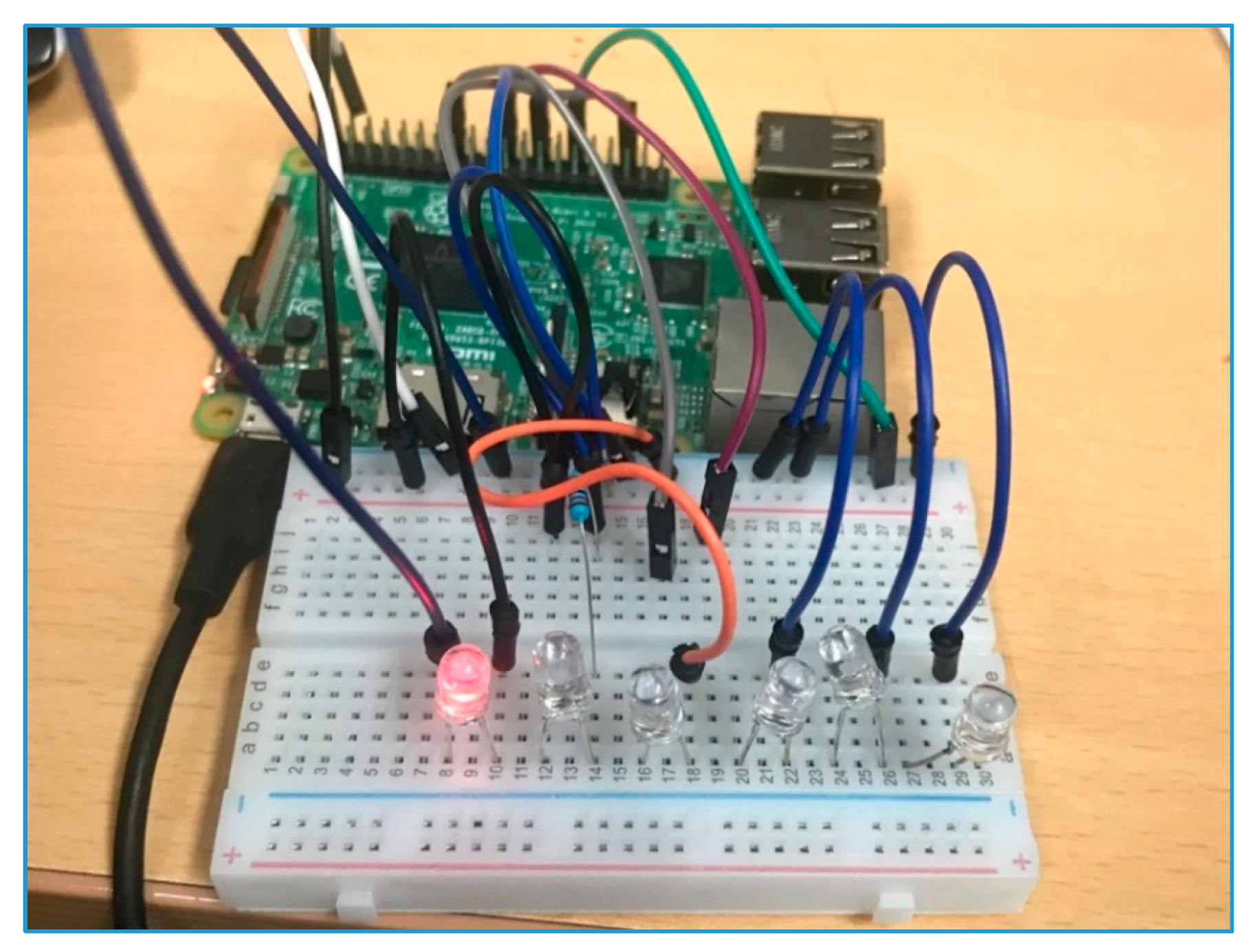
| Abbreviation | Description | Abbreviation | Description |
|---|---|---|---|
| X1 | Depth | NG | Near to Ground |
| X2 | Length | N | Normal |
| X3 | Age | ND | Near to Deep |
| X4 | Leakage | DR | Deeper |
| SHFL | Simplified Hierarchical Fuzzy Logic | DT | Deepest |
| WSPL | Water Supply Pipelines | ST | Shortest |
| BPM | Business Process Modeling | S | Short |
| TFL | Traditional Fuzzy Logic | M | Medium |
| HFL | Hierarchical Fuzzy Logic | L | Long |
| PFLR | Proposed Fuzzy Logic Rules | LT | Longest |
| TFLR | Traditional Fuzzy Logic Rules | VLLR | Very Low-Level Risk |
| M1_FL | Middle Layer 1 Fuzzy Logic | LLR | Low-Level Risk |
| M2_FL | Middle Layer 2 Fuzzy Logic | MLR | Medium-Level Risk |
| M3_FL | Out Fuzzy Logic | HLR | High-Level Risk |
| ELP | Extremely Low-level Probability | VHLR | Very High-Level Risk |
| VLP | Very Low-level Probability | FL | Fuzzy Logic |
| LP | Low-level Probability | WS | Water Supply |
| MP | Intermediate-level Probability | RI | Risk Index |
| HP | High-level Probability | DT | Deepest |
| VHP | Very High-level Probability | ST | Shortest |
| EHP | Extremely High-level Probability | S | Short |
| VO | Very Old | M | Medium |
| O | Old | L | Long |
| IA | Intermediate Age | LR | Longer |
| N | Normal | FL | Fuzzy Logic |
| BN | Brand New | WS | Water Supply |
| ENG | Extremely Near to Ground | RI | Risk Index |
| D | Deep |
| X1 | ENG | NG | N | ND | D | DR | DT | |
|---|---|---|---|---|---|---|---|---|
| X2 | ||||||||
| ST | VHLR | VLLR | VLLR | LLR | MLR | MLR | VHLR | |
| S | VHLR | LLR | LLR | ILR | MLR | HLR | LLR | |
| M | VHLR | LLR | MLR | ILR | HLR | VHLR | LLR | |
| L | VHLR | ILR | ILR | HLR | VHLR | VHLR | ILR | |
| LT | VHLR | ILR | HLR | VHLR | VHLR | VHLR | HLR | |
| X3 | ELLP | VLLP | LLP | ILP | HLP | VHLP | EHLP | |
|---|---|---|---|---|---|---|---|---|
| X4 | ||||||||
| VO | VLLR | VLLR | LLR | ILR | ILR | VHLR | VHLR | |
| O | VLLR | LLR | ILR | ILR | HLR | VHLR | VHLR | |
| IA | LLR | ILR | ILR | HLR | VHLR | VHLR | EHLR | |
