ExtrIntDetect—A New Universal Method for the Identification of Intelligent Cooperative Multiagent Systems with Extreme Intelligence
Abstract
1. Introduction
2. State-of-the-Art Metrics Designed to Measure Machine Intelligence
3. The Proposed ExtrIntDetect Method
imp1 + imp2 + … + impc = 1, impi > 0
The Scenario of Coalitions of Agent-Based Flying Drones
| Algorithm 1 MPSI measurement |
| Measuring the Problem-Solving Intelligence Algorithm IN: //Given the studied ICMk that have a specific architecture and a specific number of agents. ICMk = {Agent1, Agent2, …, Agentq}; OUT:|Probk|; Probk = {Probk,1, …, Probk,m}; Intelligk = {Intelligk,1, Intelligk,2, …, Intelligk,m}; Begin Step 1. He establishes |Probk| and Probk. |Probk|: = m; Probk = {Probk,1, …, Probk,m} Step 2. Obtaining the intelligence indicators data. //If there are more intelligence components, than each evaluated problem-solving intelligence is calculated according to (1). @Performing the problem-solving intelligence evaluations and calculus; Intelligk = {Intelligk,1, Intelligk,2, …, Intelligk,m}; EndMPSIAlgorithm |
| Algorithm 2 MMI measurement method |
| Robust Measurement of the Intelligence Quotient Algorithm IN:Intellig = {Intellig1, Intellig2, …, Intelligz};//Intelligence indicators sample of the ICM. OUT: TypeMIQ; MIQS; Begin Step 1. Calculus of the MIQS. TypeMIQ: = ”Mean”; For (i: = 1 to z) Do @Verify if Intelligi passes the normality assumption. If (Intelligi failed to passes the normality assumption) Then TypeMIQ: = ”Median”; Exit For; EndIf EndFor //He can change TypeMIQ based on the problem and domain-specific knowledge. @He makes the final decision on the TypeMIQ calculus as the mean or the median; For (i: = 1 to z) Do If (TypeMIQ = ”Mean”) then MIQi: = MEAN(Intelligi); Else MIQi: = MEDIAN(Intelligi); EndIF EndFor EndMMImeasuring |
| Algorithm 3 ExtrIntDetect method of measurement and detection |
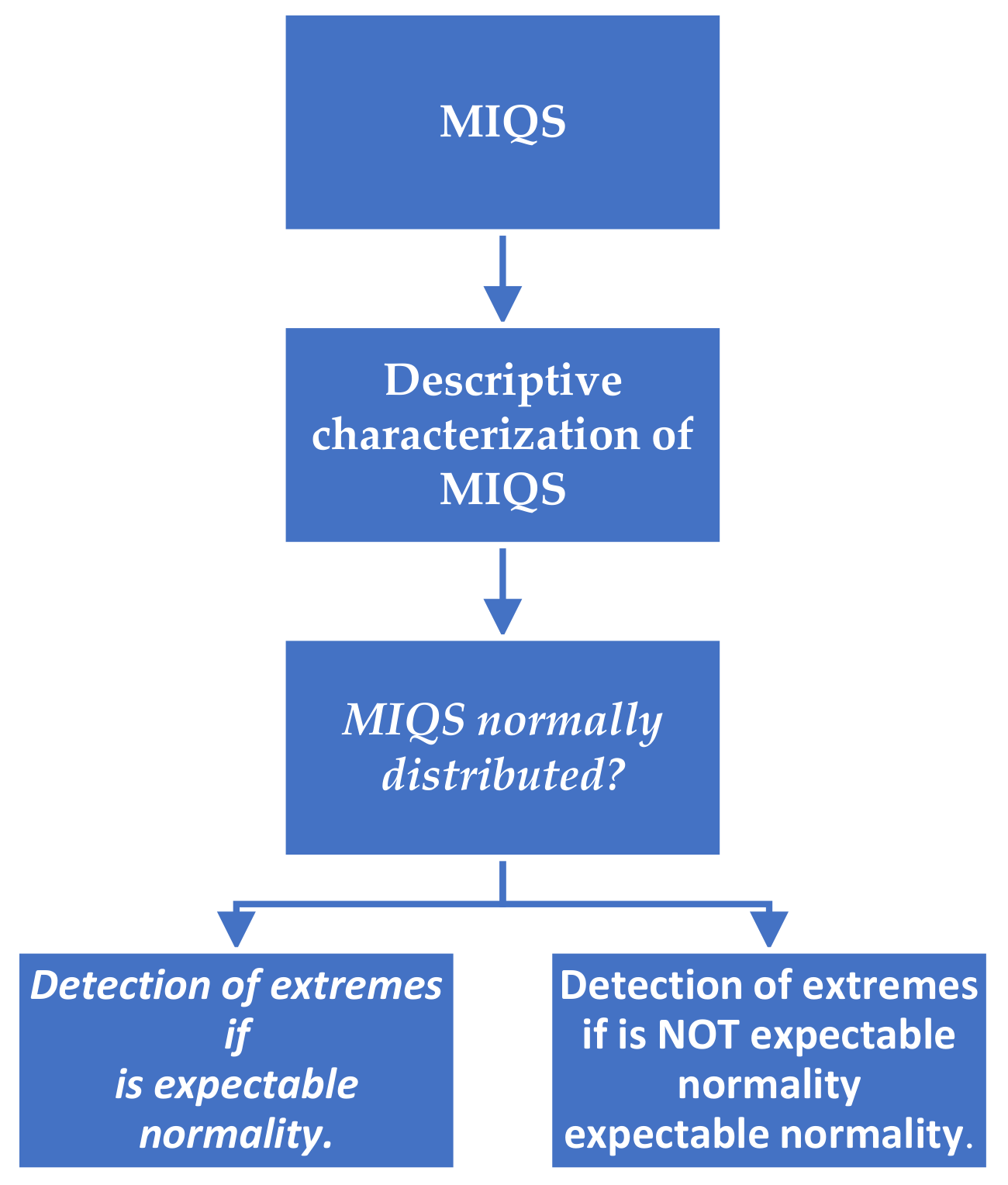
| Detection of ICMASs with Extreme Intelligence Algorithm IN:MIQS = {MIQ1, MIQ2, …, MIQz};//Calculated machine intelligence quotients. OUT: //IdOutL, IdOutH, if normality expected. IdOutL;//MIQ of ICMASs with low extreme intelligence. IdOutH;//MIQ of ICMASs with high extreme intelligence. //HExtr, HExtrOut, if normality NOT expected. HExtr;//MIQ of ICMASs with high extreme intelligence. HExtrOut;//MIQ of ICMASs with high outlier extreme intelligence. LExtr;//MIQ of ICMASs with low extreme intelligence. HExtrOut;//MIQ of ICMASs with low outlier extreme intelligence. Begin Step 1. Descriptive characterization of the MIQS data. @Calculates for MIQS the: mean, median, SD, SEM, skew, and kurt. CV: = 100 × (SD/mean); Step 2. Analyze if MIQS data passes the normality assumption. @Apply Lill and SW tests in order to verify MIQS normality. @Constructs the QQ plot for visual analysis of MIQS. @Based on the obtained result of data normality analysis set the value of norm variable; If (norm = ”No”) Then @He has the right to change norm value to “Yes”. EndIf Step 3. Detection of extremes if normality expected. If (norm = ”Yes”) Then IdOutL: = ∅;IdOutH: = ∅; OutFound: = ”Yes”; IdOut: = MIQS; avg*: = mean(IdOut); While ((OutFound = ”Yes”) and (|IdOut|≥3)) Do OutFound: = ”No”; @It is applied the Grubbs test; If (an outlier denoted OUT was identified) Then IdOut: = IdOut\{OUT}; OutFound: =”Yes”; If (OUT < avg*) Then IdOutL: = IdOutL ∪ {OUT}; Else IdOutH: = IdOutH ∪ {OUT}; EndIf EndIf avg* = mean(IdOut); EndWhile EndIF If (|IdOutL| ≥ 2) Then @Order ascending IdOutL. EndIf If (|IdOutH| ≥ 2) Then @Order ascending IdOutH. EndIf Step 4. Detection of extremes if normality is NOT expected. If (Norm = ”No”) Then HExtr: = ∅; HExtrOut: = ∅; LExtr: = ∅; LExtrOut: = ∅; @Arrange MIQS = {MIQ1, MIQ2, …, MIQz} in ascending order. @Calculate Q1 and Q3;//The first and third quartile. IQR: = Q3−Q1;//Calculates the interquartile range. @He establishes RangeL and RangeU values. HLowLim: = Q3 + RangeL × IQR; HUppLim: = Q3 + RangeU × IQR; LLowLim: = Q1 − RangeU × IQR; LUppLim: = Q1 − RangeL × IQR; For (i: = 1 to z) Do If (MIQi ∈ [HLowLim, HUppLim)) Then HExtr: = HExtr ∪ {MIQi}; ElseIf (MIQi ≥ HUppLim) Then HExtrOut: = HExtrOut ∪ {MIQi}; EndIf If (MIQi ∈ (LLowLim, LUppLim]) Then LExtr: = LExtr ∪ {MIQi}; ElseIf (MIQi ≤ LLowLim) Then LExtrOut: = LExtrOut ∪ {MIQi}; EndIf EndFor If (|HExtr| ≥ 2) Then @Order ascending HExtr. EndIf If (|HExtrOut| ≥ 2) Then @Order ascending HExtrOut. EndIf If (|LExtr| ≥ 2) Then @Order ascending LExtr. EndIf If (|LExtrOut| ≥ 2) Then @Order ascending LExtrOut. EndIF End EndExtrIntDetectAlgorithm |
4. Experimental Evaluation of the ExtrIntDetect Method
5. Discussion
5.1. Discussion of the Experimental Results
5.2. Discussion of the ExtrIntDetect Method
6. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
References
- Gelenbe, E.; Lent, R.; Xu, Z. Design and performance of cognitive packet networks. Perform. Eval. 2001, 46, 155–176. [Google Scholar] [CrossRef]
- Sakellari, G. Performance evaluation of the Cognitive Packet Network in the presence of network worms. Perform. Eval. 2011, 68, 927–937. [Google Scholar] [CrossRef]
- Spoto, S.; Gribaudo, M.; Manini, D. Performance evaluation of peering-agreements among autonomous systems subject to peer-to-peer traffic. Perform. Eval. 2014, 77, 1–20. [Google Scholar] [CrossRef]
- Crovella, M.; Lindemann, C.; Reiser, M. Internet performance modeling: The state of the art at the turn of the century. Perform. Eval. 2000, 42, 91–108. [Google Scholar] [CrossRef]
- Al-Rousan, M.; Archibald, J.K.; Bearnson, L. Evaluating the impact of locality on the performance of large-scale SCI multiprocessors. Perform. Eval. 2001, 46, 275–302. [Google Scholar] [CrossRef]
- Liu, L.; Lim, S. A voxel-based multiscale morphological airborne lidar filtering algorithm for digital elevation models for forest regions. Measurement 2018, 123, 135–144. [Google Scholar] [CrossRef]
- Wibowo, S.; Grandhi, S. Fuzzy Multicriteria Analysis for Performance Evaluation of Internet-of-Things-Based Supply Chains. Symmetry 2018, 10, 603. [Google Scholar] [CrossRef]
- Karimi, N.; Kondrood, R.R.; Alizadeh, T. An intelligent system for quality measurement of Golden Bleached raisins using two comparative machine learning algorithms. Measurement 2017, 107, 68–76. [Google Scholar] [CrossRef]