| N | ILR | ILR | HLR | VHLR | VHLR | VHLR | EHLR | |
| BN | ILR | HLR | VHLR | VHLR | VHLR | VHLR | EHLR | |
| PR1 | VLR | LR | IR | HR | VHR | |
|---|---|---|---|---|---|---|
| PR2 | ||||||
| VLR | VLLR | VLLR | LLR | ILR | ILR | |
| LR | VLLR | LLR | ILR | ILR | HLR | |
| IR | LLR | ILR | ILR | HLR | VHLR | |
| HR | ILR | ILR | HLR | VHLR | VHLR | |
| VHR | ILR | HLR | VHLR | VHLR | VHLR | |
| Component | Description |
|---|---|
| Hardware | Raspberry Pi 3 Model B |
| Operating System | Raspbian |
| Memory | 1GB Resources |
| Actuators | LEDs |
| IDE | Vim, PyCharm (Remote Access) |
| Programming Language | Python 3 |
| Component | Description |
|---|---|
| Operation System | Window 7 64 bits |
| CPU | Intel Xeon E3-1230 V2 @ 3.3 Ghz × 2 |
| Memory | 8GB |
| Development environment | Eclipse Luna |
| CoAP Platform | Californium |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Fayaz, M.; Pham, Q.B.; Linh, N.T.T.; Nhi, P.T.T.; Khoi, D.N.; Qureshi, M.S.; Shah, A.S.; Khalid, S. A Water Supply Pipeline Risk Analysis Methodology Based on DIY and Hierarchical Fuzzy Inference. Symmetry 2020, 12, 44. https://doi.org/10.3390/sym12010044
Fayaz M, Pham QB, Linh NTT, Nhi PTT, Khoi DN, Qureshi MS, Shah AS, Khalid S. A Water Supply Pipeline Risk Analysis Methodology Based on DIY and Hierarchical Fuzzy Inference. Symmetry. 2020; 12(1):44. https://doi.org/10.3390/sym12010044
Chicago/Turabian StyleFayaz, Muhammad, Quoc Bao Pham, Nguyen Thi Thuy Linh, Pham Thi Thao Nhi, Dao Nguyen Khoi, Muhammad Shuaib Qureshi, Abdul Salam Shah, and Shah Khalid. 2020. "A Water Supply Pipeline Risk Analysis Methodology Based on DIY and Hierarchical Fuzzy Inference" Symmetry 12, no. 1: 44. https://doi.org/10.3390/sym12010044
APA StyleFayaz, M., Pham, Q. B., Linh, N. T. T., Nhi, P. T. T., Khoi, D. N., Qureshi, M. S., Shah, A. S., & Khalid, S. (2020). A Water Supply Pipeline Risk Analysis Methodology Based on DIY and Hierarchical Fuzzy Inference. Symmetry, 12(1), 44. https://doi.org/10.3390/sym12010044