- Sen, B.; Mandal, U.K.; Mondal, S.P. Advancement of an intelligent system based on ANFIS for predicting machining performance parameters of Inconel 690—A perspective of metaheuristic approach. Measurement 2017, 109, 9–17. [Google Scholar] [CrossRef]
- Ahmadi, F.F.; Layegh, N.F. Integration of close range photogrammetry and expert system capabilities in order to design and implement optical image based measurement systems for intelligent diagnosing disease. Measurement 2014, 51, 9–17. [Google Scholar] [CrossRef]
- Sobolev, V.; Aumala, O. Metrological automatic support of measurement results in intelligent measurement systems. Measurement 1996, 17, 151–159. [Google Scholar] [CrossRef]
- Liu, W. Intelligent fault diagnosis of wind turbines using multi-dimensional kernel domain spectrum technique. Measurement 2019, 133, 303–309. [Google Scholar] [CrossRef]
- Popescu, D.; Ichim, L. Intelligent Image Processing System for Detection and Segmentation of Regions of Interest in Retinal Images. Symmetry 2018, 10, 73. [Google Scholar] [CrossRef]
- Wang, D.; Ren, H.; Shao, F. Distributed Newton Methods for Strictly Convex Consensus Optimization Problems in Multi-Agent Networks. Symmetry 2017, 9, 163. [Google Scholar] [CrossRef]
- Iantovics, L.B.; Zamfirescu, C.B. ERMS: An evolutionary reorganizing multiagent system. Innov. Comput. Inf. Control 2013, 9, 1171–1188. [Google Scholar]
- Kwon, H.; Pack, D.J. A Robust Mobile Target Localization Method for Cooperative Unmanned Aerial Vehicles Using Sensor Fusion Quality. J. Intell. Robot. Syst. 2012, 65, 479–493. [Google Scholar] [CrossRef]
- Saska, M.; Vonasek, V.; Krajnik, T.; Preucil, L. Coordination and Navigation of Heterogeneous MAV-UGV Formations Localized by a ‘hawk-eye’-like Approach Under a Model Predictive Control Scheme. Int. J. Robot. Res. 2014, 33, 1393–1412. [Google Scholar] [CrossRef]
- Chase, D. Underlying Factor Structures of the Stanford-Binet Intelligence Scales, 5th ed.; Drexel University: Philadelphia, PA, USA, 2005. [Google Scholar]
- Kaufman, A.S. IQ Testing 101; Springer: New York, NY, USA, 2009. [Google Scholar]
- Nicolas, S.; Andrieu, B.; Croizet, J.C.; Sanitioso, R.B.; Burman, J.T. Sick? Or slow? On the origins of intelligence as a psychological object. Intelligence 2013, 41, 699–711. [Google Scholar] [CrossRef]
- Bilker, W.B.; Hansen, J.A.; Brensinger, C.M.; Richard, J.; Gur, R.E.; Gur, R.C. Development of abbreviated nine-item forms of the Raven’s standard progressive matrices test. Assessment 2012, 19, 354–369. [Google Scholar] [CrossRef]
- Raven, J.C. Mental Tests used in Genetic studies: The performance of Related Individuals on Tests Mainly Educative and Mainly Reproductive. MSc Thesis, University of London, London, UK, 1936. [Google Scholar]
- Kaufman, A.S.; Lichtenberger, E. Assessing Adolescent and Adult Intelligence, 3rd ed.; Wiley: Hoboken, NJ, USA, 2006; p. 3. [Google Scholar]
- Wechsler, D. The Measurement of Adult Intelligence. Baltimore (MD); Williams & Witkins: Philadelphia, PA, USA, 1939; p. 229. [Google Scholar]
- Kaufman, A.S.; Kaufman, N.L. Kaufman test of Educational Achievement Comprehensive Form, 2nd ed.; Circle Pines, N., Ed.; American Guidance Service: Circle Pines, MN, USA, 2004. [Google Scholar]
- Kaufman, A.S.; Kaufman, N.L. Kaufman Assessment Battery for Children; American Guidance Service: Circle Pines, MN, USA, 1983. [Google Scholar]
- Kaufman, A.S.; Kaufman, N.L. Kaufman Assessment Battery for Children, 2nd ed.; American Guidance Service: Circle Pines, MN, USA, 2004. [Google Scholar]
- Neisser, U.; Boodoo, G.; Bouchard, T.J.J.; Boykin, A.W.; Brody, N.; Ceci, S.J.; Halpern, D.F.; Loehlin, J.C.; Perloff, R.; Sternberg, R.J.; et al. Intelligence: Knowns and unknowns. Am. Psychol. 1996, 51, 77–101. [Google Scholar] [CrossRef]
- Schmidt, F.L.; Hunter, J. General mental ability in the world of work: Occupational attainment and job performance. J. Pers. Soc. Psychol. 2004, 86, 162–173. [Google Scholar] [CrossRef] [PubMed]
- Arik, S.; Iantovics, L.B.; Szilagyi, S.M. OutIntSys—A Novel Method for the Detection of the Most Intelligent Cooperative Multiagent Systems. In Proceedings of the 24th International Conference on Neural Information Processing (ICONIP 2017), Guangzhou, China, 14–18 November 2017; pp. 31–40, LNCS 10637. [Google Scholar]
- Iantovics, L.B.; Dehmer, M.; Emmert-Streib, F. MetrIntSimil-An Accurate and Robust Metric for Comparison of Similarity in Intelligence of Any Number of Cooperative Multiagent Systems. Symmetry 2018, 10, 48. [Google Scholar] [CrossRef]
- Iantovics, L.B.; Gligor, A.; Niazi, A.M.; Biro, A.I.; Szilagyi, S.M.; Tokody, D. Review of Recent Trends in Measuring the Computing Systems Intelligence. BRAIN Broad Res. Artif. Intell. Neurosci. 2018, 9, 77–94. [Google Scholar]
- Turing, A.M. Computing machinery and intelligence. Oxford University Press on behalf of the Mind Association, Mind. New Ser. 1950, 59, 433–460. [Google Scholar] [CrossRef]
- Dowe, D.L.; Hajek, A.R. A non-behavioural, computational extension to the Turing Test. In Proceedings of the International Conference on Computational Intelligence & Multimedia Applications (ICCIMA 1998), 7–10 February 1998, Gippsland, Australia; World Scientific Publishing: Singapore, 1998; pp. 101–106. [Google Scholar]
- Schreiner, K. Measuring IS: Toward a US standard. IEEE Intell. Syst. Appl. 2000, 15, 19–21. [Google Scholar] [CrossRef]
- Park, H.J.; Kim, B.K.; Lim, K.Y. Measuring the machine intelligence quotient (MIQ) of human-machine cooperative systems. IEEE Trans. Syst. Man Cybern. Part A Syst. Hum. 2001, 31, 89–96. [Google Scholar] [CrossRef]
- Sanghi, P.; Dowe, D.L. A Computer Program Capable of Passing I.Q. Tests. In Proceedings of the Joint International Conference on Cognitive Science, 4th ICCS International Conference on Cognitive Science and 7th ASCS Australasian Society for Cognitive Science (ICCS/ASCS 2003), Sydney, NSW, Australia, 13–17 July 2003; pp. 570–575. [Google Scholar]
- Legg, S.; Hutter, M. A formal measure of machine intelligence. In Proceedings of the 15th Annual Machine Learning Conference, Ghent, Belgium, 11–12 May 2006; pp. 73–80. [Google Scholar]
- Anthony, A.; Jannett, T.C. Measuring Machine Intelligence of an Agent-Based Distributed Sensor Network System; Advances and Innovations in Systems; Elleithy, K., Ed.; Springer: Dordrecht, The Netherland, 2007; pp. 531–535. [Google Scholar]
- Hernández-Orallo, J. Beyond the Turing Test. J. Logic. Lang. Inf. 2000, 9, 447–466. [Google Scholar] [CrossRef]
- Hernández-Orallo, J.; Dowe, D.L. Measuring universal intelligence: Towards an anytime intelligence test. Artif. Intell. 2010, 174, 1508–1539. [Google Scholar] [CrossRef]
- Hibbard, B. Measuring Agent Intelligence Via Hierarchies of Environments. In Artificial General Intelligence, Lecture Notes in Computer Science 6830; Schmidhuber, J., Thórisson, K.R., Looks, M., Eds.; Springer: Berlin/Heidelberg, Germany, 2011; pp. 303–308. [Google Scholar]
- Hernández-Orallo, J.; Dowe, D.L.; Hernández-Lloreda, M.V. Universal psychometrics: Measuring cognitive abilities in the machine kingdom. Cogn. Syst. Res. 2014, 27, 50–74. [Google Scholar] [CrossRef]
- Besold, T.; Hernandez-Orallo, J.; Schmid, U. Can machine intelligence be measured in the same way as human intelligence? Künstliche Intelligenz 2015, 29, 291–297. [Google Scholar] [CrossRef]
- Chmait, N.; Li, Y.F.; Dowe, D.L.; Green, D.G. A Dynamic Intelligence Test Framework for Evaluating AI Agents. In Proceedings of the Workshop Evaluating General-Purpose AI, The Hague, The Netherlands, 30 August 2016; pp. 1–8, EGPAI 2016. [Google Scholar]
- Liu, F.; Shi, Y.; Liu, Y. Intelligence quotient and intelligence grade of artificial intelligence. Ann. Data Sci. 2017, 4, 179–191. [Google Scholar] [CrossRef]
- Razali, N.; Wah, Y.B. Power comparisons of Shapiro-Wilk, Kolmogorov-Smirnov, Lilliefors, Anderson-Darling tests. J. Stat. Model. Anal. 2011, 2, 2–33. [Google Scholar]
- Lilliefors, H. On the Kolmogorov-Smirnov test for the exponential distribution with mean unknown. J. Am. Stat. Assoc. 1969, 64, 387–389. [Google Scholar] [CrossRef]
- Lilliefors, H. On the Kolmogorov–Smirnov test for normality with mean and variance unknown. J. Am. Stat. Assoc. 1967, 62, 399–402. [Google Scholar] [CrossRef]
- Shapiro, S.S.; Wilk, M.B. An analysis of variance test for normality (complete samples). Biometrika 1965, 52, 591–611. [Google Scholar] [CrossRef]
- Stephens, M.A. EDF Statistics for Goodness of Fit and Some Comparisons. J. Am. Stat. Assoc. 1974, 69, 730–737. [Google Scholar] [CrossRef]
- Wilk, M.B.; Gnanadesikan, R. Probability plotting methods for the analysis of data, Biometrika. Biometrika Trust 1968, 55, 1–17. [Google Scholar]
- Bland, J.M.; Altman, D.G. Statistics notes: Measurement error. BMJ 1996, 312, 1654. [Google Scholar] [CrossRef]
- Joanes, D.N.; Gill, C.A. Comparing measures of sample skewness and kurtosis. J. R. Stat. Soc. (Ser. D) Stat. 1998, 47, 183–189. [Google Scholar] [CrossRef]
- Tian, Y.; Yin, Z.; Huang, M. Missing Data Probability Estimation-Based Bayesian Outlier Detection for Plant-Wide Processes with Multisampling Rates. Symmetry 2018, 10, 475. [Google Scholar] [CrossRef]
- Li, G.; Wang, J.; Liang, J.; Yue, C. The Application of a Double CUSUM Algorithm in Industrial Data Stream Anomaly Detection. Symmetry 2018, 10, 264. [Google Scholar] [CrossRef]
- Li, G.; Wang, J.; Liang, J.; Yue, C. Application of Sliding Nest Window Control Chart in Data Stream Anomaly Detection. Symmetry 2018, 10, 113. [Google Scholar] [CrossRef]
- Ross, S.M. Peirce’s Criterion for the Elimination of Suspect Experimental Data. J. Engr. Technol. 2003, 2, 1–12. [Google Scholar]
- Motulsky, H.J.; Brown, R.E. Detecting outliers when fitting data with nonlinear regression: A new method based on robust nonlinear regression and the false discovery rate. BMC Bioinform. 2006, 7, 123. [Google Scholar] [CrossRef] [PubMed]
- Tietjen, G.; Moore, R. Some Grubbs-Type Statistics for the Detection of Several Outliers. Technometrics 1972, 14, 583–597. [Google Scholar] [CrossRef]
- Zerbet, A.; Nikulin, M. A new statistics for detecting outliers in exponential case. Commun. Stat. Theory Methods 2003, 32, 573–584. [Google Scholar] [CrossRef]
- Dean, R.B.; Dixon, W.J. Simplified Statistics for Small Numbers of Observations. Anal. Chem. 1951, 23, 636–638. [Google Scholar] [CrossRef]
- Grubbs, F.E. Sample criteria for testing outlying observations. Ann. Math. Stat. 1950, 21, 27–58. [Google Scholar] [CrossRef]
- Barnett, V.; Lewis, T. Outliers in Statistical Data, 3rd ed.; Wiley: Hoboken, NJ, USA, 1994. [Google Scholar]
- Grubbs, F.E. Procedures for Detecting Outlying Observations in Samples. Technometrics 1969, 11, 1–21. [Google Scholar] [CrossRef]
- Stefansky, W. Rejecting Outliers in Factorial Designs. Technometrics 1972, 14, 469–479. [Google Scholar] [CrossRef]
- Dantzig, G.B.; Fulkerson, D.R.; Johnson, S.M. Solution of a large-scale traveling-salesman problem. Oper. Res. 1954, 2, 393–410. [Google Scholar] [CrossRef]
- Kovács, L.; Iantovics, L.B.; Iakovidis, D.K. IntraClusTSP—An Incremental Intra-Cluster Refinement Heuristic Algorithm for Symmetric Travelling Salesman Problem. Symmetry 2018, 10, 663. [Google Scholar]
- Laporte, G. The Traveling Salesman Problem: An overview of exact and approximate algorithms. Eur. J. Oper. Res. 1992, 59, 231–247. [Google Scholar] [CrossRef]
- Merkle, D.; Middendorf, M. On solving permutation scheduling problems with ant colony optimization. Int. J. Syst. Sci. 2005, 36, 255–266. [Google Scholar] [CrossRef]
- Runkler, T.A. Ant colony optimization of clustering models. Int. J. Int. Syst. 2005, 20, 1233–1251. [Google Scholar] [CrossRef]
- Crisan, G.C.; Pintea, C.M.; Palade, V. Emergency Management Using Geographic Information Systems. Application to the first Romanian Traveling Salesman Problem Instance. Knowl. Inf. Syst. 2017, 50, 265–285. [Google Scholar] [CrossRef]
- Pholdee, N.; Bureerat, S. Hybrid real-code ant colony optimisation for constrained mechanical design. Int. J. Syst. Sci. 2016, 47, 474–491. [Google Scholar] [CrossRef]
- Dorigo, M.; Maniezzo, V.; Colorni, A. Positive Feedback as a Search Strategy; Dipartimento di Elettronica, Politecnico di Milano: Milano, Italy, 1991. [Google Scholar]
- Colorni, A.; Dorigo, M.; Maniezzo, V. Distributed optimization by ant colonies. In Actes de la Premiere Conference Europeenne Sur la vie Artificielle; Elsevier Publishing: Paris, France, 1991; pp. 134–142. [Google Scholar]
- Dorigo, M. Optimization, Learning and Natural Algorithms. Ph.D. Thesis, Politecnico di Milano, Milano, Italy, 1992. [Google Scholar]
- Jaradat, G.M.; Ayob, M. An Elitist-Ant System for Solving the Post-Enrolment Course Timetabling Problem; Zhang, Y., Cuzzocrea, A., Ma, J., Chung, K., Arslan, T., Song, X., Eds.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 167–176, FGIT 2010. CCIS 118. [Google Scholar]
- Bullnheimer, B.; Hartl, R.F.; Strauss, C. A new rank based version of the ant system. A computational study. Cent. Eur. J. Oper. Res. 1999, 7, 25–38. [Google Scholar]
- Cordón, O.; de Viana, I.F.; Herrera, F. Analysis of the Best-Worst Ant System and its Variants on the QAP; Dorigo, M., Di Caro, G., Sampels, M., Eds.; Springer: Heidelberg, Germany, 2002; pp. 228–234, ANTS 2002. LNCS 2463. [Google Scholar]
- Stutzle, T.; Hoos, H.H. Max-min ant system. Future Gener. Comput. Syst. 2000, 16, 889–914. [Google Scholar] [CrossRef]
- Dorigo, M.; Stützle, T. Ant Colony Optimization; MIT Press: Cambridge, MA, USA, 2004. [Google Scholar]
- Buscarino, A.; Fortuna, L.; Frasca, M.; Latora, V. Disease spreading in populations of moving agents, IOP Publishing. Europhys. Lett. (EPL) 2008, 82, 38002. [Google Scholar] [CrossRef]

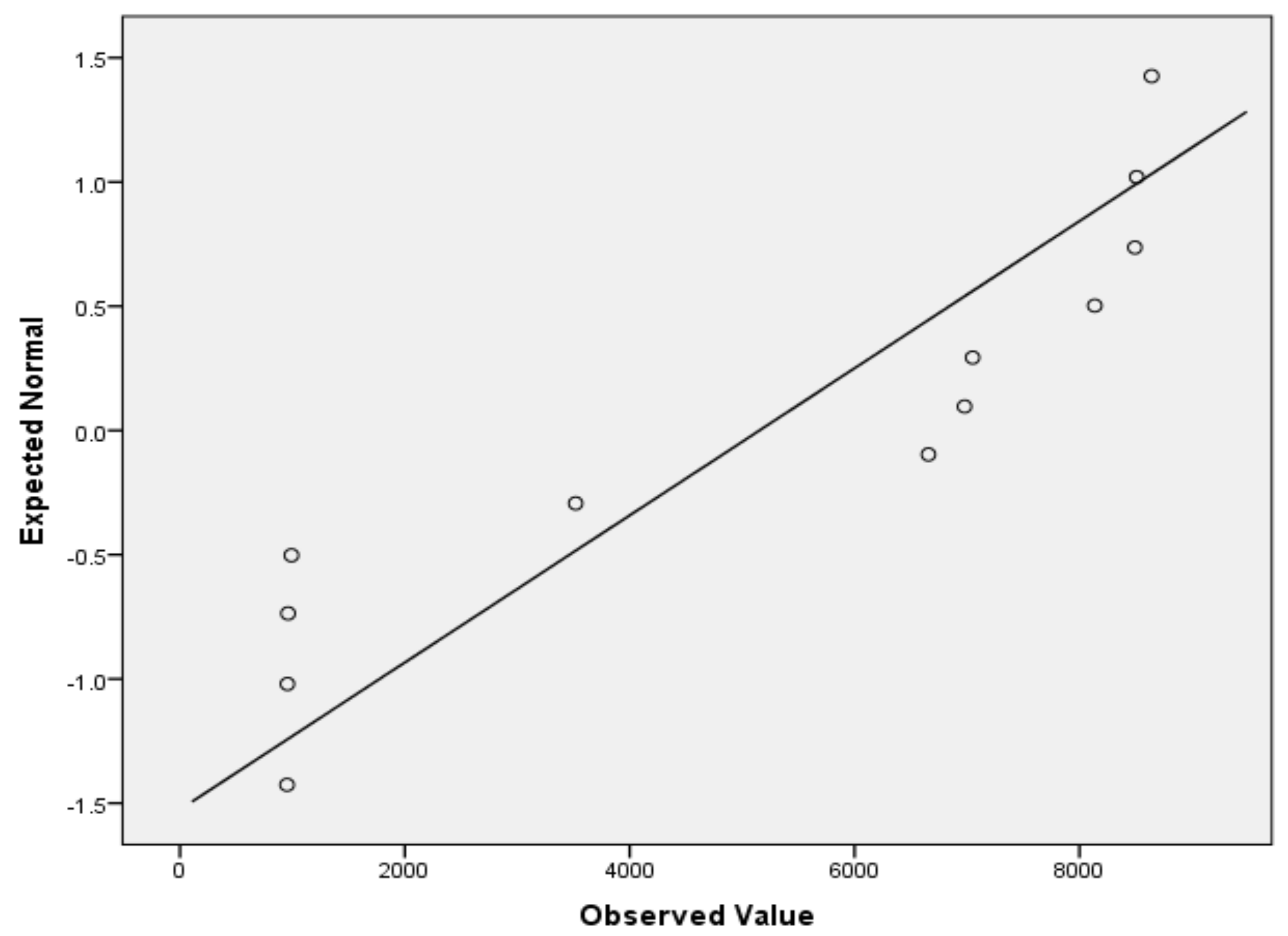






| Evaluation Number | ICM1 | ICM2 | ICM3 | ICM4 | ICM5 | ICM6 |
|---|---|---|---|---|---|---|
| ms1/ms2 | ms1/ms2 | ms1/ms2 | ms1/ms2 | ms1/ms2 | ms1/ms2 | |
| Nr1 | 1063/104 | 1050/165 | 1268/18 | 1583/22 | 1488/29 | 1093/146 |
| Nr2 | 1073/559 | 1045/115 | 1157/32 | 1709/32 | 1387/38 | 1123/226 |
| Nr3 | 1067/306 | 1094/70 | 1255/58 | 1792/22 | 1481/19 | 1184/221 |
| Nr4 | 1046/92 | 1048/131 | 1170/47 | 1645/21 | 1380/33 | 1170/68 |
| Nr5 | 3698/21 | 3906/43 | 7730/53 | 9518/18 | 8597/10 | 3628/67 |
| Nr6 | 8304/29 | 7747/64 | 9484/31 | 1381/12 | 1198/38 | 7935/53 |
| Nr7 | 7527/16 | 7384/110 | 8791/37 | 1590/27 | 1090/44 | 7860/91 |
| Nr8 | 8291/16 | 7823/93 | 9911/16 | 1423/15 | 1059/100 | 8359/87 |
| Nr9 | 8054/168 | 8930/991 | 1023/37 | 1470/17 | 1156/39 | 9123/31 |
| Nr10 | 9294/181 | 9598/41 | 1098/24 | 1424/28 | 1205/64 | 1092/290 |
| Nr11 | 1015/68 | 9427/93 | 1124/48 | 1664/43 | 1263/28 | 1023/174 |
| Nr12 | 1019/64 | 9434/182 | 1182/27 | 1377/22 | 1371/19 | 1024/68 |
| Evaluation Number | Intellig1 | Intellig2 | Intellig3 | Intellig4 | Intellig5 | Intellig6 |
|---|---|---|---|---|---|---|
| Nr1 | 967.1 | 961.5 | 1143.0 | 1426.9 | 1342.1 | 998.3 |
| Nr2 | 1021.6 | 952.0 | 1044.5 | 1541.3 | 1252.1 | 1033.3 |
| Nr3 | 990.9 | 991.6 | 1135.3 | 1615.0 | 1334.8 | 1087.7 |
| Nr4 | 950.6 | 956.3 | 1057.7 | 1482.6 | 1245.3 | 1059.8 |
| Nr5 | 3330.3 | 3519.7 | 6962.3 | 8568.0 | 7738.3 | 3271.9 |
| Nr6 | 7476.5 | 6978.7 | 8538.7 | 1244.1 | 1082.0 | 7146.8 |
| Nr7 | 6775.9 | 6656.6 | 7915.6 | 1433.7 | 985.4 | 7083.1 |
| Nr8 | 7463.5 | 7050.0 | 8921.5 | 1282.2 | 963.1 | 7531.8 |
| Nr9 | 7265.4 | 8136.1 | 924.4 | 1324.7 | 1044.3 | 8213.8 |
| Nr10 | 8382.7 | 8642.3 | 990.6 | 1284.4 | 1090.9 | 1011.8 |
| Nr11 | 920.3 | 8493.6 | 1016.4 | 1501.9 | 1139.5 | 938.1 |
| Nr12 | 923.5 | 8508.8 | 1066.5 | 1241.5 | 1235.8 | 928.4 |
| Calculus | Intellig1 | Intellig2 | Intellig3 | Intellig4 | Intellig5 | Intellig6 |
|---|---|---|---|---|---|---|
| Mean | 3872.36 | 5153.93 | 3393.04 | 1995.53 | 1704.47 | 3358.73 |
| SD | 3265.3 | 3377.76 | 3494.04 | 2073.47 | 1904.44 | 3132.09 |
| Median | 2175.95 | 6817.65 | 1100.9 | 1430.3 | 1187.65 | 1073.75 |
| Kurt | −2.1 | −1.9 | −1.4 | 11.9 | 11.9 | −1.6 |
| Skew | 0.3 | −0.4 | 0.9 | 3.4 | 3.4 | 0.7 |
| Min | 920.3 | 952 | 924.4 | 1241.5 | 963.1 | 928.4 |
| Max | 8382.7 | 8642.3 | 8921.5 | 8568 | 7738.3 | 8213.8 |
| range | 7462.4 | 7690.3 | 7997.1 | 7326.5 | 6775.2 | 7285.4 |
| CV | 84.3 | 65.5 | 102 | 103.9 | 111.7 | 93.3 |
| hom.-het. | het. | het. | het. | het. | het. | het. |
| Calculus | Intellig1 | Intellig2 | Intellig3 | Intellig4 | Intellig5 | Intellig6 |
|---|---|---|---|---|---|---|
| Lill Test | ||||||
| Lill statistic | 0.309 | 0.255 | 0.407 | 0.489 | 0.492 | 0.349 |
| Pnorm (calculated p-value) | 0.002 | 0.03 | ~0 | ~0 | ~0 | ~0 |
| Normality passed (Pnorm > αNorm) | No | No | No | No | No | No |
| SW Test | ||||||
| SW statistic | 0.753 | 0.79 | 0.666 | 0.381 | 0.389 | 0.717 |
| Pnorm (calculated p-value) | 0.003 | 0.007 | ~0 | ~0 | ~0 | 0.001 |
| Normality passed (Pnorm > αNorm) | No | No | No | No | No | No |
| Type of Calculus | Obtained Result |
|---|---|
| mean/SD/median | 2297.7/2252.1/1308.98 |
| Skew/interpretation | 2.28/highly skewed |
| kurt/interpretation | 5.28/leptokurtic |
| CV/hom-het | 98/heterogeneous |
| Performed Calculus | Lill Test | SW Test |
|---|---|---|
| Statistic | 0.355 | 0.636 |
| Pnorm (calculated p-value) | 0.017 | 0.001 |
| Normality passed (Pnorm > αNorm) | No | No |
| ICMAS | MIQ | Extreme */Furthest # | No.Id @ | Type & |
|---|---|---|---|---|
| ICM1 | 2175.95 | No/Yes | 2 | Low |
| ICM2 | 6817.65 | Yes/No | 1 | Low |
| ICM3 | 1100.9 | / | ||
| ICM4 | 1430.3 | No/Yes | 3 | Low |
| ICM5 | 1187.65 | No/Yes | 4 | Low |
| ICM6 | 1073.75 | / |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Iantovics, L.B.; Kountchev, R.; Crișan, G.C. ExtrIntDetect—A New Universal Method for the Identification of Intelligent Cooperative Multiagent Systems with Extreme Intelligence. Symmetry 2019, 11, 1123. https://doi.org/10.3390/sym11091123
Iantovics LB, Kountchev R, Crișan GC. ExtrIntDetect—A New Universal Method for the Identification of Intelligent Cooperative Multiagent Systems with Extreme Intelligence. Symmetry. 2019; 11(9):1123. https://doi.org/10.3390/sym11091123
Chicago/Turabian StyleIantovics, László Barna, Roumen Kountchev, and Gloria Cerasela Crișan. 2019. "ExtrIntDetect—A New Universal Method for the Identification of Intelligent Cooperative Multiagent Systems with Extreme Intelligence" Symmetry 11, no. 9: 1123. https://doi.org/10.3390/sym11091123
APA StyleIantovics, L. B., Kountchev, R., & Crișan, G. C. (2019). ExtrIntDetect—A New Universal Method for the Identification of Intelligent Cooperative Multiagent Systems with Extreme Intelligence. Symmetry, 11(9), 1123. https://doi.org/10.3390/sym11091123







